University of Hertfordshire 7COM1068: Penetration Testing Report
VerifiedAdded on 2022/08/18
|13
|2748
|20
Report
AI Summary
This report delves into the realm of penetration testing, a crucial practice for identifying security vulnerabilities in computer systems and networks. It explores various approaches, including manual and automated methods, and categorizes methodologies into white box, black box, and gray box testing, each with its own characteristics and applications. The report provides a comparative analysis of these approaches, highlighting their strengths and weaknesses. Furthermore, it outlines standard operating procedures for IT security penetration testing, emphasizing the importance of planning, vulnerability analysis, and ethical considerations. The report also addresses statutory and ethical issues, including the Open Source Security Testing Methodology Manual (OSSTMM) guidelines. Finally, a decision tree is presented to aid in the penetration testing process, and the conclusion summarizes the key findings and recommendations related to the subject. The report is a comprehensive resource for understanding and implementing effective penetration testing strategies.

Running head: PENETRATION TESTING
PENETRATION TESTING
Name of the Student
Name of the university
Author note
PENETRATION TESTING
Name of the Student
Name of the university
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1PENETRATION TESTING
Table of Contents
Introduction................................................................................................................................2
Approaches to perform pen testing............................................................................................2
Methodologies of Penetration Testing.......................................................................................3
Comparison of the approaches...............................................................................................5
Procedures for IT Security Penetration Testing.........................................................................6
Statutory and ethical issue of penetration testing.......................................................................8
Decision Tree.............................................................................................................................9
Conclusion..................................................................................................................................9
References................................................................................................................................11
Table of Contents
Introduction................................................................................................................................2
Approaches to perform pen testing............................................................................................2
Methodologies of Penetration Testing.......................................................................................3
Comparison of the approaches...............................................................................................5
Procedures for IT Security Penetration Testing.........................................................................6
Statutory and ethical issue of penetration testing.......................................................................8
Decision Tree.............................................................................................................................9
Conclusion..................................................................................................................................9
References................................................................................................................................11

2PENETRATION TESTING
Introduction
Penetration testing or pen testing refers to the practice of checking a computer system,
Web application or a network so that the security vulnerabilities in these can be found out.
Software applications can be made use to automate penetration testing or this can also be
performed manually. Whether by software applications or manually, this requires gathering
information related to the target before it is done. The probable entry points and the attempts
of breaking in to the system and all such aspects that relates to the security of the system is to
be considered in this (Baloch 2017). The primary objective of pen testing is identifying
security vulnerabilities. This is made use of to check organization’s security policy, whether
it compliances to various requirements, the security awareness of employees as well as the
firm’s ability to both indentify and provide response to security related incidents.
In this paper, the various methodologies of penetration testing will be discussed and a
comparison been made between them. The statutory as well as legal issues related to pen
testing will be discussed as well. Standard Operating Procedure (SOP) and a decision making
tree will also be designed considering a pen testing against a specific target system.
Approaches to perform pen testing
The below mentioned approaches can be made use of to conduct penetration testing:
1. Manual Pen Testing- Manual penetration testing involves a specific standard approach
comprising of different activities that needs to be carried out in a certain sequence (Sandhya,
Purkayastha, Joshua and Deep 2017). The sequence is as given below:
a) Planning for conducting the penetration testing
b) Reconnaissance
Introduction
Penetration testing or pen testing refers to the practice of checking a computer system,
Web application or a network so that the security vulnerabilities in these can be found out.
Software applications can be made use to automate penetration testing or this can also be
performed manually. Whether by software applications or manually, this requires gathering
information related to the target before it is done. The probable entry points and the attempts
of breaking in to the system and all such aspects that relates to the security of the system is to
be considered in this (Baloch 2017). The primary objective of pen testing is identifying
security vulnerabilities. This is made use of to check organization’s security policy, whether
it compliances to various requirements, the security awareness of employees as well as the
firm’s ability to both indentify and provide response to security related incidents.
In this paper, the various methodologies of penetration testing will be discussed and a
comparison been made between them. The statutory as well as legal issues related to pen
testing will be discussed as well. Standard Operating Procedure (SOP) and a decision making
tree will also be designed considering a pen testing against a specific target system.
