Research Project: 5G Network Security Challenges Analysis
VerifiedAdded on 2023/06/04
|13
|5988
|211
Project
AI Summary
This project proposal outlines a research plan to investigate the security challenges of 5G cellular networks. It begins with an executive summary, followed by an introduction to 5G technology and its evolution from previous generations. A literature review explores existing research on 5G security issues, including potential vulnerabilities, threats, and the impact of new business models and the Internet of Things (IoT). The research aims to identify major security issues, propose solutions, and develop a roadmap for addressing these challenges. The methodology involves qualitative data collection and analysis, along with an experimental setup to simulate and study 5G networks. The expected outcomes include identifying exploitable points in the network and providing recommendations for improving security. The project also includes a project planning and Gantt chart outlining the scope, timeline, and resource allocation. The research emphasizes the relevance of 5G security, given its anticipated widespread adoption and the need to protect users. The project will focus on areas like standardization bodies, security architecture, and subscriber privacy.

Prof. Curran/Dr. Saunders, 2013, project template v2
5G Cellular Network and Security Challenges
By Sunny Shingala
Affiliation (MEMEM - Telecommunication) and Study no.
Executive Summary
This paper is mainly based on the development of research proposal for the study and analysis of
5G cellular network and its possible impacts on the telecommunication industry as well as the
general users. 5G or 5th Generation Cellular Network is an upcoming telecommunication system
that will much faster and more efficient than the current 4G network. In spite of the benefits, 5G
network has some significant security challenges that are also discussed in this proposal.
1. Introduction
5G is a cellular network system that will provide internet access to the users at very fast data
rates. While the initial cellular network started with G few years ago, telecommunication
technology has developed and evolved in a lighting pace and after 2G, 3G and 4G, 5G is
currently under testing before it will be implemented for public use. The 5G technology will
revolutionize the data streaming system with the data rates expected to run in several gigabytes
per second speeds. However, most of the studies on 5G cellular network suggest that there can be
many security challenges that can be faced by the 5G network users and hence, suitable actions
must be taken before rolling out the network for general users.
This report is based on the literature review of the security challenges of 5G cellular network and
is also aimed to develop a suitable research project plan for the analysis of the 5G network
security challenges.
2. State-of-the-art/Literature Review
According to the authors Chopra, Jain and Jha (2018), the telecommunication technology is
constantly evolving at a fast pace and the development of the 5G technology reflects this. The
name “5G” corresponds to “5th Generation” of cellular mobile communications. Currently, in
most of the countries around the world, 4th Generation (4G) is mostly used with 5G yet to be
released for public. The authors discussed about the potential of the 5G technology after it is
implemented around the world. The implementation of 5G technology will enable the internet
users to surf and operate on the internet at extremely high speeds without the chances of runtime
errors, lags and others. However, the authors also mentioned that the new technology has a lot of
security issues and problems that have not been addressed yet. Before addressing these issues, it
is not safe to roll out the 5G technology for public use.
Authors Hsiao and Huang (2016) discussed about potential security issues that may occur in 5G
technology unless suitable technical measures are not implemented. One major security challenge
of 5G technology, as the authors discussed, is the emergence of new business models that are
using the telecommunication technology as a part of their IT setup. As a result, the 5G
5G Cellular Network and Security Challenges
By Sunny Shingala
Affiliation (MEMEM - Telecommunication) and Study no.
Executive Summary
This paper is mainly based on the development of research proposal for the study and analysis of
5G cellular network and its possible impacts on the telecommunication industry as well as the
general users. 5G or 5th Generation Cellular Network is an upcoming telecommunication system
that will much faster and more efficient than the current 4G network. In spite of the benefits, 5G
network has some significant security challenges that are also discussed in this proposal.
1. Introduction
5G is a cellular network system that will provide internet access to the users at very fast data
rates. While the initial cellular network started with G few years ago, telecommunication
technology has developed and evolved in a lighting pace and after 2G, 3G and 4G, 5G is
currently under testing before it will be implemented for public use. The 5G technology will
revolutionize the data streaming system with the data rates expected to run in several gigabytes
per second speeds. However, most of the studies on 5G cellular network suggest that there can be
many security challenges that can be faced by the 5G network users and hence, suitable actions
must be taken before rolling out the network for general users.
This report is based on the literature review of the security challenges of 5G cellular network and
is also aimed to develop a suitable research project plan for the analysis of the 5G network
security challenges.
2. State-of-the-art/Literature Review
According to the authors Chopra, Jain and Jha (2018), the telecommunication technology is
constantly evolving at a fast pace and the development of the 5G technology reflects this. The
name “5G” corresponds to “5th Generation” of cellular mobile communications. Currently, in
most of the countries around the world, 4th Generation (4G) is mostly used with 5G yet to be
released for public. The authors discussed about the potential of the 5G technology after it is
implemented around the world. The implementation of 5G technology will enable the internet
users to surf and operate on the internet at extremely high speeds without the chances of runtime
errors, lags and others. However, the authors also mentioned that the new technology has a lot of
security issues and problems that have not been addressed yet. Before addressing these issues, it
is not safe to roll out the 5G technology for public use.
Authors Hsiao and Huang (2016) discussed about potential security issues that may occur in 5G
technology unless suitable technical measures are not implemented. One major security challenge
of 5G technology, as the authors discussed, is the emergence of new business models that are
using the telecommunication technology as a part of their IT setup. As a result, the 5G
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Prof. Curran/Dr. Saunders, 2013, project template v2
technology will need to suit the varying needs of the business models instead of a constant and
similar service to regular internet users. Due to different business models as well as extensive
implementation of the Internet of Things (IoT), it is a significant challenge to manage the security
requirements of the network to which, various business sectors are connected.
Bai and Heath (2015) said that the IT-focused network architecture is one of the main challenges
to deploy a suitable security system in the 5G network. 5G utilizes cost effective IT technologies,
e.g. Software Defined Network (SDN) and virtualization that often do not allow the service
providers to implement any new security measures. Hence, in these cases, controlling the security
of the 5G network will be a significant challenge.
Vassilakis et al. (2017) discussed about the main cyber security threats that may arise in the 5G
networking system. The authors argued that due to very fast data speed, the main cyber threats
like hackers, malwares and other entities can quickly enter into the system even before they get
detected by the security firewalls. Once these entities are able to penetrate into the system, they
will be able steal personal and confidential information from the cloud storage and quickly
transmit them back to the origin. Moreover, with varying security requirements for different
models, it is extremely difficult to take suitable protective measures against the cyber security
threats.
3. Research Question, Aim/Objectives and Sub-goals
Based on the initial analysis and literature review on the chosen research topic, the research
questions are determined and listed as follows.
▪ What are the major security issues that are associated with the 5G technology?
▪ How can the major security issues of 5G technology be addressed?
In addition to the research questions, the main aim of this research is to explore the new 5G
telecommunication technology as well as existing works on the same in order identify the main
and critical security challenges of the technology. Accordingly, some recommendations will also
be provided that will be useful for addressing the security challenges.
The sub goals of the research are as follows.
o To conduct literature survey on the works of various reputed authors regarding the
telecommunication technology
o To collect data from the literature in order to reach a certain conclusion regarding the
research topic
o To use the data to develop a future roadmap for the technology
o To specify the issues that must be avoided on top priority before rolling out the
technology for public use
4. Theoretical Content/Methodology
Since, this particular research is based on a topic of upcoming technology, it can be said that the
works of the authors on this particular technology will be hypothetical in nature and cannot be
tested until the technology is rolled out and tested for the specific security challenges. However,
5G technology is actually a significant upgrade of an already existing telecommunication
technology will need to suit the varying needs of the business models instead of a constant and
similar service to regular internet users. Due to different business models as well as extensive
implementation of the Internet of Things (IoT), it is a significant challenge to manage the security
requirements of the network to which, various business sectors are connected.
Bai and Heath (2015) said that the IT-focused network architecture is one of the main challenges
to deploy a suitable security system in the 5G network. 5G utilizes cost effective IT technologies,
e.g. Software Defined Network (SDN) and virtualization that often do not allow the service
providers to implement any new security measures. Hence, in these cases, controlling the security
of the 5G network will be a significant challenge.
Vassilakis et al. (2017) discussed about the main cyber security threats that may arise in the 5G
networking system. The authors argued that due to very fast data speed, the main cyber threats
like hackers, malwares and other entities can quickly enter into the system even before they get
detected by the security firewalls. Once these entities are able to penetrate into the system, they
will be able steal personal and confidential information from the cloud storage and quickly
transmit them back to the origin. Moreover, with varying security requirements for different
models, it is extremely difficult to take suitable protective measures against the cyber security
threats.
