Comprehensive IT/IS Risk Management Report for Caduceus Partners
VerifiedAdded on 2020/04/07
|25
|5698
|242
Report
AI Summary
This report provides a comprehensive analysis of IT/IS risk management for Caduceus Partners Pty Ltd, an infrastructural service provider to the medical sector. The report identifies and assesses various threats and vulnerabilities, including technical, operational, and managerial risks. It emphasize...

Running head: IT/IS RISK MANAGEEMENT
IT/IS Security Management
Name of the Student
Name of the University
Author Note
IT/IS Security Management
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT/IS SECURITY MANAGEMENT
Table of Contents
Introduction......................................................................................................................................2
Usage of Salient Features of an Established Risk Mitigation Framework:.....................................2
Identification and Analysis of the Threats and Vulnerabilities within Caduceus...........................5
The Technical Threats.................................................................................................................5
The operational threats................................................................................................................6
Managerial risks...........................................................................................................................7
Impact Analysis...............................................................................................................................7
Data Collection and Analysis......................................................................................................7
Planning Data Collection and Analysis.......................................................................................8
Data Collection............................................................................................................................9
Quantitative and Qualitative Approaches in Impact Evaluation.................................................9
Threats, risk and vulnerabilities assessment..............................................................................11
Risk severity matrix...................................................................................................................16
Legal and Regulatory Requirements.............................................................................................16
Conclusion.....................................................................................................................................18
References:....................................................................................................................................20
IT/IS SECURITY MANAGEMENT
Table of Contents
Introduction......................................................................................................................................2
Usage of Salient Features of an Established Risk Mitigation Framework:.....................................2
Identification and Analysis of the Threats and Vulnerabilities within Caduceus...........................5
The Technical Threats.................................................................................................................5
The operational threats................................................................................................................6
Managerial risks...........................................................................................................................7
Impact Analysis...............................................................................................................................7
Data Collection and Analysis......................................................................................................7
Planning Data Collection and Analysis.......................................................................................8
Data Collection............................................................................................................................9
Quantitative and Qualitative Approaches in Impact Evaluation.................................................9
Threats, risk and vulnerabilities assessment..............................................................................11
Risk severity matrix...................................................................................................................16
Legal and Regulatory Requirements.............................................................................................16
Conclusion.....................................................................................................................................18
References:....................................................................................................................................20

2
IT/IS SECURITY MANAGEMENT
Introduction
The Caduceus Partners Pty Ltd, Australia, also recognized as Caduceus, has specialized
in supplying the infrastructural services to the medical services. It has comprised of the Strategic
IS/IT division, the ream responsible to oversee the IT infrastructure. Moreover, it has been
looking actively for the latest technologies and applications bringing value to the organization.
The internet security management at Caduceus has been the set of procedures and
policies to manage the sensitive data of the organization systematically. The aim has been to
minimize the risk and assure the business continuity through limiting the effect of the security
breach proactively.
The report has identified the key components of the risks, threat and vulnerabilities along
with effect on Caduceus. It has determined the future scopes of risk management and the security
risk mitigation procedures. The study has provided the solution for the risks and produced an
effective risk analysis.
Usage of Salient Features of an Established Risk Mitigation Framework:
The risk management framework for the IS/IT Risk Management Project is needed to be
developed to eradicate the risks related to the development or inclusion of the technologies. The
framework is intended to deal with the variation of risks from the nominal values designed
inherent by any manufacturing process. For mitigating the risks the processes and products
should be characterized clearly (Shamala, Ahmad and Mariana 2013). The simulations are
helpful tools for modeling the behavior of the process and the product. The outcomes of the
numerical simulations help in recognizing the optimal design and conditions. Despite all this, the
IT/IS SECURITY MANAGEMENT
Introduction
The Caduceus Partners Pty Ltd, Australia, also recognized as Caduceus, has specialized
in supplying the infrastructural services to the medical services. It has comprised of the Strategic
IS/IT division, the ream responsible to oversee the IT infrastructure. Moreover, it has been
looking actively for the latest technologies and applications bringing value to the organization.
The internet security management at Caduceus has been the set of procedures and
policies to manage the sensitive data of the organization systematically. The aim has been to
minimize the risk and assure the business continuity through limiting the effect of the security
breach proactively.
The report has identified the key components of the risks, threat and vulnerabilities along
with effect on Caduceus. It has determined the future scopes of risk management and the security
risk mitigation procedures. The study has provided the solution for the risks and produced an
effective risk analysis.
Usage of Salient Features of an Established Risk Mitigation Framework:
The risk management framework for the IS/IT Risk Management Project is needed to be
developed to eradicate the risks related to the development or inclusion of the technologies. The
framework is intended to deal with the variation of risks from the nominal values designed
inherent by any manufacturing process. For mitigating the risks the processes and products
should be characterized clearly (Shamala, Ahmad and Mariana 2013). The simulations are
helpful tools for modeling the behavior of the process and the product. The outcomes of the
numerical simulations help in recognizing the optimal design and conditions. Despite all this, the
You're viewing a preview
Unlock full access by subscribing today!

3
IT/IS SECURITY MANAGEMENT
presented uncertainties in the product and the process parameters, the effect on the capability and
performance could use in manufacturing the related products. This are evaluated and the related
risks for the basic parameters are to be decreased or mitigated completely by the framework.
In this report the ISO/IEC 27001 is chosen for controlling the selection addressing the
multiple risks. It has been the internationally identified excellent framework that could help
Caduceus to protect and manage the data resources such that stay secure and safe (Safa, Von and
Furnell 2016). This has been helping to continually review and the refine the method done by
this, not for the present and also for the future. In this way the ISO/IEC 27001 could protect the
business of Caduceus along with their reputation and adding value. As documented, the
framework was created with the intention to deliver the model to establish, implement, operate,
monitor, review, maintain and develop the IS\IT management system (Safa et al. 2015). It has
been using the risk-based top down approach. I have been technologically neutral in nature. The
specification has been defining the following planning process.
Defining the security policy.
Defining the scope of ISMS.
Conducting the risk assessment.
Managing of the identified risks.
Selecting the control objectives and controls for implementation.
Preparing the statement of applicability (Ogutcu, Testik and Chouseinoglou
2016).
IT/IS SECURITY MANAGEMENT
presented uncertainties in the product and the process parameters, the effect on the capability and
performance could use in manufacturing the related products. This are evaluated and the related
risks for the basic parameters are to be decreased or mitigated completely by the framework.
In this report the ISO/IEC 27001 is chosen for controlling the selection addressing the
multiple risks. It has been the internationally identified excellent framework that could help
Caduceus to protect and manage the data resources such that stay secure and safe (Safa, Von and
Furnell 2016). This has been helping to continually review and the refine the method done by
this, not for the present and also for the future. In this way the ISO/IEC 27001 could protect the
business of Caduceus along with their reputation and adding value. As documented, the
framework was created with the intention to deliver the model to establish, implement, operate,
monitor, review, maintain and develop the IS\IT management system (Safa et al. 2015). It has
been using the risk-based top down approach. I have been technologically neutral in nature. The
specification has been defining the following planning process.
Defining the security policy.
Defining the scope of ISMS.
Conducting the risk assessment.
Managing of the identified risks.
Selecting the control objectives and controls for implementation.
Preparing the statement of applicability (Ogutcu, Testik and Chouseinoglou
2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT/IS SECURITY MANAGEMENT
The above specification has been including the details to documentation, management,
roles, continual improvement and internal audits, preventive and corrective actions. The standard
has needed the cooperation. This has been among every sections of Caduceus.
The standard has not been mandating the particular controls on information security.
However it has been providing the controlling of checklists considered in the codes of practice of
ISO/IEC 27002:2005. The later one has been describing the comprehensive set of the controls of
information security aims. This has been setting the generally accepted of the good practice of
the security controls.
The ISMS has been the system of documents, processes, technology and individuals that
has been helping to monitor, manage, improve and audit of the information security of Caduceus.
It has been helping to control the security practices at a place cost-effectively and consistently
(Cheng et al. 2013).
The ISO 27001-compliant ISMS have been depending on the risk assessments regularly
(Carter and Zheng 2015). Thus it has been helpful to recognize and the control the security
threats as the risk appetite and the tolerance of Caduceus.
IT/IS SECURITY MANAGEMENT
The above specification has been including the details to documentation, management,
roles, continual improvement and internal audits, preventive and corrective actions. The standard
has needed the cooperation. This has been among every sections of Caduceus.
The standard has not been mandating the particular controls on information security.
However it has been providing the controlling of checklists considered in the codes of practice of
ISO/IEC 27002:2005. The later one has been describing the comprehensive set of the controls of
information security aims. This has been setting the generally accepted of the good practice of
the security controls.
The ISMS has been the system of documents, processes, technology and individuals that
has been helping to monitor, manage, improve and audit of the information security of Caduceus.
It has been helping to control the security practices at a place cost-effectively and consistently
(Cheng et al. 2013).
The ISO 27001-compliant ISMS have been depending on the risk assessments regularly
(Carter and Zheng 2015). Thus it has been helpful to recognize and the control the security
threats as the risk appetite and the tolerance of Caduceus.
