Hashing Software for Network Security
VerifiedAdded on 2022/12/18
|12
|1643
|1
AI Summary
This document discusses the importance of hashing software in network security and data integrity. It provides an overview of different hashing software tools and their features. The document also explains the concept of hashing, its role in ensuring data integrity, and the properties of a good hash algorithm. Additionally, it explores the types of data acquisitions in forensic investigations and the significance of digital forensic examination in recovering deleted data from hard drives.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

1
Network security
Student’s Name:
Institution Affiliation:
Network security
Student’s Name:
Institution Affiliation:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2
Introduction
Business explorers today frequently convey a few versatile gadgets to keep connected while
away. These gadgets represent an alluring objective to criminals for the private data they contain.
As digital and data security dangers become increasingly complex, the dangers to this data is
additionally elevated.
Task 1 : Hashing software
Hashing is an algorithm that computes a fixed-size bit string value from a record. A document
essentially contains blocks of information. Hashing changes this information into a far shorter
fixed-length worth or key which speaks to the first string. The hash worth can be viewed as the
refined synopsis of everything inside that document(Grevers, Kannan, Klecka III, & Cisco
Technology Inc, 2019).
a) IgorWare Hasher
Introduction
Business explorers today frequently convey a few versatile gadgets to keep connected while
away. These gadgets represent an alluring objective to criminals for the private data they contain.
As digital and data security dangers become increasingly complex, the dangers to this data is
additionally elevated.
Task 1 : Hashing software
Hashing is an algorithm that computes a fixed-size bit string value from a record. A document
essentially contains blocks of information. Hashing changes this information into a far shorter
fixed-length worth or key which speaks to the first string. The hash worth can be viewed as the
