ABC Pvt. Ltd. Information Security Policy Planning Project
VerifiedAdded on 2022/09/16
|7
|986
|15
Project
AI Summary
This project centers on the creation of an information security policy for ABC Pvt. Ltd., addressing key elements such as policy definition, purpose, scope, and target audience. The policy aims to enhance employee awareness regarding data protection and cyber security threats. It outlines objectives for availability, confidentiality, and integrity of data, alongside standards, roles, responsibilities, and detailed procedures and guidelines for employees, including password security, data encryption, and reporting of malicious activities. Compliance and enforcement measures are specified, with provisions for non-compliance and exceptions. The project also includes references and contact information for queries. The document follows the assignment brief's structure, covering all required policy elements and providing a clear framework for information security within the organization. This project is available on Desklib, along with other related assignments and solutions.

Running head: POLICY PLANNING
Policy for information security within Organization
Name of the Student
Name of the University
Author Note
Policy for information security within Organization
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1POLICY PLANNING
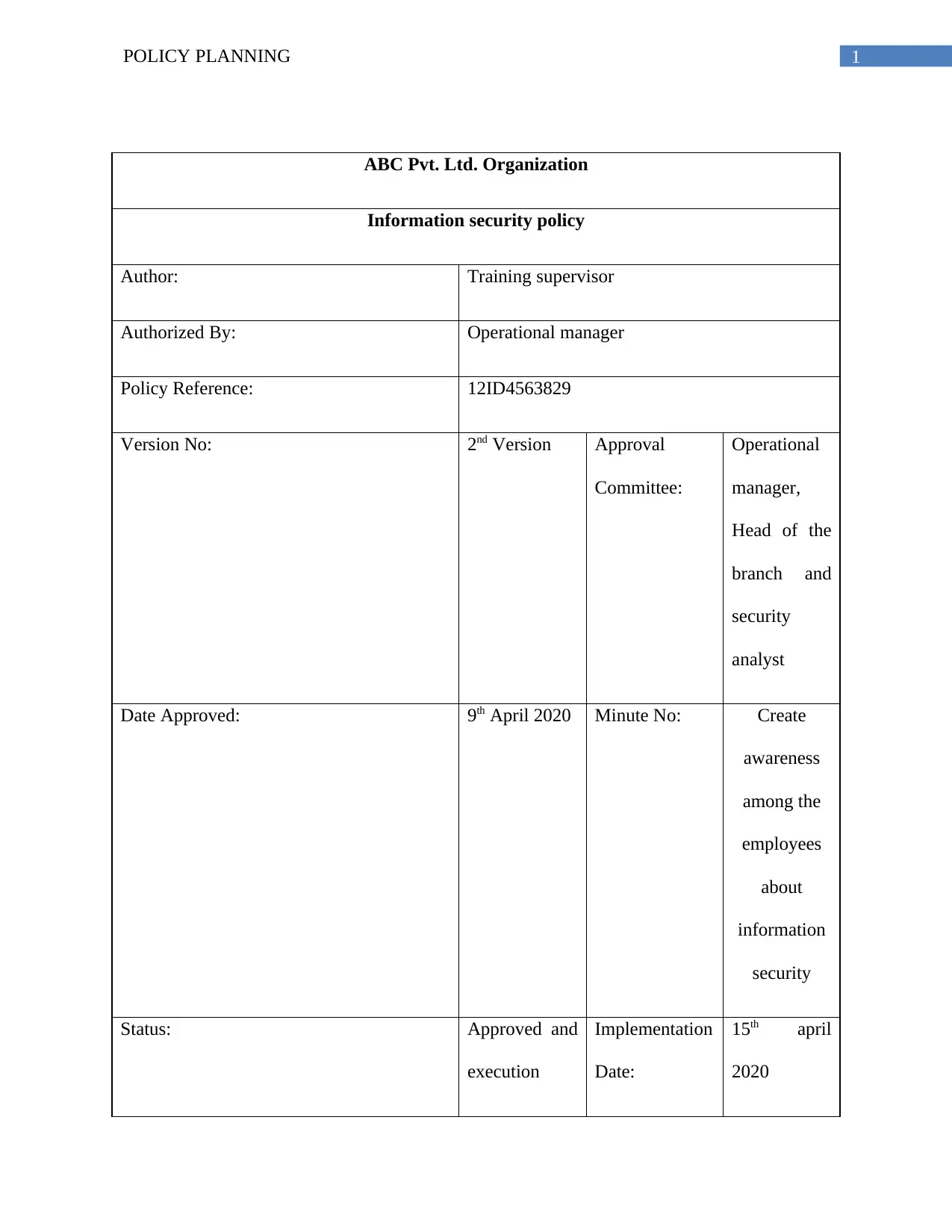
ABC Pvt. Ltd. Organization
Information security policy
Author: Training supervisor
Authorized By: Operational manager
Policy Reference: 12ID4563829
Version No: 2nd Version Approval
Committee:
Operational
manager,
Head of the
branch and
security
analyst
Date Approved: 9th April 2020 Minute No: Create
awareness
among the
employees
about
information
security
Status: Approved and
execution
Implementation
Date:
15th april
2020
ABC Pvt. Ltd. Organization
Information security policy
Author: Training supervisor
Authorized By: Operational manager
Policy Reference: 12ID4563829
Version No: 2nd Version Approval
Committee:
Operational
manager,
Head of the
branch and
security
analyst
Date Approved: 9th April 2020 Minute No: Create
awareness
among the
employees
about
information
security