5
IT/IS SECURITY MANAGEMENT
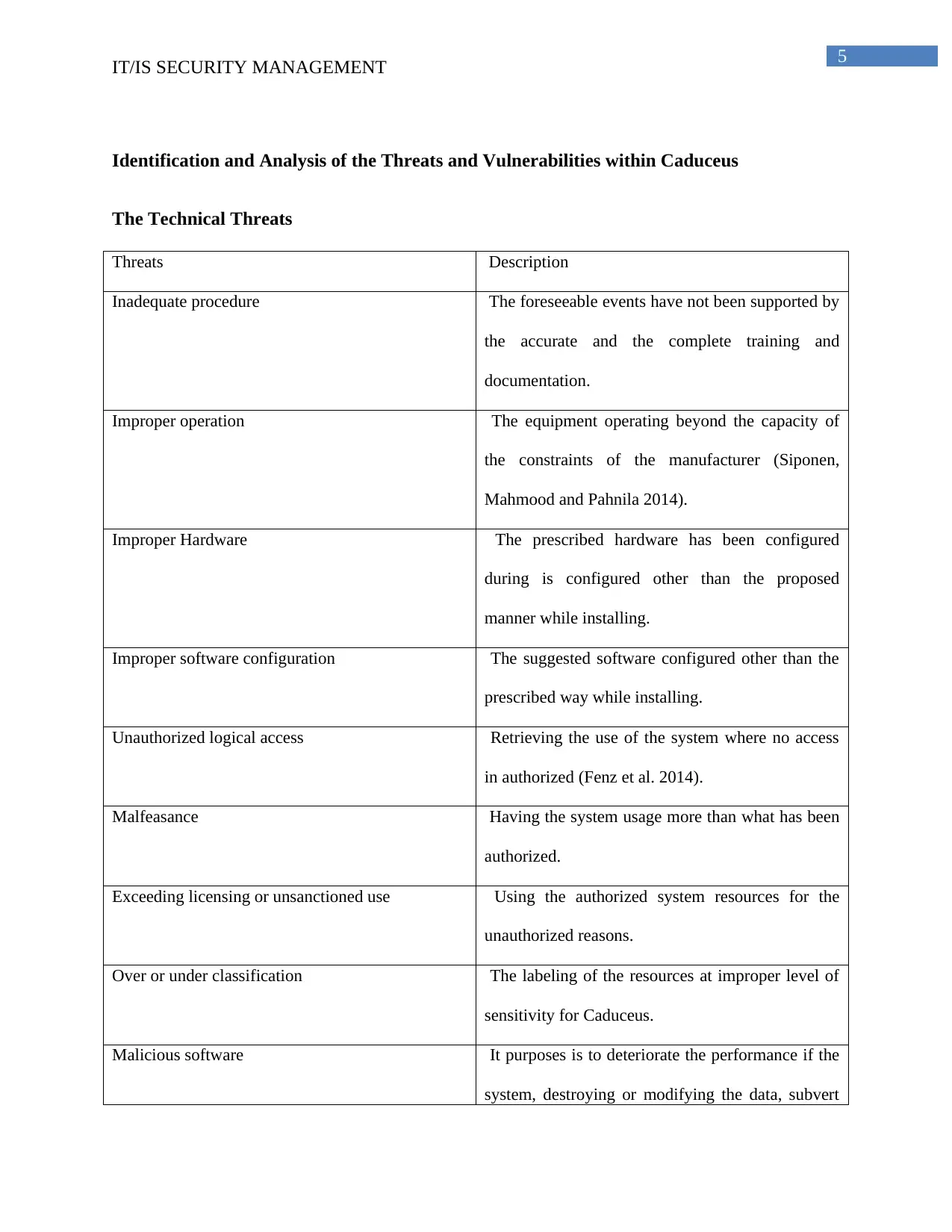
Identification and Analysis of the Threats and Vulnerabilities within Caduceus
The Technical Threats
Threats Description
Inadequate procedure The foreseeable events have not been supported by
the accurate and the complete training and
documentation.
Improper operation The equipment operating beyond the capacity of
the constraints of the manufacturer (Siponen,
Mahmood and Pahnila 2014).
Improper Hardware The prescribed hardware has been configured
during is configured other than the proposed
manner while installing.
Improper software configuration The suggested software configured other than the
prescribed way while installing.
Unauthorized logical access Retrieving the use of the system where no access
in authorized (Fenz et al. 2014).
Malfeasance Having the system usage more than what has been
authorized.
Exceeding licensing or unsanctioned use Using the authorized system resources for the
unauthorized reasons.
Over or under classification The labeling of the resources at improper level of
sensitivity for Caduceus.
Malicious software It purposes is to deteriorate the performance if the
system, destroying or modifying the data, subvert
IT/IS SECURITY MANAGEMENT
Identification and Analysis of the Threats and Vulnerabilities within Caduceus
The Technical Threats
Threats Description
Inadequate procedure The foreseeable events have not been supported by
the accurate and the complete training and
documentation.
Improper operation The equipment operating beyond the capacity of
the constraints of the manufacturer (Siponen,
Mahmood and Pahnila 2014).
Improper Hardware The prescribed hardware has been configured
during is configured other than the proposed
manner while installing.
Improper software configuration The suggested software configured other than the
prescribed way while installing.
Unauthorized logical access Retrieving the use of the system where no access
in authorized (Fenz et al. 2014).
Malfeasance Having the system usage more than what has been
authorized.
Exceeding licensing or unsanctioned use Using the authorized system resources for the
unauthorized reasons.
Over or under classification The labeling of the resources at improper level of
sensitivity for Caduceus.
Malicious software It purposes is to deteriorate the performance if the
system, destroying or modifying the data, subvert
You're viewing a preview
Unlock full access by subscribing today!
6
IT/IS SECURITY MANAGEMENT
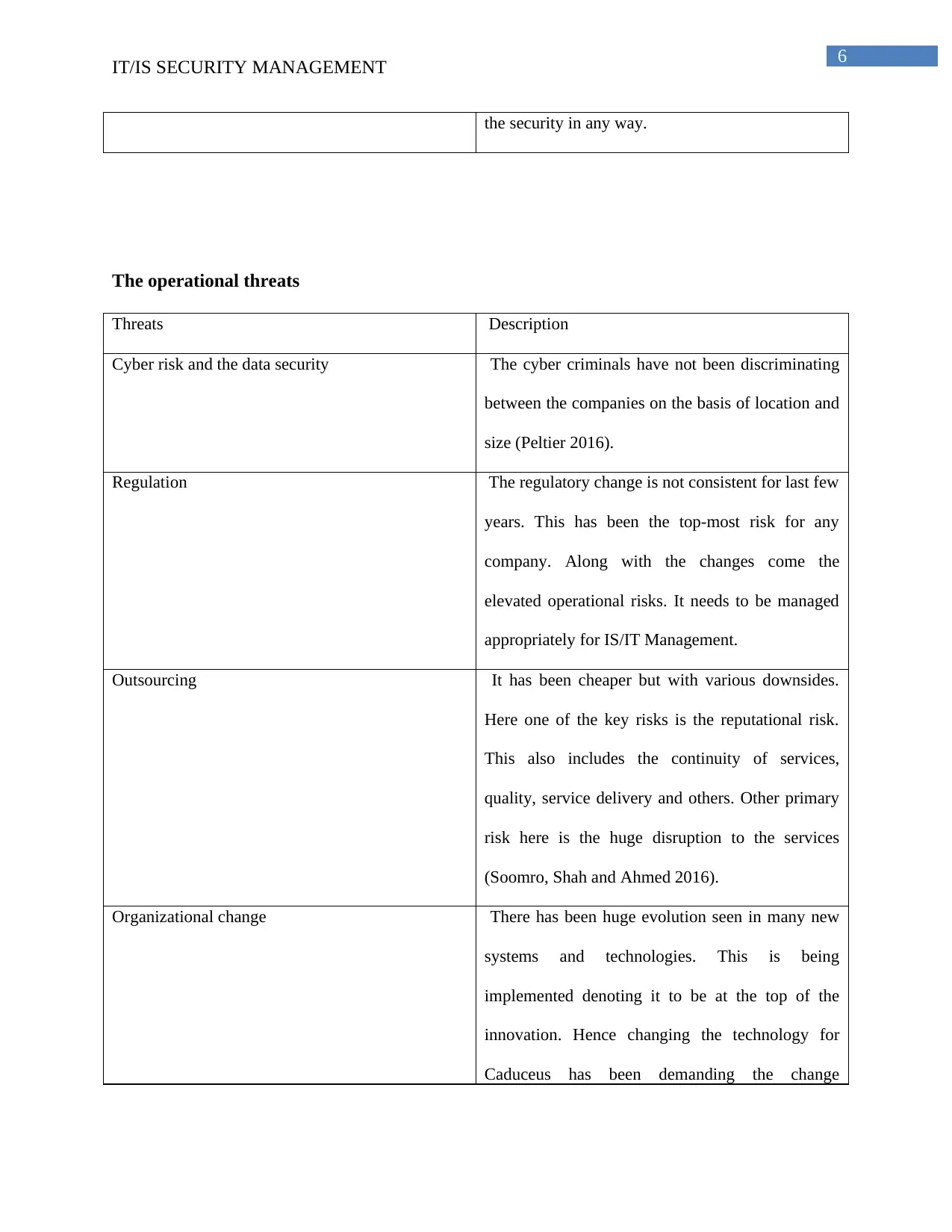
the security in any way.
The operational threats
Threats Description
Cyber risk and the data security The cyber criminals have not been discriminating
between the companies on the basis of location and
size (Peltier 2016).
