Ciphers are used here for a better performance
VerifiedAdded on 2022/09/18
|9
|2746
|44
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
COIT20262 Term 2, 2019
COIT20262 - Advanced Network Security, Term 2, 2019
Due date: 10am Monday 26 August 2019
(Week 6)
ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Page 1 of 9
COIT20262 - Advanced Network Security, Term 2, 2019
Due date: 10am Monday 26 August 2019
(Week 6)
ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Page 1 of 9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
COIT20262 Term 2, 2019
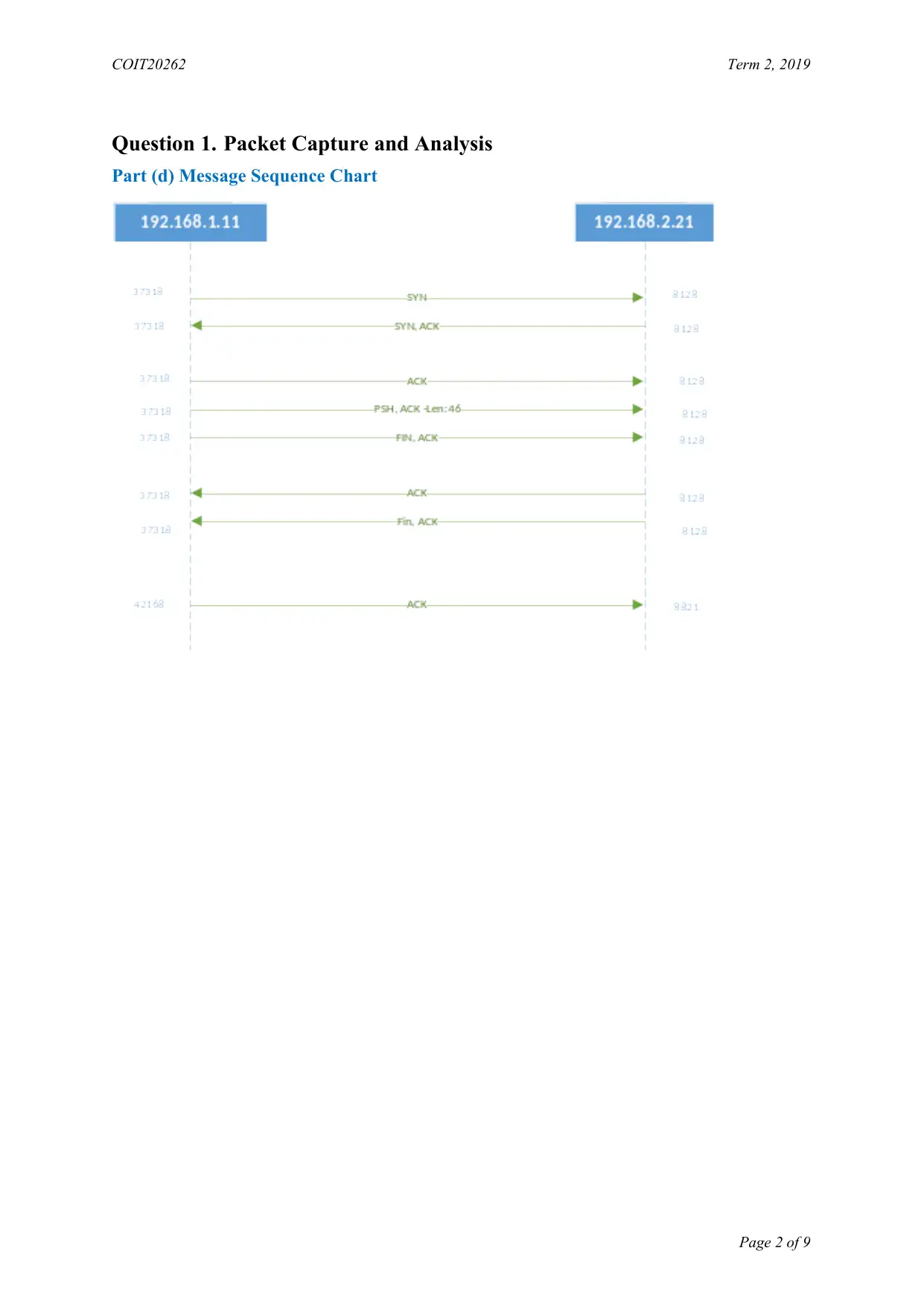
Question 1. Packet Capture and Analysis
Part (d) Message Sequence Chart
Page 2 of 9
Question 1. Packet Capture and Analysis
Part (d) Message Sequence Chart
Page 2 of 9
COIT20262 Term 2, 2019
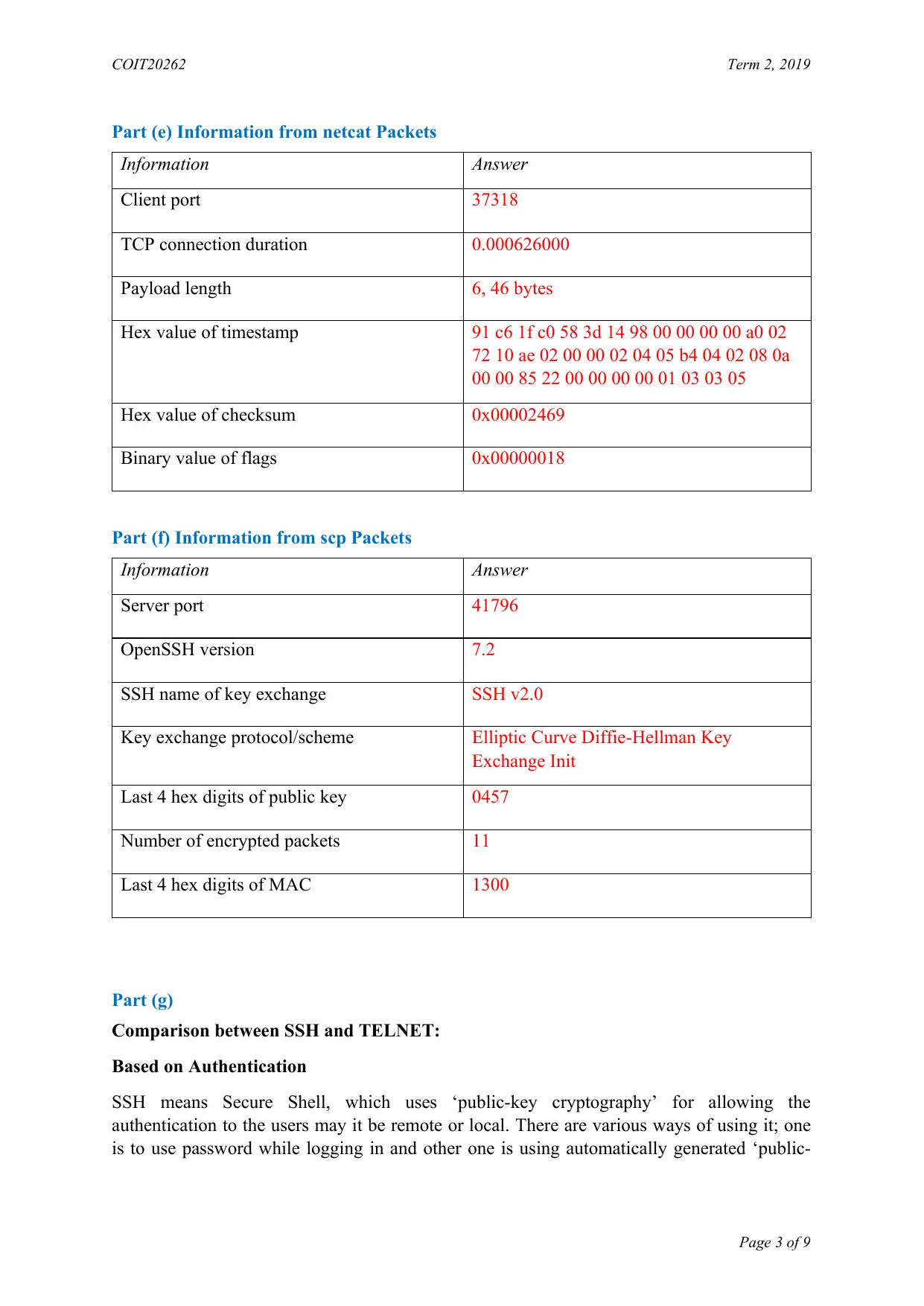
Part (e) Information from netcat Packets
Information Answer
Client port 37318
TCP connection duration 0.000626000
Payload length 6, 46 bytes
Hex value of timestamp 91 c6 1f c0 58 3d 14 98 00 00 00 00 a0 02
72 10 ae 02 00 00 02 04 05 b4 04 02 08 0a
00 00 85 22 00 00 00 00 01 03 03 05
Hex value of checksum 0x00002469
Binary value of flags 0x00000018
Part (f) Information from scp Packets
Information Answer
Server port 41796
OpenSSH version 7.2
SSH name of key exchange SSH v2.0
Key exchange protocol/scheme Elliptic Curve Diffie-Hellman Key
Exchange Init
Last 4 hex digits of public key 0457
Number of encrypted packets 11
Last 4 hex digits of MAC 1300
Part (g)
Comparison between SSH and TELNET:
Based on Authentication