3. Research Question, Aim/Objectives and Sub-goals
Based on the initial analysis and literature review on the chosen research topic, the research
questions are determined and listed as follows.
▪ What are the major security issues that are associated with the 5G technology?
▪ How can the major security issues of 5G technology be addressed?
In addition to the research questions, the main aim of this research is to explore the new 5G
telecommunication technology as well as existing works on the same in order identify the main
and critical security challenges of the technology. Accordingly, some recommendations will also
be provided that will be useful for addressing the security challenges.
The sub goals of the research are as follows.
o To conduct literature survey on the works of various reputed authors regarding the
telecommunication technology
o To collect data from the literature in order to reach a certain conclusion regarding the
research topic
o To use the data to develop a future roadmap for the technology
o To specify the issues that must be avoided on top priority before rolling out the
technology for public use
4. Theoretical Content/Methodology
Since, this particular research is based on a topic of upcoming technology, it can be said that the
works of the authors on this particular technology will be hypothetical in nature and cannot be
tested until the technology is rolled out and tested for the specific security challenges. However,
5G technology is actually a significant upgrade of an already existing telecommunication

Prof. Curran/Dr. Saunders, 2013, project template v2
technology and hence, the security challenges identified may not all be hypothetical in nature.
Most of these security challenges have already been faced in the previous generations of
telecommunication technology and hence, the challenges for the 5G can also be predicted with
high accuracy. Hence, this research does not require defining any new hypothesis but will aim to
find suitable answers to the security challenges of 5G that have already been highlighted by the
researchers.
For the purpose of the research, the main method that will be followed is the qualitative data
collection that will be followed by data analysis. Furthermore, an experimental setup will be
required to study the 5G system practically and collect suitable data for the same. The research
team will include four researchers each of whom will have specific roles and duties.
After the analysis of data collected from literature and experiment, the final results will be noted
down and the outcome and relevance of the data will be analyzed and explained.
5. Experimental Set-up
Since this is an academic research project, the scope of the overall experimental setup will be
very much limited. This is due to the lack of sufficient space and funding that are both required to
conduct such large scale projects. Furthermore, the current telecommunication industry only
provides access to 4G networks for general users and hence, in order to work with 5G network,
special permission and experimental set up will have to be provided by a telecommunication
service provider.
The general experimental setup will include electronic devices that can monitor a
telecommunication cellular network and its various attributes like data speed, data transmission
and others. Specific software will be used to determine if there are any gaps within the transport
layer of the network that might be exploited by the hackers at any time.
6. Results, Outcome and Relevance
Using the experimental setup, the results will be obtained regarding the 5G cellular networks and
the gaps that are existing in the services that might be utilized by the hackers and other unethical
entities. Using network monitoring system, the data transmission process through the 5G network
will be observed along with the data transmission speed, content, gap to exploit and others. The
main focus will be on the exploitable points of the network and results will be required to analyze
how the exploitable points in the transport layer can be facilitated by high data speeds when a
hacker is trying to breach the system.
technology and hence, the security challenges identified may not all be hypothetical in nature.
Most of these security challenges have already been faced in the previous generations of
telecommunication technology and hence, the challenges for the 5G can also be predicted with
high accuracy. Hence, this research does not require defining any new hypothesis but will aim to
find suitable answers to the security challenges of 5G that have already been highlighted by the
researchers.
For the purpose of the research, the main method that will be followed is the qualitative data
collection that will be followed by data analysis. Furthermore, an experimental setup will be
required to study the 5G system practically and collect suitable data for the same. The research
team will include four researchers each of whom will have specific roles and duties.
After the analysis of data collected from literature and experiment, the final results will be noted
down and the outcome and relevance of the data will be analyzed and explained.
5. Experimental Set-up
Since this is an academic research project, the scope of the overall experimental setup will be
very much limited. This is due to the lack of sufficient space and funding that are both required to
conduct such large scale projects. Furthermore, the current telecommunication industry only
provides access to 4G networks for general users and hence, in order to work with 5G network,
special permission and experimental set up will have to be provided by a telecommunication
service provider.
The general experimental setup will include electronic devices that can monitor a
telecommunication cellular network and its various attributes like data speed, data transmission
and others. Specific software will be used to determine if there are any gaps within the transport
layer of the network that might be exploited by the hackers at any time.
6. Results, Outcome and Relevance
Using the experimental setup, the results will be obtained regarding the 5G cellular networks and
the gaps that are existing in the services that might be utilized by the hackers and other unethical
entities. Using network monitoring system, the data transmission process through the 5G network
will be observed along with the data transmission speed, content, gap to exploit and others. The
main focus will be on the exploitable points of the network and results will be required to analyze
how the exploitable points in the transport layer can be facilitated by high data speeds when a
hacker is trying to breach the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Prof. Curran/Dr. Saunders, 2013, project template v2
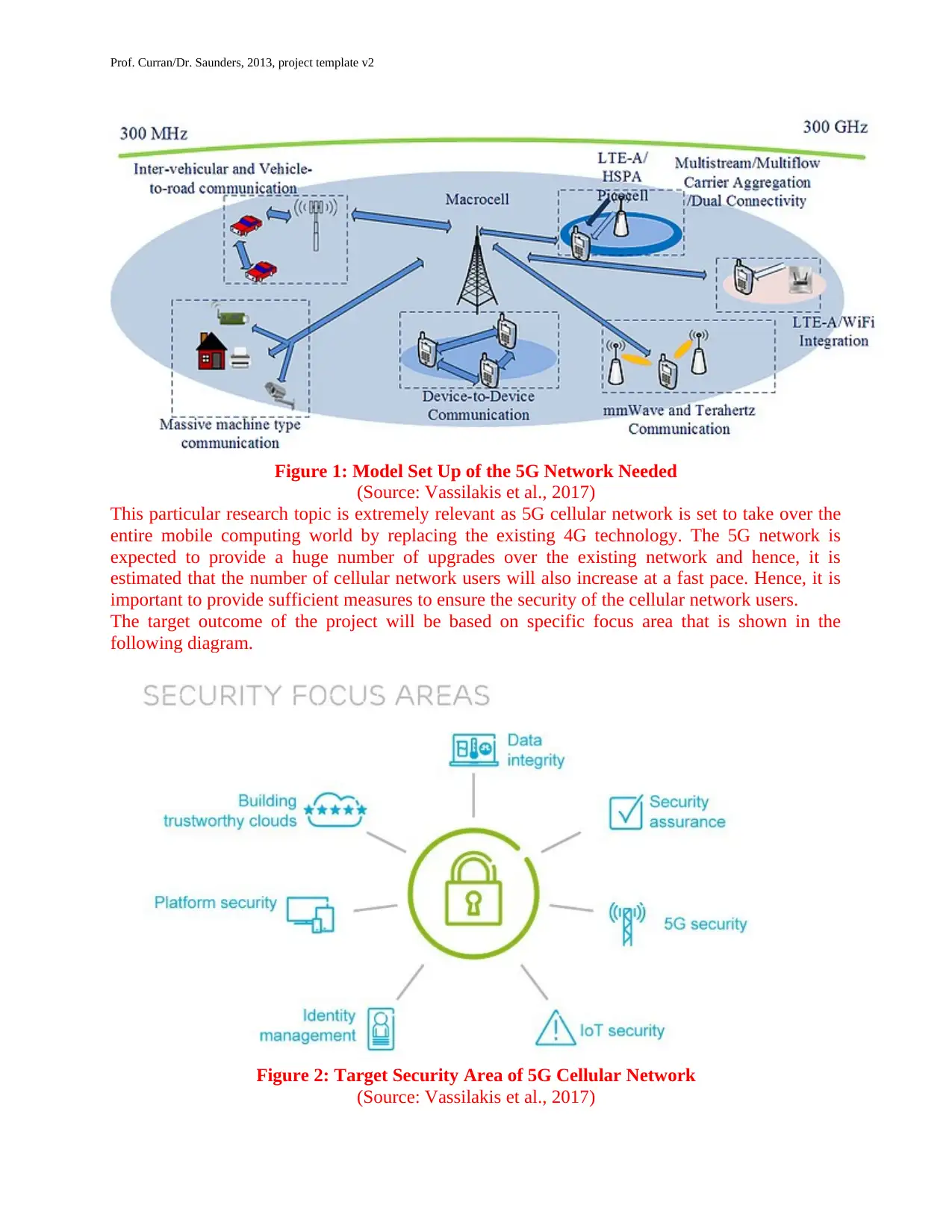
Figure 1: Model Set Up of the 5G Network Needed
(Source: Vassilakis et al., 2017)
This particular research topic is extremely relevant as 5G cellular network is set to take over the
entire mobile computing world by replacing the existing 4G technology. The 5G network is
expected to provide a huge number of upgrades over the existing network and hence, it is
estimated that the number of cellular network users will also increase at a fast pace. Hence, it is
important to provide sufficient measures to ensure the security of the cellular network users.