Regulation The regulatory change is not consistent for last few
years. This has been the top-most risk for any
company. Along with the changes come the
elevated operational risks. It needs to be managed
appropriately for IS/IT Management.
Outsourcing It has been cheaper but with various downsides.
Here one of the key risks is the reputational risk.
This also includes the continuity of services,
quality, service delivery and others. Other primary
risk here is the huge disruption to the services
(Soomro, Shah and Ahmed 2016).
Organizational change There has been huge evolution seen in many new
systems and technologies. This is being
implemented denoting it to be at the top of the
innovation. Hence changing the technology for
Caduceus has been demanding the change
IT/IS SECURITY MANAGEMENT
the security in any way.
The operational threats
Threats Description
Cyber risk and the data security The cyber criminals have not been discriminating
between the companies on the basis of location and
size (Peltier 2016).
Regulation The regulatory change is not consistent for last few
years. This has been the top-most risk for any
company. Along with the changes come the
elevated operational risks. It needs to be managed
appropriately for IS/IT Management.
Outsourcing It has been cheaper but with various downsides.
Here one of the key risks is the reputational risk.
This also includes the continuity of services,
quality, service delivery and others. Other primary
risk here is the huge disruption to the services
(Soomro, Shah and Ahmed 2016).
Organizational change There has been huge evolution seen in many new
systems and technologies. This is being
implemented denoting it to be at the top of the
innovation. Hence changing the technology for
Caduceus has been demanding the change
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IT/IS SECURITY MANAGEMENT
management and the redesigning controls and
processes in the other spaces. It has been the central
of the operational risks, the systems and processes,
staying at the top of the changes in that area.
Managerial risks
The managerial risks have been another critical aspect of the strategic management at
Caduceus. For improving the competitive performance and advantage the managers require to
take the risks. However it has been in the uncertain environment. The formal economic
assumptions of risks have been suggesting that it has been the excepted values regarding the two
strategies. They have been similar but however one has been more uncertain in nature. The
managers need to choose the strategy more definite results for the IS/IT Risk Management
Project (Whitman and Mattord 2013). On the basis of those assumptions the agency theory has
been assuming that the top managers must be monitored or compensated for achieving the better
outcomes for Caduceus.
Impact Analysis
Data Collection and Analysis
There is the necessity of well-chosen and well implementation of chosen data for any
type of evaluation. Impact evaluation is an approach that should go beyond assessing the size of
the effects that means average impact in manner to identify for whom and in what manner the
policy and the program has been successful (Oliveira, Thomas and Esadanal 2014). Main
objectives regarding the impact analysis can be stated as the collection of the data and methods
IT/IS SECURITY MANAGEMENT
management and the redesigning controls and
processes in the other spaces. It has been the central
of the operational risks, the systems and processes,
staying at the top of the changes in that area.
Managerial risks
The managerial risks have been another critical aspect of the strategic management at
Caduceus. For improving the competitive performance and advantage the managers require to
take the risks. However it has been in the uncertain environment. The formal economic
assumptions of risks have been suggesting that it has been the excepted values regarding the two
strategies. They have been similar but however one has been more uncertain in nature. The
managers need to choose the strategy more definite results for the IS/IT Risk Management
Project (Whitman and Mattord 2013). On the basis of those assumptions the agency theory has
been assuming that the top managers must be monitored or compensated for achieving the better
outcomes for Caduceus.
Impact Analysis
Data Collection and Analysis
There is the necessity of well-chosen and well implementation of chosen data for any
type of evaluation. Impact evaluation is an approach that should go beyond assessing the size of
the effects that means average impact in manner to identify for whom and in what manner the
policy and the program has been successful (Oliveira, Thomas and Esadanal 2014). Main
objectives regarding the impact analysis can be stated as the collection of the data and methods

8
IT/IS SECURITY MANAGEMENT
for the analysis should be chosen specifically in manner to match the specific evaluations with
respond to the KEQs (Key Evaluation Questions) and the available resources. Other objective
can be stated as there should be use of proper existing data and the gaps that have been created
should be filled with new data (Van 2016). The collection and analysis of data should be chosen
in a manner that both will be complement of strengths and weaknesses of each other in the IS/IT
Risk Management.
Planning Data Collection and Analysis
There are various phases in this approach that includes the following:
The start should be made with the whole planning for the evaluation that includes this
consists of various questions that have been stated in the table 1. A well-developed ‘theory of
change’ can be described as the essential tool in the process of impact analysis for Caduceus that
can be helpful in describing the policy or program understandings (webb et al. 2014). This will
depict a casual model that can be helpful in linking the activities and inputs with the desired
outcomes, outputs, and impacts.
Maximum usage of existing data can be stated as the next approach for the data collection
planning considering the data that has been already existing. Considering the term indicators, the
aim of the evaluation should be on drawing different types of indicators such as outputs, inputs,
impacts, outcomes in manner to reflect the key result in the programs of ‘theory of change’.
Identifying and addressing important data gaps, which focuses on reviewing the
information those are available in manner to consider whether the qualitative or quantitative
analysis is capable of answering the key questions that has been stated in the table (Durn 2015).
IT/IS SECURITY MANAGEMENT
for the analysis should be chosen specifically in manner to match the specific evaluations with
respond to the KEQs (Key Evaluation Questions) and the available resources. Other objective
can be stated as there should be use of proper existing data and the gaps that have been created
should be filled with new data (Van 2016). The collection and analysis of data should be chosen
in a manner that both will be complement of strengths and weaknesses of each other in the IS/IT
Risk Management.
Planning Data Collection and Analysis
There are various phases in this approach that includes the following:
The start should be made with the whole planning for the evaluation that includes this
consists of various questions that have been stated in the table 1. A well-developed ‘theory of
change’ can be described as the essential tool in the process of impact analysis for Caduceus that
can be helpful in describing the policy or program understandings (webb et al. 2014). This will
depict a casual model that can be helpful in linking the activities and inputs with the desired
outcomes, outputs, and impacts.
Maximum usage of existing data can be stated as the next approach for the data collection
planning considering the data that has been already existing. Considering the term indicators, the
aim of the evaluation should be on drawing different types of indicators such as outputs, inputs,
impacts, outcomes in manner to reflect the key result in the programs of ‘theory of change’.
Identifying and addressing important data gaps, which focuses on reviewing the
information those are available in manner to consider whether the qualitative or quantitative
analysis is capable of answering the key questions that has been stated in the table (Durn 2015).
You're viewing a preview
Unlock full access by subscribing today!
9
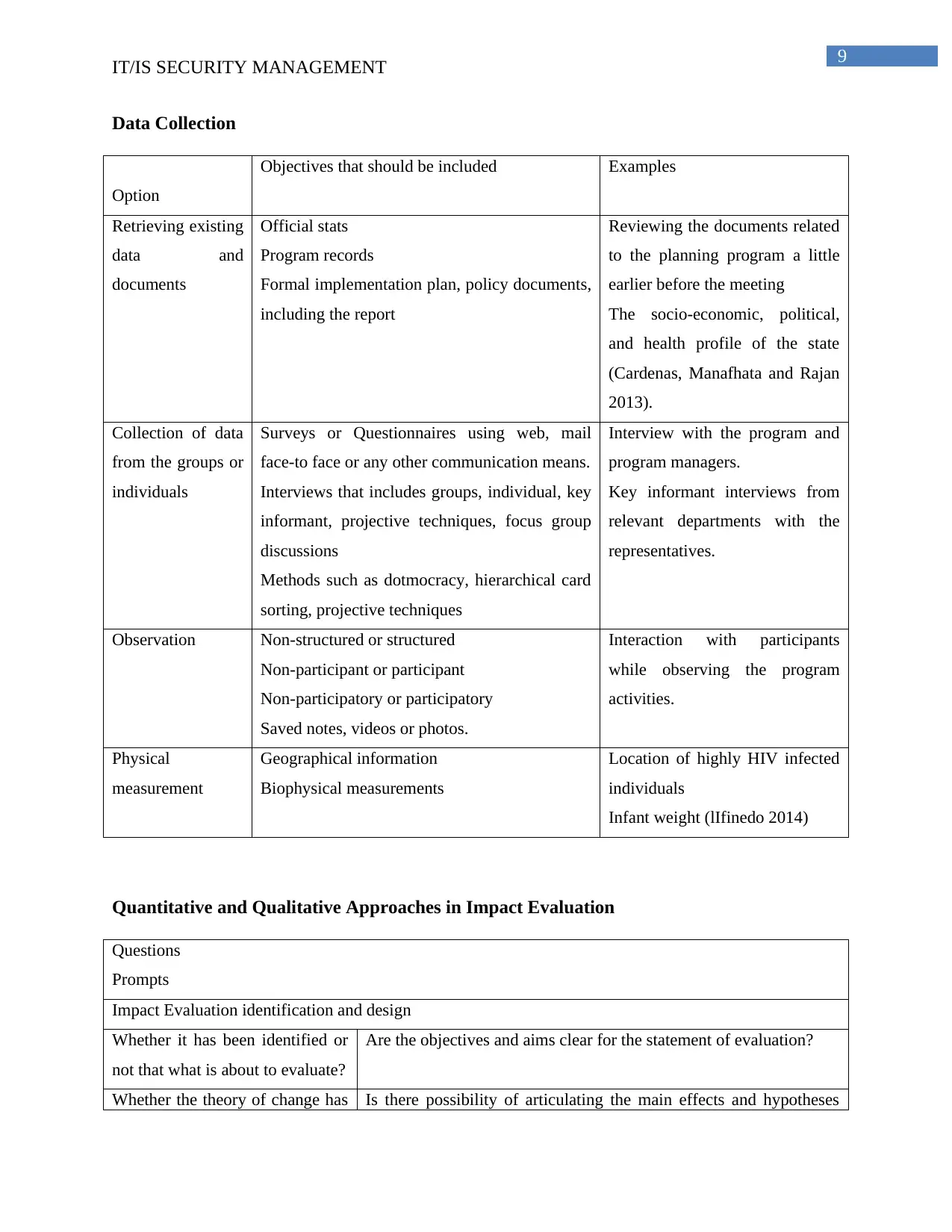
IT/IS SECURITY MANAGEMENT
Data Collection
Option
Objectives that should be included Examples
Retrieving existing
data and
documents
Official stats
Program records
Formal implementation plan, policy documents,
including the report
Reviewing the documents related
to the planning program a little
earlier before the meeting
The socio-economic, political,
and health profile of the state
(Cardenas, Manafhata and Rajan
2013).