SSH means Secure Shell, which uses ‘public-key cryptography’ for allowing the
authentication to the users may it be remote or local. There are various ways of using it; one
is to use password while logging in and other one is using automatically generated ‘public-
Page 3 of 9
Part (e) Information from netcat Packets
Information Answer
Client port 37318
TCP connection duration 0.000626000
Payload length 6, 46 bytes
Hex value of timestamp 91 c6 1f c0 58 3d 14 98 00 00 00 00 a0 02
72 10 ae 02 00 00 02 04 05 b4 04 02 08 0a
00 00 85 22 00 00 00 00 01 03 03 05
Hex value of checksum 0x00002469
Binary value of flags 0x00000018
Part (f) Information from scp Packets
Information Answer
Server port 41796
OpenSSH version 7.2
SSH name of key exchange SSH v2.0
Key exchange protocol/scheme Elliptic Curve Diffie-Hellman Key
Exchange Init
Last 4 hex digits of public key 0457
Number of encrypted packets 11
Last 4 hex digits of MAC 1300
Part (g)
Comparison between SSH and TELNET:
Based on Authentication
SSH means Secure Shell, which uses ‘public-key cryptography’ for allowing the
authentication to the users may it be remote or local. There are various ways of using it; one
is to use password while logging in and other one is using automatically generated ‘public-
Page 3 of 9

COIT20262 Term 2, 2019
private key pairs’ to do the encryption of a network connection. This cryptographic network
protocol is used by many OS.
Hence, there is a security threat on using Telnet and for that reason Telnet is not being used
anymore to access any network devices over the shared network. No policies for
authentication.
Based on Confidentiality
