Network Topology Design for a University Campus
VerifiedAdded on 2020/02/24
|11
|1836
|203
AI Summary
This assignment focuses on designing a robust computer network topology for a university campus. It covers the conceptual framework, specific implementations, including routing protocols, subnet configurations, and security measures. The design incorporates elements of redundancy and monitoring to ensure system reliability and performance. The document also outlines the process of testing and verifying the implemented network topology.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Executive Summary
The network design and the hardware requirements are being analysed in order to set up a wide
network infrastructure for GITAM University. The network design requirements are then identified
as per their campus structure and thereby analyzation has been carried out for the University.
The network design and the hardware requirements are being analysed in order to set up a wide
network infrastructure for GITAM University. The network design requirements are then identified
as per their campus structure and thereby analyzation has been carried out for the University.

Contents
1. Introduction.......................................................................................................................................4
2. Project Scope.....................................................................................................................................4
A. Analyse and discuss the significance of internetworking for GITAM University............................4
B. The role of internetworking to support business and technical goals through planning and
design................................................................................................................................................4
C. An architectural internetworking design for the business, information, technology, and
application domains..........................................................................................................................5
3. Project hardware requirements........................................................................................................5
3.1 Network Device...........................................................................................................................5
Other requirements.......................................................................................................................5
3.2 Cable Types..................................................................................................................................7
4. Network Design in Netsim.............................................................................................................7
4.1 Testing and Verification.............................................................................................................10
5. Conclusion.......................................................................................................................................11
References...........................................................................................................................................11
1. Introduction.......................................................................................................................................4
2. Project Scope.....................................................................................................................................4
A. Analyse and discuss the significance of internetworking for GITAM University............................4
B. The role of internetworking to support business and technical goals through planning and
design................................................................................................................................................4
C. An architectural internetworking design for the business, information, technology, and
application domains..........................................................................................................................5
3. Project hardware requirements........................................................................................................5
3.1 Network Device...........................................................................................................................5
Other requirements.......................................................................................................................5
3.2 Cable Types..................................................................................................................................7
4. Network Design in Netsim.............................................................................................................7
4.1 Testing and Verification.............................................................................................................10
5. Conclusion.......................................................................................................................................11
References...........................................................................................................................................11

1. Introduction
The fundamentals of network design for the University Campus are discussed in this section. To
design a network, its basic concepts such as the network topology also important to be considered
and its selection is an important criterion. The geometric representation of network topology is to
build relationship among all the links connecting the device nodes (Chapman Cooper & Zwicky,
2000). Network topology represents the physical topology and represents the way in which a
network is physically connected. It is logical topology that defines flow of data through the network.
Design types determine the type of Network for the Campus is interested to adopt in order to meet
their work system requirements. There are different types of designs available for the company to
adopt into their system. The various configurations used in the network set up is LAN, WAN, MAN
and CAN. The specific requirement depends upon how much big the area need to get covered along
with their complexity. In the small business network setting the need of high frequency Wi-Fi
connections demand are high in demand (Chen, Iyer & Whisnant, 2002).
2. Project Scope
To design, plan and develop IT network infrastructure for GITAM University and to select the
appropriate networking devices.
A. Analyse and discuss the significance of internetworking for GITAM University.
The plan is to analyse and address the star up issues with the University. It is related to their network
design, inter networking and implementation process. Since the University is going to have highly
distributed, heterogeneous and globalised set of branches across the area hence a comprehensive
system of network is designed to maintain their connectivity without any interruption. The network
topology is chosen initially and designed as per their requirements.
B. The role of internetworking to support business and technical goals through planning and
design.
Network is designed in order to provide 100% availability with time. Efforts are made to maintain the
network availability in wide adverse situations of link failure, equipment failure and overload
conditions. Network designed to support tremendous traffic loads with the time. Design is carried
out with consistent application response time. Protection is provided against unexpected security
incidents. The important necessity to build the network includes proper network topology, router,
wireless adaptor through which all their systems are internally connected.
