Detailed Comparison of Current and Future IEEE 802.11 Standards
VerifiedAdded on 2021/04/17
|26
|7309
|66
Report
AI Summary
This report offers a detailed comparison of current and future IEEE 802.11 standards, crucial for wireless network applications. It begins with an executive summary, followed by an introduction to the convergence of communication networks and the importance of IEEE 802.11 standards in WLAN, Wi-Fi, WiMAX, and other technologies. The report examines standardization within IEEE 802, including the IEEE Standards Association and the LAN/MAN standards committee. It delves into the physical and MAC layers of the standards, the development of IEEE 802.11, and authentication/encryption methods like WEP, WPA, and WPA2. The discussion covers various IEEE 802.11 standards, their data rates, frequency bands, and security protocols, providing a comprehensive overview of wireless network technologies and their evolution. The report also analyzes the security risks, vulnerabilities, and benefits of wireless technology, along with the challenges and protocols involved in configuring a wireless network. The report also includes tables comparing data rates, typical ranges, and frequency bands of different IEEE standards.

Running head: A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11
STANDARDS
A Detailed Comparison of current and future IEEE 802.11
Standards
Name of the Student
Name of the University
Author’s Note
STANDARDS
A Detailed Comparison of current and future IEEE 802.11
Standards
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
Executive Summary
The report is prepared for presentation of a detailed comparison of the IEEE 802.11 standards for
its application in the current and future needs of the network. The IEEE 802.11 are air interface
standards that is used for connecting the wireless interfaces and communicating with each other.
There are different network technologies that are based on wired solution, but with the
deployment of the 802.11 standards the wireless LAN technologies have improved and it have
increased the scope to provide unlimited broadband access. The paper discusses on different
IEEE 802.11 standards and the encryption techniques followed for securing the wireless
networks. The security risk of the wireless network and the vulnerability are analyzed and
discussed in the report. There are several benefits of the wireless technology such as less
complexity in installation and elimination of the cabling cost and access of the network from the
mobile devices. There are several challenges of the wireless technology and this paper discussed
about the different IEEE 802.11 standards and the protocols used for the configuration of a
wireless network.
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
Executive Summary
The report is prepared for presentation of a detailed comparison of the IEEE 802.11 standards for
its application in the current and future needs of the network. The IEEE 802.11 are air interface
standards that is used for connecting the wireless interfaces and communicating with each other.
There are different network technologies that are based on wired solution, but with the
deployment of the 802.11 standards the wireless LAN technologies have improved and it have
increased the scope to provide unlimited broadband access. The paper discusses on different
IEEE 802.11 standards and the encryption techniques followed for securing the wireless
networks. The security risk of the wireless network and the vulnerability are analyzed and
discussed in the report. There are several benefits of the wireless technology such as less
complexity in installation and elimination of the cabling cost and access of the network from the
mobile devices. There are several challenges of the wireless technology and this paper discussed
about the different IEEE 802.11 standards and the protocols used for the configuration of a
wireless network.

2
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
Table of Contents
Introduction..........................................................................................................................3
Standardization in IEEE 802...............................................................................................4
IEEE Standard Association..............................................................................................4
IEEE 802: LAN MAN standard committee.....................................................................5
Physical Layer:..............................................................................................................10
Medium Access Control Layer:.....................................................................................11
Development of IEEE 802.11:...........................................................................................12
Authentication and Encryption in 802.11:.........................................................................12
Other Standards:................................................................................................................13
Conclusion.........................................................................................................................18
References..........................................................................................................................20
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
Table of Contents
Introduction..........................................................................................................................3
Standardization in IEEE 802...............................................................................................4
IEEE Standard Association..............................................................................................4
IEEE 802: LAN MAN standard committee.....................................................................5
Physical Layer:..............................................................................................................10
Medium Access Control Layer:.....................................................................................11
Development of IEEE 802.11:...........................................................................................12
Authentication and Encryption in 802.11:.........................................................................12
Other Standards:................................................................................................................13
Conclusion.........................................................................................................................18
References..........................................................................................................................20
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
Introduction
There has been a convergence of the networks of communication and technologies and it
is used for the development of the data communications for application in different fields of the
telecommunication environment. The technology is not dependent on the application in different
telecommunication networks, there are different communication standards that should be
followed for establishment of connection between the nodes installed in a telecommunication
framework. The telecommunication standards are followed internationally and the specification
of the standards are set by the IETF Internet Task Engineering Force (Xie et al. 2015). The
communication devices has increased and the use of mobile handheld devices has also increased
in the recent times. Thus with the increase in the mobile users new connection technology is
required to be deployed. IEEE 802.11 standard finds its application in the WLAN, Wifi,
WiMAX, 3G, 4G, etc. It is used for supporting the growth of the wireless networks and state the
communication methodology (Fay et al. 2016). The wireless technology is growing and a
comparison is made on the different IEEE standards for finding its application in different
wireless networks. The comparison is made based on the area of coverage, bandwidth,
interference and quality of the signals.
