Cloud Computing Security Challenges
VerifiedAdded on 2020/05/11
|24
|7063
|98
AI Summary
The provided document delves into the multifaceted realm of cloud computing security. It examines a range of prominent challenges, including data privacy concerns, effective access control mechanisms, and potential vulnerabilities within cloud infrastructure. Researchers and practitioners alike can glean valuable insights into mitigating these risks and fostering a secure cloud computing environment.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CLOUD PRIVACY AND SECURITY
Cloud Privacy and Security
Name of the Student
Name of the University
Author’s Note:
Cloud Privacy and Security
Name of the Student
Name of the University
Author’s Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
CLOUD PRIVACY AND SECURITY
Table of Contents
Introduction......................................................................................................................................3
Discussion........................................................................................................................................4
1. Personal Data Privacy Strategy...............................................................................................4
1.1 Management of Personal Information...............................................................................4
1.2 Collection and Management of Solicited Personal Information........................................5
1.3 Use and Disclosure of Personal Information.....................................................................5
1.4 Use and Security of Digital Identities................................................................................6
1.5 Security of Personal Information.......................................................................................6
1.6 Access to Personal Information.........................................................................................7
1.7 Quality and Correction of Personal Information...............................................................7
2. Privacy Control Recommendations.........................................................................................8
3. Personal Data Protection Strategies.......................................................................................14
3.1 Protection of Personal Information..................................................................................14
3.2 Authorized Access and Disclosure of Personal Information...........................................15
3.3 De-Identification of Personal Data..................................................................................15
3.4 Use of Personal Digital Identities....................................................................................15
3.5 Security of Personal Data................................................................................................16
3.6 Archiving of Personal Data.............................................................................................16
4. Privacy Control Recommendations.......................................................................................16
CLOUD PRIVACY AND SECURITY
Table of Contents
Introduction......................................................................................................................................3
Discussion........................................................................................................................................4
1. Personal Data Privacy Strategy...............................................................................................4
1.1 Management of Personal Information...............................................................................4
1.2 Collection and Management of Solicited Personal Information........................................5
1.3 Use and Disclosure of Personal Information.....................................................................5
1.4 Use and Security of Digital Identities................................................................................6
1.5 Security of Personal Information.......................................................................................6
1.6 Access to Personal Information.........................................................................................7
1.7 Quality and Correction of Personal Information...............................................................7
2. Privacy Control Recommendations.........................................................................................8
3. Personal Data Protection Strategies.......................................................................................14
3.1 Protection of Personal Information..................................................................................14
3.2 Authorized Access and Disclosure of Personal Information...........................................15
3.3 De-Identification of Personal Data..................................................................................15
3.4 Use of Personal Digital Identities....................................................................................15
3.5 Security of Personal Data................................................................................................16
3.6 Archiving of Personal Data.............................................................................................16
4. Privacy Control Recommendations.......................................................................................16

2
CLOUD PRIVACY AND SECURITY
Conclusion.....................................................................................................................................23
References......................................................................................................................................25
CLOUD PRIVACY AND SECURITY
Conclusion.....................................................................................................................................23
References......................................................................................................................................25

3
CLOUD PRIVACY AND SECURITY
Introduction
Cloud computing is the tool or technique by which confidential information or data or
any other services can be easily transferred. These services refer to the computing services,
which include storage, software, networking, servers, analytics and many more (Arora, Parashar
& Transforming, 2013). This cloud computing technique delivers or transfers the data or
computing services through Internet. Without an Internet enabled device, it is impossible to
utilize cloud computing. There are particular organizations or businesses that provide the typical
types of computing services and they are known as the cloud providers or the providers of cloud.
Cloud computing is the most effective and popular technology for transfer of data. This
particular technology delivers the software, whenever they are needed (Dinh et al., 2013). Cloud
computing secures the data or information by analyzing them. Moreover, it streams various types
of audio and video. The main advantages of cloud computing is that the confidential data or
information is absolutely safe and secured in a cost effective way. There are many more
advantages as well like the speed of transferring of data. This even increases the overall
productivity of the computing services. Cloud computing is extremely flexible and reliable and
this makes this technology extremely popular for almost all organizations (Bonomi et al., 2012).
However, every coin has an opposite side. This particular technology does have some of the
major disadvantages. The most significant disadvantage of cloud computing is that it is
absolutely dependent on the Internet. Cloud computing does not work with poor Internet
connectivity. The second main disadvantage of cloud computing is the issues with security and
privacy. In spite of being extremely reliable, data is often hacked or deleted in cloud computing
and there is a high chance that the data will lost its integrity and confidentiality (Khalil,
CLOUD PRIVACY AND SECURITY
Introduction
Cloud computing is the tool or technique by which confidential information or data or
any other services can be easily transferred. These services refer to the computing services,
which include storage, software, networking, servers, analytics and many more (Arora, Parashar
& Transforming, 2013). This cloud computing technique delivers or transfers the data or
computing services through Internet. Without an Internet enabled device, it is impossible to
utilize cloud computing. There are particular organizations or businesses that provide the typical
types of computing services and they are known as the cloud providers or the providers of cloud.
Cloud computing is the most effective and popular technology for transfer of data. This
particular technology delivers the software, whenever they are needed (Dinh et al., 2013). Cloud
computing secures the data or information by analyzing them. Moreover, it streams various types
of audio and video. The main advantages of cloud computing is that the confidential data or
information is absolutely safe and secured in a cost effective way. There are many more
advantages as well like the speed of transferring of data. This even increases the overall
productivity of the computing services. Cloud computing is extremely flexible and reliable and
this makes this technology extremely popular for almost all organizations (Bonomi et al., 2012).
However, every coin has an opposite side. This particular technology does have some of the
major disadvantages. The most significant disadvantage of cloud computing is that it is
absolutely dependent on the Internet. Cloud computing does not work with poor Internet
connectivity. The second main disadvantage of cloud computing is the issues with security and
privacy. In spite of being extremely reliable, data is often hacked or deleted in cloud computing
and there is a high chance that the data will lost its integrity and confidentiality (Khalil,
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
CLOUD PRIVACY AND SECURITY
Khreishah & Azeem, 2014). The most common types of cloud services are Software as a Service
or SaaS, Platform as a Service or PaaS and Infrastructure as a Service or IaaS.
This particular report covers the basic concept of privacy and security strategies on the
given case study of Department of Administrative Services or DAS. It provides all kinds of
services to the Australian State Government (Gellman, 2012). The services are of several
categories and types. The main services are the procurement management, payroll, personnel
management, human resources management and contractor management. The following report
describes about the several privacy and security strategies. Proper approaches are mentioned in
the report for mitigating the security or data risks or threats. Moreover, relevant suggestions are
also provided in the report for DAS case study.
Discussion
1. Personal Data Privacy Strategy
1.1 Management of Personal Information
Management of personal information is the most important step for DAS. They will have
to control their information, so that the information is not lost. There are few steps to manage or
secure the data. They are as follows:
a) Passwords: The most simple and efficient way of securing any type of information is
keeping passwords (Lee & Zomaya, 2012). The passwords prevent any type of hacker from
intruder in the cloud. Moreover, passwords should be changed or altered periodically.
b) Secured Browser: A secured browser is also helpful for any type of security of
information (Gampala, Inuganti & Muppidi, 2012). The secured browser prevents or disallows
CLOUD PRIVACY AND SECURITY
Khreishah & Azeem, 2014). The most common types of cloud services are Software as a Service
or SaaS, Platform as a Service or PaaS and Infrastructure as a Service or IaaS.