The fundamentals of network design for the University Campus are discussed in this section. To
design a network, its basic concepts such as the network topology also important to be considered
and its selection is an important criterion. The geometric representation of network topology is to
build relationship among all the links connecting the device nodes (Chapman Cooper & Zwicky,
2000). Network topology represents the physical topology and represents the way in which a
network is physically connected. It is logical topology that defines flow of data through the network.
Design types determine the type of Network for the Campus is interested to adopt in order to meet
their work system requirements. There are different types of designs available for the company to
adopt into their system. The various configurations used in the network set up is LAN, WAN, MAN
and CAN. The specific requirement depends upon how much big the area need to get covered along
with their complexity. In the small business network setting the need of high frequency Wi-Fi
connections demand are high in demand (Chen, Iyer & Whisnant, 2002).
2. Project Scope
To design, plan and develop IT network infrastructure for GITAM University and to select the
appropriate networking devices.
A. Analyse and discuss the significance of internetworking for GITAM University.
The plan is to analyse and address the star up issues with the University. It is related to their network
design, inter networking and implementation process. Since the University is going to have highly
distributed, heterogeneous and globalised set of branches across the area hence a comprehensive
system of network is designed to maintain their connectivity without any interruption. The network
topology is chosen initially and designed as per their requirements.
B. The role of internetworking to support business and technical goals through planning and
design.
Network is designed in order to provide 100% availability with time. Efforts are made to maintain the
network availability in wide adverse situations of link failure, equipment failure and overload
conditions. Network designed to support tremendous traffic loads with the time. Design is carried
