7COM1068: Penetration Testing Report - Models, SOP, and Legal Aspects
VerifiedAdded on 2022/08/17
|13
|2609
|17
Report
AI Summary
This report provides a comprehensive overview of penetration testing, exploring different models including black box, grey box, and white box testing, and comparing their knowledge requirements, transparency, internal codes, testing space, and algorithm-based approach. It delves into the statutory and legal considerations that pen testers must adhere to, highlighting the importance of certified personnel, proper reporting, and adherence to established processes to avoid legal issues. The report also outlines a Standard Operating Procedure (SOP) for a penetration test, detailing the purpose, scope, roles, responsibilities, and the step-by-step process from planning to data analysis, ensuring a structured and organized approach to security assessments. The assignment also includes a decision tree to guide the testing process.

Running head: PEN TESTING
PEN TESTING
Name of the Student
Name of the University
Author note
PEN TESTING
Name of the Student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
PEN TESTING
Table of Contents
Different penetration model.............................................................................................................2
Statutory and Legal consideration of the pen testers.......................................................................4
SOP for task 2..................................................................................................................................6
Decision Tree...................................................................................................................................9
References......................................................................................................................................10
PEN TESTING
Table of Contents
Different penetration model.............................................................................................................2
Statutory and Legal consideration of the pen testers.......................................................................4
SOP for task 2..................................................................................................................................6
Decision Tree...................................................................................................................................9
References......................................................................................................................................10

2
PEN TESTING
Different penetration model
Penetration testing is considered to be an ethical hacking process that is often used by
different business organizations for checking of the security process of their network and
applications. Pen testing can be performed in 3 different manners. They are namely Black box
testing, grey box testing and white box testing. All the 3 testing methods have been in use in
today's society and have been effectual in the penetration process. The entire process is
performed with the help of data gathering and hence wise this ensures that there has been a
proper assessment of the weaknesses in the server (Mehta, Raj and Singh 2018). With the help of
pen testing, the security policies of the organizations are tested. Ability to identify the processing
of the awareness of the security assessors is included in the process.
The three methods that are being discussed in the process are as follows: -
White box method
Grey Box Method
Black box method
Despite the fact that the prime objective of these methods is similar, the working process of these
methods has been different.
Comparison between different pen testing models
The difference between these methods are as follows: -
White box method Grey Box Method Black box method
PEN TESTING
Different penetration model
Penetration testing is considered to be an ethical hacking process that is often used by
different business organizations for checking of the security process of their network and
applications. Pen testing can be performed in 3 different manners. They are namely Black box
testing, grey box testing and white box testing. All the 3 testing methods have been in use in
today's society and have been effectual in the penetration process. The entire process is
performed with the help of data gathering and hence wise this ensures that there has been a
proper assessment of the weaknesses in the server (Mehta, Raj and Singh 2018). With the help of
pen testing, the security policies of the organizations are tested. Ability to identify the processing
of the awareness of the security assessors is included in the process.
The three methods that are being discussed in the process are as follows: -
White box method
Grey Box Method
Black box method
Despite the fact that the prime objective of these methods is similar, the working process of these
methods has been different.
Comparison between different pen testing models
The difference between these methods are as follows: -
White box method Grey Box Method Black box method
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
PEN TESTING
Knowledge
requirement
It have been seen that in
case of the white box
testing, the knowledge of
the internal working
structure is to be known
by the pen tester. This is
considered to be one of
the most efficient process
of performing the test.
Coding of the software is
also known by the pen
tester in the process. It
have been seen that
proper knowledge of the
testing process is well
known in the processing
of the testing (Stefinko,
Piskozub and Banakh
2016).
Whereas, in case of the
grey box testing, partial
section of the internal
working process is
known to the pen tester
Again in case of black
box testing, the main
aspect that is
considered in the
process is that there is
no access to the internal
framework of the
testing process. This
pen tester does not
require any kind of
knowledge regarding
the codes that have
been performing the
internal framework (de
Jiménez 2016). The
main aspect that is
required in the process
is the Graphical User
Interface.
White box testing is
known as clear box
testing and hence wise is
considered to be
Again in the case of the
grey box testing, the
pen tester has limited
knowledge regarding
The black box testing is
considered to be a data-
driven testing process.
