Cybersecurity Threats and Mitigation Strategies
VerifiedAdded on 2020/05/28
|10
|3551
|91
AI Summary
The assignment delves into the multifaceted world of cybersecurity, examining prevalent cyber threats such as phishing, malware, DDoS attacks, and SQL injection. It analyzes the vulnerabilities associated with social networking websites, UAVs, and information systems. Furthermore, it discusses the growing challenge of ransomware, the security implications of password attacks, and the need for robust authentication methods. The document highlights mitigation strategies like firewalls, secure coding practices, and awareness training to combat these threats effectively.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: IT MANAGEMENT-CYBER SECURITY
IT Management-Cyber Security
Name of the Student
Name of the University
Author Note
IT Management-Cyber Security
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
IT MANAGEMENT-CYBER SECURITY
Table of Contents
Executive Summary.............................................................................................................2
Risk Assessment..................................................................................................................3
Risk Register....................................................................................................................3
Protection mechanism..........................................................................................................7
References............................................................................................................................8
IT MANAGEMENT-CYBER SECURITY
Table of Contents
Executive Summary.............................................................................................................2
Risk Assessment..................................................................................................................3
Risk Register....................................................................................................................3
Protection mechanism..........................................................................................................7
References............................................................................................................................8

2
IT MANAGEMENT-CYBER SECURITY
Executive Summary
As an IT risk assessment, lead consultant for Gigantic Corporation for cyber security. The
organization deals with many online activities including regular data back up in cloud.
Therefore, it becomes utmost essential to take proper measures in ensuring proper online security
and privacy of all the systems within running within the organization. This includes protection of
information privacy of the employees as well. The project deals with the development of proper
plan in order to implement the security system across the organization. The project is complex,
as every associated risk lingering over the present systems of the organization is needed to be
identified and mitigated. The report discusses the possible threats the system could face due to
their online operations. Assessment of the identified risks is provided in the report along with the
recommendations for risk mitigation. The IT risk assessment report consists of the details of the
threats; the systems are exposed to along with the proper evaluation of the risks. The project
aims at developing a secure system within the organization and therefore, proper risk evaluation
strategy is necessary. The project can only be successful if the systems of the Gigantic
Corporation are deployed with proper intrusion detection system. In order to design an effective
intrusion detection system, it becomes utmost necessary to identify and evaluate all the possible
risks associated with the system. Ensuring cyber security in an organization is a complex task. It
starts with proper identification of the domain or the areas of vulnerability, understanding the
vectors, tools and mechanism of exploitation and their resulting impact on a system. Proper
analysis of these factors helps in proper identification of associated risks in a system. The
identified risks then should be properly management in order to successfully complete the
project that deals with establishment of secure network and computer devices within the
organization. However, this needs a proper plan and a considerable amount of time in order to
evaluate properly the threat agents and the outcome of the threats associated with the systems
installed within an organization. One of the biggest threats that every organizations are exposed
to is an insider threat. It is a major concern because threat insider is difficult to detect and
therefore the cyber crimes from an insider threat is more costly and damaging from an external
threat. Those employees of the organization, who have an access to the secure and confidential
data of the organization, can only carry out insider security breach. The outside threats include
compromising the systems or the network by the cyber criminals. One of the prominent external
attacks in the organization is phishing. It is a targeted attack and a fraudulent practice of sending
spam emails to the different individuals with an aim of revealing their personal information. The
report is mainly based on the risk assessment matrix that is identified for the systems and the
network of Gigantic Corporation. The different types of vulnerabilities and the threats in the
system are identified so that it can be eliminated from the system. The report further discusses
the different protection mechanisms that can be employed within the organization in order to
ensure proper security of the data.
IT MANAGEMENT-CYBER SECURITY
Executive Summary
As an IT risk assessment, lead consultant for Gigantic Corporation for cyber security. The
organization deals with many online activities including regular data back up in cloud.
