NIT6042 Thesis 2: IAAS Cloud Scheduling Algorithms Workflow Efficiency
VerifiedAdded on 2023/02/01

Determine the workflow efficiency of
scheduling algorithms/techniques in
IAAS in the cloud computing
Full Name
Student ID
Submitted for unit NIT6042 (Thesis 2)
Date
Paraphrase This Document

ABSTRACT
Current research is about Cloud computing where the efficiency of the scheduling the
technique will check by researcher whether these algorithms are efficiently increases the
workflows of an organization. Along with the concept of IAS and the cloud computing will
also explain in detail to give a short idea in the initial phase.
The purpose of this research study is to increase the recognition of cloud computing
the technical and non-technical users who do not know about IT terminologies. the
emergence of cloud computing will make their life easy as this is very flexible and cost
efficient the software which will increase the productivity of the business and the normal
individual.
Inductive research approach follows by the researcher for this study as this involves
formulating aims and the objectives of the research. Experimental research design is
preferred by a user as this involves physical experiments to compare the existing and the
current scheduling algorithms. Quantitative research technique is involved as monetary data
collected by an individual will test by applying statistical tools in the MS excel in the data
analysis section using descriptive statistics.
The results of this research will favour the aim of this research by affirming the
efficient of the scheduling techniques or algorithms in IAAS. The results show that the
application software’s is also an efficient technique of cloud computing better than the IAAS.
It is concluded that the information includes in this study will help future scholars in
accomplishing their needs in the future period.

TABLE OF CONTENTS
1.0 INTRODUCTION................................................................................................................6
1.1 Background.......................................................................................................................6
1.2 Aim and objectives...........................................................................................................6
1.3...........................................................................................................................................7
Problem statement..................................................................................................................7
Motivation..............................................................................................................................7
1.4 Contributions....................................................................................................................7
1.5 Importance of research topic............................................................................................8
1.6 Proposed methodologies...................................................................................................8
1.7 Structure of the thesis.......................................................................................................8
2.0 LITERATURE REVIEW...................................................................................................10
2.1 Literature review............................................................................................................10
2.1.1 Determine the concept of IAAS in cloud computing..............................................11
2.2.2 Explore the efficient workflow scheduling in IAAS in cloud computing...............12
2.3.3 Analyse the efficient workflow scheduling in IAAS in cloud computing...............13
2.2 Conceptual Framework..................................................................................................14
3.0 RESEARCH METHODOLOGY.......................................................................................17
3.1 Research problem and questions....................................................................................17
3.2 Research Approach.........................................................................................................17
3.3 Research Design.............................................................................................................19
3.4 Research technique.........................................................................................................21
3.5 Data collection................................................................................................................21
3.6 Sampling.........................................................................................................................21
3.7 Ethical consideration......................................................................................................22
4.0 EXPERIMENTS AND DATA ANALYSIS......................................................................22
4.1 Experimental design.......................................................................................................22
4.2 Comparison of existing and current techniques.............................................................25
4.3 Data collection................................................................................................................28
4.4 Data analysis...................................................................................................................28
5.0 RESULTS..........................................................................................................................29
5.1 Presentation of results.....................................................................................................29
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

5.2 Discussion.......................................................................................................................34
6.0 CONCLUSION..................................................................................................................35
7.0 REFERENCES...................................................................................................................36
Paraphrase This Document

INDEX OF TABLES
Table 5 Global public cloud service revenue forecast...........................................................................31
Table 6 Cloud categories.....................................................................................................................32
Table 8 Cloud Market revenue in Billions of dollars...........................................................................33
INDEX OF FIGURES
Figure 1 Variable relationship............................................................................................................15
Figure 2 task scheduling......................................................................................................................24
Figure 3 Priority of work based on deadlines.....................................................................................25
Figure 6 Global public cloud..............................................................................................................32
Figure 7 Cloud categories...................................................................................................................33
Figure 9 Cloud market revenue...........................................................................................................34

1.0 INTRODUCTION
1.1 Background
Current research is about the scheduling techniques of IAAS in cloud computing as the
researcher will perform this study in knowing that these techniques are workflow efficient or
not. This thesis will contribute is spreading the knowledge about cloud computing with the
help of this study a majority of the users do not aware of this concept. The detailed
description of cloud computing and its kinds explains in this assignment. Bu knowing about
cloud computing and its several variants, an individual will also know about its importance in
an organisation that what is the worth of this tool in a normal daily routine of an organization.
An activity is compared with each other to know what changes witnessed in an entity by
using cloud computing and not using it.
Along with the explanation of the cloud computing and IAAS, an investigator will
also draw light in the wide applications and uses of the cloud computing in an organization to
inspire non-users of this tool to include in their daily routine to smoothens its work
functioning. This tool is apt for the business professionals and the normal people. The
importance of identifying the scheduling algorithm for this research has a dual objective for
an entity such as this will helps in determining the workflow efficiency of these tools along
with the management of the business activities by utilizing these methods in an entity using
IAAS aspects.
1.2 Aim and objectives
The objectives or goals develop by an individual for conducting its research that works as
guiding paths to accomplish the same in a desired period of time. This will include several
objectives develops by a researcher is mention below:
Aim
To determine the workflow efficiency of the scheduling techniques or algorithms in
infrastructure as a service in cloud computing.
Objectives
To show the concept of IAAS(service clouds) in cloud computing
To determine the efficient workflow scheduling in IAAS in cloud computing
To analyze the efficiency of the workflow scheduling in IAAS in cloud computing.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1.3
Problem statement
Let’s talk about the generation of the idea or using this topic as a primary aim of this
research to increase the recognition of the entire Information technology environment and
spreading the knowledge of IAAS and the cloud computing field among the users (Mishra,
Sahoo and Parida, 2018). Target users of this research consist of business professionals,
normal individuals, It users, software developers, UT students, Tech savvy to get the latest
information and the facts regarding this research (Abdelaziz, Elhoseny, Salama and Riad,
2018, pp.117-128). The idea generates for this research from a research article addressing the
emergence of the cloud computing in the current IT sector with a question that ‘Are there
challenges in the IT sector due to the introduction of the cloud computing’ (Alkhanak and
Lee, 2018, pp.480-506). Due to this question, the researcher considers the topic of cloud
computing for performing this thesis. The scope of cloud computing is secondary for this
study as the focus of an examiner lies in analysing the scheduling algorithms in the IAAS
(Wang and Gelenbe, 2018, pp.33-45).
Motivation
The researcher gets motivation for conducting this researcher after reading several
articles on the cloud computing and the IAAS to know the flexibility and cost benefits of this
tool as this mode helps a user’s in accessing the information using the virtual machines (Li,
Lu, Misic and Mahmoud, 2018, pp.4-6). In the traditional sense, where a user need to meet
the hardware and the software requirements before installing any software’s but in this
approach, there is no such requirements which makes easy for a user to accomplish their
work on time.
1.4 Contributions
It is important to know various contributions of this research study to reflect its
significance in front of the final users who utilizes the information lies in this study (Hu,
Ning, Qiu, Xu, Luo and Sangaiah, 2018, pp.582-592). The current research topic is about the
exploration of the cloud computing concept by knowing the work efficiency of the
scheduling algorithms in IAAs. This research gives advantages to the majority of the users
such as research scholars, IT users, IT scientist, Technical students, Normal individual, and
technology surveyors (Zhang,Yang, Chen, Li and Bu, 2018). All these users conduct research
studies and the surveys in knowing the latest information about the technology and the
Paraphrase This Document

information technology sector to increase the recognition of the same in the external
environment.
1.5 Importance of research topic
By explaining the importance or the significance of the current research topic, it is
also important to explain its worth for the business and the normal people in the external
entity (Gai, Qiu, Zhao and Sun, 2018, pp.60-72). The significance of this research reflects its
meaning in the aim itself. The research aim is segregated to identify the three elements
involved in its scheduling algorithms, IAAS and cloud computing. With the help of this
research, the latest trends of all these components of research will explain in detail by a
researcher (Kaur, K., et al., 2018, pp.44-51).
1.6 Proposed methodologies
The inductive research approach will use for performing the entire research as the
nature of the study demands the identification of the scheduling techniques in the service
clouds. In fulfilling this need, research questions developed by an entity. The experimental
research design will consider as the experiments performed by a user in comparing the
existing and proposed scheduling techniques. Quantitative research techniques and secondary
collection of the data will prefer to assess the collected data using the statistical tools.
1.7 Structure of the thesis
ABSTRACT
First and the foremost section of this dissertation which is a summary of an entire
research study adding the crux of all the research chapters to get a brief idea of what will
cover in the thesis. The context of research will include in the abstract part. After discussing
the research context, the objective or purpose of this research will include in the executive
summary to allow all its users in knowing the intention of this study to analyse the further
results of the study in advance. The brief research methodology will also cover in the abstract
part. The results ads the conclusion part will also cover in the executive summary to give a
complete summary of an entire dissertation in the initial part itself.
INTRODUCTION
After the executive summary, the next step is the introduction chapter of a dissertation
which will give the detailed introduction of this research topic by discussing the entire
research issue. A researcher will categorize the entire introduction section into various parts

such as background, aims and objectives, motivation to research, idea generation,
contribution and significance to this research study (Fu, Liu, Chao, Bhargava and Zhang,
2018, pp.4519-4528). The information included in the introduction chapter guides a user
about the fundamental of this thesis as what triggers an individual to use this topic for
research to allow other scholars in performing their study by following the process of
selecting a topic.
LITERATURE REVIEW
The literature review will include the inclusion of the secondary information used in
the past published research studies in the current study based on the research objectives. This
will also include the conceptual framework and the other related studies similar to the current
research issue (Yu, R., et al., 2018, pp.72-84). The conceptual framework will explain the
dependent and the independent variables to the research to know the cause root behind the
research problems. The other related study which is similar to the current research study is
discussed with this study to know the inter-relationship between the previous studies with the
current study.
RESEARCH METHODOLOGY
An examiner follows a systematic process of selecting the best suitable methodology
in conducting the entire research consist of identifying the research issue and questions to
research, selecting research approach, designs techniques and finally including the ethical
considerations (Yu, R., et al., 2018, pp.72-84). A user puts a great emphasis on the
methodology chapter as this will consider as an important chapter of a dissertation that guides
an individual in collecting suitable data and facts to proceed with the current research. This
will also include the data collection approaches and the sampling methods to move
systematically in collecting the information related to the research.
EXPERIMENTS
The physical experiments conducted by a researcher in testing the efficiency of the
scheduling techniques or algorithms of IAAS in the cloud computing system by explaining
the variables, metrics, objectives and the parameters used in analysing all the techniques
(Yan, Yu and Long, 2019, pp. 679-681).
RESULTS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

