Security Risk Assessment for Data Services and Systems Pvt. Ltd.
VerifiedAdded on 2019/09/20
|17
|3540
|102
Report
AI Summary
This report presents a security risk assessment for Data Services and Systems Pvt. Ltd., a hypothetical data analytics company based in Guiyang, China. The assessment identifies twelve key security risks, categorized as adversarial (e.g., malware, phishing, brute force login) and non-adversarial (e.g., flooding, data mishandling). The report details the company's operational context, including its global client base, reliance on freelancers, and technological infrastructure. It outlines an Information Security Policy Statement and assesses the likelihood and impact of each risk. Mitigation strategies are proposed for six identified risks, with a focus on employee training to prevent phishing attacks, and other controls like network monitoring, access control, and data backup. The report emphasizes the importance of a robust Information Security Management System (ISMS) to protect the company's data and operations from various threats, including the risk of flooding due to the company's location.

0
Risk Assessment
Data Services and Systems Pvt. Ltd.
Student Name:
Course Name:
Risk Assessment
Data Services and Systems Pvt. Ltd.
Student Name:
Course Name:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
Abstract
The paper is concerned with identification of security risks for a company and understanding
the possible mitigation steps for them. The company selected for the assessment is Data
Services and Systems Pt. Ltd. It is a hypothetical company chosen for the security risk
assessment. The company deals in data analytics and services. The company is situated in
Guiyang city of China which is a flood prone location. The client base of the country is all
over the world. They are big and small businesses that need data analytic services for specific
market. The company is headquartered in Guiyang and accesses the data of various other
locations with the help of network of freelancers it has built in years.
The paper identified twelve security risks for the company. These security risks are: delivery
malware to internal system, network sniffing of exposed network, craft phishing attack, get
physical access through authorized staffs, communication interception attacks, brute force
login, spill sensitive information, flood at primary facility, mishandling of sensitive or critical
information, disk error, unreadable display, and incorrect privilege settings.
These risks were further analysed on various parameters and mitigation steps for six of the
risks were identified. There were multiple security controls identified to ensure that these
risks do not occur.
Abstract
The paper is concerned with identification of security risks for a company and understanding
the possible mitigation steps for them. The company selected for the assessment is Data
Services and Systems Pt. Ltd. It is a hypothetical company chosen for the security risk
assessment. The company deals in data analytics and services. The company is situated in
Guiyang city of China which is a flood prone location. The client base of the country is all
over the world. They are big and small businesses that need data analytic services for specific
market. The company is headquartered in Guiyang and accesses the data of various other
locations with the help of network of freelancers it has built in years.
The paper identified twelve security risks for the company. These security risks are: delivery
malware to internal system, network sniffing of exposed network, craft phishing attack, get
physical access through authorized staffs, communication interception attacks, brute force
login, spill sensitive information, flood at primary facility, mishandling of sensitive or critical
information, disk error, unreadable display, and incorrect privilege settings.
These risks were further analysed on various parameters and mitigation steps for six of the
risks were identified. There were multiple security controls identified to ensure that these
risks do not occur.

2
Table of Contents
Abstract......................................................................................................................................1
Introduction................................................................................................................................3
Scope of ISMS...........................................................................................................................3
Information Security Policy Statement......................................................................................3
Risk Assessment.........................................................................................................................3
Information Security Risks....................................................................................................3
Adversarial Risk.................................................................................................................4
Non-Adversarial Risk.........................................................................................................5
Response to Identified Risks......................................................................................................6
Information Security Controls....................................................................................................6
Conclusion..................................................................................................................................6
References..................................................................................................................................6
Table of Contents
Abstract......................................................................................................................................1
Introduction................................................................................................................................3
Scope of ISMS...........................................................................................................................3
Information Security Policy Statement......................................................................................3
Risk Assessment.........................................................................................................................3
Information Security Risks....................................................................................................3
Adversarial Risk.................................................................................................................4
Non-Adversarial Risk.........................................................................................................5
Response to Identified Risks......................................................................................................6
Information Security Controls....................................................................................................6
Conclusion..................................................................................................................................6
References..................................................................................................................................6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
Introduction
The company that has been selected for the assessment is Data Services and Systems Pt. Ltd.
It is a hypothetical company based out of Guiyang City, China. The company provides data
analytics services to various clients around the world. The client of the company ranges from
large companies to small companies and some governmental organizations. The company
operates with around fifty employees who work in-house. Along with that, the company also
has many individuals working for it as freelancers. The freelancers are located in various
countries around the world. They provide their services to the company from their respective
home countries. All the activities of the company are technology based and company has
never involved itself in the activities that require offline management. There are some
activities such as field survey for data collection that is conducted by country specific
freelance teams. The company is smaller in size and it has no head office outside China. The
only method that has been considered to operate for other countries is through the internet
based services. The data collection and management of those countries are taken care at the
head office. The data collection and compilation is done by the freelancers.