out with consistent application response time. Protection is provided against unexpected security
incidents. The important necessity to build the network includes proper network topology, router,
wireless adaptor through which all their systems are internally connected.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
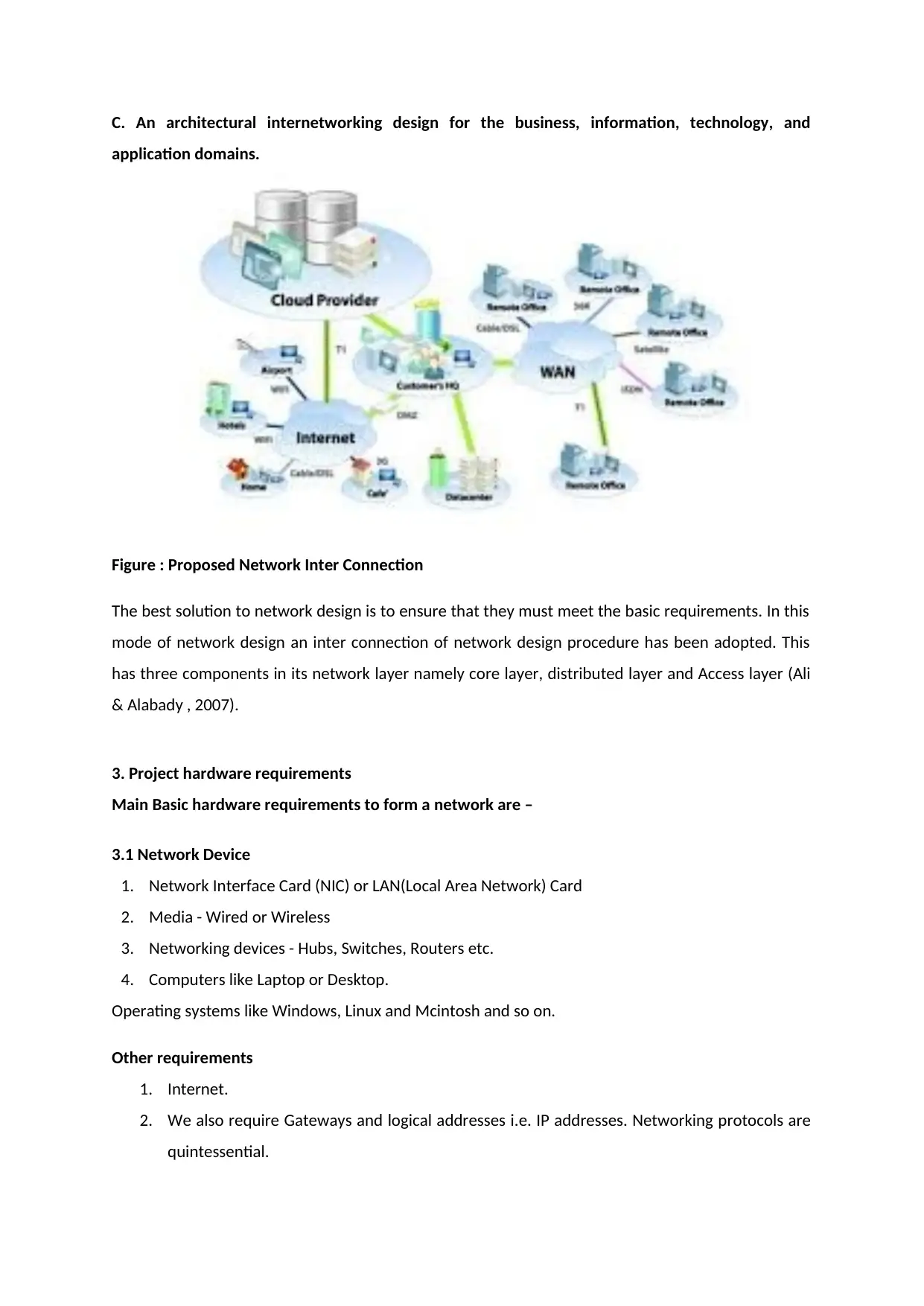
C. An architectural internetworking design for the business, information, technology, and
application domains.
Figure : Proposed Network Inter Connection
The best solution to network design is to ensure that they must meet the basic requirements. In this
mode of network design an inter connection of network design procedure has been adopted. This
has three components in its network layer namely core layer, distributed layer and Access layer (Ali
& Alabady , 2007).
3. Project hardware requirements
Main Basic hardware requirements to form a network are –
3.1 Network Device
1. Network Interface Card (NIC) or LAN(Local Area Network) Card
2. Media - Wired or Wireless
3. Networking devices - Hubs, Switches, Routers etc.
4. Computers like Laptop or Desktop.
Operating systems like Windows, Linux and Mcintosh and so on.
Other requirements
1. Internet.
2. We also require Gateways and logical addresses i.e. IP addresses. Networking protocols are
quintessential.
application domains.
Figure : Proposed Network Inter Connection
The best solution to network design is to ensure that they must meet the basic requirements. In this
mode of network design an inter connection of network design procedure has been adopted. This
has three components in its network layer namely core layer, distributed layer and Access layer (Ali
& Alabady , 2007).
3. Project hardware requirements
Main Basic hardware requirements to form a network are –
3.1 Network Device
1. Network Interface Card (NIC) or LAN(Local Area Network) Card
2. Media - Wired or Wireless
3. Networking devices - Hubs, Switches, Routers etc.
4. Computers like Laptop or Desktop.
Operating systems like Windows, Linux and Mcintosh and so on.
Other requirements
1. Internet.
2. We also require Gateways and logical addresses i.e. IP addresses. Networking protocols are
quintessential.