This will include the overall summary of the research, crux of the data used in a
research which will present in the form of figures and the tables to seek the instant feedback
of its users in the business meetings (Liu, Deng, Yang, Tran and Zhong 2018, ). Further, the
data interpretations will help in understanding the trends and the patterns of the data.
CONCLUSION
In the conclusion of the research, a scrutinizer will summarise the information from
all the chapters and give emphasis on the recommendation or solutions proposed for the
research issues (Wang, Wang and Domingo-Ferrer, 2018, pp.712-719). This will consist of
the summary of the research study and the future opportunity for all the users who get enough
benefits from this particular research study.
2.0 LITERATURE REVIEW
2.1 Literature review
Important source of a secondary data collection where a previous gap lies in the study
will get fulfilled in the research study. Similar or exact studies of scholars or authors utilize
as a benchmark in performing the literature review to meet the entire objectives (Zhang,
Deng, Liu and Zheng, 2018, pp.262-277). In this research thesis, ‘A’ rated previous research
published papers taken from authentic sources such as IEEE, ACM and ELSEVIER to ensure
the validity of the information used for this study. These sources consider as an important
source to give cent per cent assurance to the client about the high quality of the information
to be used in compiling the current dissertation.
Below mention literature review chapter of this dissertation will highlight several
concepts of cloud computing and infrastructure as a service as one of a platform of this tool.
Secondly, the study also explains the scheduling technique in the Infrastructure as a service
and to test its efficiency by analysing all the techniques using several parameters to the
research. Majority of people do not know about cloud computing so this study will contribute
to adding value for all the users in getting a new learning experience about this concept
(Muhammad, Alhamid, Alsulaiman and Gupta, 2018, pp.60-65). The concept of IAAS is also
Paraphrase This Document

new for the non-technical users as this study targets the entire technical as well as the
technical users in knowing about these terms in detail.
2.1.1 Determine the concept of IAAS in cloud computing
(Stergiou, Psannis, Kim and Gupta, 2018, pp.964-975), has asserted that cloud
computing is consider as a latest IT tool to offer reliable services to all the users. The problem
of data confidentiality will get eliminated due to the emergence of this system. In this system,
a user will store its information using the internet as data will store in the clouds to avoid its
stealing and will, in turn, increases the quality of the data. With the introduction of this
concept, this has increased the recognition of the entire information technology environment
among the external market. The exciting things about this system that it is very cost efficient
as a user will only pay on a pay per click as they will not get charged for installing the
software. This allows all the users to access the software’s remotely from any locations to
complete their work in less time as compared to other modes which are very expensive and
requires more time in accessing the information.
Secondary the aspect of this research study is infrastructure as a service as one of an
important tool of cloud computing. This kind of cloud computing eliminates the biggest
problem faces by a user in installing the software such as MS The project, MS office,
Architectural suites in accomplishing their work (Varghese and Buyya, 2018, pp.849-861).
To eradicate all these issues, infrastructure as a service concept introduces as a tool of cloud
computing to provide infrastructure in the form of software. Under this concept, an individual
will pay for the infrastructure they want to use and then remotely access the software’s on
their screen without purchasing the same (Shaik and Baskiyar, 2018, pp. 202-207). This will
minimize the overall risks such as errors in the software’s faces by a user after taking the
license of a system, complicated licenses, and expensive software’s. All these risks will
overcome by this mode by introducing a unique opportunity.
Different packages offer by the cloud computing services companies consisting of a
public, private and hybrid network that differ according to the nature of work, costing and
confidentiality and the storage requirements (Khan, Rehman, Al-Khatib, Anwar and Alam,
2018, ). Companies such as Microsoft and Google offer his cloud computing in which a user
will get the login credentials to access the information along with the virtual storage drive in
the clouds server that is through the help of internet. The system requirements such as

software and hardware requirements will control by a user in this mode as this is a virtual
system that allows all the users in fulfilling their requirements.
2.2.2 Explore the efficient workflow scheduling in IAAS in cloud computing
According to the view of Nunes, Roque, Araújo and Pereira 2018,), that says that the
round-robin scheduling method utilizes a technique to properly allocate the time to all the
activities. This method is termed as resource allocation method helps in allocating
appropriate resources to all the users to meet the requirements in a stipulated time. To survive
in the external environment, it is essential for an entity to understand the importance of the
time for which this process is used to meet the project objectives within a given time period.
(Kadri and Boctor, 2018, pp.454-462), says that genetic Algorithm uses by an individual in
the infrastructure as a service for task scheduling as the workload gets reduces by applying
this technique. By scheduling the overall tasks, it will get easy for a user to access the
information stored from the cloud to the virtual machine. Admin department will track the
usage of the information stored on the clouds using this algorithm in knowing the
decentralization of a project into tasks. It is considered as an output of progressive growth of
artificial intelligence.
As per the viewpoint of (Li, Ge, Hu, Song, Hu and Luo, 2018, ), that observes that the
minimum execution time algorithm is a unique way of task scheduling approach whose main
motive is to reduce the execution time in the cloud computing processes. Execution strategy
develops by an entity to keep track of all the project activities to accomplish all the activities
of a project in a stipulated time period. The motive of this algorithm is to reduce the makes
pan, costs and increase the resource utilization frequency to maintain the quality of the data.
(Ziaeinejad and Mehrizi-Sani, 2019, pp.4166-4176), has asserted that the switching
algorithm allows a user to switch from the data centre to another in case of network errors or
bug lies in one virtual machine. As using this way, the loopholes lie in one machine will not
affect other virtual machines and a user will continue to access the information without any
kind of hindrances. This will allow a user to switch from one task to another without starting
the whole process from the beginning as they also easily terminate the tasks in case of no
need.
According to the view of (Rasheed, et al., 2019, pp.23990-24006), that says that the
opportunistic load balancing system under which the workload of one server will shift to the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

multiple channels to maintain the smooth running of an entire system. This system will also
help in minimizing the costs of documentation and enhances the availability of the resources.
The efficiency of a user will get increases as this method will work automatically in getting
rid of all the issues easily.
2.3.3 Analyse the efficient workflow scheduling in IAAS in cloud computing
According to the opinion of (Liu et al., 2019), that says that the efficiency of the
scheduling algorithms will assess by identifying the parameters or criteria’s of these
algorithms. Majority of the scheduling algorithms are task scheduling techniques whose
motive is to reduce the workload by distributing the entire information stored in the clouds
and the data centres into different tasks to help a user n accessing the same. The efficient of
all these workflow techniques reflects its significance through all the criteria’s use as a
weapon to tests that the scheduling techniques are efficient or not. The efficiency of the
technique identifies by an individual by knowing its positive or negative impact on the
organization with the use of the algorithms (Adhikari and Amgoth, 2019, pp.547-566). Every
entity uses these algorithms in the infrastructure as a service to reduce its workload and
maintain the quality of the work.
Five of the existing scheduling algorithms used for this research such as round robin,
genetic algorithm, switching algorithm, minimum execution time and opportunistic load
balancing. Three criteria or parameters used in all these scheduling techniques are resource
allocation, task distribution and time allocation among the activities (Abdullahi, Ngadi,
Dishing and Ahmad, 2019, pp.60-74). These three parameters analyses to determine whether
these methods are efficient or inefficient.
Main motto of the resource allocation in cloud computing includes three things which
need to be fulfil by the scheduling techniques related to task scheduling. This consists of
improving the utilization of the resources, decreasing the excess consumptions of the
resources and lastly enhances energy savings. By meting all these requirements the
scheduling techniques will consider as an efficient otherwise, this will considers as an
inefficient technique (Rittinghouse and Ransome, 2016). An efficient method will not useful
for an entity so this should be eliminated from an entity as this will affects the overall
performance of the organization and also creates problems and hindrances in operating the
infrastructure as a service in the cloud computing.
Paraphrase This Document

Talking about the task distribution, some of the criteria’s or objectives to be followed
by the techniques covering under the head of task scheduling comprises of proper distribution
of tasks, clarity of tasks from user to the virtual machine, achieving a task in a stipulated
deadline (Malawski, Juve, Deelman and Nabrzyski, 2015, pp.1-18).
The last measure to tests eth workflow the efficiency of the algorithm is the time of
implementing a project in an entity as a motive of a user behind this is to check how
efficiently a project will get executed to determine the end results (Mishra, Khan, Sahoo and
Jena, 2017, pp. 715-720).
2.2 Conceptual Framework
(Prabhakaran, Balamurugan and Charanyaa, 2015, pp.77-84), says that a conceptual
framework is nothing but an important part of the literature review as the theory in the
conceptual framework develops by considering the information discussed in the literature
review. This theory will help its audiences in knowing a brief idea about the variables to the
research and to know the relationship among them. The motive of this framework is to list the
entire dependent and the independent variables to the research by creating a positive or
negative relationship among them.
The theme of this research is to check and explain the workflow efficiency of the
scheduling algorithms involves in the infrastructure as a service in cloud computing. In this
research, the aim of a research itself describes three different concepts such as describing the
scheduling algorithms, infrastructure as a service and finally the wide and broad concept of
cloud computing (Lin and Wu, 2013, pp. 90-99). All these elements are inter-related with
each other as efficiency or inefficiency of scheduling algorithms will directly affect the
infrastructure as a service as thee techniques are an integral part of IAAS. Favourable or
unfavourable condition of IAAS will directly affect cloud computing as it is associated with
each other.
Dependent variable
Infrastructure as a service
Cloud computing
Independent variable
Scheduling technique
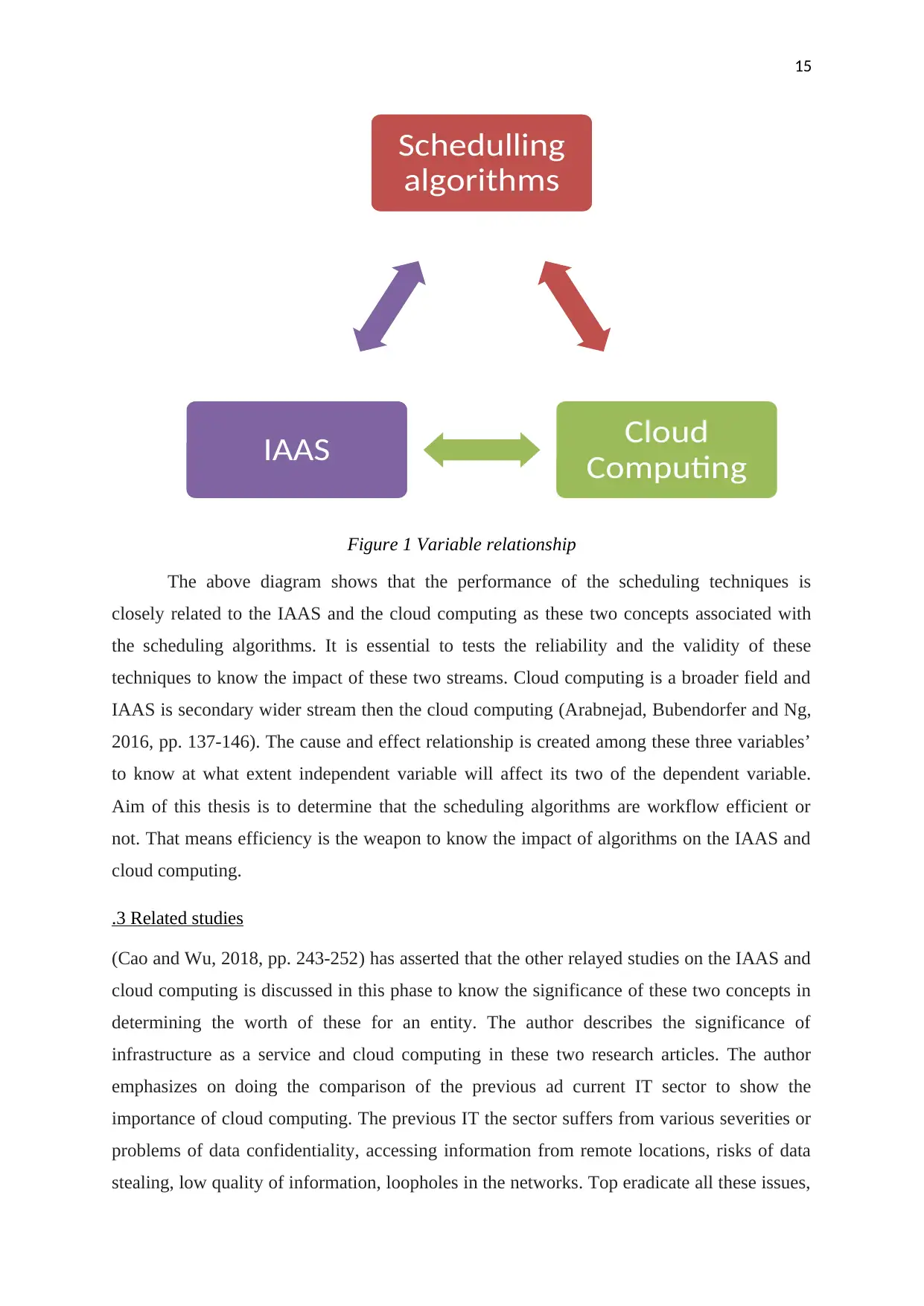
Figure 1 Variable relationship
The above diagram shows that the performance of the scheduling techniques is
closely related to the IAAS and the cloud computing as these two concepts associated with
the scheduling algorithms. It is essential to tests the reliability and the validity of these
techniques to know the impact of these two streams. Cloud computing is a broader field and
IAAS is secondary wider stream then the cloud computing (Arabnejad, Bubendorfer and Ng,
2016, pp. 137-146). The cause and effect relationship is created among these three variables’
to know at what extent independent variable will affect its two of the dependent variable.
Aim of this thesis is to determine that the scheduling algorithms are workflow efficient or
not. That means efficiency is the weapon to know the impact of algorithms on the IAAS and
cloud computing.
.3 Related studies
(Cao and Wu, 2018, pp. 243-252) has asserted that the other relayed studies on the IAAS and
cloud computing is discussed in this phase to know the significance of these two concepts in
determining the worth of these for an entity. The author describes the significance of
infrastructure as a service and cloud computing in these two research articles. The author
emphasizes on doing the comparison of the previous ad current IT sector to show the
importance of cloud computing. The previous IT the sector suffers from various severities or
problems of data confidentiality, accessing information from remote locations, risks of data
stealing, low quality of information, loopholes in the networks. Top eradicate all these issues,
Schedulling
algorithms
Cloud
Computing
IAAS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