Approaches to perform pen testing
The below mentioned approaches can be made use of to conduct penetration testing:
1. Manual Pen Testing- Manual penetration testing involves a specific standard approach
comprising of different activities that needs to be carried out in a certain sequence (Sandhya,
Purkayastha, Joshua and Deep 2017). The sequence is as given below:
a) Planning for conducting the penetration testing
b) Reconnaissance
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3PENETRATION TESTING
c) Vulnerability Analysis
d) Exploitation
i) External Attacks
ii) Internal Attacks
e) Scenario post exploitation
d) Reporting
2. Automated Penetration Testing- Automated Pen Testing is conducted by making use of
different performance testing tools (Stiawan et al. 2016). The tools that are used in most of
the cases are given below:
a) Nmap
b) Nessus
c) Metaspoilt
d) Wireshark
e) Veracode
3) Manual Pen Testing along with Automated Pen Testing- The different benefits of
manual and automated testing ensure that the pen testing being conducted is effective,
properly monitored as well as precise (Falagush, McDowell, Yu and de Bono, 2015).
Methodologies of Penetration Testing
Depending on the different testing approaches, penetration testing can be categorized
into the following:
c) Vulnerability Analysis
d) Exploitation
i) External Attacks
ii) Internal Attacks
e) Scenario post exploitation
d) Reporting
2. Automated Penetration Testing- Automated Pen Testing is conducted by making use of
different performance testing tools (Stiawan et al. 2016). The tools that are used in most of
the cases are given below:
a) Nmap
b) Nessus
c) Metaspoilt
d) Wireshark
e) Veracode
3) Manual Pen Testing along with Automated Pen Testing- The different benefits of
manual and automated testing ensure that the pen testing being conducted is effective,
properly monitored as well as precise (Falagush, McDowell, Yu and de Bono, 2015).
Methodologies of Penetration Testing
Depending on the different testing approaches, penetration testing can be categorized
into the following:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4PENETRATION TESTING
1. White Box Pen Testing- In this particular approach the tester has full access along with in-
depth knowledge of system that requires checking for security vulnerabilities. This approach
is considered to be effective in case of extensive penetration testing. In this approach, internal
perspective of the whole system along with programming skills is made use of to develop the
various test cases (Nagpal, Singh, Chauhan and Panesar 2015). The tester in this case chooses
various inputs to exercise different paths through the code thus determining the desired
outputs. This approach can be said to be testing the system or the application at the source
code level.
2. Black Box Pen Testing- In this approach the tester is provided with high-level information
and he is totally unaware of the network. This approach checks the functionality of a system
or application without trying to peer into the internal structure of workings. This method of
pen testing is generally applicable to every stage of software testing that includes unit,
system, acceptance and integration (Al Shebli and Beheshti 2018). In this approach, specific
knowledge related to the application’s code, knowledge of programming as well as internal
structure is not needed. The tester here is well aware of what is expected from the software
but is unaware of the way it is done. In this approach, the test cases are built around the
various specifications and associated requirements.
3. Gray Box Pen Testing- This is the technique or the approach in which the tester has partial
knowledge of the internal workings of the application. The main purpose of this approach is
to find out the defects that can be there for improper structure of the codes or improper
functioning usage of any application. It can be said to be a combination of white box and
black box penetration testing. This approach provides the combined benefits of both white
box penetration testing and black box penetration testing (Johns 2015). Gray Box Penetration
testing provides ample amount of free time for a developer for fixing the defects. The testing
in case is done considering the point of view of the user instead of that of the designer.
1. White Box Pen Testing- In this particular approach the tester has full access along with in-
depth knowledge of system that requires checking for security vulnerabilities. This approach
is considered to be effective in case of extensive penetration testing. In this approach, internal
perspective of the whole system along with programming skills is made use of to develop the
various test cases (Nagpal, Singh, Chauhan and Panesar 2015). The tester in this case chooses
various inputs to exercise different paths through the code thus determining the desired
outputs. This approach can be said to be testing the system or the application at the source
code level.
