Network Analyzer Design and Implementation
VerifiedAdded on 2020/02/24
|12
|2302
|33
AI Summary
This assignment focuses on designing and implementing a network analyzer for M2M Solutions, a medium-sized company expanding its operations. The report emphasizes the importance of understanding data flow and network configurations for effective utilization of the analyzer. It also provides technical details about the chosen analyzer, including its cost-effectiveness and system requirements.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: TCP/IP NETWORKING
TCP / IP Networking
Name of the Student
Name of the University
Author’s Note
TCP / IP Networking
Name of the Student
Name of the University
Author’s Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
TCP/IP NETWORKING
Table of Contents
Task 1...................................................................................................................................2
a. Design of the Network using Simple Addressing Solution.........................................2
b. Explanation..................................................................................................................6
Task 2...................................................................................................................................8
a. Protocols in the communication Network and role of network analyzer tool.............8
b. Currently available network analyzer tool...................................................................9
i. Benefits, associated costs, ease of usability.............................................................9
ii. Recommendation and preferences of using the tool..............................................10
Bibliography......................................................................................................................12
TCP/IP NETWORKING
Table of Contents
Task 1...................................................................................................................................2
a. Design of the Network using Simple Addressing Solution.........................................2
b. Explanation..................................................................................................................6
Task 2...................................................................................................................................8
a. Protocols in the communication Network and role of network analyzer tool.............8
b. Currently available network analyzer tool...................................................................9
i. Benefits, associated costs, ease of usability.............................................................9
ii. Recommendation and preferences of using the tool..............................................10
Bibliography......................................................................................................................12

2
TCP/IP NETWORKING
Task 1
a. Design of the Network using Simple Addressing Solution
The design of the network is created is proposed for the M2M solution and the
requirement of the organization is studied for the preparation of the network diagram. There is a
need of connecting 1200 nodes and workstation in the network and the private address 10.1.1.1 is
used for the whole network. The number of workstation required to be installed in each of the
office is given in the requirement and the network solution is created according to it. A central
router is installed for communicating with the branches and the offices of the organization. Each
of the workstation in the office are assigned with a router and switch is used for connecting the
hosts. The subnet is calculated for the allocation of the hosts and the range of the IP address is
required to be calculated for the accommodation of the IP address. VLSM technique is applied
for the calculation and some extra IP address are allocated such that the future growth of the
organization can be easily handled.
TCP/IP NETWORKING
Task 1
a. Design of the Network using Simple Addressing Solution
The design of the network is created is proposed for the M2M solution and the
requirement of the organization is studied for the preparation of the network diagram. There is a
need of connecting 1200 nodes and workstation in the network and the private address 10.1.1.1 is
used for the whole network. The number of workstation required to be installed in each of the
office is given in the requirement and the network solution is created according to it. A central
router is installed for communicating with the branches and the offices of the organization. Each
of the workstation in the office are assigned with a router and switch is used for connecting the
hosts. The subnet is calculated for the allocation of the hosts and the range of the IP address is
required to be calculated for the accommodation of the IP address. VLSM technique is applied
for the calculation and some extra IP address are allocated such that the future growth of the
organization can be easily handled.