cloud computing concept introduces by companies such as Microsoft ad Google to allow its
users to save their important data on the clouds with the help of internet source and to access
their information anytime and anywhere (Li, Ge, Hu, Song, Hu and Luo, 2018, pp.713-726 ).
A user can remotely access their information from all across the world by simply using the
login credentials. The problem of storage will get decreases with the introduction of this tool
that allows its users to virtually store the data on the clouds servers.
After drawing the comparison among the previous and the current information
technology environment, several things comes up in the bigger picture that cloud computing
decreases the risk of breaching the confidentiality, low quality of information, lack of latest
gadgets and technologies, storage requirements, operating system requirements, cost and
affordability issues, complex legal regulations and the licensing requirements (Wang and Lu,
2013, pp.2210-2223). By considering the severity of all these problems, cloud computing
develops by a developer to get rid of all the issues and increase the recognition of the entire
IT environment among the technical and non-technical users. The cloud computing is for
both the IT and non-IT users as can they can simply use this tool in meeting their
requirements related to the software’s and accessing the information.
Paraphrase This Document

3.0 RESEARCH METHODOLOGY
3.1 Research problem and questions
Research issue
The current issue of this thesis is to determine the workflow efficient scheduling
techniques of IAAS in the cloud computing.
Research questions
Determine the concept of IAAS in cloud computing?
Identify the efficient workflow scheduling in IAAS in cloud computing?
How does the efficient workflow scheduling affect the performance of IAAS in cloud
computing?
The research a question develops by a researcher will help in collecting authentic and
reliable data and the facts related to cloud computing, infrastructure as a service and efficient
scheduling techniques or algorithms (Haydon, Browne and van der Riet, 2018, pp.125-129).
These research questions will help a user in moving systematically in getting answers to all
the questions to tests the researcher’s claim. The success rate of a study without research
question is less as compared to a study having an appropriate question develops by a user
after assessing the nature of an entire study. Scrutinizer crafts questions after prioritizing the
entire studies into several chapters to complete the entire study in a less period. The
progresses of each section will shares with the client in taking their feedback or comments to
modify the same at the initial stage (Mikhail et al., 2018, pp.36-41). This will helps in
avoiding the situation of last minute changes which increases the workload of a user in
proofreading and check the entire research in fewer periods which, in turn, increases the
chances of project failure.
3.2 Research Approach
Deductive- This approach comes into existence in a dissertation where the research
hypothesis uses by a researcher to tests the claims in the future period. This approach
comprises of a systematically process such as creating a theory, developing a hypothesis,
making observation or testing and finally getting the final result. The final result in the case
of this research approach includes confirmation or rejection of the research hypothesis.

For instance, this research approach will in case of a research study about employee
resistance due to less work compensation (Gaur and Kumar, 2018, pp.280-289.). In this kind
of study, the researcher will create a hypothesis to tests that low work compensation is the
only issue or is there anything which decreases the interest of an employee towards the work.
Inductive- Use of this approach in a condition where there is no existence of the hypothesis
of research as it can say that it is an opposite version of deductive where aims and objectives
develop by scrutinizers. The aim of the research is further categorized into various parts in
creating objectives of the research (Sale and Thielke, 2018, pp.129-133). The objectives of
the research will act as a compass to guide a proper direction to the entire study in
accomplishing its purpose in a stipulated deadline by the client. The process to be followed
by a user in applying this approach consists of several steps such as making an observation,
analysing the pattern and then building up a theory based on the results. The theory builds up
using this approach is very practical as this will get develops after collecting authentic and
reliable data and facts.
For example, research question develops by a user for dissertation to tests the efficiency of
the employee’s in an organization and its effect on the company’s performance. In this
research question, a user will test the efficiency of employees by identifying their
performance traits and also to determine it’s a positive or negative effect on the performance
of the organization (Castka and Balzarova, 2018, pp.1642-1652). This will helps in
identifying the cause roots of all the weaknesses or strengths of an entity for affecting the
work efficiency of an employee.
Drawing comparison of both the research approaches, such as deductive and inductive
research approaches to help an investigator in considering the suitable methodology that suits
them needs of the current research study (Galliano, et al., 2018, pp.251-255).
Basis of difference Deductive Inductive
Logic Conclusion depends on the
premises as if premise is true
then directly conclusion gets
true as well.
Known facts or premises
utilizes by a user in
generating the conclusion
which is not tested.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
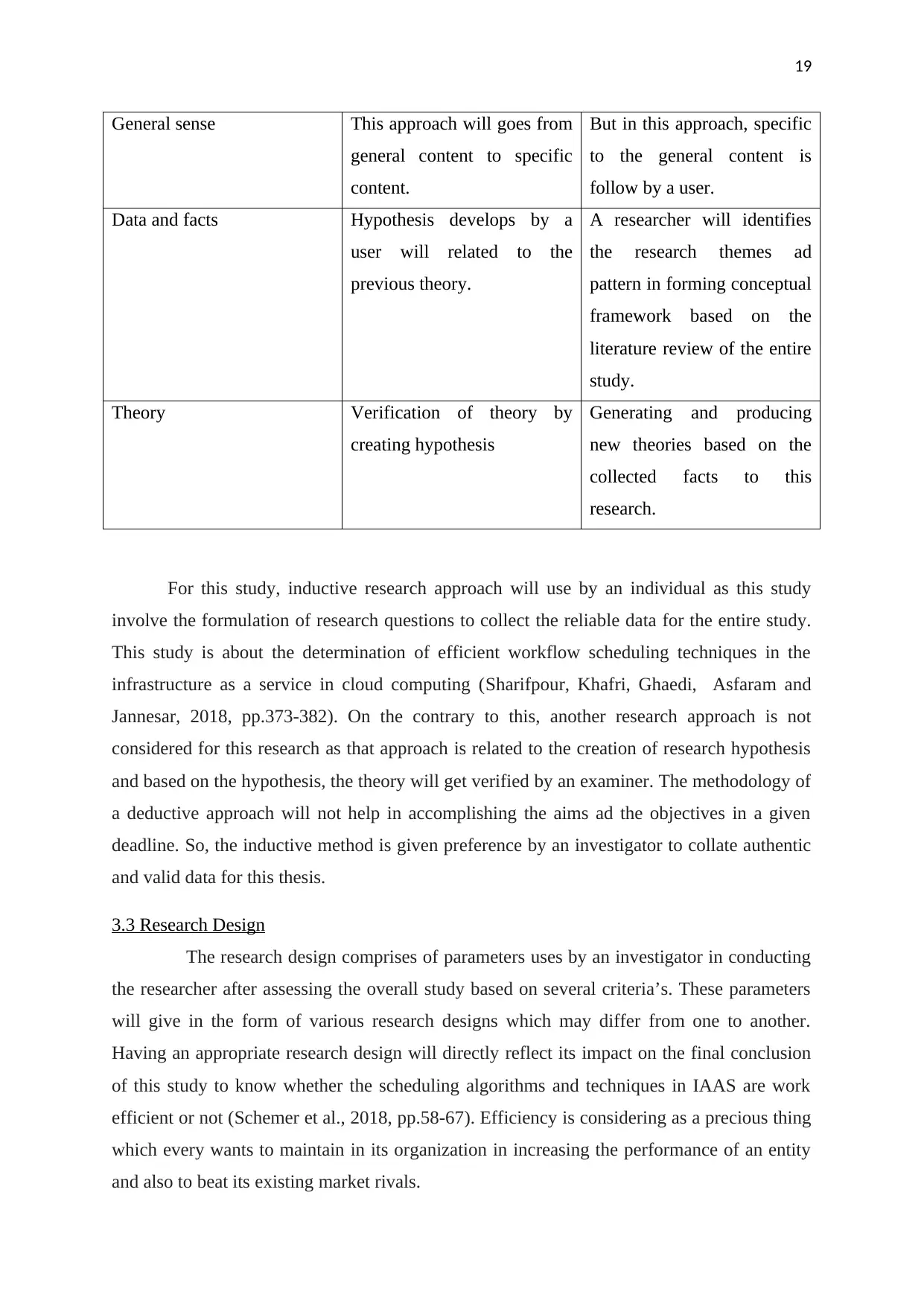
General sense This approach will goes from
general content to specific
content.
But in this approach, specific
to the general content is
follow by a user.
Data and facts Hypothesis develops by a
user will related to the
previous theory.
A researcher will identifies
the research themes ad
pattern in forming conceptual
framework based on the
literature review of the entire
study.
Theory Verification of theory by
creating hypothesis
Generating and producing
new theories based on the
collected facts to this
research.
For this study, inductive research approach will use by an individual as this study
involve the formulation of research questions to collect the reliable data for the entire study.
This study is about the determination of efficient workflow scheduling techniques in the
infrastructure as a service in cloud computing (Sharifpour, Khafri, Ghaedi, Asfaram and
Jannesar, 2018, pp.373-382). On the contrary to this, another research approach is not
considered for this research as that approach is related to the creation of research hypothesis
and based on the hypothesis, the theory will get verified by an examiner. The methodology of
a deductive approach will not help in accomplishing the aims ad the objectives in a given
deadline. So, the inductive method is given preference by an investigator to collate authentic
and valid data for this thesis.
3.3 Research Design
The research design comprises of parameters uses by an investigator in conducting
the researcher after assessing the overall study based on several criteria’s. These parameters
will give in the form of various research designs which may differ from one to another.
Having an appropriate research design will directly reflect its impact on the final conclusion
of this study to know whether the scheduling algorithms and techniques in IAAS are work
efficient or not (Schemer et al., 2018, pp.58-67). Efficiency is considering as a precious thing
which every wants to maintain in its organization in increasing the performance of an entity
and also to beat its existing market rivals.
Paraphrase This Document