The main focus of the study is made on the WLA technology and different literatures are
reviewed for analyzing the access points and modes used for communication. A centralized
communication mode is followed for establishment of the wireless connection between the nodes
installed in the network. A study is also made on the decentralized communication modes and
communicate directly with the access points installed in different location of the network. IEEE
802.11 standards are reviewed in the context of extension point and the features available on the
IEEE 802.11 standards. There are some upcoming standards for the development of the IEEE
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
Introduction
There has been a convergence of the networks of communication and technologies and it
is used for the development of the data communications for application in different fields of the
telecommunication environment. The technology is not dependent on the application in different
telecommunication networks, there are different communication standards that should be
followed for establishment of connection between the nodes installed in a telecommunication
framework. The telecommunication standards are followed internationally and the specification
of the standards are set by the IETF Internet Task Engineering Force (Xie et al. 2015). The
communication devices has increased and the use of mobile handheld devices has also increased
in the recent times. Thus with the increase in the mobile users new connection technology is
required to be deployed. IEEE 802.11 standard finds its application in the WLAN, Wifi,
WiMAX, 3G, 4G, etc. It is used for supporting the growth of the wireless networks and state the
communication methodology (Fay et al. 2016). The wireless technology is growing and a
comparison is made on the different IEEE standards for finding its application in different
wireless networks. The comparison is made based on the area of coverage, bandwidth,
interference and quality of the signals.
The main focus of the study is made on the WLA technology and different literatures are
reviewed for analyzing the access points and modes used for communication. A centralized
communication mode is followed for establishment of the wireless connection between the nodes
installed in the network. A study is also made on the decentralized communication modes and
communicate directly with the access points installed in different location of the network. IEEE
802.11 standards are reviewed in the context of extension point and the features available on the
IEEE 802.11 standards. There are some upcoming standards for the development of the IEEE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
802.11 i.e. HiperLAN. The different layers of the network such as the physical layer, access
layer and the network layer are used for the transmission of the data packets in the network.
Radio medium are used for the transmission and for the development of the IEEE 802.11 the
targeted and the available standards are analyzed. The extension of the 802.11 are evaluated and
the data rate that should be maintained in the network are analyzed. The base standards of the
802.11 provides a data rate of 2Mbps and it can reach to 11 Mbps with the implementation of the
802.11b standards.
Standardization in IEEE 802
IEEE Standard Association
The IEEE is used for the development of nonprofit transitional methodology that are
supported by different technical activities that includes active program of standardization using
the IEEE standard association. The IEEE is a nonprofit translational technical professional
organization and it supports different technical activities such as an active standardization
program (Trappe 2015). It can be openly developed and it have been proved that the participation
of the voluntary participants can help in producing high quality accepted result that can be used
for the development of the IEEE 802.11 standards. IEE 802.11 have a parameter that is the
fragmentation threshold which defines the method of transmission also known as the
fragmentation burst. The Mac protocol data unit which is larger than the threshold is divided into
smaller elements and each of the elements are transmitted in the wireless network at a regular
interval of time. This procedure saves the cost and time wireless network by retransmitting the
smaller elements where error is found instead of resending the whole MSDU unit (Lyamin et al.
2014). There is a requirement of implementation of the QoS in the wireless LAN and the
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
802.11 i.e. HiperLAN. The different layers of the network such as the physical layer, access
layer and the network layer are used for the transmission of the data packets in the network.
Radio medium are used for the transmission and for the development of the IEEE 802.11 the
targeted and the available standards are analyzed. The extension of the 802.11 are evaluated and
the data rate that should be maintained in the network are analyzed. The base standards of the
802.11 provides a data rate of 2Mbps and it can reach to 11 Mbps with the implementation of the
802.11b standards.
Standardization in IEEE 802
IEEE Standard Association
The IEEE is used for the development of nonprofit transitional methodology that are
supported by different technical activities that includes active program of standardization using
the IEEE standard association. The IEEE is a nonprofit translational technical professional
organization and it supports different technical activities such as an active standardization
program (Trappe 2015). It can be openly developed and it have been proved that the participation
of the voluntary participants can help in producing high quality accepted result that can be used
for the development of the IEEE 802.11 standards. IEE 802.11 have a parameter that is the
fragmentation threshold which defines the method of transmission also known as the
fragmentation burst. The Mac protocol data unit which is larger than the threshold is divided into
smaller elements and each of the elements are transmitted in the wireless network at a regular
interval of time. This procedure saves the cost and time wireless network by retransmitting the
smaller elements where error is found instead of resending the whole MSDU unit (Lyamin et al.