3
TCP/IP NETWORKING
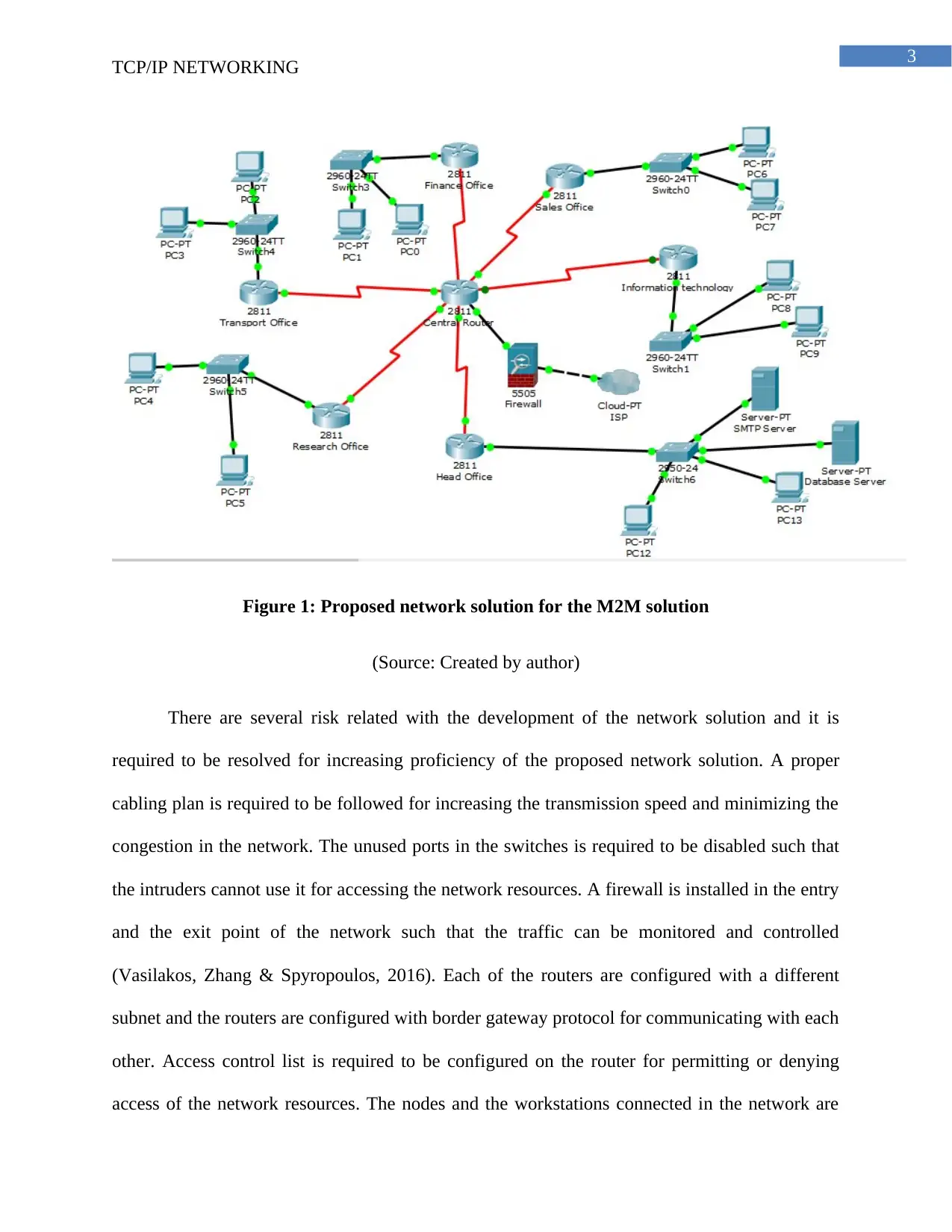
Figure 1: Proposed network solution for the M2M solution
(Source: Created by author)
There are several risk related with the development of the network solution and it is
required to be resolved for increasing proficiency of the proposed network solution. A proper
cabling plan is required to be followed for increasing the transmission speed and minimizing the
congestion in the network. The unused ports in the switches is required to be disabled such that
the intruders cannot use it for accessing the network resources. A firewall is installed in the entry
and the exit point of the network such that the traffic can be monitored and controlled
(Vasilakos, Zhang & Spyropoulos, 2016). Each of the routers are configured with a different
subnet and the routers are configured with border gateway protocol for communicating with each
other. Access control list is required to be configured on the router for permitting or denying
access of the network resources. The nodes and the workstations connected in the network are
TCP/IP NETWORKING
Figure 1: Proposed network solution for the M2M solution
(Source: Created by author)
There are several risk related with the development of the network solution and it is
required to be resolved for increasing proficiency of the proposed network solution. A proper
cabling plan is required to be followed for increasing the transmission speed and minimizing the
congestion in the network. The unused ports in the switches is required to be disabled such that
the intruders cannot use it for accessing the network resources. A firewall is installed in the entry
and the exit point of the network such that the traffic can be monitored and controlled
(Vasilakos, Zhang & Spyropoulos, 2016). Each of the routers are configured with a different
subnet and the routers are configured with border gateway protocol for communicating with each
other. Access control list is required to be configured on the router for permitting or denying
access of the network resources. The nodes and the workstations connected in the network are
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4
TCP/IP NETWORKING
assigned with the static IP address calculated from the addressing scheme such that the official
network cannot be used by the employees with their personal usage (Kulkarni & Agrawal, 2014).