Collection of data
from the groups or
individuals
Surveys or Questionnaires using web, mail
face-to face or any other communication means.
Interviews that includes groups, individual, key
informant, projective techniques, focus group
discussions
Methods such as dotmocracy, hierarchical card
sorting, projective techniques
Interview with the program and
program managers.
Key informant interviews from
relevant departments with the
representatives.
Observation Non-structured or structured
Non-participant or participant
Non-participatory or participatory
Saved notes, videos or photos.
Interaction with participants
while observing the program
activities.
Physical
measurement
Geographical information
Biophysical measurements
Location of highly HIV infected
individuals
Infant weight (lIfinedo 2014)
Quantitative and Qualitative Approaches in Impact Evaluation
Questions
Prompts
Impact Evaluation identification and design
Whether it has been identified or
not that what is about to evaluate?
Are the objectives and aims clear for the statement of evaluation?
Whether the theory of change has Is there possibility of articulating the main effects and hypotheses
IT/IS SECURITY MANAGEMENT
Data Collection
Option
Objectives that should be included Examples
Retrieving existing
data and
documents
Official stats
Program records
Formal implementation plan, policy documents,
including the report
Reviewing the documents related
to the planning program a little
earlier before the meeting
The socio-economic, political,
and health profile of the state
(Cardenas, Manafhata and Rajan
2013).
Collection of data
from the groups or
individuals
Surveys or Questionnaires using web, mail
face-to face or any other communication means.
Interviews that includes groups, individual, key
informant, projective techniques, focus group
discussions
Methods such as dotmocracy, hierarchical card
sorting, projective techniques
Interview with the program and
program managers.
Key informant interviews from
relevant departments with the
representatives.
Observation Non-structured or structured
Non-participant or participant
Non-participatory or participatory
Saved notes, videos or photos.
Interaction with participants
while observing the program
activities.
Physical
measurement
Geographical information
Biophysical measurements
Location of highly HIV infected
individuals
Infant weight (lIfinedo 2014)
Quantitative and Qualitative Approaches in Impact Evaluation
Questions
Prompts
Impact Evaluation identification and design
Whether it has been identified or
not that what is about to evaluate?
Are the objectives and aims clear for the statement of evaluation?
Whether the theory of change has Is there possibility of articulating the main effects and hypotheses
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
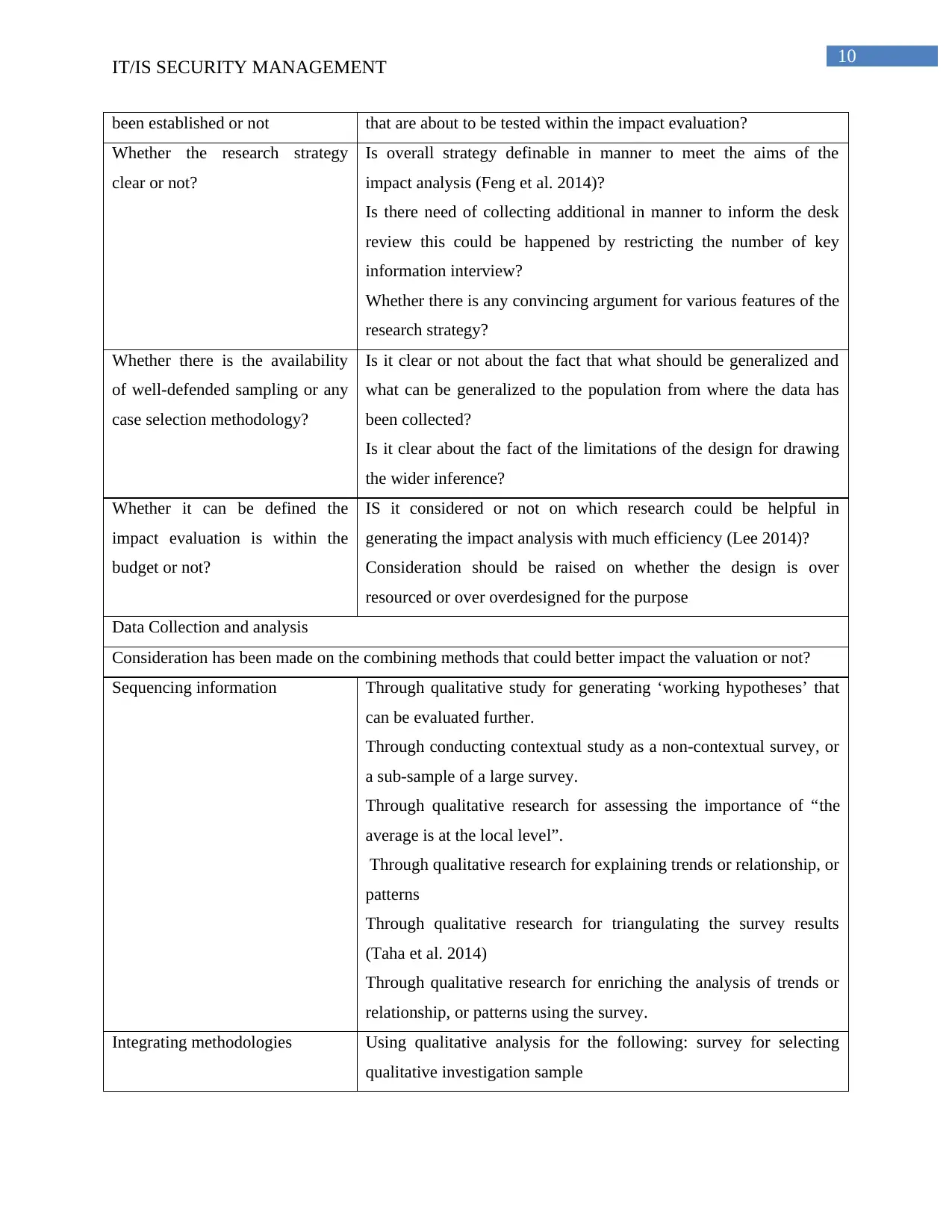
IT/IS SECURITY MANAGEMENT
been established or not that are about to be tested within the impact evaluation?
Whether the research strategy
clear or not?
Is overall strategy definable in manner to meet the aims of the
impact analysis (Feng et al. 2014)?
Is there need of collecting additional in manner to inform the desk
review this could be happened by restricting the number of key
information interview?
Whether there is any convincing argument for various features of the
research strategy?
Whether there is the availability
of well-defended sampling or any
case selection methodology?
Is it clear or not about the fact that what should be generalized and
what can be generalized to the population from where the data has
been collected?
Is it clear about the fact of the limitations of the design for drawing
the wider inference?
Whether it can be defined the
impact evaluation is within the
budget or not?
IS it considered or not on which research could be helpful in
generating the impact analysis with much efficiency (Lee 2014)?
Consideration should be raised on whether the design is over
resourced or over overdesigned for the purpose
Data Collection and analysis
Consideration has been made on the combining methods that could better impact the valuation or not?
Sequencing information Through qualitative study for generating ‘working hypotheses’ that
can be evaluated further.
Through conducting contextual study as a non-contextual survey, or
a sub-sample of a large survey.
Through qualitative research for assessing the importance of “the
average is at the local level”.
Through qualitative research for explaining trends or relationship, or
patterns
Through qualitative research for triangulating the survey results
(Taha et al. 2014)
Through qualitative research for enriching the analysis of trends or
relationship, or patterns using the survey.
Integrating methodologies Using qualitative analysis for the following: survey for selecting
qualitative investigation sample
IT/IS SECURITY MANAGEMENT
been established or not that are about to be tested within the impact evaluation?
Whether the research strategy
clear or not?
Is overall strategy definable in manner to meet the aims of the
impact analysis (Feng et al. 2014)?
Is there need of collecting additional in manner to inform the desk
review this could be happened by restricting the number of key
information interview?
Whether there is any convincing argument for various features of the
research strategy?
Whether there is the availability
of well-defended sampling or any
case selection methodology?
Is it clear or not about the fact that what should be generalized and
what can be generalized to the population from where the data has
been collected?
Is it clear about the fact of the limitations of the design for drawing
the wider inference?
Whether it can be defined the
impact evaluation is within the
budget or not?
IS it considered or not on which research could be helpful in
generating the impact analysis with much efficiency (Lee 2014)?
Consideration should be raised on whether the design is over
resourced or over overdesigned for the purpose
Data Collection and analysis
Consideration has been made on the combining methods that could better impact the valuation or not?