Status: Approved and
execution
Implementation
Date:
15th april
2020
2POLICY PLANNING
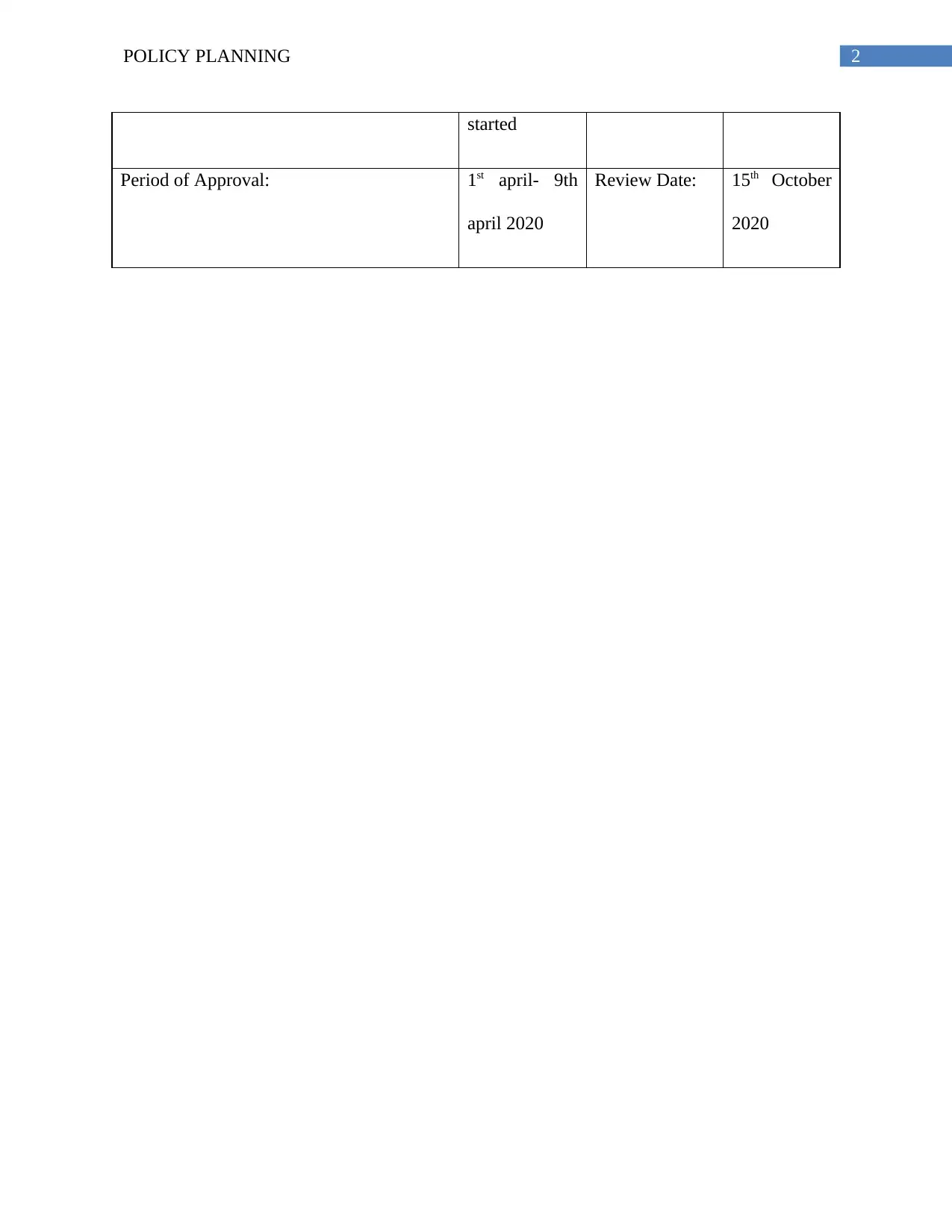
started
Period of Approval: 1st april- 9th
april 2020
Review Date: 15th October
2020
started
Period of Approval: 1st april- 9th
april 2020
Review Date: 15th October
2020
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3POLICY PLANNING
Policy definition: The aim of the policy is to create awareness among the employees so that they
can protect their system from unwanted threats. Information security is essential while working
within an organization as this ensures that all the crucial data associated with the organization are
protected from hackers. As the data are shared on cloud, there is a need to have proper
knowledge how to protect the data from cyber attackers and hackers.
Purpose: The purpose is to create awareness so that the employees can safeguard their data.
With the help of this training, it will become easy to create awareness among the employees
about the importance of information security. Every data within an employee system must be
protected so that no one can access the data with proper permission.
Scope: The training will be conducted for a week that will ensure that each and every employee
is demonstrated with the necessity of information security. In addition to this, ways to protect
information will also be explained. It is compulsory for every employee to attend the training
during their office hours. It is expected that through training it will become easy to manage the
way employee manages their data sets. Every data needs to be managed so that it does not cause
any issue in future.
Target audience or applicability: Every employee present within the organization must attend
the training and should implement the measures while working within the organization.
Objective: Information security policy is designed for the employees with certain objectives that
are discussed below:
Availability: the data stored within the system are made available towards the users. Information
is made available on correct time and with proper accessibility features.
Policy definition: The aim of the policy is to create awareness among the employees so that they
