A Report on Virtual Private Network Security Protocols and Processes
VerifiedAdded on 2021/06/18
|16
|2095
|37
Report
AI Summary
This report provides a comprehensive overview of Virtual Private Networks (VPNs), exploring various aspects of their security and functionality. It begins with an introduction to VPNs, explaining their role in secure communication and data protection. The report then delves into the authentication proce...

A REPORT
ON
VIRTUAL PRIVATE NETWORK
STUDENT NAME-
STUDENT ID-
SUBMISSION DATE-
1
ON
VIRTUAL PRIVATE NETWORK
STUDENT NAME-
STUDENT ID-
SUBMISSION DATE-
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1) Introduction……………………………………………………………………………………………….. 4-5
2) Authentication…………………………………………………………………………………………….. 5-9
3) Confidentiality and Integrity process…………………………………………………………… 10-13
4) Protection against Replay attacks……………………………………………………………….. 14
5) Conclusion………………………………………………………………………………………………….. 14
6) References…………………………………………………………………………………………………. 15-16
2
1) Introduction……………………………………………………………………………………………….. 4-5
2) Authentication…………………………………………………………………………………………….. 5-9
3) Confidentiality and Integrity process…………………………………………………………… 10-13
4) Protection against Replay attacks……………………………………………………………….. 14
5) Conclusion………………………………………………………………………………………………….. 14
6) References…………………………………………………………………………………………………. 15-16
2

Table of figures
1) Figure 1……………………………………………………………………………………………………………7
2) Figure 2……………………………………………………………………………………………………………8
3) Figure 3……………………………………………………………………………………………………………9
4) Figure 4……………………………………………………………………………………………………………11
5) Figure 5……………………………………………………………………………………………………………12
6) Figure 6……………………………………………………………………………………………………………13
3
1) Figure 1……………………………………………………………………………………………………………7
2) Figure 2……………………………………………………………………………………………………………8
3) Figure 3……………………………………………………………………………………………………………9
4) Figure 4……………………………………………………………………………………………………………11
5) Figure 5……………………………………………………………………………………………………………12
6) Figure 6……………………………………………………………………………………………………………13
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
Virtual Private System for the most part known as VPN is a safe method for associating a private
system through an open passage. As it were, it is a sort of passage which experiences open system to
a remote system. Virtual private system is the development that can be utilized from a remote
system securely, so the correspondence data is protected from sniffing or catching by programmers.
VPN association can be built up between two VPN systems by means of a secured passage with the
capacity to encode the data, ensure information trustworthiness and assurance the correspondence
simply happen between those two confirmed systems.
The VPN is to some degree associated with the past remote system called open exchanged phone
organize. VPN systems are related with IP based correspondence. Before VPN appeared huge
endeavors put bunches of assets and time in building multifaceted private systems, these private
systems are called intranets. It was exorbitant to introduce the private systems. A few organizations,
who couldn't bear the cost of rented lines, utilized low speed arrange administrations. As the Web
ended up being progressively open and exchange speed limits created, associations began to put
their Intranets onto the web and make what are as of now known as Extranets to interface inside
and outside customers. Security is the fundamental issue behind the phone arrange. Today, VPN
organize gives a secured distributed association. VPN are essentially low in costs than private or
rented organize as the correspondence is done over open system. Prior the VPN innovation was hard
to actualize yet on account of the cutting edge innovation, our innovation has achieved a level where
sending is basic and reasonable for a wide range of associations.
Fundamentally this report tells about the procedures and the security advancements being utilized
when we get to your financial balance online by means of a web program. The Web is an open
system and each and every message you trade with the server can conceivably be caught by
aggressors. This report additionally incorporates the advances and systems that are utilized to keep
aggressors from adjusting the money related exchange demands we start on the server and what
keeps your passwords and charge card subtle elements safe on the wire between your program and
the web based managing an account server.
4
Virtual Private System for the most part known as VPN is a safe method for associating a private
system through an open passage. As it were, it is a sort of passage which experiences open system to
a remote system. Virtual private system is the development that can be utilized from a remote
system securely, so the correspondence data is protected from sniffing or catching by programmers.
VPN association can be built up between two VPN systems by means of a secured passage with the
capacity to encode the data, ensure information trustworthiness and assurance the correspondence
simply happen between those two confirmed systems.
The VPN is to some degree associated with the past remote system called open exchanged phone
organize. VPN systems are related with IP based correspondence. Before VPN appeared huge
endeavors put bunches of assets and time in building multifaceted private systems, these private
systems are called intranets. It was exorbitant to introduce the private systems. A few organizations,
who couldn't bear the cost of rented lines, utilized low speed arrange administrations. As the Web
ended up being progressively open and exchange speed limits created, associations began to put
their Intranets onto the web and make what are as of now known as Extranets to interface inside
and outside customers. Security is the fundamental issue behind the phone arrange. Today, VPN
organize gives a secured distributed association. VPN are essentially low in costs than private or
rented organize as the correspondence is done over open system. Prior the VPN innovation was hard
to actualize yet on account of the cutting edge innovation, our innovation has achieved a level where
sending is basic and reasonable for a wide range of associations.
Fundamentally this report tells about the procedures and the security advancements being utilized
when we get to your financial balance online by means of a web program. The Web is an open
system and each and every message you trade with the server can conceivably be caught by
aggressors. This report additionally incorporates the advances and systems that are utilized to keep
aggressors from adjusting the money related exchange demands we start on the server and what
keeps your passwords and charge card subtle elements safe on the wire between your program and
the web based managing an account server.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Authentication Process between the server and the browser –
1.1 Analytical Task
(a.) How the browser ensures that it is communicating to the right server?