Therefore, it becomes utmost essential to take proper measures in ensuring proper online security
and privacy of all the systems within running within the organization. This includes protection of
information privacy of the employees as well. The project deals with the development of proper
plan in order to implement the security system across the organization. The project is complex,
as every associated risk lingering over the present systems of the organization is needed to be
identified and mitigated. The report discusses the possible threats the system could face due to
their online operations. Assessment of the identified risks is provided in the report along with the
recommendations for risk mitigation. The IT risk assessment report consists of the details of the
threats; the systems are exposed to along with the proper evaluation of the risks. The project
aims at developing a secure system within the organization and therefore, proper risk evaluation
strategy is necessary. The project can only be successful if the systems of the Gigantic
Corporation are deployed with proper intrusion detection system. In order to design an effective
intrusion detection system, it becomes utmost necessary to identify and evaluate all the possible
risks associated with the system. Ensuring cyber security in an organization is a complex task. It
starts with proper identification of the domain or the areas of vulnerability, understanding the
vectors, tools and mechanism of exploitation and their resulting impact on a system. Proper
analysis of these factors helps in proper identification of associated risks in a system. The
identified risks then should be properly management in order to successfully complete the
project that deals with establishment of secure network and computer devices within the
organization. However, this needs a proper plan and a considerable amount of time in order to
evaluate properly the threat agents and the outcome of the threats associated with the systems
installed within an organization. One of the biggest threats that every organizations are exposed
to is an insider threat. It is a major concern because threat insider is difficult to detect and
therefore the cyber crimes from an insider threat is more costly and damaging from an external
threat. Those employees of the organization, who have an access to the secure and confidential
data of the organization, can only carry out insider security breach. The outside threats include
compromising the systems or the network by the cyber criminals. One of the prominent external
attacks in the organization is phishing. It is a targeted attack and a fraudulent practice of sending
spam emails to the different individuals with an aim of revealing their personal information. The
report is mainly based on the risk assessment matrix that is identified for the systems and the
network of Gigantic Corporation. The different types of vulnerabilities and the threats in the
system are identified so that it can be eliminated from the system. The report further discusses
the different protection mechanisms that can be employed within the organization in order to
ensure proper security of the data.
3
IT MANAGEMENT-CYBER SECURITY
Risk Assessment
Assessment of risk is a systematic process that evaluates the potential risks involved
within an organization. It consists of overall processes and methods of identifying the present
hazards in an existing system. The identification and estimation of the different levels of risks
associated with a situation is a complex process and therefore, proper risk assessment plan is laid
out before the process initiation (Von Solms & Van Niekerk 2013). The risk assessment process
is divided into a number of stages, which includes identification of the hazards, accessing the
