Network Security Implementation Report - Network Perimeter Design
VerifiedAdded on 2022/10/09
|20
|3861
|478
Report
AI Summary
This report details the implementation of a network security perimeter, addressing key aspects like network infrastructure, security needs, and potential threats. It outlines the hardware components, including routers and firewalls, and describes the security topology design, incorporating elements like DMZ, VLANs, and NAT. The report further elaborates on the configuration of firewalls and routers, followed by a discussion of testing methodologies and tools employed to assess the network's security posture. It covers penetration testing techniques, log analysis, and the identification of vulnerabilities. Finally, the report concludes with an evaluation of the implemented perimeter's strengths and weaknesses, providing a comprehensive overview of the entire network security implementation process. The report includes network diagrams, configuration details, and test results to support the analysis.

Running head: NETWORK SECURITY IMPLEMENTATION
Network Security Implementation
Name of the Student
Name of the University
Author Note
Network Security Implementation
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK SECURITY IMPLEMENTATION
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................2
Network Infrastructure:..........................................................................................................2
Network Security Needs:.......................................................................................................4
Network Security Threats:.....................................................................................................5
Hardware Implementation:.........................................................................................................6
Security Topology Design:....................................................................................................7
Configuration of firewall and Router.........................................................................................8
Test Conducted and Outcomes.................................................................................................10
Testing Tools............................................................................................................................11
Software to analyze logs..........................................................................................................14
Weakness of installed perimeter design...................................................................................14
Conclusion................................................................................................................................15
Bibliography:............................................................................................................................17
NETWORK SECURITY IMPLEMENTATION
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................2
Network Infrastructure:..........................................................................................................2
Network Security Needs:.......................................................................................................4
Network Security Threats:.....................................................................................................5
Hardware Implementation:.........................................................................................................6
Security Topology Design:....................................................................................................7
Configuration of firewall and Router.........................................................................................8
Test Conducted and Outcomes.................................................................................................10
Testing Tools............................................................................................................................11
Software to analyze logs..........................................................................................................14
Weakness of installed perimeter design...................................................................................14
Conclusion................................................................................................................................15
Bibliography:............................................................................................................................17

2
NETWORK SECURITY IMPLEMENTATION
Introduction
Network security is a vast topic that comprises of technologies, processes and devices.
It consists of policies and practices that are used to protect the privacy, resources and
network-accessible resources. Network Infrastructure comprises of foundational hardware
used for networking, software resources, services and facilities. Networking software consists
of software abstractions and enables network administrators to manage dynamic networks
more easily. Network Service is an application at the network layer and above for data
storage, communication, manipulation used by implementing client server (Hyde et al. 2014).
Remote Network Access allows individual servers to connect to a private/enterprise network
from a remote location connected to the internet. The network security perimeter consists of
an enterprise and is interconnected. This infrastructure is used for internal/external
communications.
NETWORK SECURITY IMPLEMENTATION
Introduction
Network security is a vast topic that comprises of technologies, processes and devices.
It consists of policies and practices that are used to protect the privacy, resources and
network-accessible resources. Network Infrastructure comprises of foundational hardware
used for networking, software resources, services and facilities. Networking software consists
of software abstractions and enables network administrators to manage dynamic networks
more easily. Network Service is an application at the network layer and above for data
storage, communication, manipulation used by implementing client server (Hyde et al. 2014).