2014). There is a requirement of implementation of the QoS in the wireless LAN and the

5
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
following four parameters should be considered for maintaining the quality of the network such
as:
- Bandwidth /Throughput
- Latency / Delay
- Jitter, and
- Error or data loss
The environment of the WLAN is dependent on inference and it can cause high errors
and it should be eliminated for getting the best performance of the wireless network. The
confidentiality of the network should be maintained and data should not be access by any third
party and it should reach to the user as the same fort when it was sent by the sender over the
network.
IEEE 802: LAN MAN standard committee
The 802 standards works on the Open Systems Interconnection OSI layer. The radio
waves was first used for the transferring of data packets over short distance and it is different
from the wired medium used for transmission of the data packets. Attenuation occurs in the
signals of the radio waves and thus it is difficult to find the collision between the data packets
(Zheng and Li 2015). The 802.11 standards was developed following the home and the office
networks and it was introduced in the year 1999. The primary standard of 802.11 can provide a
data rate of 2 mbps for each of the access points installed in the network the data rate can be
increased to 11 mbps with the implementation of the 802.11b standard in the network. There are
new IEEE extensions such as IEEE 802.11g and IEEE 802.11a that can be applied for
connecting the wireless local area network. The WLAN devices selected for the transmission of
the data should fulfill the security mechanism and it should also have the QoS support for
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
following four parameters should be considered for maintaining the quality of the network such
as:
- Bandwidth /Throughput
- Latency / Delay
- Jitter, and
- Error or data loss
The environment of the WLAN is dependent on inference and it can cause high errors
and it should be eliminated for getting the best performance of the wireless network. The
confidentiality of the network should be maintained and data should not be access by any third
party and it should reach to the user as the same fort when it was sent by the sender over the
network.
IEEE 802: LAN MAN standard committee
The 802 standards works on the Open Systems Interconnection OSI layer. The radio
waves was first used for the transferring of data packets over short distance and it is different
from the wired medium used for transmission of the data packets. Attenuation occurs in the
signals of the radio waves and thus it is difficult to find the collision between the data packets
(Zheng and Li 2015). The 802.11 standards was developed following the home and the office
networks and it was introduced in the year 1999. The primary standard of 802.11 can provide a
data rate of 2 mbps for each of the access points installed in the network the data rate can be
increased to 11 mbps with the implementation of the 802.11b standard in the network. There are
new IEEE extensions such as IEEE 802.11g and IEEE 802.11a that can be applied for
connecting the wireless local area network. The WLAN devices selected for the transmission of
the data should fulfill the security mechanism and it should also have the QoS support for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
handling the security threats that can affect the network (Ma et al. 2015). There are certain
limitations of the IEEE 802.11 and it should be improved for meeting the security framework
and different features must be enabled for allowing seamless transmission between the nodes
installed in the network. Different bands are used for transmission such as the 2.4 GHZ and 5
GHz bands for reducing the inference and improve the quality of the network.
