Prevention of DoS Attacks: Methods and Strategies
Added on 2023-03-30
12 Pages2585 Words100 Views
Abstract
A DoS attack doesn't depend on a software on its malicious activities like virus or malware. Instead,
it studies the computer network structure and how it communicates before finally taking advantage
of inherited vulnerabilities. The attackers will just send simple messages especially in e-commerce
website asking the users to log in their accounts and when they do so the servers are shot down and
in that case the malicious activities are taking place. This types of spoofing are very common
nowadays but the users cannot easily recognized such messages because they are almost the same
as the real messages from the service providers (Wang, Sun, Han, & Ma, 2019). We should use the
technology or anti-DDos service to give use more secured environment of the working. This
services will help us identify between the legitimate network traffic and the DDoS attack. This
services will require a specialist because to handle it needs the understanding of the difference
between the real messages and the scam. The most important thing here is the to identify such
DDoS attacks so that we can know how to handle them (Reddy, Wing, & Patil, 2019).
Introduction
Firewalls and routers should be configured in a way that it will always reject the outside traffic. The
configurations should be done by security experts because this is a one way of securing the network
also from such spoofing. It is therefore advisable to use the latest version of the firewalls for the
more advanced security features found in such software. We should also be keeping updating the
software daily because the vendors keep on updating because of advancement of hackers also hence
they should be more secured and invulnerable to any attacks (Wang, Sun, Han, & Ma, 2019). An
IDS is a software application. It sends the alerts as soon as they receive suspicious threats on the
network traffic since the monitor closely all the network traffic of the system. This is the most
secured way of monitoring the threats but sometimes it may not be a perfect solution when it stands
alone. The more technology advances the more skills hackers will acquire. To ensure maximum
security in the network traffics the various methods should be employed. Network intrusion
detection system (NIDS) is an independent platforms which will examine network traffics and
monitor multiple hosts through intrusion process. This process happens by connecting intrusion
through network hub, switch among others. The sensors points to monitor demilitarized zone
(DMZ). It capture all the networks traffics and make sure it analyze the content of each individual
packets just to check malicious traffic (Wu, Wu, Liu, & Jiang, 2019).
1
A DoS attack doesn't depend on a software on its malicious activities like virus or malware. Instead,
it studies the computer network structure and how it communicates before finally taking advantage
of inherited vulnerabilities. The attackers will just send simple messages especially in e-commerce
website asking the users to log in their accounts and when they do so the servers are shot down and
in that case the malicious activities are taking place. This types of spoofing are very common
nowadays but the users cannot easily recognized such messages because they are almost the same
as the real messages from the service providers (Wang, Sun, Han, & Ma, 2019). We should use the
technology or anti-DDos service to give use more secured environment of the working. This
services will help us identify between the legitimate network traffic and the DDoS attack. This
services will require a specialist because to handle it needs the understanding of the difference
between the real messages and the scam. The most important thing here is the to identify such
DDoS attacks so that we can know how to handle them (Reddy, Wing, & Patil, 2019).
Introduction
Firewalls and routers should be configured in a way that it will always reject the outside traffic. The
configurations should be done by security experts because this is a one way of securing the network
also from such spoofing. It is therefore advisable to use the latest version of the firewalls for the
more advanced security features found in such software. We should also be keeping updating the
software daily because the vendors keep on updating because of advancement of hackers also hence
they should be more secured and invulnerable to any attacks (Wang, Sun, Han, & Ma, 2019). An
IDS is a software application. It sends the alerts as soon as they receive suspicious threats on the
network traffic since the monitor closely all the network traffic of the system. This is the most
secured way of monitoring the threats but sometimes it may not be a perfect solution when it stands
alone. The more technology advances the more skills hackers will acquire. To ensure maximum
security in the network traffics the various methods should be employed. Network intrusion
detection system (NIDS) is an independent platforms which will examine network traffics and
monitor multiple hosts through intrusion process. This process happens by connecting intrusion
through network hub, switch among others. The sensors points to monitor demilitarized zone
(DMZ). It capture all the networks traffics and make sure it analyze the content of each individual
packets just to check malicious traffic (Wu, Wu, Liu, & Jiang, 2019).