At the point when the client enters the URL in the program, the program starts a TCP
association with the server through its IP address show in DNS. At that point URL is changed
over into an IP address by the program and the procedure is called DNS query demands. At
that point server recognizes the TCP communication, the program sends HTTPs ask for to
the server to recover the substance. After the server answers with content for the page, the
program recoups it from the HTTP bundles and shows it as necessities be. This HTTP is
recognizable in left side corner of request bar which shows correspondence is secure or not
and the confirmation is in like manner unmistakable there. This is the way by which
program chooses in the event that it has passed on to right server or not. [1]
(b.) Describe the role of digital signatures in authentication process?
A digital signature is a computerized code confirmed by open key encryption which is
connected to an electronically transmitted archive to approve the genuineness and honesty
of the product or advanced report. In dealing with a record industry advanced marks are
valuable for different causes. Some managing an account exchange like credits, account
openings needs customer signature essentials which consistently require all chronicles to be
sent and handshakes for buyer dependability and further with the customer assertion by
denoting the record. The introduction of computerized marks into this saving money
process winds up being profitable as it passes on essential and quantifiable results the
extent that cost, increments in exchange speed and enhances the buyer devotion. [2]
(c.) How the server ensures that it is communicating to the account owner?
Server utilizes confirmation for the reason to know precisely who is getting to the data or
site. In this verification procedure, client needs to demonstrate its personality by giving the
certifications like client name and secret word. There are additionally other confirmation
forms like entering card points of interest, retina examine, voice acknowledgment and
fingerprints. Validation does not make sense of which undertakings the individual can do or
what records the individual can see. Verification checks the client is substantial or not. [3]
5
1.1 Analytical Task
(a.) How the browser ensures that it is communicating to the right server?
At the point when the client enters the URL in the program, the program starts a TCP
association with the server through its IP address show in DNS. At that point URL is changed
over into an IP address by the program and the procedure is called DNS query demands. At
that point server recognizes the TCP communication, the program sends HTTPs ask for to
the server to recover the substance. After the server answers with content for the page, the
program recoups it from the HTTP bundles and shows it as necessities be. This HTTP is
recognizable in left side corner of request bar which shows correspondence is secure or not
and the confirmation is in like manner unmistakable there. This is the way by which
program chooses in the event that it has passed on to right server or not. [1]
(b.) Describe the role of digital signatures in authentication process?
A digital signature is a computerized code confirmed by open key encryption which is
connected to an electronically transmitted archive to approve the genuineness and honesty
of the product or advanced report. In dealing with a record industry advanced marks are
valuable for different causes. Some managing an account exchange like credits, account
openings needs customer signature essentials which consistently require all chronicles to be
sent and handshakes for buyer dependability and further with the customer assertion by
denoting the record. The introduction of computerized marks into this saving money
process winds up being profitable as it passes on essential and quantifiable results the
extent that cost, increments in exchange speed and enhances the buyer devotion. [2]
(c.) How the server ensures that it is communicating to the account owner?
Server utilizes confirmation for the reason to know precisely who is getting to the data or
site. In this verification procedure, client needs to demonstrate its personality by giving the
certifications like client name and secret word. There are additionally other confirmation
forms like entering card points of interest, retina examine, voice acknowledgment and
fingerprints. Validation does not make sense of which undertakings the individual can do or
what records the individual can see. Verification checks the client is substantial or not. [3]
5

(d.) Briefly describe at least three other additional techniques that can be used to achieve
authentication of the clients by servers.
Verification is procedure of recognizing a client by its legitimate client name and secret key
and it should likewise be possible through Macintosh address.
Three strategies that can be utilized to accomplish confirmation of the customers by server
are:-
• 802.1X confirmation — 802.1X is a procedure for affirming the character of a
customer before giving framework access to the customer. Remote Validation Dial In Client
Administration (Sweep) is a tradition that gives united confirmation, endorsement, and
accounting organization. For approval reason, the remote client can accomplice to a
framework get to server (NAS) or Sweep client, for instance, a remote IAP. The remote
client can pass data movement basically after productive 802.1X approval.
• MAC validation – Media Access Control (Macintosh) affirmation is used for
confirming contraptions in perspective of their physical Macintosh addresses. Mac
confirmation requires that the Macintosh address of a machine facilitates a physically
portrayed summary of addresses. This affirmation procedure isn't endorsed for adaptable
frameworks and the frameworks that require stringent security settings. [4]
• Kerberos Verification - Kerberos is a trusted outsider affirmation system that relies
upon shared insider certainties. It presumes that the outcast is secure, and gives single sign-
on capacities, brought together watchword storing, database interface confirmation, and
overhauled PC security. It does this through a Kerberos affirmation server, or through Digital
safe Dynamic Trust, a business Kerberos-based approval server.
6
authentication of the clients by servers.
Verification is procedure of recognizing a client by its legitimate client name and secret key
and it should likewise be possible through Macintosh address.
Three strategies that can be utilized to accomplish confirmation of the customers by server
are:-
• 802.1X confirmation — 802.1X is a procedure for affirming the character of a
customer before giving framework access to the customer. Remote Validation Dial In Client
Administration (Sweep) is a tradition that gives united confirmation, endorsement, and
accounting organization. For approval reason, the remote client can accomplice to a
framework get to server (NAS) or Sweep client, for instance, a remote IAP. The remote
client can pass data movement basically after productive 802.1X approval.
