Cyber Operations: Security Frameworks, Legal and Ethical Issues
VerifiedAdded on 2023/04/25
|18
|4434
|292
Report
AI Summary
This report provides an overview of cyber operations, emphasizing the importance of cybersecurity in today's digital landscape. It delves into various tools and techniques used to protect data and infrastructure from cyber attacks, including firewalls, antivirus software, PKI services, managed detection services, penetration testing, and staff training. The report also examines cyber-security frameworks, legal and regulatory frameworks, compliance and enforcement frameworks, capacity building, cyber secure acculturation frameworks, and business development frameworks. Furthermore, it addresses the ethical and social implications of cyber operations, as well as relevant legal standards and practices. The document highlights the need for continuous improvement and adaptation in cybersecurity strategies to combat evolving threats, offering insights into risk assessment, emergency response, and the implementation of information security management systems (ISMS).

Running head: CYBER OPERATION
Cyber Operation
Name of the Student
Name of the University
Author Note:
Cyber Operation
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER OPERATION
Abstract
In the last few years, Cyber Security has gained huge amount of importance and has become a
common part of everyone’s life. When people provide their data through online mode, then they
become vulnerable to both cyber attacks or even cybercrimes. Cyber attacks can easily take place
on any DNS server or even internal firewall. It can turn down data and required infrastructure
within the given enterprise which can cause significant to the business of the given organization.
Cyber Security aims to offer proper security from any kind of authorized access or exploitation.
It tends to provide online services to the given data that is associated with the appliance and
network needed for communication. The overall life cycle of cybersecurity can be classified into
different stages. In the coming pages of the report, the latest technologies and techniques have
been discussed in details. A list of justification has been provided with respect to selection of
particular tools and equipments. Various issues have been discussed with respect to installation
and configuration has been discussed in details. The last section of the report deals with social or
ethical issues and standard or legal issues. Ransomware is a well-known cyber-security that tends
to affect the system and backup devices.
Abstract
In the last few years, Cyber Security has gained huge amount of importance and has become a
common part of everyone’s life. When people provide their data through online mode, then they
become vulnerable to both cyber attacks or even cybercrimes. Cyber attacks can easily take place
on any DNS server or even internal firewall. It can turn down data and required infrastructure
within the given enterprise which can cause significant to the business of the given organization.
Cyber Security aims to offer proper security from any kind of authorized access or exploitation.
It tends to provide online services to the given data that is associated with the appliance and
network needed for communication. The overall life cycle of cybersecurity can be classified into
different stages. In the coming pages of the report, the latest technologies and techniques have
been discussed in details. A list of justification has been provided with respect to selection of
particular tools and equipments. Various issues have been discussed with respect to installation
and configuration has been discussed in details. The last section of the report deals with social or
ethical issues and standard or legal issues. Ransomware is a well-known cyber-security that tends
to affect the system and backup devices.

2CYBER OPERATION
Table of Contents
Introduction..........................................................................................................................3
Literature review..................................................................................................................4
Tools and Techniques......................................................................................................4
Cyber –Security Framework............................................................................................5
Legal and Regulatory Framework...............................................................................7
Compliance and Enforcement Framework..................................................................8
Capacity building and Cyber Secure acculturation framework.................................10
Business Development Framework...........................................................................12
Conclusion.........................................................................................................................13
References..........................................................................................................................15
Table of Contents
Introduction..........................................................................................................................3
Literature review..................................................................................................................4
Tools and Techniques......................................................................................................4
Cyber –Security Framework............................................................................................5
Legal and Regulatory Framework...............................................................................7
Compliance and Enforcement Framework..................................................................8
Capacity building and Cyber Secure acculturation framework.................................10
Business Development Framework...........................................................................12
Conclusion.........................................................................................................................13
References..........................................................................................................................15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER OPERATION
Introduction
Cyber Security is nothing but a complex issue that cuts across various domains. It mainly
cuts up for multi-layer initiatives and multi-layer dimension. It aims to create challenges for
various government which is just because of various domain. It is mainly administered through
ministries and domain (Bada, Sasse and Nurse 2019). Overall development of Information
technology and its ease of application can be easily commercialized due to expansion of
cyberspace. Cybersecurity is all about protecting the required information and the given devices
from any kind of threat. It has ultimately become a part of the organization that collects and
maintains huge database for the information of customer. Apart from this, it aims to provide
social platform where required personal, as well as government information, is submitted. It
helps in describing the fact that how personal and key government information data are protected
from any kind of vulnerable attacks (Anwar et al. 2017). It can possess huge amount of threat to
information. The given information can be stored on either cloud, network, devices, and other
application. There is a need for huge amount of capital information in protecting the information
on online platform. With each passing day, the number of number of users are increasing so as a
result, the threat to information is also increasing.