refined synopsis of everything inside that document(Grevers, Kannan, Klecka III, & Cisco
Technology Inc, 2019).
a) IgorWare Hasher
3
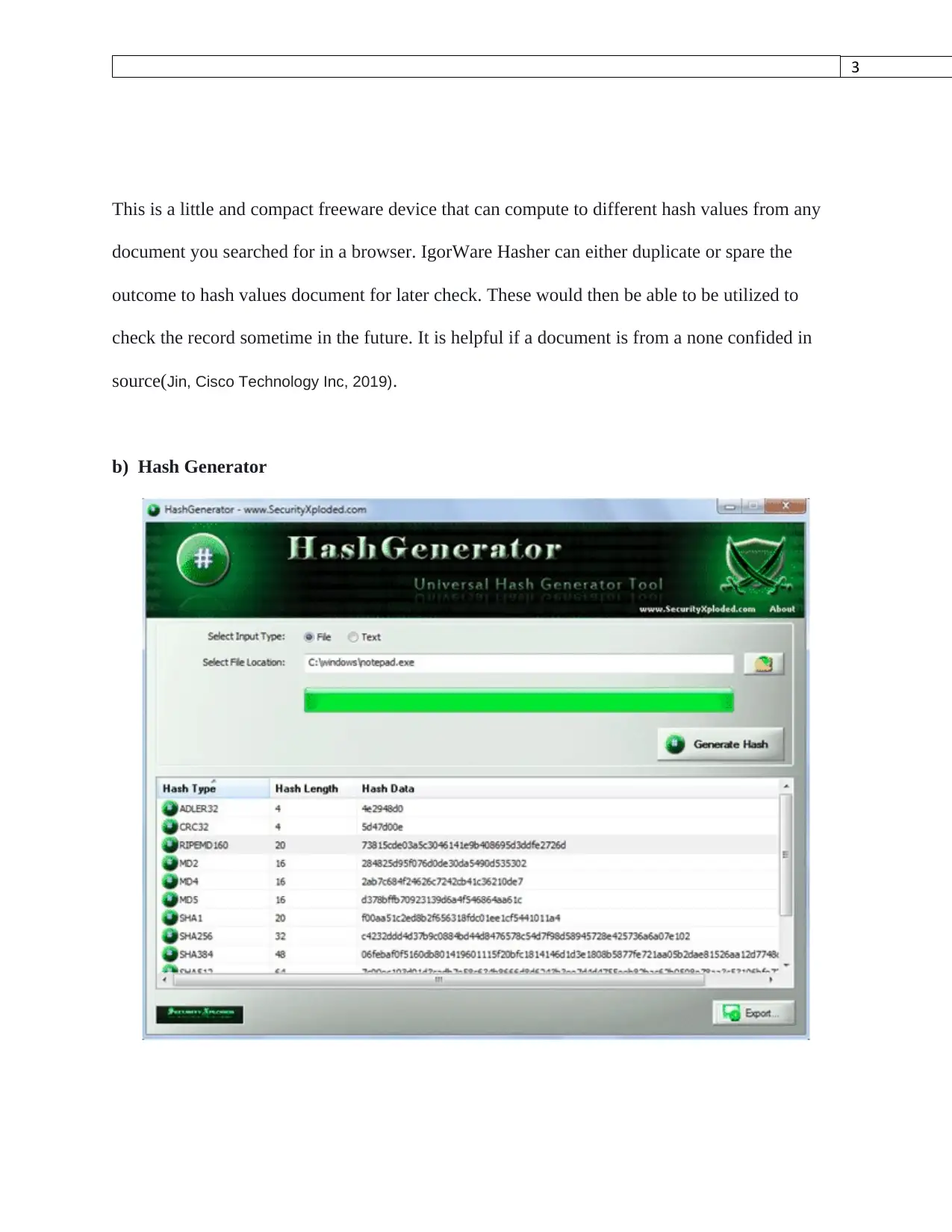
This is a little and compact freeware device that can compute to different hash values from any
document you searched for in a browser. IgorWare Hasher can either duplicate or spare the
outcome to hash values document for later check. These would then be able to be utilized to
check the record sometime in the future. It is helpful if a document is from a none confided in
source(Jin, Cisco Technology Inc, 2019).
b) Hash Generator
This is a little and compact freeware device that can compute to different hash values from any
document you searched for in a browser. IgorWare Hasher can either duplicate or spare the
outcome to hash values document for later check. These would then be able to be utilized to
check the record sometime in the future. It is helpful if a document is from a none confided in
source(Jin, Cisco Technology Inc, 2019).
b) Hash Generator
4
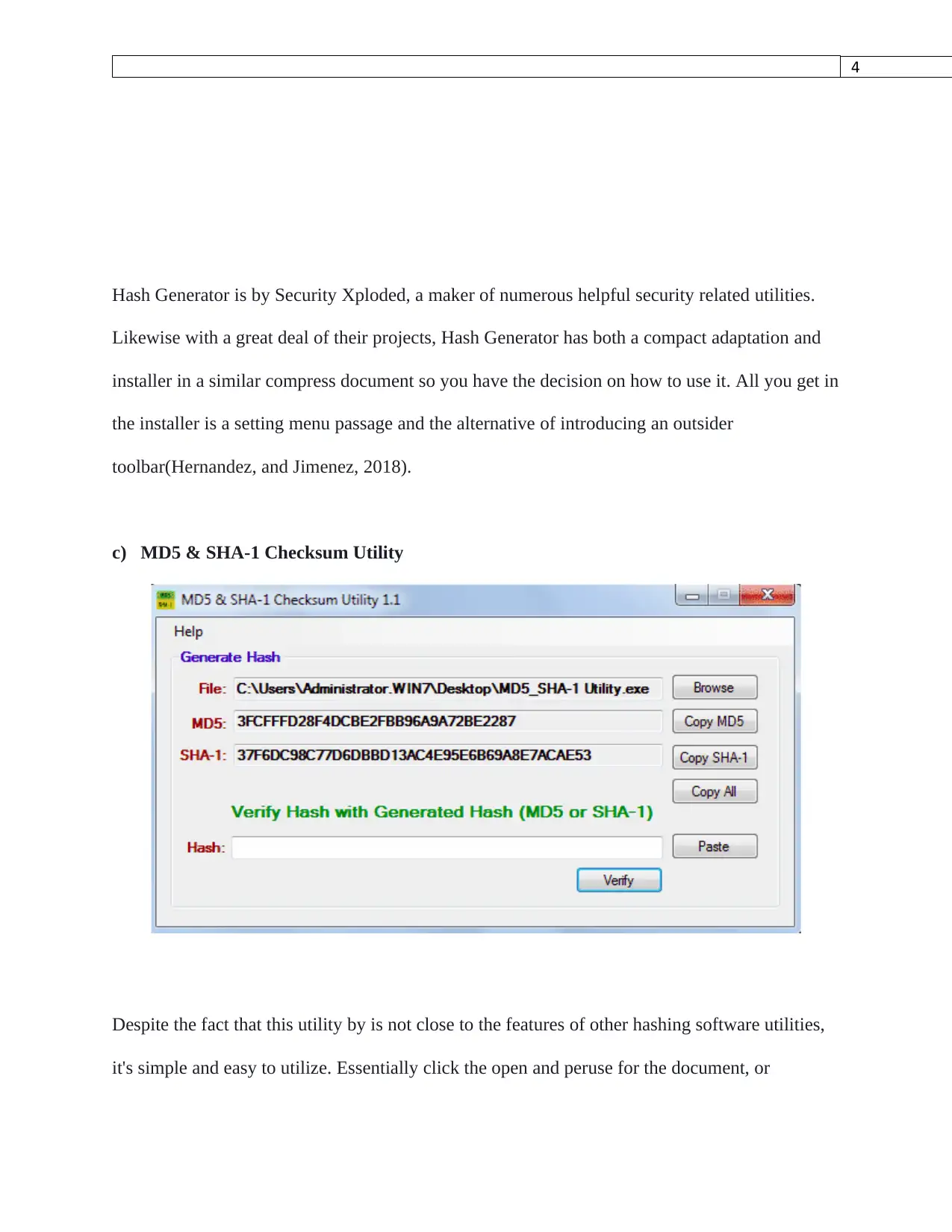
Hash Generator is by Security Xploded, a maker of numerous helpful security related utilities.
Likewise with a great deal of their projects, Hash Generator has both a compact adaptation and
installer in a similar compress document so you have the decision on how to use it. All you get in
the installer is a setting menu passage and the alternative of introducing an outsider
toolbar(Hernandez, and Jimenez, 2018).
c) MD5 & SHA-1 Checksum Utility
Despite the fact that this utility by is not close to the features of other hashing software utilities,
it's simple and easy to utilize. Essentially click the open and peruse for the document, or
Hash Generator is by Security Xploded, a maker of numerous helpful security related utilities.
Likewise with a great deal of their projects, Hash Generator has both a compact adaptation and
installer in a similar compress document so you have the decision on how to use it. All you get in
the installer is a setting menu passage and the alternative of introducing an outsider
toolbar(Hernandez, and Jimenez, 2018).
c) MD5 & SHA-1 Checksum Utility
Despite the fact that this utility by is not close to the features of other hashing software utilities,