can protect their system from unwanted threats. Information security is essential while working
within an organization as this ensures that all the crucial data associated with the organization are
protected from hackers. As the data are shared on cloud, there is a need to have proper
knowledge how to protect the data from cyber attackers and hackers.
Purpose: The purpose is to create awareness so that the employees can safeguard their data.
With the help of this training, it will become easy to create awareness among the employees
about the importance of information security. Every data within an employee system must be
protected so that no one can access the data with proper permission.
Scope: The training will be conducted for a week that will ensure that each and every employee
is demonstrated with the necessity of information security. In addition to this, ways to protect
information will also be explained. It is compulsory for every employee to attend the training
during their office hours. It is expected that through training it will become easy to manage the
way employee manages their data sets. Every data needs to be managed so that it does not cause
any issue in future.
Target audience or applicability: Every employee present within the organization must attend
the training and should implement the measures while working within the organization.
Objective: Information security policy is designed for the employees with certain objectives that
are discussed below:
Availability: the data stored within the system are made available towards the users. Information
is made available on correct time and with proper accessibility features.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4POLICY PLANNING
Confidentiality: Data stored in every individual system must be maintained with proper
confidentiality and should not be disclosed to unauthorized users.
Integrity: Every employee must ensure that the data stored within the system are maintained with
proper integrity and are not altered by any external user.
Standard: The policy is designed for the organizational standard so that every employee can
abide by the rules set.