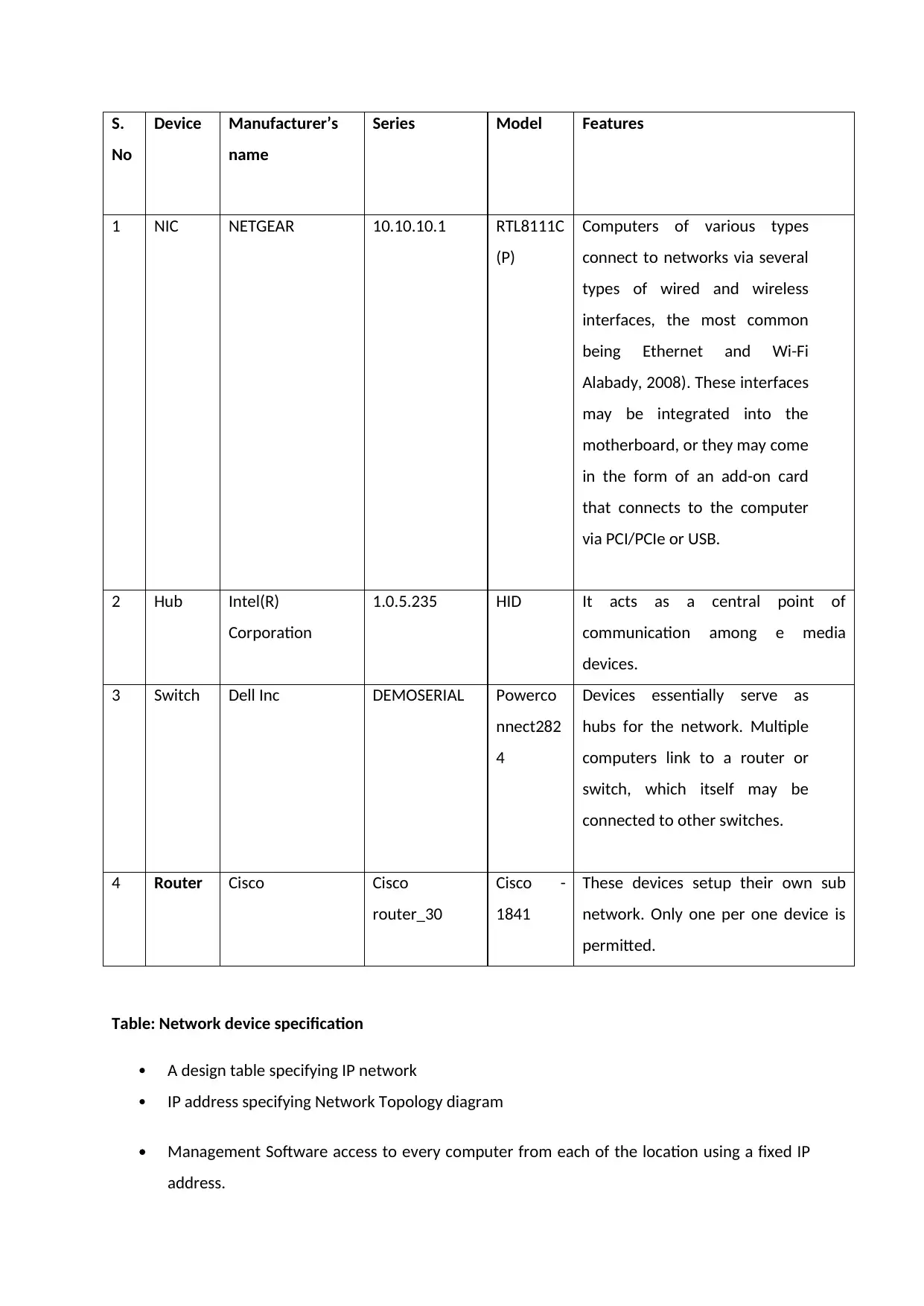
S.
No
Device Manufacturer’s
name
Series Model Features
1 NIC NETGEAR 10.10.10.1 RTL8111C
(P)
Computers of various types
connect to networks via several
types of wired and wireless
interfaces, the most common
being Ethernet and Wi-Fi
Alabady, 2008). These interfaces
may be integrated into the
motherboard, or they may come
in the form of an add-on card
that connects to the computer
via PCI/PCIe or USB.
2 Hub Intel(R)
Corporation
1.0.5.235 HID It acts as a central point of
communication among e media
devices.
3 Switch Dell Inc DEMOSERIAL Powerco
nnect282
4
Devices essentially serve as
hubs for the network. Multiple
computers link to a router or
switch, which itself may be
connected to other switches.
4 Router Cisco Cisco
router_30
Cisco -
1841
These devices setup their own sub
network. Only one per one device is
permitted.
Table: Network device specification
A design table specifying IP network
IP address specifying Network Topology diagram
Management Software access to every computer from each of the location using a fixed IP
address.