The target outcome of the project will be based on specific focus area that is shown in the
following diagram.
Figure 2: Target Security Area of 5G Cellular Network
(Source: Vassilakis et al., 2017)
Figure 1: Model Set Up of the 5G Network Needed
(Source: Vassilakis et al., 2017)
This particular research topic is extremely relevant as 5G cellular network is set to take over the
entire mobile computing world by replacing the existing 4G technology. The 5G network is
expected to provide a huge number of upgrades over the existing network and hence, it is
estimated that the number of cellular network users will also increase at a fast pace. Hence, it is
important to provide sufficient measures to ensure the security of the cellular network users.
The target outcome of the project will be based on specific focus area that is shown in the
following diagram.
Figure 2: Target Security Area of 5G Cellular Network
(Source: Vassilakis et al., 2017)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Prof. Curran/Dr. Saunders, 2013, project template v2
In addition, the focus will be on the following topics related to the security challenges of 5G
cellular network.
Standardization Bodies Major Security Areas in Focus
3GPP Security architecture, RAN security,
authentication mechanism, subscriber privacy,
network slicing
IETF Security solutions for massive IoT devices in
5G, user privacy, network security functions
(NSFs)
ETSI Security architecture, NFV security, MEC
security, privacy
5GPPP Security architecture, subscriber privacy,
authentication mechanism
NGMN Subscriber privacy, network slicing, MEC
security
7. Project Planning and Gantt Chart
Scope – The scope of the entire research project is to set up an experiment for the study and
analysis of the security challenges of 5G cellular network.
Timeline and Cost – The proposed timeline, resource usage and the funding requirements for the
research project are shown in the following table.
Task Name Duratio
n Start Finish Resource Names Cost
Research Project on
Security Challenges of 5G
Cellular Network
111 days
Mon
21-
01-19
Mon
24-06-
19
$6,946.0
0
Topic Selection and
Discussion 13 days
Mon
21-
01-19
Wed
06-02-
19
$1,168.0
0
Receive Instructions
Regarding Research and
Possible Field of Topic
1 day
Mon
21-
01-19
Mon
21-01-
19
Research Supervisor $400.00
Select a Field of
Research 1 day
Tue
22-
01-19
Tue
22-01-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Choose a Number of
Topics on the Selected Field 1 day
Wed
23-
01-19
Wed
23-01-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Consider the Scope of
the Topics 1 day
Thu
24-
01-19
Thu
24-01-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Test the Feasibility of
Topics Based on Overall
1 day Fri
25-
Fri 25-
01-19
Research Associate 1, Research
Associate 2, Research Associate
$64.00
In addition, the focus will be on the following topics related to the security challenges of 5G
cellular network.
Standardization Bodies Major Security Areas in Focus
3GPP Security architecture, RAN security,
authentication mechanism, subscriber privacy,
network slicing
IETF Security solutions for massive IoT devices in
5G, user privacy, network security functions
(NSFs)
ETSI Security architecture, NFV security, MEC
security, privacy
5GPPP Security architecture, subscriber privacy,
authentication mechanism
NGMN Subscriber privacy, network slicing, MEC
security
7. Project Planning and Gantt Chart
Scope – The scope of the entire research project is to set up an experiment for the study and
analysis of the security challenges of 5G cellular network.
Timeline and Cost – The proposed timeline, resource usage and the funding requirements for the
research project are shown in the following table.
Task Name Duratio
n Start Finish Resource Names Cost
Research Project on
Security Challenges of 5G
Cellular Network
111 days
Mon
21-
01-19
Mon
24-06-
19
$6,946.0
0
Topic Selection and
Discussion 13 days
Mon
21-
01-19
Wed
06-02-
19
$1,168.0
0
Receive Instructions
Regarding Research and
Possible Field of Topic
1 day
Mon
21-
01-19
Mon
21-01-
19
Research Supervisor $400.00
Select a Field of
Research 1 day
Tue
22-
01-19
Tue
22-01-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Choose a Number of
Topics on the Selected Field 1 day
Wed
23-
01-19
Wed
23-01-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Consider the Scope of
the Topics 1 day
Thu
24-
01-19
Thu
24-01-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Test the Feasibility of
Topics Based on Overall
1 day Fri
25-
Fri 25-
01-19
Research Associate 1, Research
Associate 2, Research Associate
$64.00
Prof. Curran/Dr. Saunders, 2013, project template v2
Scope of the Research 01-19 3, Research Associate 4
Select a Particular
Research Topic 1 day
Mon
28-
01-19
Mon
28-01-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Receive Approval from
Supervisor Regarding
Selected Topic
1 day
Tue
29-
01-19
Tue
29-01-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Prepare Research
Proposal 1 day
Wed
30-
01-19
Wed
30-01-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Submit Research
Proposal 5 days
Thu
31-
01-19
Wed
06-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$320.00
Kick Off Review 0 days
Wed
06-
02-19
Wed
06-02-
19
Research Supervisor $0.00
Research Planning 11 days
Thu
07-
02-19
Thu
21-02-
19
$704.00
Develop the Overall
Scope of the Research 1 day
Thu
07-
02-19
Thu
07-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Develop a Work
Breakdown Structure for the
Entire Research
1 day
Fri
08-
02-19
Fri 08-
02-19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Develop a Research
Schedule Using Gantt Chart 1 day
Mon
11-
02-19
Mon
11-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Allocate Duties to the
Team Members 1 day
Tue
12-
02-19
Tue
12-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Prepare Resource Plan 2 days
Wed
13-
02-19
Thu
14-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$128.00
Request Funding for the
Research Based on
Estimation of Requirements
1 day
Fri
15-
02-19
Fri 15-
02-19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Determine Research
Roadmap and Methodology
to be Followed
0.5 days
Mon
18-
02-19
Mon
18-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$32.00
Determine Research
Approach 0.5 days
Mon
18-
02-19
Mon
18-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$32.00
Determine Data 1 day Tue Tue Research Associate 1, Research $64.00
Scope of the Research 01-19 3, Research Associate 4
Select a Particular
Research Topic 1 day
Mon
28-
01-19
Mon
28-01-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Receive Approval from
Supervisor Regarding
Selected Topic
1 day
Tue
29-
01-19
Tue
29-01-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Prepare Research
Proposal 1 day
Wed
30-
01-19
Wed
30-01-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Submit Research
Proposal 5 days
Thu
31-
01-19
Wed
06-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$320.00
Kick Off Review 0 days
Wed
06-
02-19
Wed
06-02-
19
Research Supervisor $0.00
Research Planning 11 days
Thu
07-
02-19
Thu
21-02-
19
$704.00
Develop the Overall
Scope of the Research 1 day
Thu
07-
02-19
Thu
07-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Develop a Work
Breakdown Structure for the
Entire Research
1 day
Fri
08-
02-19
Fri 08-
02-19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Develop a Research
Schedule Using Gantt Chart 1 day
Mon
11-
02-19
Mon
11-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Allocate Duties to the
Team Members 1 day
Tue
12-
02-19
Tue
12-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Prepare Resource Plan 2 days
Wed
13-
02-19
Thu