Remote Network Access allows individual servers to connect to a private/enterprise network
from a remote location connected to the internet. The network security perimeter consists of
an enterprise and is interconnected. This infrastructure is used for internal/external
communications.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
NETWORK SECURITY IMPLEMENTATION
Discussion
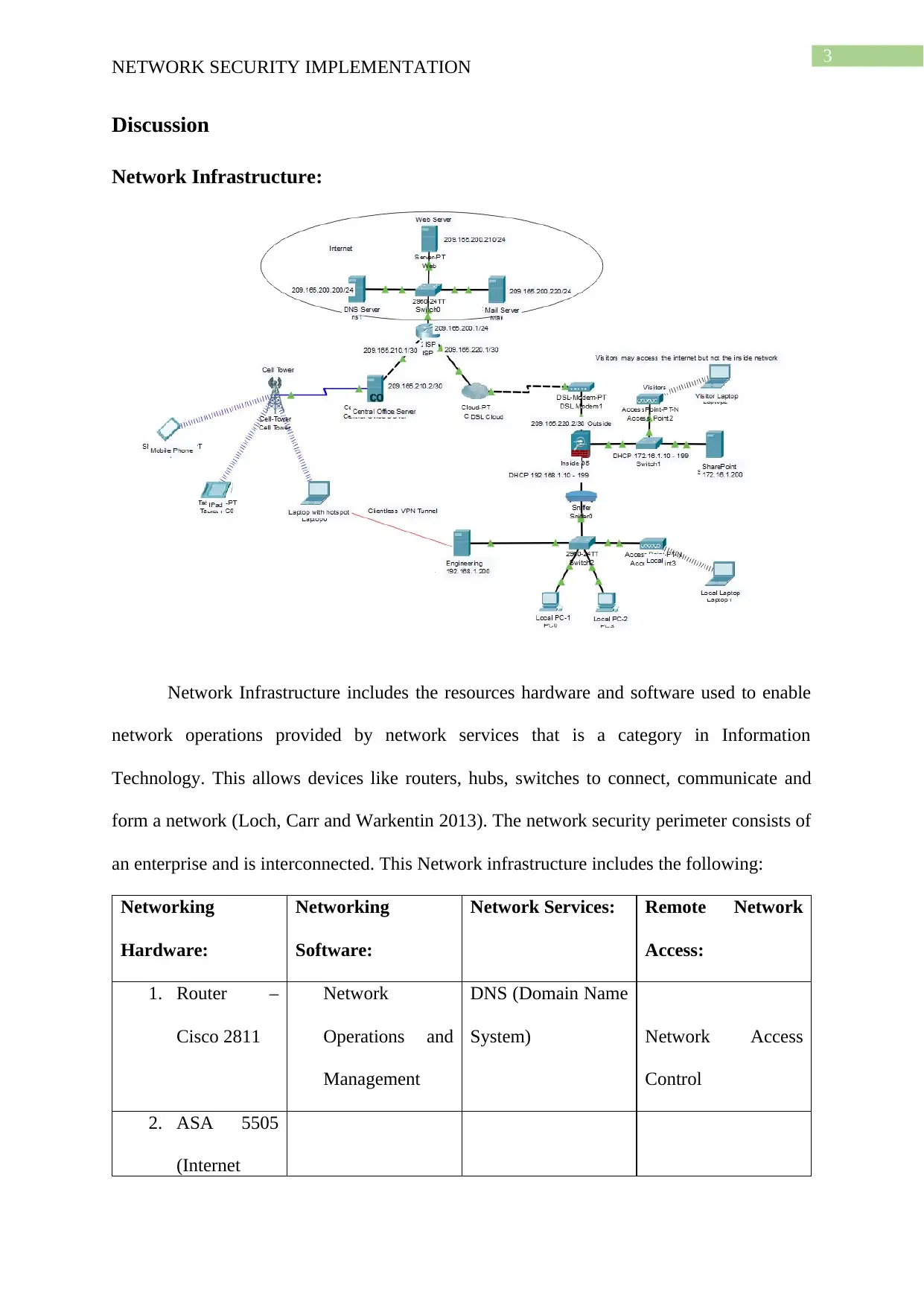
Network Infrastructure:
Network Infrastructure includes the resources hardware and software used to enable
network operations provided by network services that is a category in Information
Technology. This allows devices like routers, hubs, switches to connect, communicate and
form a network (Loch, Carr and Warkentin 2013). The network security perimeter consists of
an enterprise and is interconnected. This Network infrastructure includes the following:
Networking
Hardware:
Networking
Software:
Network Services: Remote Network
Access:
1. Router –
Cisco 2811
Network
Operations and
Management
DNS (Domain Name
System) Network Access
Control
2. ASA 5505
(Internet
NETWORK SECURITY IMPLEMENTATION
Discussion
Network Infrastructure:
Network Infrastructure includes the resources hardware and software used to enable
network operations provided by network services that is a category in Information
Technology. This allows devices like routers, hubs, switches to connect, communicate and
form a network (Loch, Carr and Warkentin 2013). The network security perimeter consists of
an enterprise and is interconnected. This Network infrastructure includes the following:
Networking
Hardware:
Networking
Software:
Network Services: Remote Network
Access:
1. Router –
Cisco 2811
Network
Operations and
Management
DNS (Domain Name
System) Network Access
Control
2. ASA 5505
(Internet
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
NETWORK SECURITY IMPLEMENTATION
Security and
Acceleration)
Operating Systems VPN (Virtual
Private Network)
Network Intrusion
Detection (IDS)
3. SMB (Server
Message
block)
Internal Firewall and
Stateful application
firewall.