• MAC validation – Media Access Control (Macintosh) affirmation is used for
confirming contraptions in perspective of their physical Macintosh addresses. Mac
confirmation requires that the Macintosh address of a machine facilitates a physically
portrayed summary of addresses. This affirmation procedure isn't endorsed for adaptable
frameworks and the frameworks that require stringent security settings. [4]
• Kerberos Verification - Kerberos is a trusted outsider affirmation system that relies
upon shared insider certainties. It presumes that the outcast is secure, and gives single sign-
on capacities, brought together watchword storing, database interface confirmation, and
overhauled PC security. It does this through a Kerberos affirmation server, or through Digital
safe Dynamic Trust, a business Kerberos-based approval server.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
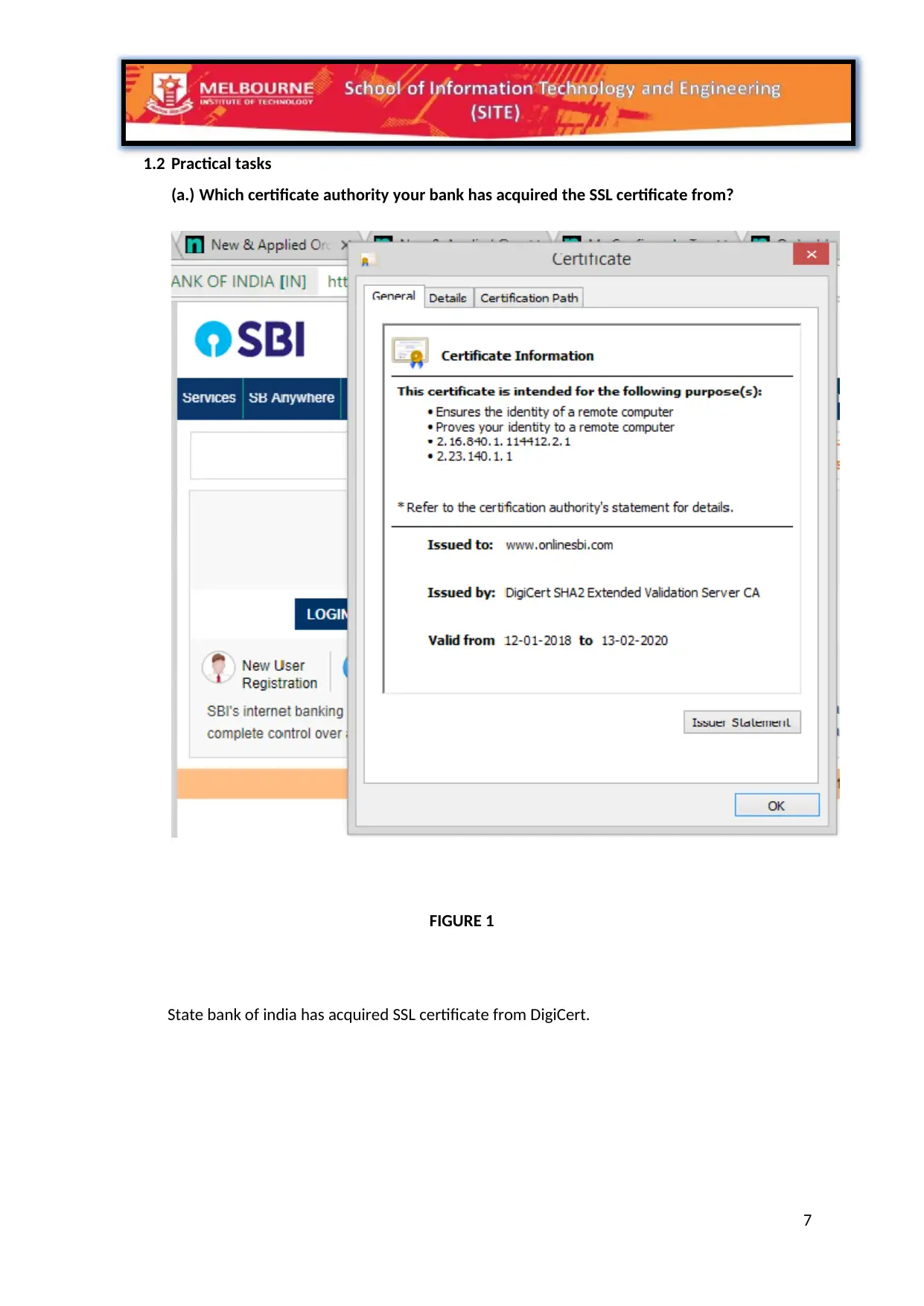
1.2 Practical tasks
(a.) Which certificate authority your bank has acquired the SSL certificate from?
FIGURE 1
State bank of india has acquired SSL certificate from DigiCert.
7
(a.) Which certificate authority your bank has acquired the SSL certificate from?