SSH is a very reliable and secure network protocol by default, which runs on port 22;
however ports are changeable. In SSH, the encryption method is complicated hence it’s
difficult to decrypt that encrypted data. Therefore, the encrypted passwords which are under
the protocol of SSH can travel on a public network carrying its security. All the data which is
shared over the network are in encrypted format.
Whereas, Telnet is not a secure communication protocol as its network protocol does not
provide security. Hence, anyone can do the sniffing attack by decrypting the shared packets
to obtain the information. Therefore TELNET is not safe to use as it does not provide any
method to maintain confidentiality. All the data which is shared over the network are in plain
text.
Based on Performance
Telnet serves an interface of command line for communicating with the remote servers. Bi-
directional interaction is used for a good performance.
The SSH works faster as it is convenient and comes in handy. And the performance can be
improved even if the file size gets higher. Ciphers are used here for a better performance.
Part (h)
ChaCha20 is an encryption algorithm used to encrypt a message, in which a key and a nonce
is present. This encryption method helps to keep the data confidential. In this stream cipher,
permutation of 128 fixed bits is operated, a 64 bit nonce and another 64 bit counter is
operated into 64 bytes of output. It has throughput and it is used to create one-time secret
keys of Poly1305 from public nonce values which results in authenticator, called ChaCha20-
Poly1305.