The coming pages of the report a literature review has been done with cybersecurity
policies. After that, a list of technologies and techniques with respect to cybersecurity has been
discussed in details. A list of justification has been provided with respect to selection of proper
equipment and tools. A list of issues with respect to configuration and implementation has been
provided in details.
Introduction
Cyber Security is nothing but a complex issue that cuts across various domains. It mainly
cuts up for multi-layer initiatives and multi-layer dimension. It aims to create challenges for
various government which is just because of various domain. It is mainly administered through
ministries and domain (Bada, Sasse and Nurse 2019). Overall development of Information
technology and its ease of application can be easily commercialized due to expansion of
cyberspace. Cybersecurity is all about protecting the required information and the given devices
from any kind of threat. It has ultimately become a part of the organization that collects and
maintains huge database for the information of customer. Apart from this, it aims to provide
social platform where required personal, as well as government information, is submitted. It
helps in describing the fact that how personal and key government information data are protected
from any kind of vulnerable attacks (Anwar et al. 2017). It can possess huge amount of threat to
information. The given information can be stored on either cloud, network, devices, and other
application. There is a need for huge amount of capital information in protecting the information
on online platform. With each passing day, the number of number of users are increasing so as a
result, the threat to information is also increasing.
The coming pages of the report a literature review has been done with cybersecurity
policies. After that, a list of technologies and techniques with respect to cybersecurity has been
discussed in details. A list of justification has been provided with respect to selection of proper
equipment and tools. A list of issues with respect to configuration and implementation has been
provided in details.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CYBER OPERATION
Literature review
Tools and Techniques
According to (Gupta, Agrawal and Yamaguchi, 2016), there are six tools and services
which is required by various business. It mainly tends to highlight the need for overall
cybersecurity that requires to be strong as much as possible.
Firewall: With the passage of time, cybercriminals have become stronger and have a
much stronger defense. Firewall is well-known network traffic along with a connection attempts
that helps in deciding whether the traffic should freely pass the network or not (Safa, Von Solms
and Furnell 2016). There are some skilled hackers who come up with ability to create data and
programs which can even trick the firewall. They mainly assure the firewall the fact that
programs are trusted so that they can pass the firewalls with any issue. Irrespective of the
limitation, firewalls are very much effective in analyzing malicious attacks on the business.
Anti-virus Software: Antivirus Software helps in altering with respect to any kind of
virus and malware infection. It aims to provide any kind of additional information with respect to
scanning of email so they can ensure they are free from any kind of malicious attack (Carr,
2016). The present antivirus programs are considered to be very much useful for protecting
various measures like understanding potential threats along with removing them. There is large
number of antivirus software which helps in finding out the package as per the business needs.
PKI Services: There is large number of people who are associated PKI with two kinds of
things like SSL or TSL based technology. It mainly helps in encrypting server-based technology
which is totally responsible for HTTPS (Safa, Von Solms and Futcher 2016). PKI is essential in
Literature review
Tools and Techniques
According to (Gupta, Agrawal and Yamaguchi, 2016), there are six tools and services
which is required by various business. It mainly tends to highlight the need for overall
cybersecurity that requires to be strong as much as possible.