DMZ
(Demilitarized
zone )
Web Proxy
(Wireless protocols)
4. Wireless
router-
Network Security
Applications
DSL (Digital
Subscriber Line)
Guest Servers/DSL
This network infrastructure involves communication and connection that are vital for
a sound success of any enterprise based Network Security. Full visibility of a Network
Infrastructure is a key factor for performance monitoring and threat detection. The Cisco
2811 router will connect devices and networks together by channeling traffic forward. The
ASA 5505 provides new firewall features; policy based administration, VPN integration,
smart caching and scalability and enhanced reporting. SMB allows systems connected to the
same network and domains to share files and folders. Wireless routers functions as a router
but also includes functions of a wireless access points.
Network Security Needs:
Network security is required to prevent downtime, compliance of government
regulation, for intrusion detection, reduced liability and protection of reputation.
Authentication techniques like one-factor (usernames and passwords), two-factor (security
token, OTP), three-factor authentication (biometrics) are used to protect the security of a
network. Some other factors for what network security is required are:
Control and access of servers,
NETWORK SECURITY IMPLEMENTATION
Security and
Acceleration)
Operating Systems VPN (Virtual
Private Network)
Network Intrusion
Detection (IDS)
3. SMB (Server
Message
block)
Internal Firewall and
Stateful application
firewall.
DMZ
(Demilitarized
zone )
Web Proxy
(Wireless protocols)
4. Wireless
router-
Network Security
Applications
DSL (Digital
Subscriber Line)
Guest Servers/DSL
This network infrastructure involves communication and connection that are vital for
a sound success of any enterprise based Network Security. Full visibility of a Network
Infrastructure is a key factor for performance monitoring and threat detection. The Cisco
2811 router will connect devices and networks together by channeling traffic forward. The
ASA 5505 provides new firewall features; policy based administration, VPN integration,
smart caching and scalability and enhanced reporting. SMB allows systems connected to the
same network and domains to share files and folders. Wireless routers functions as a router
but also includes functions of a wireless access points.
Network Security Needs:
Network security is required to prevent downtime, compliance of government
regulation, for intrusion detection, reduced liability and protection of reputation.
Authentication techniques like one-factor (usernames and passwords), two-factor (security
token, OTP), three-factor authentication (biometrics) are used to protect the security of a
network. Some other factors for what network security is required are:
Control and access of servers,

5
NETWORK SECURITY IMPLEMENTATION
Application security, software’s like antivirus- for secure coding, designing and
securing Operating systems,
Intrusion detection systems, Network firewalls and encryption techniques.
The main aim of a Network Security implementation is to protect the Information
Technology infrastructure and keep assets safe (Maiwald, 2013). It generally comprises of
practices and policies that are used to monitor a lot of things such as unauthorized access,
misuse of information, modification of existing data and denial of computer resources and
processes. Network security used are NAC (Network Access Control), Application Securing,
Antivirus and anti-malware software’s and E-mail securing and Wireless security. Network
Security needs are met by enabling firewall on routers, disabling remote router
administration, by updating router firmware, by securing the computer and by physically
securing the network components.
Network Security Threats:
Network Security threats refers to something that has a potential to harm the system
or sometimes even the whole network topology. The most common threats to a network
security are:
Viruses in servers: The most common threat to servers of an enterprise network
because it is connected to the web and is vulnerable to malwares (Ramjee et al. 2013).
These are spread using email attachments infesting as it explores the network or by
simply downloads from forged websites.
Rogue security software: A malicious software that misleads the user to think that a
virus as infested their system or that the security system is out of date. Then the
software asks the user to install a antivirus and actually provides a malware which
totally infects the system.
NETWORK SECURITY IMPLEMENTATION
Application security, software’s like antivirus- for secure coding, designing and
securing Operating systems,
Intrusion detection systems, Network firewalls and encryption techniques.
