Introduction to Risk and Due Diligence
VerifiedAdded on 2022/11/01
|12
|3152
|385
AI Summary
This document provides an introduction to vulnerability assessment and precautionary analysis for Tech Enterprise Company. It identifies critical vulnerabilities and recommends measures to protect assets from possible risks. The document also provides expert guidance on Desklib.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

1
INTRODUCTION TO RISK AND DUE DILIGENCE
By
Name
Professor’s Name
Course Number
University/College
City
Date
INTRODUCTION TO RISK AND DUE DILIGENCE
By
Name
Professor’s Name
Course Number
University/College
City
Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2
Part 1: Vulnerability Assessment
Introduction
One of the business interests of Tech Enterprise is dealing in application software which it sells
to other companies for commercial use. As a member of the business, one needs to be concerned
with the possible threats to which the company is exposed to. Identification of the possible
threats as well as a better understanding of such risks requires one to carry out vulnerability
assessment alongside other techniques to detect the vulnerabilities(Krisher et al., 2015). Through
the vulnerability assessment (VA), the Tech Enterprise Company will enhance awareness of its
environment thereby facilitating quick response and mitigation of threats. Similarly, a
comprehensive VA technique will enhance knowledge within the organization as well as the
awareness of the risk background to create a deeper understanding of the threats within the
environment
Assets relevant for the Tech Enterprise Company
The major assets that are useful to the company include computer software which is regarded as
a long-term asset and a fixed asset, hardware and software assets, property, plant and equipment
assets. These assets would be important for these organization and they have been selected
because they have been acquired and intended to be sold for ordinary course of operations.
Besides, the use of the assets are projected for a span of 2 years and more, and they have been
acquired and constructed with an aim of being used by the organization(Kotleret al., 2016).
Nevertheless, the Tech Enterprise Company is projected to capitalize on the cost of the software
especially when such software meets the standards and criteria for general plant, property, and
equipment. Within the company, general PP and E are considered as assets used in provision of
Part 1: Vulnerability Assessment
Introduction
One of the business interests of Tech Enterprise is dealing in application software which it sells
to other companies for commercial use. As a member of the business, one needs to be concerned
with the possible threats to which the company is exposed to. Identification of the possible
threats as well as a better understanding of such risks requires one to carry out vulnerability
assessment alongside other techniques to detect the vulnerabilities(Krisher et al., 2015). Through
the vulnerability assessment (VA), the Tech Enterprise Company will enhance awareness of its
environment thereby facilitating quick response and mitigation of threats. Similarly, a
comprehensive VA technique will enhance knowledge within the organization as well as the
awareness of the risk background to create a deeper understanding of the threats within the
environment
Assets relevant for the Tech Enterprise Company
The major assets that are useful to the company include computer software which is regarded as
a long-term asset and a fixed asset, hardware and software assets, property, plant and equipment
assets. These assets would be important for these organization and they have been selected
because they have been acquired and intended to be sold for ordinary course of operations.
Besides, the use of the assets are projected for a span of 2 years and more, and they have been
acquired and constructed with an aim of being used by the organization(Kotleret al., 2016).
Nevertheless, the Tech Enterprise Company is projected to capitalize on the cost of the software
especially when such software meets the standards and criteria for general plant, property, and
equipment. Within the company, general PP and E are considered as assets used in provision of

3
goods and services since the company deals in application software sold to other companies for
commercial use (Krisher et al., 2015).
Notably, for the VA to be effective for the company, four steps are key after the identification of
the assets which have consisted of hardware and software assets as provided by the nature of the
business. Subsequently the second step would employ the ascertaining of the quantifiable value
of the assets while the third step will be identification of the security techniques to the
vulnerabilities influencing the assets (Williams, Dabirsiaghi& Contrast Security, 2016).
Moreover, determination of the quantifiable risks and threats scores for eachvulnerability is
another important step in the VA. Finally, the mitigations for the risk vulnerability from the
assets provide an opportunity for putting in place mechanisms for dealing with the
risks(Krisheret al., 2015).
One of the most effective methods for the selection of the threats is the information gathering
and discovery (Ali &Awad, 2018). In this phase, the organization will conduct information
gathering and discovery approaches with an objective of establishing a better understanding of
the hardware and software assets present within the organization as well as the surrounding
environment. This phase incorporates techniques such as port scanning which is essential in the
discovery of services and protocols that are prone to vulnerability and network scanning, key in
discovering the hosts. Also the phase involves a review of the directory service and DNS
information to facilitate understanding of the hosts which might be targeted by the
attackers(Kotleret al., 2016).
In the events the assessment process has achieved a full discovery effort to understand the hosts
within the business environment, a subsequent thorough analysis and enumeration of the
operating systems, ports, services offered by the organization, protocols, applications and
goods and services since the company deals in application software sold to other companies for
commercial use (Krisher et al., 2015).