risks and putting all the control measures in place. Identification of the hazards includes analysis
of all the possible threats present in the system. The next stage includes accessing the risk. This
is needed in order to evaluate the probable effect of the identified risks into the system. After the
risk has been identified in the system and the network, it is essential to put control measures in
place, in order to mitigate the identified risks. The control measures or precautions ensure that no
data is lost from the system (O’Connell, 2012).
The online operations of the organization are subjected to a number of risks. The project
associated with the risk assessment includes identification, analyzing and evaluation of the risk.
Proper cyber security control must be ensured in order to eliminate the risk of attack into the
system. The project aims at developing a secure network within the organization along with
ensuring proper protection in the existing systems of the organization (Cherdantseva et al.,
2016). The development of the IT risk assessment report deals with the development of a risk
register for the identified risks (Jouini, Rabai & Aissa, 2014).
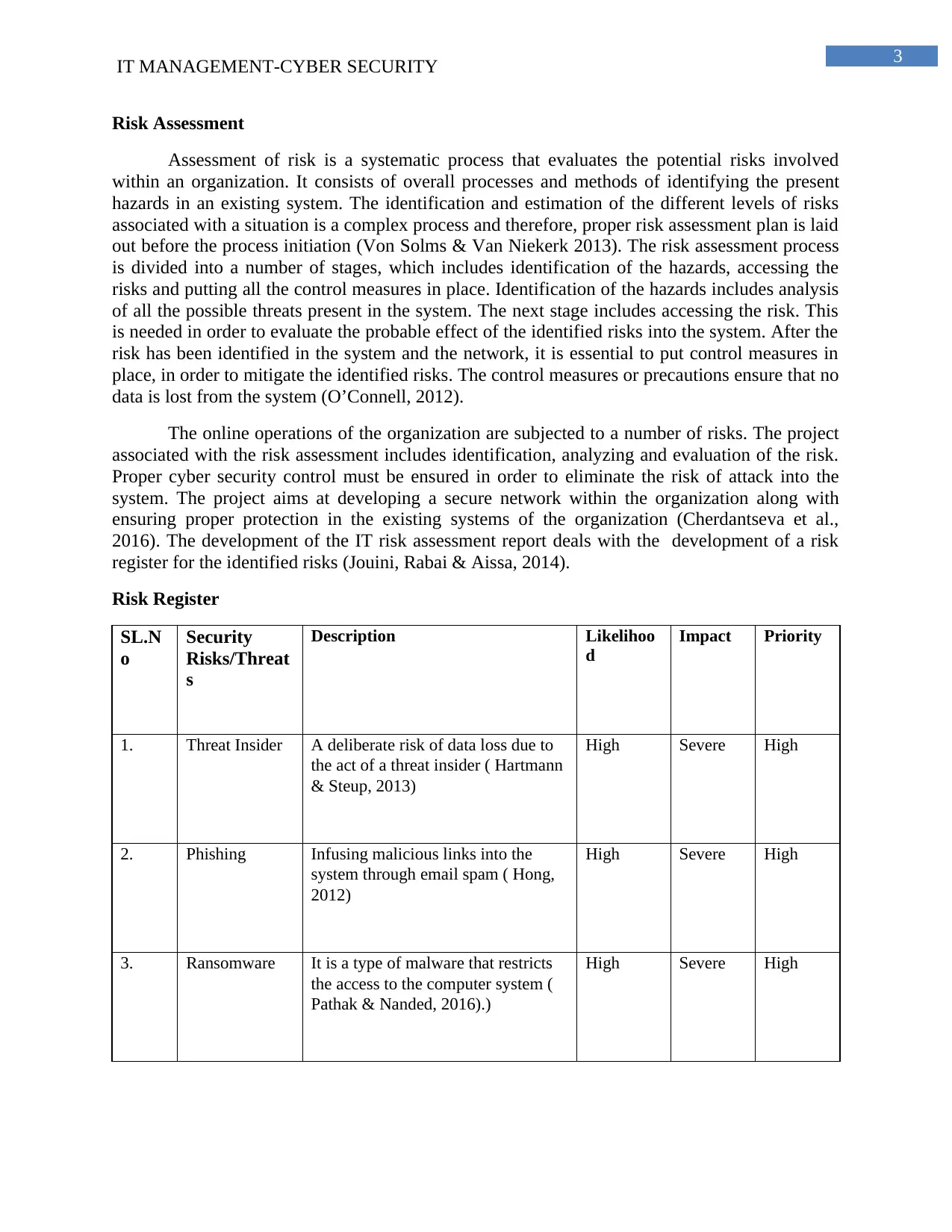
Risk Register
SL.N
o
Security
Risks/Threat
s
Description Likelihoo
d
Impact Priority
1. Threat Insider A deliberate risk of data loss due to
the act of a threat insider ( Hartmann
& Steup, 2013)
High Severe High
2. Phishing Infusing malicious links into the
system through email spam ( Hong,
2012)
High Severe High
3. Ransomware It is a type of malware that restricts
the access to the computer system (
Pathak & Nanded, 2016).)
High Severe High
IT MANAGEMENT-CYBER SECURITY
Risk Assessment
Assessment of risk is a systematic process that evaluates the potential risks involved
within an organization. It consists of overall processes and methods of identifying the present
hazards in an existing system. The identification and estimation of the different levels of risks
associated with a situation is a complex process and therefore, proper risk assessment plan is laid
out before the process initiation (Von Solms & Van Niekerk 2013). The risk assessment process
is divided into a number of stages, which includes identification of the hazards, accessing the
risks and putting all the control measures in place. Identification of the hazards includes analysis
of all the possible threats present in the system. The next stage includes accessing the risk. This
is needed in order to evaluate the probable effect of the identified risks into the system. After the
risk has been identified in the system and the network, it is essential to put control measures in
place, in order to mitigate the identified risks. The control measures or precautions ensure that no
data is lost from the system (O’Connell, 2012).
The online operations of the organization are subjected to a number of risks. The project
associated with the risk assessment includes identification, analyzing and evaluation of the risk.
Proper cyber security control must be ensured in order to eliminate the risk of attack into the
system. The project aims at developing a secure network within the organization along with
ensuring proper protection in the existing systems of the organization (Cherdantseva et al.,
2016). The development of the IT risk assessment report deals with the development of a risk
register for the identified risks (Jouini, Rabai & Aissa, 2014).
Risk Register
SL.N
o
Security
Risks/Threat
s
Description Likelihoo
d
Impact Priority
1. Threat Insider A deliberate risk of data loss due to
the act of a threat insider ( Hartmann
& Steup, 2013)
High Severe High
2. Phishing Infusing malicious links into the
system through email spam ( Hong,
2012)
High Severe High
3. Ransomware It is a type of malware that restricts
the access to the computer system (
Pathak & Nanded, 2016).)