This particular report covers the basic concept of privacy and security strategies on the
given case study of Department of Administrative Services or DAS. It provides all kinds of
services to the Australian State Government (Gellman, 2012). The services are of several
categories and types. The main services are the procurement management, payroll, personnel
management, human resources management and contractor management. The following report
describes about the several privacy and security strategies. Proper approaches are mentioned in
the report for mitigating the security or data risks or threats. Moreover, relevant suggestions are
also provided in the report for DAS case study.
Discussion
1. Personal Data Privacy Strategy
1.1 Management of Personal Information
Management of personal information is the most important step for DAS. They will have
to control their information, so that the information is not lost. There are few steps to manage or
secure the data. They are as follows:
a) Passwords: The most simple and efficient way of securing any type of information is
keeping passwords (Lee & Zomaya, 2012). The passwords prevent any type of hacker from
intruder in the cloud. Moreover, passwords should be changed or altered periodically.
b) Secured Browser: A secured browser is also helpful for any type of security of
information (Gampala, Inuganti & Muppidi, 2012). The secured browser prevents or disallows

5
CLOUD PRIVACY AND SECURITY
all types of malware and malicious code in the system and thus personal information is managed
easily.
1.2 Collection and Management of Solicited Personal Information
This is the second step for personal data privacy strategy. Certain steps complete the
collection and management of information easily. They are as follows:
a) Reliable Source: The major step is the collecting, gathering and acquiring of the
information or data from a reliable source.
b) Filtering of Information: Once the information is collected from a basic reliable
source, the information is thorughly filtered (Yang & Jia, 2013). This filtration of confidential
information will remove all the undesired information.
c) Review: The third step of the process of collection and management is to review the
personal information. When the information is relevant it is kept and it is removed or deleted, if
found to be useless.
1.3 Use and Disclosure of Personal Information
Only authenticated and sanctioned users must utilize and disclose the information
(Garrison, Kim & Wakefield, 2012). There are several ways for securing and blocking the access
from any type of unsanctioned users. They are as follows:
a) Logging Out: The moment a user logs in into his/her account containing all the
important and confidential information, the chance exists that the information would be lost.
CLOUD PRIVACY AND SECURITY
all types of malware and malicious code in the system and thus personal information is managed
easily.
1.2 Collection and Management of Solicited Personal Information
This is the second step for personal data privacy strategy. Certain steps complete the
collection and management of information easily. They are as follows:
a) Reliable Source: The major step is the collecting, gathering and acquiring of the
information or data from a reliable source.
b) Filtering of Information: Once the information is collected from a basic reliable
source, the information is thorughly filtered (Yang & Jia, 2013). This filtration of confidential
information will remove all the undesired information.
c) Review: The third step of the process of collection and management is to review the
personal information. When the information is relevant it is kept and it is removed or deleted, if
found to be useless.
1.3 Use and Disclosure of Personal Information
Only authenticated and sanctioned users must utilize and disclose the information
(Garrison, Kim & Wakefield, 2012). There are several ways for securing and blocking the access
from any type of unsanctioned users. They are as follows:
a) Logging Out: The moment a user logs in into his/her account containing all the
important and confidential information, the chance exists that the information would be lost.

6
CLOUD PRIVACY AND SECURITY
b) Limited Access to Systems: Another way of protecting the personal information from
being utilized and disclosed with the unsanctioned users (Pearson, 2013). The access to the
information must be restricted to stop the intruders from tracking the information.
1.4 Use and Security of Digital Identities
The confidential information of a particular organization, which is used for representing a
particular external representative, is called a digital identity (Yang & Jia, 2013). The digital
identity can be anything like an individual or organization. The digital identities have several
benefits. The main benefits of digital identities are as follows:
a) Data Integrity
b) Security
c) Fast
d) Simple
1.5 Security of Personal Information
Security is the principal step in the privacy and security strategy. Leakage of the personal
information is not at all permissible, as the cyber threats are increased. The most efficient ways
of securing personal information are as follows:
a) Passwords: The most simple and efficient way of securing any type of information is
keeping passwords (Chaisiri, Lee & Niyato, 2012). The passwords prevent any type of hacker
from intruder in the cloud. Moreover, passwords should be changed or altered periodically.
CLOUD PRIVACY AND SECURITY
b) Limited Access to Systems: Another way of protecting the personal information from
being utilized and disclosed with the unsanctioned users (Pearson, 2013). The access to the
information must be restricted to stop the intruders from tracking the information.
1.4 Use and Security of Digital Identities
The confidential information of a particular organization, which is used for representing a
particular external representative, is called a digital identity (Yang & Jia, 2013). The digital
identity can be anything like an individual or organization. The digital identities have several
benefits. The main benefits of digital identities are as follows:
a) Data Integrity
b) Security
c) Fast
d) Simple
1.5 Security of Personal Information
Security is the principal step in the privacy and security strategy. Leakage of the personal
information is not at all permissible, as the cyber threats are increased. The most efficient ways
of securing personal information are as follows:
a) Passwords: The most simple and efficient way of securing any type of information is
keeping passwords (Chaisiri, Lee & Niyato, 2012). The passwords prevent any type of hacker
from intruder in the cloud. Moreover, passwords should be changed or altered periodically.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CLOUD PRIVACY AND SECURITY
b) Antivirus: Antivirus is software that secures a system from malicious codes or
malware. When the system is protected, the information is also protected (Hashizume et al.,
2013). DAS should protect every system with antivirus for protecting their information.
1.6 Access to Personal Information
The access to the personal information should be restricted for the unsanctioned and
unauthenticated users (Yu et al., 2013). The several methods for protecting the access to the
personal information are as follows:
a) Access Control: The access to the system should be restricted and controlled so that all
the users access the personal information.
b) Limited Access to Systems: Another way of protecting the personal information from
being utilized and disclosed with the unsanctioned users (Pearson, 2013). The access to the
information must be restricted to stop the intruders from tracking the information.
1.7 Quality and Correction of Personal Information
Quality of the personal information ensures the fact that the information stored by the
organization is not false. DAS should protect and secure their information by undertaking
various steps (Arora, Parashar & Transforming, 2013). This is done by ensuring the quality of
the information. This removes the useless information. Moreover, if by chance wrong
information is stored or any type of erroneous information is stored within the system, the
correction is done immediately. Thus, this step is extremely needed.
CLOUD PRIVACY AND SECURITY
b) Antivirus: Antivirus is software that secures a system from malicious codes or
malware. When the system is protected, the information is also protected (Hashizume et al.,
2013). DAS should protect every system with antivirus for protecting their information.