The main aim of a Network Security implementation is to protect the Information
Technology infrastructure and keep assets safe (Maiwald, 2013). It generally comprises of
practices and policies that are used to monitor a lot of things such as unauthorized access,
misuse of information, modification of existing data and denial of computer resources and
processes. Network security used are NAC (Network Access Control), Application Securing,
Antivirus and anti-malware software’s and E-mail securing and Wireless security. Network
Security needs are met by enabling firewall on routers, disabling remote router
administration, by updating router firmware, by securing the computer and by physically
securing the network components.
Network Security Threats:
Network Security threats refers to something that has a potential to harm the system
or sometimes even the whole network topology. The most common threats to a network
security are:
Viruses in servers: The most common threat to servers of an enterprise network
because it is connected to the web and is vulnerable to malwares (Ramjee et al. 2013).
These are spread using email attachments infesting as it explores the network or by
simply downloads from forged websites.
Rogue security software: A malicious software that misleads the user to think that a
virus as infested their system or that the security system is out of date. Then the
software asks the user to install a antivirus and actually provides a malware which
totally infects the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORK SECURITY IMPLEMENTATION
Phishing: A method of social engineering with the intention of stealing personal
credentials. This attack happens in the form of legitimate looking links, mails but is
actually malicious.
Rootkit: A collection of tools that gives remote location control on administration
level to a computer of a network. Rootkit installs itself and waits for the hacker to
activate it.
SQL Injection: Exploits security vulnerabilities and attacks data-driven files and
applications. Uses malicious code to extract personal data, then changes the integrity
of the data, and sometimes even deletes it.
Man-in-the-middle attacks: Gives access to an unauthorized person to listen to or have
access to a communication happening between two individuals over the network.
Types of man-in-the-middle attacks are, DNS spoofing, IP spoofing, ARP spoofing,
SSL hijacking, Wi-Fi hacking and
HTTPS spoofing.
Trojan horse: Inviting an attacker to a protected network zone unintentionally. Used
to steal sensitive data because it is an attacking code that tricks the user. It is
embedded in an actual program of a mail.
DOS and DDOS attacks: The denial of service focuses on over trafficking a network
that makes it almost impossible for legitimate users to get services they paid for.
Distributed denial of service DDOS functions similarly but is more forceful and
launches from multiple computers using multiple resources which makes it almost
impossible for the victim to locate it.
Hardware Implementation:
The hardware’s that are used in Network Security Infrastructure can be categorized
into: In Physical Layer, devices used are- Repeater, hub, and NIC (Network interface
NETWORK SECURITY IMPLEMENTATION
Phishing: A method of social engineering with the intention of stealing personal
credentials. This attack happens in the form of legitimate looking links, mails but is
actually malicious.
Rootkit: A collection of tools that gives remote location control on administration
level to a computer of a network. Rootkit installs itself and waits for the hacker to
activate it.
SQL Injection: Exploits security vulnerabilities and attacks data-driven files and
applications. Uses malicious code to extract personal data, then changes the integrity
of the data, and sometimes even deletes it.
Man-in-the-middle attacks: Gives access to an unauthorized person to listen to or have
access to a communication happening between two individuals over the network.
Types of man-in-the-middle attacks are, DNS spoofing, IP spoofing, ARP spoofing,
SSL hijacking, Wi-Fi hacking and
HTTPS spoofing.
Trojan horse: Inviting an attacker to a protected network zone unintentionally. Used
to steal sensitive data because it is an attacking code that tricks the user. It is
embedded in an actual program of a mail.
DOS and DDOS attacks: The denial of service focuses on over trafficking a network
that makes it almost impossible for legitimate users to get services they paid for.
Distributed denial of service DDOS functions similarly but is more forceful and
launches from multiple computers using multiple resources which makes it almost
impossible for the victim to locate it.
Hardware Implementation:
The hardware’s that are used in Network Security Infrastructure can be categorized
into: In Physical Layer, devices used are- Repeater, hub, and NIC (Network interface
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORK SECURITY IMPLEMENTATION
controller). In Data Link Layer, devices used are switches and bridges. In Network Layer
device used is router. Other hardware’s are cables and Wi-Fi-routers.
A repeater is used to extend transmissions of signals received by amplifying it so that the
signal is not lost.
A hub is a connection point of the devices present in a network and are used to connect
segments of LAN (Local Area Network).
The Network Interface card/controller is an Ethernet card and also a network adapter
which lets servers connect to a network.
A switch also known as a network switch is a networking device that perform tasks like
packet switching/ receiving, processing and forwarding data on a computer system.