Servers are also required to be installed for communicating between the employees and scope of
future expansion is there for the network to meet the growing demand of the organization. The
backbone of the network is required to be strong and thus fiber optics cable is used for
communication for communicating with the different branches.
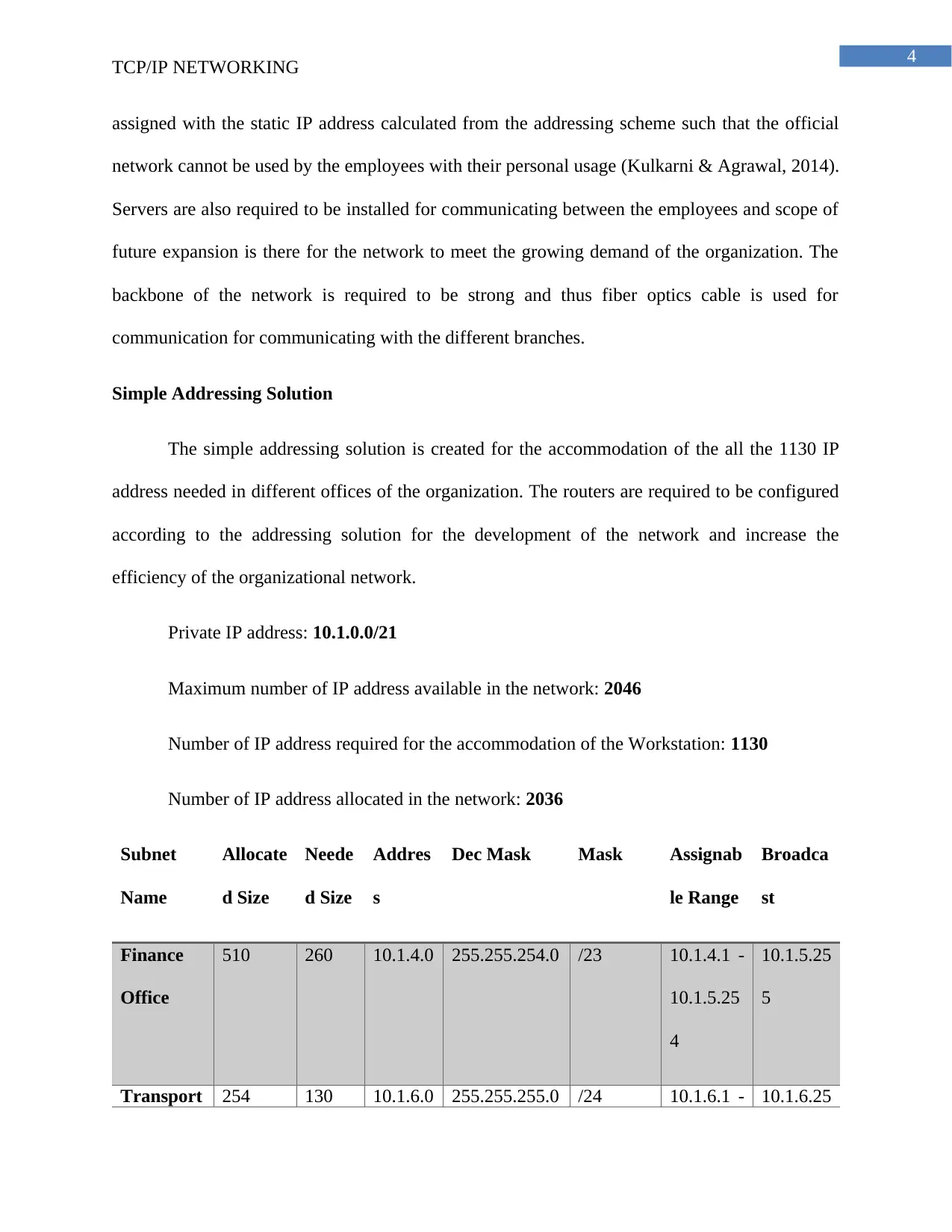
Simple Addressing Solution
The simple addressing solution is created for the accommodation of the all the 1130 IP
address needed in different offices of the organization. The routers are required to be configured
according to the addressing solution for the development of the network and increase the
efficiency of the organizational network.
