Impact of Computer Organization and Operating System, Networking and Internet Security on IT Company
VerifiedAdded on 2023/03/31
|19
|3716
|376
AI Summary
This report discusses the impact of computer organization and operating system, networking and internet security on an IT company. It covers the advantages and disadvantages of different architectures, protocols, and security measures. The report also includes a case study of EE Limited.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
Computer Network
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Task 1 Evaluation Report.................................................................................................................3
Abstract............................................................................................................................................3
Background......................................................................................................................................3
Advantages and disadvantages .......................................................................................................5
Legal and Ethical ............................................................................................................................6
Conclusion.......................................................................................................................................7
Task 3.............................................................................................................................................14
Portfolio (computer organization and operating system)...............................................................14
Introduction....................................................................................................................................14
Analysis..........................................................................................................................................14
Conclusion.....................................................................................................................................15
Portfolio (Networking and Internet Security)................................................................................16
Introduction....................................................................................................................................16
Analysis..........................................................................................................................................16
Conclusion.....................................................................................................................................17
References......................................................................................................................................18
Task 1 Evaluation Report.................................................................................................................3
Abstract............................................................................................................................................3
Background......................................................................................................................................3
Advantages and disadvantages .......................................................................................................5
Legal and Ethical ............................................................................................................................6
Conclusion.......................................................................................................................................7
Task 3.............................................................................................................................................14
Portfolio (computer organization and operating system)...............................................................14
Introduction....................................................................................................................................14
Analysis..........................................................................................................................................14
Conclusion.....................................................................................................................................15
Portfolio (Networking and Internet Security)................................................................................16
Introduction....................................................................................................................................16
Analysis..........................................................................................................................................16
Conclusion.....................................................................................................................................17
References......................................................................................................................................18

Task 1 Evaluation Report
Abstract
In this the report impact of computer organization and operating system, networking and
internet security on any IT company which analysis the process and the flow of data and
instructions on the basis of architecture. And various hierarchical systems are considered that
helps us in modulating the software system into logical fragments that helps us in identifying the
hierarchic architecture style of the software in which different process uses different approaches
such as in main-subroutine the software is divided in to fragments, in master-slave divide and
conquer asspproach is used where in virtual machine a virtual system is created by the software.
In networking various networking protocols are used that helps in communicating or share the
information with the system (Bhuyan, and Agrawal, 1984). This can also be used for resource
sharing purpose. It provides lots of protocols for the transferring the files from source to
destination with guarantee and many other protocols are provides that can helps in uploading and
downloading the mails. And internet security in which security is provided during internet
browsing, online banking transaction, while uploading and downloading the files. Because
during this period various threats such as virus, worms, trojan harms may damage your data and
corrupt your file. And may cause the situation where data loss takes place.
Background
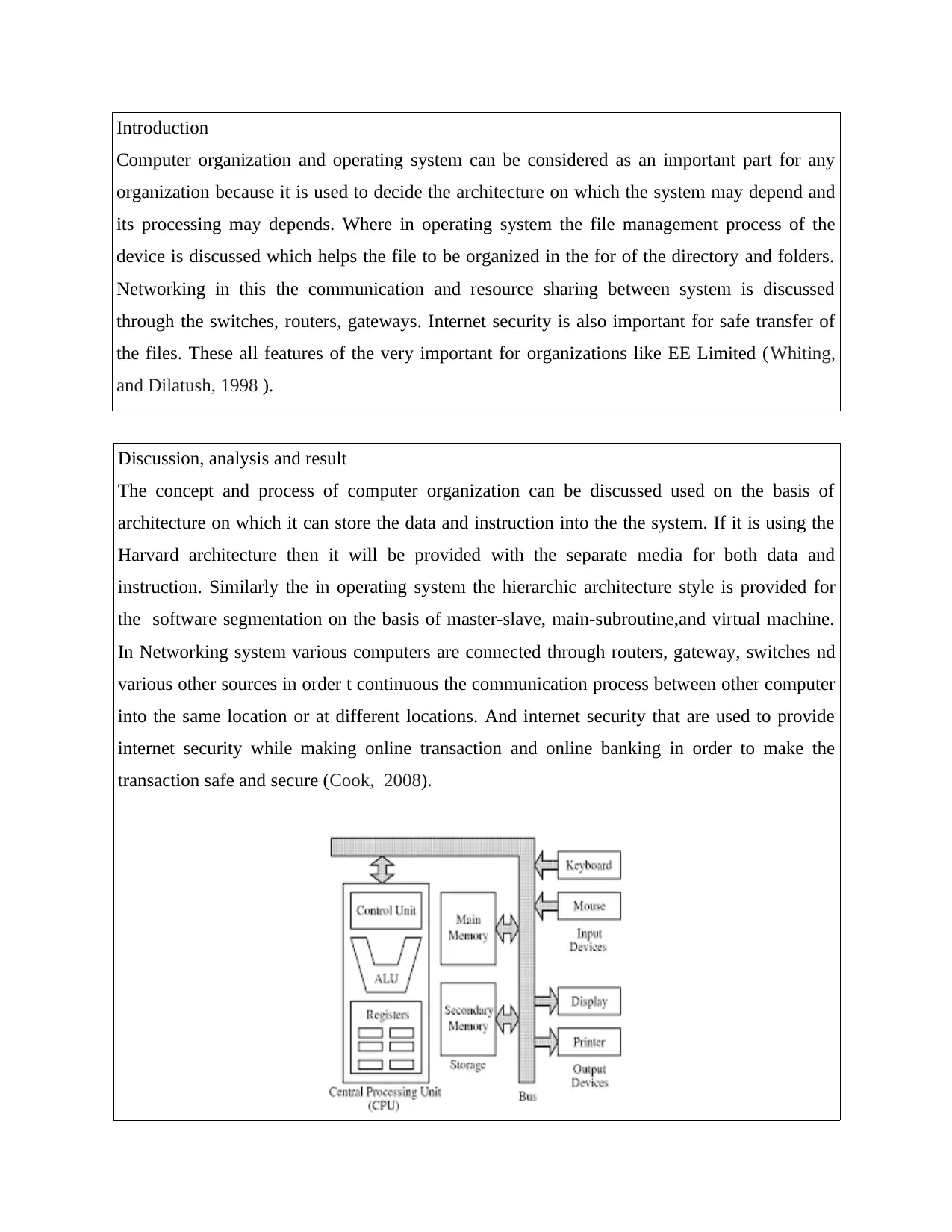
Computer organization deals with hardware of the computer such input devices, output
devices and CPU. In which computer organize its devices in a way that they make the processing
of the device smooth. Such as the CPU perform the fetching and execution process of the
instruction using program counter that holds the address of instruction into memory. Input and
output devices are used to organize the process of receiving and transmitting the process and also
use to store the information into the memory of the device. In Harvard architecture separate
memories are provided for both date and instruction (Jain, and Routhier, 1986.). It also provide
two set of address buses or data buses that is presented between CPU and memory. In Harvard
two simultaneous fetching of memory is allowed. Harvard architecture are still used by many
companies because it provides greater memory bandwidth. Where in Von Neumann architecture
common memory is provided to store the data and instruction instead of separate memory. It
have single set of address bus between CPU and memory due to which the size of memory
Abstract
In this the report impact of computer organization and operating system, networking and
internet security on any IT company which analysis the process and the flow of data and
instructions on the basis of architecture. And various hierarchical systems are considered that
helps us in modulating the software system into logical fragments that helps us in identifying the
hierarchic architecture style of the software in which different process uses different approaches
such as in main-subroutine the software is divided in to fragments, in master-slave divide and
conquer asspproach is used where in virtual machine a virtual system is created by the software.