A network bridge creates a single mass network from multiple communication segments
of a network.
Router forwards packets of data between computer networks, and on the internet routers
perform the job of traffic directing.
Security Topology Design:
A security topology design is defined as the arrangement of devices (hardware) to fulfill
needs of public access or security requirements measures on a network. Topologies are
created by dividing an existing network into zones of security (Zhang et al, 2015.). The
following are the basic components of a Security Topology design that is mandatory and
needs to be implemented:
DMZ (Demilitarized zone): Is a term used to describe the buffer in between an
internal network and an external network. DMZ is separated by an outer firewall on
the outer layer and an internal firewall on the internal side to prevent breaches.
NETWORK SECURITY IMPLEMENTATION
controller). In Data Link Layer, devices used are switches and bridges. In Network Layer
device used is router. Other hardware’s are cables and Wi-Fi-routers.
A repeater is used to extend transmissions of signals received by amplifying it so that the
signal is not lost.
A hub is a connection point of the devices present in a network and are used to connect
segments of LAN (Local Area Network).
The Network Interface card/controller is an Ethernet card and also a network adapter
which lets servers connect to a network.
A switch also known as a network switch is a networking device that perform tasks like
packet switching/ receiving, processing and forwarding data on a computer system.
A network bridge creates a single mass network from multiple communication segments
of a network.
Router forwards packets of data between computer networks, and on the internet routers
perform the job of traffic directing.
Security Topology Design:
A security topology design is defined as the arrangement of devices (hardware) to fulfill
needs of public access or security requirements measures on a network. Topologies are
created by dividing an existing network into zones of security (Zhang et al, 2015.). The
following are the basic components of a Security Topology design that is mandatory and
needs to be implemented:
DMZ (Demilitarized zone): Is a term used to describe the buffer in between an
internal network and an external network. DMZ is separated by an outer firewall on
