Assignment on Cloud Computing: its Types and Models
VerifiedAdded on 2022/05/09
|52
|11005
|22
AI Summary
Innovations brought into existence recently in the cloud computing sphere have caused a drastic evolution in the modus operandi of computing processes together with the notion and concept of computing resources. As an observer of the norm, resources are, more often than not, present in the jurisdiction of another entity’s network or premise, and cloud users could only gain access to said resources remotely
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

ABSTRACT
Innovations brought into existence of recent in the cloud computing sphere
have caused a drastic evolution in the modus operandi of computing
processes together with the notion and concept of computing resources. As
observer from the norm, resources are, more often than not, present in the
jurisdiction of another entity’s network or premise, and cloud users could only
gain access to said resources remotely.
In the cloud computing sphere, a myriad of varying sub-concepts have been
implemented over time; this however produced no alterations to the chief
notion upon which cloud computing is premised. The key concept of which
entails the presence of the cloud computing resources in the service
providers’ jurisdiction and control, which the cloud users or clients rent for use
for a certain time interval – often temporary, or in continuous stints.
The delivery models for the cloud computing architecture exist in three
subdivisions, including the Software as a service (SaaS), Infrastructure as a
service (IaaS) and the Platform as a service model (PaaS).
As the scope of cloud computing – and the business world alike – is
broadening ever rapidly across many fields, research focus should be
directed towards creating improvements in the technologies and processes
utilized in cloud security architecture.
This review seeks to discuss the security issues associated with cloud
computing and also examine the factors that are valuable and relevant in
ensuring that cloud services are safe and secure for deployment and use.
Keywords: Cloud Computing, Cloud Security, Cloud delivery models,
architecture and deployment models
Innovations brought into existence of recent in the cloud computing sphere
have caused a drastic evolution in the modus operandi of computing
processes together with the notion and concept of computing resources. As
observer from the norm, resources are, more often than not, present in the
jurisdiction of another entity’s network or premise, and cloud users could only
gain access to said resources remotely.
In the cloud computing sphere, a myriad of varying sub-concepts have been
implemented over time; this however produced no alterations to the chief
notion upon which cloud computing is premised. The key concept of which
entails the presence of the cloud computing resources in the service
providers’ jurisdiction and control, which the cloud users or clients rent for use
for a certain time interval – often temporary, or in continuous stints.
The delivery models for the cloud computing architecture exist in three
subdivisions, including the Software as a service (SaaS), Infrastructure as a
service (IaaS) and the Platform as a service model (PaaS).
As the scope of cloud computing – and the business world alike – is
broadening ever rapidly across many fields, research focus should be
directed towards creating improvements in the technologies and processes
utilized in cloud security architecture.
This review seeks to discuss the security issues associated with cloud
computing and also examine the factors that are valuable and relevant in
ensuring that cloud services are safe and secure for deployment and use.
Keywords: Cloud Computing, Cloud Security, Cloud delivery models,
architecture and deployment models
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TABLE OF CONTENTS
INTRODUCTION...............................................................................................3
TYPES OF CLOUD DELIVERY MODELS....................................................5
Infrastructure as a Service (IaaS)............................................................6
Platform as a Service (PaaS)...................................................................6
Software as a Service (SaaS)..................................................................7
TYPES OF CLOUD......................................................................................10
Public Cloud............................................................................................10
Private Cloud...........................................................................................11
Community cloud...................................................................................11
Hybrid Cloud...........................................................................................12
LITERATURE REVIEW..................................................................................18
DISCUSSION..................................................................................................32
CONCLUSION................................................................................................47
REFERENCES................................................................................................48
INTRODUCTION...............................................................................................3
TYPES OF CLOUD DELIVERY MODELS....................................................5
Infrastructure as a Service (IaaS)............................................................6
Platform as a Service (PaaS)...................................................................6
Software as a Service (SaaS)..................................................................7
TYPES OF CLOUD......................................................................................10
Public Cloud............................................................................................10
Private Cloud...........................................................................................11
Community cloud...................................................................................11
Hybrid Cloud...........................................................................................12
LITERATURE REVIEW..................................................................................18
DISCUSSION..................................................................................................32
CONCLUSION................................................................................................47
REFERENCES................................................................................................48

TABLE OF FIGURES
Figure 1. Types of Cloud Delivery Models....................................................9
Figure 2. Features of service delivery models...........................................10
Figure 3. Types of cloud deployment models............................................14
Figure 4. Service Level Agreement (SLA)..................................................16
Figure 5. Cloud Deployment Models with respect to Cloud Service
Requirements.................................................................................................40
Figure 6. How Authentication Works..........................................................47
Figure 1. Types of Cloud Delivery Models....................................................9
Figure 2. Features of service delivery models...........................................10
Figure 3. Types of cloud deployment models............................................14
Figure 4. Service Level Agreement (SLA)..................................................16
Figure 5. Cloud Deployment Models with respect to Cloud Service
Requirements.................................................................................................40
Figure 6. How Authentication Works..........................................................47

INTRODUCTION
Innovations brought into existence of recent in the cloud computing sphere
have caused a drastic evolution in the modus operandi of computing
processes together with the notion and concept of computing resources. As
observer from the norm, resources are, more often than not, present in the
jurisdiction of another entity’s network or premise, and cloud users could only
gain access to said resources remotely (Petre, 2012; Ogigau-Neamtiu, 2012;
Singh & jangwal, 2012).
Whatever processing to be carried out is done in a remote manner as well;
this alludes that it is imperative that the client submit their data to the cloud
server or infrastructure, in order for processing to be commenced upon it;
thereafter, the output is sent back, once the necessary processing is finalized.
In a number of scenarios, there is either a potentiality or prerequisite for the
user to store data on remote cloud servers. Arising from these, are delicate
cases that call for way-forwards to be devised strategically, within and around
the milieu of cloud computing operational activities. The cases in point are
underlisted thus: The transmission of clients’ individual credentials and
sensitive information to the server of the cloud; transmission of data from the
cloud infrastructure to the computing devices of the clients and as a
concluding procedure, the storage of the clients’ credentials and personal
Innovations brought into existence of recent in the cloud computing sphere
have caused a drastic evolution in the modus operandi of computing
processes together with the notion and concept of computing resources. As
observer from the norm, resources are, more often than not, present in the
jurisdiction of another entity’s network or premise, and cloud users could only
gain access to said resources remotely (Petre, 2012; Ogigau-Neamtiu, 2012;
Singh & jangwal, 2012).
Whatever processing to be carried out is done in a remote manner as well;
this alludes that it is imperative that the client submit their data to the cloud
server or infrastructure, in order for processing to be commenced upon it;
thereafter, the output is sent back, once the necessary processing is finalized.
In a number of scenarios, there is either a potentiality or prerequisite for the
user to store data on remote cloud servers. Arising from these, are delicate
cases that call for way-forwards to be devised strategically, within and around
the milieu of cloud computing operational activities. The cases in point are
underlisted thus: The transmission of clients’ individual credentials and
sensitive information to the server of the cloud; transmission of data from the
cloud infrastructure to the computing devices of the clients and as a
concluding procedure, the storage of the clients’ credentials and personal
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

information on the cloud servers, which exist as remote servers and implies
that the servers cannot be client-owned.
.
Each and every one of the three stages stated in the foregoing show a high
degree of susceptibility of sabotage in terms of security; to this end, it could
prove costly to downplay the significance of research and investigative
analysis when it comes to the security aspect of cloud computing. In the cloud
computing sphere, a myriad of varying sub-concepts have been implemented
over time; this however produced no alterations to the chief notion upon
which cloud computing is premised. The key concept of which entails the
presence of the cloud computing resources in the service providers’
jurisdiction and control, which the cloud users or clients rent for use for a
certain time interval – often temporary, or in continuous stints (Bisong &
Rahman, 2011; Rashmi, Sahoo & Mehfuz, 2013; Qaisar & Khawaja, 2012).
The stored precious data (on the remote cloud servers), in certain scenarios,
are required to be estimated, by counting. As long as the infringement upon
the privacy of clients’ computers by external parties is practicable, be it by
hacking or other illegitimate contrivance through which intruders grant
themselves unsolicited access to client personal data; uncertainties surface
with greater aplomb with regard to the security situation inasmuch as the
whole idea behind cloud computing and affiliated services were incited by a
that the servers cannot be client-owned.
.
Each and every one of the three stages stated in the foregoing show a high
degree of susceptibility of sabotage in terms of security; to this end, it could
prove costly to downplay the significance of research and investigative
analysis when it comes to the security aspect of cloud computing. In the cloud
computing sphere, a myriad of varying sub-concepts have been implemented
over time; this however produced no alterations to the chief notion upon
which cloud computing is premised. The key concept of which entails the
presence of the cloud computing resources in the service providers’
jurisdiction and control, which the cloud users or clients rent for use for a
certain time interval – often temporary, or in continuous stints (Bisong &
Rahman, 2011; Rashmi, Sahoo & Mehfuz, 2013; Qaisar & Khawaja, 2012).
The stored precious data (on the remote cloud servers), in certain scenarios,
are required to be estimated, by counting. As long as the infringement upon
the privacy of clients’ computers by external parties is practicable, be it by
hacking or other illegitimate contrivance through which intruders grant
themselves unsolicited access to client personal data; uncertainties surface
with greater aplomb with regard to the security situation inasmuch as the
whole idea behind cloud computing and affiliated services were incited by a