Notably, for the VA to be effective for the company, four steps are key after the identification of
the assets which have consisted of hardware and software assets as provided by the nature of the
business. Subsequently the second step would employ the ascertaining of the quantifiable value
of the assets while the third step will be identification of the security techniques to the
vulnerabilities influencing the assets (Williams, Dabirsiaghi& Contrast Security, 2016).
Moreover, determination of the quantifiable risks and threats scores for eachvulnerability is
another important step in the VA. Finally, the mitigations for the risk vulnerability from the
assets provide an opportunity for putting in place mechanisms for dealing with the
risks(Krisheret al., 2015).
One of the most effective methods for the selection of the threats is the information gathering
and discovery (Ali &Awad, 2018). In this phase, the organization will conduct information
gathering and discovery approaches with an objective of establishing a better understanding of
the hardware and software assets present within the organization as well as the surrounding
environment. This phase incorporates techniques such as port scanning which is essential in the
discovery of services and protocols that are prone to vulnerability and network scanning, key in
discovering the hosts. Also the phase involves a review of the directory service and DNS
information to facilitate understanding of the hosts which might be targeted by the
attackers(Kotleret al., 2016).
In the events the assessment process has achieved a full discovery effort to understand the hosts
within the business environment, a subsequent thorough analysis and enumeration of the
operating systems, ports, services offered by the organization, protocols, applications and

4
operating systems is conducted. This analysis is essential in determining the extent of the
possible attack environment that the company is vulnerable to in terms of risks and threats.
Furthermore, this phase is important in the determination of the version of details and
information that assets within the organization meet since subsequent versions tend to patch old
vulnerabilities hence prompting introduction of new ones. The final phase of VA is the detection
and reporting. This phase incorporates actual detection of the vulnerabilities, use of the detection
tool and vulnerability storehouse like National Vulnerability Database(Wysopal, et al 2019). The
storehouse is important in identification of the vulnerabilities on the assets present within the
organization and through this process, reports are established which are complete with scores as
well as risk information. Consequently, a remediation or mitigation tools are used to reinforce
and configure the assets and this is necessary to eliminate the security risks existing as a result of
the vulnerabilities identified.
The Critical Vulnerabilities
With a successful VA process, the major critical vulnerabilities that the Tech Enterprise
Company is mostly exposed to include download of codes without adequate integrity checks, use
of broken algorithms, bugs, use of software that is infected with a virus, buffer overflow, missing
authentications for key functions within the organization, unrestricted and uncontrolled upload of
unsafe files, and missing data encryption. Other vulnerabilities also include over-dependence on
entrusted and unverified inputs in security measures, weak passwords, missing authorization,
path traversal, and SQL injection, URL redirection on unverified sites, cross-site scripting and
forgery (Wysopalet al., 2019).
SQL likely to be used by the company to store website data is prone to a lot of network security
threats. This is because most of the threats associated with the system have advanced resulting to
operating systems is conducted. This analysis is essential in determining the extent of the
possible attack environment that the company is vulnerable to in terms of risks and threats.
Furthermore, this phase is important in the determination of the version of details and
information that assets within the organization meet since subsequent versions tend to patch old
vulnerabilities hence prompting introduction of new ones. The final phase of VA is the detection
and reporting. This phase incorporates actual detection of the vulnerabilities, use of the detection
tool and vulnerability storehouse like National Vulnerability Database(Wysopal, et al 2019). The
storehouse is important in identification of the vulnerabilities on the assets present within the
organization and through this process, reports are established which are complete with scores as
well as risk information. Consequently, a remediation or mitigation tools are used to reinforce
and configure the assets and this is necessary to eliminate the security risks existing as a result of
the vulnerabilities identified.
The Critical Vulnerabilities
With a successful VA process, the major critical vulnerabilities that the Tech Enterprise
Company is mostly exposed to include download of codes without adequate integrity checks, use
of broken algorithms, bugs, use of software that is infected with a virus, buffer overflow, missing
authentications for key functions within the organization, unrestricted and uncontrolled upload of
unsafe files, and missing data encryption. Other vulnerabilities also include over-dependence on
entrusted and unverified inputs in security measures, weak passwords, missing authorization,
path traversal, and SQL injection, URL redirection on unverified sites, cross-site scripting and
forgery (Wysopalet al., 2019).
SQL likely to be used by the company to store website data is prone to a lot of network security
threats. This is because most of the threats associated with the system have advanced resulting to
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

5
serious SQL injection risks and attacks. Nevertheless, the attacks are mostly designed to affect
the data dependent applications by attacking the security vulnerabilities within the application’s
software that is majorly used by the company and sold to other organizations for commercial use.