14-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$128.00
Request Funding for the
Research Based on
Estimation of Requirements
1 day
Fri
15-
02-19
Fri 15-
02-19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Determine Research
Roadmap and Methodology
to be Followed
0.5 days
Mon
18-
02-19
Mon
18-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$32.00
Determine Research
Approach 0.5 days
Mon
18-
02-19
Mon
18-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$32.00
Determine Data 1 day Tue Tue Research Associate 1, Research $64.00
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Prof. Curran/Dr. Saunders, 2013, project template v2
Collection Method 19-
02-19
19-02-
19
Associate 2, Research Associate
3, Research Associate 4
Receive Funds for
Research 2 days
Wed
20-
02-19
Thu
21-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$128.00
Mid Term Review 0 days
Thu
21-
02-19
Thu
21-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate
4,Conveyance[0]
$0.00
Research Initiation and
Execution 70 days
Fri
22-
02-19
Thu
30-05-
19
$3,650.0
0
Gather Online and
Physical Resources that will
Aid the Research
4 days
Fri
22-
02-19
Wed
27-02-
19
Research Associate 1, Research
Associate 3, Research
Resources[1]
$628.00
Get Access to Online
Literature Database 1 day
Thu
28-
02-19
Thu
28-02-
19
Online Resources[1], Research
Associate 2, Research Associate
4
$282.00
Collect Literature
Samples Related to Research
Topic
2 days
Fri
01-
03-19
Mon
04-03-
19
Research Associate 1, Research
Associate 4 $64.00
Conduct Literature
Review 6 days
Tue
05-
03-19
Tue
12-03-
19
Research Associate 1, Research
Associate 4 $192.00
Collect Necessary Data
from Literature 3 days
Wed
13-
03-19
Fri 15-
03-19
Research Associate 1, Research
Associate 4 $96.00
Develop an Overall
Framework of the Research
Problem
2 days
Mon
18-
03-19
Tue
19-03-
19
Research Associate 1, Research
Associate 4 $64.00
Develop Research
Hypothesis 1 day
Wed
20-
03-19
Wed
20-03-
19
Research Associate 1, Research
Associate 4 $32.00
Start Data Collection 1 day
Thu
21-
03-19
Thu
21-03-
19
Research Associate 2, Research
Associate 3 $32.00
Set Up
Telecommunication Lab for
Experiment
5 days
Fri
22-
03-19
Thu
28-03-
19
Research Associate 2, Research
Associate 3, Research
Resources[1]
$660.00
Set Up 5G Cellular
Network 5 days
Fri
29-
03-19
Thu
04-04-
19
Research Associate 2, Research
Associate 3 $160.00
Collect Data from the
Network Analysis
15 days Fri
05-
Thu
25-04-
Research Associate 2, Research
Associate 3
$480.00
Collection Method 19-
02-19
19-02-
19
Associate 2, Research Associate
3, Research Associate 4
Receive Funds for
Research 2 days
Wed
20-
02-19
Thu
21-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$128.00
Mid Term Review 0 days
Thu
21-
02-19
Thu
21-02-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate
4,Conveyance[0]
$0.00
Research Initiation and
Execution 70 days
Fri
22-
02-19
Thu
30-05-
19
$3,650.0
0
Gather Online and
Physical Resources that will
Aid the Research
4 days
Fri
22-
02-19
Wed
27-02-
19
Research Associate 1, Research
Associate 3, Research
Resources[1]
$628.00
Get Access to Online
Literature Database 1 day
Thu
28-
02-19
Thu
28-02-
19
Online Resources[1], Research
Associate 2, Research Associate
4
$282.00
Collect Literature
Samples Related to Research
Topic
2 days
Fri
01-
03-19
Mon
04-03-
19
Research Associate 1, Research
Associate 4 $64.00
Conduct Literature
Review 6 days
Tue
05-
03-19
Tue
12-03-
19
Research Associate 1, Research
Associate 4 $192.00
Collect Necessary Data
from Literature 3 days
Wed
13-
03-19
Fri 15-
03-19
Research Associate 1, Research
Associate 4 $96.00
Develop an Overall
Framework of the Research
Problem
2 days
Mon
18-
03-19
Tue
19-03-
19
Research Associate 1, Research
Associate 4 $64.00
Develop Research
Hypothesis 1 day
Wed
20-
03-19
Wed
20-03-
19
Research Associate 1, Research
Associate 4 $32.00
Start Data Collection 1 day
Thu
21-
03-19
Thu
21-03-
19
Research Associate 2, Research
Associate 3 $32.00
Set Up
Telecommunication Lab for
Experiment
5 days
Fri
22-
03-19
Thu
28-03-
19
Research Associate 2, Research
Associate 3, Research
Resources[1]
$660.00
Set Up 5G Cellular
Network 5 days
Fri
29-
03-19
Thu
04-04-
19
Research Associate 2, Research
Associate 3 $160.00
Collect Data from the
Network Analysis
15 days Fri
05-
Thu
25-04-
Research Associate 2, Research
Associate 3
$480.00
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Prof. Curran/Dr. Saunders, 2013, project template v2
Experiment 04-19 19
Collect Data from Other
Sources 5 days
Fri
26-
04-19
Thu
02-05-
19
Research Associate 2, Research
Associate 3 $160.00
Start Data Analysis 5 days
Fri
03-
05-19
Thu
09-05-
19
Research Associate 2, Research
Associate 3 $160.00
Analyze All Collected
Data 5 days
Fri
10-
05-19
Thu
16-05-
19
Research Associate 2, Research
Associate 3 $160.00
Find Results 5 days
Fri
17-
05-19
Thu
23-05-
19
Research Associate 2, Research
Associate 3 $160.00
Verify or Contradict
Research Questions 2 days
Fri
24-
05-19
Mon
27-05-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$128.00
Develop Research
Outcome 2 days
Tue
28-
05-19
Wed
29-05-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$128.00
Set Scope and Base for
Future Research on 5G
Technology
1 day
Thu
30-
05-19
Thu
30-05-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Green Light Review 0 days
Thu
30-
05-19
Thu
30-05-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$0.00
Research Submission and
Closing 17 days
Fri
31-
05-19
Mon
24-06-
19
$1,424.0
0
Prepare Final Research
Report Based on the
Outcomes of the Research
15 days
Fri
31-
05-19
Thu
20-06-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$960.00
Submit the Report for
Grading 1 day
Fri
21-
06-19
Fri 21-
06-19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Get Suitable Grading for
the Research 1 day
Mon
24-
06-19
Mon
24-06-
19
Research Supervisor $400.00
Sign Off 0 days
Mon
24-
06-19
Mon
24-06-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4,
Research Supervisor
$0.00
The Gantt Chart is also shown in the following diagram.
Experiment 04-19 19
Collect Data from Other
Sources 5 days
Fri
26-
04-19
Thu
02-05-
19
Research Associate 2, Research
Associate 3 $160.00
Start Data Analysis 5 days
Fri
03-
05-19
Thu
09-05-
19
Research Associate 2, Research
Associate 3 $160.00
Analyze All Collected
Data 5 days
Fri
10-
05-19
Thu
16-05-
19
Research Associate 2, Research
Associate 3 $160.00
Find Results 5 days
Fri
17-
05-19
Thu
23-05-
19
Research Associate 2, Research
Associate 3 $160.00
Verify or Contradict
Research Questions 2 days
Fri
24-
05-19
Mon
27-05-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$128.00
Develop Research
Outcome 2 days
Tue
28-
05-19
Wed
29-05-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$128.00
Set Scope and Base for
Future Research on 5G
Technology
1 day
Thu
30-
05-19
Thu
30-05-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Green Light Review 0 days
Thu
30-
05-19
Thu
30-05-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$0.00
Research Submission and
Closing 17 days
Fri
31-
05-19
Mon
24-06-
19
$1,424.0
0
Prepare Final Research
Report Based on the
Outcomes of the Research
15 days
Fri
31-
05-19
Thu
20-06-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$960.00
Submit the Report for
Grading 1 day
Fri
21-
06-19
Fri 21-
06-19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4
$64.00
Get Suitable Grading for
the Research 1 day
Mon
24-
06-19
Mon
24-06-
19
Research Supervisor $400.00
Sign Off 0 days
Mon
24-
06-19
Mon
24-06-
19
Research Associate 1, Research
Associate 2, Research Associate
3, Research Associate 4,
Research Supervisor
$0.00
The Gantt Chart is also shown in the following diagram.