1

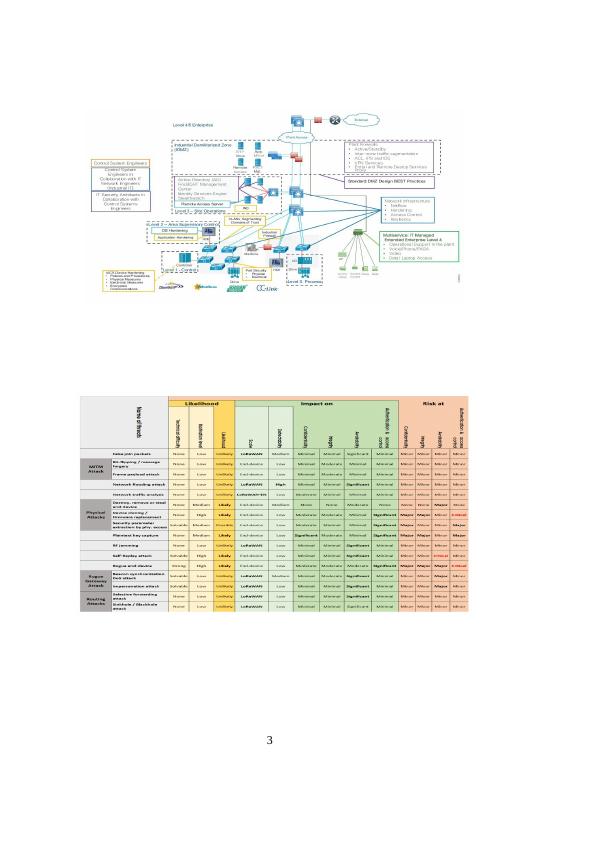
Denial of service attacks
A DoS "denial of service" attack is a process of trying to hold the website access resources so that
the users cannot be able to gain an access into such resources. In our scenario, DMZ might have
been exposed too much so the attackers will try to gain access into the web server hence causing
this trouble of the downtime in the website. A DoS attack doesn't depend on a software on its
malicious activities like virus or malware. Instead, it studies the computer network structure and
how it communicates before finally taking advantage of inherited vulnerabilities. Since there is DoS
attack on the web servers then the website is facing downtime which make the service delivery a bit
difficult and the customers wouldn't accept such issues. A DMZ from the vendor needs to be
upgraded to ensure security services are not compromised (Reddy, Wing, & Patil, 2019).
Denial of service attacks can happen in two forms such as:
1) Flooding attacks
This is the common form of attack which normally occurs when the system is attacked and all the
traffic in servers are affected hence cannot be handled. Ping flood is a DoS attacks which uses
technique of spoofing packets of informations in every computer in the targeted network. In our
case, ping spoofing will take advantage of the misconfigured networks devices of the customers
since this attack will try to send spoofing packets to the their computers and this will lead to the
information exposure of the customers. A SYN flood also will try and exploit the TCP
vulnerabilities of the connection sequence. It is normally refereed to as the three way handshake of
connection between the server and the host network. In this case, the target server receives a request
to start the handshake but through this SYN the handshake will not be completed. The connected
port will therefore be occupied and not available for more request from the users but in that process
the attackers are taking such advantage to send more requests hence the server is overworked and
this leads to the shut down. This attacks should be stopped immediately before it becomes the major
problem (Xu, Hu, Ho, & Feng, 2019).
2) Crash attacks
Crash attacks is the process which the attackers try to send the bugs which exploits packets flaws on
the systems of the targets but this attacks occurs less often. This leads to the system crashing hence
leading to the poor services delivery and hence disturbing the daily activities of the customers. All
this will lead to prevention of the legitimate users from accessing the online services such as
website services, emails and even bank account services. This attacks should be prevented as much
as possible to cover up the customers loyalty and the trust of the company (Wang, Sun, Han, & Ma,
2019).
In our case, the problem seems to be originating from the Remote Access Server. These servers are
only accessible by the vendors who connects the through the VPN so that they can offer the web
server services such as maintenance of the web application software. The securities on RAS should
be tighten to minimize this cases and also the vendor should work under the policies of the
company which governs the laws of the cyber crimes. In this case the vendor will be more careful
of the vulnerabilities which may cause such cyber crimes activities (Xu, Hu, Ho, & Feng, 2019).
2
A DoS "denial of service" attack is a process of trying to hold the website access resources so that
the users cannot be able to gain an access into such resources. In our scenario, DMZ might have
been exposed too much so the attackers will try to gain access into the web server hence causing
this trouble of the downtime in the website. A DoS attack doesn't depend on a software on its
malicious activities like virus or malware. Instead, it studies the computer network structure and
how it communicates before finally taking advantage of inherited vulnerabilities. Since there is DoS
attack on the web servers then the website is facing downtime which make the service delivery a bit
difficult and the customers wouldn't accept such issues. A DMZ from the vendor needs to be
upgraded to ensure security services are not compromised (Reddy, Wing, & Patil, 2019).
Denial of service attacks can happen in two forms such as:
1) Flooding attacks
This is the common form of attack which normally occurs when the system is attacked and all the
traffic in servers are affected hence cannot be handled. Ping flood is a DoS attacks which uses
technique of spoofing packets of informations in every computer in the targeted network. In our
case, ping spoofing will take advantage of the misconfigured networks devices of the customers
since this attack will try to send spoofing packets to the their computers and this will lead to the
information exposure of the customers. A SYN flood also will try and exploit the TCP
vulnerabilities of the connection sequence. It is normally refereed to as the three way handshake of
connection between the server and the host network. In this case, the target server receives a request
to start the handshake but through this SYN the handshake will not be completed. The connected
port will therefore be occupied and not available for more request from the users but in that process
the attackers are taking such advantage to send more requests hence the server is overworked and
this leads to the shut down. This attacks should be stopped immediately before it becomes the major
problem (Xu, Hu, Ho, & Feng, 2019).