The company management is concerned about the various security risks that might impact the
organization’s activities in the days to come. Some of the concerns are related to security of
the data and information from physical and technical damages and others. Therefore, the
management is willing to implement Information Security Management System (ISMS) to
ensure that all the risks are taken care. Various chapters in this section are focused on
identifying the likely risks that can occur and then devising appropriate mitigations plans for
them. The second chapter discusses about the scope of the ISMS for the company. The third
chapter discusses the information security policy statement. The fourth chapter assesses the
Introduction
The company that has been selected for the assessment is Data Services and Systems Pt. Ltd.
It is a hypothetical company based out of Guiyang City, China. The company provides data
analytics services to various clients around the world. The client of the company ranges from
large companies to small companies and some governmental organizations. The company
operates with around fifty employees who work in-house. Along with that, the company also
has many individuals working for it as freelancers. The freelancers are located in various
countries around the world. They provide their services to the company from their respective
home countries. All the activities of the company are technology based and company has
never involved itself in the activities that require offline management. There are some
activities such as field survey for data collection that is conducted by country specific
freelance teams. The company is smaller in size and it has no head office outside China. The
only method that has been considered to operate for other countries is through the internet
based services. The data collection and management of those countries are taken care at the
head office. The data collection and compilation is done by the freelancers.
The company management is concerned about the various security risks that might impact the
organization’s activities in the days to come. Some of the concerns are related to security of
the data and information from physical and technical damages and others. Therefore, the
management is willing to implement Information Security Management System (ISMS) to
ensure that all the risks are taken care. Various chapters in this section are focused on
identifying the likely risks that can occur and then devising appropriate mitigations plans for
them. The second chapter discusses about the scope of the ISMS for the company. The third
chapter discusses the information security policy statement. The fourth chapter assesses the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
various security risks. The fifth chapter identifies the possible responses to the assessed risks
and the sixth chapter discusses the various security controls as per ISO 27002.
Scope of ISMS
The company is situated in Guiyang City which is the capital of Guizhou province of
Southwest China. The city receives flood almost every year. The company is physically
present at this city only and there is no other physical presence in any part of the world.
However, as per the business market is concerned, the company covers various countries
such as USA, European Countries, India, and others. The company is into data analytics and
management. The clients of the company hire it to conduct various forms of analysis to
understand and analyse the market trends and other aspects. The data is collected by the
company through online network of numerous freelancers active throughout the world. The
operations department of the company handles these freelancers. The department assigns
responsibilities to these freelancers through email and chat. The completed tasks are received
through emails. At present the company uses QQ as the mail and chat messenger to conduct
its business worldwide. The freelancers use QQ International to connect with the operations
department. The report related to completion of particular task such as data collection from
field, data collation and other activities are informed to the Finance department that in the end
of each month distributes the finance. The
The dependency on the online communication is huge within the company and it cannot
operate even for a single day without the presence of this aspect. The company has current 65
desktops, in which around ten are idle and the rest are functional. The operations department
uses around 30 of these computers and the rest of the computers are distributed among other
departments. All the computers are connected with High Speed Broadband for the internet
connection. The company also uses large data storage centre which is situated on the ground
various security risks. The fifth chapter identifies the possible responses to the assessed risks
and the sixth chapter discusses the various security controls as per ISO 27002.
Scope of ISMS
The company is situated in Guiyang City which is the capital of Guizhou province of
Southwest China. The city receives flood almost every year. The company is physically
present at this city only and there is no other physical presence in any part of the world.
However, as per the business market is concerned, the company covers various countries
such as USA, European Countries, India, and others. The company is into data analytics and
management. The clients of the company hire it to conduct various forms of analysis to
understand and analyse the market trends and other aspects. The data is collected by the
company through online network of numerous freelancers active throughout the world. The
operations department of the company handles these freelancers. The department assigns
responsibilities to these freelancers through email and chat. The completed tasks are received
through emails. At present the company uses QQ as the mail and chat messenger to conduct
its business worldwide. The freelancers use QQ International to connect with the operations
department. The report related to completion of particular task such as data collection from
field, data collation and other activities are informed to the Finance department that in the end
of each month distributes the finance. The
The dependency on the online communication is huge within the company and it cannot
operate even for a single day without the presence of this aspect. The company has current 65
desktops, in which around ten are idle and the rest are functional. The operations department
uses around 30 of these computers and the rest of the computers are distributed among other
departments. All the computers are connected with High Speed Broadband for the internet
connection. The company also uses large data storage centre which is situated on the ground

5
floor of the company headquarter. The data centre of the company uses various components
for its functioning. Some of the important components are heat exchanger, transformers,
server room, cooling-units, extinguishing gas, diesel generators, cooling water, batteries,
telecommunications, and video cameras. The company uses different software available for
different types of data analysis and maintenance such as IBM’s SPSS, R, and others. There
are some more technological assets such as iPads, laptops, mobile phones, landline
connection, and others.