High Severe High
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4
IT MANAGEMENT-CYBER SECURITY
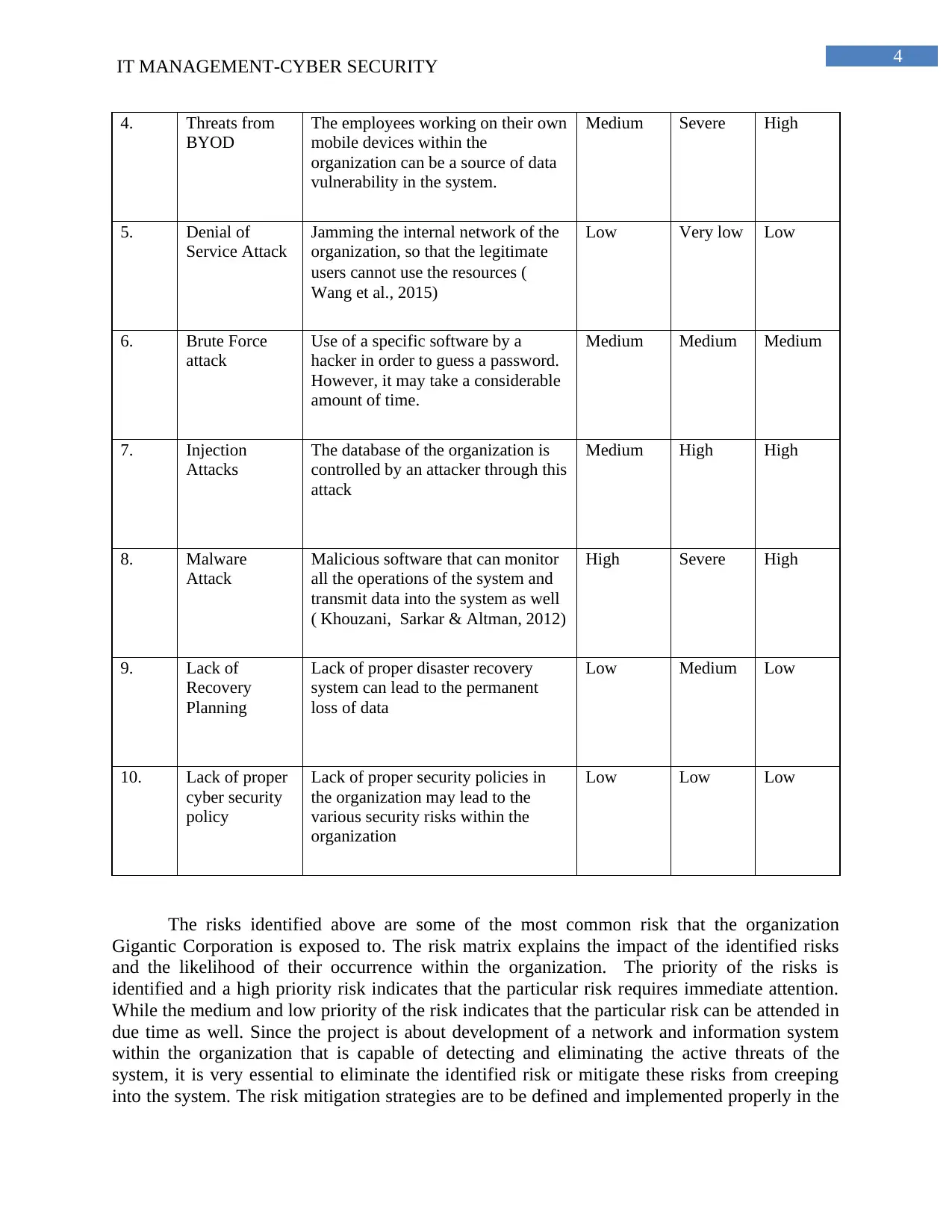
4. Threats from
BYOD
The employees working on their own
mobile devices within the
organization can be a source of data
vulnerability in the system.
Medium Severe High
5. Denial of
Service Attack
Jamming the internal network of the
organization, so that the legitimate
users cannot use the resources (
Wang et al., 2015)
Low Very low Low
6. Brute Force
attack
Use of a specific software by a
hacker in order to guess a password.
However, it may take a considerable
amount of time.
Medium Medium Medium
7. Injection
Attacks
The database of the organization is
controlled by an attacker through this
attack
Medium High High
8. Malware
Attack
Malicious software that can monitor
all the operations of the system and
transmit data into the system as well
( Khouzani, Sarkar & Altman, 2012)
High Severe High
9. Lack of
Recovery
Planning
Lack of proper disaster recovery
system can lead to the permanent
loss of data
Low Medium Low
10. Lack of proper
cyber security
policy
Lack of proper security policies in
the organization may lead to the
various security risks within the
organization
Low Low Low
The risks identified above are some of the most common risk that the organization
Gigantic Corporation is exposed to. The risk matrix explains the impact of the identified risks
and the likelihood of their occurrence within the organization. The priority of the risks is
identified and a high priority risk indicates that the particular risk requires immediate attention.
While the medium and low priority of the risk indicates that the particular risk can be attended in
due time as well. Since the project is about development of a network and information system
within the organization that is capable of detecting and eliminating the active threats of the
system, it is very essential to eliminate the identified risk or mitigate these risks from creeping
into the system. The risk mitigation strategies are to be defined and implemented properly in the
IT MANAGEMENT-CYBER SECURITY
4. Threats from
BYOD
The employees working on their own
mobile devices within the
organization can be a source of data
vulnerability in the system.
Medium Severe High
5. Denial of
Service Attack
Jamming the internal network of the
organization, so that the legitimate
users cannot use the resources (
Wang et al., 2015)
Low Very low Low
6. Brute Force
attack
Use of a specific software by a
hacker in order to guess a password.
However, it may take a considerable
amount of time.