It has been seen that the
PEN TESTING
Knowledge
requirement
It have been seen that in
case of the white box
testing, the knowledge of
the internal working
structure is to be known
by the pen tester. This is
considered to be one of
the most efficient process
of performing the test.
Coding of the software is
also known by the pen
tester in the process. It
have been seen that
proper knowledge of the
testing process is well
known in the processing
of the testing (Stefinko,
Piskozub and Banakh
2016).
Whereas, in case of the
grey box testing, partial
section of the internal
working process is
known to the pen tester
Again in case of black
box testing, the main
aspect that is
considered in the
process is that there is
no access to the internal
framework of the
testing process. This
pen tester does not
require any kind of
knowledge regarding
the codes that have
been performing the
internal framework (de
Jiménez 2016). The
main aspect that is
required in the process
is the Graphical User
Interface.
White box testing is
known as clear box
testing and hence wise is
considered to be
Again in the case of the
grey box testing, the
pen tester has limited
knowledge regarding
The black box testing is
considered to be a data-
driven testing process.
It has been seen that the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
PEN TESTING
Transparency transparent in nature. the code that is
implemented in the
processing of the server
or the application.
pen testers have the
knowledge of the
internal framework and
hence wise it is
considered as a
functional testing
process.
Internal
codes
Again in the case of
White box testing
process, the aspect
considered is that there is
no lack of internal codes
and hence wise the entire
working process ensures
that there is a proper
assessment of the
security checking.
Whereas, in the case of
the grey box testing
process, validating the
data domains are
considered. The
boundaries of the
software are also
considered in the
process (Berntsen et al
2019).
In case of the black box
testing process, the
main aspect that is
considered is that there
will be a proper
assessment of the error
and trial performance of
the entire server and the
entire architecture.
Testing
Space
However, it has been
seen that the testing
space that is required for
white box testing process
is much lower than that
of the black box testing
Whereas, the testing
space that is required in
the operational process
of the grey box testing
is much lower than that
of both the white box
The testing space of
tables that are required
in the process is the
highest in case of black
box testing. This
section ensures that
PEN TESTING
Transparency transparent in nature. the code that is
implemented in the
processing of the server
or the application.
pen testers have the
knowledge of the
internal framework and
hence wise it is
considered as a
functional testing
process.
Internal
codes
Again in the case of
White box testing
process, the aspect
considered is that there is
no lack of internal codes
and hence wise the entire
working process ensures
that there is a proper
assessment of the
security checking.
Whereas, in the case of
the grey box testing
process, validating the
data domains are
considered. The
boundaries of the
software are also
considered in the
process (Berntsen et al
2019).
In case of the black box
testing process, the
main aspect that is
considered is that there
will be a proper
assessment of the error
and trial performance of
the entire server and the
entire architecture.
Testing
Space
However, it has been
seen that the testing
space that is required for
white box testing process
is much lower than that
of the black box testing
Whereas, the testing
space that is required in
the operational process
of the grey box testing
is much lower than that
of both the white box
The testing space of
tables that are required
in the process is the
highest in case of black
box testing. This
section ensures that

5
PEN TESTING
process (Shaukat et al
2016).
testing and grey box
testing process.
there will be a proper
assessment of the
database space that is
required in the testing
process is the highest
among all the testing
process.
The major difference that is considered in the process is that the testing process of the
black box testing is considered not be algorithm-based. The testing process of white box testing
process is algorithm based and the grey box testing method is considered not to be algorithm
based.
Statutory and Legal consideration of the pen testers
Pen testers are considered to be performing a job that faces huge ethical challenges in the
working process. Thus there are certain aspects that are considered by the testers. In case of
failing to maintain the factors, the entire process fails and this is one of the major aspects that
affects the working process of the pen testers. There are laws that are to be fulfilled in the
working process of the testers. In case the laws are not followed by the pen testers, there are
major issues that are to be considered (de Jiménez 2016). The major considerations that the pen
testers need to follow in order to perform the testing process include the likes of usage of the
certified and experienced personnel. The penetration testing process needs to have proper
credentials and this is one of the major aspects that ensures that the license of the testers is
needed to be assessed. It is seen that presence of the EC Council Certified Security Analyst
license is required by the tester for performing the testing (Berntsen et al 2019). Again the pen
PEN TESTING
process (Shaukat et al
2016).
testing and grey box
testing process.
there will be a proper
assessment of the
database space that is
required in the testing
process is the highest
among all the testing
process.