The company’s headquarter is a six storey building. The ground floor has the data centre, and
the rest of floors are for staffs and company management. Other than the technological assets,
and building, the company has furniture sets used by the staffs to work.
Information Security Policy Statement
Given below is the information security policy that is active within the company:
1. The company will safeguard the entire information received from the client.
2. The data and information will be kept confidential from access to any third party until
ordered to do so by the management.
3. It should be ensured that the network infrastructure available is reliable and sound for
proper functioning of the business.
4. The compliance to international information security standards should be followed.
5. The management of the organization will handle all the security related issues and the
changes in the policy will on its discretion.
6. The continued assessment of the risks should be done to ensure any shortcomings are
identified as early as possible.
7. Before or after the implementation of any changes within the organization should be
followed by security assessment.
floor of the company headquarter. The data centre of the company uses various components
for its functioning. Some of the important components are heat exchanger, transformers,
server room, cooling-units, extinguishing gas, diesel generators, cooling water, batteries,
telecommunications, and video cameras. The company uses different software available for
different types of data analysis and maintenance such as IBM’s SPSS, R, and others. There
are some more technological assets such as iPads, laptops, mobile phones, landline
connection, and others.
The company’s headquarter is a six storey building. The ground floor has the data centre, and
the rest of floors are for staffs and company management. Other than the technological assets,
and building, the company has furniture sets used by the staffs to work.
Information Security Policy Statement
Given below is the information security policy that is active within the company:
1. The company will safeguard the entire information received from the client.
2. The data and information will be kept confidential from access to any third party until
ordered to do so by the management.
3. It should be ensured that the network infrastructure available is reliable and sound for
proper functioning of the business.
4. The compliance to international information security standards should be followed.
5. The management of the organization will handle all the security related issues and the
changes in the policy will on its discretion.
6. The continued assessment of the risks should be done to ensure any shortcomings are
identified as early as possible.
7. Before or after the implementation of any changes within the organization should be
followed by security assessment.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
8. The access to sensitive information will be protected within multiple layers and will
be accessed by authorized personnel only.
9. The information should be segregated into sensitive and general information the
moment it arrives to make a clear distinction and management (Bulgurcu et al, 2010).
10. While at employment, all the information generated by a particular employee will be
the asset of the company and will be stored in the company repository.
11. The employees are instructed not to use their personal equipment like laptops,
smartphones, and other such thing within the company premise to access the data and
information of the company (Hone and Eloff, 2002).
12. Use of any external storage device is not allowed with any computer or other
electronic equipment of the company.
13. All security issues must be reported to the management at shortest possible time.
Risk Assessment
This section is concerned with identification of various security risks that are likely to
threaten the functioning of the business. There are twelve security risks that have been
identified. Six of them are adversarial risk and the rest are non-adversarial risk (ISO 27002,
2005).