1.6 Access to Personal Information
The access to the personal information should be restricted for the unsanctioned and
unauthenticated users (Yu et al., 2013). The several methods for protecting the access to the
personal information are as follows:
a) Access Control: The access to the system should be restricted and controlled so that all
the users access the personal information.
b) Limited Access to Systems: Another way of protecting the personal information from
being utilized and disclosed with the unsanctioned users (Pearson, 2013). The access to the
information must be restricted to stop the intruders from tracking the information.
1.7 Quality and Correction of Personal Information
Quality of the personal information ensures the fact that the information stored by the
organization is not false. DAS should protect and secure their information by undertaking
various steps (Arora, Parashar & Transforming, 2013). This is done by ensuring the quality of
the information. This removes the useless information. Moreover, if by chance wrong
information is stored or any type of erroneous information is stored within the system, the
correction is done immediately. Thus, this step is extremely needed.
8
CLOUD PRIVACY AND SECURITY
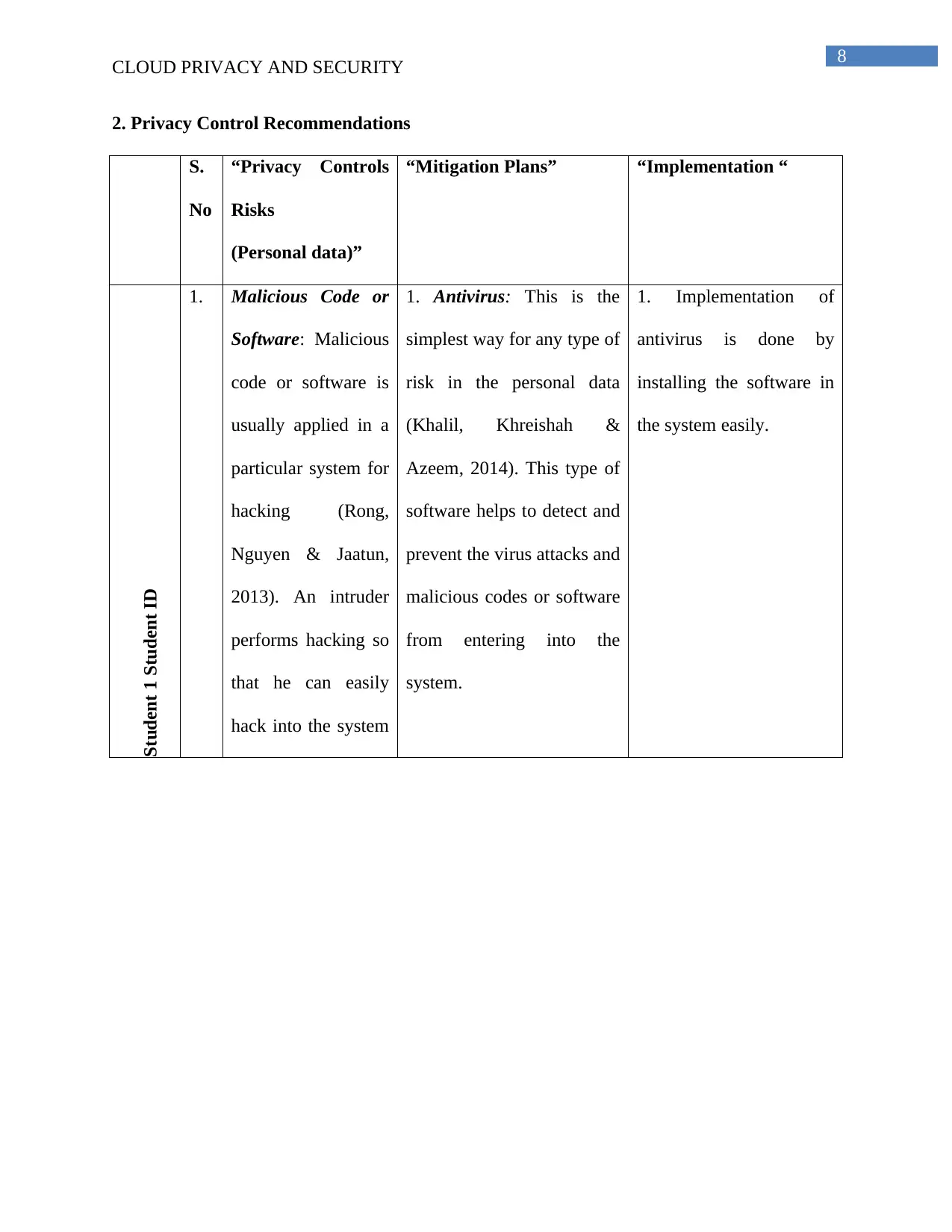
2. Privacy Control Recommendations
S.
No
“Privacy Controls
Risks
(Personal data)”
“Mitigation Plans” “Implementation “
Student 1 Student ID
1. Malicious Code or
Software: Malicious
code or software is
usually applied in a
particular system for
hacking (Rong,
Nguyen & Jaatun,
2013). An intruder
performs hacking so
that he can easily
hack into the system
1. Antivirus: This is the
simplest way for any type of
risk in the personal data
(Khalil, Khreishah &
Azeem, 2014). This type of
software helps to detect and
prevent the virus attacks and
malicious codes or software
from entering into the
system.
1. Implementation of
antivirus is done by
installing the software in
the system easily.
CLOUD PRIVACY AND SECURITY
2. Privacy Control Recommendations
S.
No
“Privacy Controls
Risks
(Personal data)”
“Mitigation Plans” “Implementation “
Student 1 Student ID
1. Malicious Code or
Software: Malicious
code or software is
usually applied in a
particular system for
hacking (Rong,
Nguyen & Jaatun,
2013). An intruder
performs hacking so
that he can easily
hack into the system
1. Antivirus: This is the
simplest way for any type of
risk in the personal data
(Khalil, Khreishah &
Azeem, 2014). This type of
software helps to detect and
prevent the virus attacks and
malicious codes or software
from entering into the
system.
1. Implementation of
antivirus is done by
installing the software in
the system easily.