ChaCha20-Poly1305 accepts 4 inputs; a key of 256-bit, a nonce of 96-bit, a plaintext of
random length and an additional authenticated data (AAD) of random length. As the name
implies ‘nonce’ of 96-bit cannot be used more than once. Both encryption and authentication
is offered by this stream cipher, in which 256 bit keys are necessary that are used by two
separate instances. The key of first instance is used to encrypt the data packet of 4 byte and
the second instance is used for conjunction purpose.
Whereas, AES uses a simple algebraic structure of encryption and same pattern is followed
for every block.
1. ChahCha20 is used for the 32 bit or higher variant processor if there is no predefined
instruction rather than AES as ChahCha20 is faster. Extra XOR (ARX) rotation
makes the ChahCha20 faster. Also, the ARX is CPU friendly. AES uses lookup table
for computation which makes it efficient.
Page 4 of 9
private key pairs’ to do the encryption of a network connection. This cryptographic network
protocol is used by many OS.
Hence, there is a security threat on using Telnet and for that reason Telnet is not being used
anymore to access any network devices over the shared network. No policies for
authentication.
Based on Confidentiality
SSH is a very reliable and secure network protocol by default, which runs on port 22;
however ports are changeable. In SSH, the encryption method is complicated hence it’s
difficult to decrypt that encrypted data. Therefore, the encrypted passwords which are under
the protocol of SSH can travel on a public network carrying its security. All the data which is
shared over the network are in encrypted format.
Whereas, Telnet is not a secure communication protocol as its network protocol does not
provide security. Hence, anyone can do the sniffing attack by decrypting the shared packets
to obtain the information. Therefore TELNET is not safe to use as it does not provide any
method to maintain confidentiality. All the data which is shared over the network are in plain
text.
Based on Performance
Telnet serves an interface of command line for communicating with the remote servers. Bi-
directional interaction is used for a good performance.
The SSH works faster as it is convenient and comes in handy. And the performance can be
improved even if the file size gets higher. Ciphers are used here for a better performance.
Part (h)
ChaCha20 is an encryption algorithm used to encrypt a message, in which a key and a nonce
is present. This encryption method helps to keep the data confidential. In this stream cipher,
permutation of 128 fixed bits is operated, a 64 bit nonce and another 64 bit counter is
operated into 64 bytes of output. It has throughput and it is used to create one-time secret
keys of Poly1305 from public nonce values which results in authenticator, called ChaCha20-
Poly1305.
ChaCha20-Poly1305 accepts 4 inputs; a key of 256-bit, a nonce of 96-bit, a plaintext of
random length and an additional authenticated data (AAD) of random length. As the name
implies ‘nonce’ of 96-bit cannot be used more than once. Both encryption and authentication
is offered by this stream cipher, in which 256 bit keys are necessary that are used by two
separate instances. The key of first instance is used to encrypt the data packet of 4 byte and
the second instance is used for conjunction purpose.
Whereas, AES uses a simple algebraic structure of encryption and same pattern is followed
for every block.
1. ChahCha20 is used for the 32 bit or higher variant processor if there is no predefined
instruction rather than AES as ChahCha20 is faster. Extra XOR (ARX) rotation
makes the ChahCha20 faster. Also, the ARX is CPU friendly. AES uses lookup table
for computation which makes it efficient.
Page 4 of 9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

COIT20262 Term 2, 2019
2. Using the lookup table makes AES vulnerable in front of time cache attack. For
resolving it ChahCha20 can be deployed.
Question 2. Cryptography
Part (c)
The information that is required to be secured through the encryption is different in terms of
size, format and content of the information as well. The different algorithms that are
described in this context contains instructions, which executes different process according to
the requirements. Encryption is important for protecting the data from any type of
unauthorized access. There are several of encryption process in which many are weak and
many are strong.
Different algorithm serves different level of encryption, some are very complex and some are
easy to decrypt. There are two categories of Cryptography: Symmetric key and Asymmetric
key cryptography, which are even further categorized.
Part (d)
MD5 is cryptographic hash function which is prone to be attacked by the collisions. ‘Birthday
attack’ assists these attacks to process faster, a hash of ‘n’ bits can be decrypted within 2n/2
time. Some major extension of collision attack is ‘chosen-prefix collision attack’, which is
very strong. In this collision attack two different ‘prefixes’ are there and two appendages are
involved which gets into operation of concatenation. The Flame malware was a new version
of ‘chose-prefix collision attack’, which did the spoofing attack on code signing and its
elements against MD5.