Firewall: With the passage of time, cybercriminals have become stronger and have a
much stronger defense. Firewall is well-known network traffic along with a connection attempts
that helps in deciding whether the traffic should freely pass the network or not (Safa, Von Solms
and Furnell 2016). There are some skilled hackers who come up with ability to create data and
programs which can even trick the firewall. They mainly assure the firewall the fact that
programs are trusted so that they can pass the firewalls with any issue. Irrespective of the
limitation, firewalls are very much effective in analyzing malicious attacks on the business.
Anti-virus Software: Antivirus Software helps in altering with respect to any kind of
virus and malware infection. It aims to provide any kind of additional information with respect to
scanning of email so they can ensure they are free from any kind of malicious attack (Carr,
2016). The present antivirus programs are considered to be very much useful for protecting
various measures like understanding potential threats along with removing them. There is large
number of antivirus software which helps in finding out the package as per the business needs.
PKI Services: There is large number of people who are associated PKI with two kinds of
things like SSL or TSL based technology. It mainly helps in encrypting server-based technology
which is totally responsible for HTTPS (Safa, Von Solms and Futcher 2016). PKI is essential in

5CYBER OPERATION
solving a large number of cybersecurity issues and they tend to deserve a proper place in
organization suite.
Managed Detection of Services: With the passing time, cybercriminals tend to become
very sophisticated as they are using technology and software which are advanced. So, it has
become important for business to invest in more powerful mode of defense (Carrapico and
Barrinha, 2017). Cybersecurity tends to look for technologies that can prevent the possibility of
any kind of attack. It tends to provides huge number of services which can react and react to any
kind of potential issues.
Penetration Testing: This particular testing is considered to be vital point for securing
business systems. At the time of penetration testing, there is large number of cybersecurity
professionals which makes use of techniques similar to potential vulnerabilities along with areas
of weakness (Khalili, Naghizadeh and Liu 2018). A pen test focus on attempting similar kind of
attack which is faced by business due to criminal hackers. It is mainly inclusive of various things
like password cracking and injection of code.
Staff training: Employees aims to understand the role of cybersecurity which is one of
the strongest forms to provide defense against the attacks. At present, there is large number of
training tools in which organization can invest to provide education to staff about cyber security
(Fowler et al. 2017). With the passage of time, cyber-criminals tend to expand their method of
attack so that business can make investment on the given tools and services.
Cyber –Security Framework
solving a large number of cybersecurity issues and they tend to deserve a proper place in
organization suite.
Managed Detection of Services: With the passing time, cybercriminals tend to become
very sophisticated as they are using technology and software which are advanced. So, it has
become important for business to invest in more powerful mode of defense (Carrapico and
Barrinha, 2017). Cybersecurity tends to look for technologies that can prevent the possibility of
any kind of attack. It tends to provides huge number of services which can react and react to any
kind of potential issues.
Penetration Testing: This particular testing is considered to be vital point for securing
business systems. At the time of penetration testing, there is large number of cybersecurity
professionals which makes use of techniques similar to potential vulnerabilities along with areas
of weakness (Khalili, Naghizadeh and Liu 2018). A pen test focus on attempting similar kind of
attack which is faced by business due to criminal hackers. It is mainly inclusive of various things
like password cracking and injection of code.
Staff training: Employees aims to understand the role of cybersecurity which is one of
the strongest forms to provide defense against the attacks. At present, there is large number of
training tools in which organization can invest to provide education to staff about cyber security
(Fowler et al. 2017). With the passage of time, cyber-criminals tend to expand their method of
attack so that business can make investment on the given tools and services.