2. Black Box Pen Testing- In this approach the tester is provided with high-level information
and he is totally unaware of the network. This approach checks the functionality of a system
or application without trying to peer into the internal structure of workings. This method of
pen testing is generally applicable to every stage of software testing that includes unit,
system, acceptance and integration (Al Shebli and Beheshti 2018). In this approach, specific
knowledge related to the application’s code, knowledge of programming as well as internal
structure is not needed. The tester here is well aware of what is expected from the software
but is unaware of the way it is done. In this approach, the test cases are built around the
various specifications and associated requirements.
3. Gray Box Pen Testing- This is the technique or the approach in which the tester has partial
knowledge of the internal workings of the application. The main purpose of this approach is
to find out the defects that can be there for improper structure of the codes or improper
functioning usage of any application. It can be said to be a combination of white box and
black box penetration testing. This approach provides the combined benefits of both white
box penetration testing and black box penetration testing (Johns 2015). Gray Box Penetration
testing provides ample amount of free time for a developer for fixing the defects. The testing
in case is done considering the point of view of the user instead of that of the designer.
5PENETRATION TESTING
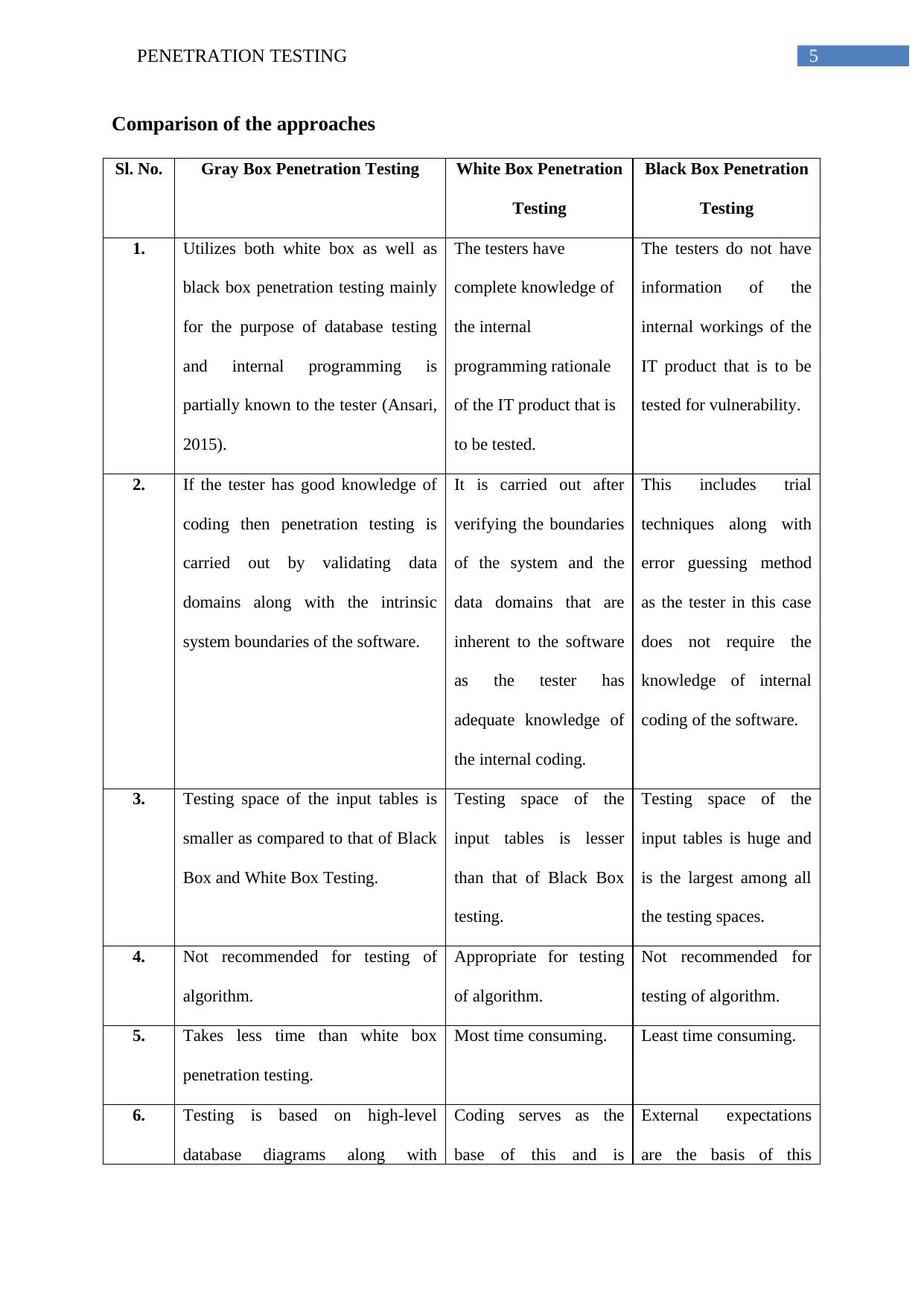
Comparison of the approaches
Sl. No. Gray Box Penetration Testing White Box Penetration
Testing
Black Box Penetration
Testing
1. Utilizes both white box as well as
black box penetration testing mainly
for the purpose of database testing
and internal programming is
partially known to the tester (Ansari,
2015).