In networking various networking protocols are used that helps in communicating or share the
information with the system (Bhuyan, and Agrawal, 1984). This can also be used for resource
sharing purpose. It provides lots of protocols for the transferring the files from source to
destination with guarantee and many other protocols are provides that can helps in uploading and
downloading the mails. And internet security in which security is provided during internet
browsing, online banking transaction, while uploading and downloading the files. Because
during this period various threats such as virus, worms, trojan harms may damage your data and
corrupt your file. And may cause the situation where data loss takes place.
Background
Computer organization deals with hardware of the computer such input devices, output
devices and CPU. In which computer organize its devices in a way that they make the processing
of the device smooth. Such as the CPU perform the fetching and execution process of the
instruction using program counter that holds the address of instruction into memory. Input and
output devices are used to organize the process of receiving and transmitting the process and also
use to store the information into the memory of the device. In Harvard architecture separate
memories are provided for both date and instruction (Jain, and Routhier, 1986.). It also provide
two set of address buses or data buses that is presented between CPU and memory. In Harvard
two simultaneous fetching of memory is allowed. Harvard architecture are still used by many
companies because it provides greater memory bandwidth. Where in Von Neumann architecture
common memory is provided to store the data and instruction instead of separate memory. It
have single set of address bus between CPU and memory due to which the size of memory

bandwidth get reduced. In this report John Lewis Partnership is an IT company that uses the
most efficient architecture in order to increase the speed (Davis,. 2001).
Operating systems are used to control and manage the computation of resources. The
services that are offered by the operating system are file system in which files are arranged in the
form of directory, folders and files into the device. Another process of the operating system is
providing commands that are used to manipulate the file system such insertion, deletion, copy
and update. And the last but most important work of operating system is to manage the
processing of the system. In operating system one of the important topic is system software
hierarchy in which the software system is divided into small logical units at different levels. The
system id divided such as main-subroutine, master-slave and virtual machine. In main-subroutine
module the software is fragmented according to the functionality of the system. In master-slave
module divide and conquer approach is used. In this method the task is divided into small parts
until we get the solution and once we get the desired result combine the result. In virtual machine
a virtual system is created which does not have any physical existence.
Networking concept is used for connecting computers through other devices using
switches, routers, gateways and other types of access points. .This can be considered as an
important part because it enable the communication between the system by enabling the
communication channel between them. EE Limited work to provide the internet services. For
this communication various Internet protocols are used such as TCP, UDP, FTP, HTTP, SMTP&
POP3 and much more. TCP (Transmission Control Protocol) in which information is braked into
small pieces of information packets and then transmission takes place and once they reached at
the destination pockets are recombine again. UDP (User Datagram Protocol) this protocol is
same as the previous one but in this we can transmit more than one at a time. SMTP(Simple
mail Transfer Protocol) &POP3( Post Office Protocol) which help in uploading and downloading
the e-mails (Roberts, and Wessler, 1970).
Internet security can be considered as an important branch of computer security in this
security is concern at the time of browsing internet, using online banking transactions,
downloading files. EE limited uses the feature of internet security. Internet security deals with all
kinds of virus, worms , threats and hackers also. In this context cloud computing security is very
important because in this the services are provided by the service provider and used by the
most efficient architecture in order to increase the speed (Davis,. 2001).
Operating systems are used to control and manage the computation of resources. The
services that are offered by the operating system are file system in which files are arranged in the
form of directory, folders and files into the device. Another process of the operating system is
providing commands that are used to manipulate the file system such insertion, deletion, copy
and update. And the last but most important work of operating system is to manage the
processing of the system. In operating system one of the important topic is system software
hierarchy in which the software system is divided into small logical units at different levels. The
system id divided such as main-subroutine, master-slave and virtual machine. In main-subroutine
module the software is fragmented according to the functionality of the system. In master-slave
module divide and conquer approach is used. In this method the task is divided into small parts
until we get the solution and once we get the desired result combine the result. In virtual machine
a virtual system is created which does not have any physical existence.
Networking concept is used for connecting computers through other devices using
switches, routers, gateways and other types of access points. .This can be considered as an
important part because it enable the communication between the system by enabling the
communication channel between them. EE Limited work to provide the internet services. For
this communication various Internet protocols are used such as TCP, UDP, FTP, HTTP, SMTP&
POP3 and much more. TCP (Transmission Control Protocol) in which information is braked into
small pieces of information packets and then transmission takes place and once they reached at
the destination pockets are recombine again. UDP (User Datagram Protocol) this protocol is
same as the previous one but in this we can transmit more than one at a time. SMTP(Simple
mail Transfer Protocol) &POP3( Post Office Protocol) which help in uploading and downloading
the e-mails (Roberts, and Wessler, 1970).
Internet security can be considered as an important branch of computer security in this
security is concern at the time of browsing internet, using online banking transactions,
downloading files. EE limited uses the feature of internet security. Internet security deals with all
kinds of virus, worms , threats and hackers also. In this context cloud computing security is very
important because in this the services are provided by the service provider and used by the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
customer but it can also access by the third party in the middle. Therefore its security is divided
into two parts at the provider end and at the customer end (Kenner, Gruber and InterVu, 1999).
Advantages and disadvantages
Computer Organization:
Architecture Advantages Disadvantage
Harvard The Harvard architecture
provides different media for
both data and instruction. EE
limited also uses the simplified
architecture.
As the architecture provide
different media due to this the
system became more large and
complex.
Von-neumann The van-neumann architecture
is flexible in nature because
both the data and instruction
are stored at the same place so
the transaction become easy.
As the instruction and data
flows from same path the
memory bandwidth get
automatically reduced.
Operating System:
Hierarchical style Advantages Disadvantages
Main-subroutine Decomposition of the system
is easy and the process is
object-oriented. EE limited
also provide such services
through mobile services.