Medium Medium Medium
7. Injection
Attacks
The database of the organization is
controlled by an attacker through this
attack
Medium High High
8. Malware
Attack
Malicious software that can monitor
all the operations of the system and
transmit data into the system as well
( Khouzani, Sarkar & Altman, 2012)
High Severe High
9. Lack of
Recovery
Planning
Lack of proper disaster recovery
system can lead to the permanent
loss of data
Low Medium Low
10. Lack of proper
cyber security
policy
Lack of proper security policies in
the organization may lead to the
various security risks within the
organization
Low Low Low
The risks identified above are some of the most common risk that the organization
Gigantic Corporation is exposed to. The risk matrix explains the impact of the identified risks
and the likelihood of their occurrence within the organization. The priority of the risks is
identified and a high priority risk indicates that the particular risk requires immediate attention.
While the medium and low priority of the risk indicates that the particular risk can be attended in
due time as well. Since the project is about development of a network and information system
within the organization that is capable of detecting and eliminating the active threats of the
system, it is very essential to eliminate the identified risk or mitigate these risks from creeping
into the system. The risk mitigation strategies are to be defined and implemented properly in the

5
IT MANAGEMENT-CYBER SECURITY
system so as to eliminate the all the threats associated with the system. The different mitigation
strategies include ensuring proper intrusion detection system and use of antivirus in such system
is necessary. There are mainly two types of attacks, active attack and passive attack. The passive
attack in the systems is difficult to detect as it deals with the silent monitoring of the system in
order to collect confidential information from the system. Active attack on the other hand is
easier to detect for is more harmful to the system.
The risk of threat insider can only be mitigated by limiting the use of confidential data of
the organization only to some selected member of the organization. In this way, the data loss (if
any) can be easily tracked and necessary actions can be taken against the member. The risk
matrix mentions that the impact of the threat from an insider is sever and therefore, this risk
should be mitigated as soon as possible.
Phishing is a critical threat that can be mitigated only by installing proper intrusion
detection system. Furthermore, all the employees should be properly trained about the proper and
safe use of emails. E-mail is a major tool of phishing attack as the malicious links are forwarded
to the victims through emails. If a user clicks on the link, the virus spreads into the entire system,
leading to the loss of confidential and personal data from the system. However, the presence of a
proper intrusion detection system might help in blocking such malicious emails.
Ransomware attack is one the most dangerous and most common cybercrimes. In this
attack, the attacker gets an access of all the important data present in a system or network and
locks them. In turn, the attacker demands a ransom from the victim for unlocking the data. This
risk can be mitigated by installing an up to date antivirus in the system (Brewer, 2016). This can
detect and eliminate the presence of ransomware from the system. Impact of the ransomware is
marked severe in the risk matrix, as this malware is capable of transferring from one system to
all the other system connected over a common network, without human interference. Therefore,
this risk should be dealt with as soon as possible. For this, it is mandatory to ensure that the
antivirus software installed for each system of the Gigantic Corporation is working effectively or
not. Furthermore, the option of automatic patches for the operating system should be ensured. It
is the responsibility of the risk manager to limit the older operating system.
Threats from BYOD can be easily mitigated by ensuring that proper antivirus protection
is installed in every device. Firewall protection of the system should be turned on in order to
detect the entry of any malicious particle into the system. This can however, be a source of
deliberate threat as a threat insider and therefore, the impact of this threat is marked severe in the
matrix.
Denial of service attack is a less severe attack that can be easily mitigated by limiting the
rate of traffic a network can withstand in a particular time limit (Bhuyan, Bhattacharyya &
Kalita, 2015). Furthermore, it does not lead to any data loss and therefore, it can be mitigated in
due course. Similarly, the brute force attack can be mitigated by the use of a strong password that
will be hard to guess (Raza et al., 2012).
Injection attack on the other hand is a severe risk that needs a proper attention. This is a
common attack that aims at gaining the confidential information of the system. This can be
mitigated by prevention of the use of dynamic SQL. Furthermore, use of firewall in the system
IT MANAGEMENT-CYBER SECURITY
system so as to eliminate the all the threats associated with the system. The different mitigation
strategies include ensuring proper intrusion detection system and use of antivirus in such system
is necessary. There are mainly two types of attacks, active attack and passive attack. The passive
attack in the systems is difficult to detect as it deals with the silent monitoring of the system in
order to collect confidential information from the system. Active attack on the other hand is
easier to detect for is more harmful to the system.
The risk of threat insider can only be mitigated by limiting the use of confidential data of
the organization only to some selected member of the organization. In this way, the data loss (if
any) can be easily tracked and necessary actions can be taken against the member. The risk
matrix mentions that the impact of the threat from an insider is sever and therefore, this risk
should be mitigated as soon as possible.
Phishing is a critical threat that can be mitigated only by installing proper intrusion
detection system. Furthermore, all the employees should be properly trained about the proper and
safe use of emails. E-mail is a major tool of phishing attack as the malicious links are forwarded
to the victims through emails. If a user clicks on the link, the virus spreads into the entire system,
leading to the loss of confidential and personal data from the system. However, the presence of a
proper intrusion detection system might help in blocking such malicious emails.