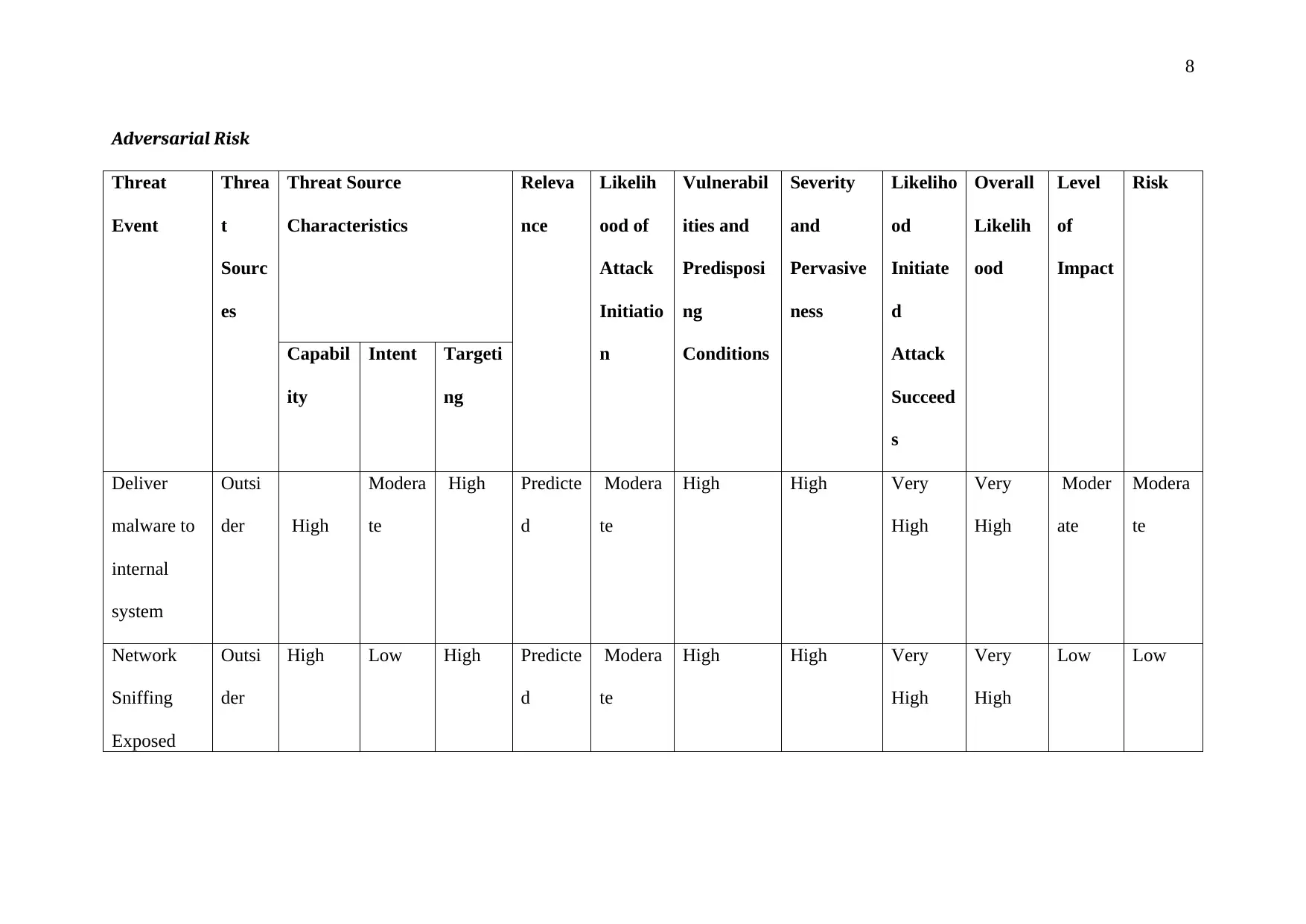
Given below are the adversarial risks that have been identified for the organization:
1. Deliver Malware to Internal System: The hackers from outside the organization can
insert malware into the system that can disrupt the functioning or steal information
that is sensitive. These are mostly done to sell the information to the competitors.
2. Network Sniffing of Exposed Network: The presence of any exposed network to the
external environment might allow the external party to gain the system access.
8. The access to sensitive information will be protected within multiple layers and will
be accessed by authorized personnel only.
9. The information should be segregated into sensitive and general information the
moment it arrives to make a clear distinction and management (Bulgurcu et al, 2010).
10. While at employment, all the information generated by a particular employee will be
the asset of the company and will be stored in the company repository.
11. The employees are instructed not to use their personal equipment like laptops,
smartphones, and other such thing within the company premise to access the data and
information of the company (Hone and Eloff, 2002).
12. Use of any external storage device is not allowed with any computer or other
electronic equipment of the company.
13. All security issues must be reported to the management at shortest possible time.
Risk Assessment
This section is concerned with identification of various security risks that are likely to
threaten the functioning of the business. There are twelve security risks that have been
identified. Six of them are adversarial risk and the rest are non-adversarial risk (ISO 27002,
2005).
Given below are the adversarial risks that have been identified for the organization:
1. Deliver Malware to Internal System: The hackers from outside the organization can
insert malware into the system that can disrupt the functioning or steal information
that is sensitive. These are mostly done to sell the information to the competitors.