Data become vulnerable due to
global sharing and ripple effect
may arise due to tight coupling
of data (Filepp,. 1994).
Master-slave Useful in the case where
reliability is important.
Implementation is hard and
may have portability issues.
Virtual Machine Runtime modification are also
introduced into the system.
Execution may be slow down.
Networking:
into two parts at the provider end and at the customer end (Kenner, Gruber and InterVu, 1999).
Advantages and disadvantages
Computer Organization:
Architecture Advantages Disadvantage
Harvard The Harvard architecture
provides different media for
both data and instruction. EE
limited also uses the simplified
architecture.
As the architecture provide
different media due to this the
system became more large and
complex.
Von-neumann The van-neumann architecture
is flexible in nature because
both the data and instruction
are stored at the same place so
the transaction become easy.
As the instruction and data
flows from same path the
memory bandwidth get
automatically reduced.
Operating System:
Hierarchical style Advantages Disadvantages
Main-subroutine Decomposition of the system
is easy and the process is
object-oriented. EE limited
also provide such services
through mobile services.
Data become vulnerable due to
global sharing and ripple effect
may arise due to tight coupling
of data (Filepp,. 1994).
Master-slave Useful in the case where
reliability is important.
Implementation is hard and
may have portability issues.
Virtual Machine Runtime modification are also
introduced into the system.
Execution may be slow down.
Networking:
Protocols Advantages Disadvantages
TCP Always provide guarantee of
data transmission at right place
on time without duplicating.
EE limited also support such
internet protocols (Kalakota,
and Whinston, 1996. ).
It does not uses the broadcast
and multicast connections. As
the process runs at OP level so
problems like downloading
may arise.
UDP In UDP both the broadcast
and multicast connections are
used for transmission.
Breaking of data into packets
takes place manually.
Internet Security:
Advantage Disadvantage
In cloud computing the investment on
software, infrastructure and server get reduced
so the security budget get increased. As the
process is very simple so people are attracting
towards it.
As the cloud computing can be done from any
where we do not need any specific
infrastructure so the third party or brokers may
also get involved into this.
Legal and Ethical
IT security persons usually have access on the confidential data of any individual or any
organization. But it sometime may misuse this information in order to avoid such situation
certain laws are presented which are known as IT acts . Under which any kind of unethical
hacking, or using the confidential data for wrong purpose will be considered under IT act. In
some case government heir the hackers but for ethical purpose. And all the IT companies strictly
follows these rules. EE limited also follow all the IT acts and does not go against any of the laws
and accordingly provides services to their customers (Wise, Mavrotheris, and Curry, 1999 ).
TCP Always provide guarantee of
data transmission at right place
on time without duplicating.
EE limited also support such
internet protocols (Kalakota,
and Whinston, 1996. ).
It does not uses the broadcast
and multicast connections. As
the process runs at OP level so
problems like downloading
may arise.
UDP In UDP both the broadcast
and multicast connections are
used for transmission.
Breaking of data into packets
takes place manually.
Internet Security:
Advantage Disadvantage
In cloud computing the investment on
software, infrastructure and server get reduced
so the security budget get increased. As the
process is very simple so people are attracting
towards it.
As the cloud computing can be done from any
where we do not need any specific
infrastructure so the third party or brokers may
also get involved into this.
Legal and Ethical
IT security persons usually have access on the confidential data of any individual or any
organization. But it sometime may misuse this information in order to avoid such situation
certain laws are presented which are known as IT acts . Under which any kind of unethical
hacking, or using the confidential data for wrong purpose will be considered under IT act. In
some case government heir the hackers but for ethical purpose. And all the IT companies strictly
follows these rules. EE limited also follow all the IT acts and does not go against any of the laws
and accordingly provides services to their customers (Wise, Mavrotheris, and Curry, 1999 ).

Conclusion
In this report the discussion is made on the concept and principle of the computer
organization and operating system, networking and internet security. In this report the
architecture, protocols of the different internet protocols are discussed in which their advantages
and disadvantage of the protocols are also included so that the brief idea of their work can be
drawn. If the computer organization architecture is Harvard then it will give more memory
bandwidth but in case of van neumann the memory bandwidth will be not be much large. During
this discussion the another important topic is operating system in which the file management
system of the device is discussed where the file is divided into the form of directory, folders and
files and are stored into that form (Ohira, and Sawatari, 1998). Such as the EE Limited use to
provide internet services to the customers of London. Another important function of operating
system is processing the commands that are helpful in the execution of the instructions and can
be used for managing the input and output devices.
Task 2 Poster
In this report the discussion is made on the concept and principle of the computer
organization and operating system, networking and internet security. In this report the
architecture, protocols of the different internet protocols are discussed in which their advantages
and disadvantage of the protocols are also included so that the brief idea of their work can be
drawn. If the computer organization architecture is Harvard then it will give more memory
bandwidth but in case of van neumann the memory bandwidth will be not be much large. During
this discussion the another important topic is operating system in which the file management
system of the device is discussed where the file is divided into the form of directory, folders and
files and are stored into that form (Ohira, and Sawatari, 1998). Such as the EE Limited use to
provide internet services to the customers of London. Another important function of operating
system is processing the commands that are helpful in the execution of the instructions and can
be used for managing the input and output devices.
Task 2 Poster
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
Computer organization and operating system can be considered as an important part for any
organization because it is used to decide the architecture on which the system may depend and
its processing may depends. Where in operating system the file management process of the
device is discussed which helps the file to be organized in the for of the directory and folders.
Networking in this the communication and resource sharing between system is discussed
through the switches, routers, gateways. Internet security is also important for safe transfer of
the files. These all features of the very important for organizations like EE Limited (Whiting,
and Dilatush, 1998 ).
Discussion, analysis and result
The concept and process of computer organization can be discussed used on the basis of
architecture on which it can store the data and instruction into the the system. If it is using the
Harvard architecture then it will be provided with the separate media for both data and
instruction. Similarly the in operating system the hierarchic architecture style is provided for
the software segmentation on the basis of master-slave, main-subroutine,and virtual machine.
In Networking system various computers are connected through routers, gateway, switches nd
various other sources in order t continuous the communication process between other computer
into the same location or at different locations. And internet security that are used to provide
internet security while making online transaction and online banking in order to make the
transaction safe and secure (Cook, 2008).
Computer organization and operating system can be considered as an important part for any
organization because it is used to decide the architecture on which the system may depend and
its processing may depends. Where in operating system the file management process of the
device is discussed which helps the file to be organized in the for of the directory and folders.
Networking in this the communication and resource sharing between system is discussed
through the switches, routers, gateways. Internet security is also important for safe transfer of
the files. These all features of the very important for organizations like EE Limited (Whiting,
and Dilatush, 1998 ).