The major difference that is considered in the process is that the testing process of the
black box testing is considered not be algorithm-based. The testing process of white box testing
process is algorithm based and the grey box testing method is considered not to be algorithm
based.
Statutory and Legal consideration of the pen testers
Pen testers are considered to be performing a job that faces huge ethical challenges in the
working process. Thus there are certain aspects that are considered by the testers. In case of
failing to maintain the factors, the entire process fails and this is one of the major aspects that
affects the working process of the pen testers. There are laws that are to be fulfilled in the
working process of the testers. In case the laws are not followed by the pen testers, there are
major issues that are to be considered (de Jiménez 2016). The major considerations that the pen
testers need to follow in order to perform the testing process include the likes of usage of the
certified and experienced personnel. The penetration testing process needs to have proper
credentials and this is one of the major aspects that ensures that the license of the testers is
needed to be assessed. It is seen that presence of the EC Council Certified Security Analyst
license is required by the tester for performing the testing (Berntsen et al 2019). Again the pen
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
PEN TESTING
tester needs to be a licensed pen tester. The pen tester also needs to be offensive security certified
professional to perform the pen-testing. A tester also needs to be a certified ethical hacker.
Another aspect that is considered in the process is that the penetration tester needs to be
preparing proper reports and hence wise this will be ensuring the fact that there will be proper
documentation of the activities that will be performed in the process.
Another major consideration that is to be considered in the process is that both manual, as
well as automated testing processes, is to be performed (Abbas, Sultan and Bhatti 2017). It is
seen that there are certain vulnerabilities that are present in the automated testing process as all
the issues are not detected in the automated testing process and hence wise the manual testing
process is to be conducted.
Another aspect that is to be considered is that the process that has been proposed in the
documentation process is to be followed. In case the process is not followed, there might be
heavy punishments for the pen testers.
In case these considerations are not followed, the pen testers will be suffering legal
issues. These legal issues might include the fact that they get arrested or get heavily penalized.
This penalization will be affecting the working process. It has been seen that despite the fact that
there are a limit of penetration is maintained by the tester but the process of penetration has been
different, the pen tester might be facing legal issues (Nugroho and Akmeliawati 2018). This is
the main aspect that is to be considered. Again it have been seen that there have been situations
where the pen tester has accidentally crossed the limits and has got access to the data that were
not to be penetrated. The pen tester will be penalized for this issues as well (Jan et al 2016).
PEN TESTING
tester needs to be a licensed pen tester. The pen tester also needs to be offensive security certified
professional to perform the pen-testing. A tester also needs to be a certified ethical hacker.
Another aspect that is considered in the process is that the penetration tester needs to be
preparing proper reports and hence wise this will be ensuring the fact that there will be proper
documentation of the activities that will be performed in the process.
Another major consideration that is to be considered in the process is that both manual, as
well as automated testing processes, is to be performed (Abbas, Sultan and Bhatti 2017). It is
seen that there are certain vulnerabilities that are present in the automated testing process as all
the issues are not detected in the automated testing process and hence wise the manual testing
process is to be conducted.
Another aspect that is to be considered is that the process that has been proposed in the
documentation process is to be followed. In case the process is not followed, there might be
heavy punishments for the pen testers.
In case these considerations are not followed, the pen testers will be suffering legal
issues. These legal issues might include the fact that they get arrested or get heavily penalized.
This penalization will be affecting the working process. It has been seen that despite the fact that
there are a limit of penetration is maintained by the tester but the process of penetration has been
different, the pen tester might be facing legal issues (Nugroho and Akmeliawati 2018). This is
the main aspect that is to be considered. Again it have been seen that there have been situations
where the pen tester has accidentally crossed the limits and has got access to the data that were
not to be penetrated. The pen tester will be penalized for this issues as well (Jan et al 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
PEN TESTING
Another major consideration that is considered in the process is that the elimination of the false
problems are also considered to be an important job role of the pen tester.
In case the tester follows the above stated considerations, the issues that might be faced
by the pen testers will be analyzed. These considerations will be reducing the rigorousness of
penalties that might be getting imposed. Hence the penalties that will be imposed will be on a
decreasing node.
SOP for task 2
Introduction
Performing the testing process is considered to be an important process and hence wise
this ensures that there is a requirement of proper testing of the server and application.