need to explore innovative avenues to access and have control over one’s
personal data.
Owing to the above, cloud computing activities have always had, and still
have quagmires with how security is handled in the sphere. In the computing
world, matters of security are always held preponderant.
The nature and methodology used in cloud computing makes it almost
impracticable for the broadness, and vastness of said ambit to be bridled, or
totally eliminated. A formidable system of security and safe infrastructure for
computing cannot be realized with a single, one off endeavor, as it demands
continuity; for this reason, it is of the essence to conduct proper analysis and
acknowledge advanced cloud computing security as a sine qua non. By the
operating standards of the cloud computing sphere, the cloud is segmented
into three groups/types, comprising of the public cloud, private cloud,
community cloud and hybrid cloud, as evidenced by a number of studies
(Ogigau-Neamtiu, 2012; Singh & Jangwal, 2012; Rashmi et al., 2013; Qaisar
& Khawaja, 2012; Kuyoro, Ibikunle & Awodele, 2011; Suresh & Prasad, 2012;
Youssef, 2012).
personal data.
Owing to the above, cloud computing activities have always had, and still
have quagmires with how security is handled in the sphere. In the computing
world, matters of security are always held preponderant.
The nature and methodology used in cloud computing makes it almost
impracticable for the broadness, and vastness of said ambit to be bridled, or
totally eliminated. A formidable system of security and safe infrastructure for
computing cannot be realized with a single, one off endeavor, as it demands
continuity; for this reason, it is of the essence to conduct proper analysis and
acknowledge advanced cloud computing security as a sine qua non. By the
operating standards of the cloud computing sphere, the cloud is segmented
into three groups/types, comprising of the public cloud, private cloud,
community cloud and hybrid cloud, as evidenced by a number of studies
(Ogigau-Neamtiu, 2012; Singh & Jangwal, 2012; Rashmi et al., 2013; Qaisar
& Khawaja, 2012; Kuyoro, Ibikunle & Awodele, 2011; Suresh & Prasad, 2012;
Youssef, 2012).

TYPES OF CLOUD DELIVERY MODELS
The delivery models for the cloud computing architecture exist in three
subdivisions, including the Software as a service (SaaS), Infrastructure as a
service (IaaS) and the Platform as a service models (PaaS).
Infrastructure as a Service (IaaS)
Here, in the Infrastructure as a Service model – abbreviated as IaaS –
computing resources used on the cloud, take processing power, data storage
and networks as instances, are made available in form of services. The cloud
services – virtualized and standardized, to a fault – are purchased by the
client, who then supplements the received service with services they already
have in possession, for use internally or externally. To explain this with an
instance, a cloud user could rent memory for operation, data storage as well
as server time, and in simultaneity with all of that, still run an operating
system using application programs they wish to.
Platform as a Service (PaaS)
In this service delivery model, the customer is availed infrastructure in its
entirety by the PaaS provider, who makes standardized interfaces which the
customer’s services would need to implement on the platform as well. The
platform could avail – for instance – scalability, multi-tenancy, access control,
and database accesses and the likes, as services. However, the client cannot
have direct access to the underlying strata, such as hardware or operating
The delivery models for the cloud computing architecture exist in three
subdivisions, including the Software as a service (SaaS), Infrastructure as a
service (IaaS) and the Platform as a service models (PaaS).
Infrastructure as a Service (IaaS)
Here, in the Infrastructure as a Service model – abbreviated as IaaS –
computing resources used on the cloud, take processing power, data storage
and networks as instances, are made available in form of services. The cloud
services – virtualized and standardized, to a fault – are purchased by the
client, who then supplements the received service with services they already
have in possession, for use internally or externally. To explain this with an
instance, a cloud user could rent memory for operation, data storage as well
as server time, and in simultaneity with all of that, still run an operating
system using application programs they wish to.
Platform as a Service (PaaS)
In this service delivery model, the customer is availed infrastructure in its
entirety by the PaaS provider, who makes standardized interfaces which the
customer’s services would need to implement on the platform as well. The
platform could avail – for instance – scalability, multi-tenancy, access control,
and database accesses and the likes, as services. However, the client cannot
have direct access to the underlying strata, such as hardware or operating
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