Ransomware attack is one the most dangerous and most common cybercrimes. In this
attack, the attacker gets an access of all the important data present in a system or network and
locks them. In turn, the attacker demands a ransom from the victim for unlocking the data. This
risk can be mitigated by installing an up to date antivirus in the system (Brewer, 2016). This can
detect and eliminate the presence of ransomware from the system. Impact of the ransomware is
marked severe in the risk matrix, as this malware is capable of transferring from one system to
all the other system connected over a common network, without human interference. Therefore,
this risk should be dealt with as soon as possible. For this, it is mandatory to ensure that the
antivirus software installed for each system of the Gigantic Corporation is working effectively or
not. Furthermore, the option of automatic patches for the operating system should be ensured. It
is the responsibility of the risk manager to limit the older operating system.
Threats from BYOD can be easily mitigated by ensuring that proper antivirus protection
is installed in every device. Firewall protection of the system should be turned on in order to
detect the entry of any malicious particle into the system. This can however, be a source of
deliberate threat as a threat insider and therefore, the impact of this threat is marked severe in the
matrix.
Denial of service attack is a less severe attack that can be easily mitigated by limiting the
rate of traffic a network can withstand in a particular time limit (Bhuyan, Bhattacharyya &
Kalita, 2015). Furthermore, it does not lead to any data loss and therefore, it can be mitigated in
due course. Similarly, the brute force attack can be mitigated by the use of a strong password that
will be hard to guess (Raza et al., 2012).
Injection attack on the other hand is a severe risk that needs a proper attention. This is a
common attack that aims at gaining the confidential information of the system. This can be
mitigated by prevention of the use of dynamic SQL. Furthermore, use of firewall in the system

6
IT MANAGEMENT-CYBER SECURITY
can reduce the risk of injection attack. It is utmost essential to use proper antivirus software for
mitigation of the risk (Sharma, Johari & Sarma, 2012).
Malware attack is another severe attack and therefore needs a wide attention. The systems
of the Gigantic Corporation are exposed to malware threat due to the use of un-patched systems
and absence of proper antivirus in the system. Furthermore, malware can easily spread to
different systems connected over a single network and therefore, it is essential to mitigate the
risk at once. A proper intrusion detection system will help in detecting the entry of malware into
the system. Use of firewall into the system is essential in order to mitigate the risk associated
with the systems.
However, even after ensuring proper risk mitigation strategies into the system, it becomes
essential to ensure that the organization has a proper disaster recovery plan. This will help the
organization in recovering all the important and the confidential data in case it is being
compromised. A proper disaster recovery plan ensures that the catastrophic events do not destroy
the company or its data (Wallace & Webber, 2017).
IT MANAGEMENT-CYBER SECURITY
can reduce the risk of injection attack. It is utmost essential to use proper antivirus software for
mitigation of the risk (Sharma, Johari & Sarma, 2012).
Malware attack is another severe attack and therefore needs a wide attention. The systems
of the Gigantic Corporation are exposed to malware threat due to the use of un-patched systems
and absence of proper antivirus in the system. Furthermore, malware can easily spread to
different systems connected over a single network and therefore, it is essential to mitigate the
risk at once. A proper intrusion detection system will help in detecting the entry of malware into
the system. Use of firewall into the system is essential in order to mitigate the risk associated
with the systems.
However, even after ensuring proper risk mitigation strategies into the system, it becomes
essential to ensure that the organization has a proper disaster recovery plan. This will help the
organization in recovering all the important and the confidential data in case it is being
compromised. A proper disaster recovery plan ensures that the catastrophic events do not destroy
the company or its data (Wallace & Webber, 2017).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IT MANAGEMENT-CYBER SECURITY
Protection mechanism
There are many security risks associated with websites that are needed to be properly
mitigated in order to ensure the normal operations of the website. The major security risks
associated with a website includes hacking, virus attack and identity theft. These are the most
common security threats associated with the operation of the websites. Hacking is a common
method by which an attacker gains access to the website with an aim of stealing confidential data
from the same. The confidential data includes the customers’ list of the company, passwords of
the employees and financial information (Gharibi & Shaabi, 2012). The gained information is
generally used by the hacker for their own benefit, such as selling the information to the rival
company in exchange of money. This might lead to the considerable loss of the company.
Similar is the case for virus as well. Virus is a specialized code that is designed or written
in order to cause damage to the system. This can be a key logger and or a software that is capable
of stealing the users files. Virus is generally uploaded to a web server with the help of input
forms or with the use of backdoors. This can cause various issues in the website, such as change
of the contents of the website, so as to redirect the users to a malicious website. Another severe
problem with the presence of virus is a website is that the same virus can be downloaded in the
computer of the user. This can help the attacker in gaining access to the confidential information
present in the system. Gigantic Corporation is exposed to this threat as well. Furthermore, virus
can be easily transferred to the different system that are connected over a single network.
Therefore, presence of virus in the website is a major risk, which requires proper protection
mechanism in order to secure the website’s data.