2. Network Sniffing of Exposed Network: The presence of any exposed network to the
external environment might allow the external party to gain the system access.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
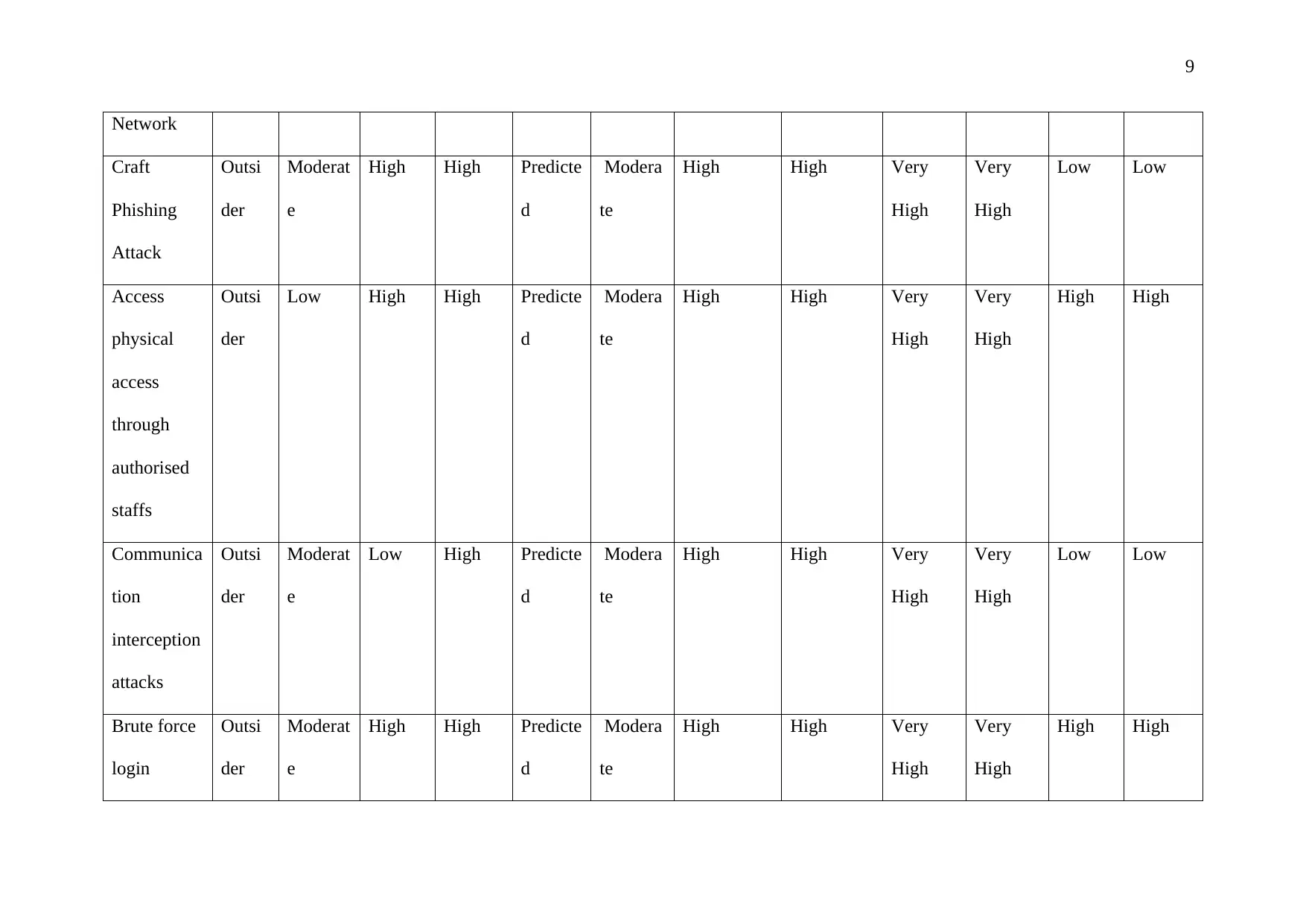
3. Craft Phishing attack: There can be various forms of phishing such as webpage
cloning or emails that seem to be coming from authorized personnel but not in actual.
4. Get physical access through authorized staffs: Stealing the access of authorized
person physically to get into the system.
5. Communication interception attacks: gaining access by attacking the
communication that use weak encryptions
6. Brute force login: External parties can guess access passwords and other
authorizations codes. Software to crack codes possibly used in these cases.