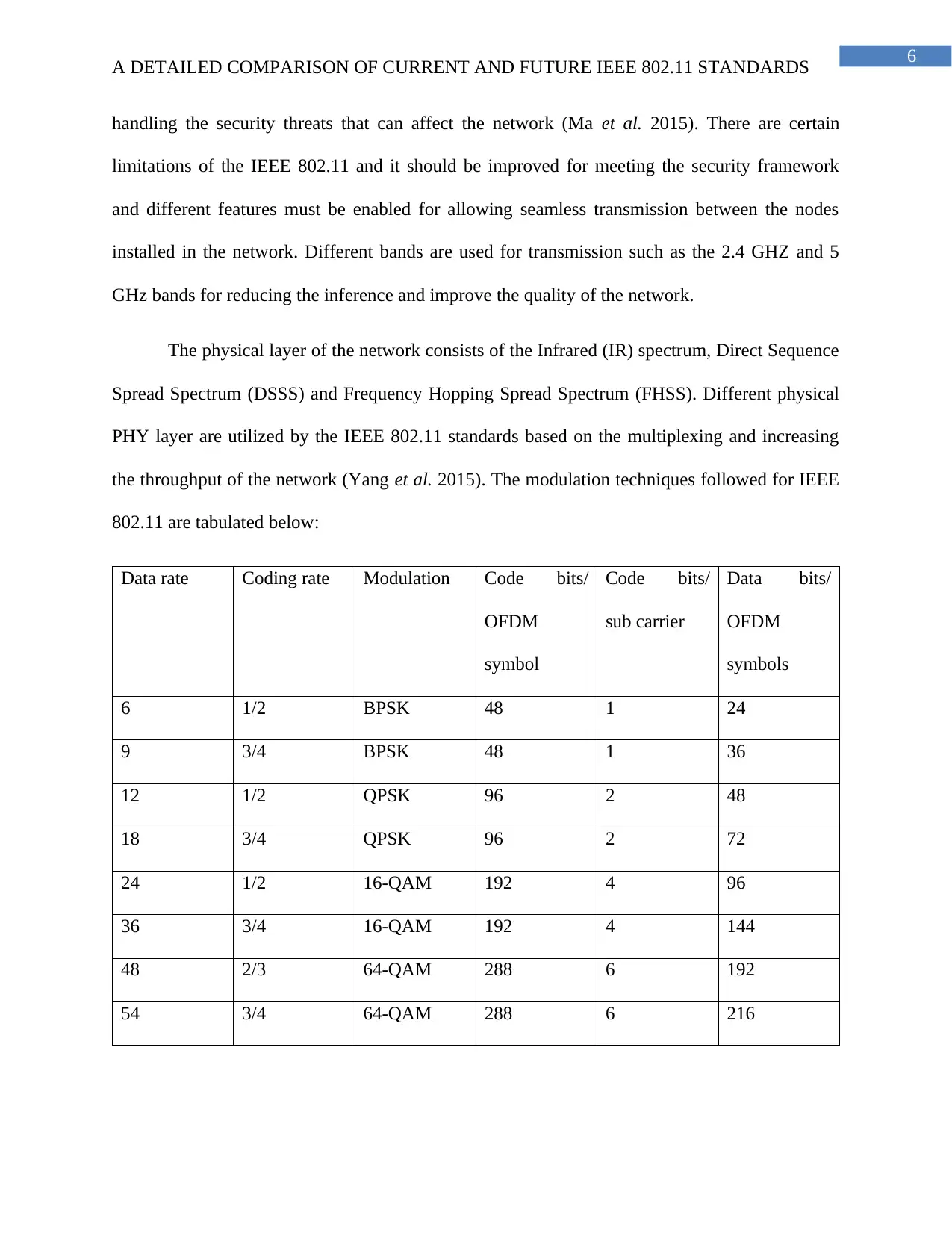
The physical layer of the network consists of the Infrared (IR) spectrum, Direct Sequence
Spread Spectrum (DSSS) and Frequency Hopping Spread Spectrum (FHSS). Different physical
PHY layer are utilized by the IEEE 802.11 standards based on the multiplexing and increasing
the throughput of the network (Yang et al. 2015). The modulation techniques followed for IEEE
802.11 are tabulated below:
Data rate Coding rate Modulation Code bits/
OFDM
symbol
Code bits/
sub carrier
Data bits/
OFDM
symbols
6 1/2 BPSK 48 1 24
9 3/4 BPSK 48 1 36
12 1/2 QPSK 96 2 48
18 3/4 QPSK 96 2 72
24 1/2 16-QAM 192 4 96
36 3/4 16-QAM 192 4 144
48 2/3 64-QAM 288 6 192
54 3/4 64-QAM 288 6 216
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
handling the security threats that can affect the network (Ma et al. 2015). There are certain
limitations of the IEEE 802.11 and it should be improved for meeting the security framework
and different features must be enabled for allowing seamless transmission between the nodes
installed in the network. Different bands are used for transmission such as the 2.4 GHZ and 5
GHz bands for reducing the inference and improve the quality of the network.