Hash collision can be used for the MD5 for finding two inputs which produces same hash
value. Content of the message remains intact in this attack.
SHA is an important algorithm for encryption which can produce 160-bit hash value.
Functions of SHA is vulnerable to partial-message collision attacks.
MD5 hash function contains 128 bit whether for SHA, it is 256 bits. However, it is easy to
calculate hash function for any provided input. The MD5 algorithm has security issues due to
collisions and therefore, not considered trustworthy.
Part (e)
A masquerade attack utilizes a fake identity over the network to acquire illegal access to
information. The weaker the authorization process the stronger the masquerade attack. These
attacks can be performed by using theft passwords and logons. The attackers can be present
in the organization itself or can be an outsider. In case of attacker within the organization,
gaining access to someone’s account is easier by simply stealing the victim’s account ID and
its password. If once the attacker gets the access then the gaining all the essential and
sensitive information would not be difficult. The attacker can do the modification in the data
which will violate the confidentiality and authorization. To detect the masquerade attack user
Page 5 of 9
2. Using the lookup table makes AES vulnerable in front of time cache attack. For
resolving it ChahCha20 can be deployed.
Question 2. Cryptography
Part (c)
The information that is required to be secured through the encryption is different in terms of
size, format and content of the information as well. The different algorithms that are
described in this context contains instructions, which executes different process according to
the requirements. Encryption is important for protecting the data from any type of
unauthorized access. There are several of encryption process in which many are weak and
many are strong.
Different algorithm serves different level of encryption, some are very complex and some are
easy to decrypt. There are two categories of Cryptography: Symmetric key and Asymmetric
key cryptography, which are even further categorized.
Part (d)
MD5 is cryptographic hash function which is prone to be attacked by the collisions. ‘Birthday
attack’ assists these attacks to process faster, a hash of ‘n’ bits can be decrypted within 2n/2
time. Some major extension of collision attack is ‘chosen-prefix collision attack’, which is
very strong. In this collision attack two different ‘prefixes’ are there and two appendages are
involved which gets into operation of concatenation. The Flame malware was a new version
of ‘chose-prefix collision attack’, which did the spoofing attack on code signing and its
elements against MD5.
Hash collision can be used for the MD5 for finding two inputs which produces same hash
value. Content of the message remains intact in this attack.
SHA is an important algorithm for encryption which can produce 160-bit hash value.
Functions of SHA is vulnerable to partial-message collision attacks.
MD5 hash function contains 128 bit whether for SHA, it is 256 bits. However, it is easy to
calculate hash function for any provided input. The MD5 algorithm has security issues due to
collisions and therefore, not considered trustworthy.
Part (e)
A masquerade attack utilizes a fake identity over the network to acquire illegal access to
information. The weaker the authorization process the stronger the masquerade attack. These
attacks can be performed by using theft passwords and logons. The attackers can be present
in the organization itself or can be an outsider. In case of attacker within the organization,
gaining access to someone’s account is easier by simply stealing the victim’s account ID and
its password. If once the attacker gets the access then the gaining all the essential and
sensitive information would not be difficult. The attacker can do the modification in the data
which will violate the confidentiality and authorization. To detect the masquerade attack user
Page 5 of 9

COIT20262 Term 2, 2019
behaviour profiling can be used. Two categories of detection are the biometrics and command
sequence.
Part (f)
If suspicious activity is detected properly, it is easier to prevent these type of security
vulnerabilities. However, effective algorithm is required in this context.
This type of profiling have limitations while operating the behaviour of keystroke, for
example if someone’s hand is weak or broken then the keystroke would be quite different
from a normal user. Other techniques of biometric faces these kind of challenges.
In the second category, analysing the frequency of the occurrence, duration of the events,
multiple events. The unusual sequences of command is mainly focused. Six masquerade
detection methods were applied by Schonlau to a dataset of UNIX shell commands. One of
them is called ‘uniqueness’, in which the unique training data is detected. Another detection
method was ‘one-step transitions’ from one command to the other and this was originally
approached by DuMouchel.