system; but it must be stated that application they opt for could be run on the
platform, for which the CSP would often provide its own tools.
Software as a Service (SaaS)
Here, as a software distribution model, the Software as a Service (SaaS)
model is characterized by application hosting by a service provider or vendor
and distributed to the clients across a network, typically the internet. As
underlying technologies compatible with web-based services and service
oriented (SOA) mature and unprecedented developmental approaches
continue to progress in popularity, so does the SaaS continue to become
more prevalent as delivery model by the day, in correspondence. What is
more, the Software as a Service model has, in many cases, been seen to be
affiliated with a pay-as-you-go subscription licensing model. On the other
hand, the rate at which broadband service is accessible to facilitate user
admittance proliferates and continues to reach more regions across the
globe. Many a time, the SaaS is applied in order to make provisions for the
functionality of business software, at lessened costs whilst, at the same time,
enabling the clients to reap whatever gains would have been gotten from
internally managed software with commercial license(s). The benefits would
be devoid of the complexities with which the management, support,
installation, high initial costs and licensing are originally accompanied. What
the concept of multi-tenancy alludes here, is the capacity of the SaaS’s
infrastructure to cater to a horde of users at the same point in time; it is
worthy of note that the infrastructure was specially fabricated to function in
platform, for which the CSP would often provide its own tools.
Software as a Service (SaaS)
Here, as a software distribution model, the Software as a Service (SaaS)
model is characterized by application hosting by a service provider or vendor
and distributed to the clients across a network, typically the internet. As
underlying technologies compatible with web-based services and service
oriented (SOA) mature and unprecedented developmental approaches
continue to progress in popularity, so does the SaaS continue to become
more prevalent as delivery model by the day, in correspondence. What is
more, the Software as a Service model has, in many cases, been seen to be
affiliated with a pay-as-you-go subscription licensing model. On the other
hand, the rate at which broadband service is accessible to facilitate user
admittance proliferates and continues to reach more regions across the
globe. Many a time, the SaaS is applied in order to make provisions for the
functionality of business software, at lessened costs whilst, at the same time,
enabling the clients to reap whatever gains would have been gotten from
internally managed software with commercial license(s). The benefits would
be devoid of the complexities with which the management, support,
installation, high initial costs and licensing are originally accompanied. What
the concept of multi-tenancy alludes here, is the capacity of the SaaS’s
infrastructure to cater to a horde of users at the same point in time; it is
worthy of note that the infrastructure was specially fabricated to function in
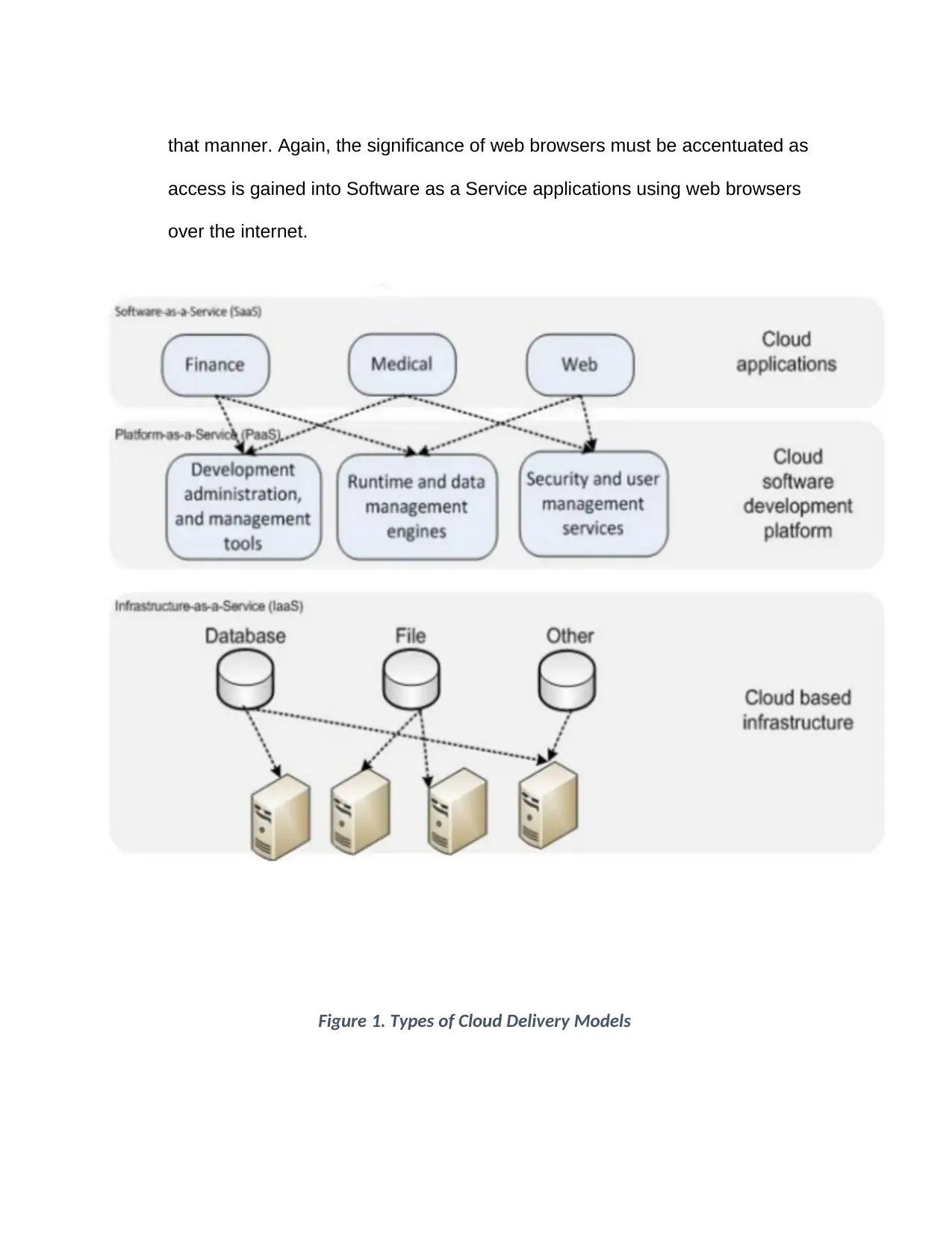
that manner. Again, the significance of web browsers must be accentuated as
access is gained into Software as a Service applications using web browsers
over the internet.
Figure 1. Types of Cloud Delivery Models
access is gained into Software as a Service applications using web browsers
over the internet.
Figure 1. Types of Cloud Delivery Models
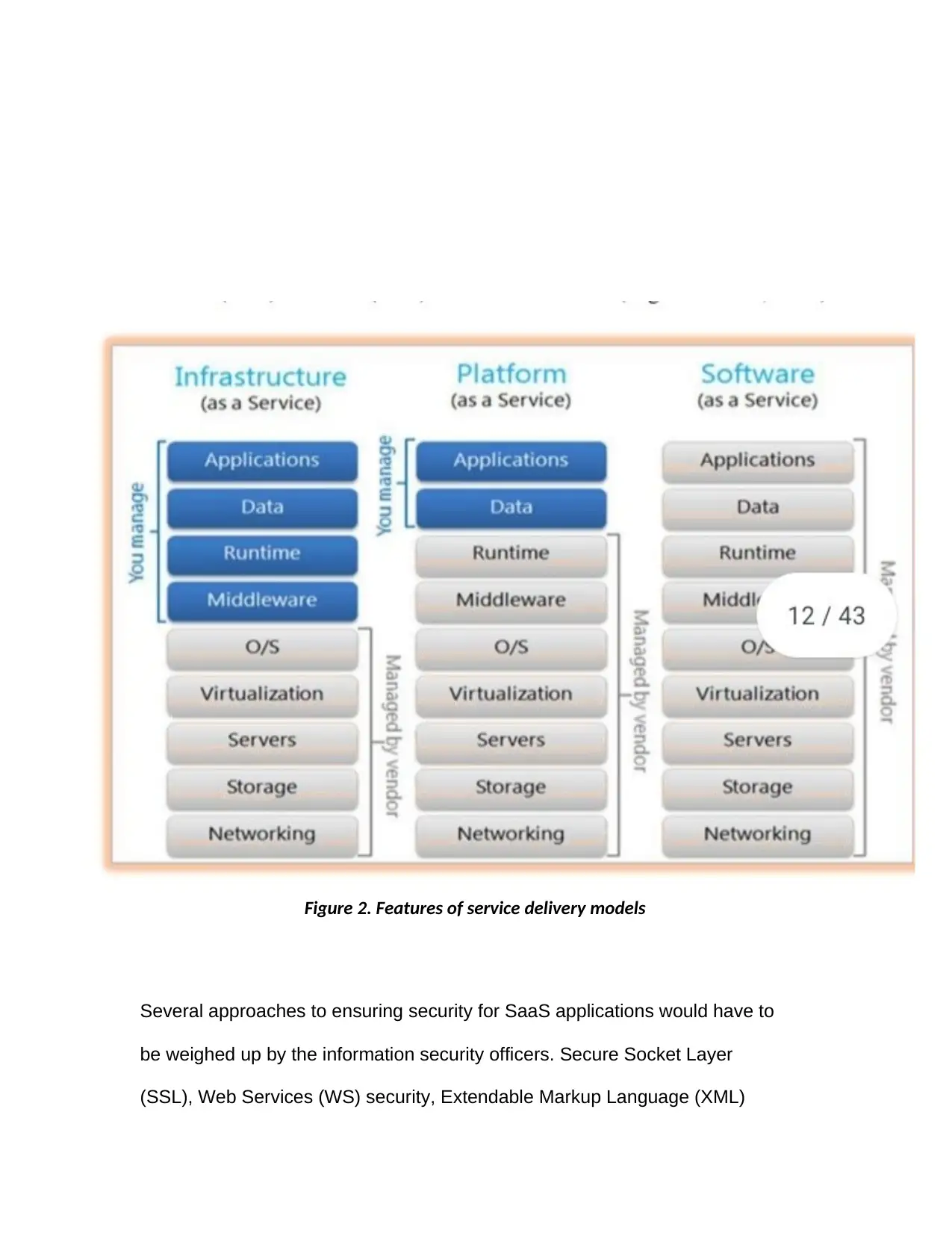
Several approaches to ensuring security for SaaS applications would have to
be weighed up by the information security officers. Secure Socket Layer
(SSL), Web Services (WS) security, Extendable Markup Language (XML)
Figure 2. Features of service delivery models
be weighed up by the information security officers. Secure Socket Layer
(SSL), Web Services (WS) security, Extendable Markup Language (XML)
Figure 2. Features of service delivery models
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

encryption and a vast array of alternatives available are used to protect data,
and create a secure network through which information is transmitted within
and about the internet, as stated by Subashini and Kavitha (2011). .
In every interface where it is necessary, the service providers for cloud
services, as well as the clients have to maintain security in the cloud
computing field.
TYPES OF CLOUD
On the basis of discrepancies as to the entity that gets admittance to the
services, who is in control of the infrastructure, the location of the
infrastructure and the manner with which it is made available; fundamentally,
there exist four deployment models for cloud computing (Woolley & Fletcher,
2009).
The elements listed in the foregoing possess separate, distinct properties,
that exert an influence on chances and uncertainties with which each and
every cloud development model is connected.
and create a secure network through which information is transmitted within
and about the internet, as stated by Subashini and Kavitha (2011). .
In every interface where it is necessary, the service providers for cloud
services, as well as the clients have to maintain security in the cloud
computing field.
TYPES OF CLOUD
On the basis of discrepancies as to the entity that gets admittance to the
services, who is in control of the infrastructure, the location of the
infrastructure and the manner with which it is made available; fundamentally,
there exist four deployment models for cloud computing (Woolley & Fletcher,
2009).
The elements listed in the foregoing possess separate, distinct properties,
that exert an influence on chances and uncertainties with which each and
every cloud development model is connected.

Public Cloud
Fundamentally, the major benefit of public cloud deployment model lies in its
capacity to offer cost efficiency to the user on the basis of management
overheads and capital expenditure. However, it is not without its downsides
as it also has risks affiliated with latency, performance, location and
ownership of data, data security and privacy attached to it as cons.
The infrastructure of this cloud is run solely for an organization. It could either
be superintended by the organization itself, or by a third party and may exist
and operate in an off-premise or on-premise form.
Private Cloud
Here, whether internal or third-party resources oriented, in the private cloud
deployment model, the control over organizational or personal information is
amplified; also, checks ingrained in architecture of this model cause a large
portion of the risks associated with the foregoing cloud deployment model to
be put in place, thus proffering solutions to the conundrums brought into
existence by said demerits.
It should be stated however, that the trade-offs come with greater costs for
renting or procuring sites, as well as managing the infrastructure upon which
the cloud runs (Kraska, 2010). In a similar manner with the model discussed
afore, the cloud infrastructure is run solely for an organization; it may be
presided over by the organization or a third party and has the capacity to run
either off-premise or on-premise.
Fundamentally, the major benefit of public cloud deployment model lies in its
capacity to offer cost efficiency to the user on the basis of management
overheads and capital expenditure. However, it is not without its downsides
as it also has risks affiliated with latency, performance, location and
ownership of data, data security and privacy attached to it as cons.
The infrastructure of this cloud is run solely for an organization. It could either
be superintended by the organization itself, or by a third party and may exist
and operate in an off-premise or on-premise form.
Private Cloud
Here, whether internal or third-party resources oriented, in the private cloud
deployment model, the control over organizational or personal information is
amplified; also, checks ingrained in architecture of this model cause a large
portion of the risks associated with the foregoing cloud deployment model to
be put in place, thus proffering solutions to the conundrums brought into
existence by said demerits.
It should be stated however, that the trade-offs come with greater costs for
renting or procuring sites, as well as managing the infrastructure upon which
the cloud runs (Kraska, 2010). In a similar manner with the model discussed
afore, the cloud infrastructure is run solely for an organization; it may be
presided over by the organization or a third party and has the capacity to run
either off-premise or on-premise.