9
CLOUD PRIVACY AND SECURITY
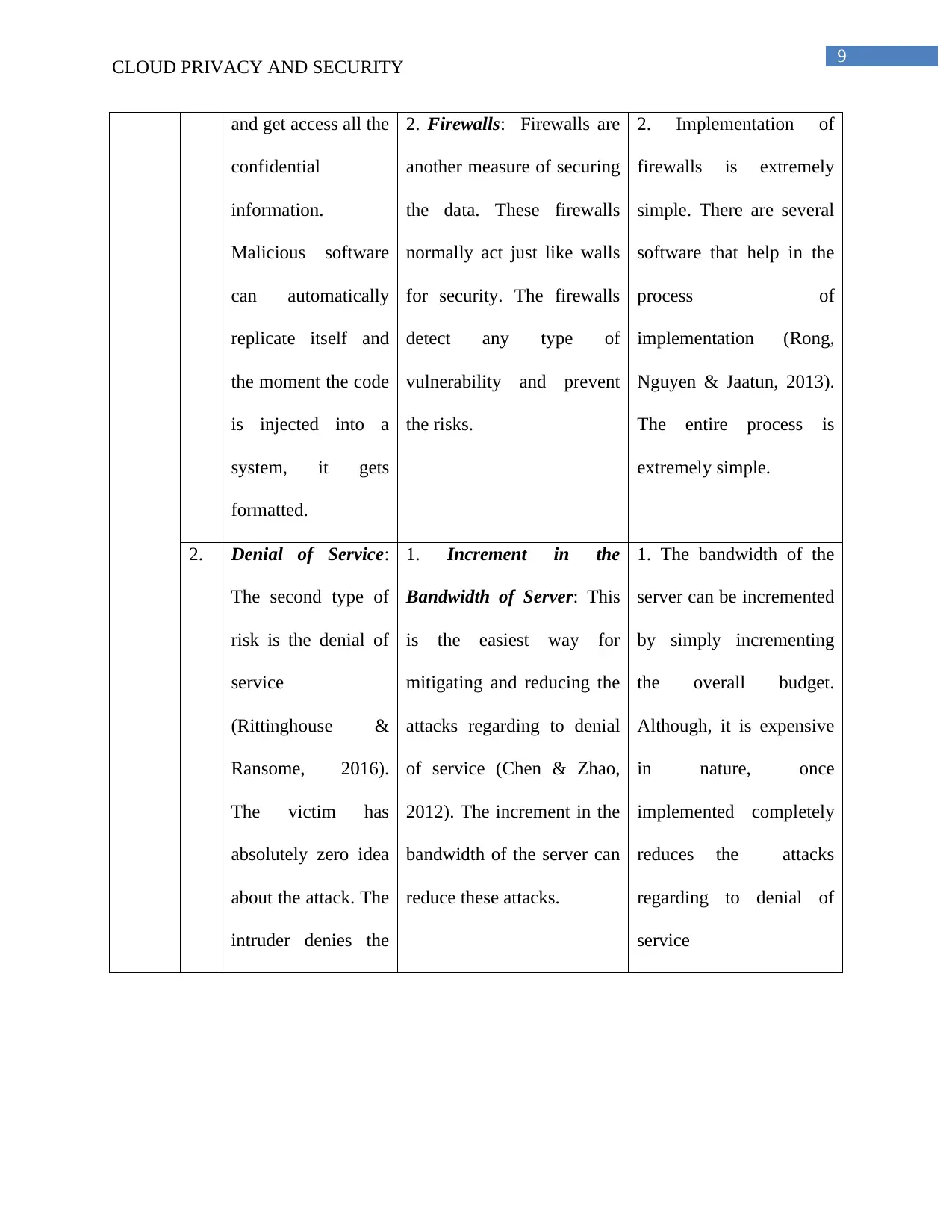
and get access all the
confidential
information.
Malicious software
can automatically
replicate itself and
the moment the code
is injected into a
system, it gets
formatted.
2. Firewalls: Firewalls are
another measure of securing
the data. These firewalls
normally act just like walls
for security. The firewalls
detect any type of
vulnerability and prevent
the risks.
2. Implementation of
firewalls is extremely
simple. There are several
software that help in the
process of
implementation (Rong,
Nguyen & Jaatun, 2013).
The entire process is
extremely simple.
2. Denial of Service:
The second type of
risk is the denial of
service
(Rittinghouse &
Ransome, 2016).
The victim has
absolutely zero idea
about the attack. The
intruder denies the
1. Increment in the
Bandwidth of Server: This
is the easiest way for
mitigating and reducing the
attacks regarding to denial
of service (Chen & Zhao,
2012). The increment in the
bandwidth of the server can
reduce these attacks.
1. The bandwidth of the
server can be incremented
by simply incrementing
the overall budget.
Although, it is expensive
in nature, once
implemented completely
reduces the attacks
regarding to denial of
service
CLOUD PRIVACY AND SECURITY
and get access all the
confidential
information.
Malicious software
can automatically
replicate itself and
the moment the code
is injected into a
system, it gets
formatted.
2. Firewalls: Firewalls are
another measure of securing
the data. These firewalls
normally act just like walls
for security. The firewalls
detect any type of
vulnerability and prevent
the risks.
2. Implementation of
firewalls is extremely
simple. There are several
software that help in the
process of
implementation (Rong,
Nguyen & Jaatun, 2013).
The entire process is
extremely simple.
2. Denial of Service:
The second type of
risk is the denial of
service
(Rittinghouse &
Ransome, 2016).
The victim has
absolutely zero idea
about the attack. The
intruder denies the
1. Increment in the
Bandwidth of Server: This
is the easiest way for
mitigating and reducing the
attacks regarding to denial
of service (Chen & Zhao,
2012). The increment in the
bandwidth of the server can
reduce these attacks.
1. The bandwidth of the
server can be incremented
by simply incrementing
the overall budget.
Although, it is expensive
in nature, once
implemented completely
reduces the attacks
regarding to denial of
service
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10
CLOUD PRIVACY AND SECURITY
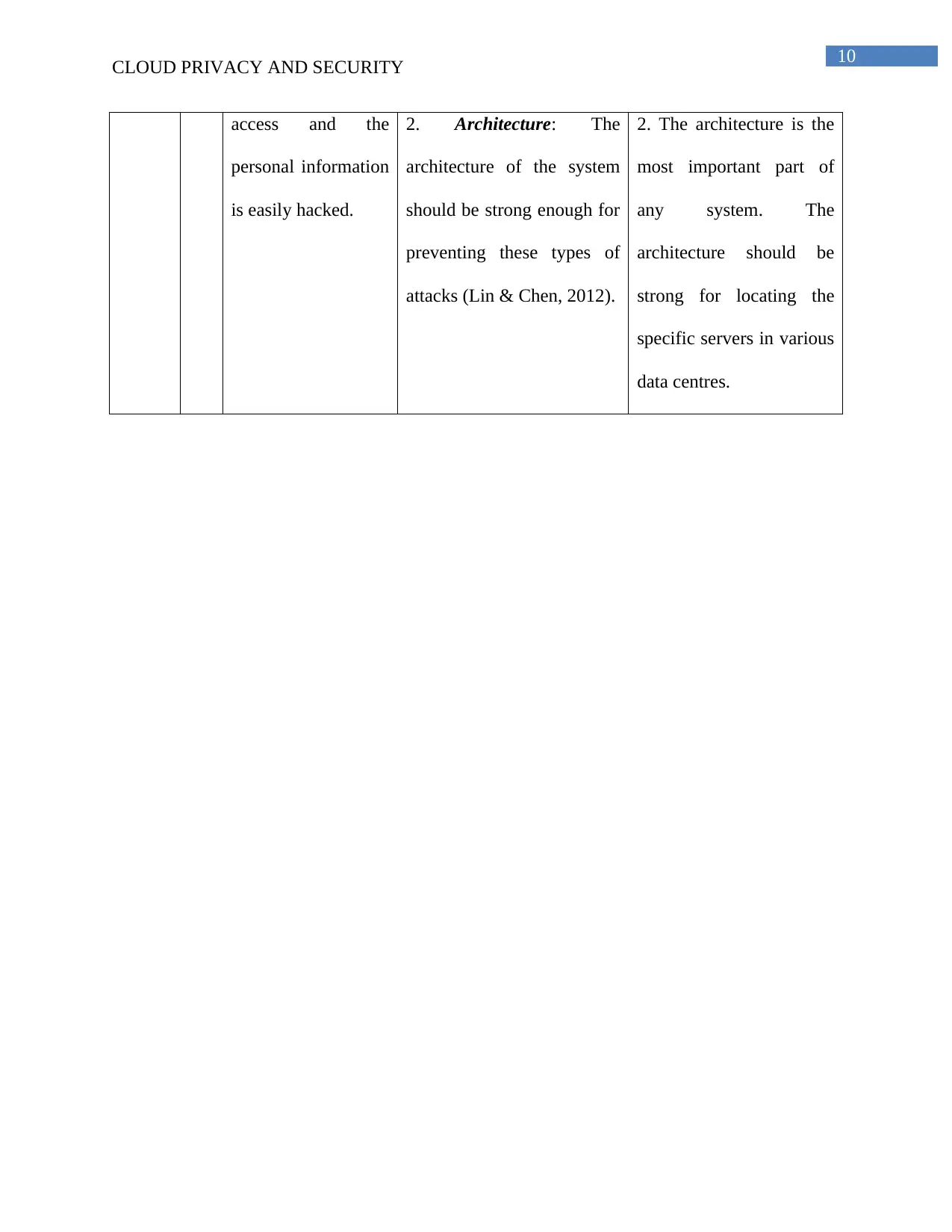
access and the
personal information
is easily hacked.