FIGURE 1
State bank of india has acquired SSL certificate from DigiCert.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
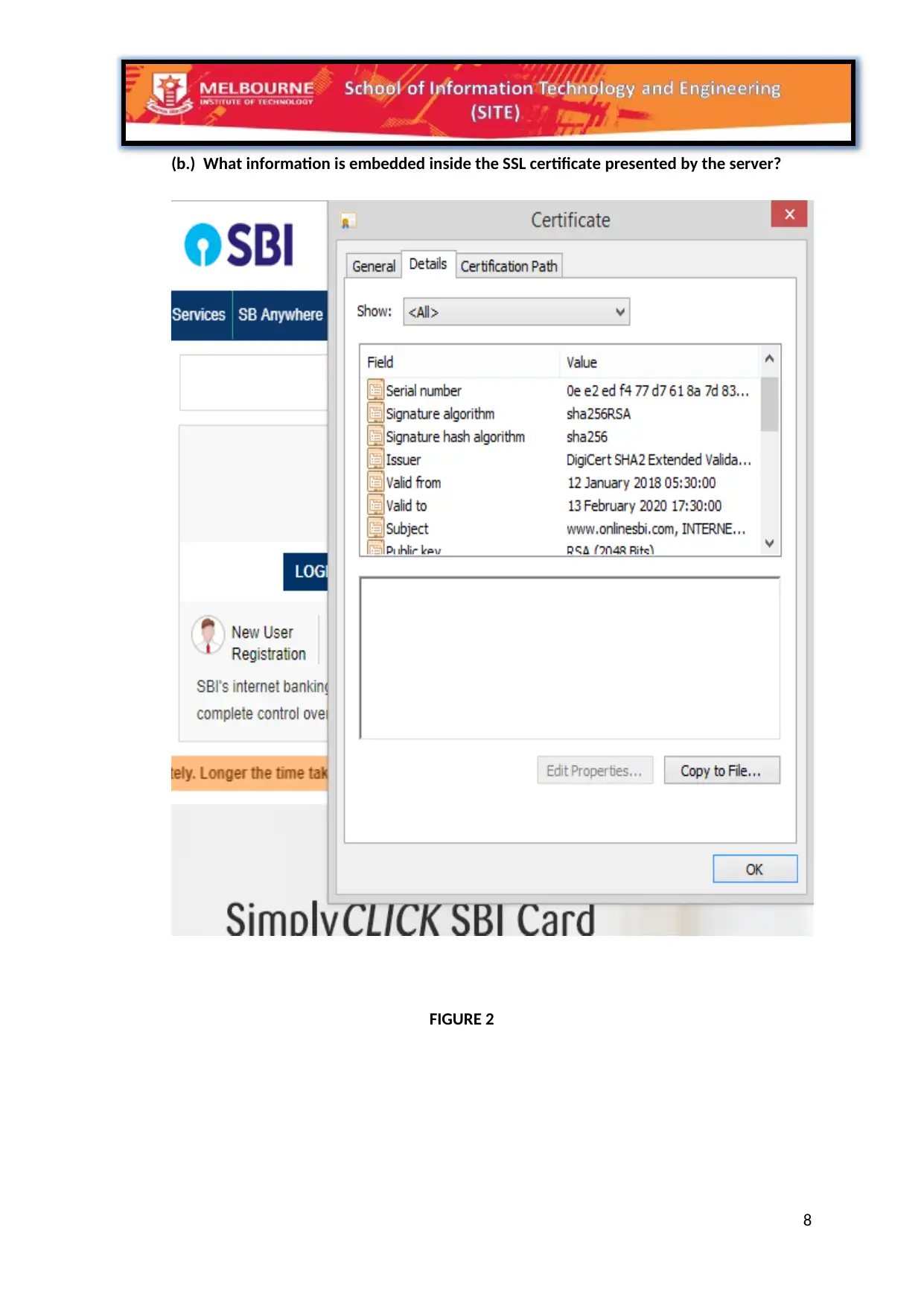
(b.) What information is embedded inside the SSL certificate presented by the server?
FIGURE 2
8
FIGURE 2
8
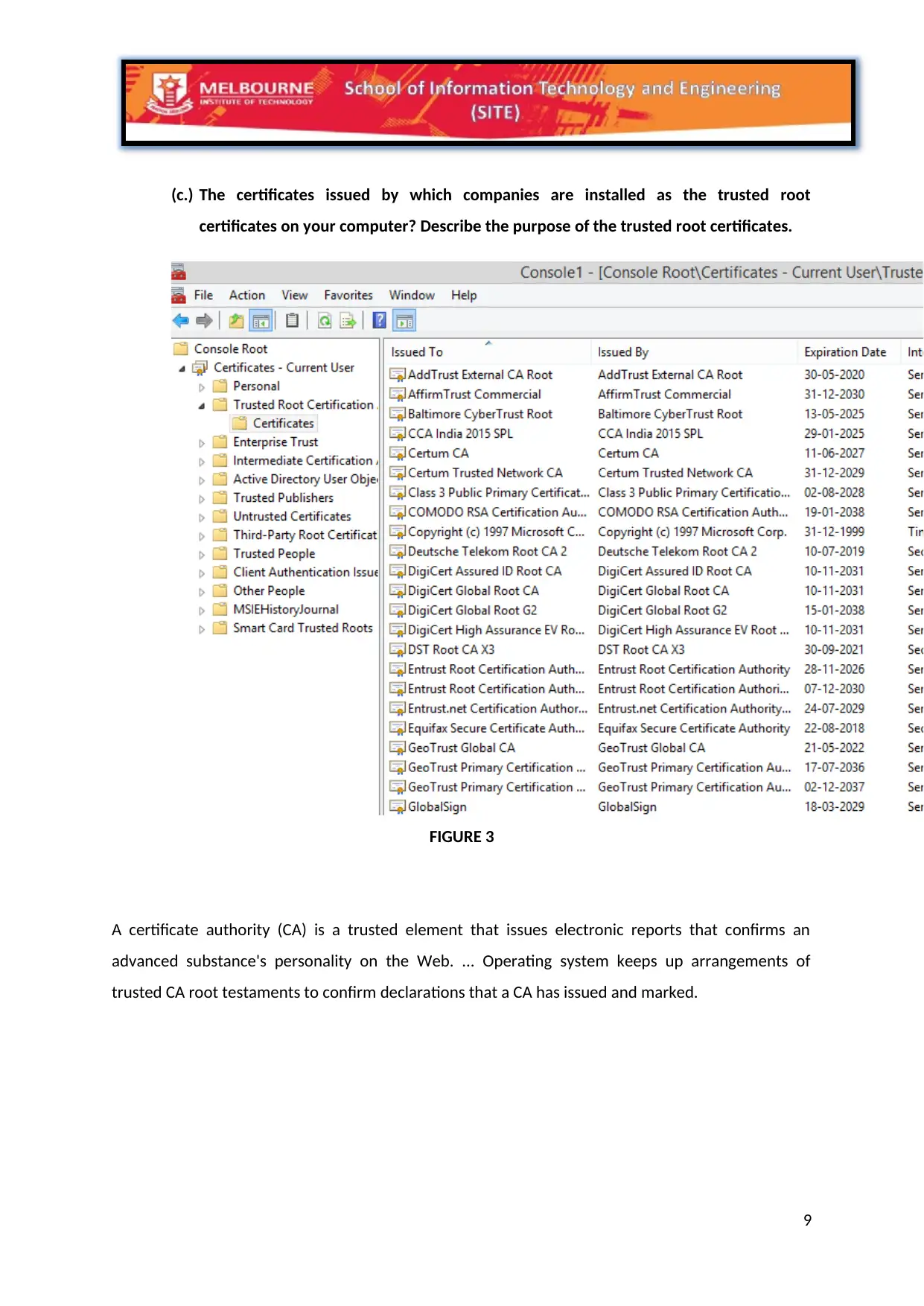
(c.) The certificates issued by which companies are installed as the trusted root
certificates on your computer? Describe the purpose of the trusted root certificates.
FIGURE 3
A certificate authority (CA) is a trusted element that issues electronic reports that confirms an
advanced substance's personality on the Web. ... Operating system keeps up arrangements of
trusted CA root testaments to confirm declarations that a CA has issued and marked.
9
certificates on your computer? Describe the purpose of the trusted root certificates.
FIGURE 3
A certificate authority (CA) is a trusted element that issues electronic reports that confirms an
advanced substance's personality on the Web. ... Operating system keeps up arrangements of
trusted CA root testaments to confirm declarations that a CA has issued and marked.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2. The confidentiality and the integrity services used for to secure the communication between
the server and the browser.
2.1 Analytical Tasks
(a.) How the server and the browser agree on which cipher suite to use?
Cipher suite is the specialized convention term that depicts the sort, size, and procedures
that are used when data (plaintext) is changed into "figure message", or encoded data. To
know how the server and the program agree on which figure suite to use, we need to get to
know SSL 2.0, SSL 3.0 and TLS 1.0 tradition. TLS 1.0 is the vehicle layer security and is the
latest variation of SSL 3.0. The program has each one of the traditions and estimations and