Discussion, analysis and result
The concept and process of computer organization can be discussed used on the basis of
architecture on which it can store the data and instruction into the the system. If it is using the
Harvard architecture then it will be provided with the separate media for both data and
instruction. Similarly the in operating system the hierarchic architecture style is provided for
the software segmentation on the basis of master-slave, main-subroutine,and virtual machine.
In Networking system various computers are connected through routers, gateway, switches nd
various other sources in order t continuous the communication process between other computer
into the same location or at different locations. And internet security that are used to provide
internet security while making online transaction and online banking in order to make the
transaction safe and secure (Cook, 2008).
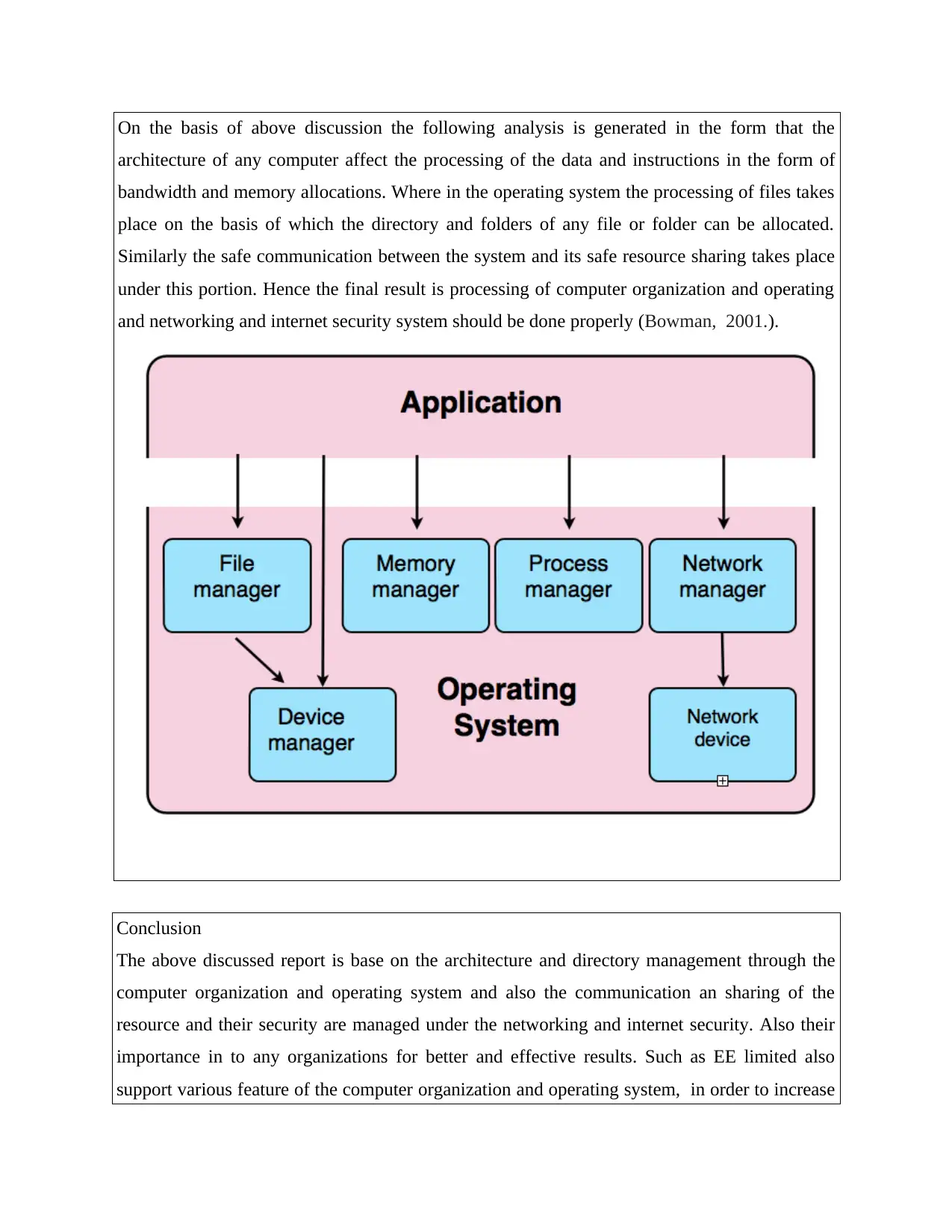
On the basis of above discussion the following analysis is generated in the form that the
architecture of any computer affect the processing of the data and instructions in the form of
bandwidth and memory allocations. Where in the operating system the processing of files takes
place on the basis of which the directory and folders of any file or folder can be allocated.
Similarly the safe communication between the system and its safe resource sharing takes place
under this portion. Hence the final result is processing of computer organization and operating
and networking and internet security system should be done properly (Bowman, 2001.).
Conclusion
The above discussed report is base on the architecture and directory management through the
computer organization and operating system and also the communication an sharing of the
resource and their security are managed under the networking and internet security. Also their
importance in to any organizations for better and effective results. Such as EE limited also
support various feature of the computer organization and operating system, in order to increase
architecture of any computer affect the processing of the data and instructions in the form of
bandwidth and memory allocations. Where in the operating system the processing of files takes
place on the basis of which the directory and folders of any file or folder can be allocated.
Similarly the safe communication between the system and its safe resource sharing takes place
under this portion. Hence the final result is processing of computer organization and operating
and networking and internet security system should be done properly (Bowman, 2001.).
Conclusion
The above discussed report is base on the architecture and directory management through the
computer organization and operating system and also the communication an sharing of the
resource and their security are managed under the networking and internet security. Also their
importance in to any organizations for better and effective results. Such as EE limited also
support various feature of the computer organization and operating system, in order to increase
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

the customer satisfaction. The networking and internet security are considered as an important
issue because it helps to improve the customer and owner's relationship (Pitkin, and Morency,
1994).
issue because it helps to improve the customer and owner's relationship (Pitkin, and Morency,
1994).