The physical layer of the network consists of the Infrared (IR) spectrum, Direct Sequence
Spread Spectrum (DSSS) and Frequency Hopping Spread Spectrum (FHSS). Different physical
PHY layer are utilized by the IEEE 802.11 standards based on the multiplexing and increasing
the throughput of the network (Yang et al. 2015). The modulation techniques followed for IEEE
802.11 are tabulated below:
Data rate Coding rate Modulation Code bits/
OFDM
symbol
Code bits/
sub carrier
Data bits/
OFDM
symbols
6 1/2 BPSK 48 1 24
9 3/4 BPSK 48 1 36
12 1/2 QPSK 96 2 48
18 3/4 QPSK 96 2 72
24 1/2 16-QAM 192 4 96
36 3/4 16-QAM 192 4 144
48 2/3 64-QAM 288 6 192
54 3/4 64-QAM 288 6 216
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
The IEEE 802.11b utilizes a new PHY layer and high rate DSSS which is based on the
orthogonal Frequency Division Multiplexing and is used for increasing the overall throughput of
the access point installed in different location of the network. Most of the extension of IEEE
Conclusion works on the 2.4 Ghz frequency band and it has 14 different channels. The
availability of the channels depends on different countries (Rajandekar and Sikdar 2015). In the
year 1997 the 802.11 standard was developed for the WLANs and it supports the radio
transmission in the 2.4 Ghz frequency bands. In the year 1999, IEEE made two amendments in
the 802.11 standards i.e. the 802.11 a standard and the 802.11 b standard, which is used for
defining the transmission methodology and the WLAN equipment’s for the enterprise and the
personal usage.
The 802.11b is the most successful wireless technology and it can offer data rate of about
11 mbps. It is designed to get the maximum performance from the network with more security
and throughput when compared with the wired network. The IEEE 802.11g was launched in the
year 2003 that offers the network utilizing the 2.4 Ghz frequency band to support a data rate of
54 mbps and most importantly it was designed such that it was compatible with the previous
802.11 standards (Qiao et al. 2015). The following table is created to demonstrate the maximum
data rate that can be achieved with the different IEEE 802.11 standards in the network, their
typical range and the frequency bands.
IEEE
Standards
Typical Range Maximum Data
Rate
Frequency
bands
Comment
802.11 50 to 100 m 2.4 GHz 2 Mbps
802.11a 50 to 100 m 5 GHz 54 Mbps It is not
compatible with
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
The IEEE 802.11b utilizes a new PHY layer and high rate DSSS which is based on the
orthogonal Frequency Division Multiplexing and is used for increasing the overall throughput of
the access point installed in different location of the network. Most of the extension of IEEE
Conclusion works on the 2.4 Ghz frequency band and it has 14 different channels. The
availability of the channels depends on different countries (Rajandekar and Sikdar 2015). In the
year 1997 the 802.11 standard was developed for the WLANs and it supports the radio
transmission in the 2.4 Ghz frequency bands. In the year 1999, IEEE made two amendments in
the 802.11 standards i.e. the 802.11 a standard and the 802.11 b standard, which is used for