2. Architecture: The
architecture of the system
should be strong enough for
preventing these types of
attacks (Lin & Chen, 2012).
2. The architecture is the
most important part of
any system. The
architecture should be
strong for locating the
specific servers in various
data centres.
CLOUD PRIVACY AND SECURITY
access and the
personal information
is easily hacked.
2. Architecture: The
architecture of the system
should be strong enough for
preventing these types of
attacks (Lin & Chen, 2012).
2. The architecture is the
most important part of
any system. The
architecture should be
strong for locating the
specific servers in various
data centres.
11
CLOUD PRIVACY AND SECURITY
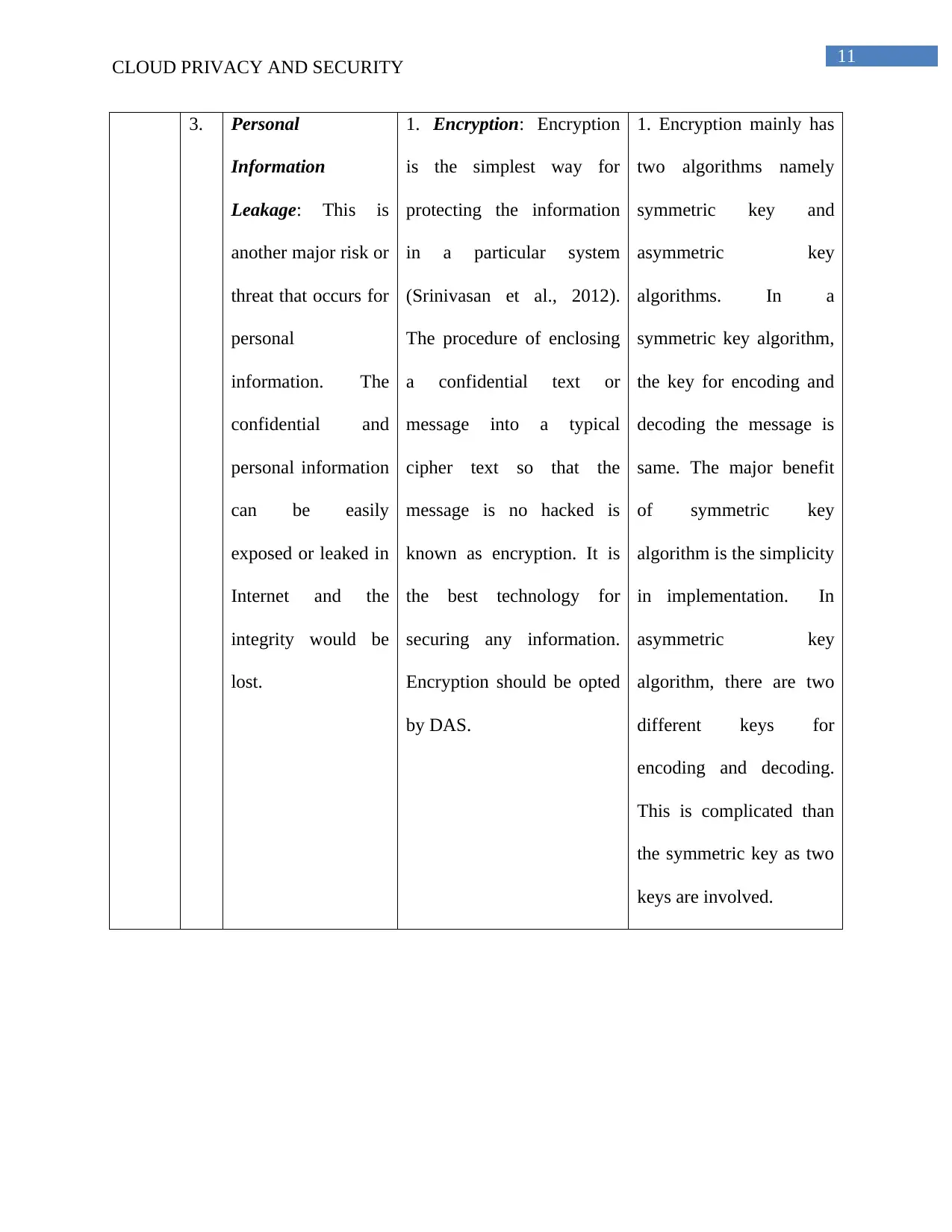
3. Personal
Information
Leakage: This is
another major risk or
threat that occurs for
personal
information. The
confidential and
personal information
can be easily
exposed or leaked in
Internet and the
integrity would be
lost.
1. Encryption: Encryption
is the simplest way for
protecting the information
in a particular system
(Srinivasan et al., 2012).
The procedure of enclosing
a confidential text or
message into a typical
cipher text so that the
message is no hacked is
known as encryption. It is
the best technology for
securing any information.
Encryption should be opted
by DAS.
1. Encryption mainly has
two algorithms namely
symmetric key and
asymmetric key
algorithms. In a
symmetric key algorithm,
the key for encoding and
decoding the message is
same. The major benefit
of symmetric key
algorithm is the simplicity
in implementation. In
asymmetric key
algorithm, there are two
different keys for
encoding and decoding.
This is complicated than
the symmetric key as two
keys are involved.
CLOUD PRIVACY AND SECURITY
3. Personal
Information
Leakage: This is
another major risk or
threat that occurs for
personal
information. The
confidential and
personal information
can be easily
exposed or leaked in
Internet and the
integrity would be
lost.
1. Encryption: Encryption
is the simplest way for
protecting the information
in a particular system
(Srinivasan et al., 2012).
The procedure of enclosing
a confidential text or
message into a typical
cipher text so that the
message is no hacked is
known as encryption. It is
the best technology for
securing any information.
Encryption should be opted
by DAS.