the server picks one of the traditions which have all the earmarks of being more secure, by
then it is used as a piece of that channel. Basically those traditions are picked by server that
is accessible in once-over of suitable traditions. If server does not find any sensible suite, the
association is rejected. [6]
(b.) How the server and the browser agree on the symmetrical secret key for the
encryption and hashing algorithms?
Symmetrical secret encryption is a sort of encryption in which just a single key is included
both for encryption and decoding of a message. To scramble the message utilizing this
calculation right off the bat figure suite is chosen called AES figure suite (more secure), at
that point the figure content is encoded. Accurately when the program and server do TLS
handshake, program makes a symmetric key and offer it to the server and all further
correspondence is occur through symmetric encryption. [7]
10
the server and the browser.
2.1 Analytical Tasks
(a.) How the server and the browser agree on which cipher suite to use?
Cipher suite is the specialized convention term that depicts the sort, size, and procedures
that are used when data (plaintext) is changed into "figure message", or encoded data. To
know how the server and the program agree on which figure suite to use, we need to get to
know SSL 2.0, SSL 3.0 and TLS 1.0 tradition. TLS 1.0 is the vehicle layer security and is the
latest variation of SSL 3.0. The program has each one of the traditions and estimations and
the server picks one of the traditions which have all the earmarks of being more secure, by
then it is used as a piece of that channel. Basically those traditions are picked by server that
is accessible in once-over of suitable traditions. If server does not find any sensible suite, the
association is rejected. [6]
(b.) How the server and the browser agree on the symmetrical secret key for the
encryption and hashing algorithms?