Sequencing information Through qualitative study for generating ‘working hypotheses’ that
can be evaluated further.
Through conducting contextual study as a non-contextual survey, or
a sub-sample of a large survey.
Through qualitative research for assessing the importance of “the
average is at the local level”.
Through qualitative research for explaining trends or relationship, or
patterns
Through qualitative research for triangulating the survey results
(Taha et al. 2014)
Through qualitative research for enriching the analysis of trends or
relationship, or patterns using the survey.
Integrating methodologies Using qualitative analysis for the following: survey for selecting
qualitative investigation sample
11
IT/IS SECURITY MANAGEMENT
Highlighting the priority issues
Identifying knowledge gaps
Identifying categories for the responses from survey
For constructing indicators of non-material impacts.
“Using insights from qualitative and quantitative studies help to
define population sub-group sampling frames” (Kriaa et al. 2015)
Merging findings Through analytical framework that can be helpful in interpreting
quantitative and qualitative data
Whether the identification of qualitative methods have been done or not?
Change observation Through the scoring module of survey for the qualitative perception
Measuring the observable change in behavior
Community score card
Change analysis Through contextual methods that includes ethnography, participatory
research methods, interviews, theatre,focus group discussions,
video analysis, andobservationand documentary.
Contextual research has been
considered or not
The primarily extractive and transformative has been considered or
not?
Whether the approach of
quantifying and measuring non-
material (qualitative) impacts
have been considered or not?
Perception scoring, observable change and a mix of perception
scoring and observable have been considered or not (Silva et al
2014)?
Threats, risk and vulnerabilities assessment
Sl.No Vulnerabilities
in IS security
management
Likelihood
Impact
Priority
Description Preventive measures
R. 1 Dust/ Airborne
particles
M H M Dust and airborne particles
travelling in the environment
could alter the function of IT
technologies and could result
in inaccurate results or failure
of information security
management
Physical security of the
IT infrastructure should
be given very high
priority in manner to
protect the infrastructure
and related devices.
IT/IS SECURITY MANAGEMENT
Highlighting the priority issues
Identifying knowledge gaps
Identifying categories for the responses from survey
For constructing indicators of non-material impacts.
“Using insights from qualitative and quantitative studies help to
define population sub-group sampling frames” (Kriaa et al. 2015)
Merging findings Through analytical framework that can be helpful in interpreting
quantitative and qualitative data
Whether the identification of qualitative methods have been done or not?
Change observation Through the scoring module of survey for the qualitative perception
Measuring the observable change in behavior
Community score card
Change analysis Through contextual methods that includes ethnography, participatory
research methods, interviews, theatre,focus group discussions,
video analysis, andobservationand documentary.
Contextual research has been
considered or not
The primarily extractive and transformative has been considered or
not?
Whether the approach of
quantifying and measuring non-
material (qualitative) impacts
have been considered or not?
Perception scoring, observable change and a mix of perception
scoring and observable have been considered or not (Silva et al
2014)?
Threats, risk and vulnerabilities assessment
Sl.No Vulnerabilities
in IS security
management
Likelihood
Impact
Priority
Description Preventive measures
R. 1 Dust/ Airborne
particles
M H M Dust and airborne particles
travelling in the environment
could alter the function of IT
technologies and could result
in inaccurate results or failure
of information security
management
Physical security of the
IT infrastructure should
be given very high
priority in manner to
protect the infrastructure
and related devices.
You're viewing a preview
Unlock full access by subscribing today!
12
IT/IS SECURITY MANAGEMENT
R. 2 Earthquake VL VH H This are very less likely
events however, might affect
very seriously to the
information security system
of the organization (Malhotra
2015).
The IT infrastructure
should be established
regarding the facts related
to such natural
calamities.
R. 3 Failure of
network
components
M H M Network components might
cause failure or disruption due
to many factors such as
technical fault, bad weather
and many others that might
affect the exchange of
information between two
devices connected to the same
network.
Mainly, internet is the
network that has been
adopting by various
industries and Caduceus
should also implement
high bandwidth internet
connection.
R. 4 Natural disasters L VH M Natural calamities are not
most likely to happen but it
also includes terrorist attack
and many others that are
capable of completely
destroying the IT/IS
management system of any
organization (Feng, Wang and
Li 2014).
Caduceus should always
be prepared for such
unwanted situation and
should establish the
infrastructure regarding
these issues, threats and
vulnerabilities.
R .5 Maintenance
error
H H M Not regularly maintain the IT
components that are
contributing in managing the
information related to the
operation activities of the
organization could raise
various issues related to the
information security
management
There should be proper
and regular audit for the
errors that might affect
the system and should
maintain the update for
the hardware and
software of Caduceus.
R. 6 Malicious H VH H This is mainly done The operating system
IT/IS SECURITY MANAGEMENT
R. 2 Earthquake VL VH H This are very less likely
events however, might affect
very seriously to the
information security system
of the organization (Malhotra
2015).
The IT infrastructure
should be established
regarding the facts related
to such natural
calamities.
R. 3 Failure of
network
components
M H M Network components might
cause failure or disruption due
to many factors such as
technical fault, bad weather
and many others that might
affect the exchange of
information between two
devices connected to the same
network.
Mainly, internet is the
network that has been
adopting by various
industries and Caduceus
should also implement
high bandwidth internet
connection.
R. 4 Natural disasters L VH M Natural calamities are not
most likely to happen but it
also includes terrorist attack
and many others that are
capable of completely
destroying the IT/IS
management system of any
organization (Feng, Wang and
Li 2014).
Caduceus should always
be prepared for such
unwanted situation and
should establish the
infrastructure regarding
these issues, threats and
vulnerabilities.
R .5 Maintenance
error
H H M Not regularly maintain the IT
components that are
contributing in managing the
information related to the
operation activities of the
organization could raise
various issues related to the
information security
management
There should be proper
and regular audit for the
errors that might affect
the system and should
maintain the update for
the hardware and
software of Caduceus.
R. 6 Malicious H VH H This is mainly done The operating system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
13
IT/IS SECURITY MANAGEMENT
Coding intentionally for revenge
purpose or for money. This is
one the major issues in the
field of IT and getting
multiplied by every minute
this lead to the privacy and
security of the individuals
related to the organization.
should be original and
updated with the newest
version; proper anti-virus
should be used in all the
systems including
updated firewalls and
anti-malwares.
R. 7 Identity theft M M M This is not just the digital
identity however it also
includes the credentials that
could be stolen by an
unauthorized user that could
give him or her access to the
whole data that has been
saved into the system (Latif et
al 2014).
There should be different
level security for the
staffs based on their
position.
R. 8 Misuse of
Resources
M VH H Resources might be used by
the employees in different
manner such activities that
might affect the policies of
the organization or many
other legal aspects related to
the crime for IS/IT Risk
Management .
There should be a large
compensation for the
employees violating the
laws and regulations that
has been established by
the organization.
R. 9 Malicious
Insider
VL H H This is a type of threat to the
information that generally
arises due to some formal
employees those have the
credentials that could give
them access to the
organizational network and
could alter the data and
information that had been
After the retirement,
resignation or distinction
of any employee the
passwords and other
related information
should be changed and
agreement should also be
made before employing
them about not disclosing
IT/IS SECURITY MANAGEMENT
Coding intentionally for revenge
purpose or for money. This is
one the major issues in the
field of IT and getting
multiplied by every minute
this lead to the privacy and
security of the individuals
related to the organization.
should be original and
updated with the newest
version; proper anti-virus
should be used in all the
systems including
updated firewalls and
anti-malwares.
R. 7 Identity theft M M M This is not just the digital
identity however it also
includes the credentials that
could be stolen by an
unauthorized user that could
give him or her access to the
whole data that has been
saved into the system (Latif et
al 2014).
There should be different
level security for the
staffs based on their
position.
R. 8 Misuse of
Resources
M VH H Resources might be used by
the employees in different
manner such activities that
might affect the policies of
the organization or many
other legal aspects related to
the crime for IS/IT Risk
Management .
There should be a large
compensation for the
employees violating the
laws and regulations that
has been established by
the organization.
R. 9 Malicious
Insider
VL H H This is a type of threat to the
information that generally
arises due to some formal
employees those have the
credentials that could give
them access to the
organizational network and
could alter the data and
information that had been
After the retirement,
resignation or distinction
of any employee the
passwords and other
related information
should be changed and
agreement should also be
made before employing
them about not disclosing
14
IT/IS SECURITY MANAGEMENT
saved into the database. the data of the
organization.
R. 10 Unauthorized
access
M VH H There are various actions that
could be put into the category
of unauthorized access such
as data breaches, identity
theft, malicious virus attack
and many more that
technically states the access
of the data by an individual
who is not authorized to
access the data that has been
saved in that network
(Baskerville, Spagnoletti and
Kim 2014).
Proper care should be
given for the IS/IT Risk
Management while
sharing the credentials
and rest precautions
should be taken in
increasing the
information security for
the data and encryption
or tokenization can also
be a better option for
such cases.
R. 11 Repudiation VH H M It focuses on the digital
signature which is attached to
the electronic message when
an user sends it and is not a
full-proof system
The system should be
non-repudiation.
R. 12 Software failure H VH H There are chances of failures
of software such as crashing,
glitches and bugs that could
result alter outputs (Lee 2014)
There should be proper
update available for the
software.