1. Encryption mainly has
two algorithms namely
symmetric key and
asymmetric key
algorithms. In a
symmetric key algorithm,
the key for encoding and
decoding the message is
same. The major benefit
of symmetric key
algorithm is the simplicity
in implementation. In
asymmetric key
algorithm, there are two
different keys for
encoding and decoding.
This is complicated than
the symmetric key as two
keys are involved.

12
CLOUD PRIVACY AND SECURITY
2. Digital Authentication:
Digital authentication is
another popular way of
protecting the personal
information. Digital
authentication is the
procedure of authenticating
a person or an individual by
digital means (Ren, Wang &
Wang, 2012). The popular
examples of digital
authentication are the
fingerprint recognition,
face recognition software,
and digital signatures.
2. Digital authentication
is implemented by
installing biometric
entrance to all the systems
in the organization (Ren,
Wang, & Wang, 2012).
CLOUD PRIVACY AND SECURITY
2. Digital Authentication:
Digital authentication is
another popular way of
protecting the personal
information. Digital
authentication is the
procedure of authenticating
a person or an individual by
digital means (Ren, Wang &
Wang, 2012). The popular
examples of digital
authentication are the
fingerprint recognition,
face recognition software,
and digital signatures.
2. Digital authentication
is implemented by
installing biometric
entrance to all the systems
in the organization (Ren,
Wang, & Wang, 2012).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13
CLOUD PRIVACY AND SECURITY
et
4. Identity Theft: One
of the most
dangerous and
vulnerable threat is
the identity theft.
The hacker or the
intruder acts as the
user and thus access
all the information
easily (Ren, Wang,
& Wang, 2012). The
identity of the user is
stolen in this type of
1. Passwords: The most
simple and efficient way of
securing any type of
information is keeping
passwords (Chaisiri, Lee &
Niyato, 2012). The
passwords prevent any type
of hacker from intruder in
the cloud. Moreover,
passwords should be
changed or altered
periodically.
1. Passwords are set by
the specific users in any
system. Special characters
are used to set this
password. Only
authenticated users have
the right to know the
passwords. Moreover,
they are changed and
altered periodically. This
particular step would be
helpful for DAS.
CLOUD PRIVACY AND SECURITY
et
4. Identity Theft: One
of the most
dangerous and
vulnerable threat is
the identity theft.
The hacker or the
intruder acts as the
user and thus access
all the information
easily (Ren, Wang,
& Wang, 2012). The
identity of the user is
stolen in this type of
1. Passwords: The most
simple and efficient way of
securing any type of
information is keeping
passwords (Chaisiri, Lee &
Niyato, 2012). The
passwords prevent any type
of hacker from intruder in
the cloud. Moreover,
passwords should be
changed or altered
periodically.
1. Passwords are set by
the specific users in any
system. Special characters
are used to set this
password. Only
authenticated users have
the right to know the
passwords. Moreover,
they are changed and
altered periodically. This
particular step would be
helpful for DAS.
14
CLOUD PRIVACY AND SECURITY
risk. 2. Not Responding to
Unsolicited Mails: Another
easiest way of reducing tese
types of risks is to not
respond to the unsolicited
mails. Unsolicited e-mails
attract various hackers and
intruders into the system.
Even avoiding similar types
of phones that want to know
about confidential
information can mitigate
this type of risk..
2. This type of step does
not require any specific
implementation plan
(Arora, Parashar &
Transforming, 2013). The
simplest approach is by
avoiding similar types of
emails and phones so that
the hacker gets no idea
about the personal
information.
5. Receiving
Unsolicited E-mails:
This is also a
vulnerable security
threat for any
organization. Such
mails are known as
spam. They have the
ability to steal and
modify all
1. Avoid Clicking: This is
the simplest step to mitigate
reducing this type of emails
(Sefraoui, Aissaoui &
Eleuldj, 2012). The user
should avoid or stop
attending all type of mails
and attend only those, which
are important and required
emails.
1. No such
implementation is
required for this
mitigation plan. Just the
user has to be careful
before entertaining any
sort of emails.
CLOUD PRIVACY AND SECURITY
risk. 2. Not Responding to
Unsolicited Mails: Another
easiest way of reducing tese
types of risks is to not
respond to the unsolicited
mails. Unsolicited e-mails
attract various hackers and
intruders into the system.
Even avoiding similar types
of phones that want to know
about confidential
information can mitigate
this type of risk..
2. This type of step does
not require any specific
implementation plan
(Arora, Parashar &
Transforming, 2013). The
simplest approach is by
avoiding similar types of
emails and phones so that
the hacker gets no idea
about the personal
information.
5. Receiving
Unsolicited E-mails:
This is also a
vulnerable security
threat for any
organization. Such
mails are known as
spam. They have the
ability to steal and
modify all
1. Avoid Clicking: This is
the simplest step to mitigate
reducing this type of emails
(Sefraoui, Aissaoui &
Eleuldj, 2012). The user
should avoid or stop
attending all type of mails
and attend only those, which
are important and required
emails.
1. No such
implementation is
required for this
mitigation plan. Just the
user has to be careful
before entertaining any
sort of emails.
15
CLOUD PRIVACY AND SECURITY
confidential
information within
few moments.
2. Use a Disposable Email
Address: A disposable email
always protects the user
from receiving all sorts of
unsolicited emails from fake
addresses (Wu et al. 2013).
This in turn helps the user to
avoid spam messages.
2. The Department of
Administrative Services
should use a disposable
email address. They will
only have to open their
accounts in that email.
This particular step will
be useful and will secure
the data.
6. Loss of Data in the
Clouds: This is
again a dangerous
and a significant risk
in case of securing
personal
information. While
storing or retrieving
the data in the cloud,
there is always a
high chance that the
data will be lost in
the clouds. Often,
these data cannot be
1. Encryption: Encryption
is the simplest way for
protecting the information
in a particular system
(Srinivasan et al., 2012).
The procedure of enclosing
a confidential text or
message into a typical
cipher text so that the
message is no hacked is
known as encryption. It is
the best technology for
securing any information.
Encryption should be opted
1. Encryption mainly has
two algorithms namely
symmetric key and
asymmetric key
algorithms. In a
symmetric key algorithm,
the key for encoding and
decoding the message is
same (Yu et al., 2013).
The major benefit of
symmetric key algorithm
is the simplicity in
implementation. In
asymmetric key
CLOUD PRIVACY AND SECURITY
confidential
information within
few moments.
2. Use a Disposable Email
Address: A disposable email
always protects the user
from receiving all sorts of
unsolicited emails from fake
addresses (Wu et al. 2013).
This in turn helps the user to
avoid spam messages.
2. The Department of
Administrative Services
should use a disposable
email address. They will
only have to open their
accounts in that email.
This particular step will
be useful and will secure
the data.
6. Loss of Data in the
Clouds: This is
again a dangerous
and a significant risk
in case of securing
personal
information. While
storing or retrieving
the data in the cloud,
there is always a
high chance that the
data will be lost in
the clouds. Often,
these data cannot be
1. Encryption: Encryption
is the simplest way for
protecting the information
in a particular system
(Srinivasan et al., 2012).
The procedure of enclosing
a confidential text or
message into a typical
cipher text so that the
message is no hacked is
known as encryption. It is
the best technology for
securing any information.