Private IP address: 10.1.0.0/21
Maximum number of IP address available in the network: 2046
Number of IP address required for the accommodation of the Workstation: 1130
Number of IP address allocated in the network: 2036
Subnet
Name
Allocate
d Size
Neede
d Size
Addres
s
Dec Mask Mask Assignab
le Range
Broadca
st
Finance
Office
510 260 10.1.4.0 255.255.254.0 /23 10.1.4.1 -
10.1.5.25
4
10.1.5.25
5
Transport 254 130 10.1.6.0 255.255.255.0 /24 10.1.6.1 - 10.1.6.25
TCP/IP NETWORKING
assigned with the static IP address calculated from the addressing scheme such that the official
network cannot be used by the employees with their personal usage (Kulkarni & Agrawal, 2014).
Servers are also required to be installed for communicating between the employees and scope of
future expansion is there for the network to meet the growing demand of the organization. The
backbone of the network is required to be strong and thus fiber optics cable is used for
communication for communicating with the different branches.
Simple Addressing Solution
The simple addressing solution is created for the accommodation of the all the 1130 IP
address needed in different offices of the organization. The routers are required to be configured
according to the addressing solution for the development of the network and increase the
efficiency of the organizational network.
Private IP address: 10.1.0.0/21
Maximum number of IP address available in the network: 2046
Number of IP address required for the accommodation of the Workstation: 1130
Number of IP address allocated in the network: 2036
Subnet
Name
Allocate
d Size
Neede
d Size
Addres
s
Dec Mask Mask Assignab
le Range
Broadca
st
Finance
Office
510 260 10.1.4.0 255.255.254.0 /23 10.1.4.1 -
10.1.5.25
4
10.1.5.25
5
Transport 254 130 10.1.6.0 255.255.255.0 /24 10.1.6.1 - 10.1.6.25