This stands as one of the major risks for the Tech Enterprise Company since it affects its major
services directly(Hugard et al., 2016). The attackers use venomous codes to acquire private data
stored by the organization. They then change and to some extent destroy the data which has a
major implication on the transactions on the website for the company.
Part 2: Precautionary Analysis
Before the recommendation of the relevant measures to protect the assets from the possible risks
as a result of the vulnerabilities, the risk analysis process is undertaken. The risk analysis process
will enable Tech Enterprise Company to identify the information about the assets at risks and
consequently attach the matching values to the risks. Furthermore, the process will enhance
identification of protective strategies with aims of minimizing the effects of the threats
associated with the identified vulnerabilities. Most importantly, the risk analysis process would
help ascertain if the recommendations are effective(Reybok et al., 2017).
The precautionary analysis process would give the management of the Tech Enterprise Company
the information required to make educated and informed judgment pertaining to the information
security. The analysis procedure identifies the already existing security management measures,
the calculated vulnerabilities, alongside assessing the impacts of the threats on each vulnerability
identified (Goel, &Mehtre, 2015). Security policy moreover, requires the establishment of a
continuous information management planning process that incorporates planning for the security
of each assets of the Tech Enterprise Company. Risk management and precautionary analysis
would assist the company maintain an acceptable information system and security framework.
serious SQL injection risks and attacks. Nevertheless, the attacks are mostly designed to affect
the data dependent applications by attacking the security vulnerabilities within the application’s
software that is majorly used by the company and sold to other organizations for commercial use.
This stands as one of the major risks for the Tech Enterprise Company since it affects its major
services directly(Hugard et al., 2016). The attackers use venomous codes to acquire private data
stored by the organization. They then change and to some extent destroy the data which has a
major implication on the transactions on the website for the company.
Part 2: Precautionary Analysis
Before the recommendation of the relevant measures to protect the assets from the possible risks
as a result of the vulnerabilities, the risk analysis process is undertaken. The risk analysis process
will enable Tech Enterprise Company to identify the information about the assets at risks and
consequently attach the matching values to the risks. Furthermore, the process will enhance
identification of protective strategies with aims of minimizing the effects of the threats
associated with the identified vulnerabilities. Most importantly, the risk analysis process would
help ascertain if the recommendations are effective(Reybok et al., 2017).
The precautionary analysis process would give the management of the Tech Enterprise Company
the information required to make educated and informed judgment pertaining to the information
security. The analysis procedure identifies the already existing security management measures,
the calculated vulnerabilities, alongside assessing the impacts of the threats on each vulnerability
identified (Goel, &Mehtre, 2015). Security policy moreover, requires the establishment of a
continuous information management planning process that incorporates planning for the security
of each assets of the Tech Enterprise Company. Risk management and precautionary analysis
would assist the company maintain an acceptable information system and security framework.

6
Baseline reporting is one of the precautionary techniquesthat can be used by the company to
guide the process of establishing recommendations for the identified vulnerabilities. Through the
technique, the management can record system’s baseline such as the system facts and how it
operates and performs under normal working conditions (Kotleret al., 2016). It can then be
compared to the current performance data. To avoid SQL injection for instance, it is
recommended that the code be reviewed. Reviewing of the code would facilitate observation of
all written codes to ascertain the present loopholes within the system (Czarny et al., 2017).
Moreover, the review can also assess the changes in code occurring within different points in
time. Subsequently, the code can be examined while at the same time errors in logic and flaws in
programming are identified since they are responsible for improper coding and SQL injection as
well as cross-site forgery (Reybok et al., 2017).
Furthermore, identification of the attack surface system is another recommendation for
addressing the vulnerabilities. This method is termed as attack surface reduction and is targeted
at minimizing the possibilities and probability of exploitation by the potential damage (Yang,
Zhou, Ren, & Liu, 2018). This method incorporates installed applications, protocols and services
that are set for the users who are authorized. Since the larger the surface and exposure to the
outside the more vulnerable the system hence the method reduces the size of the exposure and
attack surface(Hugard et al., 2016). The attack surface is also reduced by removing the unwanted
software services. Nevertheless, it can also be reduced by a number of techniques such as
addition of authentication, reduction of privileges and turning off unwanted functions.
Another important recommendation for the Tech Enterprise Company is to review the system’s
architecture to enhance the assessment of the security of the assets and the network system. With
the architectural approach, a control framework can be employed to examine the foundational
Baseline reporting is one of the precautionary techniquesthat can be used by the company to
guide the process of establishing recommendations for the identified vulnerabilities. Through the
technique, the management can record system’s baseline such as the system facts and how it
operates and performs under normal working conditions (Kotleret al., 2016). It can then be
compared to the current performance data. To avoid SQL injection for instance, it is
recommended that the code be reviewed. Reviewing of the code would facilitate observation of
all written codes to ascertain the present loopholes within the system (Czarny et al., 2017).