R. 13 Device lost or
theft
M VH H This could lead to the heavy
lost for the organizations that
allows employees to bring
their own device for the
official purpose and the data
and information could be
exposed to an unauthorized
user (Silva et al. 2014)
Physical security should
be given priority in
manner to leave behind
such issues. A training
program could be helpful
R. 15 Social
engineering
M M H This can be described as a
trick to hamper the data that
IT/IS SECURITY MANAGEMENT
saved into the database. the data of the
organization.
R. 10 Unauthorized
access
M VH H There are various actions that
could be put into the category
of unauthorized access such
as data breaches, identity
theft, malicious virus attack
and many more that
technically states the access
of the data by an individual
who is not authorized to
access the data that has been
saved in that network
(Baskerville, Spagnoletti and
Kim 2014).
Proper care should be
given for the IS/IT Risk
Management while
sharing the credentials
and rest precautions
should be taken in
increasing the
information security for
the data and encryption
or tokenization can also
be a better option for
such cases.
R. 11 Repudiation VH H M It focuses on the digital
signature which is attached to
the electronic message when
an user sends it and is not a
full-proof system
The system should be
non-repudiation.
R. 12 Software failure H VH H There are chances of failures
of software such as crashing,
glitches and bugs that could
result alter outputs (Lee 2014)
There should be proper
update available for the
software.
R. 13 Device lost or
theft
M VH H This could lead to the heavy
lost for the organizations that
allows employees to bring
their own device for the
official purpose and the data
and information could be
exposed to an unauthorized
user (Silva et al. 2014)
Physical security should
be given priority in
manner to leave behind
such issues. A training
program could be helpful
R. 15 Social
engineering
M M H This can be described as a
trick to hamper the data that
You're viewing a preview
Unlock full access by subscribing today!
15
IT/IS SECURITY MANAGEMENT
attack has been saved into the
system
R. 16 No backup or
loss of backup
L H VH Caduceus is already aware
with the importance of
backup but loss of backup
could affect the proper
functioning of the business
and could even cause privacy
and security issues if placed
in the wrong hands (Band et
al. 2015).
There should be more
than one backup.
Appointing third party for
the management of data
can also be helpful for the
IS/IT Risk Management.
R. 17 Legal Risks H M VH The policy of the organization
should be incompatible with
the policies of government
The manager should
properly go through the
policies and laws as
stated in the above report
before modifying the IT
infrastructure
R. 18 Physical security H H M Physical security should
always be the priority while
implementing IT
infrastructure into the existing
system of the organization as
these could lead to the
information security issues
(Albakri et al. 2014).
Proper fencing and using
biometric for the location
where database and
servers are located.
R. 19 Fluctuation
power supply
L H H These could also lead to
various issues including the
crashing of whole systems
Power supply should be
maintained all the time
Risk severity matrix
Probability
IT/IS SECURITY MANAGEMENT
attack has been saved into the
system
R. 16 No backup or
loss of backup
L H VH Caduceus is already aware
with the importance of
backup but loss of backup
could affect the proper
functioning of the business
and could even cause privacy
and security issues if placed
in the wrong hands (Band et
al. 2015).
There should be more
than one backup.
Appointing third party for
the management of data
can also be helpful for the
IS/IT Risk Management.
R. 17 Legal Risks H M VH The policy of the organization
should be incompatible with
the policies of government
The manager should
properly go through the
policies and laws as
stated in the above report
before modifying the IT
infrastructure
R. 18 Physical security H H M Physical security should
always be the priority while
implementing IT
infrastructure into the existing
system of the organization as
these could lead to the
information security issues
(Albakri et al. 2014).
Proper fencing and using
biometric for the location
where database and
servers are located.
R. 19 Fluctuation
power supply
L H H These could also lead to
various issues including the
crashing of whole systems
Power supply should be
maintained all the time
Risk severity matrix
Probability
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
16
IT/IS SECURITY MANAGEMENT
Very High R. 11
High R. 17
R. 5
R. 18
R. 6
R. 12
Medium
R. 7
R. 15
R. 1
R. 3
R. 8
R. 10
R. 13
Low
R. 16
R. 19 R. 4
Very Low R. 9 R. 2
Severity Very Low Low Medium High Very High
Legal and Regulatory Requirements
There are various steps in accomplishing proper regulation within the system of the
Caduceus that can be listed as follows:
Regulatory institution: This is the very first step in implementing the regulation within
the existing system of Caduceus IS/IT Risk Management Project, which states that the regulatory
actions and decisions emanate from the governmental entity that might be the parliamentary
body, ministry body or any other government representative (Coffee, Sale and Henderson 2015).
The institution will exist within the larger environment of the society including the social,
political, and economic constraints and pressures and will have its own unique organizational
characteristics.
Regulatory policy: The second step, which states that the environmental and
organizational characteristics of Caduceus that are contributing to the regulatory institution will
IT/IS SECURITY MANAGEMENT
Very High R. 11
High R. 17
R. 5
R. 18
R. 6
R. 12
Medium
R. 7
R. 15
R. 1
R. 3
R. 8
R. 10
R. 13
Low
R. 16
R. 19 R. 4
Very Low R. 9 R. 2
Severity Very Low Low Medium High Very High
Legal and Regulatory Requirements
There are various steps in accomplishing proper regulation within the system of the
Caduceus that can be listed as follows:
Regulatory institution: This is the very first step in implementing the regulation within
the existing system of Caduceus IS/IT Risk Management Project, which states that the regulatory
actions and decisions emanate from the governmental entity that might be the parliamentary
body, ministry body or any other government representative (Coffee, Sale and Henderson 2015).
The institution will exist within the larger environment of the society including the social,
political, and economic constraints and pressures and will have its own unique organizational
characteristics.
Regulatory policy: The second step, which states that the environmental and
organizational characteristics of Caduceus that are contributing to the regulatory institution will

17
IT/IS SECURITY MANAGEMENT
be the general ones, irrespective of the procedures, practices, or rules those have been specially
directed at thee regulatory behavior and decision making for the IS/IT Risk Management. It
includes the consultation and transparency rules for example: “regulatory impact analysis, cost-
benefit analysis, impacts on small businesses or local governments, or paperwork burden
analysis”. The regulatory policy is also capable of including various other rules that could
contribute in the structure regulatory decision making for Caduceus. For example, “regulatory
budgets, pay-as-you-go or one-in-one-out mandates, or requirements for legislative authorisation
of certain regulations initiated at a ministry oragency level” could be considered here for
Caduceus.
Regulation: Regarding the regulation under evaluation the ROI (regulation of interest),
there will different regulations the might affect and exist the behaviour of the organization and
the individuals connected with the organization (Laudon and laudon 2016).
Implementation: The regulations conceivably have the capability to quickly affect the
adoption within the organization. If the regulations have been planner in targeting the law; they
could be implemented and enforced into the law before the government takes any steps towards
this approach of IS/IT Risk Management.
Behavioural change: This will be the first consideration about how the individuals related
to the organization are being affected due to the implementation of these regulations. In general
behavioural change might occur as intend for example there are the chances that the speed limits
or breakers might cause the driver to drive slowly. There are the possibilities of various types of
influences on the behaviour that might lie beyond the regulations and their implementations at
Caduceus.
IT/IS SECURITY MANAGEMENT
be the general ones, irrespective of the procedures, practices, or rules those have been specially
directed at thee regulatory behavior and decision making for the IS/IT Risk Management. It
includes the consultation and transparency rules for example: “regulatory impact analysis, cost-
benefit analysis, impacts on small businesses or local governments, or paperwork burden
analysis”. The regulatory policy is also capable of including various other rules that could
contribute in the structure regulatory decision making for Caduceus. For example, “regulatory
budgets, pay-as-you-go or one-in-one-out mandates, or requirements for legislative authorisation
of certain regulations initiated at a ministry oragency level” could be considered here for
Caduceus.
Regulation: Regarding the regulation under evaluation the ROI (regulation of interest),
there will different regulations the might affect and exist the behaviour of the organization and
the individuals connected with the organization (Laudon and laudon 2016).
Implementation: The regulations conceivably have the capability to quickly affect the
adoption within the organization. If the regulations have been planner in targeting the law; they
could be implemented and enforced into the law before the government takes any steps towards
this approach of IS/IT Risk Management.
Behavioural change: This will be the first consideration about how the individuals related
to the organization are being affected due to the implementation of these regulations. In general
behavioural change might occur as intend for example there are the chances that the speed limits
or breakers might cause the driver to drive slowly. There are the possibilities of various types of
influences on the behaviour that might lie beyond the regulations and their implementations at
Caduceus.
You're viewing a preview
Unlock full access by subscribing today!

18
IT/IS SECURITY MANAGEMENT
Intermediate outcomes: Outcomes in this case can be represented as the effects of
regulations in the real world. These are the outcomes that casual relation to the ultimate
outcomes. This also explains about typical intermediate outcomes that could raise concerns about
other outcomes that include costs and various other side effects in IS/IT Risk Management.