5
TCP/IP NETWORKING
Office 10.1.6.25
4
5
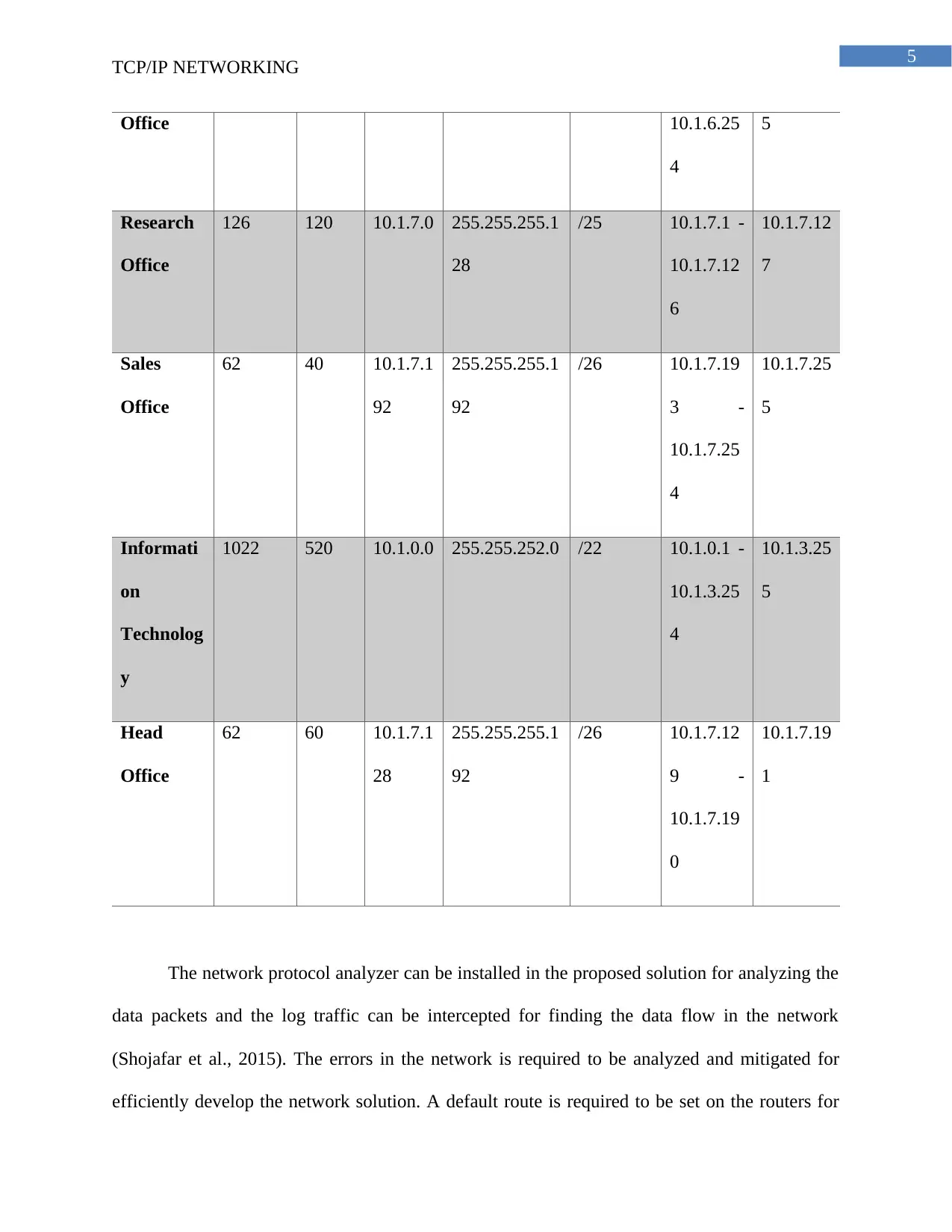
Research
Office
126 120 10.1.7.0 255.255.255.1
28
/25 10.1.7.1 -
10.1.7.12
6
10.1.7.12
7
Sales
Office
62 40 10.1.7.1
92
255.255.255.1
92
/26 10.1.7.19
3 -
10.1.7.25
4
10.1.7.25
5
Informati
on
Technolog
y
1022 520 10.1.0.0 255.255.252.0 /22 10.1.0.1 -
10.1.3.25
4
10.1.3.25
5
Head
Office
62 60 10.1.7.1
28
255.255.255.1
92
/26 10.1.7.12
9 -
10.1.7.19
0
10.1.7.19
1
The network protocol analyzer can be installed in the proposed solution for analyzing the
data packets and the log traffic can be intercepted for finding the data flow in the network
(Shojafar et al., 2015). The errors in the network is required to be analyzed and mitigated for
efficiently develop the network solution. A default route is required to be set on the routers for
TCP/IP NETWORKING
Office 10.1.6.25
4
5
Research
Office
126 120 10.1.7.0 255.255.255.1
28
/25 10.1.7.1 -
10.1.7.12
6
10.1.7.12
7
Sales
Office
62 40 10.1.7.1
92
255.255.255.1
92
/26 10.1.7.19
3 -
10.1.7.25
4
10.1.7.25
5
Informati
on
Technolog
y
1022 520 10.1.0.0 255.255.252.0 /22 10.1.0.1 -
10.1.3.25
4
10.1.3.25
5
Head
Office
62 60 10.1.7.1
28
255.255.255.1
92
/26 10.1.7.12
9 -
10.1.7.19
0
10.1.7.19
1
The network protocol analyzer can be installed in the proposed solution for analyzing the
data packets and the log traffic can be intercepted for finding the data flow in the network
(Shojafar et al., 2015). The errors in the network is required to be analyzed and mitigated for
efficiently develop the network solution. A default route is required to be set on the routers for

6
TCP/IP NETWORKING
transferring the data packets and they are required to be configured properly and network address
translation is required to be implemented for securing the network from external access.