The testers have
complete knowledge of
the internal
programming rationale
of the IT product that is
to be tested.
The testers do not have
information of the
internal workings of the
IT product that is to be
tested for vulnerability.
2. If the tester has good knowledge of
coding then penetration testing is
carried out by validating data
domains along with the intrinsic
system boundaries of the software.
It is carried out after
verifying the boundaries
of the system and the
data domains that are
inherent to the software
as the tester has
adequate knowledge of
the internal coding.
This includes trial
techniques along with
error guessing method
as the tester in this case
does not require the
knowledge of internal
coding of the software.
3. Testing space of the input tables is
smaller as compared to that of Black
Box and White Box Testing.
Testing space of the
input tables is lesser
than that of Black Box
testing.
Testing space of the
input tables is huge and
is the largest among all
the testing spaces.
4. Not recommended for testing of
algorithm.
Appropriate for testing
of algorithm.
Not recommended for
testing of algorithm.
5. Takes less time than white box
penetration testing.
Most time consuming. Least time consuming.
6. Testing is based on high-level
database diagrams along with
Coding serves as the
base of this and is
External expectations
are the basis of this
Comparison of the approaches
Sl. No. Gray Box Penetration Testing White Box Penetration
Testing
Black Box Penetration
Testing
1. Utilizes both white box as well as
black box penetration testing mainly
for the purpose of database testing
and internal programming is
partially known to the tester (Ansari,
2015).
The testers have
complete knowledge of
the internal
programming rationale
of the IT product that is
to be tested.
The testers do not have
information of the
internal workings of the
IT product that is to be
tested for vulnerability.
2. If the tester has good knowledge of
coding then penetration testing is
carried out by validating data
domains along with the intrinsic
system boundaries of the software.
It is carried out after
verifying the boundaries
of the system and the
data domains that are
inherent to the software
as the tester has
adequate knowledge of
the internal coding.
This includes trial
techniques along with
error guessing method
as the tester in this case
does not require the
knowledge of internal
coding of the software.
3. Testing space of the input tables is
smaller as compared to that of Black
Box and White Box Testing.
Testing space of the
input tables is lesser
than that of Black Box
testing.
Testing space of the
input tables is huge and
is the largest among all
the testing spaces.
4. Not recommended for testing of
algorithm.
Appropriate for testing
of algorithm.
Not recommended for
testing of algorithm.
5. Takes less time than white box
penetration testing.
Most time consuming. Least time consuming.
6. Testing is based on high-level
database diagrams along with
Coding serves as the
base of this and is
External expectations
are the basis of this
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6PENETRATION TESTING
dataflow diagrams. responsible for the
internal working as well.
testing as the intrinsic
behavior of the software
is not known.