No
Device Manufacturer’s
name
Series Model Features
1 NIC NETGEAR 10.10.10.1 RTL8111C
(P)
Computers of various types
connect to networks via several
types of wired and wireless
interfaces, the most common
being Ethernet and Wi-Fi
Alabady, 2008). These interfaces
may be integrated into the
motherboard, or they may come
in the form of an add-on card
that connects to the computer
via PCI/PCIe or USB.
2 Hub Intel(R)
Corporation
1.0.5.235 HID It acts as a central point of
communication among e media
devices.
3 Switch Dell Inc DEMOSERIAL Powerco
nnect282
4
Devices essentially serve as
hubs for the network. Multiple
computers link to a router or
switch, which itself may be
connected to other switches.
4 Router Cisco Cisco
router_30
Cisco -
1841
These devices setup their own sub
network. Only one per one device is
permitted.
Table: Network device specification
A design table specifying IP network
IP address specifying Network Topology diagram
Management Software access to every computer from each of the location using a fixed IP
address.

Network configuration (ACL configuration and Router interface with explanation)
3.2 Cable Types
The cables are often used in the networking set up. Although now a days the cable requirements are
often, but the use of cable is perhaps required in minimum amount. There are various type of cable
such twisted pair cable unshielded, twisted pair cable shielded, co axial cable, fibre optic cable, and
wireless LANs.
3.3 Server and PC characteristics
The most important server operating system used is that UNIX –like operating system. They are open
source system. They have the features of ability to fast recognise and software and hardware
updating capacity without re starting the system. They have the capacity of flexibility an transparent
data transfer among the devices. They have to store tera bytes of data in daily basis and hence th
size of the data sources are enormous. The server has space ranging from 16 GB to 128 GB RAM and
are equipped with multi-tera byte HDD storage.
4. Network Design in Netsim
NetSim 8.0 is an application. This system of software allows to apply the vision of network design
within the application. They are performed using the Cisco command line equipment. NetSim is a
network simulation and emulation tool. It is mainly used for the purpose of network design. It is
done with the basis of network planning and management system. Many technologies are being
covered in th design process using NetSim. Thy are wireless sensor networks, wireless land area
network system, MANETs, LTE and many more.
Network Navigation
Network navigation mode allows viewing the devices tat are closely connected with each other and
with whom they are connected sequentially. At the same time they have the feature of displaying
the network connectivity in the active mode. By right clicking on the device, we can view the device
with the topology in order to access the selected device. The sequential set connectivity using
NetSim has been shown in the below representation. The simple way of connection is at first shown
and it is then followed by rest of the connectivity for the entire University campus.
3.2 Cable Types
The cables are often used in the networking set up. Although now a days the cable requirements are
often, but the use of cable is perhaps required in minimum amount. There are various type of cable
such twisted pair cable unshielded, twisted pair cable shielded, co axial cable, fibre optic cable, and
wireless LANs.
3.3 Server and PC characteristics
The most important server operating system used is that UNIX –like operating system. They are open
source system. They have the features of ability to fast recognise and software and hardware
updating capacity without re starting the system. They have the capacity of flexibility an transparent
data transfer among the devices. They have to store tera bytes of data in daily basis and hence th
size of the data sources are enormous. The server has space ranging from 16 GB to 128 GB RAM and
are equipped with multi-tera byte HDD storage.
4. Network Design in Netsim
NetSim 8.0 is an application. This system of software allows to apply the vision of network design
within the application. They are performed using the Cisco command line equipment. NetSim is a
network simulation and emulation tool. It is mainly used for the purpose of network design. It is
done with the basis of network planning and management system. Many technologies are being
covered in th design process using NetSim. Thy are wireless sensor networks, wireless land area
network system, MANETs, LTE and many more.