b. Explanation
With the increase in the number of host per network of the office building the subnets are
calculated and the current network configuration is required to be changed in the routers for
application of the change. The subnets are calculated for the accommodation of the 1024 hosts
per network and this causes change in the static IP address of the hosts, unblocking the ports on
the switches and configuring the routers with the new IP address and the subnet mask. Multiple
subnets are created for the network and for addition of the host there are different technique that
can be applied but the cost effective solution is the reconfiguration of the routers and the other
hardware devices connected in the network. Some IP bits are kept in reserve and the host
formula is used calculating the new subnet and accommodate the increased number of hosts in
the network. The calculation work and the result is given below:
Finance Office:
Address 10.0.0.0
Mask /22
Dec Mask 255.255.252.0
Assignable Range 10.0.0.1 - 10.0.3.254
Transport Office:
Address 10.0.4.0
Mask /22
TCP/IP NETWORKING
transferring the data packets and they are required to be configured properly and network address
translation is required to be implemented for securing the network from external access.
b. Explanation
With the increase in the number of host per network of the office building the subnets are
calculated and the current network configuration is required to be changed in the routers for
application of the change. The subnets are calculated for the accommodation of the 1024 hosts
per network and this causes change in the static IP address of the hosts, unblocking the ports on
the switches and configuring the routers with the new IP address and the subnet mask. Multiple
subnets are created for the network and for addition of the host there are different technique that
can be applied but the cost effective solution is the reconfiguration of the routers and the other
hardware devices connected in the network. Some IP bits are kept in reserve and the host
formula is used calculating the new subnet and accommodate the increased number of hosts in
the network. The calculation work and the result is given below:
Finance Office:
Address 10.0.0.0
Mask /22
Dec Mask 255.255.252.0
Assignable Range 10.0.0.1 - 10.0.3.254
Transport Office:
Address 10.0.4.0
Mask /22
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
TCP/IP NETWORKING
Dec Mask 255.255.252.0
Assignable Range 10.0.4.1 - 10.0.7.254
Research Office:
Address 10.0.8.0
Mask /22
Dec Mask 255.255.252.0
Assignable Range 10.0.8.1 - 10.0.11.254
Sales Office:
Address 10.0.12.0
Mask /22
Dec Mask 255.255.252.0
Assignable Range 10.0.12.1 - 10.0.15.254
Information Technology:
Address 10.0.16.0
Mask /22
Dec Mask 255.255.252.0
Assignable Range 10.0.16.1 - 10.0.19.254
Head Office:
TCP/IP NETWORKING
Dec Mask 255.255.252.0
Assignable Range 10.0.4.1 - 10.0.7.254
Research Office:
Address 10.0.8.0
Mask /22
Dec Mask 255.255.252.0
Assignable Range 10.0.8.1 - 10.0.11.254
Sales Office:
Address 10.0.12.0
Mask /22
Dec Mask 255.255.252.0
Assignable Range 10.0.12.1 - 10.0.15.254
Information Technology:
Address 10.0.16.0
Mask /22
Dec Mask 255.255.252.0
Assignable Range 10.0.16.1 - 10.0.19.254
Head Office:

8
TCP/IP NETWORKING
Address 10.0.20.0
Mask /22
Dec Mask 255.255.252.0
Assignable Range 10.0.20.1 - 10.0.23.254
Task 2
a. Protocols in the communication Network and role of network analyzer tool
The protocol requirements in the network are HTTP, FTP and SMTP. The HTTP is the
hyper text transfer protocol, SMTP is the Simple mail transfer protocol and FTP is the File
transfer protocol. The HTTP protocol would empower the system to approach the web
association and framework would have the capacity to go on the web. Furthermore, the FTP
protocol would enable the frameworks in empower to exchange records inside the system
(Edwards & Bramante, 2015). The SMTP protocol would empower the segments of the system
to convey among them proficiently. Furthermore, the correspondence in the middle of the staffs
of the organization would likewise be extremely productive and they would have the capacity to
trade messages among themselves.