Symmetrical secret encryption is a sort of encryption in which just a single key is included
both for encryption and decoding of a message. To scramble the message utilizing this
calculation right off the bat figure suite is chosen called AES figure suite (more secure), at
that point the figure content is encoded. Accurately when the program and server do TLS
handshake, program makes a symmetric key and offer it to the server and all further
correspondence is occur through symmetric encryption. [7]
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
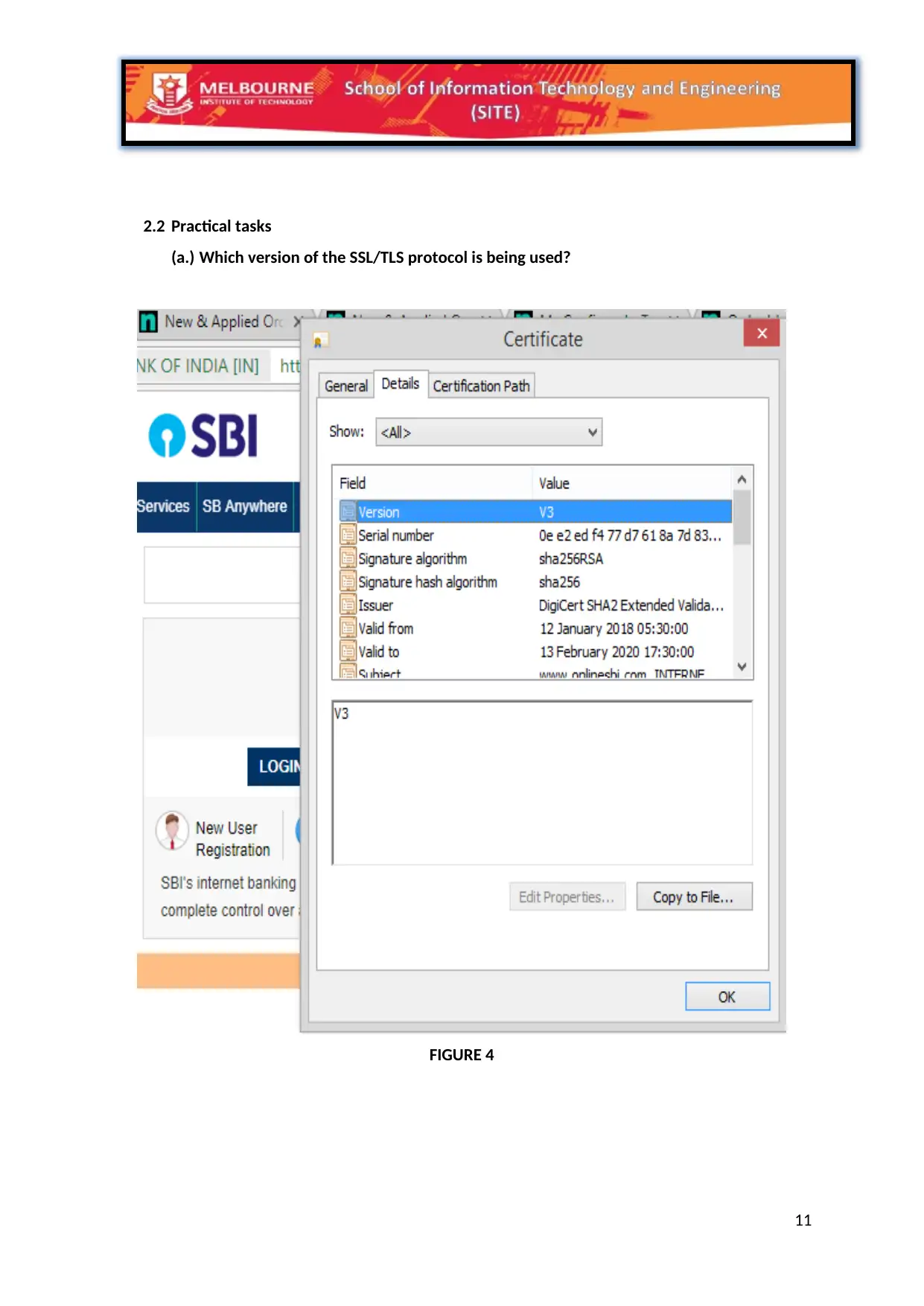
2.2 Practical tasks
(a.) Which version of the SSL/TLS protocol is being used?
FIGURE 4
11
(a.) Which version of the SSL/TLS protocol is being used?
FIGURE 4
11
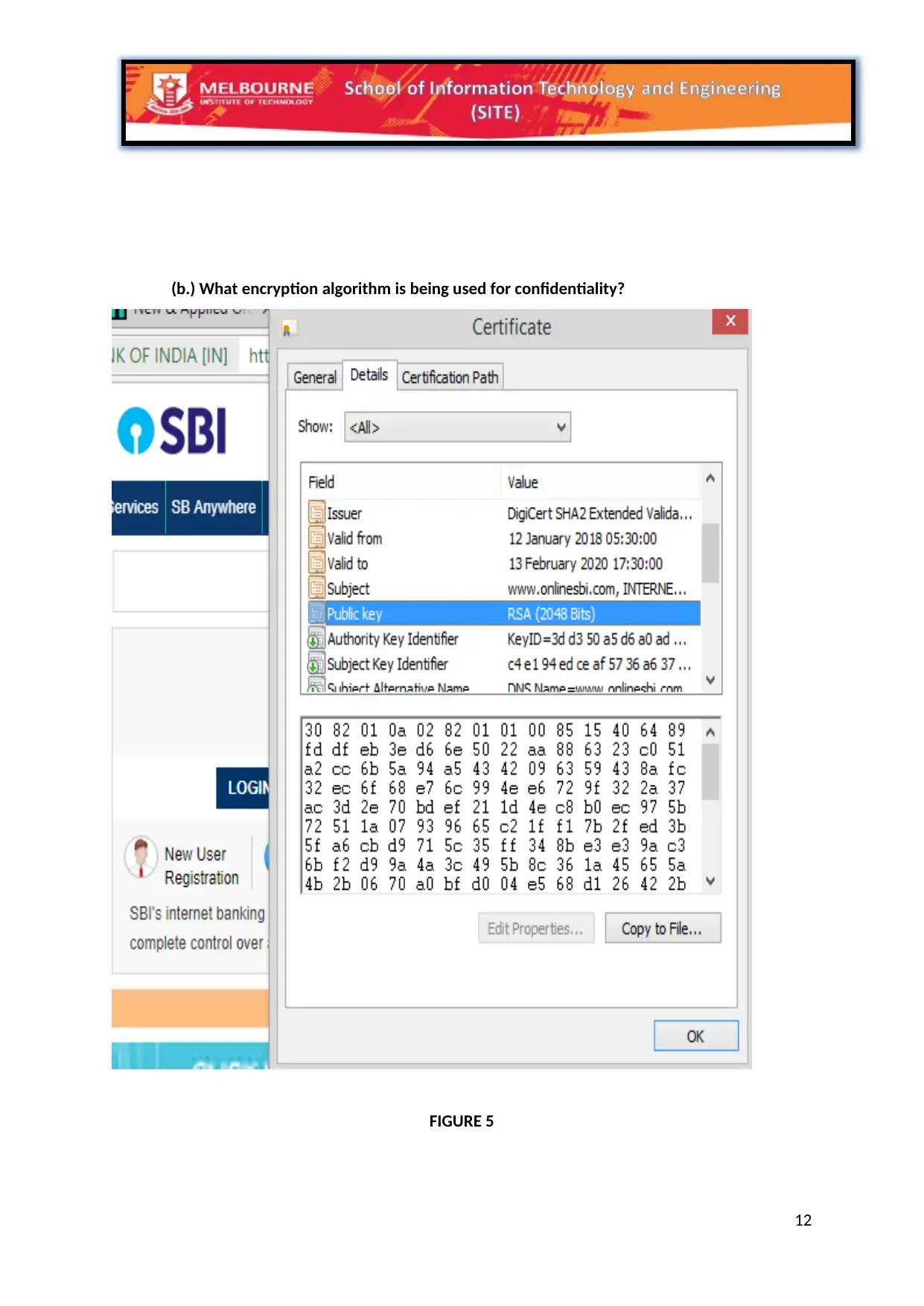
(b.) What encryption algorithm is being used for confidentiality?