Prof. Curran/Dr. Saunders, 2013, project template v2
ID Task
Mode
WBS Task Name Duration Start Finish Predecessors Resource Names
0 0 Research Project on
Security Challenges of
5G Cellular Network
111 days Mon
21-01-19
Mon
24-06-19
1 1 Topic Selection and
Discussion
13 days Mon
21-01-19
Wed
06-02-19
2 1.1 Receive Instructions
Regarding Research
and Possible Field
of Topic
1 day Mon
21-01-19
Mon
21-01-19
Research
Supervisor
3 1.2 Select a Field of
Research
1 day Tue
22-01-19
Tue
22-01-19
2 Research
Associate
1,Research4 1.3 Choose a Number of
Topics on the
Selected Field
1 day Wed
23-01-19
Wed
23-01-19
3 Research
Associate
1,Research
Associate5 1.4 Consider the Scope
of the Topics
1 day Thu
24-01-19
Thu
24-01-19
4 Research
Associate
1,Research6 1.5 Test the Feasibility
of Topics Based on
Overall Scope of the
Research
1 day Fri
25-01-19
Fri
25-01-19
5 Research
Associate
1,Research
Associate7 1.6 Select a Particular
Research Topic
1 day Mon
28-01-19
Mon
28-01-19
6 Research
Associate
1,Research8 1.7 Receive Approval
from Supervisor
Regarding Selected
Topic
1 day Tue
29-01-19
Tue
29-01-19
7 Research
Associate
1,Research
Associate9 1.8 Prepare Research
Proposal
1 day Wed
30-01-19
Wed
30-01-19
8 Research
Associate
1,Research10 1.9 Submit Research
Proposal
5 days Thu
31-01-19
Wed
06-02-19
9 Research
Associate
1,Research11 1.10 Receive
Confirmation to
Proceed with the
Research
0 days Wed
06-02-19
Wed
06-02-19
10 Research
Supervisor
12 2 Research Planning 11 days Thu
07-02-19
Thu
21-02-19
13 2.1 Develop the Overall
Scope of the
Research
1 day Thu
07-02-19
Thu
07-02-19
11 Research
Associate
1,Research14 2.2 Develop a Work
Breakdown
Structure for the
Entire Research
1 day Fri
08-02-19
Fri
08-02-19
13 Research
Associate
1,Research
Associate15 2.3 Develop a Research
Schedule Using
Gantt Chart
1 day Mon
11-02-19
Mon
11-02-19
14 Research
Associate
1,Research
Associate16 2.4 Allocate Duties to
the Team Members
1 day Tue
12-02-19
Tue
12-02-19
15 Research
Associate
1,Research17 2.5 Prepare Resource Plan2 days Wed 13-02-19Thu 14-02-1916 Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
18 2.6 Request Funding for
the Research Based
on Estimation of
Requirements
1 day Fri
15-02-19
Fri
15-02-19
17 Research
Associate
1,Research
Associate
2,Research19 2.7 Determine Research
Roadmap and
Methodology to be
Followed
0.5 days Mon
18-02-19
Mon
18-02-19
18 Research
Associate
1,Research
Associate
2,Research20 2.8 Determine Research
Approach
0.5 days Mon
18-02-19
Mon
18-02-19
19 Research
Associate
1,Research21 2.9 Determine Data
Collection Method
1 day Tue
19-02-19
Tue
19-02-19
20 Research
Associate
1,Research22 2.10 Receive Funds for
Research
2 days Wed
20-02-19
Thu
21-02-19
21 Research
Associate
1,Research23 2.11 Proceed to Research 0 days Thu 21-02-19Thu 21-02-1922 Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4,Conveyance[0]
24 3 Research Initiation
and Execution
70 days Fri
22-02-19
Thu
30-05-19
25 3.1 Gather Online and
Physical Resources
that will Aid the
Research
4 days Fri
22-02-19
Wed
27-02-19
23 Research
Associate
1,Research
Associate26 3.2 Get Access to
Online Literature
Database
1 day Thu
28-02-19
Thu
28-02-19
25 Online
Resources[1],Research
Associate27 3.3 Collect Literature
Samples Related to
Research Topic
2 days Fri
01-03-19
Mon
04-03-19
26 Research
Associate
1,Research
Associate 428 3.4 Conduct Literature
Review
6 days Tue
05-03-19
Tue
12-03-19
27 Research
Associate
1,Research29 3.5 Collect Necessary
Data from Literature
3 days Wed
13-03-19
Fri
15-03-19
28 Research
Associate
1,Research30 3.6 Develop an Overall
Framework of the
Research Problem
2 days Mon
18-03-19
Tue
19-03-19
29 Research
Associate
1,Research
Associate 431 3.7 Develop Research
Hypothesis
1 day Wed
20-03-19
Wed
20-03-19
30 Research
Associate
1,Research32 3.8 Start Data Collection 1 day Thu 21-03-19Thu 21-03-1931 Research Associate 2,Research Associate 3
33 3.9 Set Up
Telecommunication
Lab for Experiment
5 days Fri
22-03-19
Thu
28-03-19
32 Research
Associate
2,Research
Associate34 3.10 Set Up 5G Cellular
Network
5 days Fri
29-03-19
Thu
04-04-19
33 Research
Associate
2,Research35 3.11 Collect Data from
the Network
Analysis Experiment
15 days Fri
05-04-19
Thu
25-04-19
34 Research
Associate
2,Research
Associate 336 3.12 Collect Data from
Other Sources
5 days Fri
26-04-19
Thu
02-05-19
35 Research
Associate
2,Research37 3.13 Start Data Analysis 5 days Fri 03-05-19Thu 09-05-1936 Research Associate 2,Research Associate 3
38 3.14 Analyze All
Collected Data
5 days Fri
10-05-19
Thu
16-05-19
37 Research
Associate
2,Research39 3.15 Find Results 5 days Fri 17-05-19Thu 23-05-1938 Research Associate 2,Research Associate 3
40 3.16 Verify or Contradict
Research Questions
2 days Fri
24-05-19
Mon
27-05-19
39 Research
Associate
1,Research41 3.17 Develop Research
Outcome
2 days Tue
28-05-19
Wed
29-05-19
40 Research
Associate
1,Research42 3.18 Set Scope and Base
for Future Research
on 5G Technology
1 day Thu
30-05-19
Thu
30-05-19
41 Research
Associate
1,Research
Associate43 3.19 Complete the
Research Process
0 days Thu
30-05-19
Thu
30-05-19
42 Research
Associate
1,Research44 4 Research Submission
and Closing
17 days Fri
31-05-19
Mon
24-06-19
45 4.1 Prepare Final
Research Report
Based on the
Outcomes of the
15 days Fri
31-05-19
Thu
20-06-19
43 Research
Associate
1,Research
Associate46 4.2 Submit the Report
for Grading
1 day Fri
21-06-19
Fri
21-06-19
45 Research
Associate
1,Research47 4.3 Get Suitable
Grading for the
Research
1 day Mon
24-06-19
Mon
24-06-19
46 Research
Supervisor
48 4.4 Sign Off 0 days Mon 24-06-19Mon 24-06-1947 Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4,Research Supervisor
Research Supervisor
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
06-02
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
21-02
Research Associate 1,Research Associate 3,Research Resources[1]