Roles and responsibilities: It is responsibility of the operational manger and training supervisor
to ensure that proper objective off the policy is explained towards the employees. It is important
to understand the importance of the policy developed as this will protect the confidential data
sets associated with the organization. Every member must work efficiently so that the objective
behind implementing the policy can be fulfilled successfully.
Procedures and guidelines: Every member of the organization must attend the training. The
training will be conducted for 45 minutes every day and will ensure that all necessary
information security aspects are explained. The follow guidelines for the employees:
Every must use strong passwords
No one is allowed to share their devices with other employees
Before sharing any data on cloud it is important to use proper encryption
Data must be updated frequently
Employee must change their password frequently
Use firewall and anti-spyware
Malicious activities on the system must be reported to operational manager
Confidentiality: Data stored in every individual system must be maintained with proper
confidentiality and should not be disclosed to unauthorized users.
Integrity: Every employee must ensure that the data stored within the system are maintained with
proper integrity and are not altered by any external user.
Standard: The policy is designed for the organizational standard so that every employee can
abide by the rules set.
Roles and responsibilities: It is responsibility of the operational manger and training supervisor
to ensure that proper objective off the policy is explained towards the employees. It is important
to understand the importance of the policy developed as this will protect the confidential data
sets associated with the organization. Every member must work efficiently so that the objective
behind implementing the policy can be fulfilled successfully.
Procedures and guidelines: Every member of the organization must attend the training. The
training will be conducted for 45 minutes every day and will ensure that all necessary
information security aspects are explained. The follow guidelines for the employees:
Every must use strong passwords
No one is allowed to share their devices with other employees
Before sharing any data on cloud it is important to use proper encryption
Data must be updated frequently
Employee must change their password frequently
Use firewall and anti-spyware
Malicious activities on the system must be reported to operational manager

5POLICY PLANNING
Compliance and enforcement: Every individual must abide by the laws and anyone found not
to follow the rules will be punished. Following the policy is very essential as this will ensure that
the data stored are protected from unauthorized users. The policy will be affected from 15th of
June 2020. Every employee performance will be monitored so that it becomes easy to understand
the issues that are faced by them while using the system.
Non-compliance and Exceptions: After implementing the policy, one week will be provided
towards every employee for understanding the policy efficiently. In case of any unintended
mistakes, the employees will be offered with a second chance. Employee must report the issues
if needed so that they does not face any challenges in future.
References:
Cherdantseva, Y. and Hilton, J., 2013, September. A reference model of information assurance &
security. In 2013 International Conference on Availability, Reliability and Security (pp. 546-
555). IEEE.
Goodman, S., Straub, D.W. and Baskerville, R., 2016. Information security: policy, processes,
and practices. Routledge.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance model
in organizations. computers & security, 56, pp.70-82.
Siponen, M., Mahmood, M.A. and Pahnila, S., 2014. Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), pp.217-224.
Contacts: For any query, employees can contact HR Manger, Operational manager and Training
supervisor.
Compliance and enforcement: Every individual must abide by the laws and anyone found not
to follow the rules will be punished. Following the policy is very essential as this will ensure that
the data stored are protected from unauthorized users. The policy will be affected from 15th of
June 2020. Every employee performance will be monitored so that it becomes easy to understand
the issues that are faced by them while using the system.
Non-compliance and Exceptions: After implementing the policy, one week will be provided
towards every employee for understanding the policy efficiently. In case of any unintended
mistakes, the employees will be offered with a second chance. Employee must report the issues
if needed so that they does not face any challenges in future.
References:
Cherdantseva, Y. and Hilton, J., 2013, September. A reference model of information assurance &
security. In 2013 International Conference on Availability, Reliability and Security (pp. 546-
555). IEEE.
Goodman, S., Straub, D.W. and Baskerville, R., 2016. Information security: policy, processes,
and practices. Routledge.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance model
in organizations. computers & security, 56, pp.70-82.
Siponen, M., Mahmood, M.A. and Pahnila, S., 2014. Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), pp.217-224.