Network Navigation
Network navigation mode allows viewing the devices tat are closely connected with each other and
with whom they are connected sequentially. At the same time they have the feature of displaying
the network connectivity in the active mode. By right clicking on the device, we can view the device
with the topology in order to access the selected device. The sequential set connectivity using
NetSim has been shown in the below representation. The simple way of connection is at first shown
and it is then followed by rest of the connectivity for the entire University campus.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
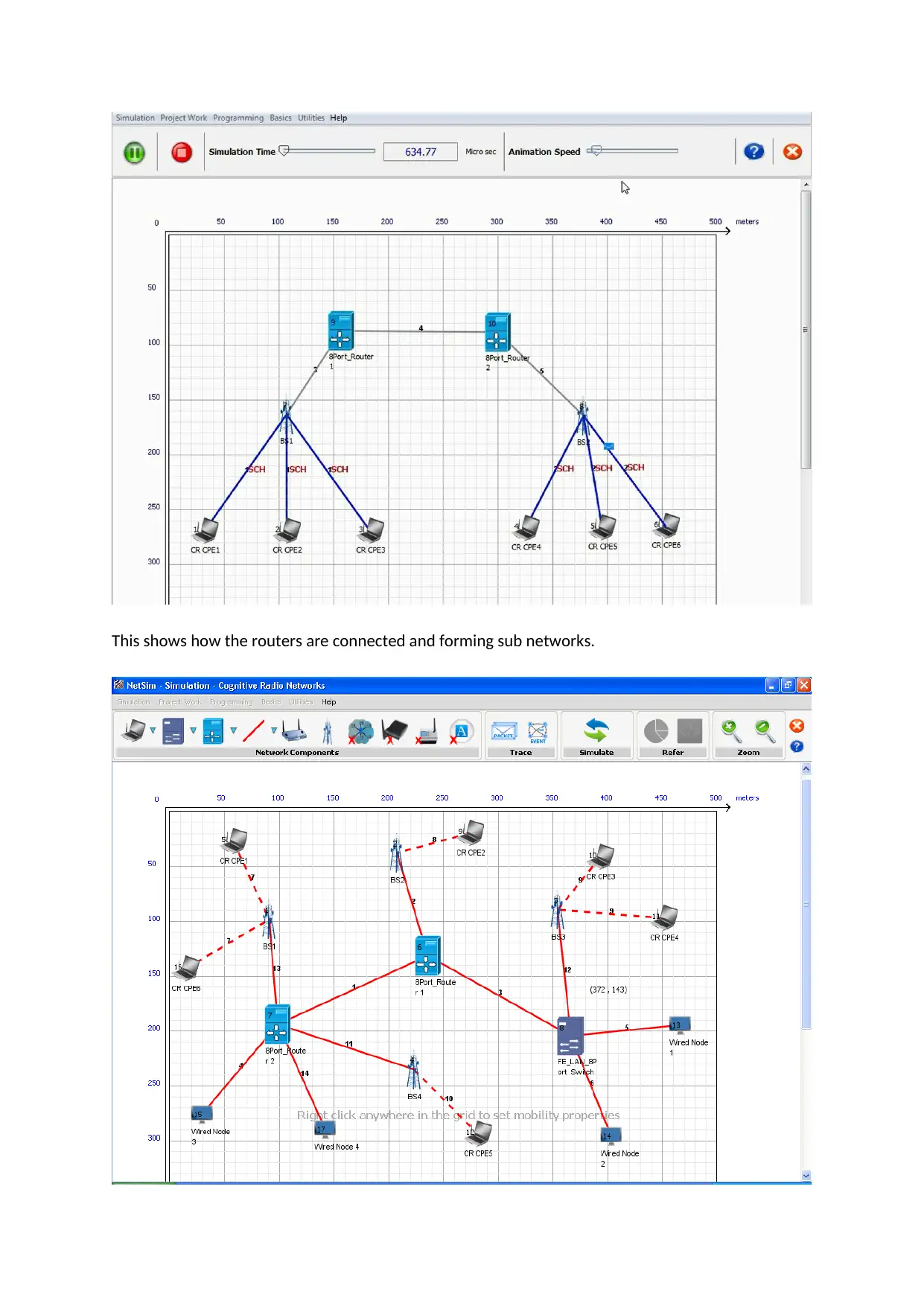
This shows how the routers are connected and forming sub networks.