Moreover, the review can also assess the changes in code occurring within different points in
time. Subsequently, the code can be examined while at the same time errors in logic and flaws in
programming are identified since they are responsible for improper coding and SQL injection as
well as cross-site forgery (Reybok et al., 2017).
Furthermore, identification of the attack surface system is another recommendation for
addressing the vulnerabilities. This method is termed as attack surface reduction and is targeted
at minimizing the possibilities and probability of exploitation by the potential damage (Yang,
Zhou, Ren, & Liu, 2018). This method incorporates installed applications, protocols and services
that are set for the users who are authorized. Since the larger the surface and exposure to the
outside the more vulnerable the system hence the method reduces the size of the exposure and
attack surface(Hugard et al., 2016). The attack surface is also reduced by removing the unwanted
software services. Nevertheless, it can also be reduced by a number of techniques such as
addition of authentication, reduction of privileges and turning off unwanted functions.
Another important recommendation for the Tech Enterprise Company is to review the system’s
architecture to enhance the assessment of the security of the assets and the network system. With
the architectural approach, a control framework can be employed to examine the foundational

7
infrastructure in aspects of its resistance to unauthorized entries. Consequently, the measure
would be effective in strengthening crime prevention via the environmental design.
Environmental design works by motivating designers thereby boosting the security system
(Cabrera, 2018). One of the advantages of this method is that it is compliant to the security
regulatory standards as provided for by international organization for standardization. Another
recommendation would be the use the three-ring architecture of computer processors. This
approach is the key in executing applications.
System monitoring is another recommended measure to minimize the risks. It can be
done by software designed for the purpose or by security analysis. Monitoring a system factors in
several parts of the system as well as searching for any anomalies. Monitoring the system should
be done on a regular basis for the technique to be effective (Roytman, Bellis, &Heuer, 2016).
When the system is monitored regularly through a well-designed interval, it can enhance a
continuous vigil observation of the system. By monitoring the system security violation can be
detected in good time to enable speedy reaction.
Setting surveillance is also an important recommendation for the Tech Enterprise
Company. Surveillance is important for the physical security of the company as whole hence
security of the assets is also guaranteed. For instance, locking the door to the server room is
critical step in eliminating unauthorized access and misuse of the assets within the company.
Contingency planning is another important recommendation for the company to help in reducing
the impacts associated with the identified vulnerabilities (Hugard et al., 2016). It includes
procedures and steps targeted at recovering the losses are a result of temporary outages and
major disasters. For example, onsite back up is employed to ensure availability of the existing
current data machine and the production area in the event that the operating system lost,
infrastructure in aspects of its resistance to unauthorized entries. Consequently, the measure
would be effective in strengthening crime prevention via the environmental design.
Environmental design works by motivating designers thereby boosting the security system
(Cabrera, 2018). One of the advantages of this method is that it is compliant to the security
regulatory standards as provided for by international organization for standardization. Another
recommendation would be the use the three-ring architecture of computer processors. This
approach is the key in executing applications.
System monitoring is another recommended measure to minimize the risks. It can be
done by software designed for the purpose or by security analysis. Monitoring a system factors in
several parts of the system as well as searching for any anomalies. Monitoring the system should
be done on a regular basis for the technique to be effective (Roytman, Bellis, &Heuer, 2016).
When the system is monitored regularly through a well-designed interval, it can enhance a
continuous vigil observation of the system. By monitoring the system security violation can be
detected in good time to enable speedy reaction.
Setting surveillance is also an important recommendation for the Tech Enterprise
Company. Surveillance is important for the physical security of the company as whole hence
security of the assets is also guaranteed. For instance, locking the door to the server room is
critical step in eliminating unauthorized access and misuse of the assets within the company.
Contingency planning is another important recommendation for the company to help in reducing
the impacts associated with the identified vulnerabilities (Hugard et al., 2016). It includes
procedures and steps targeted at recovering the losses are a result of temporary outages and
major disasters. For example, onsite back up is employed to ensure availability of the existing
current data machine and the production area in the event that the operating system lost,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
corrupted or damaged. The method is convenient and prevents the organization to resort to re-
entry of the data from the source material. Similarly, offsite backup and storage encompasses the
same principle for physical security system however, they are designed for longer-term
protection in a sterile environment (Ma, 2018). When offsite security measures are employed
within the organization, there will less need of frequent updating and it will also provide
additional protection against the risks that could damage the data stored. Backing up of the data
and software essential for the operation of the company is a key recommendation. The process of
backing up the data can be initiated by the implementation of the security control over the
backup resources.