Online Resources[1],Research Associate 2,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3,Research Resources[1]
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 1,Research Associate 2,Research Associate
Research Associate 1,Research Associate 2,Research Associat
Research Associate 1,Research Associate 2,Research Associat
30-05
Research Associate 1,Research Associate 2,Researc
Research Associate 1,Research Associate 2,Resear
Research Supervisor
24-06
S S M T W T F S S M T W
23 Dec '18 27 Jan '19 03 Mar '19 07 Apr '19 12 May '19 16 Jun '19
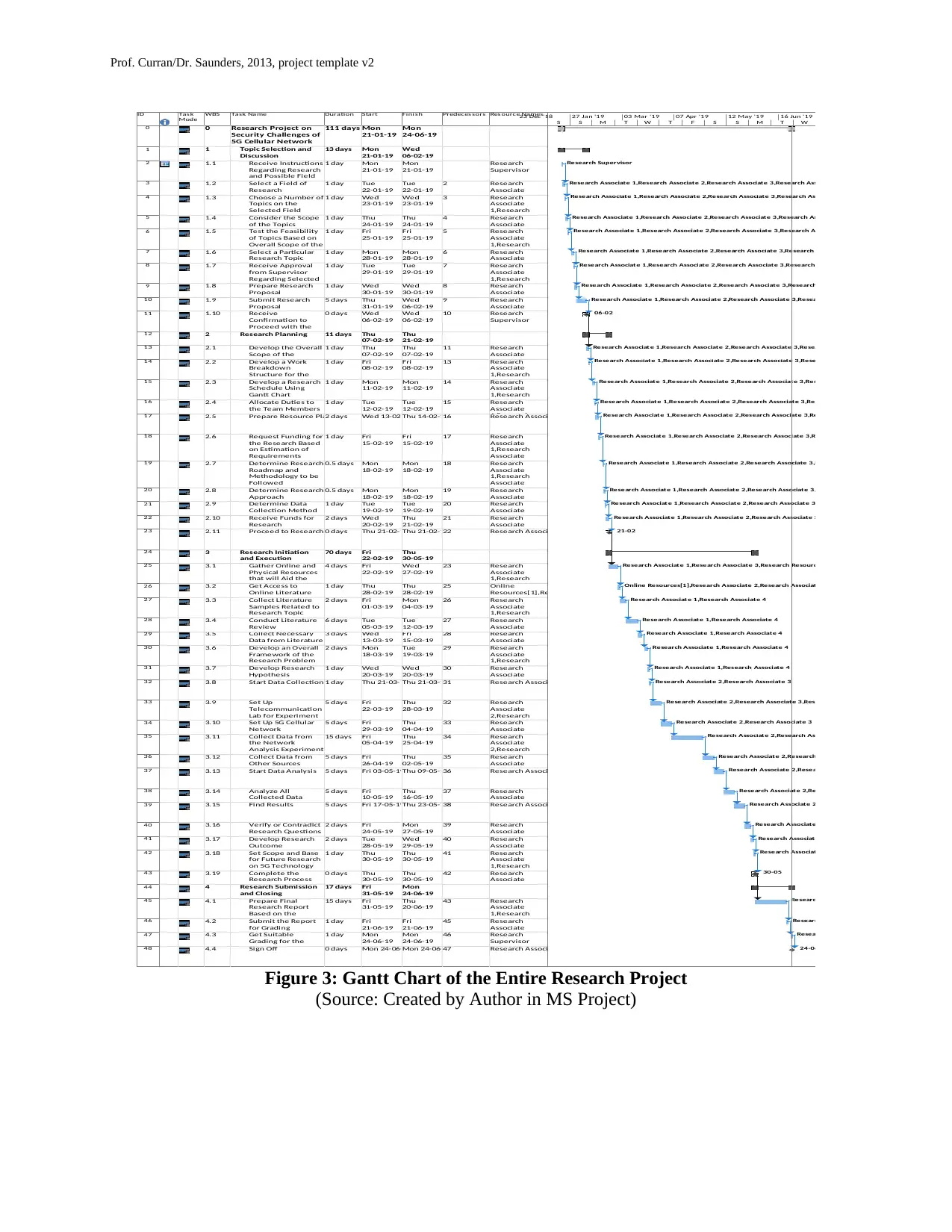
Figure 3: Gantt Chart of the Entire Research Project
(Source: Created by Author in MS Project)
ID Task
Mode
WBS Task Name Duration Start Finish Predecessors Resource Names
0 0 Research Project on
Security Challenges of
5G Cellular Network
111 days Mon
21-01-19
Mon
24-06-19
1 1 Topic Selection and
Discussion
13 days Mon
21-01-19
Wed
06-02-19
2 1.1 Receive Instructions
Regarding Research
and Possible Field
of Topic
1 day Mon
21-01-19
Mon
21-01-19
Research
Supervisor
3 1.2 Select a Field of
Research
1 day Tue
22-01-19
Tue
22-01-19
2 Research
Associate
1,Research4 1.3 Choose a Number of
Topics on the
Selected Field
1 day Wed
23-01-19
Wed
23-01-19
3 Research
Associate
1,Research
Associate5 1.4 Consider the Scope
of the Topics
1 day Thu
24-01-19
Thu
24-01-19
4 Research
Associate
1,Research6 1.5 Test the Feasibility
of Topics Based on
Overall Scope of the
Research
1 day Fri
25-01-19
Fri
25-01-19
5 Research
Associate
1,Research
Associate7 1.6 Select a Particular
Research Topic
1 day Mon
28-01-19
Mon
28-01-19
6 Research
Associate
1,Research8 1.7 Receive Approval
from Supervisor
Regarding Selected
Topic
1 day Tue
29-01-19
Tue
29-01-19
7 Research
Associate
1,Research
Associate9 1.8 Prepare Research
Proposal
1 day Wed
30-01-19
Wed
30-01-19
8 Research
Associate
1,Research10 1.9 Submit Research
Proposal
5 days Thu
31-01-19
Wed
06-02-19
9 Research
Associate
1,Research11 1.10 Receive
Confirmation to
Proceed with the
Research
0 days Wed
06-02-19
Wed
06-02-19
10 Research
Supervisor
12 2 Research Planning 11 days Thu
07-02-19
Thu
21-02-19
13 2.1 Develop the Overall
Scope of the
Research
1 day Thu
07-02-19
Thu
07-02-19
11 Research
Associate
1,Research14 2.2 Develop a Work
Breakdown
Structure for the
Entire Research
1 day Fri
08-02-19
Fri
08-02-19
13 Research
Associate
1,Research
Associate15 2.3 Develop a Research
Schedule Using
Gantt Chart
1 day Mon
11-02-19
Mon
11-02-19
14 Research
Associate
1,Research
Associate16 2.4 Allocate Duties to
the Team Members
1 day Tue
12-02-19
Tue
12-02-19
15 Research
Associate
1,Research17 2.5 Prepare Resource Plan2 days Wed 13-02-19Thu 14-02-1916 Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
18 2.6 Request Funding for
the Research Based
on Estimation of
Requirements
1 day Fri
15-02-19
Fri
15-02-19
17 Research
Associate
1,Research
Associate
2,Research19 2.7 Determine Research
Roadmap and
Methodology to be
Followed
0.5 days Mon
18-02-19
Mon
18-02-19
18 Research
Associate
1,Research
Associate
2,Research20 2.8 Determine Research
Approach
0.5 days Mon
18-02-19
Mon
18-02-19
19 Research
Associate
1,Research21 2.9 Determine Data
Collection Method
1 day Tue
19-02-19
Tue
19-02-19
20 Research
Associate
1,Research22 2.10 Receive Funds for
Research
2 days Wed
20-02-19
Thu
21-02-19
21 Research
Associate
1,Research23 2.11 Proceed to Research 0 days Thu 21-02-19Thu 21-02-1922 Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4,Conveyance[0]
24 3 Research Initiation
and Execution
70 days Fri
22-02-19
Thu
30-05-19
25 3.1 Gather Online and
Physical Resources
that will Aid the
Research
4 days Fri
22-02-19
Wed
27-02-19
23 Research
Associate
1,Research
Associate26 3.2 Get Access to
Online Literature
Database
1 day Thu
28-02-19
Thu
28-02-19
25 Online
Resources[1],Research
Associate27 3.3 Collect Literature
Samples Related to
Research Topic
2 days Fri
01-03-19
Mon
04-03-19
26 Research
Associate
1,Research
Associate 428 3.4 Conduct Literature
Review
6 days Tue
05-03-19
Tue
12-03-19
27 Research
Associate
1,Research29 3.5 Collect Necessary
Data from Literature
3 days Wed
13-03-19
Fri
15-03-19
28 Research
Associate
1,Research30 3.6 Develop an Overall
Framework of the
Research Problem
2 days Mon
18-03-19
Tue
19-03-19
29 Research
Associate
1,Research
Associate 431 3.7 Develop Research
Hypothesis
1 day Wed
20-03-19
Wed
20-03-19
30 Research
Associate
1,Research32 3.8 Start Data Collection 1 day Thu 21-03-19Thu 21-03-1931 Research Associate 2,Research Associate 3
33 3.9 Set Up
Telecommunication
Lab for Experiment
5 days Fri
22-03-19
Thu
28-03-19
32 Research
Associate
2,Research
Associate34 3.10 Set Up 5G Cellular
Network
5 days Fri
29-03-19
Thu
04-04-19
33 Research
Associate
2,Research35 3.11 Collect Data from
the Network
Analysis Experiment
15 days Fri
05-04-19
Thu
25-04-19
34 Research
Associate
2,Research
Associate 336 3.12 Collect Data from
Other Sources
5 days Fri
26-04-19
Thu
02-05-19
35 Research
Associate
2,Research37 3.13 Start Data Analysis 5 days Fri 03-05-19Thu 09-05-1936 Research Associate 2,Research Associate 3
38 3.14 Analyze All
Collected Data
5 days Fri
10-05-19
Thu
16-05-19
37 Research
Associate
2,Research39 3.15 Find Results 5 days Fri 17-05-19Thu 23-05-1938 Research Associate 2,Research Associate 3
40 3.16 Verify or Contradict
Research Questions
2 days Fri
24-05-19
Mon
27-05-19
39 Research
Associate
1,Research41 3.17 Develop Research
Outcome
2 days Tue
28-05-19
Wed
29-05-19
40 Research
Associate
1,Research42 3.18 Set Scope and Base
for Future Research
on 5G Technology
1 day Thu
30-05-19
Thu
30-05-19
41 Research
Associate
1,Research
Associate43 3.19 Complete the
Research Process
0 days Thu
30-05-19
Thu
30-05-19
42 Research
Associate
1,Research44 4 Research Submission
and Closing
17 days Fri
31-05-19
Mon
24-06-19
45 4.1 Prepare Final
Research Report
Based on the
Outcomes of the
15 days Fri
31-05-19
Thu
20-06-19
43 Research
Associate
1,Research
Associate46 4.2 Submit the Report