Community cloud
In a community cloud deployment model, several organizations having similar
intentions or goals in the aspects of delicacy or discreetness of data to be
stored or processed and/or prerequisites for security, coalesce to share a
private cloud. The major schema behind the conception of this model, is to
exploit majority of the security benefits associated with a private cloud,
coupled with the key economic advantages a public cloud has to offer.
A case in point of the community cloud can be drawn from the activity in
which various, separate agencies of a government share a private cloud.
Hybrid Cloud
Existing within the confines of a secure network, a hybrid cloud is also a sub-
type of the private cloud which is connected to one or more external cloud
services, controlled at a central level, and provisioned as a single unit (Global
Netopex Incorporated, 2009).
By way of an amalgamation of private and public cloud models, the hybrid
cloud proffers virtual IT solutions. Hybrid clouds take the security and control
over data and applications up a couple of notches, amplifies it; also allowing
multiple, several parties to gain access to information within and about the
internet space. In addition to the above, the hybrid cloud comes with an open
architecture that enables or supports interfaces with other management
systems.
In a community cloud deployment model, several organizations having similar
intentions or goals in the aspects of delicacy or discreetness of data to be
stored or processed and/or prerequisites for security, coalesce to share a
private cloud. The major schema behind the conception of this model, is to
exploit majority of the security benefits associated with a private cloud,
coupled with the key economic advantages a public cloud has to offer.
A case in point of the community cloud can be drawn from the activity in
which various, separate agencies of a government share a private cloud.
Hybrid Cloud
Existing within the confines of a secure network, a hybrid cloud is also a sub-
type of the private cloud which is connected to one or more external cloud
services, controlled at a central level, and provisioned as a single unit (Global
Netopex Incorporated, 2009).
By way of an amalgamation of private and public cloud models, the hybrid
cloud proffers virtual IT solutions. Hybrid clouds take the security and control
over data and applications up a couple of notches, amplifies it; also allowing
multiple, several parties to gain access to information within and about the
internet space. In addition to the above, the hybrid cloud comes with an open
architecture that enables or supports interfaces with other management
systems.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Given the fact that cloud computing resources are put out as services, a client
or cloud customer could thus apply the information security metrics via a
Service Level Agreement (SLA). The Service Level Agreement is the result of
a legal consensus reached between the customer and a service provider and
exists as the major framework with which the services made available on the
cloud are superintended and controlled (Jansen & Grance, 2011). Hence, the
SLA metrics are applied to evaluate the service level in place between a
Figure 3. Types of cloud deployment models
or cloud customer could thus apply the information security metrics via a
Service Level Agreement (SLA). The Service Level Agreement is the result of
a legal consensus reached between the customer and a service provider and
exists as the major framework with which the services made available on the
cloud are superintended and controlled (Jansen & Grance, 2011). Hence, the
SLA metrics are applied to evaluate the service level in place between a
Figure 3. Types of cloud deployment models

vendor of cloud-based services and its customers, and function as a medium
with which the rendered services can be bettered (Jansen & Grance, 2011).
Having said that, the general movement observed in the existing cloud SLAs
is centered majorly on the measurement of performance, rather than the
metrics of security which should be held paramount. Instances of such SLAs
would include but not limited to the GoGrid SLA (ENISA, 2009). Information
security risks is one out of the myriad of issues that preclude an organization
from taking up the cloSL computing (NIST, 2009) (Subashini & Kavitha,
2011). Be that as it may, this has not sparked any form of evolution as cloud
providers have failed to see to this issue (NIST, 2009) (Subashini & Kavitha,
2011).
OBJECTIVES
To discuss means to amplify and consolidate the security of
information in the cloud computing sphere.
To evaluate the threats and risks posed toward the client or
service providers of the cloud services
with which the rendered services can be bettered (Jansen & Grance, 2011).
Having said that, the general movement observed in the existing cloud SLAs
is centered majorly on the measurement of performance, rather than the
metrics of security which should be held paramount. Instances of such SLAs
would include but not limited to the GoGrid SLA (ENISA, 2009). Information
security risks is one out of the myriad of issues that preclude an organization
from taking up the cloSL computing (NIST, 2009) (Subashini & Kavitha,
2011). Be that as it may, this has not sparked any form of evolution as cloud
providers have failed to see to this issue (NIST, 2009) (Subashini & Kavitha,
2011).
OBJECTIVES
To discuss means to amplify and consolidate the security of
information in the cloud computing sphere.
To evaluate the threats and risks posed toward the client or
service providers of the cloud services
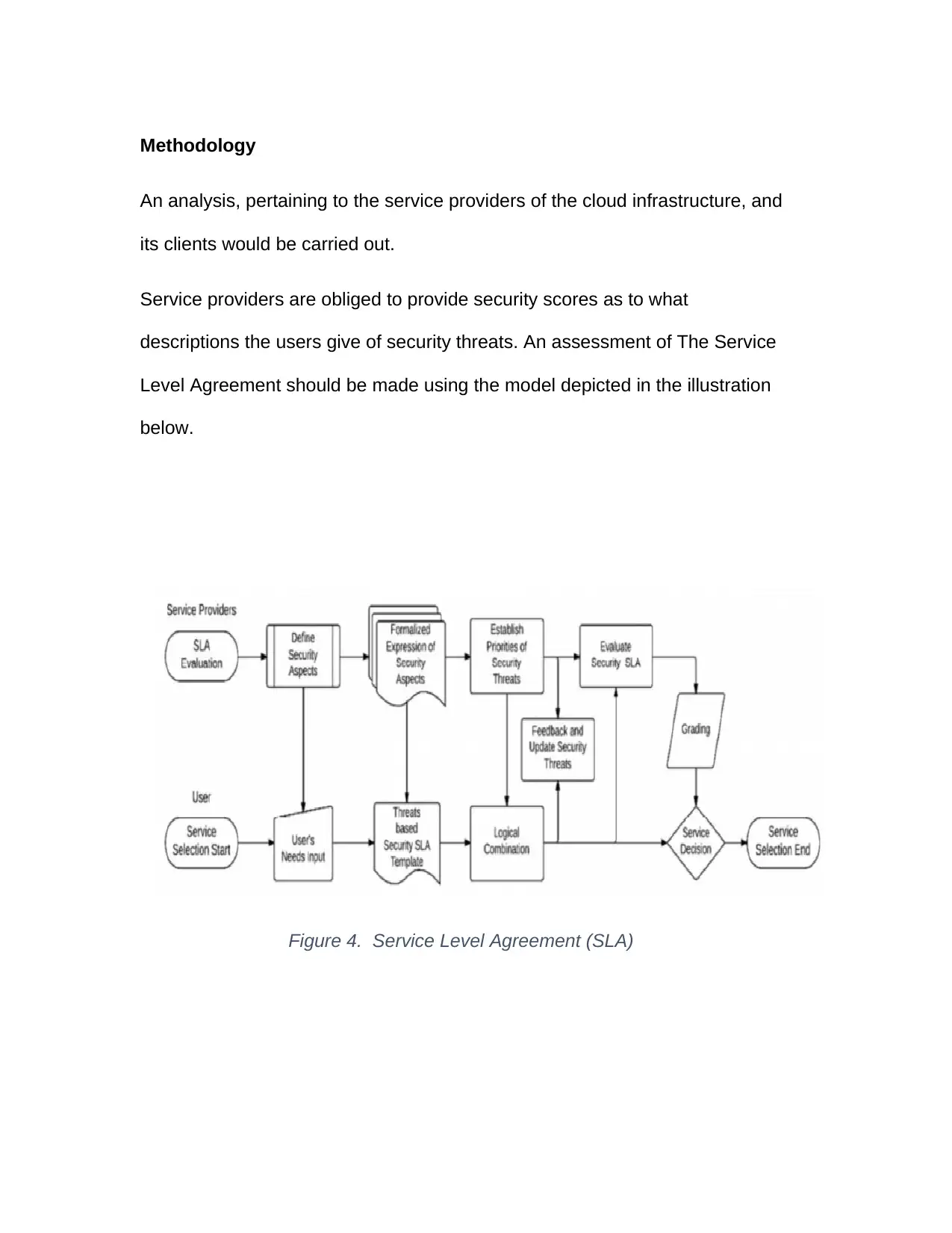
Methodology
An analysis, pertaining to the service providers of the cloud infrastructure, and
its clients would be carried out.
Service providers are obliged to provide security scores as to what
descriptions the users give of security threats. An assessment of The Service
Level Agreement should be made using the model depicted in the illustration
below.
Figure 4. Service Level Agreement (SLA)
An analysis, pertaining to the service providers of the cloud infrastructure, and
its clients would be carried out.
Service providers are obliged to provide security scores as to what
descriptions the users give of security threats. An assessment of The Service
Level Agreement should be made using the model depicted in the illustration
below.
Figure 4. Service Level Agreement (SLA)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

However, it is imperative that the vendors of cloud services clearly define
security aspects for the agreements, and start to devise a course of action
thorough which the agreements reached would be formalized. The reason for
this (formalization) is to eliminate all forms of uncertainty that could arise as a
consequence of varying definitions of the Service level agreements.
It is possible for users to draw answers from a threat-based service level
agreement format to give forth security aspects assured by each cloud
service provider. Local weight-gauges are attached to requirements
pertaining to security, in an attempt to analyze prospective threats posed, by
service providers.
In this study however, a qualitative research method was used; with data
extracted from several articles, journals, papers. The papers used in the
course of this study were sourced for using terms and phrases such as cloud,
cloud computing, security in cloud computing, cloud security architecture,
SLA (service level agreement) and suchlike.
This review seeks to discuss the security issues associated with cloud
computing and also examine the factors that are valuable and relevant in
ensuring that cloud services are safe and secure for deployment and use.
security aspects for the agreements, and start to devise a course of action
thorough which the agreements reached would be formalized. The reason for
this (formalization) is to eliminate all forms of uncertainty that could arise as a
consequence of varying definitions of the Service level agreements.
It is possible for users to draw answers from a threat-based service level
agreement format to give forth security aspects assured by each cloud
service provider. Local weight-gauges are attached to requirements
pertaining to security, in an attempt to analyze prospective threats posed, by
service providers.
In this study however, a qualitative research method was used; with data
extracted from several articles, journals, papers. The papers used in the
course of this study were sourced for using terms and phrases such as cloud,
cloud computing, security in cloud computing, cloud security architecture,
SLA (service level agreement) and suchlike.
This review seeks to discuss the security issues associated with cloud
computing and also examine the factors that are valuable and relevant in
ensuring that cloud services are safe and secure for deployment and use.