Assessment of external and internal intruders are also considered to be important. Demonstration
of the ability to manipulate the target computers have been one of the major aspects. Proper
assessment of the specific nature of the testing process will be maintained.
Purpose
The major purpose of the SOP is that for laying of the procedures and hence wise
establish the rules of engagement for the security penetration testing will be performed.
Scope
The scope of the SOP is to apply the facilities and hence wise this ensures that the
contractors will be considering cooperative agreements and hence patterns and the programs of
institutional requirements will be considered.
Roles and Responsibilities
PEN TESTING
Another major consideration that is considered in the process is that the elimination of the false
problems are also considered to be an important job role of the pen tester.
In case the tester follows the above stated considerations, the issues that might be faced
by the pen testers will be analyzed. These considerations will be reducing the rigorousness of
penalties that might be getting imposed. Hence the penalties that will be imposed will be on a
decreasing node.
SOP for task 2
Introduction
Performing the testing process is considered to be an important process and hence wise
this ensures that there is a requirement of proper testing of the server and application.
Assessment of external and internal intruders are also considered to be important. Demonstration
of the ability to manipulate the target computers have been one of the major aspects. Proper
assessment of the specific nature of the testing process will be maintained.
Purpose
The major purpose of the SOP is that for laying of the procedures and hence wise
establish the rules of engagement for the security penetration testing will be performed.
Scope
The scope of the SOP is to apply the facilities and hence wise this ensures that the
contractors will be considering cooperative agreements and hence patterns and the programs of
institutional requirements will be considered.
Roles and Responsibilities

8
PEN TESTING
There are certain roles and responsibilities that are to be followed in the process. This
includes the fact that there will be proper assessment of the site POC. This will be bettering the
coordination process and hence wise this will be bettering the activities and the schedules which
will be helping in notifying the management. These are performed for proper performing planned
activities. After this process proper coordination of the penetration process, the main aspect that
is considered is that there is a requirement of proper documentation of ITS security penetration
testing protocol. The pen testers need to ensure that the data that are collected during the
penetration process is properly stored and hence wise this ensures that there is a better storage of
the data.
The pen testing POC includes the fact that there is a proper user interface and this will be
bettering the processing of primary interface. This ensures that the penetration testing process is
also performed in a better manner. After this process, developing of the documentation as well as
planning of the penetration testing can be considered for performing an assessment of the pen
testing. Another aspect that is considered in the process is that major milestones are proper
assessment of identification of the estimated dates that will be considering the major milestones.
This has been indicating the importance of the critical path. After this process, identification of
the roles of the pen testing process is made. After this process, test plan, results and financial
deliverables will be analyzed. This section also includes the fact that there will be proper
coordination of the IT security penetration testing with the help of the POC. After this process,
proper assessment of the documents that ensures data regarding the processing of logs and results
are included in the process.
Process
PEN TESTING
There are certain roles and responsibilities that are to be followed in the process. This
includes the fact that there will be proper assessment of the site POC. This will be bettering the
coordination process and hence wise this will be bettering the activities and the schedules which
will be helping in notifying the management. These are performed for proper performing planned
activities. After this process proper coordination of the penetration process, the main aspect that
is considered is that there is a requirement of proper documentation of ITS security penetration
testing protocol. The pen testers need to ensure that the data that are collected during the
penetration process is properly stored and hence wise this ensures that there is a better storage of
the data.
The pen testing POC includes the fact that there is a proper user interface and this will be
bettering the processing of primary interface. This ensures that the penetration testing process is
also performed in a better manner. After this process, developing of the documentation as well as
planning of the penetration testing can be considered for performing an assessment of the pen
testing. Another aspect that is considered in the process is that major milestones are proper
assessment of identification of the estimated dates that will be considering the major milestones.
This has been indicating the importance of the critical path. After this process, identification of
the roles of the pen testing process is made. After this process, test plan, results and financial
deliverables will be analyzed. This section also includes the fact that there will be proper
coordination of the IT security penetration testing with the help of the POC. After this process,
proper assessment of the documents that ensures data regarding the processing of logs and results
are included in the process.
Process
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
PEN TESTING
The very initial step of the processing is planning of the process. This section ensures that
there have been proper identification of the POC. This will be ensuring the fact that there will be
a proper coordination in between the penetration testing activities. This also includes the fact that
there will be a proper assessment of the primary interface.