it's simple and easy to utilize. Essentially click the open and peruse for the document, or
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

5
simplified, at that point the MD5 and SHA1 hash esteems will show up. In the event that you
need to check the produced hash with a past one, simply paste it and Verify(Kamath, Singh, and
Dutta, 2018).
Task 2: Case project
A decent hashing algorithm would show a property called the torrential slide impact, where the
subsequent hash yield would change essentially or totally notwithstanding when a solitary bit or
byte of information inside a document is changed. A hash function that doesn't do this is
considered to have poor randomization, which would be anything but difficult to break by
programmers.
A hash is normally a hexadecimal string of a few characters. Hashing is likewise a unidirectional
procedure so you can never work in reverse to get back the first information(Kwak, and Song,
Samsung Electronics Co Ltd, 2018).
A decent hash algorithm ought to be mind boggling enough with the end goal that it doesn't
deliver a similar hash an incentive from two unique information sources. On the off chance that
it does, this is known as a hash crash. A hash algorithm must be viewed as great and adequate on
the off chance that it can offer an exceptionally low collision impact.
Hashing is significant in light of the fact that it gives a strategy for guaranteeing information
trustworthiness; that is, a check that the information has not been either deliberately or
inadvertently adjusted. Information can be a string of content (model: secret key stockpiling), a
simplified, at that point the MD5 and SHA1 hash esteems will show up. In the event that you
need to check the produced hash with a past one, simply paste it and Verify(Kamath, Singh, and
Dutta, 2018).
Task 2: Case project
A decent hashing algorithm would show a property called the torrential slide impact, where the
subsequent hash yield would change essentially or totally notwithstanding when a solitary bit or
byte of information inside a document is changed. A hash function that doesn't do this is
considered to have poor randomization, which would be anything but difficult to break by
programmers.