Identity theft is another major risk associated with a particular website. This refers to a
situation, where the identity of a person or user is compromised and used for carrying on various
criminal activities. Websites generally posses an increasing threat of identity theft. Hackers for
using ones personal information for identity fraud generally intercept this.
These threats in the website can be mitigated by the ensuring proper protection measures
such as use of firewalls, secure socket layer and standards adherence.
Firewall application can be installed in a web server in order to check all the
communication and traffic to and fro the server. This ensures that any foreign or malicious data
packet is blocked from entering the system (Suh et al., 2014). The firewall ensures only the
legitimate packets enter into the system.
Secure socket layer is a commonly used method for preventing the identity theft. The use
of HTTPS ensures that a secure connection is established between the client and the server.
Proper encryption of any information sent between the client and the server ensures that no third
person is able to decrypt the information (Zissis & Lekkas, 2012).
The website and the web server are needed to adhere with the standard security
guidelines in order to prevent any outside attack (Vance, Siponen & Pahnila, 2012). Use of a
strong password in a server prevents it from being hacked.
IT MANAGEMENT-CYBER SECURITY
Protection mechanism
There are many security risks associated with websites that are needed to be properly
mitigated in order to ensure the normal operations of the website. The major security risks
associated with a website includes hacking, virus attack and identity theft. These are the most
common security threats associated with the operation of the websites. Hacking is a common
method by which an attacker gains access to the website with an aim of stealing confidential data
from the same. The confidential data includes the customers’ list of the company, passwords of
the employees and financial information (Gharibi & Shaabi, 2012). The gained information is
generally used by the hacker for their own benefit, such as selling the information to the rival
company in exchange of money. This might lead to the considerable loss of the company.
Similar is the case for virus as well. Virus is a specialized code that is designed or written
in order to cause damage to the system. This can be a key logger and or a software that is capable
of stealing the users files. Virus is generally uploaded to a web server with the help of input
forms or with the use of backdoors. This can cause various issues in the website, such as change
of the contents of the website, so as to redirect the users to a malicious website. Another severe
problem with the presence of virus is a website is that the same virus can be downloaded in the
computer of the user. This can help the attacker in gaining access to the confidential information
present in the system. Gigantic Corporation is exposed to this threat as well. Furthermore, virus
can be easily transferred to the different system that are connected over a single network.
Therefore, presence of virus in the website is a major risk, which requires proper protection
mechanism in order to secure the website’s data.
Identity theft is another major risk associated with a particular website. This refers to a
situation, where the identity of a person or user is compromised and used for carrying on various
criminal activities. Websites generally posses an increasing threat of identity theft. Hackers for
using ones personal information for identity fraud generally intercept this.
These threats in the website can be mitigated by the ensuring proper protection measures
such as use of firewalls, secure socket layer and standards adherence.
Firewall application can be installed in a web server in order to check all the
communication and traffic to and fro the server. This ensures that any foreign or malicious data
packet is blocked from entering the system (Suh et al., 2014). The firewall ensures only the
legitimate packets enter into the system.
Secure socket layer is a commonly used method for preventing the identity theft. The use
of HTTPS ensures that a secure connection is established between the client and the server.
Proper encryption of any information sent between the client and the server ensures that no third
person is able to decrypt the information (Zissis & Lekkas, 2012).
The website and the web server are needed to adhere with the standard security
guidelines in order to prevent any outside attack (Vance, Siponen & Pahnila, 2012). Use of a
strong password in a server prevents it from being hacked.

8
IT MANAGEMENT-CYBER SECURITY
References
Bhuyan, M. H., Bhattacharyya, D. K., & Kalita, J. K. (2015). An empirical evaluation of
information metrics for low-rate and high-rate DDoS attack detection. Pattern
Recognition Letters, 51, 1-7.
Brewer, R. (2016). Ransomware attacks: detection, prevention and cure. Network
Security, 2016(9), 5-9.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H., & Stoddart, K. (2016).
A review of cyber security risk assessment methods for SCADA systems. computers &
security, 56, 1-27.
Gharibi, W., & Shaabi, M. (2012). Cyber threats in social networking websites. arXiv preprint
arXiv:1202.2420.
Hartmann, K., & Steup, C. (2013, June). The vulnerability of UAVs to cyber attacks-An
approach to the risk assessment. In Cyber Conflict (CyCon), 2013 5th International
Conference on(pp. 1-23). IEEE.
Hong, J. (2012). The state of phishing attacks. Communications of the ACM, 55(1), 74-81.
Jouini, M., Rabai, L. B. A., & Aissa, A. B. (2014). Classification of security threats in
information systems. Procedia Computer Science, 32, 489-496.
Khouzani, M. H. R., Sarkar, S., & Altman, E. (2012). Maximum damage malware attack in
mobile wireless networks. IEEE/ACM Transactions on Networking (TON), 20(5), 1347-
1360.