Descriptive- As the name describes its meaning that this kind of research designs is a
theoretical type of researcher where the aim of an investigator is to examine the case study or
situation. This method will be based on three critical pillars such as gathering information,
analysing the presenting the information in front of the ends users of the study (Delgado-
Sánchez et al., 2018, p.7-15).
Experimental- This kind of method emphasizes creating a cause and effect relationship
between the dependent and independent variables to research. The experiment will conduct
by a researcher in knowing the effect of one element on another to test its relationship with
each other (Núñez, Veglia and Pacioni, 2018, pp.110-117). This process follows some of the
steps such as identifying variables, categorizing into dependent and independent and testing
the relationship with each other.
Correlational- Non-experimental research design utilizes statistical toll such as data analysis
in the Ms excels to tests the correlation among the two variables. These methods do not
involve building assumptions for a research study (Beck, JDia, Espath, Long and Tempone,
2018, pp.523-553). Positive or negative correlation among the variables to research will use
in concluding the entire research to know the relationship between the elements of the study.
Diagnostic- In this procedure, the greater emphasis lies in analysing a specific topic rather
than considering the general aspects of research. This kind of research design considers by an
examiner when the study is about a specific issue whose solution is required to minimize its
impact on other variables. Severe situations will be treated in this research design to know
about the issue in detail in order to make relevant solutions for this problem. This method is
further segmented into three aspects such as the inception of the problem, diagnosis and
solution of the problem.
Exploratory- A the motive of the researcher in applying this designing method for this study
which involves hidden aspects that are not explored by people. Unique ideas and thoughts
utilized by a user in analysing a particular matter as an investigator follows its intuition in
knowing about a study which is very hidden and uncommon.
After discussing above mention research design, now it’s time to consider the suitable
design that meets the needs of this study. The experimental research design will select by an
individual for performing this research as this thesis’s aim is to determine the workflow
efficient scheduling in IAAS in the clouds computing. The research will come to know that

how certainly the efficiency of the scheduling algorithms will boost the work performance of
an entity (Longhi et al., 2018, pp.20-26).
3.4 Research technique
Qualitative- This technique involves the collection of information through face to face
communication and interaction with the respondent to seek answers to the research questions.
This will help in answering questions like the thinking of people about a research problem
and why they think so. Several methods cover under this head includes an interview, focus
groups, case study, and record keeping (Radivojević et al., 2018, pp.106-119).
Quantitative- Monetary data collected by an examiner and tests the collected data using
statistical; measures such as T test, ANNOVA, chi-square, Pareto analysis, F tests,
descriptive statistics and correlation to tests the trends of the collected data. This technique
includes several ways such as surveys, questionnaires, experimental research.
3.5 Data collection
Tow common form of data collection utilizes by a user in collating the relevant data
to meet the desired needs and the objectives of a research study. This consists of primary as
well as secondary data collection methods to collect the data (Issard and Gervain, 2018,
pp.182-193). The primary method of data collection requires one to one collection of data as
this will suitable when the study is about a specific topi where there is fear of affecting the
confidentiality when using used data. On another hand, secondary method will use in a nature
of study where there is no such fears. This comprises of online sources, ‘A’ grade research
papers, literature review, internet, books, journals, company’s websites, IT sites to gather
relevant data and facts to meet the requirement.
An investigator uses secondary method of data collection for collating the data for this
research study in knowing about the workflow efficient scheduling algorithms that will meets
the performance needs of an entity (Carteret, Jacoby and Blin, 2018, pp.39-45). The
increasing efficiency of scheduling algorithms will, in turn, increases the scope of IAAS and
the cloud computing as these two concepts are linked with the performance of the scheduling
techniques.
3.6 Sampling
Random sampling method and stratum sampling is used for this study in considering
the random samples of existing scheduling technique in IAAS and analyses its parameters use
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

to evaluate all of these. Stratum sampling is also used by a researcher in creating stratums or
groups such as Parameters use to evaluate the techniques, IT companies, scheduling
techniques, previous and proposed techniques (Barzegar et al., 2019). 50 samples of all these
groups is used for testing the data to this research study.
3.7 Ethical consideration
Seeking permission of the previous research scholars is essential before utilizing their
content in this research to avoid the allegation of plagiarism. Using someone’s content will be
punished under the infringement of the copyright act so it is better to include the references of
authors when using their matter in the study.
4.0 EXPERIMENTS AND DATA ANALYSIS
4.1 Experimental design
Variables
Round Robin
Genetic Algorithm
Minimum execution time Algorithm
Switching algorithm
Opportunistic load balancing
The current experiment aims to tests the existing scheduling technique’s efficiency that
this will increase the workflow in an organization as the focus of an investigator is to test
all these techniques with the currently proposed techniques to know the difference among
them (Edge, Riche, Larson and White, 2018).
Round Robin- Resource allocation and task scheduling approach aims to reduce the
adversities lies in allocating all the resources among the entire project (Shi, Luo,
Dong, Zhang and Zhang, 2016, pp.167-182).
Genetic Algorithm- This technique emphasizes on the task scheduling where the
complex tasks will further categorize into smaller parts to help a user in tracking the
progress of all such parts to complete the same in the desired time period.
Minimum execution time Algorithm- Time is very important for an entity to get the
trust of its clients by meeting their requirements before the final deadline as in this
Paraphrase This Document

way; their trust on the business gets increases. This tool will help in saving time while
executing the task to the end users.
Switching algorithm- this will allow a user’s to shift from one task to another in
meeting their requirements as a user is not restricted to start the entire process from
the beginning as they simply can terminate to start the project according to its choice.
Opportunistic load balancing- things which are very important for this consists of
workload reducing, errors reducing, maintaining quality of work, easy to track the
task and the counts of users access the data, de-centralization of the tasks and the data
centers.
Proposed techniques
This will include the current technique to be utilized for this research studies as all
these are scheduling algorithms is better than the existing techniques (Reani, Davies, Peek
and Jay, 2018, pp.62-77). The issues of the existing techniques will get eliminated by
proposing new techniques for this study and later on the current and the previous techniques
will compare with each other to know the actual differences and the cause roots of all the
issues.
Task scheduling- work is prioritized according to its urgency which will help an
admin's head and a user to pick the task according to its necessary requirements. The
previous and the current task’s progress can be easily compared using this mode that
will aid a user in judging the performance (Reani, Peek and Jay, 2019, pp.55-64). The
task is presented in the form of layers which will include the users, tasks to be pick by
them and virtual machines that will show the information on the dashboard of an
individual

Figure 2 task scheduling
First, come first, serve- This is a similar methodology of First in the first out system of
inventory where stock come in the store first will sell first just like a process started firstly in
an entity will firstly get implemented (Liu, Ren, Deng and Song, 2016). This is also
considered as a batch system in which the implementation of a process get easier following
this system where processes will be aligned in a systematical order according to their overall
rankings to get executed on time.
The priority of work based on deadlines- As the name suggests its meaning itself in the
name of this term that work is prioritized according to the mentioned deadlines of the tasks
(Wu, Lin, Yu, Xu and Li, 2015, pp.169-181). A technical or technical user can easily execute
the tasks according to the deadline. This will allow a user in completing the most important
task before then the less important tasks.
USER User's need
Task Performing a task
Virtual
machine
Information on dashboard
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
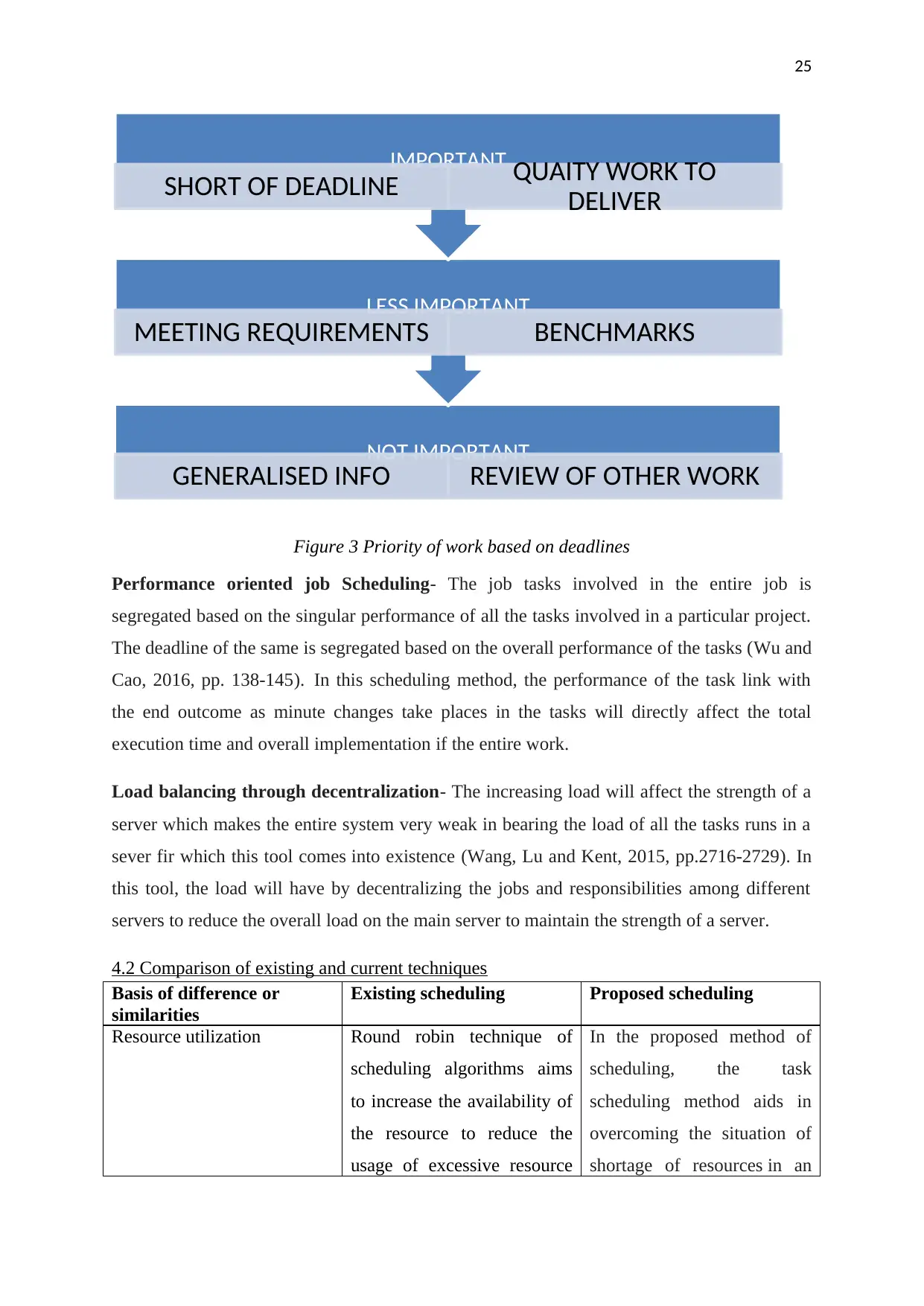
Figure 3 Priority of work based on deadlines
Performance oriented job Scheduling- The job tasks involved in the entire job is
segregated based on the singular performance of all the tasks involved in a particular project.
The deadline of the same is segregated based on the overall performance of the tasks (Wu and
Cao, 2016, pp. 138-145). In this scheduling method, the performance of the task link with
the end outcome as minute changes take places in the tasks will directly affect the total
execution time and overall implementation if the entire work.
Load balancing through decentralization- The increasing load will affect the strength of a
server which makes the entire system very weak in bearing the load of all the tasks runs in a
sever fir which this tool comes into existence (Wang, Lu and Kent, 2015, pp.2716-2729). In
this tool, the load will have by decentralizing the jobs and responsibilities among different
servers to reduce the overall load on the main server to maintain the strength of a server.
4.2 Comparison of existing and current techniques
Basis of difference or
similarities
Existing scheduling Proposed scheduling
Resource utilization Round robin technique of
scheduling algorithms aims
to increase the availability of
the resource to reduce the
usage of excessive resource
In the proposed method of
scheduling, the task
scheduling method aids in
overcoming the situation of
shortage of resources in an
NOT IMPORTANT
GENERALISED INFO REVIEW OF OTHER WORK
LESS IMPORTANT
MEETING REQUIREMENTS BENCHMARKS
IMPORTANT
SHORT OF DEADLINE QUAITY WORK TO
DELIVER
Paraphrase This Document
unnecessarily on one
particular task as this guides
a user in knowing the actual
requirement of resource for
one task.
entity as the flow charts
develops y a user will help in
analysing the requirement of
the task resources in advance.
His is even better than the
round robin as this system
will identify the current
resource requirement and not
the future one.
Time reduction Switching algorithm aims to
reduce the time as this gives
a short cut method to move
from one data centre to
another.
The deadline will achieve by
a project using a priority of
work based in the deadline as
in this mode there is to scope
id delaying in the activities
which save the time.
Performance booster On the performance booster,
there is no such existing
scheduling technique which
will meet this criterion as in
this case, the current or
proposed technique is
proficient.
Performance-oriented of
scheduling is one of a
technique whose motto is to
categorize the existing tasks
in a project according to its
performance This will
segregates in various
categories such as efficiency,
less efficient ad weak.
Low execution time Minimum execution time
emphasizes reducing the time
required in executing the
tasks.
On contrary to this, first
come first serve the
scheduling algorithm is far
better than minimum
execution time as this will
only considers the tasks sir
process which started first as
only the task which started
early will get executed firsts
in this ways the quality of
information and the
confidentiality tasks will get
maintained which started
earlier.
Work load reduction Opportunistic load balancing
is meant for reducing the
workload by the distribution
of the complex project and
tasks s into smaller and
simplified data packets.
Opportunistic load balancing
only focusing on the
distribution of the work to
lessen the workload but this
issue will resolve by
introducing the load
balancing through
decentralization. In this
approach, the work is not
only distributed but the roles
and the responsibilities are
also shared with all the
workers working in an entity
to take spontaneous decisions
at the time of any problem
without seeking approval
from its superior.
Cost efficient Only scheduling method in
IAAS is round robin which is
a cost-efficient mode to save
the costing requirements of a
project after implementing
this tool as compared to all
other existing scheduling
algorithms.
But in the currently proposed
technique, all the tolls are
cost-efficient ways which
will save the time and costs
of an entity and also
contributes to increasing the
performance and the final
output of an organization.
Flexibility In terms of flexibility, there
is no such mode which meets
the flexibility requirements
of an entity.
All the newly proposed
techniques are very flexible
enough to meet the needs and
the requirements of an entity
in accomplishing all their
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