Conclusion
Vulnerability assessment is a wider operation and process that involves security control measures
and the use of both technical and non-technical methods. Technical approaches incorporate
measures targeted the safety of the assets such as software, hardware and firmware. Most of the
technical methods involve access control strategies, identification and authentication of measures
put in place and encryption methods. Intrusion detection of the software is also an approach in
technical control methods. On the other hand, non-technical controls as security measures factors
in operational managements such as operational procedures, environmental security and security
policies.
corrupted or damaged. The method is convenient and prevents the organization to resort to re-
entry of the data from the source material. Similarly, offsite backup and storage encompasses the
same principle for physical security system however, they are designed for longer-term
protection in a sterile environment (Ma, 2018). When offsite security measures are employed
within the organization, there will less need of frequent updating and it will also provide
additional protection against the risks that could damage the data stored. Backing up of the data
and software essential for the operation of the company is a key recommendation. The process of
backing up the data can be initiated by the implementation of the security control over the
backup resources.
Conclusion
Vulnerability assessment is a wider operation and process that involves security control measures
and the use of both technical and non-technical methods. Technical approaches incorporate
measures targeted the safety of the assets such as software, hardware and firmware. Most of the
technical methods involve access control strategies, identification and authentication of measures
put in place and encryption methods. Intrusion detection of the software is also an approach in
technical control methods. On the other hand, non-technical controls as security measures factors
in operational managements such as operational procedures, environmental security and security
policies.

9
References
Ali, B. and Awad, A., 2018. Cyber and physical security vulnerability assessment for IoT-based
smart homes. Sensors, 18(3), p.817.doi.org/10.3390/s18030817
Cabrera, G.A., 2018. The Use of Computer Applications in Qualitative Research: A
Review. Asia Pacific Journal of Academic Research in Social Sciences, 3.
Czarny, B., Mo, J., Rezafard, A. and Patt, D.M., OPSWAT, Inc., 2017. Computer security
vulnerability assessment.U.S. Patent 9,749,349.
Goel, J.N. and Mehtre, B.M., 2015. Vulnerability assessment & penetration testing as a cyber
defence technology. Procedia Computer Science, 57, pp.710-
715.doi.org/10.1016/j.procs.2015.07.458
Hugard IV, J.M., Leroux, A.L., Mallabarapu, C., Muniz, J.A., Russell, B.C. and Wu, Z., McAfee
LLC, 2017. System and method for grouping computer vulnerabilities.U.S. Patent 9,811,667.
Kotler, I., Livni, I., Bar-Shalom, D. and Bejerano, G., SafeBreach Ltd., 2016.System and method
for securing a computer system against malicious actions by utilizing virtualized elements. U.S.
Patent 9,473,522.
Krisher, M., Bellis, E.T. and Heuer, J., Risk I/O Inc, 2015. Ordered computer vulnerability
remediation reporting.U.S. Patent 8,984,643.
Ma, L.J., 2018, July.A Brief Analysis of Database Security Policy.In 2018 3rd International
Conference on Education, Sports, Arts and Management Engineering (ICESAME 2018).Atlantis
Press.
doi.org/10.2991/icesame-18.2018.82
References
Ali, B. and Awad, A., 2018. Cyber and physical security vulnerability assessment for IoT-based
smart homes. Sensors, 18(3), p.817.doi.org/10.3390/s18030817
Cabrera, G.A., 2018. The Use of Computer Applications in Qualitative Research: A
Review. Asia Pacific Journal of Academic Research in Social Sciences, 3.
Czarny, B., Mo, J., Rezafard, A. and Patt, D.M., OPSWAT, Inc., 2017. Computer security
vulnerability assessment.U.S. Patent 9,749,349.
Goel, J.N. and Mehtre, B.M., 2015. Vulnerability assessment & penetration testing as a cyber
defence technology. Procedia Computer Science, 57, pp.710-
715.doi.org/10.1016/j.procs.2015.07.458
Hugard IV, J.M., Leroux, A.L., Mallabarapu, C., Muniz, J.A., Russell, B.C. and Wu, Z., McAfee
LLC, 2017. System and method for grouping computer vulnerabilities.U.S. Patent 9,811,667.
Kotler, I., Livni, I., Bar-Shalom, D. and Bejerano, G., SafeBreach Ltd., 2016.System and method
for securing a computer system against malicious actions by utilizing virtualized elements. U.S.
Patent 9,473,522.
Krisher, M., Bellis, E.T. and Heuer, J., Risk I/O Inc, 2015. Ordered computer vulnerability
remediation reporting.U.S. Patent 8,984,643.
Ma, L.J., 2018, July.A Brief Analysis of Database Security Policy.In 2018 3rd International
Conference on Education, Sports, Arts and Management Engineering (ICESAME 2018).Atlantis
Press.
doi.org/10.2991/icesame-18.2018.82

10
Reybok, R., Rhines, J., Zettel, I.K.J. and Geddes, H., ServiceNowInc, 2017. Computer Network
Threat Assessment. U.S. Patent Application 15/373,662.