Cyber –Security Framework
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
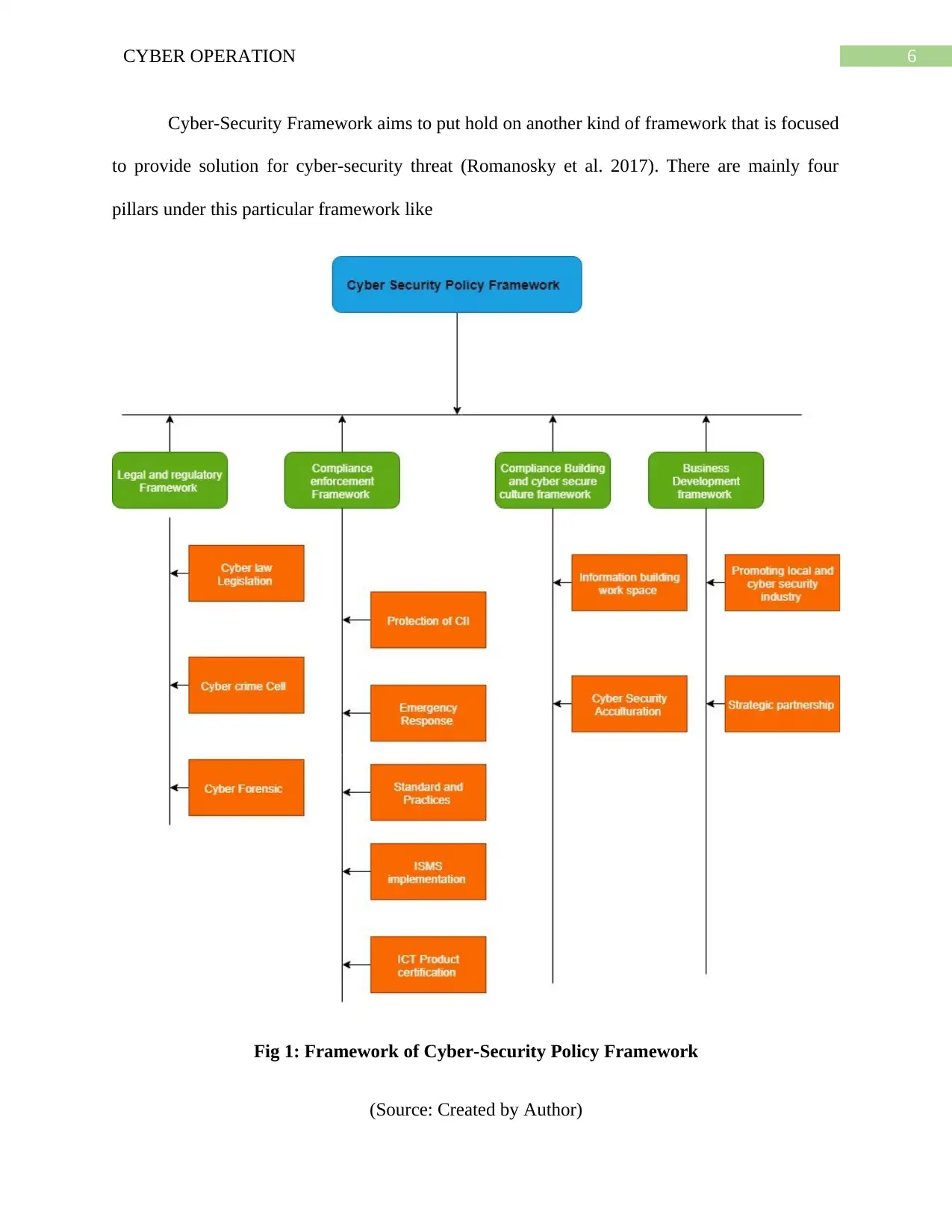
6CYBER OPERATION
Cyber-Security Framework aims to put hold on another kind of framework that is focused
to provide solution for cyber-security threat (Romanosky et al. 2017). There are mainly four
pillars under this particular framework like
Fig 1: Framework of Cyber-Security Policy Framework
(Source: Created by Author)
Cyber-Security Framework aims to put hold on another kind of framework that is focused
to provide solution for cyber-security threat (Romanosky et al. 2017). There are mainly four
pillars under this particular framework like
Fig 1: Framework of Cyber-Security Policy Framework
(Source: Created by Author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER OPERATION
Legal and Regulatory Framework
Cyberlaw and Related Legislation
The main notion of this particular framework is all about addressing specific legislation
which governs the cyberspace (Romanosky et al. 2017). It is done by various kind of
collaborative initiatives. Various government bodies have collaborated with NALSAR in the
domain of security. There is some existing framework which can identify the problem and form
proper laws for tackling real-time issues that are faced by entities (Saini et al. 2018). The
collaborative effort which is required for understanding the corner of every evolving threat.