Procedures for IT Security Penetration Testing
Security penetration testing refers to the activity in which there is attest team that attempts to
circumvent the different security processes thus controlling the computer system. The test
team poses as internal or external unauthorized intruder thus obtaining access, extracting
information as well as demonstrating the capability to manipulate the specific computer
system that has been targeted (Zhang, Arroyo, Ciantia, Gens and Butlanska 2019). The
sensitive nature of penetration testing requires that some specific rules be applied. The
procedures for penetration testing of the systems at particular sites or centers are as follows:
1. Planning for the penetration test- As the penetration testing is to done at a site therefore it
is required hat a Site Point of Contact or POC along with Pan Test POC is identified. This
identified POC is vested with the job of coordination of the various activities that are related
to pen testing. The management is to be notified of the activities and the schedule so that the
activities can take place on time (Hussain, Hasan and Chughtai 2017). The Penetration
Testing POC acts as the primary interface with that of Site POC for different activities of pen
testing. It is the duty of the Pen Tester to develop all the required documentation as well as
the plan related to penetration testing. The Pen Tester is vested with the responsibility to
assign different role to his team members so that the work is carried out properly.
2. Analysis of the vulnerabilities- This includes many important activities such as:
a) Identifying the possible targets.
dataflow diagrams. responsible for the
internal working as well.
testing as the intrinsic
behavior of the software
is not known.
Procedures for IT Security Penetration Testing
Security penetration testing refers to the activity in which there is attest team that attempts to
circumvent the different security processes thus controlling the computer system. The test
team poses as internal or external unauthorized intruder thus obtaining access, extracting
information as well as demonstrating the capability to manipulate the specific computer
system that has been targeted (Zhang, Arroyo, Ciantia, Gens and Butlanska 2019). The
sensitive nature of penetration testing requires that some specific rules be applied. The
procedures for penetration testing of the systems at particular sites or centers are as follows:
1. Planning for the penetration test- As the penetration testing is to done at a site therefore it
is required hat a Site Point of Contact or POC along with Pan Test POC is identified. This
identified POC is vested with the job of coordination of the various activities that are related
to pen testing. The management is to be notified of the activities and the schedule so that the
activities can take place on time (Hussain, Hasan and Chughtai 2017). The Penetration
Testing POC acts as the primary interface with that of Site POC for different activities of pen
testing. It is the duty of the Pen Tester to develop all the required documentation as well as
the plan related to penetration testing. The Pen Tester is vested with the responsibility to
assign different role to his team members so that the work is carried out properly.
2. Analysis of the vulnerabilities- This includes many important activities such as:
a) Identifying the possible targets.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7PENETRATION TESTING
b) Identifying all the potential vulnerabilities
c) Performing the various vulnerability scans
d) Buffering overflows
e) IP spoofing
f) Social engineering
g) Manipulating the touting tables
h) Performing certain manual tests
3. Penetration testing- For the sites being tested for vulnerabilities, the Pen Tester requires to
perform certain tasks:
i. Introductory Briefing
ii. Technical along with Administrative Face-to-Face Meeting
iii. Executive In-Briefing
iv. Reviewing the various IT Security Policies, Guidelines and Standards
v. Preparing for outside Pen Testing
vi. Inside penetration testing
vii. Documentation of the Security Programs in relation to IT, Firewalls along with other
different security tools of IT.
viii. Analysis of different data and associated findings
ix. Exit the briefing
b) Identifying all the potential vulnerabilities
c) Performing the various vulnerability scans
d) Buffering overflows
e) IP spoofing
f) Social engineering
g) Manipulating the touting tables
h) Performing certain manual tests
3. Penetration testing- For the sites being tested for vulnerabilities, the Pen Tester requires to
perform certain tasks:
i. Introductory Briefing
ii. Technical along with Administrative Face-to-Face Meeting
iii. Executive In-Briefing
iv. Reviewing the various IT Security Policies, Guidelines and Standards
v. Preparing for outside Pen Testing
vi. Inside penetration testing
vii. Documentation of the Security Programs in relation to IT, Firewalls along with other
different security tools of IT.
viii. Analysis of different data and associated findings
ix. Exit the briefing

8PENETRATION TESTING
The last step or the exit briefing step includes summarizing the findings, presenting final
reports, discussing outsider pen testing results, discussing insider pen testing results,
discussing the evaluation of the site’s IT security program as well as the management
structure (Prasad 2016). This also includes discussing on the overall recommendations that
relate to the site or the system that has been penetration tested.