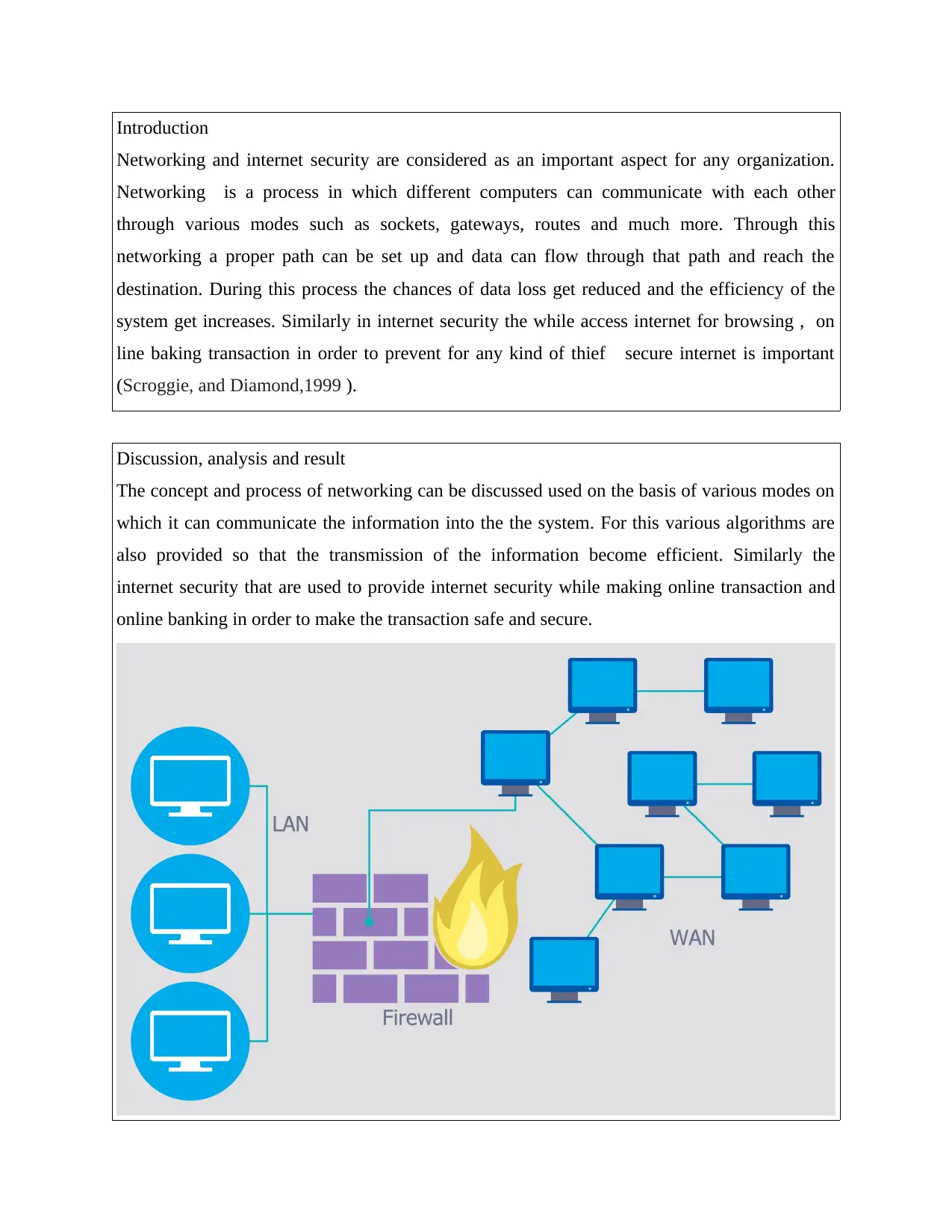
Introduction
Networking and internet security are considered as an important aspect for any organization.
Networking is a process in which different computers can communicate with each other
through various modes such as sockets, gateways, routes and much more. Through this
networking a proper path can be set up and data can flow through that path and reach the
destination. During this process the chances of data loss get reduced and the efficiency of the
system get increases. Similarly in internet security the while access internet for browsing , on
line baking transaction in order to prevent for any kind of thief secure internet is important
(Scroggie, and Diamond,1999 ).
Discussion, analysis and result
The concept and process of networking can be discussed used on the basis of various modes on
which it can communicate the information into the the system. For this various algorithms are
also provided so that the transmission of the information become efficient. Similarly the
internet security that are used to provide internet security while making online transaction and
online banking in order to make the transaction safe and secure.
Networking and internet security are considered as an important aspect for any organization.
Networking is a process in which different computers can communicate with each other
through various modes such as sockets, gateways, routes and much more. Through this
networking a proper path can be set up and data can flow through that path and reach the
destination. During this process the chances of data loss get reduced and the efficiency of the
system get increases. Similarly in internet security the while access internet for browsing , on
line baking transaction in order to prevent for any kind of thief secure internet is important
(Scroggie, and Diamond,1999 ).
Discussion, analysis and result
The concept and process of networking can be discussed used on the basis of various modes on
which it can communicate the information into the the system. For this various algorithms are
also provided so that the transmission of the information become efficient. Similarly the
internet security that are used to provide internet security while making online transaction and
online banking in order to make the transaction safe and secure.

Roberts, and Wessler, 1970).The analysis that is generated by the computer networking is that it
is used to provide the communication between the the computer system that are present at
different locations into the same organization or present across the world. This can be achieved
through various means by using router, gateway, sockets and much more that helps the system
to communicate with each other. In order to achieve this various algorithms can also be used or
the generation or to decide the path for the transmission of the data from source to destination
without any failure. Similarly the another issue is internet security in which different security
methods are considered in order to prevent from any kind of trojan worm, virus or any hacker
while accessing the internet or browsing the file. To prevent from such kind of threats one
should always refer the authorized services and internet firewall should be enable always while
using internet so that the threats cannot come into the system and cannot cause any damage to
the information that is present into your system. While using cloud computing the chances of
internet security get increases because in cloud computing the process is not installed at any
particular system and can be access by any service provider, customer and even by the third
party.
Conclusion
On the basis of the above discussion the concept and principle of the networking and internet
security is very clear. The objective behind using the networking is to provide the
communication between the computers that are places on either same location or at different
location by using routers, gateways, sockets and much more. In order to make the process more
efficient various routing algorithms are also available which helps by providing shortest path in
order to complete communication (Shwed, 1997).
is used to provide the communication between the the computer system that are present at
different locations into the same organization or present across the world. This can be achieved
through various means by using router, gateway, sockets and much more that helps the system
to communicate with each other. In order to achieve this various algorithms can also be used or
the generation or to decide the path for the transmission of the data from source to destination
without any failure. Similarly the another issue is internet security in which different security
methods are considered in order to prevent from any kind of trojan worm, virus or any hacker
while accessing the internet or browsing the file. To prevent from such kind of threats one
should always refer the authorized services and internet firewall should be enable always while
using internet so that the threats cannot come into the system and cannot cause any damage to
the information that is present into your system. While using cloud computing the chances of
internet security get increases because in cloud computing the process is not installed at any
particular system and can be access by any service provider, customer and even by the third
party.