There is some non-cyber specific legislation that is specific to cyberspace activity. It is used for
protection of various aspects like copyright, defamation and national security. It is needed for
addressing and protecting information which will help in flow of information on the internet.
Cybercrime Cells
There are different kind of government bodies that are specialized for cybercrime cell
into proper complaints. It can penetrate to offense under the given information technology Act.
Government has fully strengthened the simplify reporting and tracking process of cyber-crimes
(Xu 2015). Different government bodies around the globe have come proper plan for tackling
cyber-bullying. The cybercrime will focus on the crimes that are taking place at present.
Cyber Forensic
Various government bodies have come up with plan of investigating and analyzing any
kind of cybercrimes. It will ultimately help in recovery and preserving the overall digital
presence. In the coming years, there will be data recovery plan to recover data which have may
Legal and Regulatory Framework
Cyberlaw and Related Legislation
The main notion of this particular framework is all about addressing specific legislation
which governs the cyberspace (Romanosky et al. 2017). It is done by various kind of
collaborative initiatives. Various government bodies have collaborated with NALSAR in the
domain of security. There is some existing framework which can identify the problem and form
proper laws for tackling real-time issues that are faced by entities (Saini et al. 2018). The
collaborative effort which is required for understanding the corner of every evolving threat.
There is some non-cyber specific legislation that is specific to cyberspace activity. It is used for
protection of various aspects like copyright, defamation and national security. It is needed for
addressing and protecting information which will help in flow of information on the internet.
Cybercrime Cells
There are different kind of government bodies that are specialized for cybercrime cell
into proper complaints. It can penetrate to offense under the given information technology Act.
Government has fully strengthened the simplify reporting and tracking process of cyber-crimes
(Xu 2015). Different government bodies around the globe have come proper plan for tackling
cyber-bullying. The cybercrime will focus on the crimes that are taking place at present.
Cyber Forensic
Various government bodies have come up with plan of investigating and analyzing any
kind of cybercrimes. It will ultimately help in recovery and preserving the overall digital
presence. In the coming years, there will be data recovery plan to recover data which have may

8CYBER OPERATION
become corrupted (Liu et al. 2015). This might become as a result of any kind of cybercrime.
With respect to building efforts, there is a need for data experts that can handle forensic and
related requirements. By the help of digital evidence, there is a need for preservation facility that
aims to create secure environment for retaining digital evidence.
Compliance and Enforcement Framework
Protection of CII
Absolute security can be considered as a mere concept only but it cannot be achieved
practically irrespective of resources that are invested. By the help of risk-based approach, a
proper priority is given on the risk. In the coming years, government aims to come up with
information protection plan which is in collaboration with private sector (Knowles et al. 2015). It
can be carried out by the help of risk-based analysis approach. Proper facilitating of cooperation
and collaboration against the given security threats can be achieved at the highest level (Fowler
et al. 2017). The government aims to comes up with proper policies and procedures which is
needed for policy and decision and inputs.
Emergency Response
Government bodies have come up with T-CERT which is a nodal agency for
coordinating with various institutes and organization. T-CERT aims to contribute to safety zone
which is all about providing much safer and stronger internet based connection (Spear, 2015). It
can be achieved by responding to threats and exchange of cybersecurity information with the
partners. The main highlighting points of T-CERT are
become corrupted (Liu et al. 2015). This might become as a result of any kind of cybercrime.
With respect to building efforts, there is a need for data experts that can handle forensic and
related requirements. By the help of digital evidence, there is a need for preservation facility that
aims to create secure environment for retaining digital evidence.