Roytman, M., Bellis, E.T. and Heuer, J., Risk I/O Inc, 2016. Identifying vulnerabilities of
computing assets based on breach data. U.S. Patent 9,270,695.
Williams, J. and Dabirsiaghi, A., Contrast Security, LLC, 2016. Detection of vulnerabilities in
computer systems.U.S. Patent 9,268,945.
Wysopal, C.J., Eng, C.J. and Moynahan, M.P., VeracodeInc, 2019.Assessment and analysis of
software security flaws. U.S. Patent Application 10/275,600.
Yang, X., Zhou, S., Ren, G. and Liu, Y., 2018.Computer network attack and defense
technology. Information and Computer Security, 1(1).
Reybok, R., Rhines, J., Zettel, I.K.J. and Geddes, H., ServiceNowInc, 2017. Computer Network
Threat Assessment. U.S. Patent Application 15/373,662.
Roytman, M., Bellis, E.T. and Heuer, J., Risk I/O Inc, 2016. Identifying vulnerabilities of
computing assets based on breach data. U.S. Patent 9,270,695.
Williams, J. and Dabirsiaghi, A., Contrast Security, LLC, 2016. Detection of vulnerabilities in
computer systems.U.S. Patent 9,268,945.
Wysopal, C.J., Eng, C.J. and Moynahan, M.P., VeracodeInc, 2019.Assessment and analysis of
software security flaws. U.S. Patent Application 10/275,600.
Yang, X., Zhou, S., Ren, G. and Liu, Y., 2018.Computer network attack and defense
technology. Information and Computer Security, 1(1).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
11
Appendix
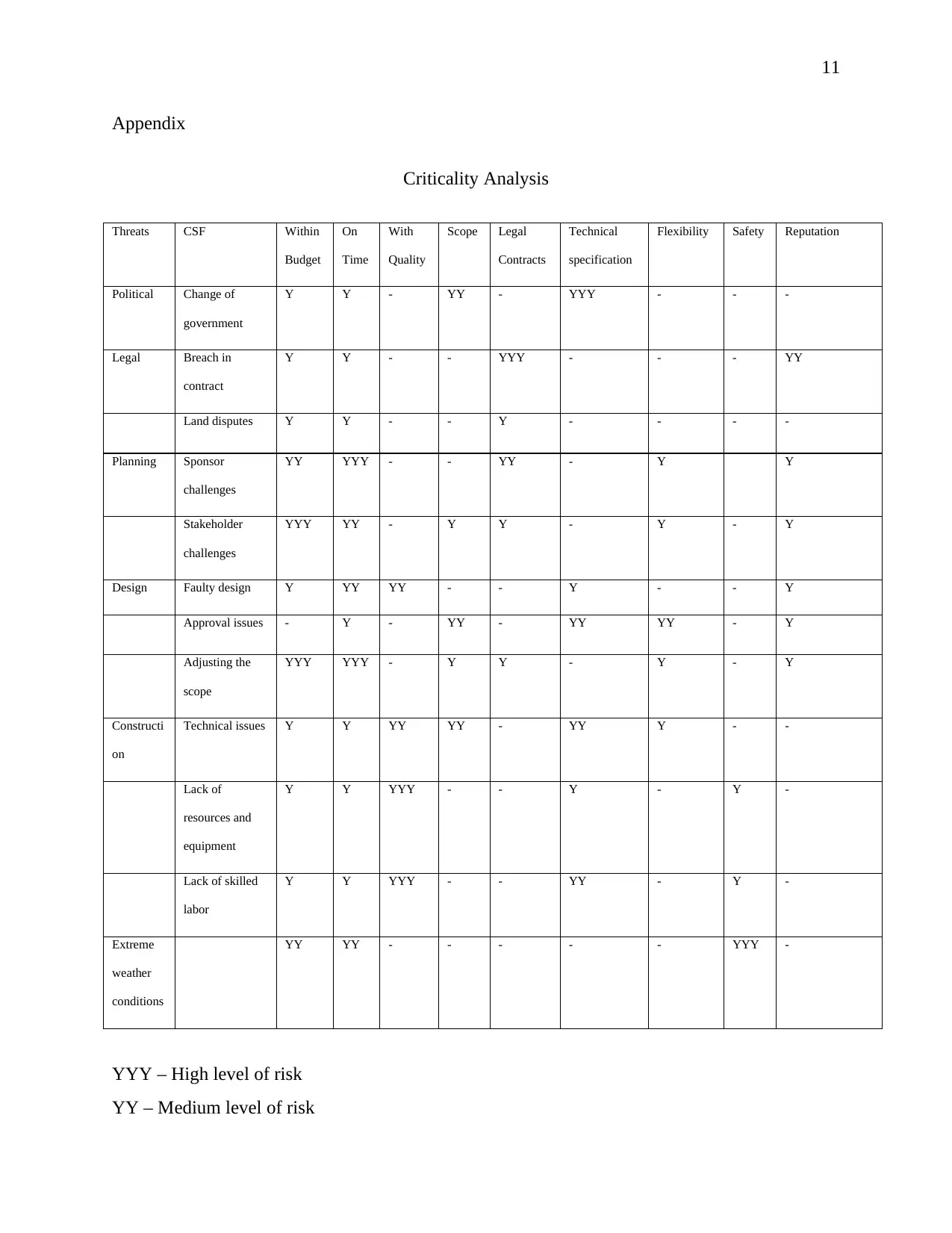
Criticality Analysis
Threats CSF Within
Budget
On
Time
With
Quality
Scope Legal
Contracts
Technical
specification
Flexibility Safety Reputation
Political Change of
government
Y Y - YY - YYY - - -
Legal Breach in
contract
Y Y - - YYY - - - YY
Land disputes Y Y - - Y - - - -
Planning Sponsor
challenges
YY YYY - - YY - Y Y
Stakeholder
challenges
YYY YY - Y Y - Y - Y
Design Faulty design Y YY YY - - Y - - Y
Approval issues - Y - YY - YY YY - Y
Adjusting the
scope
YYY YYY - Y Y - Y - Y
Constructi
on
Technical issues Y Y YY YY - YY Y - -
Lack of
resources and
equipment
Y Y YYY - - Y - Y -
Lack of skilled
labor
Y Y YYY - - YY - Y -
Extreme
weather
conditions
YY YY - - - - - YYY -
YYY – High level of risk
YY – Medium level of risk
Appendix
Criticality Analysis
Threats CSF Within