for Grading
1 day Fri
21-06-19
Fri
21-06-19
45 Research
Associate
1,Research47 4.3 Get Suitable
Grading for the
Research
1 day Mon
24-06-19
Mon
24-06-19
46 Research
Supervisor
48 4.4 Sign Off 0 days Mon 24-06-19Mon 24-06-1947 Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4,Research Supervisor
Research Supervisor
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
06-02
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
Research Associate 1,Research Associate 2,Research Associate 3,Research Associate 4
21-02
Research Associate 1,Research Associate 3,Research Resources[1]
Online Resources[1],Research Associate 2,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3,Research Resources[1]
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 1,Research Associate 2,Research Associate
Research Associate 1,Research Associate 2,Research Associat
Research Associate 1,Research Associate 2,Research Associat
30-05
Research Associate 1,Research Associate 2,Researc
Research Associate 1,Research Associate 2,Resear
Research Supervisor
24-06
S S M T W T F S S M T W
23 Dec '18 27 Jan '19 03 Mar '19 07 Apr '19 12 May '19 16 Jun '19
Figure 3: Gantt Chart of the Entire Research Project
(Source: Created by Author in MS Project)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Prof. Curran/Dr. Saunders, 2013, project template v2
ID Task
Mode
WBS Task Name Duration Start
24 3 Research Initiation
and Execution
70 days Fri
22-02-19
25 3.1 Gather Online and
Physical Resources
that will Aid the
Research
4 days Fri
22-02-19
26 3.2 Get Access to
Online Literature
Database
1 day Thu
28-02-19
27 3.3 Collect Literature
Samples Related to
Research Topic
2 days Fri
01-03-19
28 3.4 Conduct Literature
Review
6 days Tue
05-03-19
29 3.5 Collect Necessary
Data from Literature
3 days Wed
13-03-19
30 3.6 Develop an Overall
Framework of the
Research Problem
2 days Mon
18-03-19
31 3.7 Develop Research
Hypothesis
1 day Wed
20-03-19
32 3.8 Start Data Collection 1 day Thu 21-03-19
33 3.9 Set Up
Telecommunication
Lab for Experiment
5 days Fri
22-03-19
34 3.10 Set Up 5G Cellular
Network
5 days Fri
29-03-19
35 3.11 Collect Data from
the Network
Analysis Experiment
15 days Fri
05-04-19
36 3.12 Collect Data from
Other Sources
5 days Fri
26-04-19
37 3.13 Start Data Analysis 5 days Fri 03-05-19
38 3.14 Analyze All
Collected Data
5 days Fri
10-05-19
39 3.15 Find Results 5 days Fri 17-05-19
40 3.16 Verify or Contradict
Research Questions
2 days Fri
24-05-19
41 3.17 Develop Research
Outcome
2 days Tue
28-05-19
42 3.18 Set Scope and Base
for Future Research
on 5G Technology
1 day Thu
30-05-19
43 3.19 Complete the
Research Process
0 days Thu
30-05-19
Research Associate 1,Research Associate 3,Research Resources[1]
Online Resources[1],Research Associate 2,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3,Research Resource
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 2,Research Associat
Research Associate 2,Research Asso
Research Associate 1,Research Ass
Research Associate 1,Research As
Research Associate 1,Research A
30-05
M T W T F S S M T
27 Jan '19 03 Mar '19 07 Apr '19 12 May '19 16 Jun '19
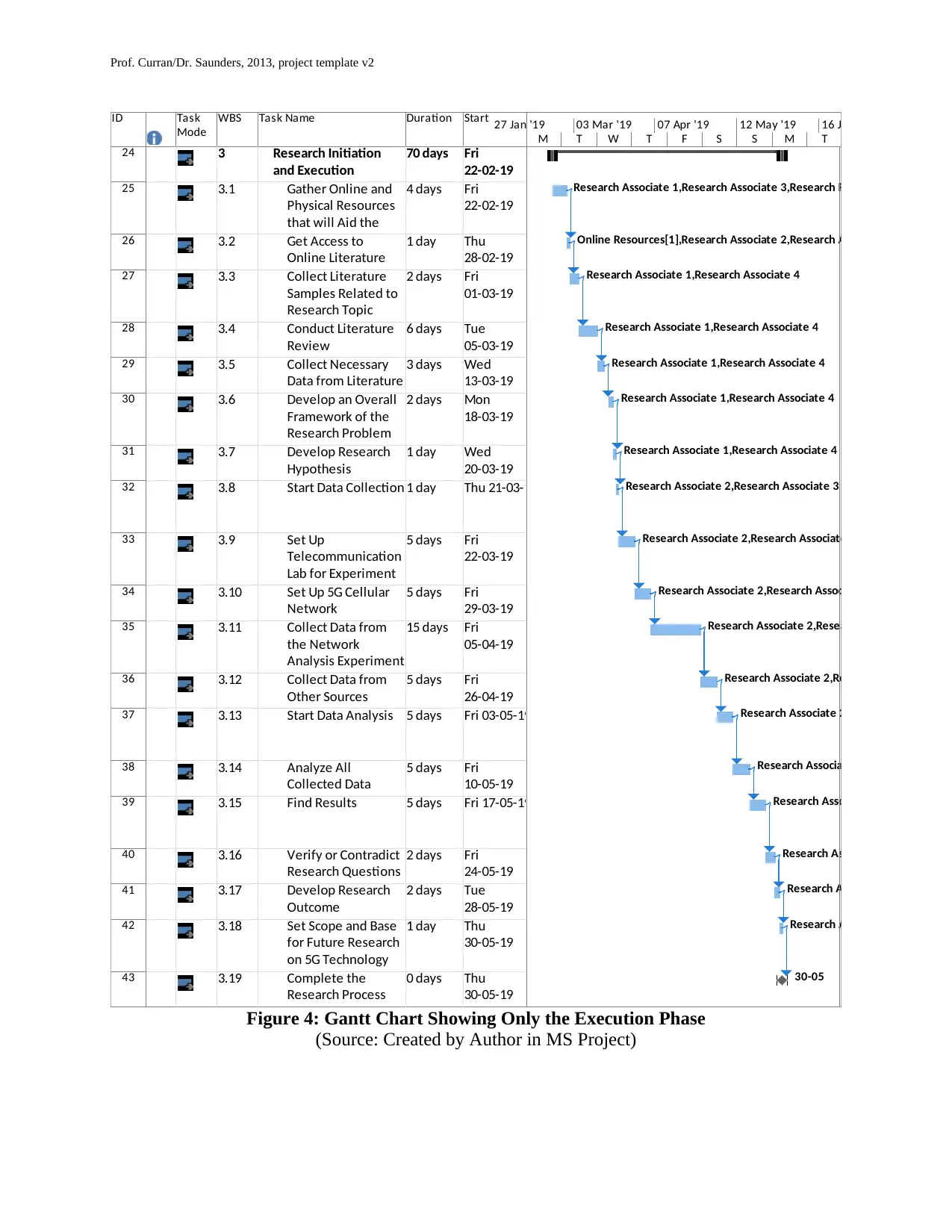
Figure 4: Gantt Chart Showing Only the Execution Phase
(Source: Created by Author in MS Project)
ID Task
Mode
WBS Task Name Duration Start
24 3 Research Initiation
and Execution
70 days Fri
22-02-19
25 3.1 Gather Online and
Physical Resources
that will Aid the
Research
4 days Fri
22-02-19
26 3.2 Get Access to
Online Literature
Database
1 day Thu
28-02-19
27 3.3 Collect Literature
Samples Related to
Research Topic
2 days Fri
01-03-19
28 3.4 Conduct Literature
Review
6 days Tue
05-03-19
29 3.5 Collect Necessary
Data from Literature
3 days Wed
13-03-19
30 3.6 Develop an Overall
Framework of the
Research Problem
2 days Mon
18-03-19
31 3.7 Develop Research
Hypothesis
1 day Wed
20-03-19
32 3.8 Start Data Collection 1 day Thu 21-03-19
33 3.9 Set Up
Telecommunication
Lab for Experiment
5 days Fri
22-03-19
34 3.10 Set Up 5G Cellular
Network
5 days Fri
29-03-19
35 3.11 Collect Data from
the Network
Analysis Experiment
15 days Fri
05-04-19
36 3.12 Collect Data from
Other Sources
5 days Fri
26-04-19
37 3.13 Start Data Analysis 5 days Fri 03-05-19
38 3.14 Analyze All
Collected Data
5 days Fri
10-05-19
39 3.15 Find Results 5 days Fri 17-05-19
40 3.16 Verify or Contradict
Research Questions
2 days Fri
24-05-19
41 3.17 Develop Research
Outcome
2 days Tue
28-05-19
42 3.18 Set Scope and Base
for Future Research
on 5G Technology
1 day Thu
30-05-19
43 3.19 Complete the
Research Process
0 days Thu
30-05-19
Research Associate 1,Research Associate 3,Research Resources[1]
Online Resources[1],Research Associate 2,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 1,Research Associate 4
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3,Research Resource
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 2,Research Associate 3
Research Associate 2,Research Associat
Research Associate 2,Research Asso
Research Associate 1,Research Ass
Research Associate 1,Research As
Research Associate 1,Research A
30-05
M T W T F S S M T
27 Jan '19 03 Mar '19 07 Apr '19 12 May '19 16 Jun '19
Figure 4: Gantt Chart Showing Only the Execution Phase
(Source: Created by Author in MS Project)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Prof. Curran/Dr. Saunders, 2013, project template v2
8. Conclusions
From the overall discussion of the research, it can be said that 5G cellular network is a vast topic
that has numerous aspects to be researched. Due to academic limitations, this particular research
is specific to the security challenges of the 5G network and it will set the stage for further
research on the selected field. In addition, telecommunication is constantly evolving and hence,
there will be even more research topics on the cellular networks when the 5G technology will be
replaced by 6G, 7G and so on.