M2M Solutions is a company that is medium sized and they are looking to expand their
operations. Therefore they are required to reconstruct the network structure for their company. I
have been entrusted with the job of implementing a network design. The organization strategies
don't include the utilization of network analyzers in their system in spite of the fact that the
network analyzers are extremely productive for the organization to do their procedures.
Likewise, the network analyzer would likewise enable the organization tom to recognize the
TCP/IP NETWORKING
Address 10.0.20.0
Mask /22
Dec Mask 255.255.252.0
Assignable Range 10.0.20.1 - 10.0.23.254
Task 2
a. Protocols in the communication Network and role of network analyzer tool
The protocol requirements in the network are HTTP, FTP and SMTP. The HTTP is the
hyper text transfer protocol, SMTP is the Simple mail transfer protocol and FTP is the File
transfer protocol. The HTTP protocol would empower the system to approach the web
association and framework would have the capacity to go on the web. Furthermore, the FTP
protocol would enable the frameworks in empower to exchange records inside the system
(Edwards & Bramante, 2015). The SMTP protocol would empower the segments of the system
to convey among them proficiently. Furthermore, the correspondence in the middle of the staffs
of the organization would likewise be extremely productive and they would have the capacity to
trade messages among themselves.
M2M Solutions is a company that is medium sized and they are looking to expand their
operations. Therefore they are required to reconstruct the network structure for their company. I
have been entrusted with the job of implementing a network design. The organization strategies
don't include the utilization of network analyzers in their system in spite of the fact that the
network analyzers are extremely productive for the organization to do their procedures.
Likewise, the network analyzer would likewise enable the organization tom to recognize the

9
TCP/IP NETWORKING
imperfections that are existent inside the system. The data about the protocols that are being
utilized as a part of the system is given beneath.
The network analyzer is very useful for the network and it provides various type of
facilities for the network. The network analyzer serves different type of purposes for the network
and the main roles of the network analyzer are:
The network analyzer performs an excellent analysis of the network and also the
monitors the network efficiently.
The network analyzer plays the role of a security system for the network.
b. Currently available network analyzer tool
The wireshark network analyzer tool can be used in different formats by the
network. The tool acts as a network analyzer for the network. They are also used for the purpose
of monitoring the network. They perform analysis of the data and the files that flows throughout
the network. Tracing the packets is one of the process that is performed by the analyzer tool
(Clavel et al., 2015). Wireshark is one the most effective software that can be utilized as a system
analyzer likewise; the item is extremely prevalent in the market and forces a significant high
positioning in the market for the division of network analyzer.
i. Benefits, associated costs, ease of usability
The network analyzer protocol is very beneficial to the network. The device additionally
helps in the examination of the system and performs observing of the frameworks. Henceforth,
they secure the frameworks shape the outer gatecrashers. It supports an extensive variety of
protocols such as the IP, BitTorrent, AppleTalk and DHCP. Likewise, with each of the refresh
TCP/IP NETWORKING
imperfections that are existent inside the system. The data about the protocols that are being
utilized as a part of the system is given beneath.
The network analyzer is very useful for the network and it provides various type of
facilities for the network. The network analyzer serves different type of purposes for the network
and the main roles of the network analyzer are:
The network analyzer performs an excellent analysis of the network and also the
monitors the network efficiently.