Part (g)
If the algorithm is applied properly, then it is easier to identify different activities in the
network that tries to exploit the security of the network through illegal access to the network
for accessing the information. Along with that, it is also possible to alert the owner of the
network if several attempts are made for network exploitation as well. Detection method can
be used for defeating the masquerade attack. Various of detection method can be used in this
case.
When the uniqueness of the attackers command is detected then it is easier to prevent the
masquerade attack. The main part is the sequence, sequence of the command is essential in
detection in this type of profiling. And another one was detecting behaviour, which is again
someone’s uniqueness.
Page 6 of 9
behaviour profiling can be used. Two categories of detection are the biometrics and command
sequence.
Part (f)
If suspicious activity is detected properly, it is easier to prevent these type of security
vulnerabilities. However, effective algorithm is required in this context.
This type of profiling have limitations while operating the behaviour of keystroke, for
example if someone’s hand is weak or broken then the keystroke would be quite different
from a normal user. Other techniques of biometric faces these kind of challenges.
In the second category, analysing the frequency of the occurrence, duration of the events,
multiple events. The unusual sequences of command is mainly focused. Six masquerade
detection methods were applied by Schonlau to a dataset of UNIX shell commands. One of
them is called ‘uniqueness’, in which the unique training data is detected. Another detection
method was ‘one-step transitions’ from one command to the other and this was originally
approached by DuMouchel.
Part (g)
If the algorithm is applied properly, then it is easier to identify different activities in the
network that tries to exploit the security of the network through illegal access to the network
for accessing the information. Along with that, it is also possible to alert the owner of the
network if several attempts are made for network exploitation as well. Detection method can
be used for defeating the masquerade attack. Various of detection method can be used in this
case.
When the uniqueness of the attackers command is detected then it is easier to prevent the
masquerade attack. The main part is the sequence, sequence of the command is essential in
detection in this type of profiling. And another one was detecting behaviour, which is again
someone’s uniqueness.
Page 6 of 9

COIT20262 Term 2, 2019
Question 3. Malware Research
What is ransomware?
Scareware involves software for security which is rogue. Many pop-up messages appears on
the screen which shows that ‘malware has been detected’ and demands for payment. And
later if no action is taken then bunch of pop-ups might appear which is disturbing.
Ransomware is a typical type of malware software which blocks the users from accessing
their own personal system.
Screenlockers leads to terror alert, when screenlockers invades into the computer then the
screen gets frozen out. And when the computer is started then a full-size window will showed
up, which might be accompanied by an authorized-looking FBI viewing illegal activities has
been detected (Brewer 2016). This messages can terrify the users by demanding fines for the
so-called illegal activities.
The third one is Encrypting ransomware, which is extremely malicious as the attackers grab
the users’ files and encrypt those according to their methods and demands payment for the
solution. This type of ransomware is highly un-secure as the attackers has the accessibility to
do anything with the theft files. Even if the payment is done, there is no guarantee in the
confidentiality of the data.
Infection Methods
There are various methods that ransom can infect the computers of the organization. The
Malspam are used to trick the users, so that the users will open the attachments and some
links are even sent to the users with some attracting phrases hence, users might click on the
links. For ransom attacks, the cybercriminals are responsible. Spam emails are used for
delivering the ransomware malware to the other systems. Malware remains as attachment in
the email.
Another infection method is Malvertising, which is very popular. Malvertising means
malicious advertising, which uses the online platform for the advertisements to spread the
malware with a single click. While browsing any web page or website, users can be directed
to the malicious page through the main URL without even clicking on the advertisements
(Mohurle and Patil 2017). By this the attackers can access the location of the victim’s
computer through the server. The iframe is used in malvertising which shows invisible
element of the webpage to the victim then the user is redirected to the exploited web page.
Through the exploit kit a malicious code is invaded into the system.
Role of Cryptography
While on the other cryptographic encryption can be done to prevent the attacks. There are
various algorithm of cryptography: secret key cryptography, public key cryptography and
hash functions. Cryptography plays an important role in the ransomware attack. For the
cyber-attack crypto locker is used and the cryptography is also used for scrambling the file’s
content.