Statutory and ethical issue of penetration testing
The Open Source Security Testing Methodology Manual (OSSTMM) lays down
certain rules of engagement that are mainly a set of different rules developed to restrict
unethical pen testing. The rules are laid down so as to protect the client as well as to preserve
this security profession. The different objectives are met by checking on conflicts of interest,
various provisions of false positives as well as false negatives. The legally binding testers
should comply with the ethical obligations that they sign in the contract. The first and
foremost thing is that the client’s information should be protected and the security profession
preserved (Bertoglio and Zorzo 2017). Penetration testing should be performed on a system
or a site only if the client provides written permission for the same. There should be
contractual arrangements so that the work of the penetration testers can be differentiated from
that of the hackers. The penetration testers should not just rely upon certain automated tools
and the tools being used should be tested prior to their application in the pen testing at site.
The penetration tester has no rights to use the data of a past client to promote the services. It
is the responsibility of the tester to send in notifications to the client whenever vulnerability is
identified. This notification should consist of the different measures that can be taken to
rectify the flaws thus minimizing danger to human life (Dawson and McDonald 2016). The
penetration tests that fail to identify vulnerabilities should not be tagged as free service as this
represents false positives and the testing practice is misinterpreted. The tester needs to work
on the non-disclosure as well as limited liability clauses in the contract that is being signed by
The last step or the exit briefing step includes summarizing the findings, presenting final
reports, discussing outsider pen testing results, discussing insider pen testing results,
discussing the evaluation of the site’s IT security program as well as the management
structure (Prasad 2016). This also includes discussing on the overall recommendations that
relate to the site or the system that has been penetration tested.
Statutory and ethical issue of penetration testing
The Open Source Security Testing Methodology Manual (OSSTMM) lays down
certain rules of engagement that are mainly a set of different rules developed to restrict
unethical pen testing. The rules are laid down so as to protect the client as well as to preserve
this security profession. The different objectives are met by checking on conflicts of interest,
various provisions of false positives as well as false negatives. The legally binding testers
should comply with the ethical obligations that they sign in the contract. The first and
foremost thing is that the client’s information should be protected and the security profession
preserved (Bertoglio and Zorzo 2017). Penetration testing should be performed on a system
or a site only if the client provides written permission for the same. There should be
contractual arrangements so that the work of the penetration testers can be differentiated from
that of the hackers. The penetration testers should not just rely upon certain automated tools
and the tools being used should be tested prior to their application in the pen testing at site.
The penetration tester has no rights to use the data of a past client to promote the services. It
is the responsibility of the tester to send in notifications to the client whenever vulnerability is
identified. This notification should consist of the different measures that can be taken to
rectify the flaws thus minimizing danger to human life (Dawson and McDonald 2016). The
penetration tests that fail to identify vulnerabilities should not be tagged as free service as this
represents false positives and the testing practice is misinterpreted. The tester needs to work
on the non-disclosure as well as limited liability clauses in the contract that is being signed by
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9PENETRATION TESTING
him. The main issue in penetration testing is that the client’s system information are going to
the tester and if misused can lead to serious consequences. Thus it is required that the tester
chosen is certified and the activities being done during penetration testing is kept a watch on.