Conclusion
On the basis of the above discussion the concept and principle of the networking and internet
security is very clear. The objective behind using the networking is to provide the
communication between the computers that are places on either same location or at different
location by using routers, gateways, sockets and much more. In order to make the process more
efficient various routing algorithms are also available which helps by providing shortest path in
order to complete communication (Shwed, 1997).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
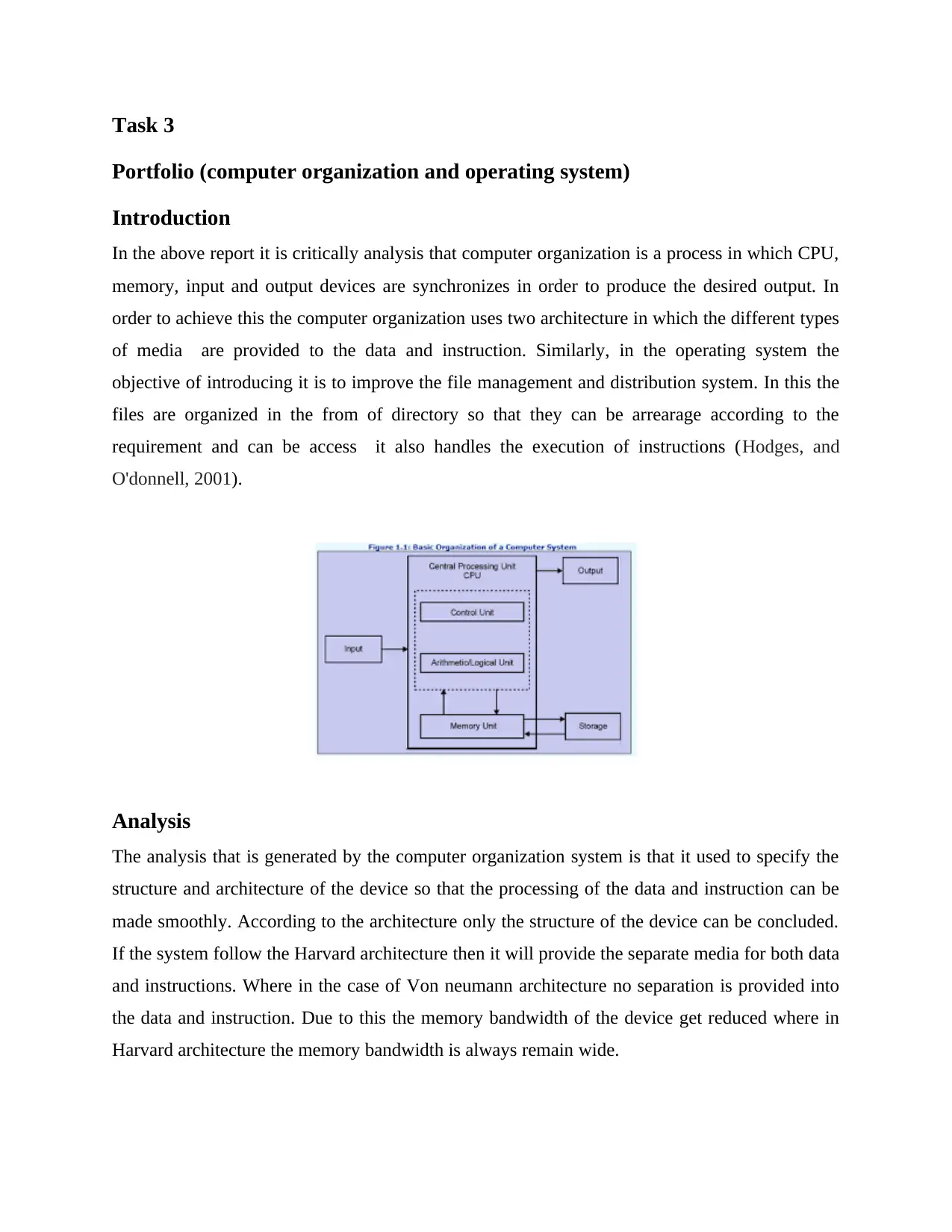
Task 3
Portfolio (computer organization and operating system)
Introduction
In the above report it is critically analysis that computer organization is a process in which CPU,
memory, input and output devices are synchronizes in order to produce the desired output. In
order to achieve this the computer organization uses two architecture in which the different types
of media are provided to the data and instruction. Similarly, in the operating system the
objective of introducing it is to improve the file management and distribution system. In this the
files are organized in the from of directory so that they can be arrearage according to the
requirement and can be access it also handles the execution of instructions (Hodges, and
O'donnell, 2001).
Analysis
The analysis that is generated by the computer organization system is that it used to specify the
structure and architecture of the device so that the processing of the data and instruction can be
made smoothly. According to the architecture only the structure of the device can be concluded.
If the system follow the Harvard architecture then it will provide the separate media for both data
and instructions. Where in the case of Von neumann architecture no separation is provided into
the data and instruction. Due to this the memory bandwidth of the device get reduced where in
Harvard architecture the memory bandwidth is always remain wide.
Portfolio (computer organization and operating system)
Introduction
In the above report it is critically analysis that computer organization is a process in which CPU,
memory, input and output devices are synchronizes in order to produce the desired output. In
order to achieve this the computer organization uses two architecture in which the different types
of media are provided to the data and instruction. Similarly, in the operating system the
objective of introducing it is to improve the file management and distribution system. In this the
files are organized in the from of directory so that they can be arrearage according to the
requirement and can be access it also handles the execution of instructions (Hodges, and
O'donnell, 2001).
Analysis
The analysis that is generated by the computer organization system is that it used to specify the
structure and architecture of the device so that the processing of the data and instruction can be
made smoothly. According to the architecture only the structure of the device can be concluded.
If the system follow the Harvard architecture then it will provide the separate media for both data
and instructions. Where in the case of Von neumann architecture no separation is provided into
the data and instruction. Due to this the memory bandwidth of the device get reduced where in
Harvard architecture the memory bandwidth is always remain wide.

In operating system the process is completely dependent on the file management system because
in this system files are separated on the basis of their directory, their folder and file. On the basis
of this a directory hierarchic is generated which help the system to find out the path of the
particular file. Along with this operating system also manages the execution of the instructions
and commands that are generated due to input and output instructions and also stored into the
memory. Hence the operation system use to play an important role into the system.
Conclusion
On the basis of the above discussion the concept and principle of the operating system is very
clear. And the importance and the implementation of the architecture of the computer
organization and operation system can be described on the basis of their data and instruction
storage and the memory band width that is provided by the system. Similarly in the operating
system the and the how they may affect the system if the processing of the system is not done
properly. The operation of operating system on which the input and the output data of the of the
device are used to compute the result.
in this system files are separated on the basis of their directory, their folder and file. On the basis
of this a directory hierarchic is generated which help the system to find out the path of the
particular file. Along with this operating system also manages the execution of the instructions
and commands that are generated due to input and output instructions and also stored into the
memory. Hence the operation system use to play an important role into the system.