Budget
On
Time
With
Quality
Scope Legal
Contracts
Technical
specification
Flexibility Safety Reputation
Political Change of
government
Y Y - YY - YYY - - -
Legal Breach in
contract
Y Y - - YYY - - - YY
Land disputes Y Y - - Y - - - -
Planning Sponsor
challenges
YY YYY - - YY - Y Y
Stakeholder
challenges
YYY YY - Y Y - Y - Y
Design Faulty design Y YY YY - - Y - - Y
Approval issues - Y - YY - YY YY - Y
Adjusting the
scope
YYY YYY - Y Y - Y - Y
Constructi
on
Technical issues Y Y YY YY - YY Y - -
Lack of
resources and
equipment
Y Y YYY - - Y - Y -
Lack of skilled
labor
Y Y YYY - - YY - Y -
Extreme
weather
conditions
YY YY - - - - - YYY -
YYY – High level of risk
YY – Medium level of risk
12
Y –Low level of risk
(-) – Negligible risk
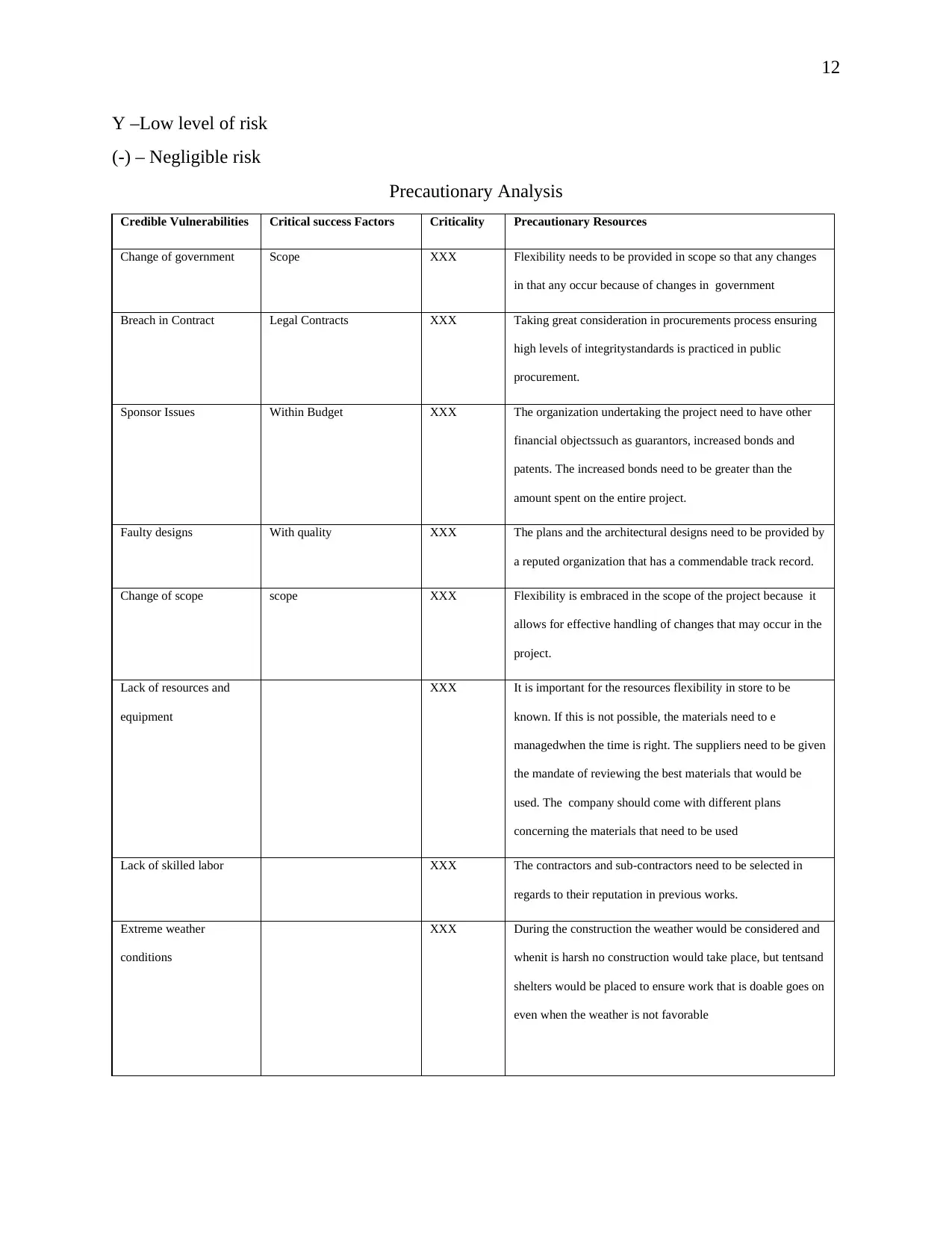
Precautionary Analysis
Credible Vulnerabilities Critical success Factors Criticality Precautionary Resources
Change of government Scope XXX Flexibility needs to be provided in scope so that any changes
in that any occur because of changes in government
Breach in Contract Legal Contracts XXX Taking great consideration in procurements process ensuring
high levels of integritystandards is practiced in public
procurement.
Sponsor Issues Within Budget XXX The organization undertaking the project need to have other
financial objectssuch as guarantors, increased bonds and
patents. The increased bonds need to be greater than the
amount spent on the entire project.
Faulty designs With quality XXX The plans and the architectural designs need to be provided by
a reputed organization that has a commendable track record.
Change of scope scope XXX Flexibility is embraced in the scope of the project because it
allows for effective handling of changes that may occur in the
project.
Lack of resources and
equipment
XXX It is important for the resources flexibility in store to be
known. If this is not possible, the materials need to e
managedwhen the time is right. The suppliers need to be given
the mandate of reviewing the best materials that would be
used. The company should come with different plans
concerning the materials that need to be used
Lack of skilled labor XXX The contractors and sub-contractors need to be selected in