the outer layer and an internal firewall on the internal side to prevent breaches.

8
NETWORK SECURITY IMPLEMENTATION
Internet: The public network that anyone wishes to access is known as the internet.
The internet is worldwide. The internet enables a network to access to remote located
servers with the help of e-mails, texts, calls or simply a remote access.
Intranet: Intranet is a mini internet secured in a minor zone and is private and not
accessible worldwide. External access to the Intranet is possible if VPN is used.
Extranet: It is a part of the Intranet that is made accessible to only privileged users
outside the intranet network and is controlled by strict authentication and
authorization to maintain the integrity.
VLAN (Virtual Local Area Network): A collection of devices connected to a single
switch into multiple domains and segments of networks.
NAT (Network Address Translation): Uses two sets of IP addresses for internal
network devices and external network devices. Translation of NAT occurs in a router,
firewall and lets assign communication across the internet.
Tunneling:The packaging of packets of data to safely deliver/ transfer them in an
encapsulated manner.
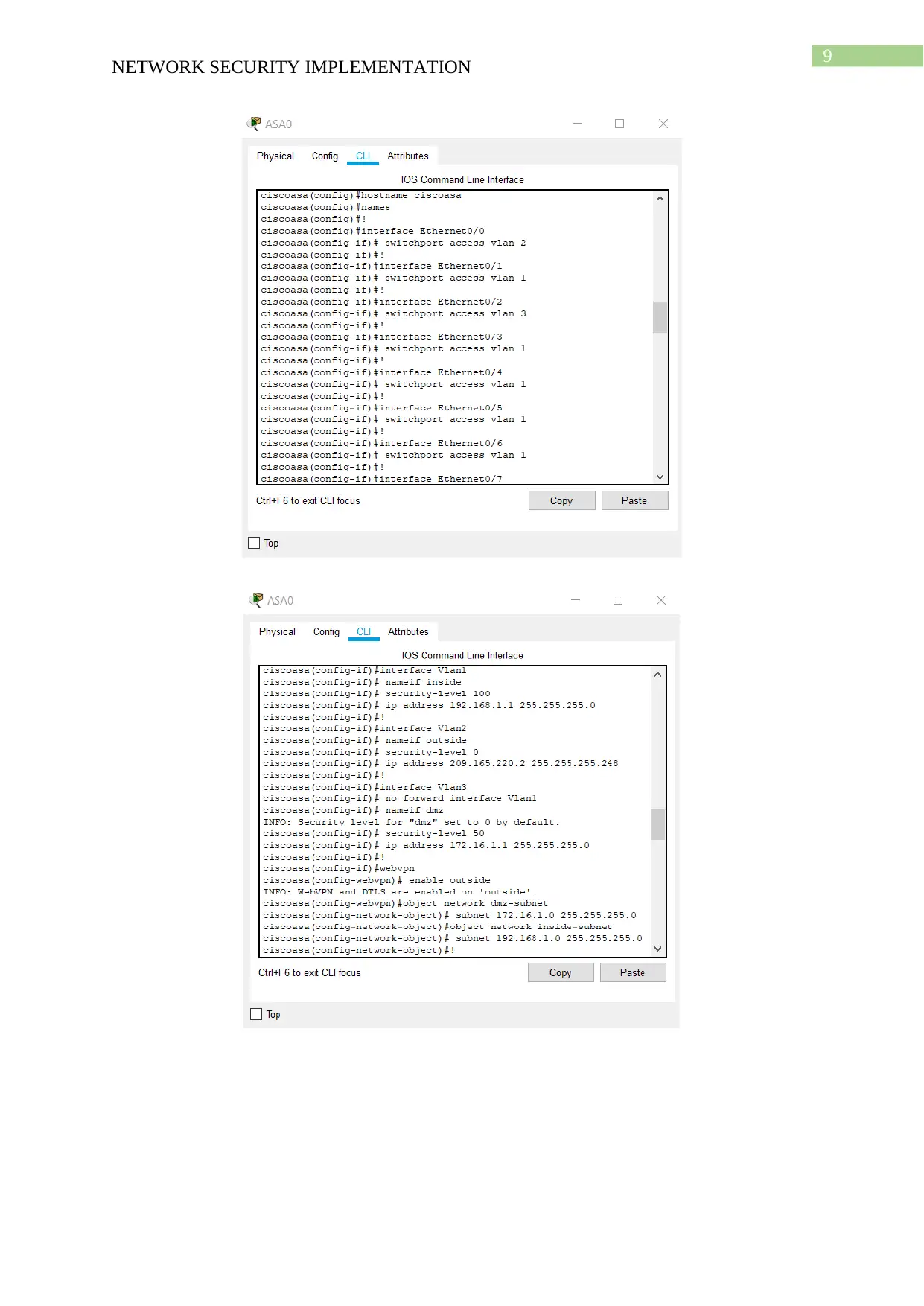
Configuration of firewall and Router
Firewall
NETWORK SECURITY IMPLEMENTATION
Internet: The public network that anyone wishes to access is known as the internet.
The internet is worldwide. The internet enables a network to access to remote located
servers with the help of e-mails, texts, calls or simply a remote access.
Intranet: Intranet is a mini internet secured in a minor zone and is private and not
accessible worldwide. External access to the Intranet is possible if VPN is used.
Extranet: It is a part of the Intranet that is made accessible to only privileged users
outside the intranet network and is controlled by strict authentication and
authorization to maintain the integrity.
VLAN (Virtual Local Area Network): A collection of devices connected to a single
switch into multiple domains and segments of networks.
NAT (Network Address Translation): Uses two sets of IP addresses for internal
network devices and external network devices. Translation of NAT occurs in a router,
firewall and lets assign communication across the internet.
Tunneling:The packaging of packets of data to safely deliver/ transfer them in an
encapsulated manner.