MD5 uses hash functions with a 128-bit hash value. It has various application for security.
RSA algorithm uses one public key and a private key, the encryption is done through the
public key and is decrypted by private key. The keys are created by applying few methods.
Page 7 of 9
Question 3. Malware Research
What is ransomware?
Scareware involves software for security which is rogue. Many pop-up messages appears on
the screen which shows that ‘malware has been detected’ and demands for payment. And
later if no action is taken then bunch of pop-ups might appear which is disturbing.
Ransomware is a typical type of malware software which blocks the users from accessing
their own personal system.
Screenlockers leads to terror alert, when screenlockers invades into the computer then the
screen gets frozen out. And when the computer is started then a full-size window will showed
up, which might be accompanied by an authorized-looking FBI viewing illegal activities has
been detected (Brewer 2016). This messages can terrify the users by demanding fines for the
so-called illegal activities.
The third one is Encrypting ransomware, which is extremely malicious as the attackers grab
the users’ files and encrypt those according to their methods and demands payment for the
solution. This type of ransomware is highly un-secure as the attackers has the accessibility to
do anything with the theft files. Even if the payment is done, there is no guarantee in the
confidentiality of the data.
Infection Methods
There are various methods that ransom can infect the computers of the organization. The
Malspam are used to trick the users, so that the users will open the attachments and some
links are even sent to the users with some attracting phrases hence, users might click on the
links. For ransom attacks, the cybercriminals are responsible. Spam emails are used for
delivering the ransomware malware to the other systems. Malware remains as attachment in
the email.
Another infection method is Malvertising, which is very popular. Malvertising means
malicious advertising, which uses the online platform for the advertisements to spread the
malware with a single click. While browsing any web page or website, users can be directed
to the malicious page through the main URL without even clicking on the advertisements
(Mohurle and Patil 2017). By this the attackers can access the location of the victim’s
computer through the server. The iframe is used in malvertising which shows invisible
element of the webpage to the victim then the user is redirected to the exploited web page.
Through the exploit kit a malicious code is invaded into the system.
Role of Cryptography
While on the other cryptographic encryption can be done to prevent the attacks. There are
various algorithm of cryptography: secret key cryptography, public key cryptography and
hash functions. Cryptography plays an important role in the ransomware attack. For the
cyber-attack crypto locker is used and the cryptography is also used for scrambling the file’s
content.
MD5 uses hash functions with a 128-bit hash value. It has various application for security.
RSA algorithm uses one public key and a private key, the encryption is done through the
public key and is decrypted by private key. The keys are created by applying few methods.
Page 7 of 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COIT20262 Term 2, 2019
AES uses the symmetric key algorithm which uses the same key for encryption as well as for
decryption. In this algorithm principle of ‘substitution-permutation’ network is followed.
Not Pay Ransom
The attackers can encrypt the files of their own can scramble the contents of files and can
either return or not. In most cases, if ransom is not paid then the files are never returned. If
the university does not want to pay the ransomware then they must be having a local backup
from which data can be restored.
Pay Ransom
Since the attackers are not loyal they can return the files but in encrypted form and data of
files might not be exact. Hence, payment does not assure of confidentiality of the data. If the
files are important then ransom for the files need to be paid but it is not assured that the
affected files will always going to be recovered (Brewer 2016). The payment is done through
a cryptocurrency medium.
Payment is done online, as the attackers prefers early payment as the attackers would not
reveal their identity. The attackers sends links for the payment which are later altered so that
the link cannot be traced further after payment. The attackers prefers this platform for the
payment which is beneficial for them.
Recommendations
To avoid these infections the organizations are recommended to maintain some precautions.
The first and important recommendation is that proper backup must be taken for
security of the data. Also, anti-malware programs must be installed within the system
so that system always remains safe from any type of malware attack including the
ransomware attack.
Verifying the links before clicking on it is essential to prevent attacks. The email that
seems to be suspicious should be deleted and by avoiding the clicking on provided
links. These steps could avoid phishing, the cyber-attack.
Highly recommended precaution is to keep the system updated. As the technologies
are getting evolved gradually the security is also getting evolved hence, the updated
system will prevent the general ransom attacks.