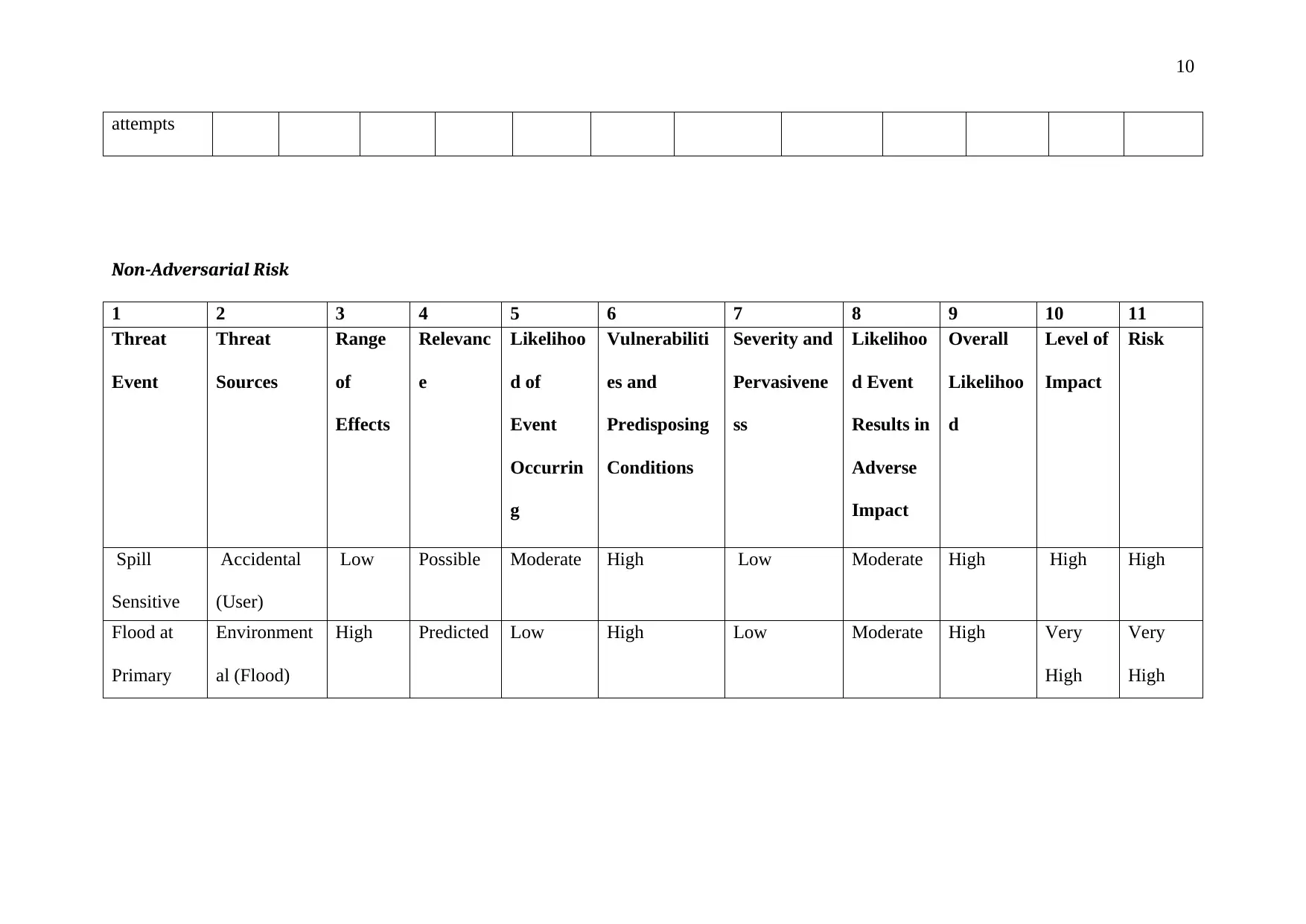
Given below are the non-adversarial risks that have been identified for the organization:
1. Spill sensitive information: it is about sending the sensitive material to the
unauthorized individuals.
2. Flood at primary facility: This company is located in Guiyang which is a flood
prone location. The location of server is on the first floor of the building and it is
likely to get impacted if flooding occurs. Therefore, flood is a major threat to the
company.
3. Mishandling of sensitive or critical information: Mishandles the information and
unknowingly leaves at places where it should not have been.
4. Disk error: Storage corruption occurrences that destroys the information present on
the disk
5. Unreadable display: The company has desktops that are of no appreciable quality
and it is expected that due to the poor display of some of the computer, challenge in
handling the information can come up.
6. Incorrect privilege settings: Due to the mistake of the administrators, some
unauthorized person is allowed access to sensitive material
3. Craft Phishing attack: There can be various forms of phishing such as webpage
cloning or emails that seem to be coming from authorized personnel but not in actual.
4. Get physical access through authorized staffs: Stealing the access of authorized
person physically to get into the system.
5. Communication interception attacks: gaining access by attacking the
communication that use weak encryptions
6. Brute force login: External parties can guess access passwords and other
authorizations codes. Software to crack codes possibly used in these cases.
Given below are the non-adversarial risks that have been identified for the organization:
1. Spill sensitive information: it is about sending the sensitive material to the
unauthorized individuals.
2. Flood at primary facility: This company is located in Guiyang which is a flood
prone location. The location of server is on the first floor of the building and it is
likely to get impacted if flooding occurs. Therefore, flood is a major threat to the
company.
3. Mishandling of sensitive or critical information: Mishandles the information and
unknowingly leaves at places where it should not have been.