needs in fewer periods.
4.3 Data collection
The data for the experimental analysis collected from different modes such as
collecting data about the revenue generated by cloud computing companies, size of the cloud
computing market in the current as well as in the future periods and the proportion of clouds
using various categories. Secondary collection of data is preferred by researcher for his
research by accessing the sites of IT companies, cloud computing industry facts to know the
increasing or decreasing trend of the cloud computing in the external market and it’s a direct
impact on the business.
4.4 Data analysis
Implementation
The newly proposed scheduling algorithms will execute by creating web
applications which will give complete detail regarding these methods to a user in selecting
the same according to their requirements before the stipulated time as their aim is to meet the
requirements of all the users. Secondly, the website is created illustrating special instructions
for the users in getting a detail description about the scheduling algorithm to draw a
comparison among the existing and proposed methods with each other.
Paraphrase This Document
5.0 RESULTS
5.1 Presentation of results
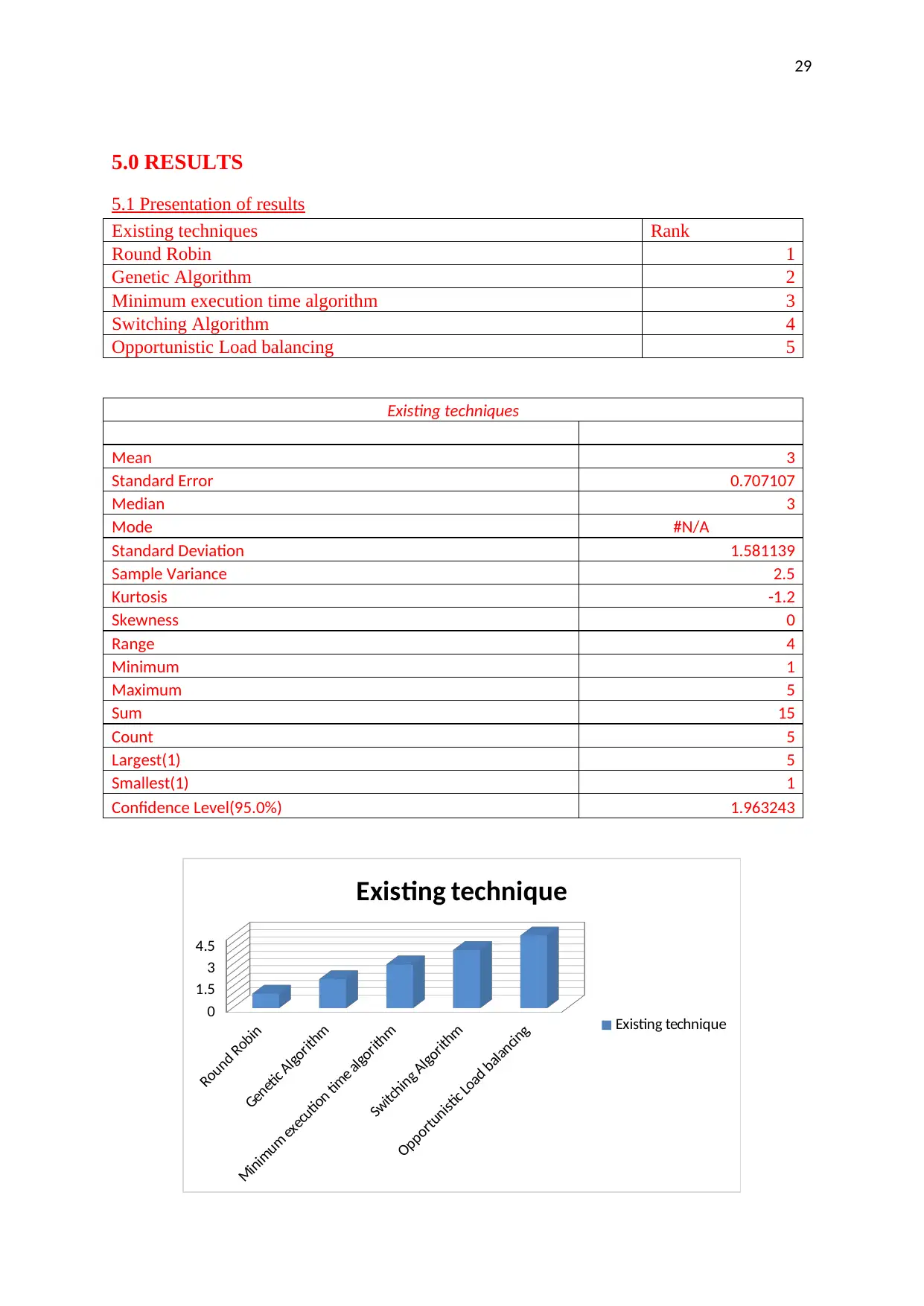
Existing techniques Rank
Round Robin 1
Genetic Algorithm 2
Minimum execution time algorithm 3
Switching Algorithm 4
Opportunistic Load balancing 5
Existing techniques
Mean 3
Standard Error 0.707107
Median 3
Mode #N/A
Standard Deviation 1.581139
Sample Variance 2.5
Kurtosis -1.2
Skewness 0
Range 4
Minimum 1
Maximum 5
Sum 15
Count 5
Largest(1) 5
Smallest(1) 1
Confidence Level(95.0%) 1.963243
Round Robin
Genetic Algorithm
Minimum execution time algorithm
Switching Algorithm
Opportunistic Load balancing
0
1.5
3
4.5
Existing technique
Existing technique
Interpretations
The descriptive statistical measures apply to test the efficiency of the data that how
efficiently the data will meet its future business targets and the requirements. Round Robin
technique remains on a top position and opportunistic load balancing is on the last position
due to the characteristics and traits used in these two techniques.
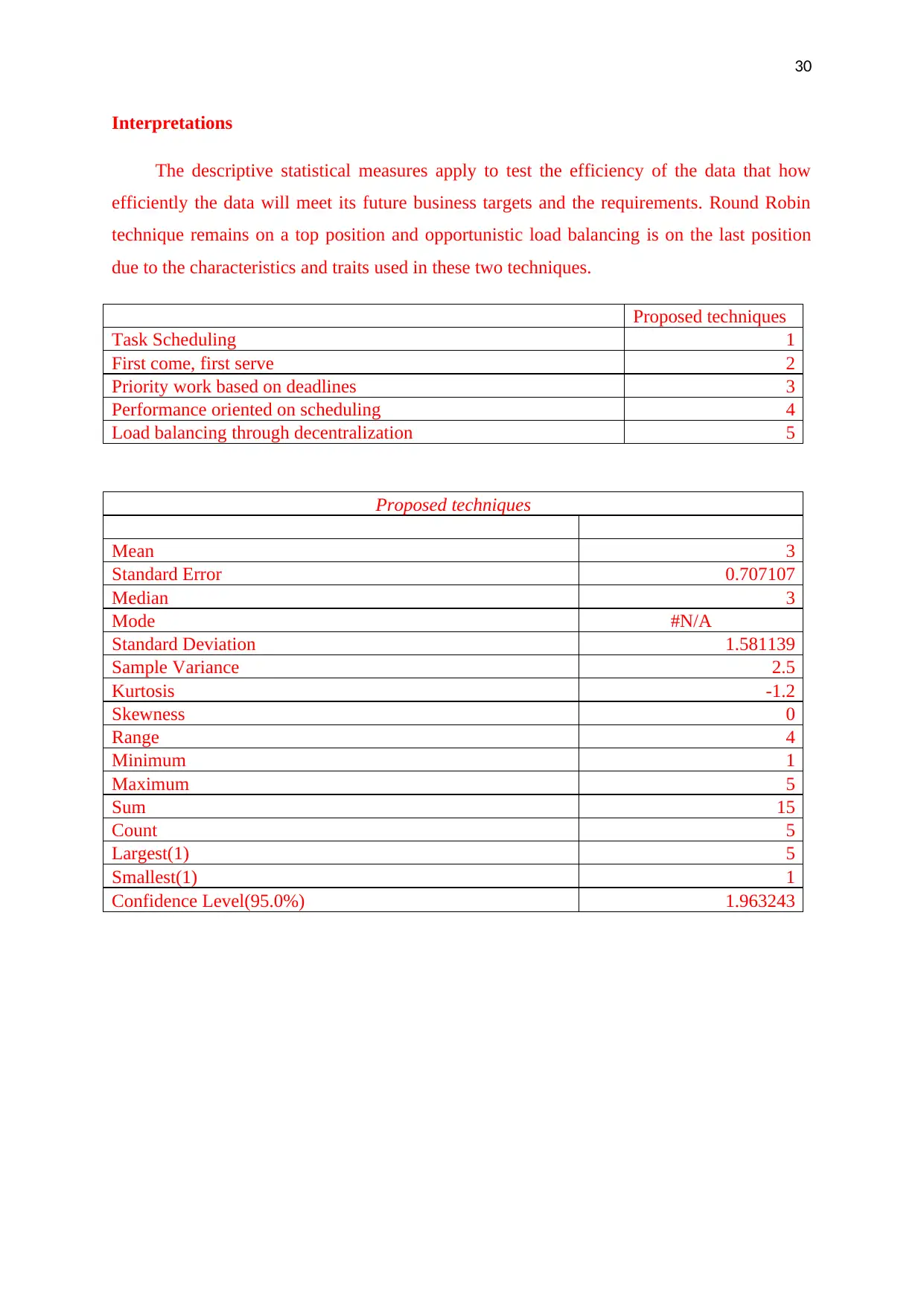
Proposed techniques
Task Scheduling 1
First come, first serve 2
Priority work based on deadlines 3
Performance oriented on scheduling 4
Load balancing through decentralization 5
Proposed techniques
Mean 3
Standard Error 0.707107
Median 3
Mode #N/A
Standard Deviation 1.581139
Sample Variance 2.5
Kurtosis -1.2
Skewness 0
Range 4
Minimum 1
Maximum 5
Sum 15
Count 5
Largest(1) 5
Smallest(1) 1
Confidence Level(95.0%) 1.963243
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
0
1.5
3
4.5
Proposed techniques
Proposed techniques
Interpretations
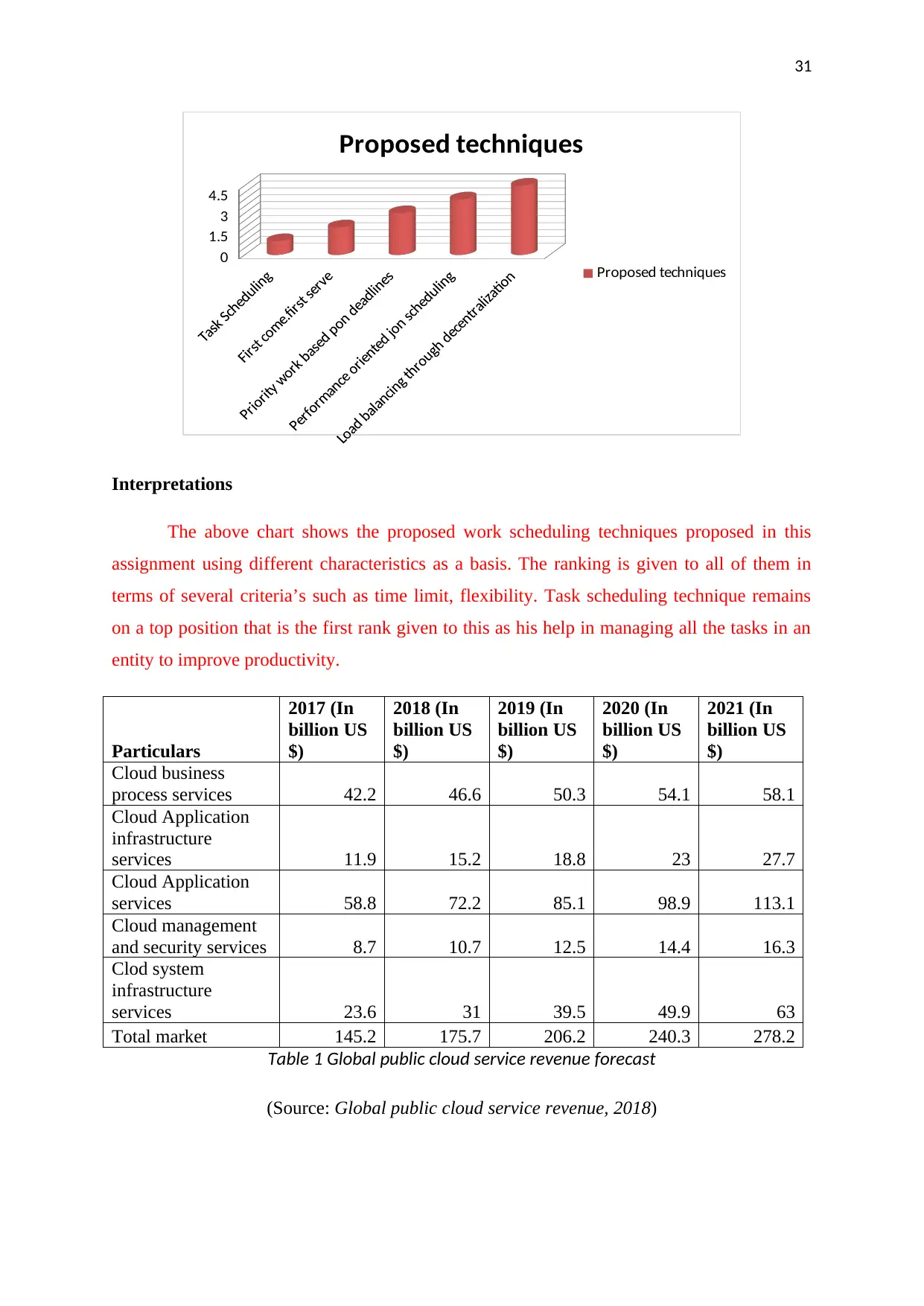
The above chart shows the proposed work scheduling techniques proposed in this
assignment using different characteristics as a basis. The ranking is given to all of them in
terms of several criteria’s such as time limit, flexibility. Task scheduling technique remains
on a top position that is the first rank given to this as his help in managing all the tasks in an
entity to improve productivity.
Particulars
2017 (In
billion US
$)
2018 (In
billion US
$)
2019 (In
billion US
$)
2020 (In
billion US
$)
2021 (In
billion US
$)
Cloud business
process services 42.2 46.6 50.3 54.1 58.1
Cloud Application
infrastructure
services 11.9 15.2 18.8 23 27.7
Cloud Application
services 58.8 72.2 85.1 98.9 113.1
Cloud management
and security services 8.7 10.7 12.5 14.4 16.3
Clod system
infrastructure
services 23.6 31 39.5 49.9 63
Total market 145.2 175.7 206.2 240.3 278.2
Table 1 Global public cloud service revenue forecast
(Source: Global public cloud service revenue, 2018)