After the planning stage, the conduction process starts. This ensures the fact that there is
an introduction process. The testers will be introduced in this stage, objective of the entire
process will be discussed as well. Reviewing of the resources that are present will also be stated
in the process. After this process, another aspect that is considered in the process is that face to
face meeting is performed. Selecting the criterions are also considered in the process. After
selecting the criteria, reviewing the object of pen testing will be performed. After this process,
selection of the target audience will be helpful. Data analysis is another aspect that is to be
considered in the process. This section includes the fact that proper management of the security
related data are gathered and analyzed. Issues present in the server is also well known in the
process. After performing these activities, the main activities that are to be performed includes
performing proper documentation process.
Approval
These are the activities that will be performed Detailed theoretic documentation of the
process is stated above. After getting proper approval the process will begin.
PEN TESTING
The very initial step of the processing is planning of the process. This section ensures that
there have been proper identification of the POC. This will be ensuring the fact that there will be
a proper coordination in between the penetration testing activities. This also includes the fact that
there will be a proper assessment of the primary interface.
After the planning stage, the conduction process starts. This ensures the fact that there is
an introduction process. The testers will be introduced in this stage, objective of the entire
process will be discussed as well. Reviewing of the resources that are present will also be stated
in the process. After this process, another aspect that is considered in the process is that face to
face meeting is performed. Selecting the criterions are also considered in the process. After
selecting the criteria, reviewing the object of pen testing will be performed. After this process,
selection of the target audience will be helpful. Data analysis is another aspect that is to be
considered in the process. This section includes the fact that proper management of the security
related data are gathered and analyzed. Issues present in the server is also well known in the
process. After performing these activities, the main activities that are to be performed includes
performing proper documentation process.
Approval
These are the activities that will be performed Detailed theoretic documentation of the
process is stated above. After getting proper approval the process will begin.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
PEN TESTING