defining the transmission methodology and the WLAN equipment’s for the enterprise and the
personal usage.
The 802.11b is the most successful wireless technology and it can offer data rate of about
11 mbps. It is designed to get the maximum performance from the network with more security
and throughput when compared with the wired network. The IEEE 802.11g was launched in the
year 2003 that offers the network utilizing the 2.4 Ghz frequency band to support a data rate of
54 mbps and most importantly it was designed such that it was compatible with the previous
802.11 standards (Qiao et al. 2015). The following table is created to demonstrate the maximum
data rate that can be achieved with the different IEEE 802.11 standards in the network, their
typical range and the frequency bands.
IEEE
Standards
Typical Range Maximum Data
Rate
Frequency
bands
Comment
802.11 50 to 100 m 2.4 GHz 2 Mbps
802.11a 50 to 100 m 5 GHz 54 Mbps It is not
compatible with
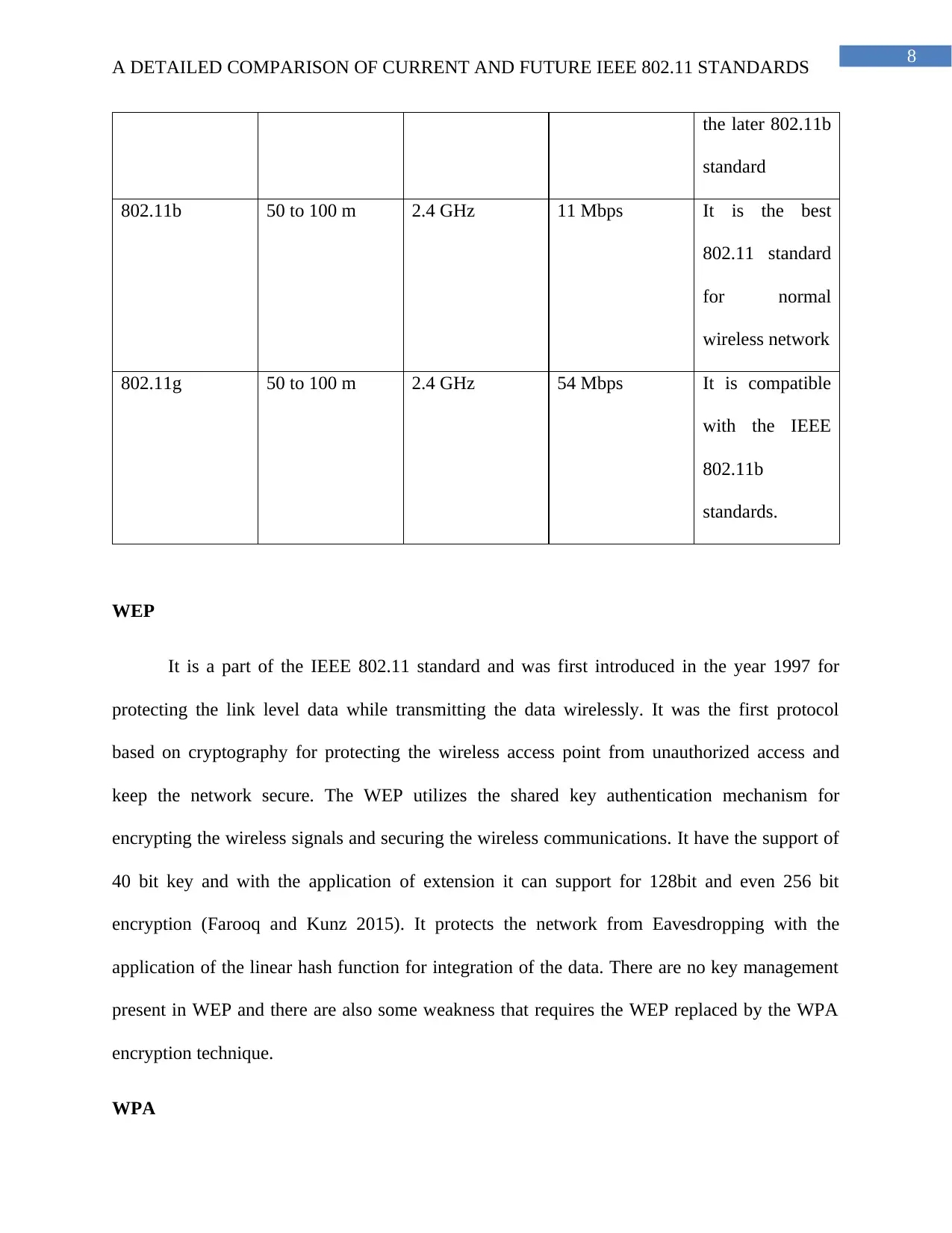
8
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
the later 802.11b
standard
802.11b 50 to 100 m 2.4 GHz 11 Mbps It is the best
802.11 standard
for normal
wireless network
802.11g 50 to 100 m 2.4 GHz 54 Mbps It is compatible
with the IEEE
802.11b
standards.
WEP
It is a part of the IEEE 802.11 standard and was first introduced in the year 1997 for
protecting the link level data while transmitting the data wirelessly. It was the first protocol
based on cryptography for protecting the wireless access point from unauthorized access and
keep the network secure. The WEP utilizes the shared key authentication mechanism for
encrypting the wireless signals and securing the wireless communications. It have the support of
40 bit key and with the application of extension it can support for 128bit and even 256 bit
encryption (Farooq and Kunz 2015). It protects the network from Eavesdropping with the
application of the linear hash function for integration of the data. There are no key management
present in WEP and there are also some weakness that requires the WEP replaced by the WPA
encryption technique.
WPA
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
the later 802.11b
standard
802.11b 50 to 100 m 2.4 GHz 11 Mbps It is the best
802.11 standard
for normal
wireless network
802.11g 50 to 100 m 2.4 GHz 54 Mbps It is compatible
with the IEEE
802.11b
standards.
WEP
It is a part of the IEEE 802.11 standard and was first introduced in the year 1997 for
protecting the link level data while transmitting the data wirelessly. It was the first protocol
based on cryptography for protecting the wireless access point from unauthorized access and
keep the network secure. The WEP utilizes the shared key authentication mechanism for
encrypting the wireless signals and securing the wireless communications. It have the support of
40 bit key and with the application of extension it can support for 128bit and even 256 bit
encryption (Farooq and Kunz 2015). It protects the network from Eavesdropping with the
application of the linear hash function for integration of the data. There are no key management
present in WEP and there are also some weakness that requires the WEP replaced by the WPA
encryption technique.