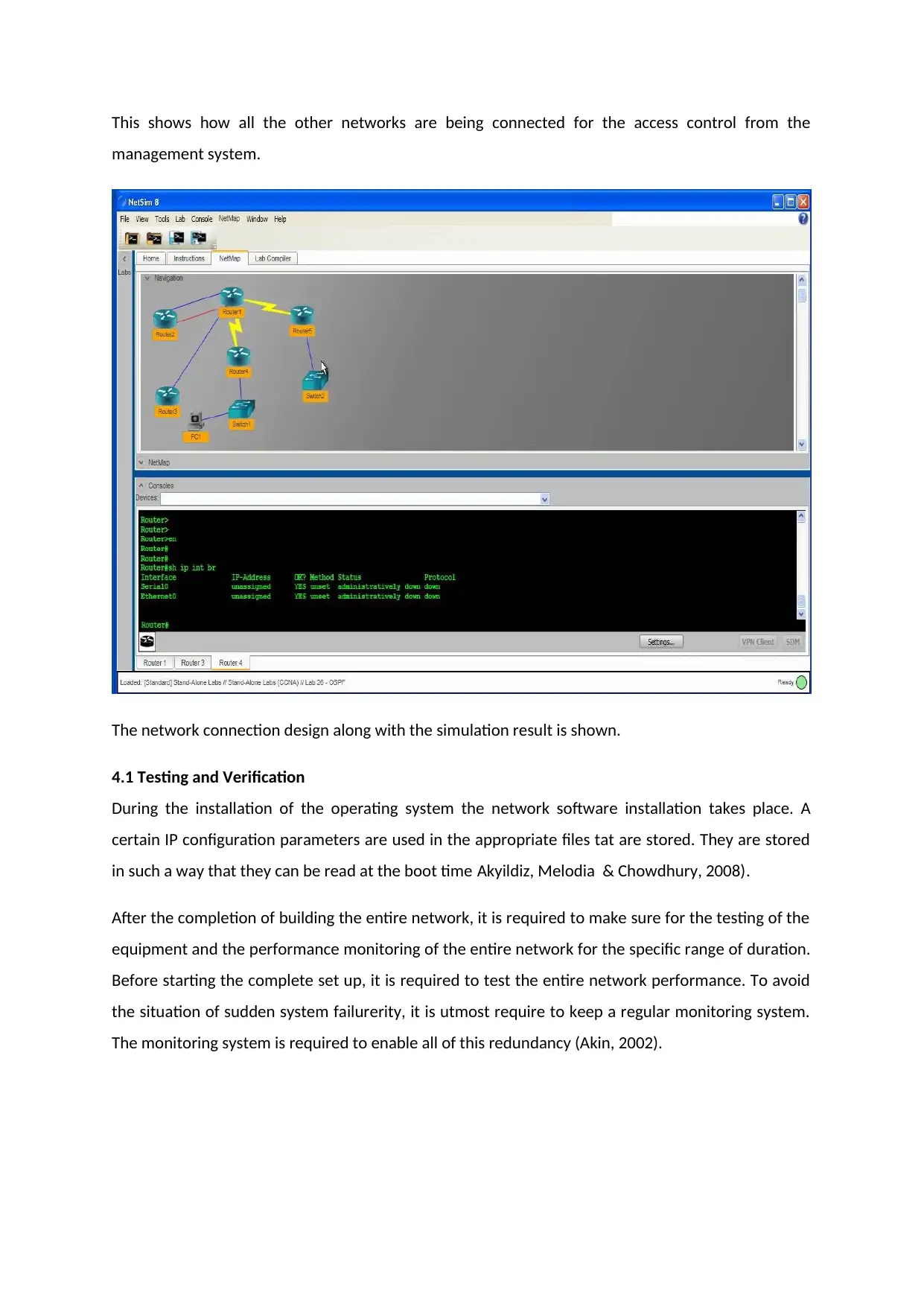
This shows how all the other networks are being connected for the access control from the
management system.
The network connection design along with the simulation result is shown.
4.1 Testing and Verification
During the installation of the operating system the network software installation takes place. A
certain IP configuration parameters are used in the appropriate files tat are stored. They are stored
in such a way that they can be read at the boot time Akyildiz, Melodia & Chowdhury, 2008).