4. Disk error: Storage corruption occurrences that destroys the information present on
the disk
5. Unreadable display: The company has desktops that are of no appreciable quality
and it is expected that due to the poor display of some of the computer, challenge in
handling the information can come up.
6. Incorrect privilege settings: Due to the mistake of the administrators, some
unauthorized person is allowed access to sensitive material
8
Adversarial Risk
Threat
Event
Threa
t
Sourc
es
Threat Source
Characteristics
Releva
nce
Likelih
ood of
Attack
Initiatio
n
Vulnerabil
ities and
Predisposi
ng
Conditions
Severity
and
Pervasive
ness
Likeliho
od
Initiate
d
Attack
Succeed
s
Overall
Likelih
ood
Level
of
Impact
Risk
Capabil
ity
Intent Targeti
ng
Deliver
malware to
internal
system
Outsi
der High
Modera
te
High Predicte
d
Modera
te
High High Very
High
Very
High
Moder
ate
Modera
te
Network
Sniffing
Exposed
Outsi
der
High Low High Predicte
d
Modera
te
High High Very
High
Very
High
Low Low
Adversarial Risk
Threat
Event
Threa
t
Sourc
es
Threat Source
Characteristics
Releva
nce
Likelih
ood of
Attack
Initiatio
n
Vulnerabil
ities and
Predisposi
ng
Conditions
Severity
and
Pervasive
ness
Likeliho
od
Initiate
d
Attack
Succeed
s
Overall
Likelih
ood
Level
of
Impact
Risk
Capabil
ity
Intent Targeti
ng
Deliver
malware to
internal
system
Outsi
der High
Modera
te
High Predicte
d
Modera
te
High High Very
High
Very
High
Moder
ate
Modera
te
Network
Sniffing
Exposed
Outsi
der
High Low High Predicte
d
Modera
te
High High Very
High
Very
High
Low Low
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
Network
Craft
Phishing
Attack
Outsi
der
Moderat
e
High High Predicte
d
Modera
te
High High Very
High
Very
High
Low Low
Access
physical
access
through
authorised
staffs
Outsi
der
Low High High Predicte
d
Modera
te
High High Very
High
Very
High
High High
Communica
tion
interception
attacks
Outsi
der
Moderat
e
Low High Predicte
d
Modera
te
High High Very
High
Very
High
Low Low
Brute force
login
Outsi
der
Moderat
e
High High Predicte
d
Modera
te
High High Very
High
Very
High
High High
Network
Craft
Phishing
Attack
Outsi
der
Moderat
e
High High Predicte
d
Modera
te
High High Very
High
Very
High
Low Low
Access
physical
access
through
authorised
staffs
Outsi
der
Low High High Predicte
d
Modera
te
High High Very