Conclusion
On the basis of the above discussion the concept and principle of the operating system is very
clear. And the importance and the implementation of the architecture of the computer
organization and operation system can be described on the basis of their data and instruction
storage and the memory band width that is provided by the system. Similarly in the operating
system the and the how they may affect the system if the processing of the system is not done
properly. The operation of operating system on which the input and the output data of the of the
device are used to compute the result.
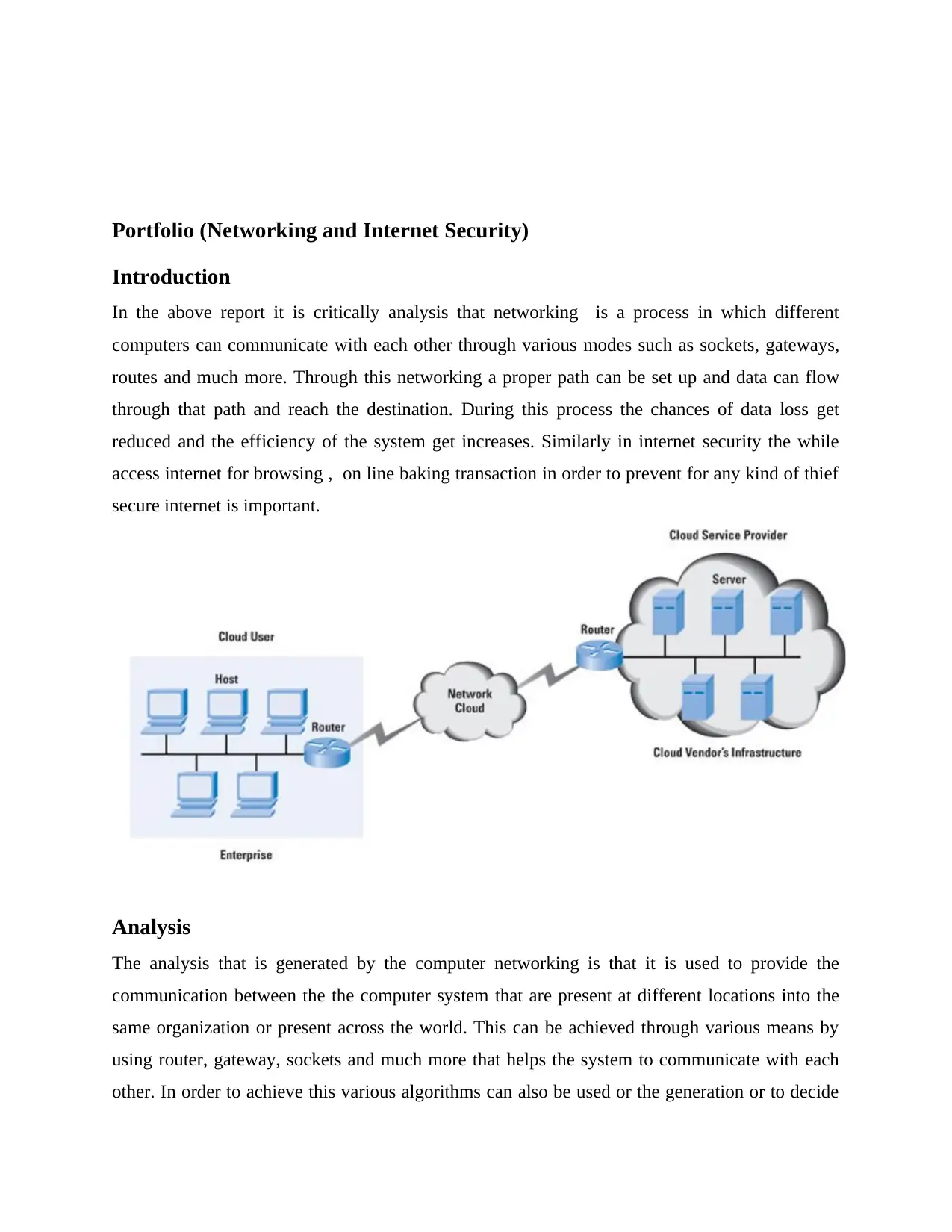
Portfolio (Networking and Internet Security)
Introduction
In the above report it is critically analysis that networking is a process in which different
computers can communicate with each other through various modes such as sockets, gateways,
routes and much more. Through this networking a proper path can be set up and data can flow
through that path and reach the destination. During this process the chances of data loss get
reduced and the efficiency of the system get increases. Similarly in internet security the while
access internet for browsing , on line baking transaction in order to prevent for any kind of thief
secure internet is important.
Analysis
The analysis that is generated by the computer networking is that it is used to provide the
communication between the the computer system that are present at different locations into the
same organization or present across the world. This can be achieved through various means by
using router, gateway, sockets and much more that helps the system to communicate with each
other. In order to achieve this various algorithms can also be used or the generation or to decide
Introduction
In the above report it is critically analysis that networking is a process in which different
computers can communicate with each other through various modes such as sockets, gateways,
routes and much more. Through this networking a proper path can be set up and data can flow
through that path and reach the destination. During this process the chances of data loss get
reduced and the efficiency of the system get increases. Similarly in internet security the while
access internet for browsing , on line baking transaction in order to prevent for any kind of thief
secure internet is important.
Analysis
The analysis that is generated by the computer networking is that it is used to provide the
communication between the the computer system that are present at different locations into the
same organization or present across the world. This can be achieved through various means by
using router, gateway, sockets and much more that helps the system to communicate with each
other. In order to achieve this various algorithms can also be used or the generation or to decide
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

the path for the transmission of the data from source to destination without any failure. Similarly
the another issue is internet security in which different security methods are considered in order
to prevent from any kind of trojan worm, virus or any hacker while accessing the internet or
browsing the file. To prevent from such kind of threats one should always refer the authorized
services and internet firewall should be enable always while using internet so that the threats
cannot come into the system and cannot cause any damage to the information that is present into
your system. While using cloud computing the chances of internet security get increases because
in cloud computing the process is not installed at any particular system and can be access by any
service provider, customer and even by the third party.
Conclusion
On the basis of the above discussion the concept and principle of the networking and internet
security is very clear. The importance and the implementation of the security into the system is
to provide the path to the resources and during all his process the security of the system does not
get affected. The major objective of networking is to provide the communication between the
computers that are places on either same location or at different location. In order to make the
process more efficient various routing algorithms are also available which helps by providing
shortest path in order to complete communication.
the another issue is internet security in which different security methods are considered in order
to prevent from any kind of trojan worm, virus or any hacker while accessing the internet or
browsing the file. To prevent from such kind of threats one should always refer the authorized
services and internet firewall should be enable always while using internet so that the threats
cannot come into the system and cannot cause any damage to the information that is present into
your system. While using cloud computing the chances of internet security get increases because
in cloud computing the process is not installed at any particular system and can be access by any
service provider, customer and even by the third party.