Paraphrase This Document
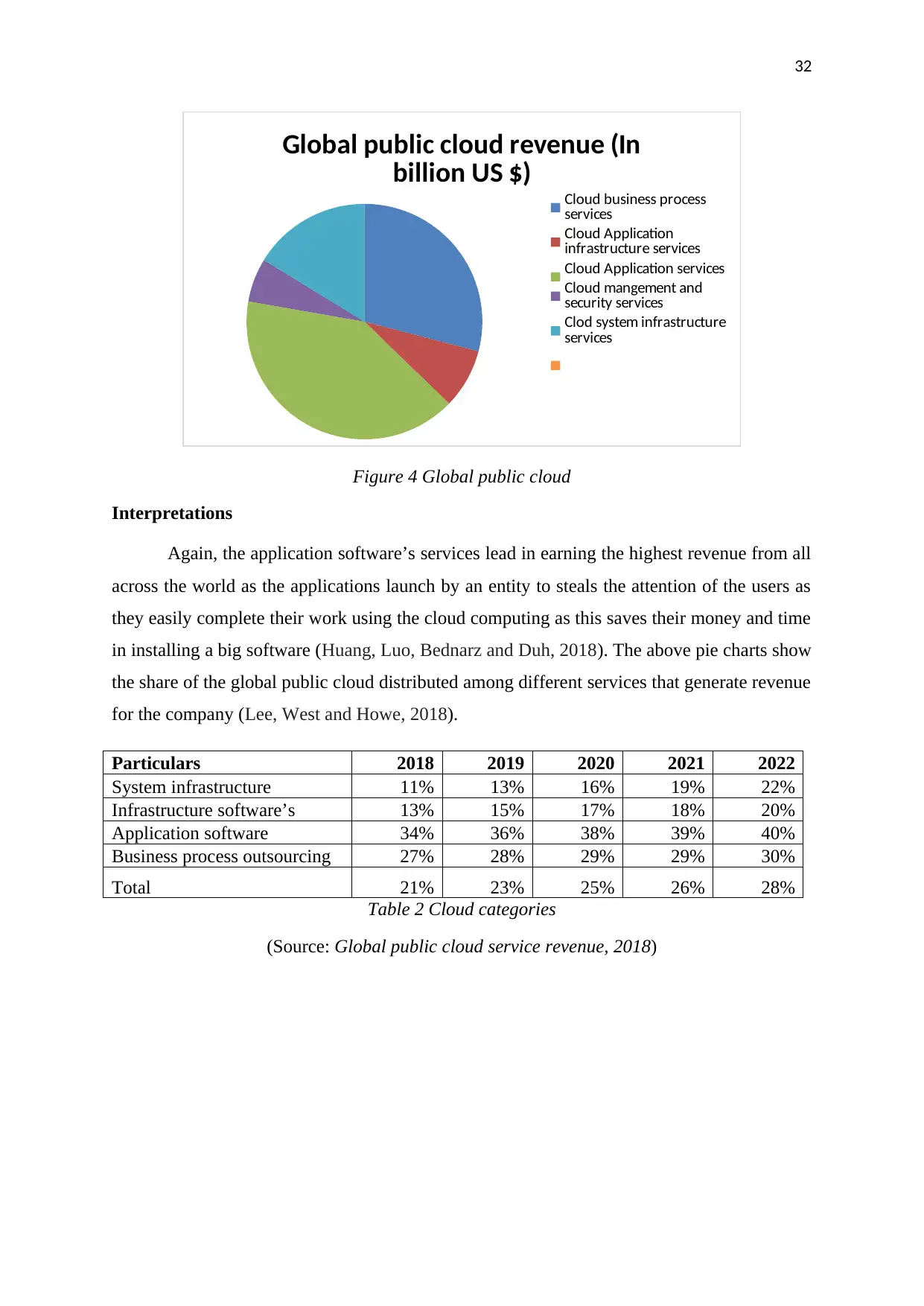
Global public cloud revenue (In
billion US $) Cloud business process
services
Cloud Application
infrastructure services
Cloud Application services
Cloud mangement and
security services
Clod system infrastructure
services
Figure 4 Global public cloud
Interpretations
Again, the application software’s services lead in earning the highest revenue from all
across the world as the applications launch by an entity to steals the attention of the users as
they easily complete their work using the cloud computing as this saves their money and time
in installing a big software (Huang, Luo, Bednarz and Duh, 2018). The above pie charts show
the share of the global public cloud distributed among different services that generate revenue
for the company (Lee, West and Howe, 2018).
Particulars 2018 2019 2020 2021 2022
System infrastructure 11% 13% 16% 19% 22%
Infrastructure software’s 13% 15% 17% 18% 20%
Application software 34% 36% 38% 39% 40%
Business process outsourcing 27% 28% 29% 29% 30%
Total 21% 23% 25% 26% 28%
Table 2 Cloud categories
(Source: Global public cloud service revenue, 2018)
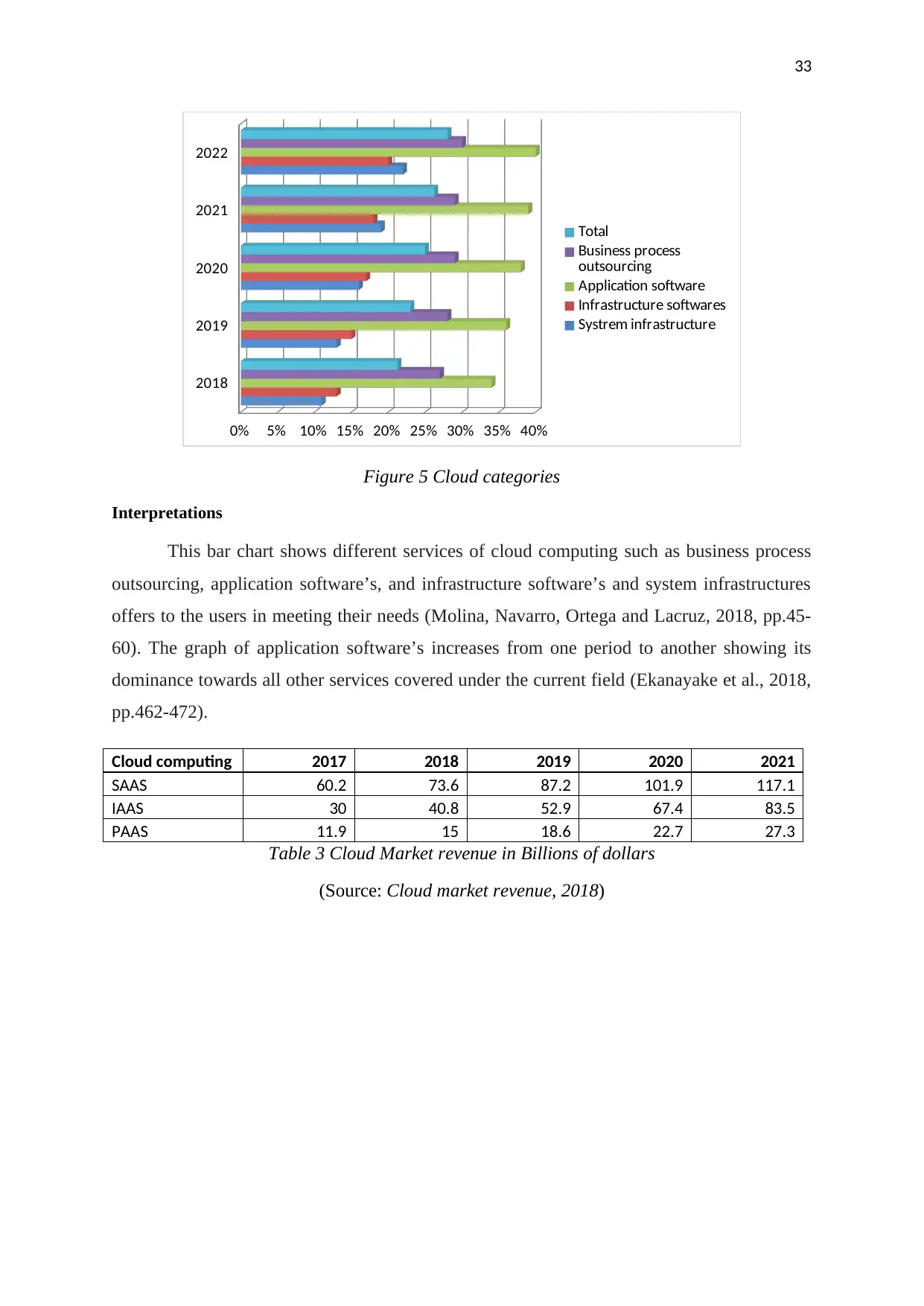
2018
2019
2020
2021
2022
0% 5% 10% 15% 20% 25% 30% 35% 40%
Total
Business process
outsourcing
Application software
Infrastructure softwares
Systrem infrastructure
Figure 5 Cloud categories
Interpretations
This bar chart shows different services of cloud computing such as business process
outsourcing, application software’s, and infrastructure software’s and system infrastructures
offers to the users in meeting their needs (Molina, Navarro, Ortega and Lacruz, 2018, pp.45-
60). The graph of application software’s increases from one period to another showing its
dominance towards all other services covered under the current field (Ekanayake et al., 2018,
pp.462-472).
Cloud computing 2017 2018 2019 2020 2021
SAAS 60.2 73.6 87.2 101.9 117.1
IAAS 30 40.8 52.9 67.4 83.5
PAAS 11.9 15 18.6 22.7 27.3
Table 3 Cloud Market revenue in Billions of dollars
(Source: Cloud market revenue, 2018)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
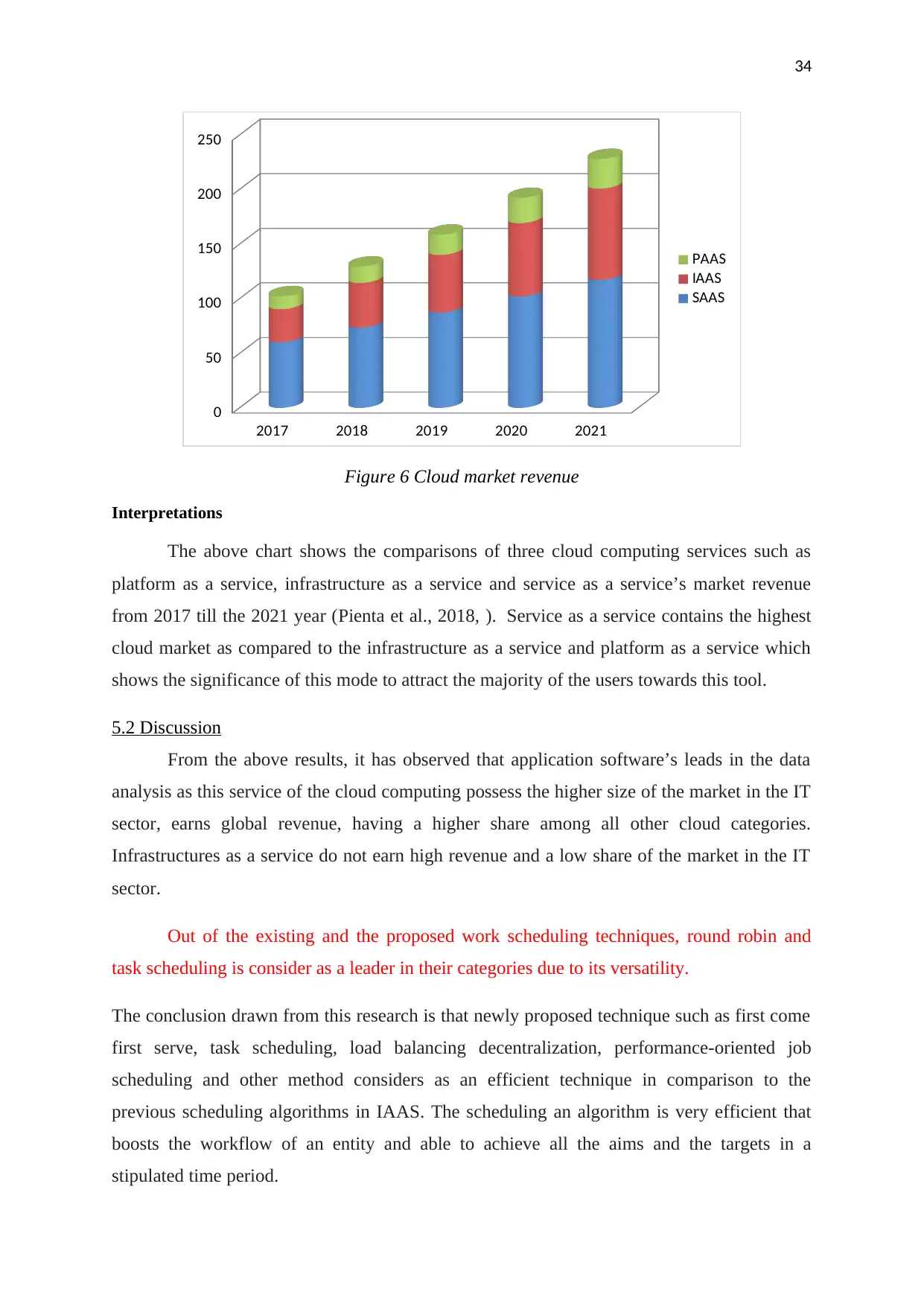
2017 2018 2019 2020 2021
0
50
100
150
200
250
PAAS
IAAS
SAAS
Figure 6 Cloud market revenue
Interpretations
The above chart shows the comparisons of three cloud computing services such as
platform as a service, infrastructure as a service and service as a service’s market revenue
from 2017 till the 2021 year (Pienta et al., 2018, ). Service as a service contains the highest
cloud market as compared to the infrastructure as a service and platform as a service which
shows the significance of this mode to attract the majority of the users towards this tool.
5.2 Discussion
From the above results, it has observed that application software’s leads in the data
analysis as this service of the cloud computing possess the higher size of the market in the IT
sector, earns global revenue, having a higher share among all other cloud categories.
Infrastructures as a service do not earn high revenue and a low share of the market in the IT
sector.
Out of the existing and the proposed work scheduling techniques, round robin and
task scheduling is consider as a leader in their categories due to its versatility.
The conclusion drawn from this research is that newly proposed technique such as first come
first serve, task scheduling, load balancing decentralization, performance-oriented job
scheduling and other method considers as an efficient technique in comparison to the
previous scheduling algorithms in IAAS. The scheduling an algorithm is very efficient that
boosts the workflow of an entity and able to achieve all the aims and the targets in a
stipulated time period.
Paraphrase This Document