Contacts: For any query, employees can contact HR Manger, Operational manager and Training
supervisor.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6POLICY PLANNING
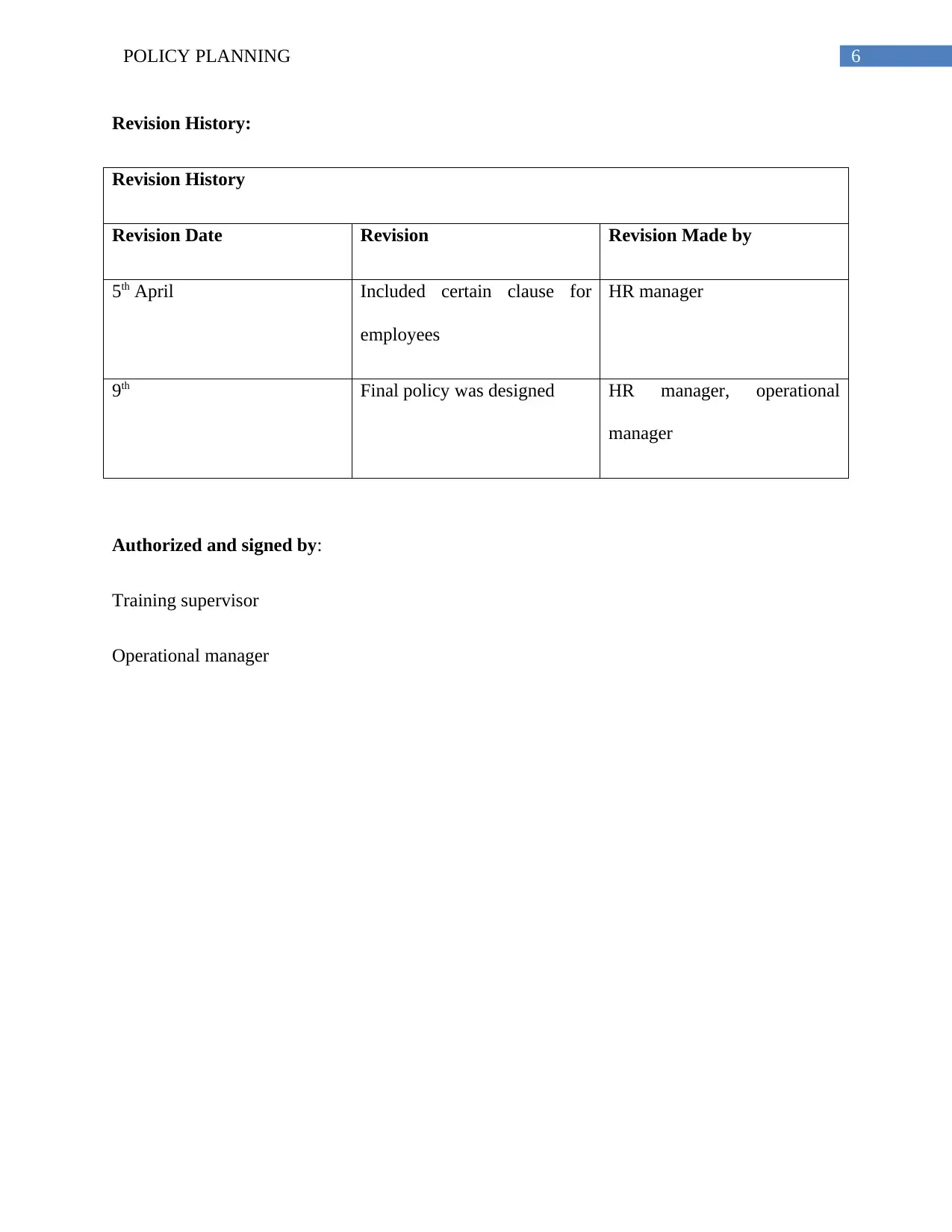
Revision History:
Revision History
Revision Date Revision Revision Made by
5th April Included certain clause for
employees
HR manager
9th Final policy was designed HR manager, operational
manager
Authorized and signed by:
Training supervisor
Operational manager
Revision History:
Revision History
Revision Date Revision Revision Made by
5th April Included certain clause for
employees
HR manager
9th Final policy was designed HR manager, operational
manager
Authorized and signed by:
Training supervisor
Operational manager
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