A hash is normally a hexadecimal string of a few characters. Hashing is likewise a unidirectional
procedure so you can never work in reverse to get back the first information(Kwak, and Song,
Samsung Electronics Co Ltd, 2018).
A decent hash algorithm ought to be mind boggling enough with the end goal that it doesn't
deliver a similar hash an incentive from two unique information sources. On the off chance that
it does, this is known as a hash crash. A hash algorithm must be viewed as great and adequate on
the off chance that it can offer an exceptionally low collision impact.
Hashing is significant in light of the fact that it gives a strategy for guaranteeing information
trustworthiness; that is, a check that the information has not been either deliberately or
inadvertently adjusted. Information can be a string of content (model: secret key stockpiling), a

6
record (model: linux .deb document), an entire hard-drive (model: think measurable
examination), and so forth.
On a fundamental level, a hashing capacity restores a cluster file straightforwardly. It is expected
to utilize its (arbitrary) return esteem modulo the quantity of buckets as the real file. Utilizing a
prime number of buckets that isn't excessively near an intensity of two will in general produce an
adequately uniform key appropriation(Liu, Kashef, Lee, Benmohamed, and Candell, 2019).
The straightforward method to determine collision is to abstain from putting away keys and
values legitimately in buckets, and to utilize per-pail connected records. To locate a specific
worth, its key is hashed to discover the file of a bucket, and the connected rundown is filtered to
locate the precise key. The rundowns are known as chains, and this method is called
chaining(Moniz, Pedro, and Pires, 2019).
Steps of hashing with Hash Generator
Step 1: Input a file
record (model: linux .deb document), an entire hard-drive (model: think measurable
examination), and so forth.
On a fundamental level, a hashing capacity restores a cluster file straightforwardly. It is expected
to utilize its (arbitrary) return esteem modulo the quantity of buckets as the real file. Utilizing a
prime number of buckets that isn't excessively near an intensity of two will in general produce an
adequately uniform key appropriation(Liu, Kashef, Lee, Benmohamed, and Candell, 2019).