Page 8 of 9
AES uses the symmetric key algorithm which uses the same key for encryption as well as for
decryption. In this algorithm principle of ‘substitution-permutation’ network is followed.
Not Pay Ransom
The attackers can encrypt the files of their own can scramble the contents of files and can
either return or not. In most cases, if ransom is not paid then the files are never returned. If
the university does not want to pay the ransomware then they must be having a local backup
from which data can be restored.
Pay Ransom
Since the attackers are not loyal they can return the files but in encrypted form and data of
files might not be exact. Hence, payment does not assure of confidentiality of the data. If the
files are important then ransom for the files need to be paid but it is not assured that the
affected files will always going to be recovered (Brewer 2016). The payment is done through
a cryptocurrency medium.
Payment is done online, as the attackers prefers early payment as the attackers would not
reveal their identity. The attackers sends links for the payment which are later altered so that
the link cannot be traced further after payment. The attackers prefers this platform for the
payment which is beneficial for them.
Recommendations
To avoid these infections the organizations are recommended to maintain some precautions.
The first and important recommendation is that proper backup must be taken for
security of the data. Also, anti-malware programs must be installed within the system
so that system always remains safe from any type of malware attack including the
ransomware attack.
Verifying the links before clicking on it is essential to prevent attacks. The email that
seems to be suspicious should be deleted and by avoiding the clicking on provided
links. These steps could avoid phishing, the cyber-attack.
Highly recommended precaution is to keep the system updated. As the technologies
are getting evolved gradually the security is also getting evolved hence, the updated
system will prevent the general ransom attacks.
Page 8 of 9

COIT20262 Term 2, 2019
Bibliography
Brewer, R., 2016. Ransomware attacks: detection, prevention and cure. Network
Security, 2016(9), pp.5-9.
Kumar, S.D., Patranabis, S., Breier, J., Mukhopadhyay, D., Bhasin, S., Chattopadhyay, A.
and Baksi, A., 2017, September. A practical fault attack on ARX-like ciphers with a case
study on ChaCha20. In 2017 Workshop on Fault Diagnosis and Tolerance in Cryptography
(FDTC) (pp. 33-40). IEEE.
Lim, J.P. and Nagarakatte, S., 2019, February. Automatic equivalence checking for assembly
implementations of cryptography libraries. In 2019 IEEE/ACM International Symposium on
Code Generation and Optimization (CGO) (pp. 37-49). IEEE.
Mohurle, S. and Patil, M., 2017. A brief study of wannacry threat: Ransomware attack
2017. International Journal of Advanced Research in Computer Science, 8(5).
Velea, R., Gurzău, F., Mărgărit, L., Bica, I. and Patriciu, V.V., 2016, May. Performance of
parallel ChaCha20 stream cipher. In 2016 IEEE 11th International Symposium on Applied
Computational Intelligence and Informatics (SACI) (pp. 391-396). IEEE.
Page 9 of 9
Bibliography
Brewer, R., 2016. Ransomware attacks: detection, prevention and cure. Network
Security, 2016(9), pp.5-9.
Kumar, S.D., Patranabis, S., Breier, J., Mukhopadhyay, D., Bhasin, S., Chattopadhyay, A.
and Baksi, A., 2017, September. A practical fault attack on ARX-like ciphers with a case
study on ChaCha20. In 2017 Workshop on Fault Diagnosis and Tolerance in Cryptography
(FDTC) (pp. 33-40). IEEE.
Lim, J.P. and Nagarakatte, S., 2019, February. Automatic equivalence checking for assembly
implementations of cryptography libraries. In 2019 IEEE/ACM International Symposium on
Code Generation and Optimization (CGO) (pp. 37-49). IEEE.
Mohurle, S. and Patil, M., 2017. A brief study of wannacry threat: Ransomware attack
2017. International Journal of Advanced Research in Computer Science, 8(5).
Velea, R., Gurzău, F., Mărgărit, L., Bica, I. and Patriciu, V.V., 2016, May. Performance of
parallel ChaCha20 stream cipher. In 2016 IEEE 11th International Symposium on Applied
Computational Intelligence and Informatics (SACI) (pp. 391-396). IEEE.
Page 9 of 9
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