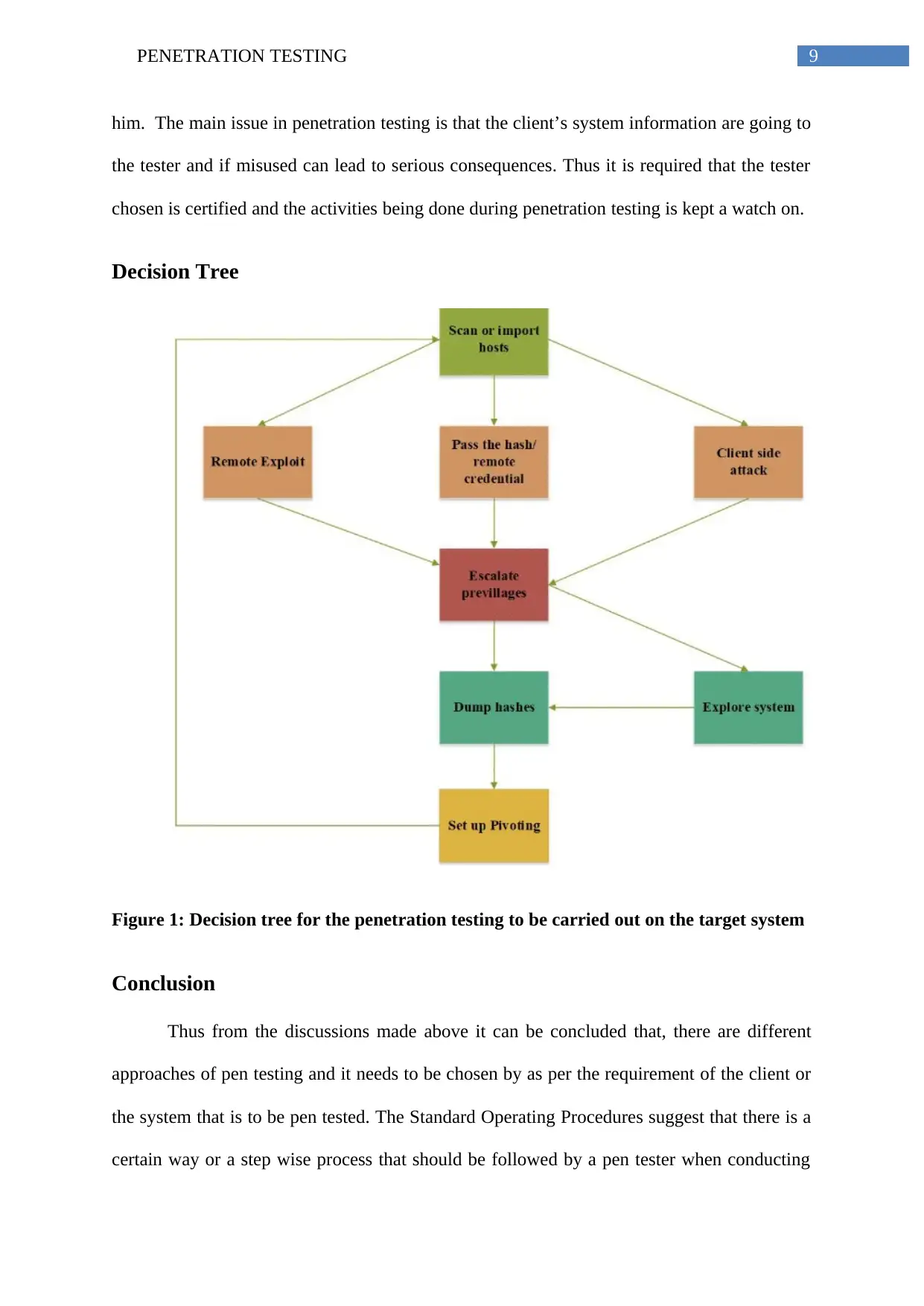
Decision Tree
Figure 1: Decision tree for the penetration testing to be carried out on the target system
Conclusion
Thus from the discussions made above it can be concluded that, there are different
approaches of pen testing and it needs to be chosen by as per the requirement of the client or
the system that is to be pen tested. The Standard Operating Procedures suggest that there is a
certain way or a step wise process that should be followed by a pen tester when conducting
him. The main issue in penetration testing is that the client’s system information are going to
the tester and if misused can lead to serious consequences. Thus it is required that the tester
chosen is certified and the activities being done during penetration testing is kept a watch on.