The straightforward method to determine collision is to abstain from putting away keys and
values legitimately in buckets, and to utilize per-pail connected records. To locate a specific
worth, its key is hashed to discover the file of a bucket, and the connected rundown is filtered to
locate the precise key. The rundowns are known as chains, and this method is called
chaining(Moniz, Pedro, and Pires, 2019).
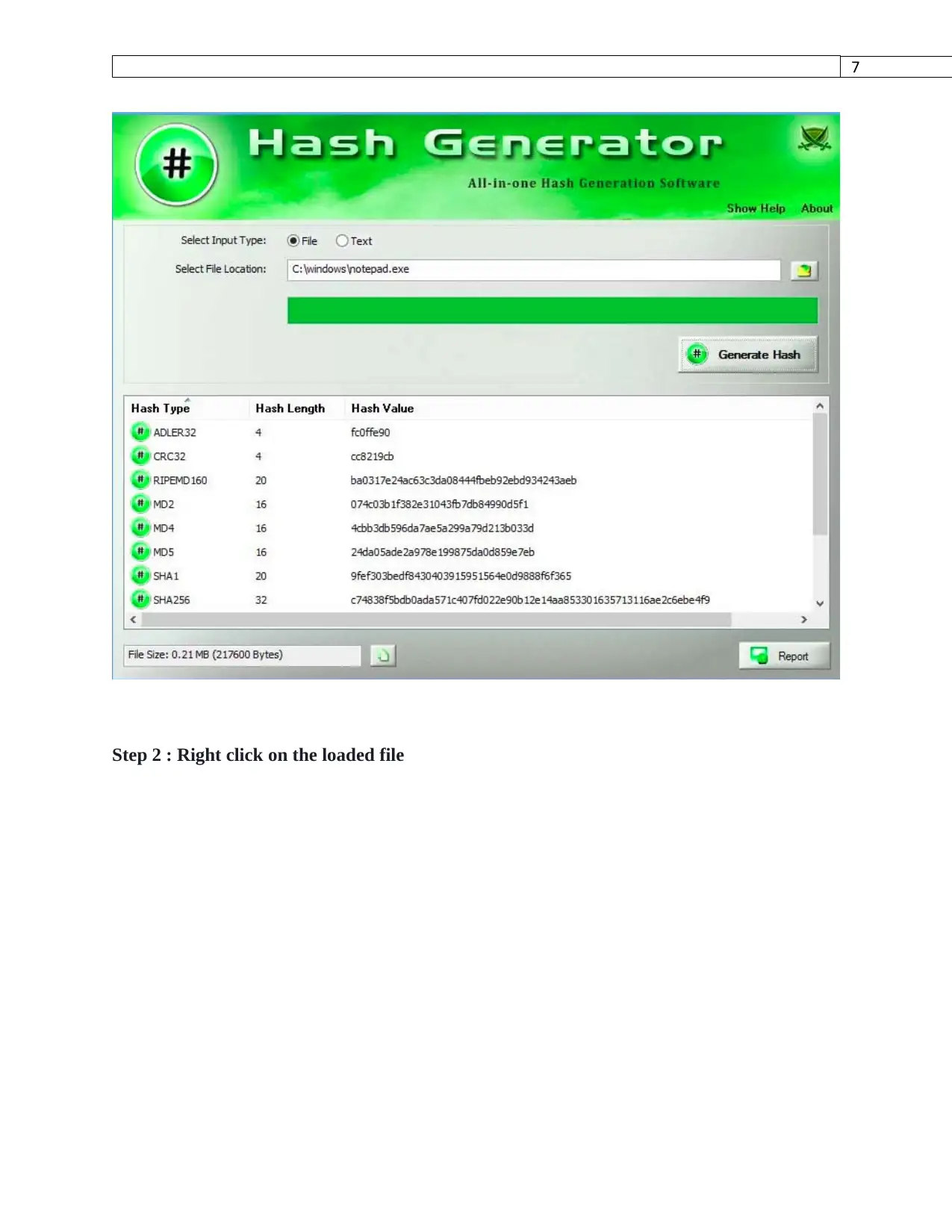
Steps of hashing with Hash Generator
Step 1: Input a file
7
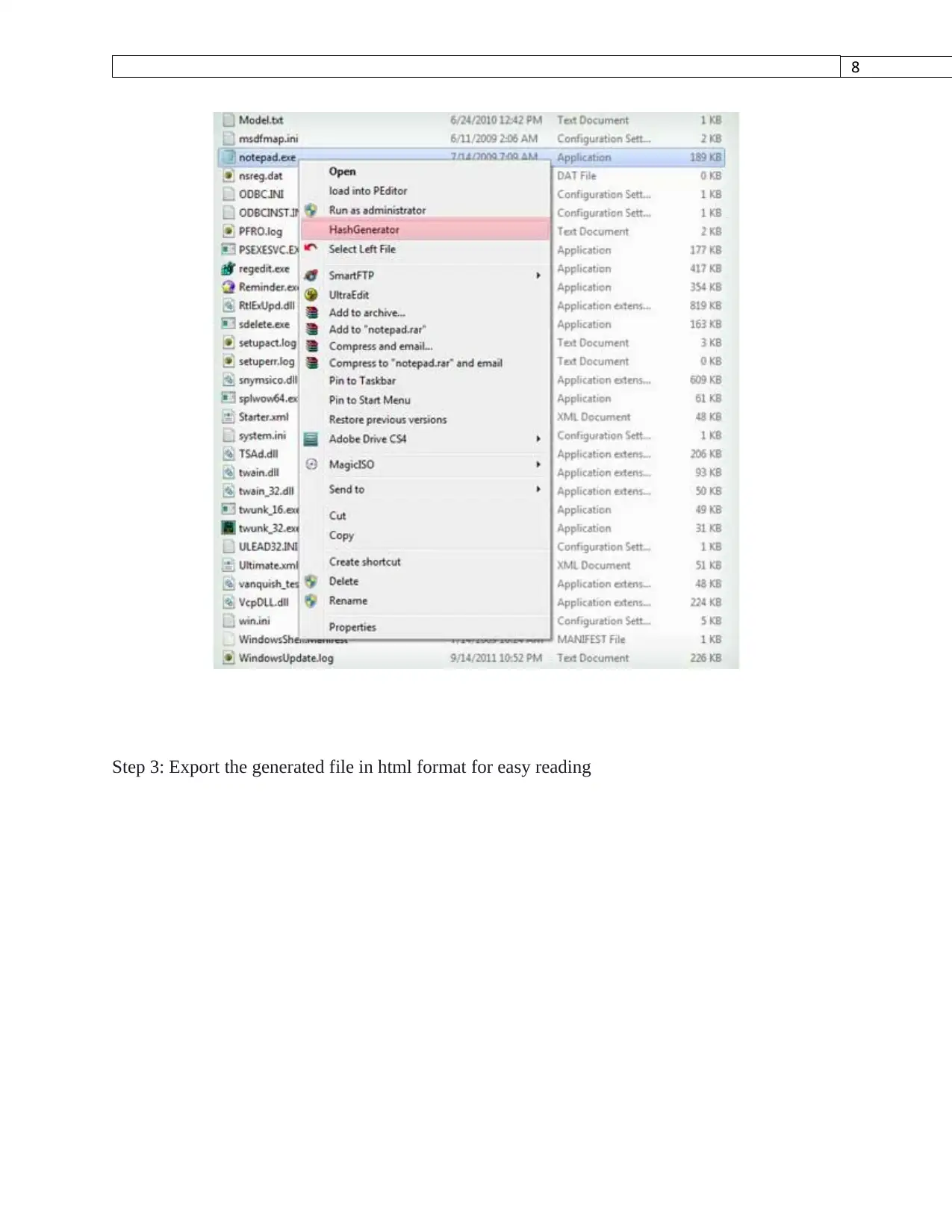
Step 2 : Right click on the loaded file
Step 2 : Right click on the loaded file
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
8
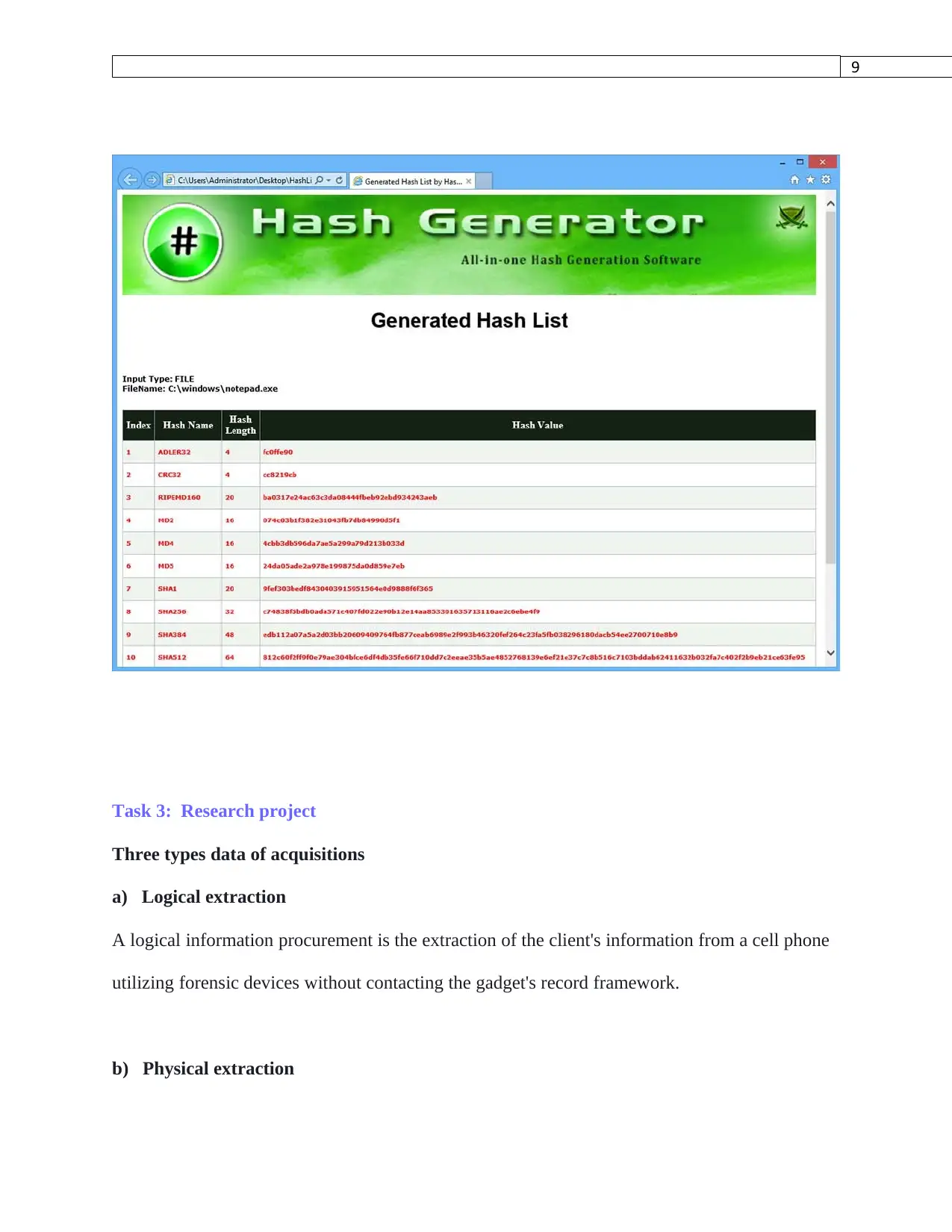
Step 3: Export the generated file in html format for easy reading
Step 3: Export the generated file in html format for easy reading
9
Task 3: Research project
Three types data of acquisitions
a) Logical extraction
A logical information procurement is the extraction of the client's information from a cell phone
utilizing forensic devices without contacting the gadget's record framework.