LITERATURE REVIEW
In a 2010 study, Shen et al conducted an analysis of the preconditions
necessary in the field of security services for cloud computing. Propositions to
create solutions for the cloud services and develop an archetypal model of
cloud, using a trust based platform as the foundation of the structure. The
said model amalgamates the cloud services employed in a Trusted
Computing Platform (TCP) and that of the Trusted Platform Services (TSS)
whose whole structure is premised on trust component/module. The
emergence and evolution had grown with rapidity in the past few years; this is
down to the wealth of facilities and comparative advantages to the
organizations and end users it has in at its disposal. A large number of
security factors have recorded substantial growth within this period, as a
result of the rapid development of the cloud and related services across the IT
sphere. Numerous security models, and approaches to seal trust have been
deployed and are being implemented to facilitate the strengthening of data
security, most particularly in hierarchy of sensitivity and privacy.
In a 2010 study, Shen et al conducted an analysis of the preconditions
necessary in the field of security services for cloud computing. Propositions to
create solutions for the cloud services and develop an archetypal model of
cloud, using a trust based platform as the foundation of the structure. The
said model amalgamates the cloud services employed in a Trusted
Computing Platform (TCP) and that of the Trusted Platform Services (TSS)
whose whole structure is premised on trust component/module. The
emergence and evolution had grown with rapidity in the past few years; this is
down to the wealth of facilities and comparative advantages to the
organizations and end users it has in at its disposal. A large number of
security factors have recorded substantial growth within this period, as a
result of the rapid development of the cloud and related services across the IT
sphere. Numerous security models, and approaches to seal trust have been
deployed and are being implemented to facilitate the strengthening of data
security, most particularly in hierarchy of sensitivity and privacy.

In spite of the formidability of security in place, a substantial portion of models
and methodologies fall short in certain aspects pertaining to measures taken
to thwart threats to the cloud.
Neisse et al (2011) centered their study around a paradigmatic system of
cloud computing that supports review, and mandates the concept of focused
reliability dimensions, and distant crucial points of reference as regards
attestation for cloud organizations. Here, the authors construct a model that
should be employed for the Ven platform of cloud computing and in addition
to that, reliable/trusted technologies whose sole function is to ensure security
within and about the cloud environment. In this framework, a synopsis of the
several interwoven cases of separate attacks is conducted, so as to draw
inferences that cloud computing is majorly premised upon the notion of trust.
The model established by the authors comes with a lot of advantages.
Judging from the perspective of scalability and economy, to start with, it can
be inferred that this very framework avails supplementary, trust-oriented
services for cloud computing. It is designed in such a way that it comprises
multiple strata in the mold of cloud computing model, design, security
performance, and implementation. The Xen platform is utilized for the cloud
model. The conceptualization of the model’s design exists as an embodiment
of the effective functionalities of physical hosting service on the narrow level,
and gives a rundown of history for storage. The authors have applied certain
practical methodologies such as trusted boot, attestation constellation, tamper
detection, and integrity management systems. The proposed framework is
and methodologies fall short in certain aspects pertaining to measures taken
to thwart threats to the cloud.
Neisse et al (2011) centered their study around a paradigmatic system of
cloud computing that supports review, and mandates the concept of focused
reliability dimensions, and distant crucial points of reference as regards
attestation for cloud organizations. Here, the authors construct a model that
should be employed for the Ven platform of cloud computing and in addition
to that, reliable/trusted technologies whose sole function is to ensure security
within and about the cloud environment. In this framework, a synopsis of the
several interwoven cases of separate attacks is conducted, so as to draw
inferences that cloud computing is majorly premised upon the notion of trust.
The model established by the authors comes with a lot of advantages.
Judging from the perspective of scalability and economy, to start with, it can
be inferred that this very framework avails supplementary, trust-oriented
services for cloud computing. It is designed in such a way that it comprises
multiple strata in the mold of cloud computing model, design, security
performance, and implementation. The Xen platform is utilized for the cloud
model. The conceptualization of the model’s design exists as an embodiment
of the effective functionalities of physical hosting service on the narrow level,
and gives a rundown of history for storage. The authors have applied certain
practical methodologies such as trusted boot, attestation constellation, tamper
detection, and integrity management systems. The proposed framework is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

secured to the maximum, and could be trusted to an corresponding degree; it
ensures the security of data stored in whatever form, be it in folders, reports
and fields. Should a DoS command attack occur, overloading of the system
should be avoided. Here in this study, the authors put forth a prospective
means to remedy cases of malicious intent towards customers who employ
the services of the cloud. Also, the authors keep close tabs on the integrity of
data and files stored on the Xen cloud platform. Key factors that would
determine if the cloud environment would continue to thrive and expand are
the safety of data stored on the cloud, privacy and trust; with these in their
apposite conditions, it is most likely for the cloud services to be adopted to a
greater extent and the whole horizon broadened as a consequence.
Yeluri et al (2012), conducted an investigative study to have an insight into
cloud services with respect to the aspect of security, and inquire into the main
encumbrances that security is faced with in the cloud environment, especially
when it involved the deployment of cloud services.
The authors addressed issues pertaining to the software vendors, and
hardware security in the course of this research, in an endeavor to augment
the hold on cloud services. Yeluri et al utilized the employment of Intel TXT
hardware platform for the validation of secure and reliable cloud computing
services as a case study. A solution for cloud computing security
shortcomings was suggested by the authors, as well as propositions for an
hardware root of trusted computing chain. The structure employed in this
ensures the security of data stored in whatever form, be it in folders, reports
and fields. Should a DoS command attack occur, overloading of the system
should be avoided. Here in this study, the authors put forth a prospective
means to remedy cases of malicious intent towards customers who employ
the services of the cloud. Also, the authors keep close tabs on the integrity of
data and files stored on the Xen cloud platform. Key factors that would
determine if the cloud environment would continue to thrive and expand are
the safety of data stored on the cloud, privacy and trust; with these in their
apposite conditions, it is most likely for the cloud services to be adopted to a
greater extent and the whole horizon broadened as a consequence.
Yeluri et al (2012), conducted an investigative study to have an insight into
cloud services with respect to the aspect of security, and inquire into the main
encumbrances that security is faced with in the cloud environment, especially
when it involved the deployment of cloud services.
The authors addressed issues pertaining to the software vendors, and
hardware security in the course of this research, in an endeavor to augment
the hold on cloud services. Yeluri et al utilized the employment of Intel TXT
hardware platform for the validation of secure and reliable cloud computing
services as a case study. A solution for cloud computing security
shortcomings was suggested by the authors, as well as propositions for an
hardware root of trusted computing chain. The structure employed in this

model is premised upon the three core services of the cloud. In the study, the
authors elucidated on cardinal elements that function as impetuses in the
aspect of cloud security, they are: data recovery and management, identity
management, visibility, trust, assurance and application architecture and
security in cloud confidentiality. A trusted computing concatenation created
for the function of protecting cloud data from untrusted software was used in
this study. Placed under protection from dangerous virtual machines, the
projected solution employed trusted computer pools and remote attestation.
The authors’ suggested framework would aid in guaranteeing the security of
cloud computing and affiliated services it comes with; therefore, building trust
to a great degree.
Behl (2011) conducted a study, with particular focus on cloud architecture and
its milieu; the author also discussed approaches with which the incompetency
and flaws in the cloud architecture could be remedied, or palliated. How the
concept of grid computing, as a whole, is perceived today has been altered
since the inception of cloud computing; emerging into prominence with an
innovative contrivance of data distribution – cloud computing, that is. The
researcher, in this study, projected a possible solution for the issues with
which security in cloud computing is plagued, along with methodologies to
solve the conundrums of security concerns, complex distributed computing,
security strategy, concerns and impediments to the whole scheme that is
being devised for the palliation or solving of the security issues. The
encumbrances talked about by the author include data loss, insider threats,
authors elucidated on cardinal elements that function as impetuses in the
aspect of cloud security, they are: data recovery and management, identity
management, visibility, trust, assurance and application architecture and
security in cloud confidentiality. A trusted computing concatenation created
for the function of protecting cloud data from untrusted software was used in
this study. Placed under protection from dangerous virtual machines, the
projected solution employed trusted computer pools and remote attestation.
The authors’ suggested framework would aid in guaranteeing the security of
cloud computing and affiliated services it comes with; therefore, building trust
to a great degree.
Behl (2011) conducted a study, with particular focus on cloud architecture and
its milieu; the author also discussed approaches with which the incompetency
and flaws in the cloud architecture could be remedied, or palliated. How the
concept of grid computing, as a whole, is perceived today has been altered
since the inception of cloud computing; emerging into prominence with an
innovative contrivance of data distribution – cloud computing, that is. The
researcher, in this study, projected a possible solution for the issues with
which security in cloud computing is plagued, along with methodologies to
solve the conundrums of security concerns, complex distributed computing,
security strategy, concerns and impediments to the whole scheme that is
being devised for the palliation or solving of the security issues. The
encumbrances talked about by the author include data loss, insider threats,