Ultimate outcomes: UOC (Ultimate outcomes of concern) refers to the reduction or
solution of the primary problems those had been animated the regulation. It might reflect to the
“public health, safety,environmental quality, domestic security, or economic competition, to pick
several commonexamples of problems that justify government regulation”. For few cases this
could cover more than one outcome of concern that could justify the regulations. Although the
outcomes may be of ultimate concern, this does not mean that they are of absolute concern. As
already noted,few if any regulatory problems call for solutions to be made at any cost. Thus, in
addition to a regulation’s impact on its ultimate outcome of concern, it could ultimately lead to
other outcomes as well for Caduceus
Conclusion
Based on the above report it can be concluded that Caduceus could use this risk
management report for enhancing the performance of both of its sections and manage the
information security for the data and information that are being saved into the system. Risk
mitigation framework has been proposed in this report that could be helpful in assessing the risks
related to the IT or IS within the organizational existing system. Thereafter, emphasis has been
given on the impact analysis that could be the best approach for paving the path of a strong
secured IT structure within the organization in manner to manage the information and
operational activities related to the Caduceus. After that a risk assessment has been provided
IT/IS SECURITY MANAGEMENT
Intermediate outcomes: Outcomes in this case can be represented as the effects of
regulations in the real world. These are the outcomes that casual relation to the ultimate
outcomes. This also explains about typical intermediate outcomes that could raise concerns about
other outcomes that include costs and various other side effects in IS/IT Risk Management.
Ultimate outcomes: UOC (Ultimate outcomes of concern) refers to the reduction or
solution of the primary problems those had been animated the regulation. It might reflect to the
“public health, safety,environmental quality, domestic security, or economic competition, to pick
several commonexamples of problems that justify government regulation”. For few cases this
could cover more than one outcome of concern that could justify the regulations. Although the
outcomes may be of ultimate concern, this does not mean that they are of absolute concern. As
already noted,few if any regulatory problems call for solutions to be made at any cost. Thus, in
addition to a regulation’s impact on its ultimate outcome of concern, it could ultimately lead to
other outcomes as well for Caduceus
Conclusion
Based on the above report it can be concluded that Caduceus could use this risk
management report for enhancing the performance of both of its sections and manage the
information security for the data and information that are being saved into the system. Risk
mitigation framework has been proposed in this report that could be helpful in assessing the risks
related to the IT or IS within the organizational existing system. Thereafter, emphasis has been
given on the impact analysis that could be the best approach for paving the path of a strong
secured IT structure within the organization in manner to manage the information and
operational activities related to the Caduceus. After that a risk assessment has been provided
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

19
IT/IS SECURITY MANAGEMENT
related to the threats, vulnerabilities and other issues that might affect the information security
issues within the organization. In this assessment the vulnerabilities have been provided with
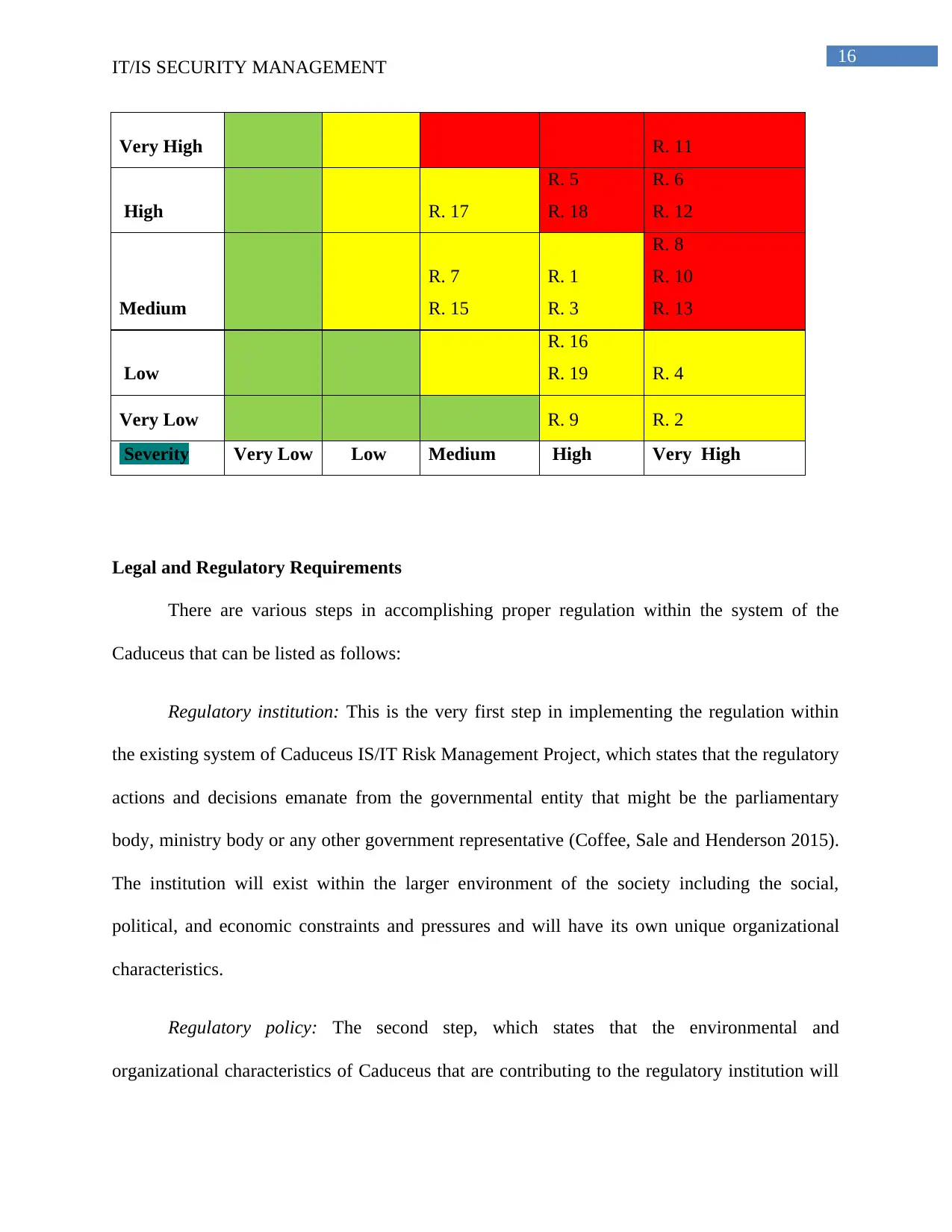
their impact and probability of happening and based on that a risk severity matrix has also been
proposed in this report. This matrix could be helpful in prioritizing the risks and based on that the
precautions could be taken or a manager could decide which risk should be mitigated at the very
first for the IS/IT Risk Management Project. This report presents a concise thorough research on
the IT/IS risk management in manner to enhance the security within the organizational
information covering many aspects related to the regulation and policies that might affect the
implementation of IT infrastructure within the Caduceus.
IT/IS SECURITY MANAGEMENT
related to the threats, vulnerabilities and other issues that might affect the information security
issues within the organization. In this assessment the vulnerabilities have been provided with
their impact and probability of happening and based on that a risk severity matrix has also been
proposed in this report. This matrix could be helpful in prioritizing the risks and based on that the
precautions could be taken or a manager could decide which risk should be mitigated at the very
first for the IS/IT Risk Management Project. This report presents a concise thorough research on
the IT/IS risk management in manner to enhance the security within the organizational
information covering many aspects related to the regulation and policies that might affect the
implementation of IT infrastructure within the Caduceus.

20
IT/IS SECURITY MANAGEMENT
References:
Albakri, S.H., Shanmugam, B., Samy, G.N., Idris, N.B. and Ahmed, A., 2014. Security risk
assessment framework for cloud computing environments.Security and Communication
Networks, 7(11), pp.2114-2124
Band, I., Engelsman, W., Feltus, B.C., Paredes, S.G. and Diligens, D., 2015.Modeling Enterprise
Risk Management and Security with the ArchiMate®.
Baskerville, R., Spagnoletti, P. and Kim, J., 2014. Incident-centered information security:
Managing a strategic balance between prevention and response. Information & Management,
51(1), pp.138-151.
Cardenas, A.A., Manadhata, P.K. and Rajan, S.P., 2013. Big data analytics for security.IEEE
Security & Privacy, 11(6), pp.74-76.
Carter, W.A. and Zheng, D.E., 2015. The Evolution of Cybersecurity Requirements for the US
Financial Industry.Center for Strategic and International Studies.
Cheng, L., Li, Y., Li, W., Holm, E. and Zhai, Q., 2013. Understanding the violation of IS
security policy in organizations: An integrated model based on social control and deterrence
theory. Computers & Security, 39, pp.447-459.
Coffee Jr, J.C., Sale, H. and Henderson, M.T., 2015. Securities regulation: Cases and materials.
Dunn, W.N., 2015. Public policy analysis.Routledge.
IT/IS SECURITY MANAGEMENT
References:
Albakri, S.H., Shanmugam, B., Samy, G.N., Idris, N.B. and Ahmed, A., 2014. Security risk
assessment framework for cloud computing environments.Security and Communication
Networks, 7(11), pp.2114-2124
Band, I., Engelsman, W., Feltus, B.C., Paredes, S.G. and Diligens, D., 2015.Modeling Enterprise
Risk Management and Security with the ArchiMate®.
Baskerville, R., Spagnoletti, P. and Kim, J., 2014. Incident-centered information security:
Managing a strategic balance between prevention and response. Information & Management,
51(1), pp.138-151.
Cardenas, A.A., Manadhata, P.K. and Rajan, S.P., 2013. Big data analytics for security.IEEE
Security & Privacy, 11(6), pp.74-76.
Carter, W.A. and Zheng, D.E., 2015. The Evolution of Cybersecurity Requirements for the US
Financial Industry.Center for Strategic and International Studies.