b) Physical extraction
Task 3: Research project
Three types data of acquisitions
a) Logical extraction
A logical information procurement is the extraction of the client's information from a cell phone
utilizing forensic devices without contacting the gadget's record framework.
b) Physical extraction

10
It is a sort of information collection that incorporates framework documents, application
information, and other data, that isn't assessable to the client by means of the GUI of the gadget.
It tends to be considered as the total portrayal of information stored in the real mobile flash
gadgets or other storage gadgets but measurable tools like encase, and so on for making a picture
document.
c) File system extraction
Defined as the accumulations of records and folders that the gadget utilized alongside as
available applications, framework arrangements, and client setups and client storage zones
(media records, archives, zip, and different configurations).
The information stored inside each hard drive recounts to a story. A criminological specialist's
main responsibility is to look at the information cautiously and sort out the story as precisely as
could be expected under the circumstances. The records on a hard drive and the metadata
characterizing them can uncover how and when the hard drive was utilized. When were records
made on the drive, and when were they changed? Who was utilizing the hard drive? Which
gadgets, (for example, cell phones or USB blaze drives) were associated with the PC when it was
being used? A talented and learned scientific examiner can reveal the responses to these
inquiries(Santos, and Marcillo, 2018).
The vast majority of the hard drives experienced by legal agents are fit. Yet, there are
circumstances in which someone has purposefully attempted to pulverize the information on a
It is a sort of information collection that incorporates framework documents, application
information, and other data, that isn't assessable to the client by means of the GUI of the gadget.
It tends to be considered as the total portrayal of information stored in the real mobile flash
gadgets or other storage gadgets but measurable tools like encase, and so on for making a picture
document.
c) File system extraction
Defined as the accumulations of records and folders that the gadget utilized alongside as
available applications, framework arrangements, and client setups and client storage zones
(media records, archives, zip, and different configurations).
The information stored inside each hard drive recounts to a story. A criminological specialist's
main responsibility is to look at the information cautiously and sort out the story as precisely as
could be expected under the circumstances. The records on a hard drive and the metadata
characterizing them can uncover how and when the hard drive was utilized. When were records
made on the drive, and when were they changed? Who was utilizing the hard drive? Which
gadgets, (for example, cell phones or USB blaze drives) were associated with the PC when it was
being used? A talented and learned scientific examiner can reveal the responses to these
inquiries(Santos, and Marcillo, 2018).
The vast majority of the hard drives experienced by legal agents are fit. Yet, there are
circumstances in which someone has purposefully attempted to pulverize the information on a
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

11
hard drive, either by erasing it from the drive or reformatting the drive to delete its substance. An
unpracticed individual endeavoring to inspect the information on a hard drive can likewise
prompt accidental information deterioration. At the point when these things occur, recounting to
the tale of a hard drive's utilization turns out to be significantly more troublesome, requiring the
guide of experience information forensic experts to rescue missing information.