service disruption, external attacks with malicious intent, multi-tenancy
problems. Inasmuch as there exists an ample of problems to be dealt with in
the world of cloud computing, the author merely looks to assuage the
problems (relating to cloud security) laid out in the foregoing, with proposed
solutions. This research develops an expansive, well detailed schema to
tackle the some of the issues in cloud security.
Chen et al (n.d.) conducted an analytical research which was focalized in
confidentiality, and sensitivity of data, in conjunction with security problems
plaguing cloud architecture and environment; the study encompasses the all
the stages of which the life cycle of data is comprised. The authors, in the
research, lucubrate on the conceptual issues of data security, privacy
protection, data segregation, cloud security and cloud computing. An
evaluation of the aforesaid dilemmas was carried out, and potential solutions
for the resolution of the issues put forward by the researchers.
Fundamentally, these subjects exist at the SPI (PaaS, SaaS and IaaS) phase,
and the main hurdle to scale here is sharing of data. Subsequent to the
analysis of data security and privacy, the logical comprehensive solution to be
inferred is to cater to what is required in the procedures of isolation and
identification of data; this is the principal undertaking to be accomplished at
the design phase of cloud applications, according to Chen et al (n.d.).
In line with the research of Sulochana and Parimelazhagan (2013), cloud
computing functions as some sort of medium, with which a vast ambit of
problems. Inasmuch as there exists an ample of problems to be dealt with in
the world of cloud computing, the author merely looks to assuage the
problems (relating to cloud security) laid out in the foregoing, with proposed
solutions. This research develops an expansive, well detailed schema to
tackle the some of the issues in cloud security.
Chen et al (n.d.) conducted an analytical research which was focalized in
confidentiality, and sensitivity of data, in conjunction with security problems
plaguing cloud architecture and environment; the study encompasses the all
the stages of which the life cycle of data is comprised. The authors, in the
research, lucubrate on the conceptual issues of data security, privacy
protection, data segregation, cloud security and cloud computing. An
evaluation of the aforesaid dilemmas was carried out, and potential solutions
for the resolution of the issues put forward by the researchers.
Fundamentally, these subjects exist at the SPI (PaaS, SaaS and IaaS) phase,
and the main hurdle to scale here is sharing of data. Subsequent to the
analysis of data security and privacy, the logical comprehensive solution to be
inferred is to cater to what is required in the procedures of isolation and
identification of data; this is the principal undertaking to be accomplished at
the design phase of cloud applications, according to Chen et al (n.d.).
In line with the research of Sulochana and Parimelazhagan (2013), cloud
computing functions as some sort of medium, with which a vast ambit of
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

internet-based services can be accessed, to handle routine operations in a
daily basis, and control a multiplicity of services offered within the information
technology space. Inasmuch as the benefits reaped from cloud computing are
extremely numerous and almost without bound with few instances made
above, the susceptibility to threat is also, in correspondence, increased when
a Trusted Third Party (TTP) comes into the fray. There is a good amount of
likelihood that heterogeneity would exist amongst the users of cloud when a
Trusted Third Party is incorporated; this, in turn, impacts cloud security.
A standalone methodology of TTP (Trusted Third Party) for Identity
Management (IDM) was suggested by the authors; this approach was
designed with the capacity to utilize unique data on untrusted data protection
techniques for developing trust in the scope of cloud computing. The
strategies employed in this study are use of predicate data over encoded
data, calculation and computing at a multi-organizational level, and active
bundle scheme. The bundle in this scheme possesses a chain of procedures
for inspection of self reliability; the procedures are stated thus: PII, protection
mechanism, privacy policies and deployment of a virtual machine to
implement the mentioned policies. This approach permits the usage of IDM
solicitation on untrusted clouds. Of the vast multitude of issues that exist in
cloud computing, retrieval, and security of data stored on the cloud are two
very core points of concern.
daily basis, and control a multiplicity of services offered within the information
technology space. Inasmuch as the benefits reaped from cloud computing are
extremely numerous and almost without bound with few instances made
above, the susceptibility to threat is also, in correspondence, increased when
a Trusted Third Party (TTP) comes into the fray. There is a good amount of
likelihood that heterogeneity would exist amongst the users of cloud when a
Trusted Third Party is incorporated; this, in turn, impacts cloud security.
A standalone methodology of TTP (Trusted Third Party) for Identity
Management (IDM) was suggested by the authors; this approach was
designed with the capacity to utilize unique data on untrusted data protection
techniques for developing trust in the scope of cloud computing. The
strategies employed in this study are use of predicate data over encoded
data, calculation and computing at a multi-organizational level, and active
bundle scheme. The bundle in this scheme possesses a chain of procedures
for inspection of self reliability; the procedures are stated thus: PII, protection
mechanism, privacy policies and deployment of a virtual machine to
implement the mentioned policies. This approach permits the usage of IDM
solicitation on untrusted clouds. Of the vast multitude of issues that exist in
cloud computing, retrieval, and security of data stored on the cloud are two
very core points of concern.

Kulkarni et al (2012) did a study bordered around secured cloud services and
data protection, via the use of encryption and decryption mechanisms at the
services level. The authors laid especial emphasis on the threats to cloud
computing, on the basis of security in this study; they also elaborated on the
courses of action, and schemes to devise in order to evade or thwart the
threats. In preceding years, the concept of cloud computing, as a whole, was
subject to rapid emergence and growth; this was down to the vastness of
facilities and advantages it had at its disposal to be offered to organizations
and end users. The increment recorded in a large number of data security
factors is connected to the rapidity with which the cloud is evolving in the
information technology space. And as such, numerous security models and
mechanisms for trust establishment have been emplaced, and are set for the
purpose of providing a more formidable form of aegis to the data on the cloud;
most particularly the ones higher up the scale of sensitivity and privacy. In
defiance of the strength of security, there would still be loopholes in one
aspect of security or the other for a greater portion of the paradigms in
existence. An unprecedented model was created by the authors; it gives brief
highlight of what is to be expected of a Security conscious cloud.
To begin with, trust with the user or organization is built, then and only then
can the data be secured by way of encryption systems and privacy. Under the
Internal Trust layer, Authentication, and Key Management are encompassed;
whilst in the security and Level of Quality of Service fall under the Contract
Trust Layer. However, in cases where data encryption or privacy has reached
data protection, via the use of encryption and decryption mechanisms at the
services level. The authors laid especial emphasis on the threats to cloud
computing, on the basis of security in this study; they also elaborated on the
courses of action, and schemes to devise in order to evade or thwart the
threats. In preceding years, the concept of cloud computing, as a whole, was
subject to rapid emergence and growth; this was down to the vastness of
facilities and advantages it had at its disposal to be offered to organizations
and end users. The increment recorded in a large number of data security
factors is connected to the rapidity with which the cloud is evolving in the
information technology space. And as such, numerous security models and
mechanisms for trust establishment have been emplaced, and are set for the
purpose of providing a more formidable form of aegis to the data on the cloud;
most particularly the ones higher up the scale of sensitivity and privacy. In
defiance of the strength of security, there would still be loopholes in one
aspect of security or the other for a greater portion of the paradigms in
existence. An unprecedented model was created by the authors; it gives brief
highlight of what is to be expected of a Security conscious cloud.
To begin with, trust with the user or organization is built, then and only then
can the data be secured by way of encryption systems and privacy. Under the
Internal Trust layer, Authentication, and Key Management are encompassed;
whilst in the security and Level of Quality of Service fall under the Contract
Trust Layer. However, in cases where data encryption or privacy has reached