After the completion of building the entire network, it is required to make sure for the testing of the
equipment and the performance monitoring of the entire network for the specific range of duration.
Before starting the complete set up, it is required to test the entire network performance. To avoid
the situation of sudden system failurerity, it is utmost require to keep a regular monitoring system.
The monitoring system is required to enable all of this redundancy (Akin, 2002).
management system.
The network connection design along with the simulation result is shown.
4.1 Testing and Verification
During the installation of the operating system the network software installation takes place. A
certain IP configuration parameters are used in the appropriate files tat are stored. They are stored
in such a way that they can be read at the boot time Akyildiz, Melodia & Chowdhury, 2008).
After the completion of building the entire network, it is required to make sure for the testing of the
equipment and the performance monitoring of the entire network for the specific range of duration.
Before starting the complete set up, it is required to test the entire network performance. To avoid
the situation of sudden system failurerity, it is utmost require to keep a regular monitoring system.
The monitoring system is required to enable all of this redundancy (Akin, 2002).

5. Conclusion
World class University in today’s scenario is impossible without emails, online banking and all other
important services that are linked by the internet. The services computer network plays an
important role to access the information necessary to maintain the connecting operation. For
interconnectivity of components within the campus a network topology adapts to the physical and
set up and to maintain the interconnection between arrangement of computers, cables and other
component. It is important in a data communication network since the information travels through
packet form from one device and sending it through the network to another device on a different
network.
World class University in today’s scenario is impossible without emails, online banking and all other
important services that are linked by the internet. The services computer network plays an
important role to access the information necessary to maintain the connecting operation. For
interconnectivity of components within the campus a network topology adapts to the physical and
set up and to maintain the interconnection between arrangement of computers, cables and other
component. It is important in a data communication network since the information travels through
packet form from one device and sending it through the network to another device on a different
network.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

References
Akin, T. (2002), Hardening Cisco Routers. O’Reilly & Associates.
Akyildiz, F., Melodia, T. & Chowdhury, R. (2008). Wireless Multimedia Sensor Networks: Applications
and Testbeds, Proceedings of the IEEE, vol. 96, no. 10, pp. 1588-1605.
Alabady, S. (2008). Design and Implementation of a Network Security Model using Static VLAN and
AAA Server, In Proceedings International Conference on Information & Communication
Technologies: from Theory to Applications, ICTTA.
Ali, Q. & Alabady ,S. (2007). Design and Implementation of A Secured Remotely Administrated
Network, In Proceedings International Arab Conference on Information Technology, ACIT .
Chapman D., Cooper S. & Zwicky, E. (2000). Building Internet Firewalls, 2nd Edition, O’Reilly &
Associates.
Chen S., Iyer R., & Whisnant K. (2002). Evaluating the Security Threat of Firewall Data Corruption
Caused by Instruction Transient Errors, In Proceedings of the 2002 International Conference
on Dependable Systems & Network, Washington, D.C.
Akin, T. (2002), Hardening Cisco Routers. O’Reilly & Associates.
Akyildiz, F., Melodia, T. & Chowdhury, R. (2008). Wireless Multimedia Sensor Networks: Applications
and Testbeds, Proceedings of the IEEE, vol. 96, no. 10, pp. 1588-1605.
Alabady, S. (2008). Design and Implementation of a Network Security Model using Static VLAN and
AAA Server, In Proceedings International Conference on Information & Communication
Technologies: from Theory to Applications, ICTTA.
Ali, Q. & Alabady ,S. (2007). Design and Implementation of A Secured Remotely Administrated
Network, In Proceedings International Arab Conference on Information Technology, ACIT .
Chapman D., Cooper S. & Zwicky, E. (2000). Building Internet Firewalls, 2nd Edition, O’Reilly &
Associates.
Chen S., Iyer R., & Whisnant K. (2002). Evaluating the Security Threat of Firewall Data Corruption
Caused by Instruction Transient Errors, In Proceedings of the 2002 International Conference
on Dependable Systems & Network, Washington, D.C.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





