T1 2019 MN502 Network Security Report: Digital Security Analysis
VerifiedAdded on 2023/03/20
|16
|1143
|95
Report
AI Summary
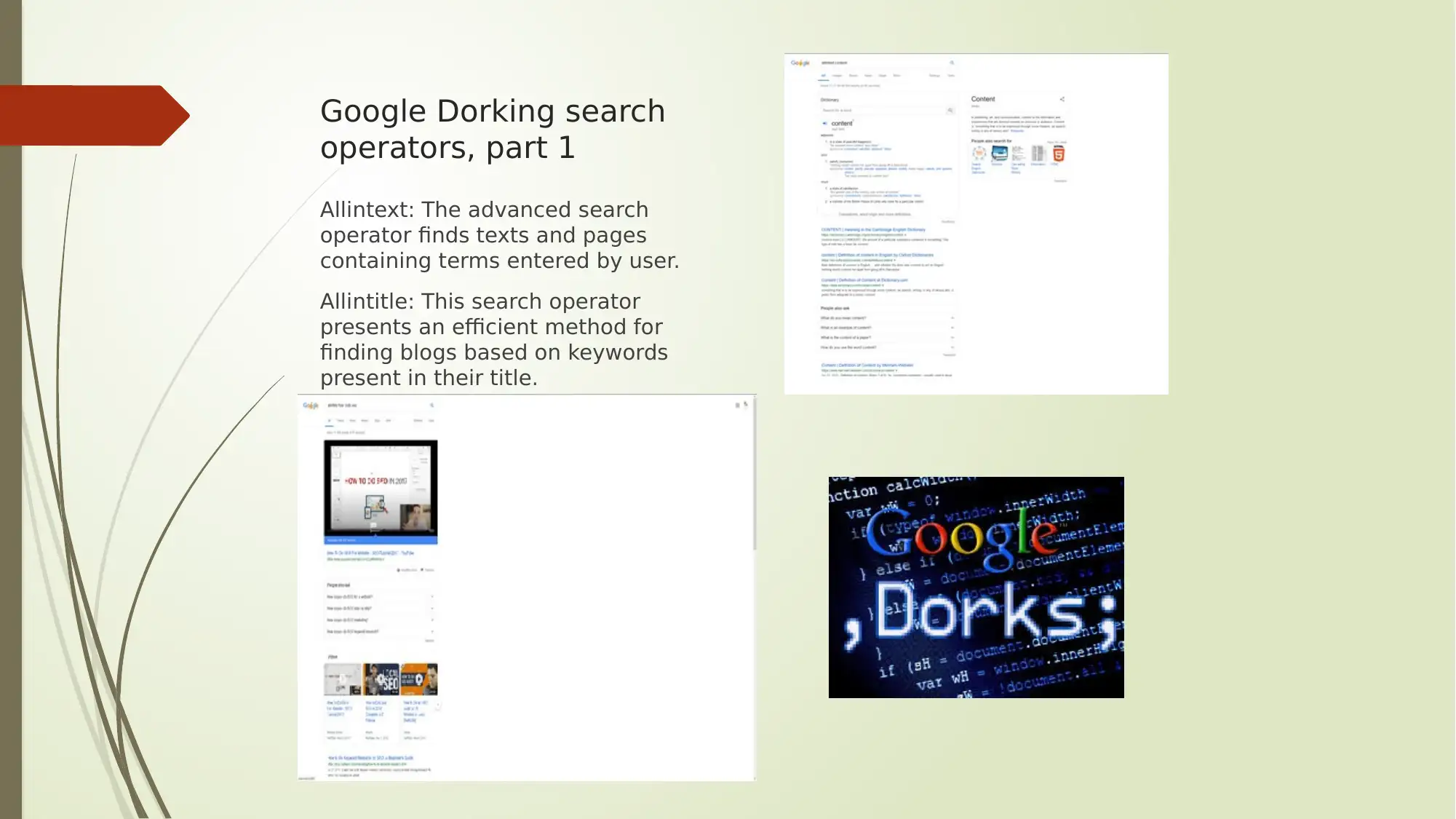
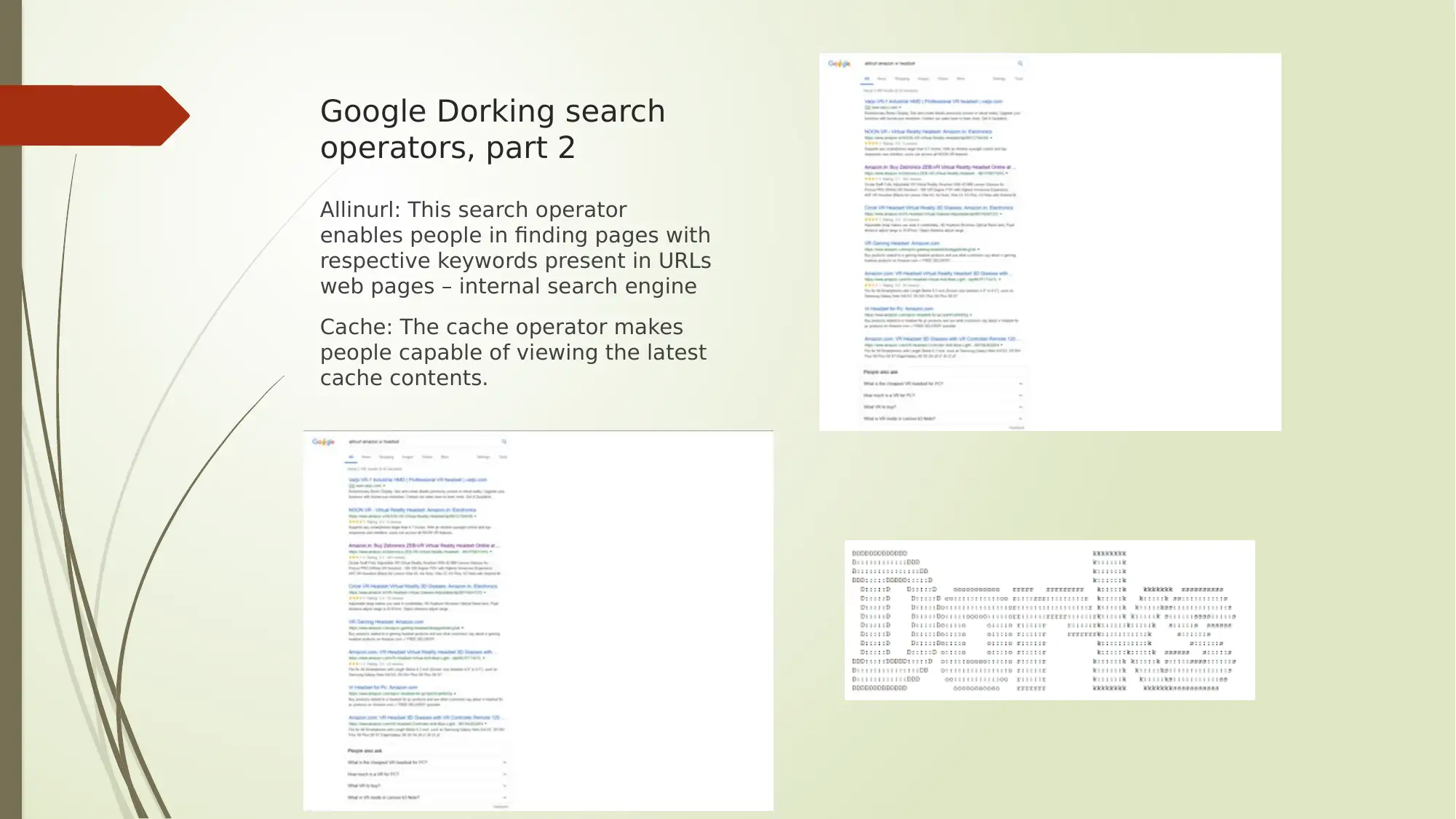