FIGURE 5
12
FIGURE 5
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
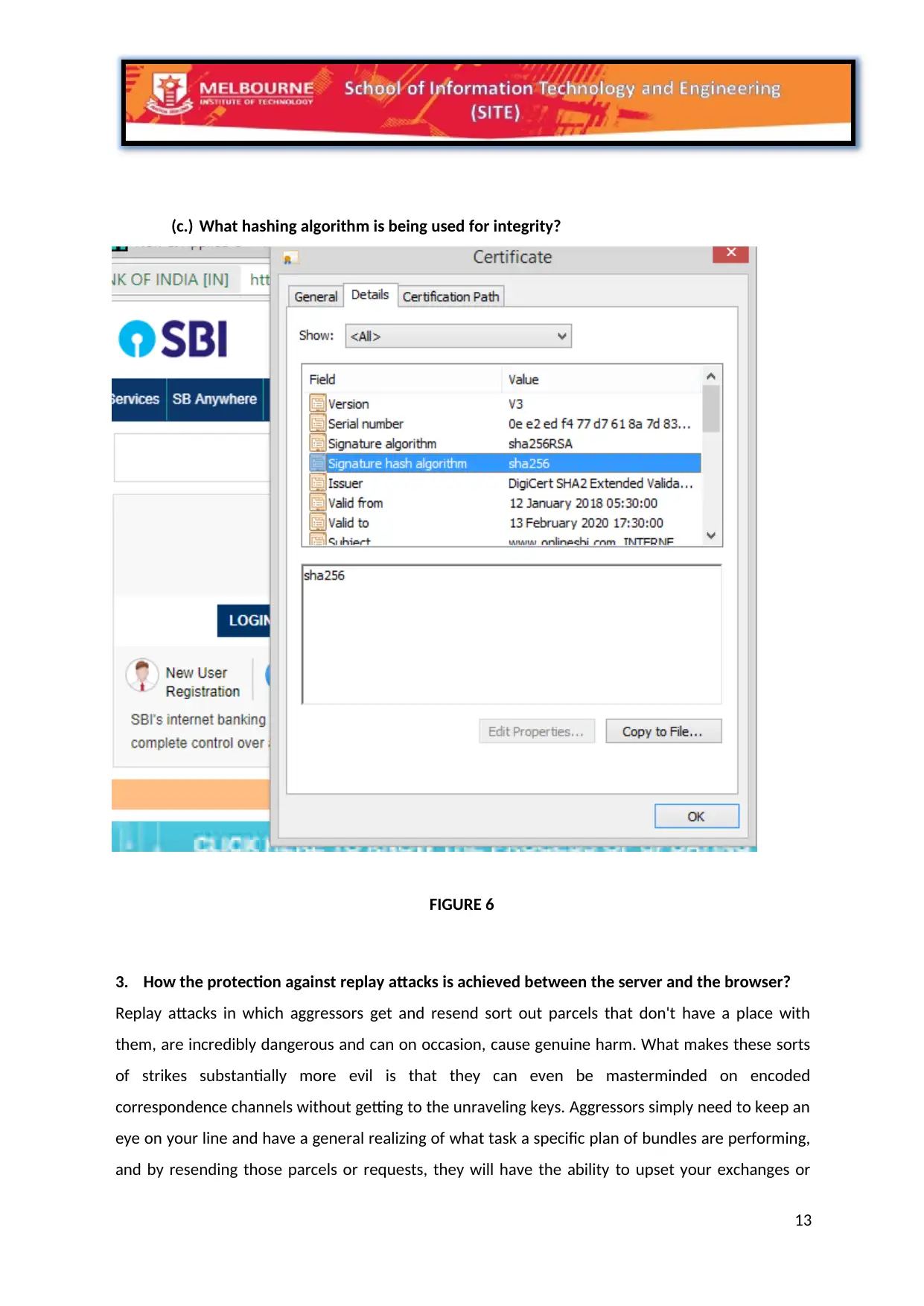
(c.) What hashing algorithm is being used for integrity?