Encryption should be opted
1. Encryption mainly has
two algorithms namely
symmetric key and
asymmetric key
algorithms. In a
symmetric key algorithm,
the key for encoding and
decoding the message is
same (Yu et al., 2013).
The major benefit of
symmetric key algorithm
is the simplicity in
implementation. In
asymmetric key
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16
CLOUD PRIVACY AND SECURITY
retrieved once lost.
This can lead an
organization to a
serious trouble.
by DAS. algorithm, there are two
different keys for
encoding and decoding.
This is complicated than
the symmetric key as two
keys are involved.
2. Passwords: The most
simple and efficient way of
securing any type of
information is keeping
passwords (Chaisiri, Lee &
Niyato, 2012). The
passwords prevent any type
of hacker from intruder in
the cloud. Moreover,
passwords should be
changed or altered
periodically.
2. Passwords are set by
users in any system.
Special characters are
used to set this password.
Only authenticated users
have the right to know the
passwords. Moreover,
they are changed and
altered periodically. This
particular step would be
helpful for DAS.
CLOUD PRIVACY AND SECURITY
retrieved once lost.
This can lead an
organization to a
serious trouble.
by DAS. algorithm, there are two
different keys for
encoding and decoding.
This is complicated than
the symmetric key as two
keys are involved.
2. Passwords: The most
simple and efficient way of
securing any type of
information is keeping
passwords (Chaisiri, Lee &
Niyato, 2012). The
passwords prevent any type
of hacker from intruder in
the cloud. Moreover,
passwords should be
changed or altered
periodically.
2. Passwords are set by
users in any system.
Special characters are
used to set this password.
Only authenticated users
have the right to know the
passwords. Moreover,
they are changed and
altered periodically. This
particular step would be
helpful for DAS.

17
CLOUD PRIVACY AND SECURITY
3. Personal Data Protection Strategies
3.1 Protection of Personal Information
DAS is worried about their security of their personal information. The intruders or the
hackers get easy access to the information if it is not secured. The various ways for protecting the
personal information are as follows:
a) Passwords: The most simple and efficient way of securing any type of information is
keeping passwords. The passwords prevent any type of hacker from intruder in the cloud.
Moreover, passwords should be changed or altered periodically.
b) Secured Browser: A secured browser is also helpful for any type of security of
information. The secured browser prevents or disallows all types of malware and malicious code
in the system and thus personal information is managed easily.
3.2 Authorized Access and Disclosure of Personal Information
Access to the information is the most important factor for any organization. DAS should
restrict the access and disclosure of their information to authorized users only (Ren, Wang &
Wang, 2012). The simplest measures of restricting the access to only authorized users are
passwords, antivirus, access control and firewalls.
3.3 De-Identification of Personal Data
The procedure that restricts an intruder to get the identity of personal data is called the
de-identification of that data (Chen & Zhao, 2012). The simplest measures of preventing an
intruder from getting the identity of personal data are passwords, antivirus, security policies,
access control and firewalls. These measures would help DAS for de-identification of personal
data.
CLOUD PRIVACY AND SECURITY
3. Personal Data Protection Strategies
3.1 Protection of Personal Information
DAS is worried about their security of their personal information. The intruders or the
hackers get easy access to the information if it is not secured. The various ways for protecting the
personal information are as follows:
a) Passwords: The most simple and efficient way of securing any type of information is
keeping passwords. The passwords prevent any type of hacker from intruder in the cloud.
Moreover, passwords should be changed or altered periodically.
b) Secured Browser: A secured browser is also helpful for any type of security of
information. The secured browser prevents or disallows all types of malware and malicious code
in the system and thus personal information is managed easily.
3.2 Authorized Access and Disclosure of Personal Information
Access to the information is the most important factor for any organization. DAS should
restrict the access and disclosure of their information to authorized users only (Ren, Wang &
Wang, 2012). The simplest measures of restricting the access to only authorized users are
passwords, antivirus, access control and firewalls.
3.3 De-Identification of Personal Data
The procedure that restricts an intruder to get the identity of personal data is called the
de-identification of that data (Chen & Zhao, 2012). The simplest measures of preventing an
intruder from getting the identity of personal data are passwords, antivirus, security policies,
access control and firewalls. These measures would help DAS for de-identification of personal
data.

18
CLOUD PRIVACY AND SECURITY
3.4 Use of Personal Digital Identities
The confidential information of a particular organization, which is used for representing a
particular external representative, is called a digital identity (Yang & Jia, 2013). The digital
identity can be anything like an individual or organization. The digital identities have several
benefits. The main benefits of digital identities are as follows:
a) Data Integrity
b) Security
c) Fast
d) Simple
3.5 Security of Personal Data
Security is the principal step in the personal data protection strategy. Leakage of the
personal information is not at all permissible, as the cyber threats are increased (Gupta,
Seetharaman & Raj, 2013). The most efficient ways of securing personal information are
passwords, antivirus, security policies, digital authentication and firewalls.
3.6 Archiving of Personal Data
The final step for this particular strategy is the archiving of personal data. Archiving or
data refer to the storing of that data (Gonzalez et al., 2012). It helps to maintain the integrity and
the confidentiality of personal data. DAS should archive their data in proper way.
CLOUD PRIVACY AND SECURITY
3.4 Use of Personal Digital Identities
The confidential information of a particular organization, which is used for representing a
particular external representative, is called a digital identity (Yang & Jia, 2013). The digital
identity can be anything like an individual or organization. The digital identities have several
benefits. The main benefits of digital identities are as follows:
a) Data Integrity
b) Security
c) Fast
d) Simple
3.5 Security of Personal Data
Security is the principal step in the personal data protection strategy. Leakage of the
personal information is not at all permissible, as the cyber threats are increased (Gupta,
Seetharaman & Raj, 2013). The most efficient ways of securing personal information are
passwords, antivirus, security policies, digital authentication and firewalls.
3.6 Archiving of Personal Data
The final step for this particular strategy is the archiving of personal data. Archiving or
data refer to the storing of that data (Gonzalez et al., 2012). It helps to maintain the integrity and
the confidentiality of personal data. DAS should archive their data in proper way.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
19
CLOUD PRIVACY AND SECURITY
4. Privacy Control Recommendations
S.
No
“Security Risks
(Personal data)”
“Mitigation Plans” “Implementation
Methods”
Student 1 Student ID
1. Loss of storage: The
storage stores or
preserves all the
necessary and
confidential data in a
particular storage
(Beloglazov, Abawaj
& Buyya, 2012). This
storage is extremely
important for any
privacy security
1. Upgrading
Architecture: The storage
should have the best
possible architecture
within it so that there is no
chance of loss of that
storage.
1. The architecture of the
storage can be upgraded by
simply increasing the
budget to a certain level so
that a better storage is
affordable. This up
gradation of architecture
even will help DAS to store
their data fast and with
secured method.
CLOUD PRIVACY AND SECURITY
4. Privacy Control Recommendations
S.