Decision Tree
Figure 1: Decision tree for the penetration testing to be carried out on the target system
Conclusion
Thus from the discussions made above it can be concluded that, there are different
approaches of pen testing and it needs to be chosen by as per the requirement of the client or
the system that is to be pen tested. The Standard Operating Procedures suggest that there is a
certain way or a step wise process that should be followed by a pen tester when conducting
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10PENETRATION TESTING
this test. The most important part is the ethical issues related to penetration testing. It can be
said that as this has a lot to do with the client’s system and data it can have serious
consequences if misused by the pen tester. The penetration tester should be made to sign
proper contracts to differentiate his work from that of the hacker. Thus, it can be said that
penetration is important to find out vulnerabilities of a system but at the same time it is
important to check that the data is safe with the tester being hired for this purpose keeping in
mind that anything can be done by using the data.
this test. The most important part is the ethical issues related to penetration testing. It can be
said that as this has a lot to do with the client’s system and data it can have serious
consequences if misused by the pen tester. The penetration tester should be made to sign
proper contracts to differentiate his work from that of the hacker. Thus, it can be said that
penetration is important to find out vulnerabilities of a system but at the same time it is
important to check that the data is safe with the tester being hired for this purpose keeping in
mind that anything can be done by using the data.

11PENETRATION TESTING
References
Al Shebli, H.M.Z. and Beheshti, B.D., 2018, May. A study on penetration testing process and
tools. In 2018 IEEE Long Island Systems, Applications and Technology Conference
(LISAT) (pp. 1-7). IEEE.
Ansari, J.A., 2015. Web penetration testing with Kali Linux. Packt Publishing Ltd.
Baloch, R., 2017. Ethical hacking and penetration testing guide. CRC Press.
Bertoglio, D.D. and Zorzo, A.F., 2017. Overview and open issues on penetration test. Journal
of the Brazilian Computer Society, 23(1), p.2.
Dawson, J. and McDonald, J.T., 2016, April. Improving Penetration Testing Methodologies
for Security-Based Risk Assessment. In 2016 Cybersecurity Symposium (CYBERSEC) (pp.
51-58). IEEE.
Falagush, O., McDowell, G.R., Yu, H.S. and de Bono, J.P., 2015. Discrete element modelling
and cavity expansion analysis of cone penetration testing. Granular Matter, 17(4), pp.483-
495.
Hussain, M.Z., Hasan, M.Z. and Chughtai, M.T.A., 2017. Penetration testing in system
administration. International Journal of Scientific & Technology Research, 6(6), p.3.
Johns, A., 2015. Mastering wireless penetration testing for highly secured environments.
Packt Publishing Ltd.
Nagpal, B., Singh, N., Chauhan, N. and Panesar, A., 2015, May. Tool based implementation
of SQL injection for penetration testing. In International Conference on Computing,
Communication & Automation (pp. 746-749). IEEE.
References
Al Shebli, H.M.Z. and Beheshti, B.D., 2018, May. A study on penetration testing process and
tools. In 2018 IEEE Long Island Systems, Applications and Technology Conference
(LISAT) (pp. 1-7). IEEE.
Ansari, J.A., 2015. Web penetration testing with Kali Linux. Packt Publishing Ltd.
Baloch, R., 2017. Ethical hacking and penetration testing guide. CRC Press.
Bertoglio, D.D. and Zorzo, A.F., 2017. Overview and open issues on penetration test. Journal
of the Brazilian Computer Society, 23(1), p.2.
Dawson, J. and McDonald, J.T., 2016, April. Improving Penetration Testing Methodologies
for Security-Based Risk Assessment. In 2016 Cybersecurity Symposium (CYBERSEC) (pp.
51-58). IEEE.
Falagush, O., McDowell, G.R., Yu, H.S. and de Bono, J.P., 2015. Discrete element modelling
and cavity expansion analysis of cone penetration testing. Granular Matter, 17(4), pp.483-
495.
Hussain, M.Z., Hasan, M.Z. and Chughtai, M.T.A., 2017. Penetration testing in system
administration. International Journal of Scientific & Technology Research, 6(6), p.3.
Johns, A., 2015. Mastering wireless penetration testing for highly secured environments.
Packt Publishing Ltd.
Nagpal, B., Singh, N., Chauhan, N. and Panesar, A., 2015, May. Tool based implementation
of SQL injection for penetration testing. In International Conference on Computing,
Communication & Automation (pp. 746-749). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