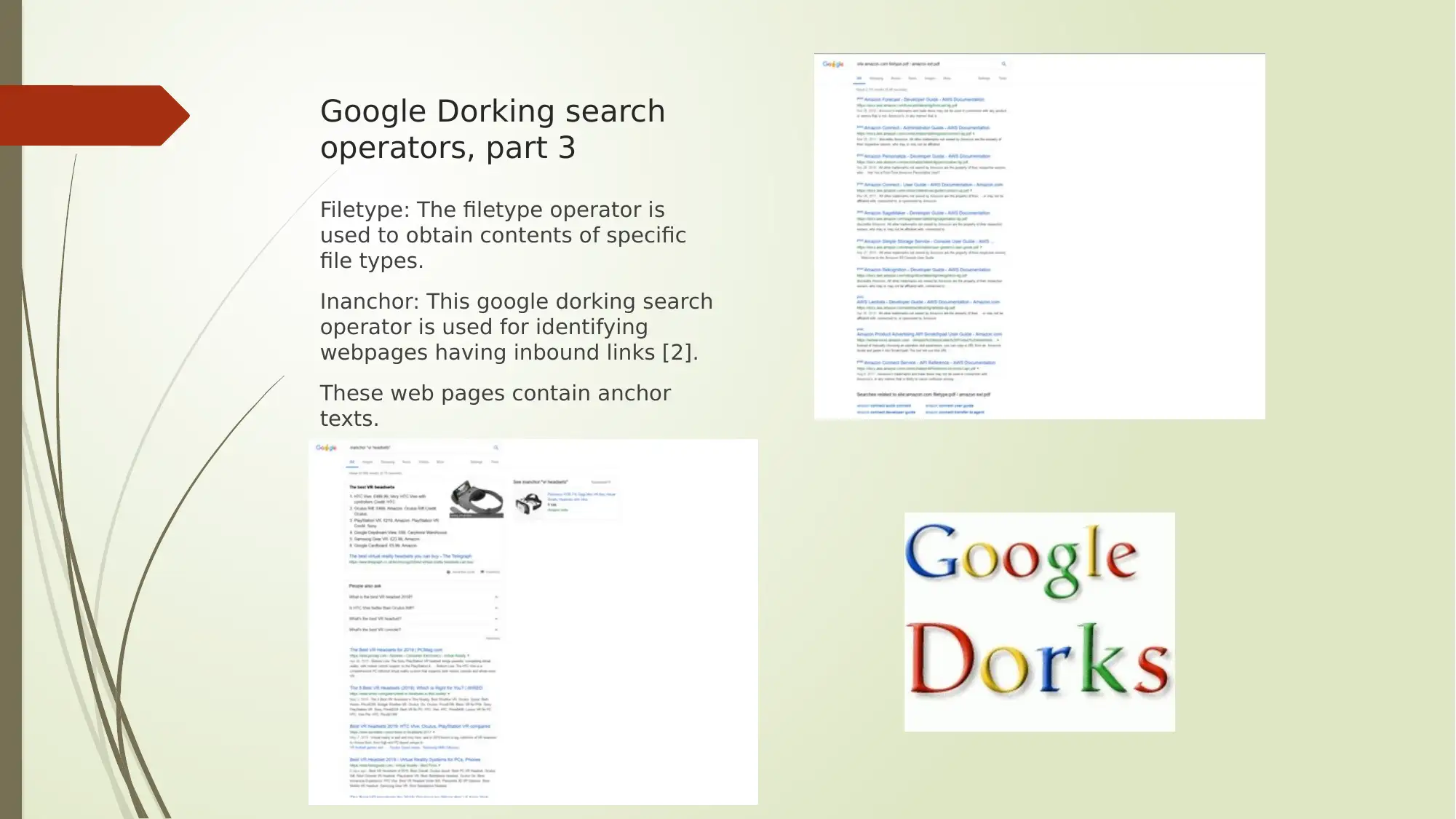
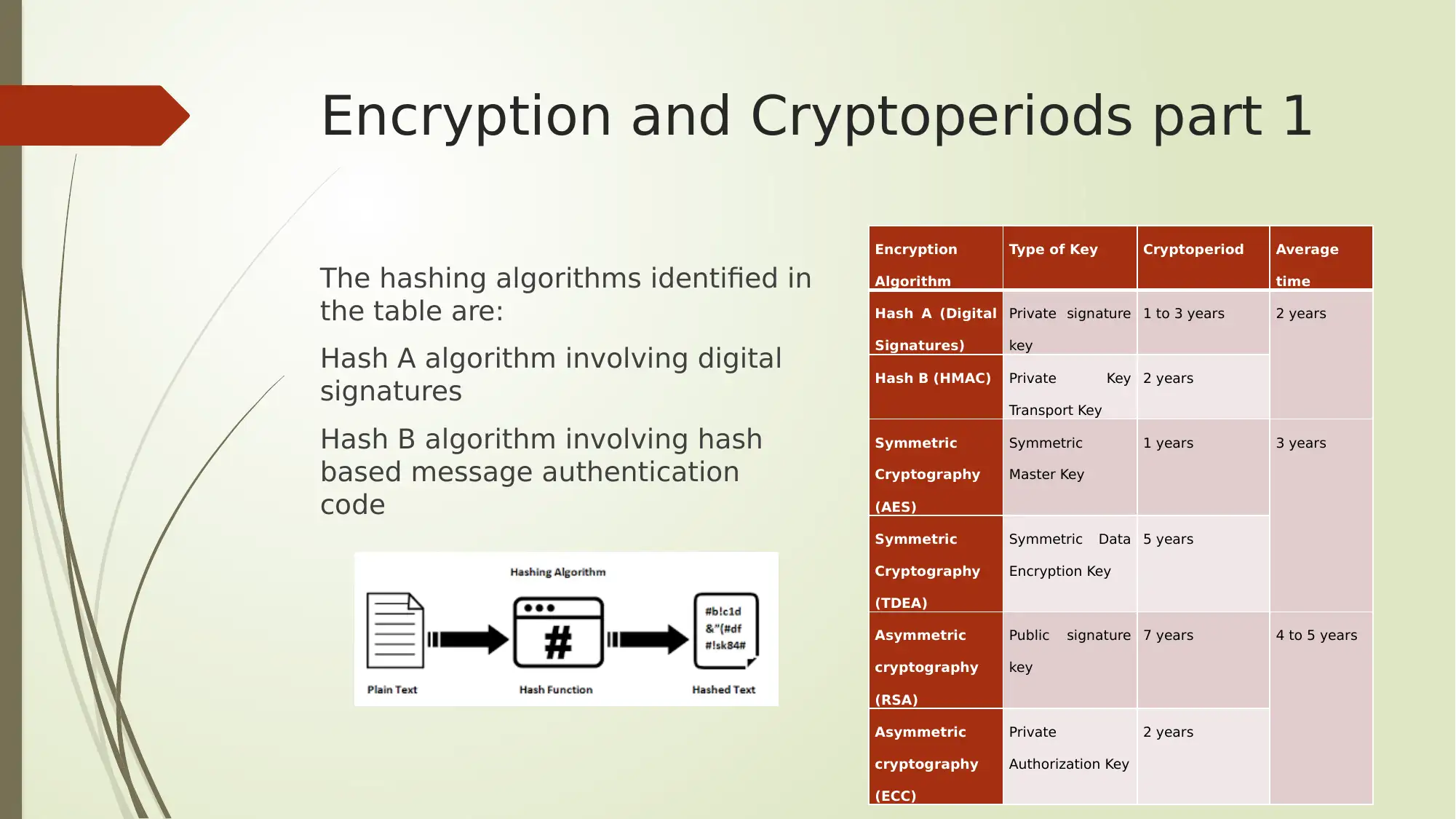
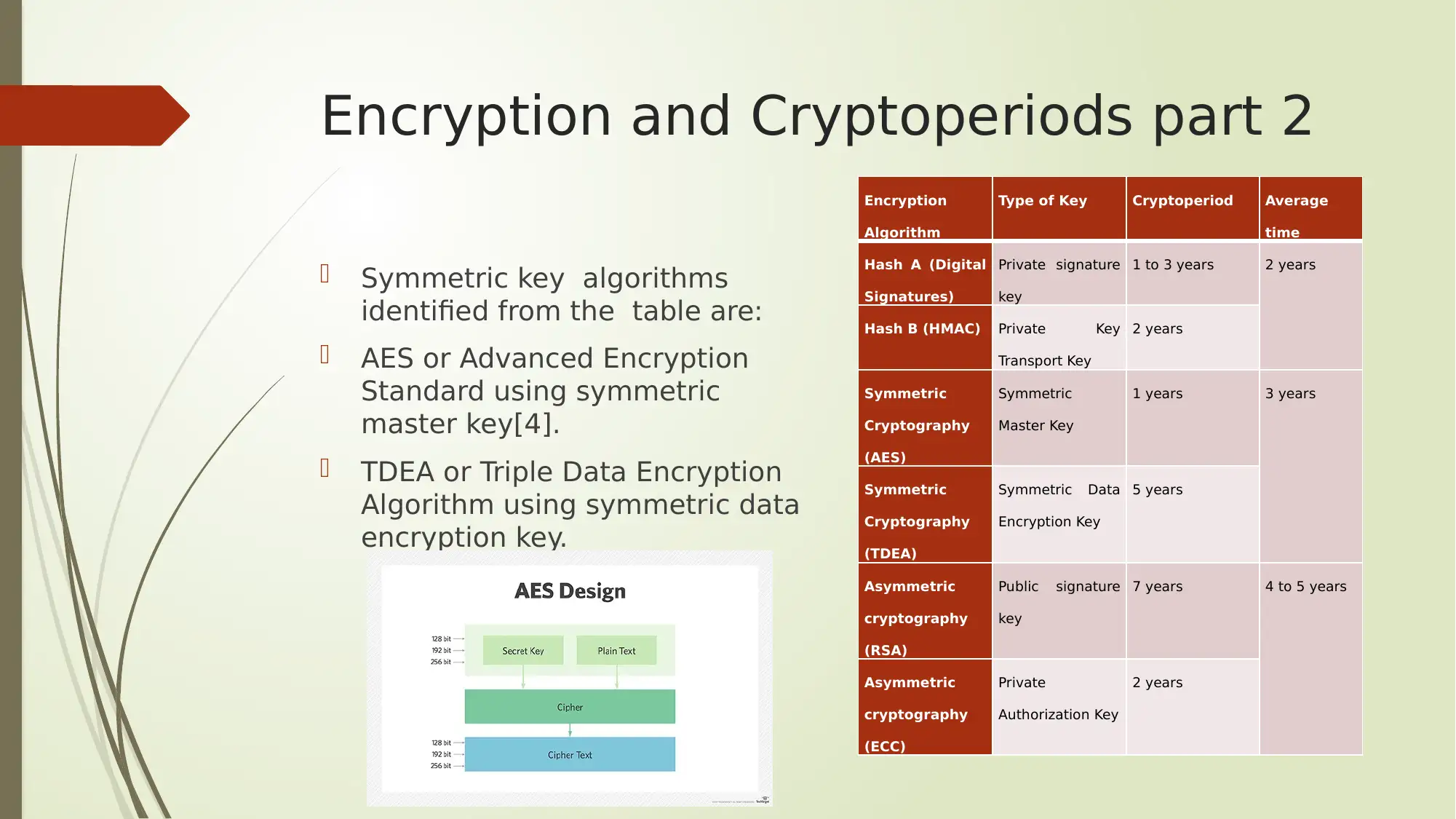
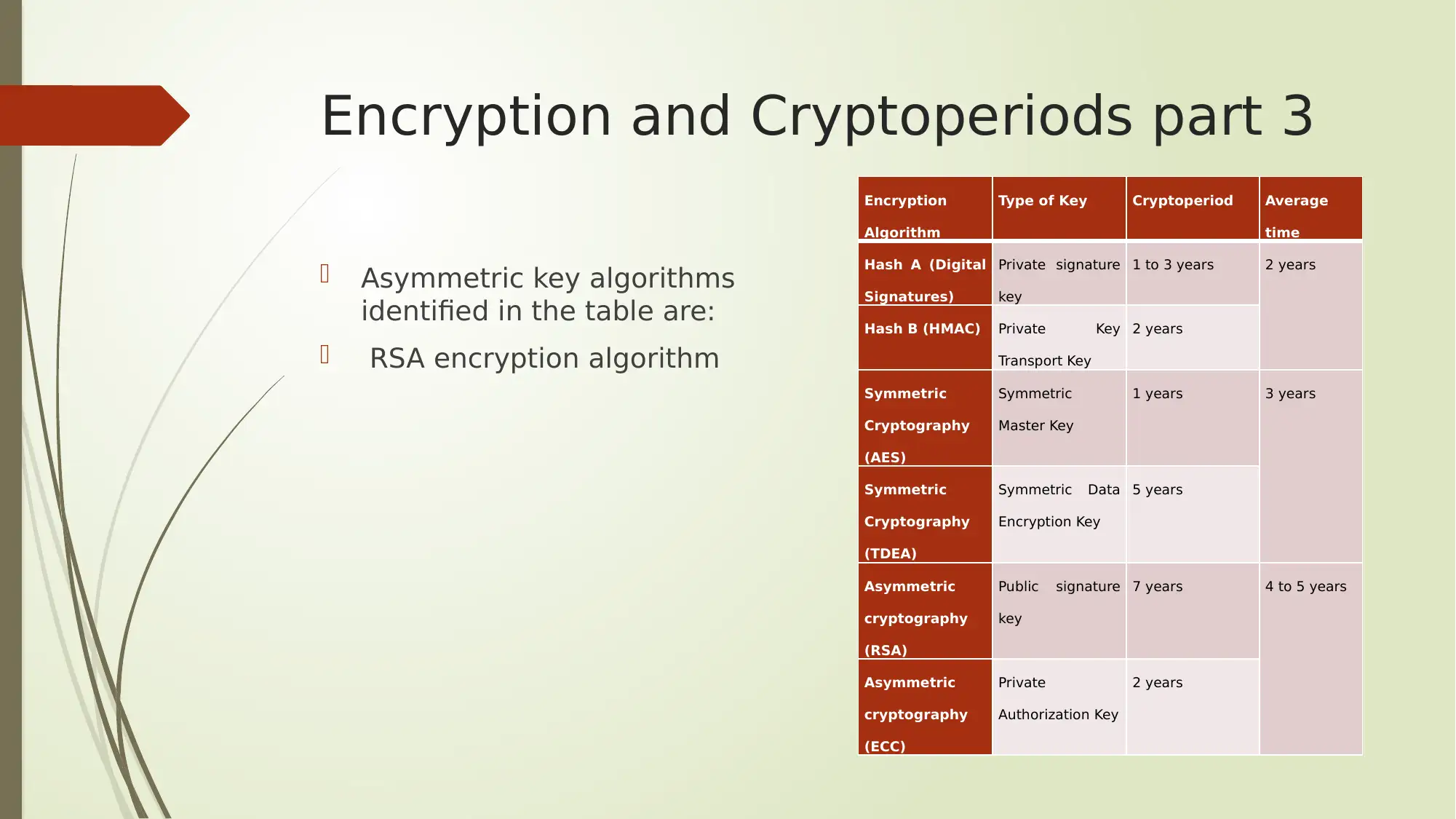
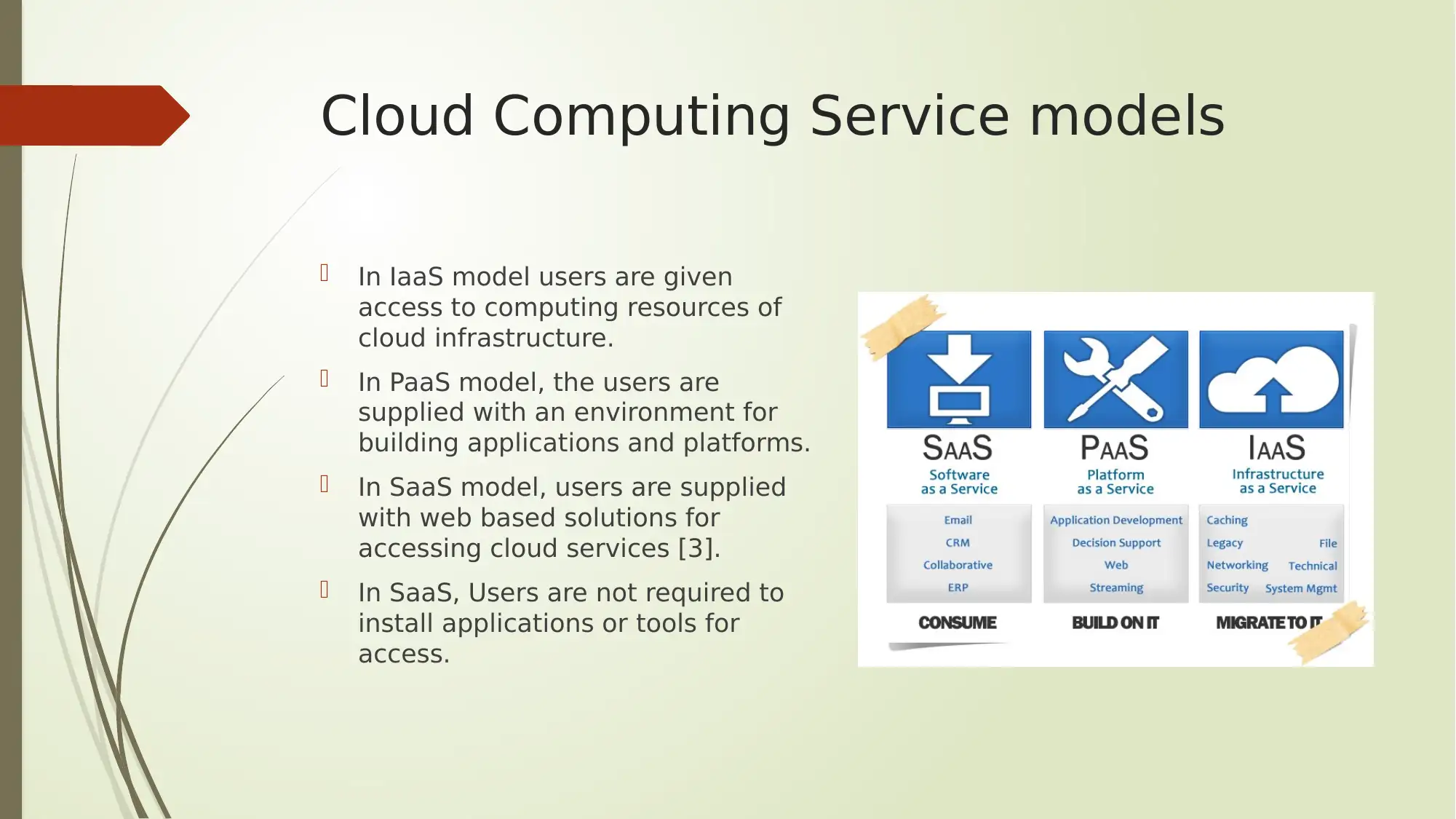