O’Connell, M. E. (2012). Cyber security without cyber war. Journal of Conflict and Security
Law, 17(2), 187-209.
Pathak, D. P., & Nanded, Y. M. (2016). A dangerous trend of cybercrime: ransomware growing
challenge. International Journal of Advanced Research in Computer Engineering &
Technology (IJARCET) Volume, 5.
Raza, M., Iqbal, M., Sharif, M., & Haider, W. (2012). A survey of password attacks and
comparative analysis on methods for secure authentication. World Applied Sciences
Journal, 19(4), 439-444.
Sharma, P., Johari, R., & Sarma, S. S. (2012). Integrated approach to prevent SQL injection
attack and reflected cross site scripting attack. International Journal of System Assurance
Engineering and Management, 3(4), 343-351.
Suh, M., Park, S. H., Lee, B., & Yang, S. (2014, February). Building firewall over the software-
defined network controller. In Advanced Communication Technology (ICACT), 2014
16th International Conference on (pp. 744-748). IEEE.
Vance, A., Siponen, M., & Pahnila, S. (2012). Motivating IS security compliance: insights from
habit and protection motivation theory. Information & Management, 49(3), 190-198.
IT MANAGEMENT-CYBER SECURITY
References
Bhuyan, M. H., Bhattacharyya, D. K., & Kalita, J. K. (2015). An empirical evaluation of
information metrics for low-rate and high-rate DDoS attack detection. Pattern
Recognition Letters, 51, 1-7.
Brewer, R. (2016). Ransomware attacks: detection, prevention and cure. Network
Security, 2016(9), 5-9.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H., & Stoddart, K. (2016).
A review of cyber security risk assessment methods for SCADA systems. computers &
security, 56, 1-27.
Gharibi, W., & Shaabi, M. (2012). Cyber threats in social networking websites. arXiv preprint
arXiv:1202.2420.
Hartmann, K., & Steup, C. (2013, June). The vulnerability of UAVs to cyber attacks-An
approach to the risk assessment. In Cyber Conflict (CyCon), 2013 5th International
Conference on(pp. 1-23). IEEE.
Hong, J. (2012). The state of phishing attacks. Communications of the ACM, 55(1), 74-81.
Jouini, M., Rabai, L. B. A., & Aissa, A. B. (2014). Classification of security threats in
information systems. Procedia Computer Science, 32, 489-496.
Khouzani, M. H. R., Sarkar, S., & Altman, E. (2012). Maximum damage malware attack in
mobile wireless networks. IEEE/ACM Transactions on Networking (TON), 20(5), 1347-
1360.
O’Connell, M. E. (2012). Cyber security without cyber war. Journal of Conflict and Security
Law, 17(2), 187-209.
Pathak, D. P., & Nanded, Y. M. (2016). A dangerous trend of cybercrime: ransomware growing
challenge. International Journal of Advanced Research in Computer Engineering &
Technology (IJARCET) Volume, 5.
Raza, M., Iqbal, M., Sharif, M., & Haider, W. (2012). A survey of password attacks and
comparative analysis on methods for secure authentication. World Applied Sciences
Journal, 19(4), 439-444.
Sharma, P., Johari, R., & Sarma, S. S. (2012). Integrated approach to prevent SQL injection
attack and reflected cross site scripting attack. International Journal of System Assurance
Engineering and Management, 3(4), 343-351.
Suh, M., Park, S. H., Lee, B., & Yang, S. (2014, February). Building firewall over the software-
defined network controller. In Advanced Communication Technology (ICACT), 2014
16th International Conference on (pp. 744-748). IEEE.
Vance, A., Siponen, M., & Pahnila, S. (2012). Motivating IS security compliance: insights from
habit and protection motivation theory. Information & Management, 49(3), 190-198.

9
IT MANAGEMENT-CYBER SECURITY
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
Wallace, M., & Webber, L. (2017). The disaster recovery handbook: A step-by-step plan to
ensure business continuity and protect vital operations, facilities, and assets. AMACOM
Div American Mgmt Assn.
Wang, B., Zheng, Y., Lou, W., & Hou, Y. T. (2015). DDoS attack protection in the era of cloud
computing and software-defined networking. Computer Networks, 81, 308-319.
Zissis, D., & Lekkas, D. (2012). Addressing cloud computing security issues. Future Generation
computer systems, 28(3), 583-592.
IT MANAGEMENT-CYBER SECURITY
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
Wallace, M., & Webber, L. (2017). The disaster recovery handbook: A step-by-step plan to
ensure business continuity and protect vital operations, facilities, and assets. AMACOM
Div American Mgmt Assn.
Wang, B., Zheng, Y., Lou, W., & Hou, Y. T. (2015). DDoS attack protection in the era of cloud
computing and software-defined networking. Computer Networks, 81, 308-319.
Zissis, D., & Lekkas, D. (2012). Addressing cloud computing security issues. Future Generation
computer systems, 28(3), 583-592.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