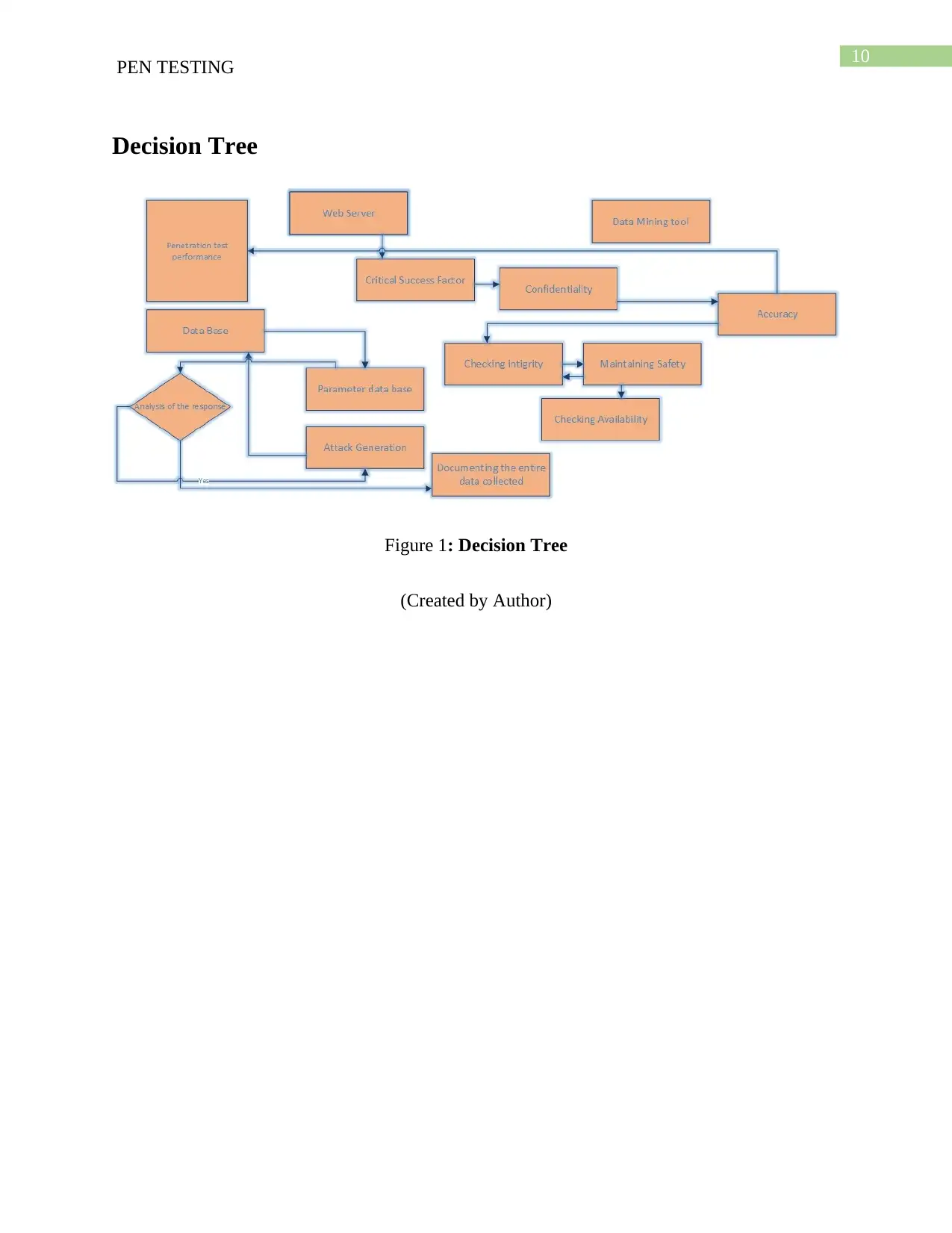
Decision Tree
Figure 1: Decision Tree
(Created by Author)
PEN TESTING
Decision Tree
Figure 1: Decision Tree
(Created by Author)

11
PEN TESTING
References
Mehta, S., Raj, G. and Singh, D., 2018. Penetration Testing as a Test Phase in Web Service
Testing a Black Box Pen Testing Approach. In Smart Computing and Informatics (pp. 623-635).
Springer, Singapore.
Berntsen, S.L., Einmo, E., Granerud, S. and Moe, T., 2019. Pentesting Exercise Management
Application (Bachelor's thesis, NTNU).
Shaukat, K., Faisal, A., Masood, R., Usman, A. and Shaukat, U., 2016, December. Security
quality assurance through penetration testing. In 2016 19th International Multi-Topic
Conference (INMIC) (pp. 1-6). IEEE.
Jan, S.R., Shah, S.T.U., Johar, Z.U., Shah, Y. and Khan, F., 2016. An innovative approach to
investigate various software testing techniques and strategies. International Journal of Scientific
Research in Science, Engineering and Technology (IJSRSET), Print ISSN, pp.2395-1990.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated penetration
testing. Benefits and drawbacks. Modern tendency. In 2016 13th International Conference on
Modern Problems of Radio Engineering, Telecommunications and Computer Science
(TCSET) (pp. 488-491). IEEE.
de Jiménez, R.E.L., 2016, November. Pentesting on web applications using ethical-hacking.
In 2016 IEEE 36th Central American and Panama Convention (CONCAPAN XXXVI) (pp. 1-6).
IEEE.
PEN TESTING
References
Mehta, S., Raj, G. and Singh, D., 2018. Penetration Testing as a Test Phase in Web Service
Testing a Black Box Pen Testing Approach. In Smart Computing and Informatics (pp. 623-635).
Springer, Singapore.
Berntsen, S.L., Einmo, E., Granerud, S. and Moe, T., 2019. Pentesting Exercise Management
Application (Bachelor's thesis, NTNU).
Shaukat, K., Faisal, A., Masood, R., Usman, A. and Shaukat, U., 2016, December. Security
quality assurance through penetration testing. In 2016 19th International Multi-Topic
Conference (INMIC) (pp. 1-6). IEEE.
Jan, S.R., Shah, S.T.U., Johar, Z.U., Shah, Y. and Khan, F., 2016. An innovative approach to
investigate various software testing techniques and strategies. International Journal of Scientific
Research in Science, Engineering and Technology (IJSRSET), Print ISSN, pp.2395-1990.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated penetration
testing. Benefits and drawbacks. Modern tendency. In 2016 13th International Conference on
Modern Problems of Radio Engineering, Telecommunications and Computer Science
(TCSET) (pp. 488-491). IEEE.
de Jiménez, R.E.L., 2016, November. Pentesting on web applications using ethical-hacking.
In 2016 IEEE 36th Central American and Panama Convention (CONCAPAN XXXVI) (pp. 1-6).
IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