Conclusion
On the basis of the above discussion the concept and principle of the networking and internet
security is very clear. The importance and the implementation of the security into the system is
to provide the path to the resources and during all his process the security of the system does not
get affected. The major objective of networking is to provide the communication between the
computers that are places on either same location or at different location. In order to make the
process more efficient various routing algorithms are also available which helps by providing
shortest path in order to complete communication.

References
Bhuyan, L.N. and Agrawal, D.P., 1984. for Computer Network. IEEE Transactions on
computers, 100(33).
Jain, R. and Routhier, S., 1986. Packet trains--measurements and a new model for computer
network traffic. IEEE journal on selected areas in Communications, 4(6), pp.986- 995.
Davis, D.J., Derer, M., Garcia, J., Greco, L., Kurt, T.E., Kwong, T., Lee, J.C., Lee, K.L., Pfarner,
P. and Skovran, S., Goto. Com, 2001. System and method for influencing a position on a
search result list generated by a computer network search engine. U.S. Patent 6,269,361.
Roberts, L.G. and Wessler, B.D., 1970, May. Computer network development to achieve
resource sharing. In Proceedings of the May 5-7, 1970, spring joint computer
conference (pp. 543-549). ACM.
Kenner, B. and Gruber, H., InterVu, Inc., 1999. System and method for delivery of video data
over a computer network. U.S. Patent 5,956,716.
Filepp, R., Gordon, M.L., Bidwell, A.W., Young, F.C., Wolf, A.M., Meo, S., Tiemann, D.,
Cohen, R.D., Bellar, M., Appleman, K.H. and Abrahams, L., 1994. Reception system for
an interactive computer network and method of operation. U.S. Patent 5,347,632.
Kalakota, R. and Whinston, A.B., 1996. Frontiers of electronic commerce(Vol. 19, No. 2, pp. 1-
3). Reading, MA: Addison-Wesley.
Wise, L.H., Mavrotheris, E. and Curry, J.E., Bell Atlantic Network Services, Inc.,
1999. Computer network audio access and conversion system. U.S. Patent 5,884,262.
Ohira, T. and Sawatari, R., 1998. Phase transition in a computer network traffic model. Physical
Review E, 58(1), p.193.
Whiting, D.L. and Dilatush, T., Stac, Inc., 1998. System for backing up files from disk volumes
on multiple nodes of a computer network. U.S. Patent 5,778,395.
Cook, R.L., Cook Rachael L, 2008. System and method for generating, capturing, and managing
customer lead information over a computer network. U.S. Patent 7,340,411.
Bhuyan, L.N. and Agrawal, D.P., 1984. for Computer Network. IEEE Transactions on
computers, 100(33).
Jain, R. and Routhier, S., 1986. Packet trains--measurements and a new model for computer
network traffic. IEEE journal on selected areas in Communications, 4(6), pp.986- 995.
Davis, D.J., Derer, M., Garcia, J., Greco, L., Kurt, T.E., Kwong, T., Lee, J.C., Lee, K.L., Pfarner,
P. and Skovran, S., Goto. Com, 2001. System and method for influencing a position on a
search result list generated by a computer network search engine. U.S. Patent 6,269,361.
Roberts, L.G. and Wessler, B.D., 1970, May. Computer network development to achieve
resource sharing. In Proceedings of the May 5-7, 1970, spring joint computer
conference (pp. 543-549). ACM.
Kenner, B. and Gruber, H., InterVu, Inc., 1999. System and method for delivery of video data
over a computer network. U.S. Patent 5,956,716.
Filepp, R., Gordon, M.L., Bidwell, A.W., Young, F.C., Wolf, A.M., Meo, S., Tiemann, D.,
Cohen, R.D., Bellar, M., Appleman, K.H. and Abrahams, L., 1994. Reception system for
an interactive computer network and method of operation. U.S. Patent 5,347,632.
Kalakota, R. and Whinston, A.B., 1996. Frontiers of electronic commerce(Vol. 19, No. 2, pp. 1-
3). Reading, MA: Addison-Wesley.
Wise, L.H., Mavrotheris, E. and Curry, J.E., Bell Atlantic Network Services, Inc.,
1999. Computer network audio access and conversion system. U.S. Patent 5,884,262.
Ohira, T. and Sawatari, R., 1998. Phase transition in a computer network traffic model. Physical
Review E, 58(1), p.193.
Whiting, D.L. and Dilatush, T., Stac, Inc., 1998. System for backing up files from disk volumes
on multiple nodes of a computer network. U.S. Patent 5,778,395.
Cook, R.L., Cook Rachael L, 2008. System and method for generating, capturing, and managing
customer lead information over a computer network. U.S. Patent 7,340,411.

Bowman-Amuah, M.K., Accenture, Llp, 2001. Method for providing communication services
over a computer network system. U.S. Patent 6,332,163.
Pitkin, R.P. and Morency, J.P., Digital Equipment Corporation, 1994. Broker for computer
network server selection. U.S. Patent 5,341,477.
Scroggie, M.C., Kacaba, M.E., Rochon, D.A. and Diamond, D.M., SuperMarkets Online, Inc.,
1999. System and method for providing shopping aids and incentives to customers
through a computer network. U.S. Patent 5,970,469.
Huberman, B.A., Xerox Corporation, 1998. Method and system for providing a document
service over a computer network using an automated brokered auction. U.S. Patent
5,826,244.
Shwed, G., Checkpoint Software Technologies Ltd., 1997. System for securing inbound and
outbound data packet flow in a computer network. U.S. Patent 5,606,668.
Hodges, V. and O'donnell, S., Network Associates, Inc., 2001. Method and system for providing
automated updating and upgrading of antivirus applications using a computer network.
U.S. Patent 6,269,456.
over a computer network system. U.S. Patent 6,332,163.
Pitkin, R.P. and Morency, J.P., Digital Equipment Corporation, 1994. Broker for computer
network server selection. U.S. Patent 5,341,477.
Scroggie, M.C., Kacaba, M.E., Rochon, D.A. and Diamond, D.M., SuperMarkets Online, Inc.,
1999. System and method for providing shopping aids and incentives to customers
through a computer network. U.S. Patent 5,970,469.
Huberman, B.A., Xerox Corporation, 1998. Method and system for providing a document
service over a computer network using an automated brokered auction. U.S. Patent
5,826,244.
Shwed, G., Checkpoint Software Technologies Ltd., 1997. System for securing inbound and
outbound data packet flow in a computer network. U.S. Patent 5,606,668.
Hodges, V. and O'donnell, S., Network Associates, Inc., 2001. Method and system for providing
automated updating and upgrading of antivirus applications using a computer network.
U.S. Patent 6,269,456.
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