Compliance and Enforcement Framework
Protection of CII
Absolute security can be considered as a mere concept only but it cannot be achieved
practically irrespective of resources that are invested. By the help of risk-based approach, a
proper priority is given on the risk. In the coming years, government aims to come up with
information protection plan which is in collaboration with private sector (Knowles et al. 2015). It
can be carried out by the help of risk-based analysis approach. Proper facilitating of cooperation
and collaboration against the given security threats can be achieved at the highest level (Fowler
et al. 2017). The government aims to comes up with proper policies and procedures which is
needed for policy and decision and inputs.
Emergency Response
Government bodies have come up with T-CERT which is a nodal agency for
coordinating with various institutes and organization. T-CERT aims to contribute to safety zone
which is all about providing much safer and stronger internet based connection (Spear, 2015). It
can be achieved by responding to threats and exchange of cybersecurity information with the
partners. The main highlighting points of T-CERT are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CYBER OPERATION
Providing cybersecurity action to government, agencies, private industries and general
public by the help of advisories.
Providing protection of cybersecurity protection by the help of intrusion detection and
capabilities for prevention (Khalili, Naghizadeh and Liu 2018).
Increasing overall security measures so that they increase awareness of information
security along with understanding the computer security issues.
Standard and Practices
By the help of partnership of private players, government can create proper infrastructure.
It aims to set up information sharing and analysis center for providing proper actionable
information (Bagheri et al. 2016). It is all about analyzing trends by which they can find out
threats and opportunities. It is mainly inclusive of large number of points like
Development and implementation of proper information security standard
Development of information security guidelines along with understanding proper
practices.
ISMS Implementation
Government bodies need to encourage the overall adaptation of ISMS in various
organization around the globe. Apart from this, government bodies need to understand the
potential of having ISMS initiative that will call both small and medium scale organization
(Gove 2016). It will ultimately focus on practical governance and issues in different system
taking account of business and challenges associated with it. It might not address the technical
problem associated with it.
Providing cybersecurity action to government, agencies, private industries and general
public by the help of advisories.
Providing protection of cybersecurity protection by the help of intrusion detection and
capabilities for prevention (Khalili, Naghizadeh and Liu 2018).
Increasing overall security measures so that they increase awareness of information
security along with understanding the computer security issues.
Standard and Practices
By the help of partnership of private players, government can create proper infrastructure.
It aims to set up information sharing and analysis center for providing proper actionable
information (Bagheri et al. 2016). It is all about analyzing trends by which they can find out
threats and opportunities. It is mainly inclusive of large number of points like
Development and implementation of proper information security standard
Development of information security guidelines along with understanding proper
practices.
ISMS Implementation
Government bodies need to encourage the overall adaptation of ISMS in various
organization around the globe. Apart from this, government bodies need to understand the
potential of having ISMS initiative that will call both small and medium scale organization
(Gove 2016). It will ultimately focus on practical governance and issues in different system
taking account of business and challenges associated with it. It might not address the technical
problem associated with it.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CYBER OPERATION
ICT Security Certification
Government bodies aim to create ICT security assessment facility where there can be
product certificate compliance (Alotaibi, Furnell and Clarke 2016). It is mainly done for various
sensitive products of ICT which is linked both directly and indirectly. Facilities will be provided
to another kind of services also like:
Both penetration testing and vulnerability testing can be done for the security assessment
for given control system.
ICT product security and required certification of services.
Evaluation of common criteria.
Common criteria for given information technology as known as common criteria model is
a well-known standard for security certification of computer. Common criteria are used by
government-driven certification and product testing and evaluation. It will be mainly conducted
through government agencies and critical infrastructure (Tsigkanos et al. 2018). Various
government bodies are also focusing on to introduce any kind of security kite-marks that will
help both individual and organization in identifying security products. In the coming days,
certification of both cybersecurity products and ICT products will be considered to be
mandatory.
Capacity building and Cyber Secure acculturation framework
Information Security Workforce Capacity Building
Different government bodies need to encourage, develop training programs so that they
can increase cyber-security awareness among the organization. Government aims to play a key
ICT Security Certification
Government bodies aim to create ICT security assessment facility where there can be
product certificate compliance (Alotaibi, Furnell and Clarke 2016). It is mainly done for various
sensitive products of ICT which is linked both directly and indirectly. Facilities will be provided
to another kind of services also like:
Both penetration testing and vulnerability testing can be done for the security assessment
for given control system.
