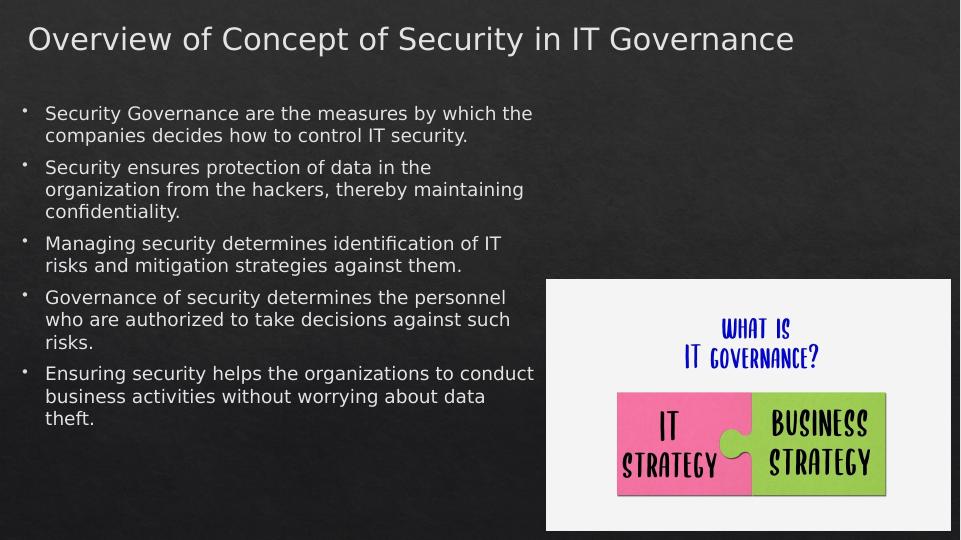
Security ensures protection of data
13 Pages1016 Words18 Views
Added on 2022-09-09
Security ensures protection of data
Added on 2022-09-09
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Criminal Justice.
|10
|416
|33
Project Management in Reserve Bank of Australia
|15
|1257
|25
Governance for Information Security
|10
|643
|19
Cyber Security and Resilience: A Report for the Board of the Company
|10
|3070
|72
Cyber-security Program
|5
|914
|463
Personal Cyber Security Measures and Future Exploration
|4
|525
|332