6.0 CONCLUSION
It is summarizes from the above research study that existing scheduling algorithms
are not efficient as gaps lie in the previous technique will get filled with the proposed
technique in this research study. The data analysis section of this study also draws light on
another aspect that this research that applications software’s or service as a service kind of
cloud computing is better than the infrastructure as a service. This can one of a reason of
inefficiency of the scheduling algorithms as people do not wish to prefer IAAS as compared
to the applications software’s a majority of people get attracted to the latest applications.
Information shared in this research study will help all the future research
scholars to perform their research on the similar output to fill the gaps lies in performing this
research. The future research can conducted on comparing the infrastructure as a service or
application as a service and to know the causes of differences between the earning of these
two methods.

7.0 REFERENCES
Books and Journals
. Rasheed, M. B., et al., 2019. Intelligent multi-agent based multilayered control system for
opportunistic load scheduling in smart buildings. IEEE Access. 7. pp.23990-24006.
Abdelaziz, A., Elhoseny, M., Salama, A. S. and Riad, A. M., 2018. A machine learning
model for improving healthcare services on cloud computing environment. Measurement.
119. pp.117-128.
Abdullahi, M., Ngadi, M. A., Dishing, S. I. and Ahmad, B. I. E., 2019. An efficient symbiotic
organisms search algorithm with chaotic optimization strategy for multi-objective task
scheduling problems in cloud computing environment. Journal of Network and Computer
Applications, 133, pp.60-74.
Adhikari, M. and Amgoth, T., 2019. An intelligent water drops-based workflow scheduling
for IaaS cloud. Applied Soft Computing, 77, pp.547-566.
Alkhanak, E. N. and Lee, S. P., 2018. A hyper-heuristic cost optimisation approach for
Scientific Workflow Scheduling in cloud computing. Future Generation Computer
Systems. 86. pp.480-506.
Arabnejad, V., Bubendorfer, K. and Ng, B., 2016, October. Budget distribution strategies for
scientific workflow scheduling in commercial clouds. In 2016 IEEE 12th International
Conference on e-Science (e-Science) (pp. 137-146). IEEE.
Barzegar, M. H., et al., 2019. Electrochemical synthesis and efficient photocatalytic
degradation of azo dye alizarin yellow R by Cu/CuO nanorods under visible LED light
irradiation using experimental design methodology. Polyhedron. 158. pp.506-514.
Beck, J., Dia, B. M., Espath, L.F., Long, Q. and Tempone, R., 2018. Fast Bayesian
experimental design: Laplace-based importance sampling for the expected information
gain. Computer Methods in Applied Mechanics and Engineering. 334. pp.523-553.
Cao, H. and Wu, C. Q., 2018, May. Performance optimization of budget-constrained
mapreduce workflows in multi-clouds. In 2018 18th IEEE/ACM International Symposium
on Cluster, Cloud and Grid Computing (CCGRID) (pp. 243-252). IEEE.
Carteret, C., Jacoby, J. and Blin, J. L., 2018. Using factorial experimental design to optimize
biocatalytic biodiesel production from Mucor Miehei Lipase immobilized onto ordered
mesoporous materials. Microporous and Mesoporous Materials. 268. pp.39-45.
Castka, P. and Balzarova, M. A., 2018. An exploration of interventions in ISO 9001 and ISO
14001 certification context–A multiple case study approach. Journal of cleaner production.
174. pp.1642-1652.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Delgado-Sánchez, C., et al., 2018. Optimisation of “green” tannin-furanic foams for thermal
insulation by experimental design. Materials & Design.139. p.7-15.
Edge, D., Riche, N. H., Larson, J. and White, C., 2018. Beyond Tasks: An Activity Typology
for Visual Analytics. IEEE transactions on visualization and computer graphics. 24(1).
pp.267-277.
Ekanayake, J., et al., 2018. Real-time decoding of covert attention in higher-order visual
areas. NeuroImage. 169. pp.462-472.
Fu, J. S., Liu, Y., Chao, H. C., Bhargava, B. K. and Zhang, Z. J., 2018. Secure data storage
and searching for industrial IoT by integrating fog computing and cloud computing. IEEE
Transactions on Industrial Informatics. 14(10). pp.4519-4528.
Gai, K., Qiu, M., Zhao, H. and Sun, X., 2018. Resource management in sustainable cyber-
physical systems using heterogeneous cloud computing. IEEE Transactions on Sustainable
Computing. 3(2). pp.60-72.
Galliano, S., et al., 2018. Finely tuning electrolytes and photoanodes in aqueous solar cells by
experimental design. Solar Energy. 163. pp.251-255.
Gaur, A. and Kumar, M., 2018. A systematic approach to conducting review studies: An
assessment of content analysis in 25 years of IB research. Journal of World Business. 53(2).
pp.280-289.
Haydon, G., Browne, G. and van der Riet, P., 2018. Narrative inquiry as a research
methodology exploring person centred care in nursing. Collegian. 25(1). pp.125-129.
Hu, P., Ning, H., Qiu, T., Xu, Y., Luo, X. and Sangaiah, A. K., 2018. A unified face
identification and resolution scheme using cloud computing in Internet of Things. Future
Generation Computer Systems. 81. pp.582-592.
Huang, W., Luo, J., Bednarz, T. and Duh, H., 2018. Making graph visualization a user-
centered process. Journal of Visual Languages & Computing. 48. pp.1-8.
Issard, C. and Gervain, J., 2018. Variability of the hemodynamic response in infants:
Influence of experimental design and stimulus complexity. Developmental cognitive
neuroscience. 33. pp.182-193.
Kadri, R. L. and Boctor, F. F., 2018. An efficient genetic algorithm to solve the resource-
constrained project scheduling problem with transfer times: The single mode
case. European Journal of Operational Research. 265(2). pp.454-462.
Kaur, K., et al., 2018. Edge computing in the industrial internet of things environment:
Software-defined-networks-based edge-cloud interplay. IEEE communications magazine.
56(2). pp.44-51.
Paraphrase This Document