Conclusion
In conclusion, the significance of computerized scientific examination of document System in
recouping erased information from the hard drive have been highlighted. The shrouded
information and investigation is significant as it helps in distinguishing suspicious or touchy data
covered up by noxious insider or outside elements. Subsequent to experiencing the different
existing calculations to recognize and show shrouded information, recuperation of erased records
and legal examination of the erased records and by considering existing distinctive document.
hard drive, either by erasing it from the drive or reformatting the drive to delete its substance. An
unpracticed individual endeavoring to inspect the information on a hard drive can likewise
prompt accidental information deterioration. At the point when these things occur, recounting to
the tale of a hard drive's utilization turns out to be significantly more troublesome, requiring the
guide of experience information forensic experts to rescue missing information.
Conclusion
In conclusion, the significance of computerized scientific examination of document System in
recouping erased information from the hard drive have been highlighted. The shrouded
information and investigation is significant as it helps in distinguishing suspicious or touchy data
covered up by noxious insider or outside elements. Subsequent to experiencing the different
existing calculations to recognize and show shrouded information, recuperation of erased records
and legal examination of the erased records and by considering existing distinctive document.

12
References
Grevers, T.R., Kannan, R.R., Klecka III, R.B. and Morris, G.F., Cisco Technology Inc,
2019. Automated network entity replacement based on historical topology consciousness.
U.S. Patent Application 15/808,984.
Hernandez, L. and Jimenez, G., 2018, April. Design and Validation of a Scheme of Infrastructure
of Servers, under the PPDIOO Methodology, in the University Institution-ITSA.
Jin, H., Cisco Technology Inc, 2019. Network architecture for predictive services management in cable
network environments. U.S. Patent Application 10/367,699.
Kamath, P., Singh, A. and Dutta, D., 2018. AMLA: an AutoML frAmework for Neural Network
Design. In International workshop on Automated Machine Learning.
Kwak, J. and Song, J., Samsung Electronics Co Ltd, 2018. Network terminal. U.S. Patent
Application 29/608,359.
Liu, Y., Kashef, M., Lee, K.B., Benmohamed, L. and Candell, R., 2019. Wireless Network Design for
Emerging IIoT Applications: Reference Framework and Use Cases. Proceedings of the
IEEE, 107(6), pp.1166-1192.
Moniz, D., Pedro, J. and Pires, J., 2019. Network design framework to optimally provision
services using higher-symbol rate line interfaces. Journal of Optical Communications
and Networking, 11(2), pp.A174-A185.
Santos, M.G.M. and Marcillo, P.A.A., 2018. Security in the data link layer of the OSI model on
LANs wired Cisco. Journal of Science and Research: Revista Ciencia e Investigación.
ISSN 2528-8083, 3(CITT2017), pp.106-112.
In Computer Science On-line Conference (pp. 367-379). Springer, Cham.
References
Grevers, T.R., Kannan, R.R., Klecka III, R.B. and Morris, G.F., Cisco Technology Inc,
2019. Automated network entity replacement based on historical topology consciousness.
U.S. Patent Application 15/808,984.
Hernandez, L. and Jimenez, G., 2018, April. Design and Validation of a Scheme of Infrastructure
of Servers, under the PPDIOO Methodology, in the University Institution-ITSA.
Jin, H., Cisco Technology Inc, 2019. Network architecture for predictive services management in cable
network environments. U.S. Patent Application 10/367,699.
Kamath, P., Singh, A. and Dutta, D., 2018. AMLA: an AutoML frAmework for Neural Network
Design. In International workshop on Automated Machine Learning.
Kwak, J. and Song, J., Samsung Electronics Co Ltd, 2018. Network terminal. U.S. Patent
Application 29/608,359.
Liu, Y., Kashef, M., Lee, K.B., Benmohamed, L. and Candell, R., 2019. Wireless Network Design for
Emerging IIoT Applications: Reference Framework and Use Cases. Proceedings of the
IEEE, 107(6), pp.1166-1192.
Moniz, D., Pedro, J. and Pires, J., 2019. Network design framework to optimally provision
services using higher-symbol rate line interfaces. Journal of Optical Communications
and Networking, 11(2), pp.A174-A185.
Santos, M.G.M. and Marcillo, P.A.A., 2018. Security in the data link layer of the OSI model on
LANs wired Cisco. Journal of Science and Research: Revista Ciencia e Investigación.
ISSN 2528-8083, 3(CITT2017), pp.106-112.
In Computer Science On-line Conference (pp. 367-379). Springer, Cham.
1 out of 12
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.