2) Crash attacks
Crash attacks is the process which the attackers try to send the bugs which exploits packets flaws on
the systems of the targets but this attacks occurs less often. This leads to the system crashing hence
leading to the poor services delivery and hence disturbing the daily activities of the customers. All
this will lead to prevention of the legitimate users from accessing the online services such as
website services, emails and even bank account services. This attacks should be prevented as much
as possible to cover up the customers loyalty and the trust of the company (Wang, Sun, Han, & Ma,
2019).
In our case, the problem seems to be originating from the Remote Access Server. These servers are
only accessible by the vendors who connects the through the VPN so that they can offer the web
server services such as maintenance of the web application software. The securities on RAS should
be tighten to minimize this cases and also the vendor should work under the policies of the
company which governs the laws of the cyber crimes. In this case the vendor will be more careful
of the vulnerabilities which may cause such cyber crimes activities (Xu, Hu, Ho, & Feng, 2019).
2

3
Prevention of DoS attacks
A DoS attack doesn't depend on a software on its malicious activities like virus or malware. Instead,
it studies the computer network structure and how it communicates before finally taking advantage
of inherited vulnerabilities. The attackers will just send simple messages especially in e-commerce
website asking the users to log in their accounts and when they do so the servers are shot down and
in that case the malicious activities are taking place. This types of spoofing are very common
nowadays but the users cannot easily recognized such messages because they are almost the same
as the real messages from the service providers (Wang, Sun, Han, & Ma, 2019).
Methods of prevention
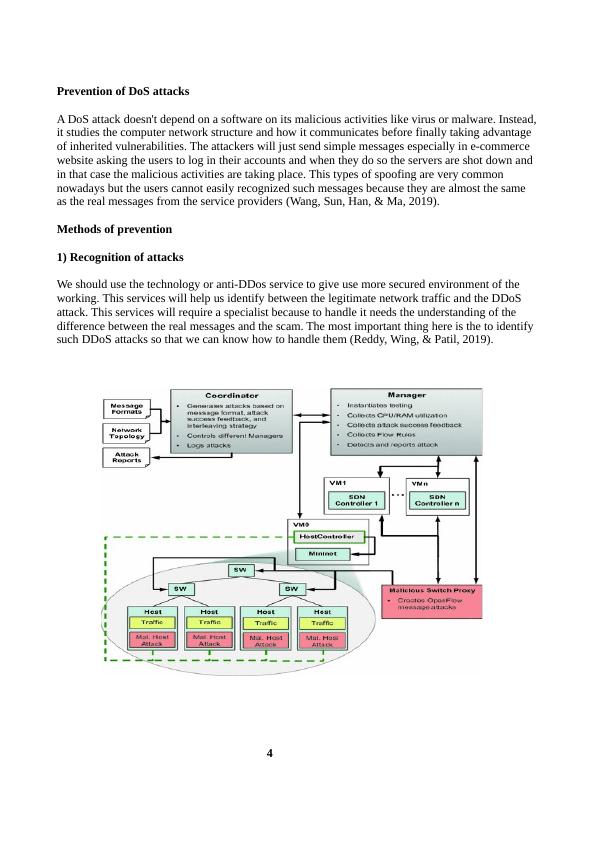
1) Recognition of attacks
We should use the technology or anti-DDos service to give use more secured environment of the
working. This services will help us identify between the legitimate network traffic and the DDoS
attack. This services will require a specialist because to handle it needs the understanding of the
difference between the real messages and the scam. The most important thing here is the to identify
such DDoS attacks so that we can know how to handle them (Reddy, Wing, & Patil, 2019).
4
A DoS attack doesn't depend on a software on its malicious activities like virus or malware. Instead,
it studies the computer network structure and how it communicates before finally taking advantage
of inherited vulnerabilities. The attackers will just send simple messages especially in e-commerce
website asking the users to log in their accounts and when they do so the servers are shot down and
in that case the malicious activities are taking place. This types of spoofing are very common
nowadays but the users cannot easily recognized such messages because they are almost the same
as the real messages from the service providers (Wang, Sun, Han, & Ma, 2019).
Methods of prevention
1) Recognition of attacks
We should use the technology or anti-DDos service to give use more secured environment of the
working. This services will help us identify between the legitimate network traffic and the DDoS
attack. This services will require a specialist because to handle it needs the understanding of the
difference between the real messages and the scam. The most important thing here is the to identify
such DDoS attacks so that we can know how to handle them (Reddy, Wing, & Patil, 2019).
4
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
IT Security: Types of Risks, Organizational Procedures, Impact of Firewall Configuration, Implementation of DMZ, Static IP and NATlg...
|18
|1181
|61
Mobile and Wireless Security: Issues, Threats, and Solutionslg...
|10
|615
|231
Network Addressing and Security - Deskliblg...
|5
|1385
|497
Security Awareness Program Issues 2022lg...
|4
|772
|13
DDOS attacklg...
|5
|1194
|491
IT Security Risks and Solutionslg...
|14
|3425
|60