Khan, I., Rehman, H. U., Al-Khatib, M. H. F., Anwar, Z. and Alam, M., 2018. A thin client
friendly trusted execution framework for infrastructure-as-a-service clouds. Future
Generation Computer Systems. 89. pp.239-248.
Lee, P. S., West, J. D. and Howe, B., 2018. Viziometrics: Analyzing visual information in the
scientific literature. IEEE Transactions on Big Data. 4(1). pp.117-129.
Li, H., Lu, R., Misic, J. and Mahmoud, M., 2018. Security and privacy of connected
vehicular cloud computing. IEEE Network. 32(3). pp.4-6.
Li, Z., Ge, J., Hu, H., Song, W., Hu, H. and Luo, B., 2018. Cost and energy aware scheduling
algorithm for scientific workflows with deadline constraint in clouds. IEEE Transactions
on Services Computing. 11(4). pp.713-726.
Li, Z., Ge, J., Hu, H., Song, W., Hu, H. and Luo, B., 2018. Cost and energy aware scheduling
algorithm for scientific workflows with deadline constraint in clouds. IEEE Transactions
on Services Computing. 11(4). pp.713-726.
Lin, X. and Wu, C.Q., 2013, October. On scientific workflow scheduling in clouds under
budget constraint. In 2013 42nd International Conference on Parallel Processing (pp. 90-
99). IEEE.
Liu, J., et al., 2019. Online Multi-Workflow Scheduling under Uncertain Task Execution
Time in IaaS Clouds. IEEE Transactions on Cloud Computing.
Liu, S., Ren, K., Deng, K. and Song, J., 2016, May. A dynamic resource allocation and task
scheduling strategy with uncertain task runtime on IaaS clouds. In 2016 Sixth International
Conference on Information Science and Technology (ICIST) (pp. 174-180). IEEE.
Liu, X., Deng, R. H., Yang, Y., Tran, H. N. and Zhong, S., 2018. Hybrid privacy-preserving
clinical decision support system in fog–cloud computing. Future Generation Computer
Systems. 78. pp.825-837.
Longhi, D. A., aet al., 2018. Optimal experimental design to model spoilage bacteria growth
in vacuum-packaged ham. Journal of Food Engineering. 216. pp.20-26.
Malawski, M., Juve, G., Deelman, E. and Nabrzyski, J., 2015. Algorithms for cost-and
deadline-constrained provisioning for scientific workflow ensembles in IaaS clouds. Future
Generation Computer Systems. 48. pp.1-18.
Mikhail, D. S., et al., 2018. Methodology of a multispecialty outpatient Obesity Treatment
Research Program. Contemporary clinical trials communications. 10. pp.36-41.
Mishra, S. K., Khan, M. A., Sahoo, B. and Jena, S. K., 2017, April. Time efficient task
allocation in cloud computing environment. In 2017 2nd International Conference for
Convergence in Technology (I2CT) (pp. 715-720). IEEE.

Mishra, S. K., Sahoo, B. and Parida, P. P., 2018. Load balancing in cloud computing: a big
picture. Journal of King Saud University-Computer and Information Sciences.
Molina, A. I., Navarro, Ó., Ortega, M. and Lacruz, M., 2018. Evaluating multimedia learning
materials in primary education using eye tracking. Computer Standards & Interfaces. 59.
pp.45-60.
Muhammad, G., Alhamid, M.F., Alsulaiman, M. and Gupta, B., 2018. Edge computing with
cloud for voice disorder assessment and treatment. IEEE Communications Magazine. 56(4).
pp.60-65.
Nunes, G. L., Roque, A. S., Araújo, S. R. and Pereira, C. E., 2018. Downlink cyclic resources
scheduling algorithm for industrial wireless M2M communication. IFAC-PapersOnLine.
51(10). pp.157-162
Núñez, R. N., Veglia, A.V. and Pacioni, N. L., 2018. Improving reproducibility between
batches of silver nanoparticles using an experimental design approach. Microchemical
Journal. 141. pp.110-117.
Pienta, R., et al., 2018. Vigor: Interactive visual exploration of graph query results. IEEE
transactions on visualization and computer graphics. 24(1). pp.215-225.
Prabhakaran, V., Balamurugan, S. and Charanyaa, S., 2015. Data flow modelling for
effective protection of electronic health records (EHRs) in cloud. International Journal of
Innovative Research in Computer and Communication Engineering. 3. pp.77-84.
Radivojević, M., et al., 2018. Experimental design of the Cu-As-Sn ternary colour
diagram. Journal of Archaeological Science. 90. pp.106-119.
Reani, M., Davies, A., Peek, N. and Jay, C., 2018. How do people use information
presentation to make decisions in Bayesian reasoning tasks?. International Journal of
Human-Computer Studies. 111.pp.62-77.
Reani, M., Peek, N. and Jay, C., 2019. How different visualizations affect human reasoning
about uncertainty: An analysis of visual behaviour. Computers in Human Behavior. 92.
pp.55-64.
Rittinghouse, J. W. and Ransome, J. F., 2016. Cloud computing: implementation,
management, and security. CRC press.
Sale, J. E. and Thielke, S., 2018. Qualitative research is a fundamental scientific
process. Journal of clinical epidemiology. 102. pp.129-133.
Schemer, L., et al., 2018. Treatment processes during exposure and cognitive-behavioral
therapy for chronic back pain: A single-case experimental design with multiple
baselines. Behaviour research and therapy. 108. pp.58-67.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Shaik, S. and Baskiyar, S., 2018, September. Network-Aware Service Pricing Approach for
Fog Infrastructure as a Service. In 2018 IEEE International Conference on Smart Cloud
(SmartCloud) (pp. 202-207). IEEE.
Sharifpour, E., Khafri, H. Z., Ghaedi, M., Asfaram, A. and Jannesar, R., 2018. Isotherms and
kinetic study of ultrasound-assisted adsorption of malachite green and Pb2+ ions from
aqueous samples by copper sulfide nanorods loaded on activated carbon: experimental
design optimization. Ultrasonics sonochemistry. 40. pp.373-382.
Shi, J., Luo, J., Dong, F., Zhang, J. and Zhang, J., 2016. Elastic resource provisioning for
scientific workflow scheduling in cloud under budget and deadline constraints. Cluster
Computing. 19(1). pp.167-182.
Stergiou, C., Psannis, K. E., Kim, B. G. and Gupta, B., 2018. Secure integration of IoT and
cloud computing. Future Generation Computer Systems. 78. pp.964-975.
Varghese, B. and Buyya, R., 2018. Next generation cloud computing: New trends and
research directions. Future Generation Computer Systems. 79. pp.849-861.
Wang, H., Wang, Z. and Domingo-Ferrer, J., 2018. Anonymous and secure aggregation
scheme in fog-based public cloud computing. Future Generation Computer Systems. 78.
pp.712-719.
Wang, L. and Gelenbe, E., 2018. Adaptive dispatching of tasks in the cloud. IEEE
Transactions on Cloud Computing. 6(1). pp.33-45.
Wang, Y. and Lu, P., 2013. Maximizing active storage resources with deadlock avoidance in
workflow-based computations. IEEE Transactions on Computers. 62(11). pp.2210-2223.
Wang, Y., Lu, P. and Kent, K. B., 2015. WaFS: a workflow-aware file system for effective
storage utilization in the cloud. IEEE Transactions on Computers. 64(9). pp.2716-2729.
Wu, C. Q. and Cao, H., 2016, June. Optimizing the performance of big data workflows in
multi-cloud environments under budget constraint. In 2016 IEEE International Conference
on Services Computing (SCC) (pp. 138-145). IEEE.
Wu, C.Q., Lin, X., Yu, D., Xu, W. and Li, L., 2015. End-to-end delay minimization for
scientific workflows in clouds under budget constraint. IEEE Transactions on Cloud
Computing. 3(2). pp.169-181.
Yan, H., Yu, P. and Long, D., 2019, January. Study on Deep Unsupervised Learning
Optimization Algorithm Based on Cloud Computing. In 2019 International Conference on
Intelligent Transportation, Big Data & Smart City (ICITBS) (pp. 679-681). IEEE.
Yu, R., et al., 2018. Decentralized and optimal resource cooperation in geo-distributed mobile
cloud computing. IEEE Transactions on Emerging Topics in Computing. 6(1). pp.72-84.
Paraphrase This Document

Zhang, Q., Yang, L.T., Chen, Z., Li, P. and Bu, F., 2018. An adaptive droupout deep
computation model for industrial IoT big data learning with crowdsourcing to cloud
computing. IEEE Transactions on Industrial Informatics.
Zhang, Y., Deng, R. H., Liu, X. and Zheng, D., 2018. Blockchain based efficient and robust
fair payment for outsourcing services in cloud computing. Information Sciences. 462.
pp.262-277.
Ziaeinejad, S. and Mehrizi-Sani, A., 2019. PWM A-CHB Converter Based on Trinary
Multilevel Converter: Topology, Switching Algorithm, and Stability Analysis. IEEE
Transactions on Industrial Electronics. 66(6). pp.4166-4176.
Online
Cloud market revenue, 2018. Available through: < https://www.skyhighnetworks.com/cloud-
security-blog/microsoft-azure-closes-iaas-adoption-gap-with-amazon-aws/> [Accessed on
4th may 2019].
Global public cloud service revenue, 2018. Available through:
<https://www.forbes.com/sites/louiscolumbus/2018/09/23/roundup-of-cloud-computing-
forecasts-and-market-estimates-2018/#6f671b65507b> [Accessed on 4th may 2019].
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
© 2024 | Zucol Services PVT LTD | All rights reserved.