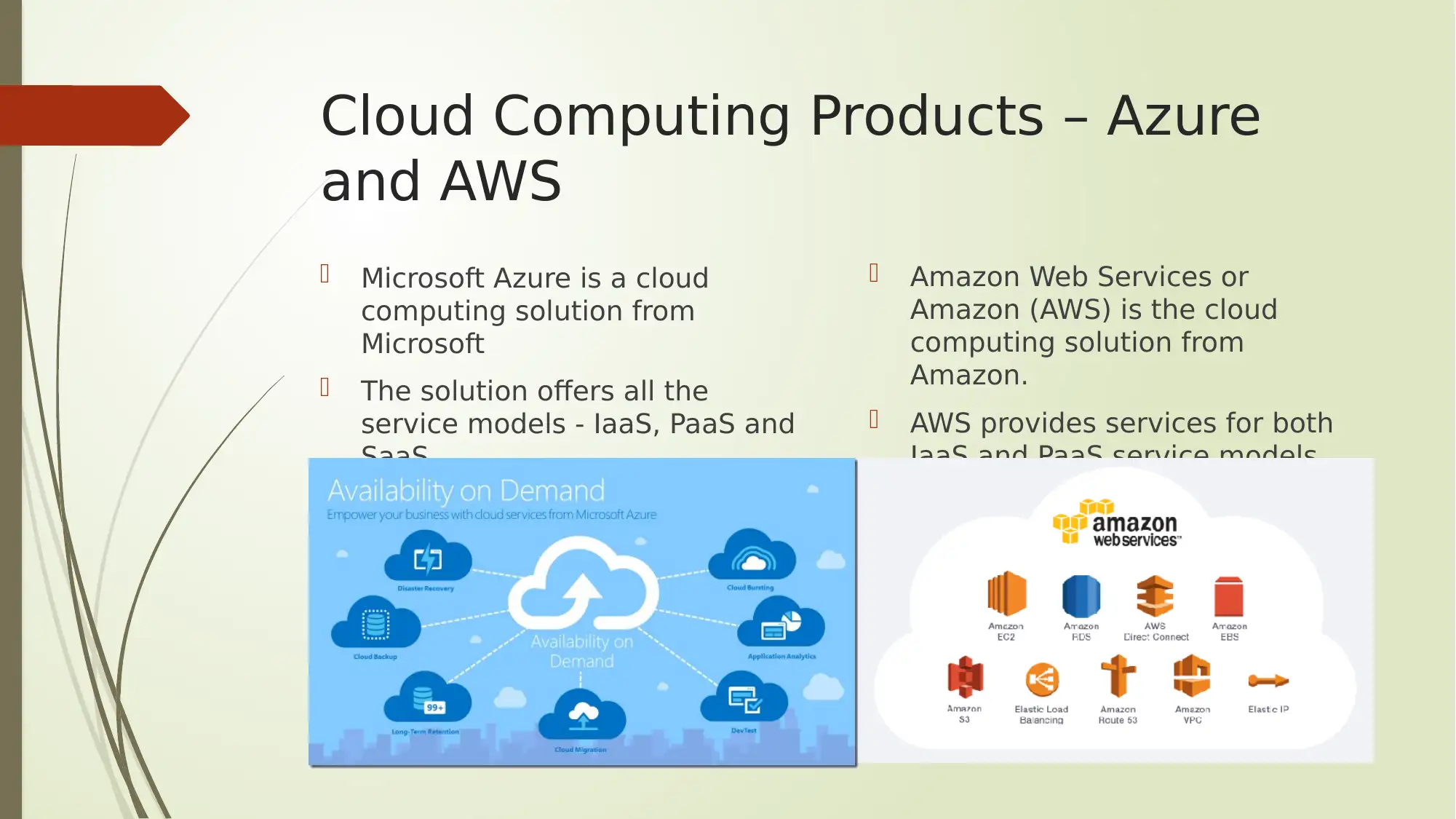
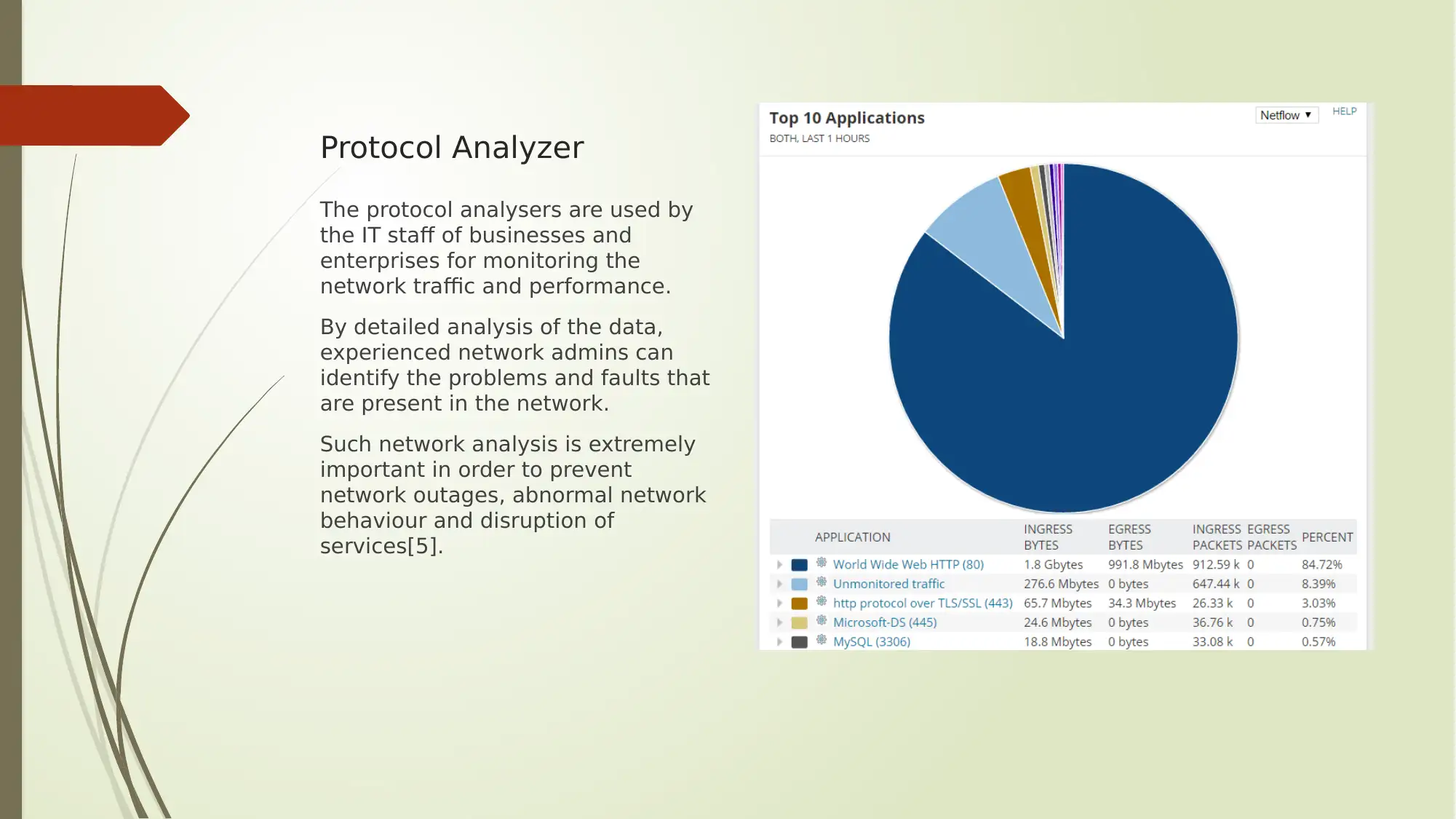
This report provides an analysis of several key aspects of digital security, encompassing Google Dorking search operators, encryption methods, cloud computing service models, and protocol analyzers. The report begins by outlining various Google Dorking operators like allintext, allintitle, allinurl, filetype, and inanchor, along with their potential security threats and recommended protective measures. It then delves into encryption and cryptoperiods, detailing different hashing algorithms, symmetric and asymmetric key algorithms (AES, TDEA, RSA, ECC), and their respective key types and average cryptoperiods. Furthermore, the report explores cloud computing service models such as IaaS, PaaS, and SaaS, and highlights leading cloud computing solutions like Microsoft Azure and Amazon Web Services (AWS). Finally, the report discusses the role of protocol analyzers, particularly Wireshark, in network monitoring and performance analysis, emphasizing their importance in identifying network issues and preventing service disruptions. The report concludes by summarizing the key findings and emphasizing the significance of these topics in the context of network security.
1 out of 16