ICT product security and required certification of services.
Evaluation of common criteria.
Common criteria for given information technology as known as common criteria model is
a well-known standard for security certification of computer. Common criteria are used by
government-driven certification and product testing and evaluation. It will be mainly conducted
through government agencies and critical infrastructure (Tsigkanos et al. 2018). Various
government bodies are also focusing on to introduce any kind of security kite-marks that will
help both individual and organization in identifying security products. In the coming days,
certification of both cybersecurity products and ICT products will be considered to be
mandatory.
Capacity building and Cyber Secure acculturation framework
Information Security Workforce Capacity Building
Different government bodies need to encourage, develop training programs so that they
can increase cyber-security awareness among the organization. Government aims to play a key

11CYBER OPERATION
role in forensic and provide cybersecurity-related services. It will ultimately create tool which
will help cyber-security experts so that they can provide proper services. Government bodies
need to develop proper certification by collaboration with various academic institutes. It is
mainly done so that they can encourage students to sign up for the programs (Thuraisingham et
al. 2016). TASK aims to provide different kind of assistance for recruitment to private sectors
that will ultimately reduce on-boarding cost for employers. Apart from this, various government
bodies have come up center of excellence which is in association with college for higher degree.
It is mainly done so that they can boost research in various domain of cyber-security.
Government plans to launch some particular R&D projects which is much similar to challenges
that are faced by government (Carrapico and Barrinha, 2017). It also needs to address the given
centers. In the upcoming years, there is a need for a pool of ‘cyber warriors’ that are trained in
cyber security which will work as part-time security consultant.
Cyber Security Acculturation
In the upcoming years, the state expects to launch a multi-wide channel awareness
campaign that requires involvement of digital media and social. It mainly focuses on creating
cyber-security awareness among people. Cyber-security will play a key role in understanding
digital education (Toch et al. 2018). Government bodies are planning to modify the schools due
to cyber-security for the children. The program can be deployed along with school literacy. Apart
from this, government is planning to launch a program which is accessible to children to deal
with issues like privacy and theft. With the passage of time, number of human interaction is
being shifted to online mode. There is an importance of good and acceptable behavior which will
be outlined to behavior mode (Safa, Von Solms and Futcher 2016). By the help of collaboration
role in forensic and provide cybersecurity-related services. It will ultimately create tool which
will help cyber-security experts so that they can provide proper services. Government bodies
need to develop proper certification by collaboration with various academic institutes. It is
mainly done so that they can encourage students to sign up for the programs (Thuraisingham et
al. 2016). TASK aims to provide different kind of assistance for recruitment to private sectors
that will ultimately reduce on-boarding cost for employers. Apart from this, various government
bodies have come up center of excellence which is in association with college for higher degree.
It is mainly done so that they can boost research in various domain of cyber-security.
Government plans to launch some particular R&D projects which is much similar to challenges
that are faced by government (Carrapico and Barrinha, 2017). It also needs to address the given
centers. In the upcoming years, there is a need for a pool of ‘cyber warriors’ that are trained in
cyber security which will work as part-time security consultant.
Cyber Security Acculturation
In the upcoming years, the state expects to launch a multi-wide channel awareness
campaign that requires involvement of digital media and social. It mainly focuses on creating
cyber-security awareness among people. Cyber-security will play a key role in understanding
digital education (Toch et al. 2018). Government bodies are planning to modify the schools due
to cyber-security for the children. The program can be deployed along with school literacy. Apart
from this, government is planning to launch a program which is accessible to children to deal
with issues like privacy and theft. With the passage of time, number of human interaction is
being shifted to online mode. There is an importance of good and acceptable behavior which will
be outlined to behavior mode (Safa, Von Solms and Futcher 2016). By the help of collaboration
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