WPA
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
There are two security protocol WPA and WPA2 developed by the Wi Fi alliance, one
was designed for mitigation of the problem faced in the WEP while the later WPA 2 was
designed for the enterprise and the personal usage. For the personal mode of 802.11 a pre shared
key is used for authentication and for the enterprise mode the IEEE 802.1X is applied for getting
an optimum result. There are different encryption algorithm applied for securing the wireless
network, among them the WPA and the WPA2 was developed for overcoming the shortcomings
of the WEP ad reducing the complexity of the network (Ma et al. 2015). The WPA 2 can be
easily deployed and meets the 802.11i specification for addressing the weakness of WEP. The
TKIP algorithm is used by the WPA and it works by providing each of the client with a unique
key and an encrypted message is used for checking the integrity and with the fields in the
packets. It is specially designed such that the attackers cannot capture the data packets sent over
the wireless network and preventing the spoofing and denial of service attacks (Shokri-
Ghadikolaei et al. 2015). There are four different key factors for the WPA2 authentication such
as:
- Mutual authentication
- Ease to Use
- Interoperability, and
- Strong Encryption
WPA2 have several advantages because it can be used for the management of the keys
and detection of the replays. The main aspect of the wireless network are the security and the
confidentiality of the users must be maintained while sending and receiving the information over
the network (Trivedi 2016). There are different types of attacks that can compromise the security
of the network such as spoofing, man in the middle attack, session hijacking, etc. With the
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
There are two security protocol WPA and WPA2 developed by the Wi Fi alliance, one
was designed for mitigation of the problem faced in the WEP while the later WPA 2 was
designed for the enterprise and the personal usage. For the personal mode of 802.11 a pre shared
key is used for authentication and for the enterprise mode the IEEE 802.1X is applied for getting
an optimum result. There are different encryption algorithm applied for securing the wireless
network, among them the WPA and the WPA2 was developed for overcoming the shortcomings
of the WEP ad reducing the complexity of the network (Ma et al. 2015). The WPA 2 can be
easily deployed and meets the 802.11i specification for addressing the weakness of WEP. The
TKIP algorithm is used by the WPA and it works by providing each of the client with a unique
key and an encrypted message is used for checking the integrity and with the fields in the
packets. It is specially designed such that the attackers cannot capture the data packets sent over
the wireless network and preventing the spoofing and denial of service attacks (Shokri-
Ghadikolaei et al. 2015). There are four different key factors for the WPA2 authentication such
as:
- Mutual authentication
- Ease to Use
- Interoperability, and
- Strong Encryption
WPA2 have several advantages because it can be used for the management of the keys
and detection of the replays. The main aspect of the wireless network are the security and the
confidentiality of the users must be maintained while sending and receiving the information over
the network (Trivedi 2016). There are different types of attacks that can compromise the security
of the network such as spoofing, man in the middle attack, session hijacking, etc. With the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
application of the IEEE a secure wireless network can be created and the data transmission speed
similar to the wired network can be achieved (Ye 2017). It can be used for effectiveness of the
mechanism and analysis of the performance of the network.
With the implementation of the IEEE the wireless network can be secured because there
are several features in the IEEE such as filtering of the Media control access address and
disabling of the SSID. The vulnerability of the network can be reduced with the evolution of the
computer hardware and software technology but some of the wireless network still needs to
address the security problems for making it more secure. The Wi Max have some drawbacks
such as mutual authentication which makes it susceptible to spoofing and relay attacks.
Physical Layer:
In order to enhance the average throughput of the network, various Physical Layers are
used in the 802.11 standard. The physical layers that are used in the network are such as
Frequency Hopping Spread Spectrum or FHSS, Direct Sequence Spread Spectrum or DSSS and
infrared or IR. The 802.11b utilizes an additional physical layer along with the mentioned layers
named as High Rate DSSS. On the basis of the (Orthogonal Frequency Division Multiplexing,
the 802.11g and 802.11a are invented (Palattella et al. 2016). This mechanism is very assisting in
increasing the entire throughput of the access point. The OFDM mechanism is used along with
the MIMO or Multi Input Multi Output methodology. Most of the extension of the 802.11
operates in the 2.4 GHz spectrum band with fourteen distinct channels. The capability of these
channels are different in different countries. The last feature that was included in the 802.11j was
the last channel of the fourteen channels mentioned above. This channel was developed
especially for Japan (Khorov et al. 2015).
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
application of the IEEE a secure wireless network can be created and the data transmission speed
similar to the wired network can be achieved (Ye 2017). It can be used for effectiveness of the
mechanism and analysis of the performance of the network.
With the implementation of the IEEE the wireless network can be secured because there
are several features in the IEEE such as filtering of the Media control access address and
disabling of the SSID. The vulnerability of the network can be reduced with the evolution of the
computer hardware and software technology but some of the wireless network still needs to
address the security problems for making it more secure. The Wi Max have some drawbacks
such as mutual authentication which makes it susceptible to spoofing and relay attacks.