FIGURE 6
3. How the protection against replay attacks is achieved between the server and the browser?
Replay attacks in which aggressors get and resend sort out parcels that don't have a place with
them, are incredibly dangerous and can on occasion, cause genuine harm. What makes these sorts
of strikes substantially more evil is that they can even be masterminded on encoded
correspondence channels without getting to the unraveling keys. Aggressors simply need to keep an
eye on your line and have a general realizing of what task a specific plan of bundles are performing,
and by resending those parcels or requests, they will have the ability to upset your exchanges or
13
FIGURE 6
3. How the protection against replay attacks is achieved between the server and the browser?
Replay attacks in which aggressors get and resend sort out parcels that don't have a place with
them, are incredibly dangerous and can on occasion, cause genuine harm. What makes these sorts
of strikes substantially more evil is that they can even be masterminded on encoded
correspondence channels without getting to the unraveling keys. Aggressors simply need to keep an
eye on your line and have a general realizing of what task a specific plan of bundles are performing,
and by resending those parcels or requests, they will have the ability to upset your exchanges or
13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

cause all the all the more hurting impacts. This replay assaults can be avoided by utilizing SSL/TLS
affirmations. SSL/TSL keeps the resending of bundles. Replay assault is furthermore thwarted by
using a one time password thought in which every HTTP response in settling to a token string which
will be authentic for next demand. [8]
Conclusion
VPN is a making headway that has increased huge ground. From a questionable detach of Phone
systems to a capable business help that uses the Web as its segment. VPN's headway is so far
making, and this is a remarkable favored position to affiliations especially keeping cash region,
which require improvement that can scale and make close-by them. Virtual private framework has
noteworthy security incorporates that is incredibly required in this amazing advanced world.
14
affirmations. SSL/TSL keeps the resending of bundles. Replay assault is furthermore thwarted by
using a one time password thought in which every HTTP response in settling to a token string which
will be authentic for next demand. [8]
Conclusion
VPN is a making headway that has increased huge ground. From a questionable detach of Phone
systems to a capable business help that uses the Web as its segment. VPN's headway is so far
making, and this is a remarkable favored position to affiliations especially keeping cash region,
which require improvement that can scale and make close-by them. Virtual private framework has
noteworthy security incorporates that is incredibly required in this amazing advanced world.
14

References
[1] k. Shetty. (2018). Virtual Private Network in Banking. [Online].
Available:http://www.streetdirectory.com/travel_guide/148471/technology/
virtual_private_network_in_banking.html
[2] Microsoft.com. (2008). What is a digital signature?. [Online].
Available:https://technet.microsoft.com/en-us/library/cc545901(v=office.12).aspx
[3] D.Shinder. (2001, August. 28). Understanding and selecting authentication methods.
[Online]. Available:https://www.techrepublic.com/article/understanding-and-selecting-
authentication-methods/
[4] Oracle.com. (2018). Authentication Methods. [Online].
Available:https://docs.oracle.com/cd/B19306_01/network.102/b14266/authmeth.htm#i1009722
[5] Anonymous, (2018). Understanding Authentication Methods. [Online].
Available:http://www.arubanetworks.com/techdocs/Instant_40_Mobile/Advanced/Content/
UG_files/Authentication/AuthenticationMethods.htm
[6] Microsoft.com. (2018). How to: View Certificates with the MMC Snap-in. [Online]. Available:
https://docs.microsoft.com/en-us/dotnet/framework/wcf/feature-details/how-to-view-certificates-
with-the-mmc-snap-in
[7] Microsoft.com. (2018). How to Determine the Cipher Suite for the Server and Client. [Online].
Available:https://support.microsoft.com/en-in/help/299520/how-to-determine-the-cipher-suite-for-
the-server-and-client
15
[1] k. Shetty. (2018). Virtual Private Network in Banking. [Online].
Available:http://www.streetdirectory.com/travel_guide/148471/technology/
virtual_private_network_in_banking.html
[2] Microsoft.com. (2008). What is a digital signature?. [Online].
Available:https://technet.microsoft.com/en-us/library/cc545901(v=office.12).aspx
[3] D.Shinder. (2001, August. 28). Understanding and selecting authentication methods.
[Online]. Available:https://www.techrepublic.com/article/understanding-and-selecting-
authentication-methods/
[4] Oracle.com. (2018). Authentication Methods. [Online].
Available:https://docs.oracle.com/cd/B19306_01/network.102/b14266/authmeth.htm#i1009722
[5] Anonymous, (2018). Understanding Authentication Methods. [Online].
Available:http://www.arubanetworks.com/techdocs/Instant_40_Mobile/Advanced/Content/
UG_files/Authentication/AuthenticationMethods.htm
[6] Microsoft.com. (2018). How to: View Certificates with the MMC Snap-in. [Online]. Available:
https://docs.microsoft.com/en-us/dotnet/framework/wcf/feature-details/how-to-view-certificates-
with-the-mmc-snap-in
[7] Microsoft.com. (2018). How to Determine the Cipher Suite for the Server and Client. [Online].
Available:https://support.microsoft.com/en-in/help/299520/how-to-determine-the-cipher-suite-for-
the-server-and-client
15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

[8] A.krauss. (2016, August. 11) How Public Key and Symmetric Key Encryption Work. [Online].
Available:https://thesocietea.org/2016/08/how-public-key-and-symmetric-key-encryption-work/
16
Available:https://thesocietea.org/2016/08/how-public-key-and-symmetric-key-encryption-work/
16
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