No
“Security Risks
(Personal data)”
“Mitigation Plans” “Implementation
Methods”
Student 1 Student ID
1. Loss of storage: The
storage stores or
preserves all the
necessary and
confidential data in a
particular storage
(Beloglazov, Abawaj
& Buyya, 2012). This
storage is extremely
important for any
privacy security
1. Upgrading
Architecture: The storage
should have the best
possible architecture
within it so that there is no
chance of loss of that
storage.
1. The architecture of the
storage can be upgraded by
simply increasing the
budget to a certain level so
that a better storage is
affordable. This up
gradation of architecture
even will help DAS to store
their data fast and with
secured method.
20
CLOUD PRIVACY AND SECURITY
system. However,
there is always a high
chance of losing or
destruction of that
storage.
2. Maintenance: This is
the second way of
mitigating the risk of loss
of storage in case of data
security (Garg, Versteeg
& Buyya, 2013).
Maintenance should be
done periodically so that
there exists no chance of
loss of storage and thus
data will not be lost.
2. Maintenance is the most
important step for any
device or storage (Wei et
al., 2012). If the storage is
not maintained properly,
there is a high chance that
the storage would be
destructed and the data
would be lost. DAS should
organize a periodic
maintenance so that this
storage is not lost.
CLOUD PRIVACY AND SECURITY
system. However,
there is always a high
chance of losing or
destruction of that
storage.
2. Maintenance: This is
the second way of
mitigating the risk of loss
of storage in case of data
security (Garg, Versteeg
& Buyya, 2013).
Maintenance should be
done periodically so that
there exists no chance of
loss of storage and thus
data will not be lost.
2. Maintenance is the most
important step for any
device or storage (Wei et
al., 2012). If the storage is
not maintained properly,
there is a high chance that
the storage would be
destructed and the data
would be lost. DAS should
organize a periodic
maintenance so that this
storage is not lost.

21
CLOUD PRIVACY AND SECURITY
2. Eavesdropping: This
is one of the most
vulnerable and
dangerous security
threat or risk in case
of information or data
(Gonzalez et al.,
2012). It certainly
means of hearing or
sniffing the data. The
hacker or the intruder
gets into the network
and gets to know all
the confidential
information that is
sent from the sender
to receiver.
1. Encryption: This is
the most basic and simple
way of securing data and
information in the clouds.
Encryption is the process
of encoding a confidential
message or text into a
cipher text in such a way
that only the receiver
would be able to access
that message or text (Wu
et al., 2012). It is
extremely popular for any
organization for securing
their information. DAS
should implement this
security measure.
1. Encryption has two
basic algorithms. The
symmetric key and
asymmetric key algorithms
(Wei et al., 2012).
According to the symmetric
key algorithm, the key that
will open the message is
same as the key that has
encoded the message
(Mishra et al., 2012). The
main advantage of this
algorithm is that t is
extremely simple to
implement. The second
algorithm is the asymmetric
key algorithm, which has
two different keys within it.
This is little complex as
there are two keys involved
in the case. The
implementation is done by
simply following the steps
of the algorithms.
CLOUD PRIVACY AND SECURITY
2. Eavesdropping: This
is one of the most
vulnerable and
dangerous security
threat or risk in case
of information or data
(Gonzalez et al.,
2012). It certainly
means of hearing or
sniffing the data. The
hacker or the intruder
gets into the network
and gets to know all
the confidential
information that is
sent from the sender
to receiver.
1. Encryption: This is
the most basic and simple
way of securing data and
information in the clouds.
Encryption is the process
of encoding a confidential
message or text into a
cipher text in such a way
that only the receiver
would be able to access
that message or text (Wu
et al., 2012). It is
extremely popular for any
organization for securing
their information. DAS
should implement this
security measure.
1. Encryption has two
basic algorithms. The
symmetric key and
asymmetric key algorithms
(Wei et al., 2012).
According to the symmetric
key algorithm, the key that
will open the message is
same as the key that has
encoded the message
(Mishra et al., 2012). The
main advantage of this
algorithm is that t is
extremely simple to
implement. The second
algorithm is the asymmetric
key algorithm, which has
two different keys within it.
This is little complex as
there are two keys involved
in the case. The
implementation is done by
simply following the steps
of the algorithms.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
22
CLOUD PRIVACY AND SECURITY
3. Interception of
Messages: Message
or information is
intercepted easily in
any security system.
The hackers intercept
the data. In most
cases, they even
modify or change the
data completely
before the receiver
receives it.
1. Firewalls: This is the
best way of securing
personal information. The
firewalls act as walls in
case of security (Wu et al.,
2012). They eventually
detect and prevent the
security risks and threats
of the data. The
interception of
information can be
stopped by implementing
firewalls in the system.
1. Firewalls can be easily
implemented in any system
for security. Software is
available for
implementation of firewalls
(Garg, Versteeg & Buyya,
2013). It does not incur any
type of complexities. It can
be easily installed in the
system.
CLOUD PRIVACY AND SECURITY
3. Interception of
Messages: Message
or information is
intercepted easily in
any security system.
The hackers intercept
the data. In most
cases, they even
modify or change the
data completely
before the receiver
receives it.
1. Firewalls: This is the
best way of securing
personal information. The
firewalls act as walls in
case of security (Wu et al.,
2012). They eventually
detect and prevent the
security risks and threats
of the data. The
interception of
information can be
stopped by implementing
firewalls in the system.
1. Firewalls can be easily
implemented in any system
for security. Software is
available for
implementation of firewalls
(Garg, Versteeg & Buyya,
2013). It does not incur any
type of complexities. It can
be easily installed in the
system.

23
CLOUD PRIVACY AND SECURITY
2. Encryption: This is
the most basic and simple
way of securing data and
information from
interception (Mishra et al.,
2012). Encryption is the
process of encoding a
confidential message or
text into a cipher text in
such a way that only the
receiver would be able to
access that message or
text. It is extremely
popular for any
organization for securing
their information. DAS
should implement this
security measure.
1. Encryption has two
basic algorithms. The
symmetric key and
asymmetric key algorithms.
According to the symmetric
key algorithm, the key that
will open the message is
same as the key that has
encoded the message. The
main advantage of this
algorithm is that t is
extremely simple to
implement (Bonomi et al.,
2012). The second
algorithm is the asymmetric
key algorithm, which has
two different keys within it.
This is little complex as
there are two keys involved
in the case. The
implementation is done by
simply following the steps
of the algorithms.
CLOUD PRIVACY AND SECURITY
2. Encryption: This is
the most basic and simple
way of securing data and
information from
interception (Mishra et al.,
2012). Encryption is the
process of encoding a
confidential message or
text into a cipher text in
such a way that only the
receiver would be able to
access that message or
text. It is extremely
popular for any
organization for securing
their information. DAS
should implement this
security measure.
1. Encryption has two
basic algorithms. The
symmetric key and
asymmetric key algorithms.
According to the symmetric
key algorithm, the key that
will open the message is
same as the key that has
encoded the message. The
main advantage of this
algorithm is that t is
extremely simple to
implement (Bonomi et al.,
2012). The second
algorithm is the asymmetric
key algorithm, which has
two different keys within it.
This is little complex as
there are two keys involved
in the case. The
implementation is done by
simply following the steps
of the algorithms.
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