The network analyzer plays the role of a security system for the network.
b. Currently available network analyzer tool
The wireshark network analyzer tool can be used in different formats by the
network. The tool acts as a network analyzer for the network. They are also used for the purpose
of monitoring the network. They perform analysis of the data and the files that flows throughout
the network. Tracing the packets is one of the process that is performed by the analyzer tool
(Clavel et al., 2015). Wireshark is one the most effective software that can be utilized as a system
analyzer likewise; the item is extremely prevalent in the market and forces a significant high
positioning in the market for the division of network analyzer.
i. Benefits, associated costs, ease of usability
The network analyzer protocol is very beneficial to the network. The device additionally
helps in the examination of the system and performs observing of the frameworks. Henceforth,
they secure the frameworks shape the outer gatecrashers. It supports an extensive variety of
protocols such as the IP, BitTorrent, AppleTalk and DHCP. Likewise, with each of the refresh
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10
TCP/IP NETWORKING
the apparatus is refreshed and another convention is included to the application a regular routine.
The network analyzer underpins around eight hundred and fifty protocols.
The Wireshark Network analyzer is a tool that is free to use and hence it does not
require any additional cost for the company to bear. The cost for the implementation of the
system is almost null. The cost for the incorporation of the analyzer on the system framework is
extremely insignificant. Thus, the related cost for the analyzer is nearly nil. For utilizing the
instrument the base necessities of the system are: 60mb space on the hard drive, a processor that
has a clock speed of about 400 Mhz. Additionally the Network Interface Controller is also
recommended.
ii. Recommendation and preferences of using the tool
For recommendation it can be said that:
Understanding data: The user of the network should be able to understand the type of
data and also the flow of the data through the network. This would result in better handling of the
network analyzer.
Understanding configurations: The configurations in the network should also be
utilized efficiently by the user and they should also be able to understand all the major
functionalities in the network.
It can be said that the selected network analyzer for the designed network layout. The
task 2 of this report is concerned with the information about the network analyzer. M2M
Solutions is a company that is medium sized wants to expand their operations. Therefore the
company is required to reconstruct the network structure for their company. The job of
implementing a network design has been entrusted to me. The organization strategies don't
TCP/IP NETWORKING
the apparatus is refreshed and another convention is included to the application a regular routine.
The network analyzer underpins around eight hundred and fifty protocols.
The Wireshark Network analyzer is a tool that is free to use and hence it does not
require any additional cost for the company to bear. The cost for the implementation of the
system is almost null. The cost for the incorporation of the analyzer on the system framework is
extremely insignificant. Thus, the related cost for the analyzer is nearly nil. For utilizing the
instrument the base necessities of the system are: 60mb space on the hard drive, a processor that
has a clock speed of about 400 Mhz. Additionally the Network Interface Controller is also
recommended.
ii. Recommendation and preferences of using the tool
For recommendation it can be said that:
Understanding data: The user of the network should be able to understand the type of
data and also the flow of the data through the network. This would result in better handling of the
network analyzer.
Understanding configurations: The configurations in the network should also be
utilized efficiently by the user and they should also be able to understand all the major
functionalities in the network.
It can be said that the selected network analyzer for the designed network layout. The
task 2 of this report is concerned with the information about the network analyzer. M2M
Solutions is a company that is medium sized wants to expand their operations. Therefore the
company is required to reconstruct the network structure for their company. The job of
implementing a network design has been entrusted to me. The organization strategies don't

11
TCP/IP NETWORKING
include the utilization of network analyzers in their system in spite of the fact that the network
analyzers are extremely productive for the organization to do their procedures. But the staffs are
looking to cite the importance of the network analyzer tool to the company. This report provides
the required information about the tool.
TCP/IP NETWORKING
include the utilization of network analyzers in their system in spite of the fact that the network
analyzers are extremely productive for the organization to do their procedures. But the staffs are
looking to cite the importance of the network analyzer tool to the company. This report provides
the required information about the tool.
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