Cheng, L., Li, Y., Li, W., Holm, E. and Zhai, Q., 2013. Understanding the violation of IS
security policy in organizations: An integrated model based on social control and deterrence
theory. Computers & Security, 39, pp.447-459.
Coffee Jr, J.C., Sale, H. and Henderson, M.T., 2015. Securities regulation: Cases and materials.
Dunn, W.N., 2015. Public policy analysis.Routledge.
You're viewing a preview
Unlock full access by subscribing today!

21
IT/IS SECURITY MANAGEMENT
Feng, N., Wang, H.J. and Li, M., 2014. A security risk analysis model for information systems:
Causal relationships of risk factors and vulnerability propagation analysis. Information sciences,
256, pp.57-73.
Feng, N., Wang, H.J. and Li, M., 2014. A security risk analysis model for information systems:
Causal relationships of risk factors and vulnerability propagation analysis. Information sciences,
256, pp.57-73.
Fenz, S., Heurix, J., Neubauer, T. and Pechstein, F., 2014.Current challenges in information
security risk management.Information Management & Computer Security, 22(5), pp.410-430.
Ifinedo, P., 2014. Information systems security policy compliance: An empirical study of the
effects of socialisation, influence, and cognition. Information & Management, 51(1), pp.69-79.
Kriaa, S., Pietre-Cambacedes, L., Bouissou, M. and Halgand, Y., 2015.A survey of approaches
combining safety and security for industrial control systems.Reliability Engineering & System
Safety, 139, pp.156-178.
Latif, R., Abbas, H., Assar, S. and Ali, Q., 2014. Cloud computing risk assessment: a systematic
literature review. In Future Information Technology (pp. 285-295). Springer, Berlin, Heidelberg.
Laudon, K.C. and Laudon, J.P., 2016. Management information system.Pearson Education India.
Lee, M.C., 2014. Information security risk analysis methods and research trends: AHP and fuzzy
comprehensive method. International Journal of Computer Science & Information Technology,
6(1), p.29.
IT/IS SECURITY MANAGEMENT
Feng, N., Wang, H.J. and Li, M., 2014. A security risk analysis model for information systems:
Causal relationships of risk factors and vulnerability propagation analysis. Information sciences,
256, pp.57-73.
Feng, N., Wang, H.J. and Li, M., 2014. A security risk analysis model for information systems:
Causal relationships of risk factors and vulnerability propagation analysis. Information sciences,
256, pp.57-73.
Fenz, S., Heurix, J., Neubauer, T. and Pechstein, F., 2014.Current challenges in information
security risk management.Information Management & Computer Security, 22(5), pp.410-430.
Ifinedo, P., 2014. Information systems security policy compliance: An empirical study of the
effects of socialisation, influence, and cognition. Information & Management, 51(1), pp.69-79.
Kriaa, S., Pietre-Cambacedes, L., Bouissou, M. and Halgand, Y., 2015.A survey of approaches
combining safety and security for industrial control systems.Reliability Engineering & System
Safety, 139, pp.156-178.
Latif, R., Abbas, H., Assar, S. and Ali, Q., 2014. Cloud computing risk assessment: a systematic
literature review. In Future Information Technology (pp. 285-295). Springer, Berlin, Heidelberg.
Laudon, K.C. and Laudon, J.P., 2016. Management information system.Pearson Education India.
Lee, M.C., 2014. Information security risk analysis methods and research trends: AHP and fuzzy
comprehensive method. International Journal of Computer Science & Information Technology,
6(1), p.29.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

22
IT/IS SECURITY MANAGEMENT
Lee, M.C., 2014. Information security risk analysis methods and research trends: AHP and fuzzy
comprehensive method. International Journal of Computer Science & Information Technology,
6(1), p.29.
Malhotra, Y., 2015. Cybersecurity& Cyber-Finance Risk Management: Strategies, Tactics,
Operations, &, Intelligence: Enterprise Risk Management to Model Risk Management:
Understanding Vulnerabilities, Threats, & Risk Mitigation (Presentation Slides).
Öğütçü, G., Testik, Ö.M. and Chouseinoglou, O., 2016. Analysis of personal information
security behavior and awareness.Computers & Security, 56, pp.83-93.
Oliveira, T., Thomas, M. and Espadanal, M., 2014.Assessing the determinants of cloud
computing adoption: An analysis of the manufacturing and services sectors.Information &
Management, 51(5), pp.497-510.
Peltier, T.R., 2016.Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Safa, N.S., Sookhak, M., Von Solms, R., Furnell, S., Ghani, N.A. and Herawan, T.,
2015.Information security conscious care behaviour formation in organizations.Computers &
Security, 53, pp.65-78.
Safa, N.S., Von Solms, R. and Furnell, S., 2016.Information security policy compliance model in
organizations.computers& security, 56, pp.70-82.
Shamala, P., Ahmad, R. and Yusoff, M., 2013.A conceptual framework of info structure for
information security risk assessment (ISRA).Journal of Information Security and Applications,
18(1), pp.45-52.
IT/IS SECURITY MANAGEMENT
Lee, M.C., 2014. Information security risk analysis methods and research trends: AHP and fuzzy
comprehensive method. International Journal of Computer Science & Information Technology,
6(1), p.29.
Malhotra, Y., 2015. Cybersecurity& Cyber-Finance Risk Management: Strategies, Tactics,
Operations, &, Intelligence: Enterprise Risk Management to Model Risk Management:
Understanding Vulnerabilities, Threats, & Risk Mitigation (Presentation Slides).
Öğütçü, G., Testik, Ö.M. and Chouseinoglou, O., 2016. Analysis of personal information
security behavior and awareness.Computers & Security, 56, pp.83-93.
Oliveira, T., Thomas, M. and Espadanal, M., 2014.Assessing the determinants of cloud
computing adoption: An analysis of the manufacturing and services sectors.Information &
Management, 51(5), pp.497-510.
Peltier, T.R., 2016.Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Safa, N.S., Sookhak, M., Von Solms, R., Furnell, S., Ghani, N.A. and Herawan, T.,
2015.Information security conscious care behaviour formation in organizations.Computers &
Security, 53, pp.65-78.
Safa, N.S., Von Solms, R. and Furnell, S., 2016.Information security policy compliance model in
organizations.computers& security, 56, pp.70-82.
Shamala, P., Ahmad, R. and Yusoff, M., 2013.A conceptual framework of info structure for
information security risk assessment (ISRA).Journal of Information Security and Applications,
18(1), pp.45-52.

23
IT/IS SECURITY MANAGEMENT
Silva, M.M., de Gusmão, A.P.H., Poleto, T., e Silva, L.C. and Costa, A.P.C.S., 2014.A
multidimensional approach to information security risk management using FMEA and fuzzy
theory.International Journal of Information Management, 34(6), pp.733-740.
Silva, M.M., de Gusmão, A.P.H., Poleto, T., e Silva, L.C. and Costa, A.P.C.S., 2014.A
multidimensional approach to information security risk management using FMEA and fuzzy
theory.International Journal of Information Management, 34(6), pp.733-740.
Siponen, M., Mahmood, M.A. and Pahnila, S., 2014. Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), pp.217-224.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more
holistic approach: A literature review. International Journal of Information Management, 36(2),
pp.215-225.
Taha, A., Trapero, R., Luna, J. and Suri, N., 2014, September.Ahp-based quantitative approach
for assessing and comparing cloud security. In Trust, Security and Privacy in Computing and
Communications (TrustCom), 2014 IEEE 13th International Conference on (pp. 284-291). IEEE.
VAN HEMELRIJCK, A.D.I.N.D.A., 2016. GOVERNANCE IN MYANMAR.Evaluation.
Webb, J., Ahmad, A., Maynard, S.B. and Shanks, G., 2014. A situation awareness model for
information security risk management.Computers & security, 44, pp.1-15.
Whitman, M. and Mattord, H., 2013.Management of information security.Nelson Education.
IT/IS SECURITY MANAGEMENT
Silva, M.M., de Gusmão, A.P.H., Poleto, T., e Silva, L.C. and Costa, A.P.C.S., 2014.A
multidimensional approach to information security risk management using FMEA and fuzzy
theory.International Journal of Information Management, 34(6), pp.733-740.
Silva, M.M., de Gusmão, A.P.H., Poleto, T., e Silva, L.C. and Costa, A.P.C.S., 2014.A
multidimensional approach to information security risk management using FMEA and fuzzy
theory.International Journal of Information Management, 34(6), pp.733-740.
Siponen, M., Mahmood, M.A. and Pahnila, S., 2014. Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), pp.217-224.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more
holistic approach: A literature review. International Journal of Information Management, 36(2),
pp.215-225.
Taha, A., Trapero, R., Luna, J. and Suri, N., 2014, September.Ahp-based quantitative approach
for assessing and comparing cloud security. In Trust, Security and Privacy in Computing and
Communications (TrustCom), 2014 IEEE 13th International Conference on (pp. 284-291). IEEE.
VAN HEMELRIJCK, A.D.I.N.D.A., 2016. GOVERNANCE IN MYANMAR.Evaluation.
Webb, J., Ahmad, A., Maynard, S.B. and Shanks, G., 2014. A situation awareness model for
information security risk management.Computers & security, 44, pp.1-15.
Whitman, M. and Mattord, H., 2013.Management of information security.Nelson Education.
You're viewing a preview
Unlock full access by subscribing today!

24
IT/IS SECURITY MANAGEMENT
IT/IS SECURITY MANAGEMENT
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