High
Very
High
High High
Communica
tion
interception
attacks
Outsi
der
Moderat
e
Low High Predicte
d
Modera
te
High High Very
High
Very
High
Low Low
Brute force
login
Outsi
der
Moderat
e
High High Predicte
d
Modera
te
High High Very
High
Very
High
High High
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
attempts
Non-Adversarial Risk
1 2 3 4 5 6 7 8 9 10 11
Threat
Event
Threat
Sources
Range
of
Effects
Relevanc
e
Likelihoo
d of
Event
Occurrin
g
Vulnerabiliti
es and
Predisposing
Conditions
Severity and
Pervasivene
ss
Likelihoo
d Event
Results in
Adverse
Impact
Overall
Likelihoo
d
Level of
Impact
Risk
Spill
Sensitive
Informatio
Accidental
(User)
Low Possible Moderate High Low Moderate High High High
Flood at
Primary
Facility
Environment
al (Flood)
High Predicted Low High Low Moderate High Very
High
Very
High
attempts
Non-Adversarial Risk
1 2 3 4 5 6 7 8 9 10 11
Threat
Event
Threat
Sources
Range
of
Effects
Relevanc
e
Likelihoo
d of
Event
Occurrin
g
Vulnerabiliti
es and
Predisposing
Conditions
Severity and
Pervasivene
ss
Likelihoo
d Event
Results in
Adverse
Impact
Overall
Likelihoo
d
Level of
Impact
Risk
Spill
Sensitive
Informatio
Accidental
(User)
Low Possible Moderate High Low Moderate High High High
Flood at
Primary
Facility
Environment
al (Flood)
High Predicted Low High Low Moderate High Very
High
Very
High
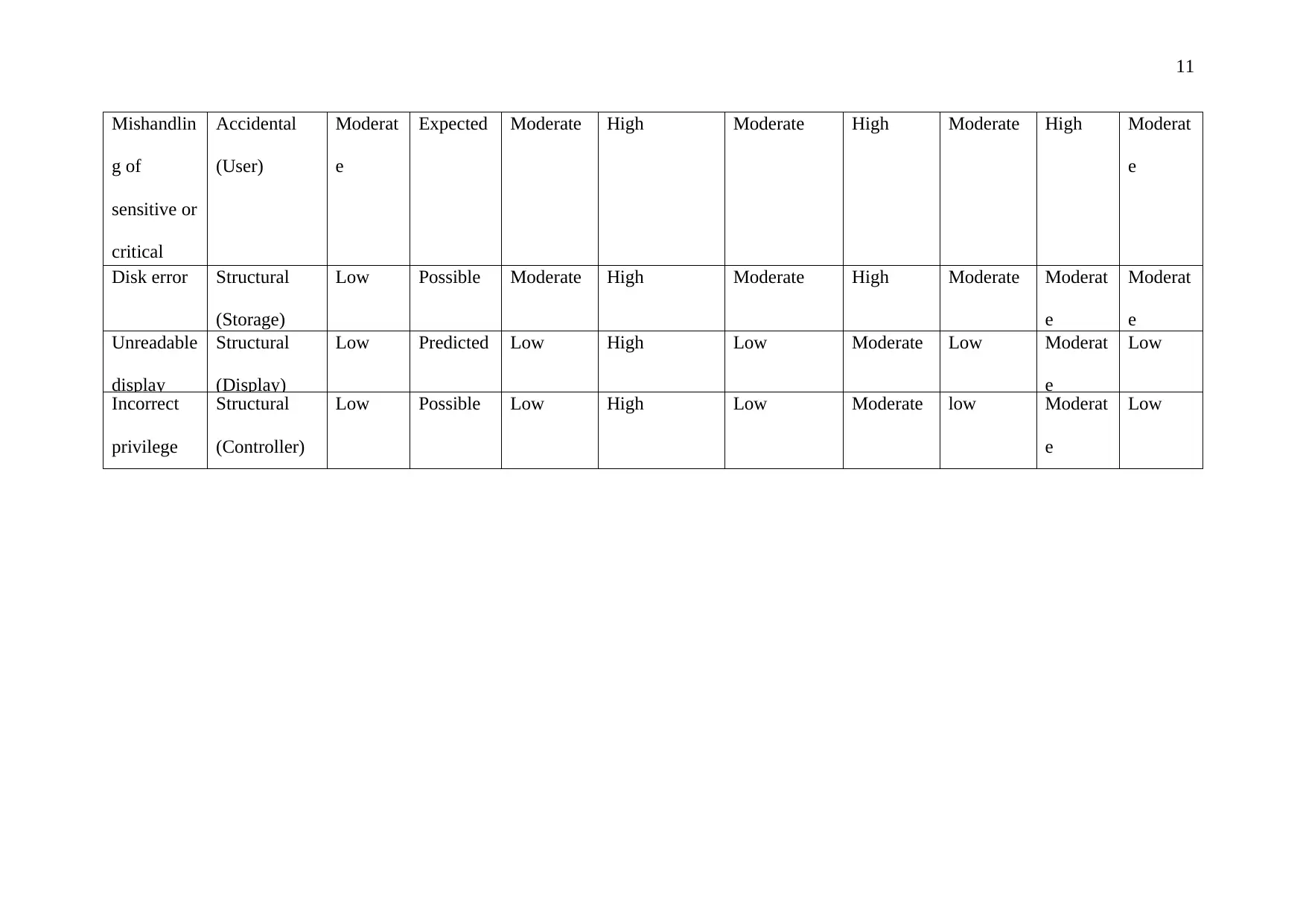
11
Mishandlin
g of
sensitive or
critical
informatio
Accidental
(User)
Moderat
e
Expected Moderate High Moderate High Moderate High Moderat
e
Disk error Structural
(Storage)
Low Possible Moderate High Moderate High Moderate Moderat
e
Moderat
e
Unreadable
display
Structural
(Display)
Low Predicted Low High Low Moderate Low Moderat
e
Low
Incorrect
privilege
settings
Structural
(Controller)
Low Possible Low High Low Moderate low Moderat
e
Low
Mishandlin
g of
sensitive or
critical
informatio
Accidental
(User)
Moderat
e
Expected Moderate High Moderate High Moderate High Moderat
e
Disk error Structural
(Storage)
Low Possible Moderate High Moderate High Moderate Moderat
e
Moderat
e
Unreadable
display
Structural
(Display)
Low Predicted Low High Low Moderate Low Moderat
e
Low
Incorrect
privilege
settings
Structural
(Controller)
Low Possible Low High Low Moderate low Moderat
e
Low
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