regards to their reputation in previous works.
Extreme weather
conditions
XXX During the construction the weather would be considered and
whenit is harsh no construction would take place, but tentsand
shelters would be placed to ensure work that is doable goes on
even when the weather is not favorable
Y –Low level of risk
(-) – Negligible risk
Precautionary Analysis
Credible Vulnerabilities Critical success Factors Criticality Precautionary Resources
Change of government Scope XXX Flexibility needs to be provided in scope so that any changes
in that any occur because of changes in government
Breach in Contract Legal Contracts XXX Taking great consideration in procurements process ensuring
high levels of integritystandards is practiced in public
procurement.
Sponsor Issues Within Budget XXX The organization undertaking the project need to have other
financial objectssuch as guarantors, increased bonds and
patents. The increased bonds need to be greater than the
amount spent on the entire project.
Faulty designs With quality XXX The plans and the architectural designs need to be provided by
a reputed organization that has a commendable track record.
Change of scope scope XXX Flexibility is embraced in the scope of the project because it
allows for effective handling of changes that may occur in the
project.
Lack of resources and
equipment
XXX It is important for the resources flexibility in store to be
known. If this is not possible, the materials need to e
managedwhen the time is right. The suppliers need to be given
the mandate of reviewing the best materials that would be
used. The company should come with different plans
concerning the materials that need to be used
Lack of skilled labor XXX The contractors and sub-contractors need to be selected in
regards to their reputation in previous works.
Extreme weather
conditions
XXX During the construction the weather would be considered and
whenit is harsh no construction would take place, but tentsand
shelters would be placed to ensure work that is doable goes on
even when the weather is not favorable
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