8. Conclusions
From the overall discussion of the research, it can be said that 5G cellular network is a vast topic
that has numerous aspects to be researched. Due to academic limitations, this particular research
is specific to the security challenges of the 5G network and it will set the stage for further
research on the selected field. In addition, telecommunication is constantly evolving and hence,
there will be even more research topics on the cellular networks when the 5G technology will be
replaced by 6G, 7G and so on.

Prof. Curran/Dr. Saunders, 2013, project template v2
9. References
Agiwal, M., Roy, A. and Saxena, N., (2016), 'Next Generation 5G Wireless Networks: A
Comprehensive Survey', IEEE Communications Surveys and Tutorials, vol. 18, no. 3, pp. 1617-
55.
Bai, T. and Heath, R.W., (2015), 'Coverage and Rate Analysis for Millimeter-Wave Cellular
Networks', IEEE Transactions on Wireless Communications, vol. 14, no. 2, pp. 1100-14.
Benisha, M., Prabu, R.T. and Bai, V.T., (2016), 'Requirements and challenges of 5G cellular
systems', 2016 2nd International Conference on Advances in Electrical, Electronics, Information,
Communication and Bio-Informatics (AEEICB), pp. 251-4.
Chopra, G., Jain, S. and Jha, R.K., (2018), 'Possible Security Attack Modeling in Ultradense
Networks Using High-Speed Handover Management', IEEE Transactions on Vehicular
Technology, vol. 67, no. 3, pp. 2178-92.
Chopra, G., Jha, R.K. and Jain, S., (2018), 'Security issues in ultra dense network for 5G
scenario', 2018 10th International Conference on Communication Systems and Networks
(COMSNETS), pp. 510-2.
Duan, X. and Wang, X., (2015), 'Authentication handover and privacy protection in 5G hetnets
using software-defined networking', IEEE Communications Magazine, vol. 53, no. 4, pp. 28-35.
Dutta, S., Mezzavilla, M., Ford, R., Zhang, M., Rangan, S. and Zorzi, M., (2017), 'Frame
Structure Design and Analysis for Millimeter Wave Cellular Systems', IEEE Transactions on
Wireless Communications, vol. 16, no. 3, pp. 1508-22.
Hossain, E. and Hasan, M., (2015), '5G cellular: key enabling technologies and research
challenges', IEEE Instrumentation and Measurement Magazine, vol. 18, no. 3, pp. 11-21.
Hsiao, W. and Huang, C., (2016), 'Multipath division multiple access for 5G cellular system
based on massive antennas in millimeter wave band', 2016 18th International Conference on
Advanced Communication Technology (ICACT), pp. 741-6.
Li, Q.C., Niu, H., Papathanassiou, A.T. and Wu, G., (2014), '5G Network Capacity: Key
Elements and Technologies', IEEE Vehicular Technology Magazine, vol. 9, no. 1, pp. 71-8.
Mehmood, Y., Afzal, W., Ahmad, F., Younas, U., Rashid, I. and Mehmood, I. 2013, 'Large
scaled multi-user MIMO system so called massive MIMO systems for future wireless
communication networks', 2013 19th International Conference on Automation and Computing,
pp. 1-4.
Qingtian, X., Bo, L., Xiaoya, Z., Zhongjiang, Y. and Mao, Y., (2016), 'Cell capacity for 5G
cellular network with inter-beam interference', 2016 IEEE International Conference on Signal
Processing, Communications and Computing (ICSPCC), pp. 1-5.
9. References
Agiwal, M., Roy, A. and Saxena, N., (2016), 'Next Generation 5G Wireless Networks: A
Comprehensive Survey', IEEE Communications Surveys and Tutorials, vol. 18, no. 3, pp. 1617-
55.
Bai, T. and Heath, R.W., (2015), 'Coverage and Rate Analysis for Millimeter-Wave Cellular
Networks', IEEE Transactions on Wireless Communications, vol. 14, no. 2, pp. 1100-14.
Benisha, M., Prabu, R.T. and Bai, V.T., (2016), 'Requirements and challenges of 5G cellular
systems', 2016 2nd International Conference on Advances in Electrical, Electronics, Information,
Communication and Bio-Informatics (AEEICB), pp. 251-4.
Chopra, G., Jain, S. and Jha, R.K., (2018), 'Possible Security Attack Modeling in Ultradense
Networks Using High-Speed Handover Management', IEEE Transactions on Vehicular
Technology, vol. 67, no. 3, pp. 2178-92.
Chopra, G., Jha, R.K. and Jain, S., (2018), 'Security issues in ultra dense network for 5G
scenario', 2018 10th International Conference on Communication Systems and Networks
(COMSNETS), pp. 510-2.
Duan, X. and Wang, X., (2015), 'Authentication handover and privacy protection in 5G hetnets
using software-defined networking', IEEE Communications Magazine, vol. 53, no. 4, pp. 28-35.
Dutta, S., Mezzavilla, M., Ford, R., Zhang, M., Rangan, S. and Zorzi, M., (2017), 'Frame
Structure Design and Analysis for Millimeter Wave Cellular Systems', IEEE Transactions on
Wireless Communications, vol. 16, no. 3, pp. 1508-22.
Hossain, E. and Hasan, M., (2015), '5G cellular: key enabling technologies and research
challenges', IEEE Instrumentation and Measurement Magazine, vol. 18, no. 3, pp. 11-21.
Hsiao, W. and Huang, C., (2016), 'Multipath division multiple access for 5G cellular system
based on massive antennas in millimeter wave band', 2016 18th International Conference on
Advanced Communication Technology (ICACT), pp. 741-6.
Li, Q.C., Niu, H., Papathanassiou, A.T. and Wu, G., (2014), '5G Network Capacity: Key
Elements and Technologies', IEEE Vehicular Technology Magazine, vol. 9, no. 1, pp. 71-8.
Mehmood, Y., Afzal, W., Ahmad, F., Younas, U., Rashid, I. and Mehmood, I. 2013, 'Large
scaled multi-user MIMO system so called massive MIMO systems for future wireless
communication networks', 2013 19th International Conference on Automation and Computing,
pp. 1-4.
Qingtian, X., Bo, L., Xiaoya, Z., Zhongjiang, Y. and Mao, Y., (2016), 'Cell capacity for 5G
cellular network with inter-beam interference', 2016 IEEE International Conference on Signal
Processing, Communications and Computing (ICSPCC), pp. 1-5.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