Configuration of firewall and Router
Firewall
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
NETWORK SECURITY IMPLEMENTATION
NETWORK SECURITY IMPLEMENTATION
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
NETWORK SECURITY IMPLEMENTATION
NETWORK SECURITY IMPLEMENTATION
11
NETWORK SECURITY IMPLEMENTATION
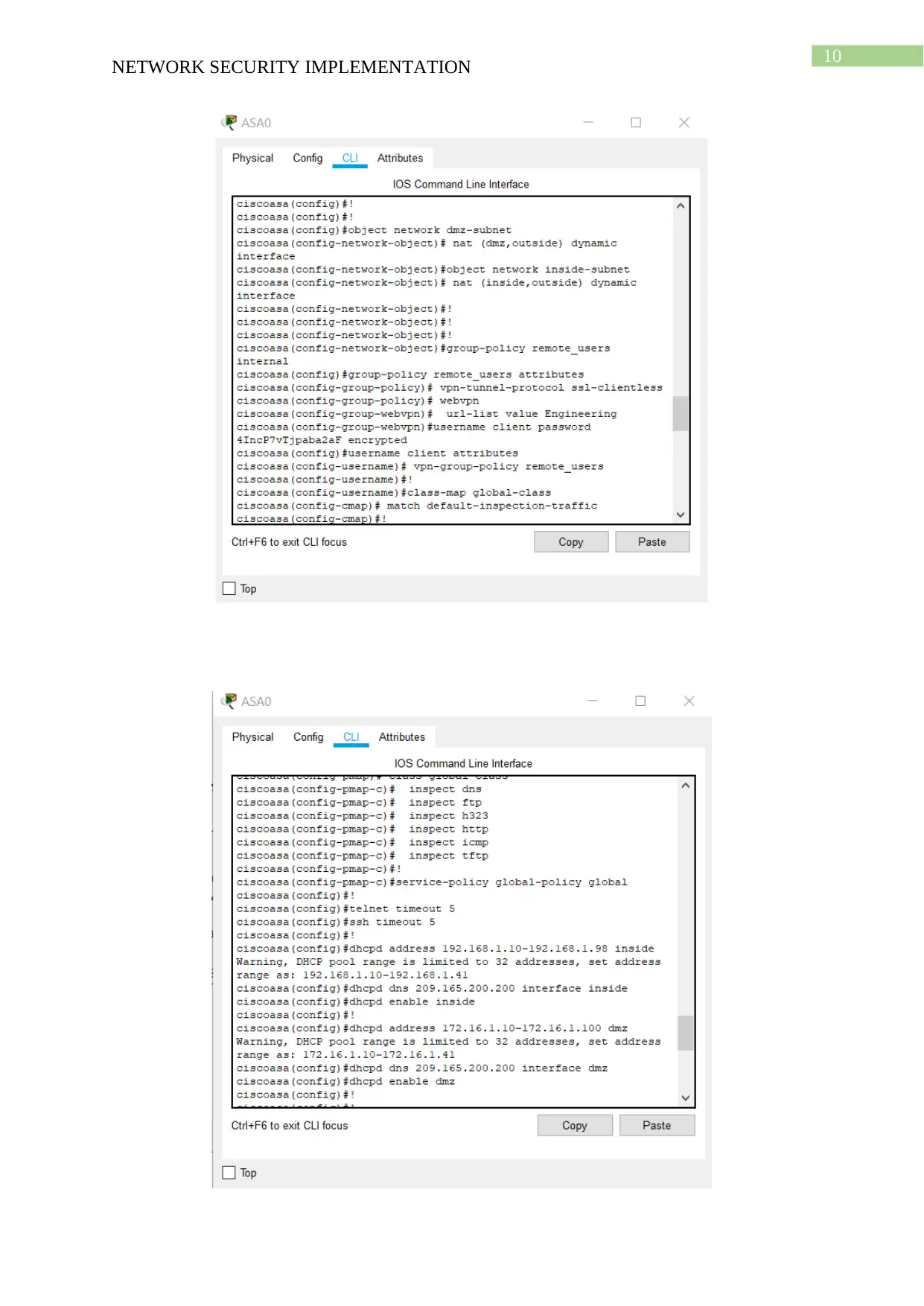
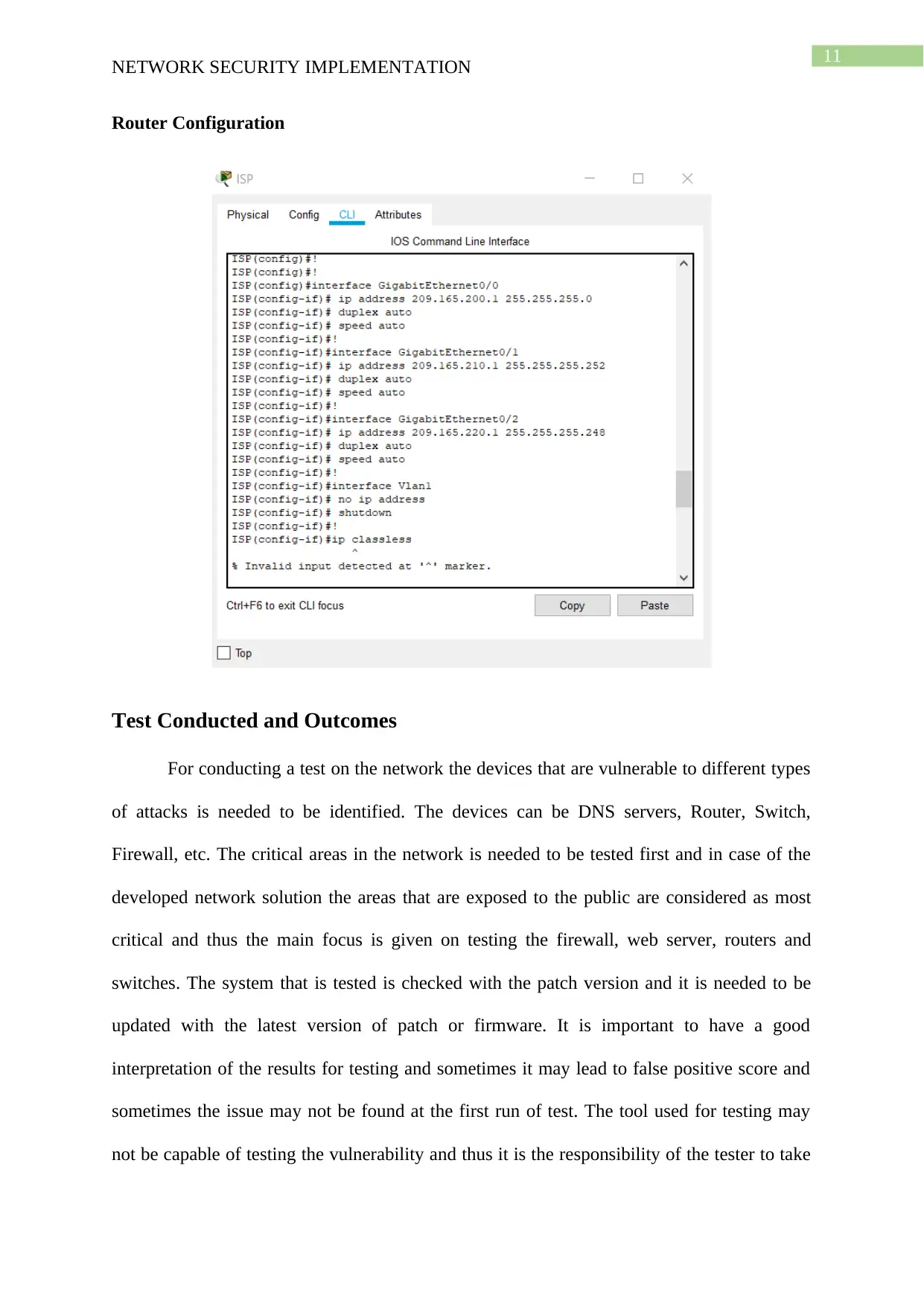
Router Configuration
Test Conducted and Outcomes
For conducting a test on the network the devices that are vulnerable to different types
of attacks is needed to be identified. The devices can be DNS servers, Router, Switch,
Firewall, etc. The critical areas in the network is needed to be tested first and in case of the
developed network solution the areas that are exposed to the public are considered as most
critical and thus the main focus is given on testing the firewall, web server, routers and
switches. The system that is tested is checked with the patch version and it is needed to be
updated with the latest version of patch or firmware. It is important to have a good
interpretation of the results for testing and sometimes it may lead to false positive score and
sometimes the issue may not be found at the first run of test. The tool used for testing may
not be capable of testing the vulnerability and thus it is the responsibility of the tester to take
NETWORK SECURITY IMPLEMENTATION
Router Configuration
Test Conducted and Outcomes
For conducting a test on the network the devices that are vulnerable to different types
of attacks is needed to be identified. The devices can be DNS servers, Router, Switch,
Firewall, etc. The critical areas in the network is needed to be tested first and in case of the
developed network solution the areas that are exposed to the public are considered as most
critical and thus the main focus is given on testing the firewall, web server, routers and
switches. The system that is tested is checked with the patch version and it is needed to be
updated with the latest version of patch or firmware. It is important to have a good
interpretation of the results for testing and sometimes it may lead to false positive score and
sometimes the issue may not be found at the first run of test. The tool used for testing may
not be capable of testing the vulnerability and thus it is the responsibility of the tester to take
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