Physical Layer:
In order to enhance the average throughput of the network, various Physical Layers are
used in the 802.11 standard. The physical layers that are used in the network are such as
Frequency Hopping Spread Spectrum or FHSS, Direct Sequence Spread Spectrum or DSSS and
infrared or IR. The 802.11b utilizes an additional physical layer along with the mentioned layers
named as High Rate DSSS. On the basis of the (Orthogonal Frequency Division Multiplexing,
the 802.11g and 802.11a are invented (Palattella et al. 2016). This mechanism is very assisting in
increasing the entire throughput of the access point. The OFDM mechanism is used along with
the MIMO or Multi Input Multi Output methodology. Most of the extension of the 802.11
operates in the 2.4 GHz spectrum band with fourteen distinct channels. The capability of these
channels are different in different countries. The last feature that was included in the 802.11j was
the last channel of the fourteen channels mentioned above. This channel was developed
especially for Japan (Khorov et al. 2015).

11
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
The extension of IEEE 802.11a functions with channels ranging from thirty-five to one
hundred and sixty one on the basis of frequency band. This standard works with only the 5 GHz
frequency. In U.S.A. and Europe there are twelve and nineteen non-overlapping channels
respectively. However, in terms of 802.11b there are only three out of fourteen non-overlapping
channels (Abdelrahman, Mustafa and Osman 2015). The bandwidth is high in case of 802.11n as
it work in the overlapping channels with 20 and 40 MHz bandwidth. The directional antennas
may be utilized for establishing the peer to peer WLAN links. The omnidirectional antennas that
are used in the distinctive WLAN access are ranged thirty-fifty and hundred meter in case of
indoor and outdoor respectively. The range can be highly affected by the obstacles placed within
the access point and station (Palattella et al. 2016). In comparison to 802.11b and 802.11g, the
802.11a is affected by the increase in the range. This is because the 802.11a operates in the
5MHz frequency range. The sectored antennas are capable of increasing the average data rate of
WLAN by two to three times.
Medium Access Control Layer:
The scheme named as the Distributed Coordinated Function or DCF is used by the IEEE
802.11 which is based on contention. Within this method, the station in connection with the
access point is responsible for scanning the interface of air regarding identifying the availability
of channel. If the interface is found to be idle then the station transmits its information to the
designated destination via access point. The collision occurs while more than a single station is
trying to access the access point or the air interface is busy (Freudiger 2015). The IEEE 802.11
CSMA/CA or Carrier Sense Multiple Access/Collision Avoidance for avoiding the collisions.
Another MAC method is utilized by IEEE 802.11 named as Point Coordination Function. This
methodology is consisted with two sections. Round Robin mechanism is used by the access
A DETAILED COMPARISON OF CURRENT AND FUTURE IEEE 802.11 STANDARDS
The extension of IEEE 802.11a functions with channels ranging from thirty-five to one
hundred and sixty one on the basis of frequency band. This standard works with only the 5 GHz
frequency. In U.S.A. and Europe there are twelve and nineteen non-overlapping channels
respectively. However, in terms of 802.11b there are only three out of fourteen non-overlapping
channels (Abdelrahman, Mustafa and Osman 2015). The bandwidth is high in case of 802.11n as
it work in the overlapping channels with 20 and 40 MHz bandwidth. The directional antennas
may be utilized for establishing the peer to peer WLAN links. The omnidirectional antennas that
are used in the distinctive WLAN access are ranged thirty-fifty and hundred meter in case of
indoor and outdoor respectively. The range can be highly affected by the obstacles placed within
the access point and station (Palattella et al. 2016). In comparison to 802.11b and 802.11g, the
802.11a is affected by the increase in the range. This is because the 802.11a operates in the
5MHz frequency range. The sectored antennas are capable of increasing the average data rate of
WLAN by two to three times.
Medium Access Control Layer:
The scheme named as the Distributed Coordinated Function or DCF is used by the IEEE
802.11 which is based on contention. Within this method, the station in connection with the
access point is responsible for scanning the interface of air regarding identifying the availability
of channel. If the interface is found to be idle then the station transmits its information to the
designated destination via access point. The collision occurs while more than a single station is
trying to access the access point or the air interface is busy (Freudiger 2015). The IEEE 802.11
CSMA/CA or Carrier Sense Multiple Access/Collision Avoidance for avoiding the collisions.
Another MAC method is utilized by IEEE 802.11 named as Point Coordination Function. This
methodology is consisted with two sections. Round Robin mechanism is used by the access
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 26
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