a critical point, the mechanism of homomorphism is applied. Data on a cloud
operates using a network; to this end, it is even more susceptible to assaults.
It is with the thought of approaches with which to counter the threats that the
authors advance a number of mechanisms. They are listed thus:
characteristics for access management and identity should be subject to
authorization; networks and servers should be safeguarded; other aspects
such as security of data repository, security as a service, authentication of
users, browser security to mention but a few should be heavily pondered.
In a study conducted in 2012, Shuanglin investigates and analyzes
management policy for data security as regards cloud computing. Here, the
author works out the whole notion of management policy, and asserts that
strong authentication is of the essence; going further, information seen as
sensitive should go through some processes of filtering. For the actuality that
the cloud is internet oriented, as a service, the data exists on each and every
network there is. The author contrives a scheme to serve the function of
protecting data of clients that make use of the cloud in this research. Be that
as it may, the protection of data is not without its complexities, as data is
situated on the public cloud. The strategy devised by the author is premised
upon the underlisted processes. They include Authentication technology,
technical support segments, visualization of delicate information, filtering
sensitive or classified data, setting up a secure management system, cloud
computing access points, and splitting of data analysis into categories.
operates using a network; to this end, it is even more susceptible to assaults.
It is with the thought of approaches with which to counter the threats that the
authors advance a number of mechanisms. They are listed thus:
characteristics for access management and identity should be subject to
authorization; networks and servers should be safeguarded; other aspects
such as security of data repository, security as a service, authentication of
users, browser security to mention but a few should be heavily pondered.
In a study conducted in 2012, Shuanglin investigates and analyzes
management policy for data security as regards cloud computing. Here, the
author works out the whole notion of management policy, and asserts that
strong authentication is of the essence; going further, information seen as
sensitive should go through some processes of filtering. For the actuality that
the cloud is internet oriented, as a service, the data exists on each and every
network there is. The author contrives a scheme to serve the function of
protecting data of clients that make use of the cloud in this research. Be that
as it may, the protection of data is not without its complexities, as data is
situated on the public cloud. The strategy devised by the author is premised
upon the underlisted processes. They include Authentication technology,
technical support segments, visualization of delicate information, filtering
sensitive or classified data, setting up a secure management system, cloud
computing access points, and splitting of data analysis into categories.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Squicciarini, (2012) performs a study which concentrates on the issue of
divulgence of problems, and detriment to the sensitivity and privacy of data
involved in cloud computing. Individuals or large--scale firms are availed
services that are sensitive to a fault in utilization of cloud computing and
related services; hence, it is logical to find reason with why the users express
anxiety and concern over the leakage and/or loss of data, should security be
breached. The authors advance a prospective solution consisting of three
phases, in a bid to preclude events that might spur into loss or leakage of
data. The three phases, in respective order, are lower protection, medium
protection and strong protection phases. As stated by the authors, the third
and most formidable layer, forestall the service providers from gaining
admittance to the credentials of a client’s user profile. The medium level
functions to prevent such occurrences from indexing effectiveness.
The first, and lower protection layer only exists to impose and mandate the
users to act in compliance with the protocols and polices of data on the cloud.
The researchers put forth an innovative approach to avoid the infringement of
privacy and loss and leakage of data; and the model tends toward the
protection techniques that comprise of seven layers. Groundbreaking
business and commercial services have been set in place with the inception
of cloud computing, it is worthy to note however, that these services work on
the basis of demand. The whole construct of the cloud networks was
developed by means of dynamic virtualization of hardware, datasets and
software.
divulgence of problems, and detriment to the sensitivity and privacy of data
involved in cloud computing. Individuals or large--scale firms are availed
services that are sensitive to a fault in utilization of cloud computing and
related services; hence, it is logical to find reason with why the users express
anxiety and concern over the leakage and/or loss of data, should security be
breached. The authors advance a prospective solution consisting of three
phases, in a bid to preclude events that might spur into loss or leakage of
data. The three phases, in respective order, are lower protection, medium
protection and strong protection phases. As stated by the authors, the third
and most formidable layer, forestall the service providers from gaining
admittance to the credentials of a client’s user profile. The medium level
functions to prevent such occurrences from indexing effectiveness.
The first, and lower protection layer only exists to impose and mandate the
users to act in compliance with the protocols and polices of data on the cloud.
The researchers put forth an innovative approach to avoid the infringement of
privacy and loss and leakage of data; and the model tends toward the
protection techniques that comprise of seven layers. Groundbreaking
business and commercial services have been set in place with the inception
of cloud computing, it is worthy to note however, that these services work on
the basis of demand. The whole construct of the cloud networks was
developed by means of dynamic virtualization of hardware, datasets and
software.

Hwang and Li (2010) carried out a research that centers on cloud computing
as a function of secure services. In the study, protection processes with which
trust can be secured were discussed by the researchers. Also, cloud
platforms, cloud service providers as well as the security features specially
fabricated for these services were elucidated.
A trust paradigm for reputation management was suggested by the
researchers; it helped to prescribe the various aspects which have been set
upon the different phases of cloud computing from time. In the paper, the
authors canvassed the data coloring mechanism, and the secure data access
mechanism; these are the exact approaches applied in the process of
constructing the model used by the researchers. In the long run, the continual
and dynamic process of cloud upgrade would necessitate cloud security
infrastructure and trust reputation management to play a crucial part.
The conundrum of security is one that cannot be taken with degree of levity
whatsoever, at this point of evolution in cloud computing. As a result, if a firm
wishes to join in, and experience the services of the cloud first hand, they
must be willing to relinquish sensitive data to cloud service providers (who act
as third-party agents). In doing so, there is a prospect of the company getting
more vulnerable, and at risk of being jeopardized.
Hence, it becomes rational as to why the decisions made by the organization
on service providers have to be correctly, and carefully made. To ensure the
safety of delicate data of the company, it is imperative to accentuate the need
as a function of secure services. In the study, protection processes with which
trust can be secured were discussed by the researchers. Also, cloud
platforms, cloud service providers as well as the security features specially
fabricated for these services were elucidated.
A trust paradigm for reputation management was suggested by the
researchers; it helped to prescribe the various aspects which have been set
upon the different phases of cloud computing from time. In the paper, the
authors canvassed the data coloring mechanism, and the secure data access
mechanism; these are the exact approaches applied in the process of
constructing the model used by the researchers. In the long run, the continual
and dynamic process of cloud upgrade would necessitate cloud security
infrastructure and trust reputation management to play a crucial part.
The conundrum of security is one that cannot be taken with degree of levity
whatsoever, at this point of evolution in cloud computing. As a result, if a firm
wishes to join in, and experience the services of the cloud first hand, they
must be willing to relinquish sensitive data to cloud service providers (who act
as third-party agents). In doing so, there is a prospect of the company getting
more vulnerable, and at risk of being jeopardized.
Hence, it becomes rational as to why the decisions made by the organization
on service providers have to be correctly, and carefully made. To ensure the
safety of delicate data of the company, it is imperative to accentuate the need

to acquire the services of trustworthy service providers (Leung, n.d.); although
this might not be as straightforward as it seems. According to Khorshed et al
(2012), to optimally put a cloud computing infrastructure to use, the
significance of security must first be acknowledged, especially seeing as the
encumbrances are close to innumerable, and evolve through time as well. In
point of fact, services based on the cloud enjoy no form of immunity from
majority of the attacks commonly directed at computer networks (Ahmad &
Hossain, 2014). Great concern is shown towards the security of the user’s
personal data (King & Raja, 2012), and data location (Teneyuca, 2011) with
regards to this. On the whole, the primary issues of security in cloud
computing are built upon data integrity and confidentiality. Asides from the
technical aspect of security, the quality of strategic methodologies the cloud
service provider is able to excogitate also have a vital role to play in ensuring
the security of the user’s data (Joint & Baker, 2011).
A duo of distinct studies conducted by Bouayad et al, and Behl & Behl in the
same year (2012), contained expansive and thorough analyses of the
complexities attached to cloud security. Numerous similarities can be drawn
from both studies, in the sense that they employed the approach of cloud
architecture, features and services enjoyed on the cloud, the service delivery
models used in the cloud infrastructure, and the stakeholders of the cloud,
and its related services, in the process of carrying out their respective
explorative researches; as regards the quagmire on hand.
this might not be as straightforward as it seems. According to Khorshed et al
(2012), to optimally put a cloud computing infrastructure to use, the
significance of security must first be acknowledged, especially seeing as the
encumbrances are close to innumerable, and evolve through time as well. In
point of fact, services based on the cloud enjoy no form of immunity from
majority of the attacks commonly directed at computer networks (Ahmad &
Hossain, 2014). Great concern is shown towards the security of the user’s
personal data (King & Raja, 2012), and data location (Teneyuca, 2011) with
regards to this. On the whole, the primary issues of security in cloud
computing are built upon data integrity and confidentiality. Asides from the
technical aspect of security, the quality of strategic methodologies the cloud
service provider is able to excogitate also have a vital role to play in ensuring
the security of the user’s data (Joint & Baker, 2011).
A duo of distinct studies conducted by Bouayad et al, and Behl & Behl in the
same year (2012), contained expansive and thorough analyses of the
complexities attached to cloud security. Numerous similarities can be drawn
from both studies, in the sense that they employed the approach of cloud
architecture, features and services enjoyed on the cloud, the service delivery
models used in the cloud infrastructure, and the stakeholders of the cloud,
and its related services, in the process of carrying out their respective
explorative researches; as regards the quagmire on hand.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

In the study conducted by Bouayad et al (2012), the major challenges with
which cloud security is faced were synopsized and brought into light. To start
with, the authors stressed on the fact that as much as they could prove
extremely advantageous, the technologies employed in the cloud are their
own bane, as they also birth a wide variety of the impediments plaguing cloud
computing – virtualization and SOA are two proper cases in point. In addition
to that, two major issues of cloud security that necessitate the contrivance of
remedies, are multi tenancy, and isolation. The concept of security
management has a crucial role to play in the supervision of configuration of
sine quibus non and protocols governing the cloud. Furthermore, the cloud
model should be provided with a holistic security wall. As asserted in the
foregoing paragraph, with the inclusion of virtualization, some of the
challenges with security arise as a consequence of the basic technologies
upon which cloud computing is premised. For this reason, it is of great
importance to ensure proper control of security and safety in the cloud, to
facilitate the supervision of user facing data, and the mode of operation
employed in the cloud service provider’s paradigm. In the quest to thwart
coming attacks directed at the personal data of unsuspecting victims, the
aspect of multi-tenancy needs to be deeply investigated. Finally, to protect the
cloud model used, a holistic security wall should be utilized; this would cinch
the emergence of a multi-layered checking system, at varying levels of
security solutions, for any objects that are transmitted within and across the
cloud.
which cloud security is faced were synopsized and brought into light. To start
with, the authors stressed on the fact that as much as they could prove
extremely advantageous, the technologies employed in the cloud are their
own bane, as they also birth a wide variety of the impediments plaguing cloud
computing – virtualization and SOA are two proper cases in point. In addition
to that, two major issues of cloud security that necessitate the contrivance of
remedies, are multi tenancy, and isolation. The concept of security
management has a crucial role to play in the supervision of configuration of
sine quibus non and protocols governing the cloud. Furthermore, the cloud
model should be provided with a holistic security wall. As asserted in the
foregoing paragraph, with the inclusion of virtualization, some of the
challenges with security arise as a consequence of the basic technologies
upon which cloud computing is premised. For this reason, it is of great
importance to ensure proper control of security and safety in the cloud, to
facilitate the supervision of user facing data, and the mode of operation
employed in the cloud service provider’s paradigm. In the quest to thwart
coming attacks directed at the personal data of unsuspecting victims, the
aspect of multi-tenancy needs to be deeply investigated. Finally, to protect the
cloud model used, a holistic security wall should be utilized; this would cinch
the emergence of a multi-layered checking system, at varying levels of
security solutions, for any objects that are transmitted within and across the
cloud.

Jaiswal (2018) highlighted the possibility of cloud service providers being
subject to attack from cyber malices; and since multiple organizations and
users have placed their sensitive credentials in care of third-party cloud
service providers, compromise is definitely not an option they would want for.
Going further, he stressed on the proliferation of noteworthy attack in the
cloud. One of the many instances is the Man in the Cloud attack; this alludes
to an approach that focuses on getting access to the synchronization token of
a cloud user illegitimately; this gambit came into prominence in recent times.
Elucidating on what a synchronization token is, it exists as either some file
stored on the cloud, users’ device in a specified directory, a registry or in
windows credential manager. More often than not, the assailant gains ingress
into the local files of the prey and launched series of attacks on them with
malwares embedded on websites or transmitted through emails. The attacker
contrives a sequence of plots to bait and manipulate the attacker into giving
up their synchronization token. First, the cloud synchronization token is
swapped with a different one which is linked to the attacker's cloud account.
Then, the original token is entrenched in the collection of files to be
synchronized. If a cloud user falls for this delicate malignant scheme, they are
most likely to cede their synchronization token, thence allowing the assailant
to access the user's cloud account and manipulate data as they deem fit.
Again, the Distributed denial of service attacks is another ploy that is targeted
at the cloud, its users and services. Many a time, the customary modus
operandi employed by DDoS attacks is use of several systems to the
subject to attack from cyber malices; and since multiple organizations and
users have placed their sensitive credentials in care of third-party cloud
service providers, compromise is definitely not an option they would want for.
Going further, he stressed on the proliferation of noteworthy attack in the
cloud. One of the many instances is the Man in the Cloud attack; this alludes
to an approach that focuses on getting access to the synchronization token of
a cloud user illegitimately; this gambit came into prominence in recent times.
Elucidating on what a synchronization token is, it exists as either some file
stored on the cloud, users’ device in a specified directory, a registry or in
windows credential manager. More often than not, the assailant gains ingress
into the local files of the prey and launched series of attacks on them with
malwares embedded on websites or transmitted through emails. The attacker
contrives a sequence of plots to bait and manipulate the attacker into giving
up their synchronization token. First, the cloud synchronization token is
swapped with a different one which is linked to the attacker's cloud account.
Then, the original token is entrenched in the collection of files to be
synchronized. If a cloud user falls for this delicate malignant scheme, they are
most likely to cede their synchronization token, thence allowing the assailant
to access the user's cloud account and manipulate data as they deem fit.
Again, the Distributed denial of service attacks is another ploy that is targeted
at the cloud, its users and services. Many a time, the customary modus
operandi employed by DDoS attacks is use of several systems to the

overload a target server; this renders the server unresponsive and as a result,
the efficiency and speed used in performing cloud activities is reduced by a
drastic amount. In the end, nearly, if not all, of the systems are seen to stop
functioning. The 2016 Dyn attack is a relatable instance to refer to, as
prominent websites and platforms with expansive, global servers could not be
accessed by their customers.
Chase, Selokar and Katara (2013) conducted an analytical study that
dissected a number of issues burdening cloud security. Moreover, the varying
challenges with respect to the influences they exert on cloud users,
computing systems and organizations were deconstructed. The said
encumbrances were assayed regarding the effects they also had on cloud
users. The authors opine that given the actuality that it is a sphere that is in its
initial phase of evolution, a myriad of issues pertaining to data storage
security in cloud computing have yet to be found out - the many potentialities
of benefits should not be discarded for this reason. The design and
development stages of this study are entrenched in the usage of public and
private data encryption systems.
The principles of dynamic outsourcing of information should be supported to a
greater extent, in a bid to allow it be perceived as a cloud computing
application, in a more practical manner. The authors conceive that there
would be abidance of activities deployed to map out the prerequisites of
the efficiency and speed used in performing cloud activities is reduced by a
drastic amount. In the end, nearly, if not all, of the systems are seen to stop
functioning. The 2016 Dyn attack is a relatable instance to refer to, as
prominent websites and platforms with expansive, global servers could not be
accessed by their customers.
Chase, Selokar and Katara (2013) conducted an analytical study that
dissected a number of issues burdening cloud security. Moreover, the varying
challenges with respect to the influences they exert on cloud users,
computing systems and organizations were deconstructed. The said
encumbrances were assayed regarding the effects they also had on cloud
users. The authors opine that given the actuality that it is a sphere that is in its
initial phase of evolution, a myriad of issues pertaining to data storage
security in cloud computing have yet to be found out - the many potentialities
of benefits should not be discarded for this reason. The design and
development stages of this study are entrenched in the usage of public and
private data encryption systems.
The principles of dynamic outsourcing of information should be supported to a
greater extent, in a bid to allow it be perceived as a cloud computing
application, in a more practical manner. The authors conceive that there
would be abidance of activities deployed to map out the prerequisites of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

cloud architecture security, and conduct further studies to investigate the
extent of security algorithms that can be used on cloud systems.
From the study, the aforementioned security algorithms could either be
software based or hardware based. Being hardware based would imply that
the use of disk encryption hardware is employed; whilst the software type
could apply methods such as encryption. The ultimate essence of this lies in
its contribution to the cause of consolidation the security of data in the cloud
computing sphere.
extent of security algorithms that can be used on cloud systems.
From the study, the aforementioned security algorithms could either be
software based or hardware based. Being hardware based would imply that
the use of disk encryption hardware is employed; whilst the software type
could apply methods such as encryption. The ultimate essence of this lies in
its contribution to the cause of consolidation the security of data in the cloud
computing sphere.
DISCUSSION
Identification
As with the field of cloud computing, however not independent of the type of
cloud used, in addition to the delivery model, specific users have to be
established, and registered, then, and only then would, supplementary access
priorities and permissions be granted in due manner.
What the procedure looks to achieve is the verification and validation of
individual users of the cloud services, by assigning usernames and password
protections to the profiles with which they gain admittance to their personal
cloud space.
Anonymity
To elucidate what this term alludes, every piece of information in existence
that could be linked to the owner and current user of a node and used to
identify them should be kept confidential, by default and restricted from
distribution by the node itself or the system software.
Authorization
Herein lies a vital information security sine qua non in cloud computing, which
is set in place to guarantee the upholding of referential integrity. Also, it
functions as a tool with which control and privileges are exercised over
process
Identification
As with the field of cloud computing, however not independent of the type of
cloud used, in addition to the delivery model, specific users have to be
established, and registered, then, and only then would, supplementary access
priorities and permissions be granted in due manner.
What the procedure looks to achieve is the verification and validation of
individual users of the cloud services, by assigning usernames and password
protections to the profiles with which they gain admittance to their personal
cloud space.
Anonymity
To elucidate what this term alludes, every piece of information in existence
that could be linked to the owner and current user of a node and used to
identify them should be kept confidential, by default and restricted from
distribution by the node itself or the system software.
Authorization
Herein lies a vital information security sine qua non in cloud computing, which
is set in place to guarantee the upholding of referential integrity. Also, it
functions as a tool with which control and privileges are exercised over
process

Flows about the cloud computing sphere. The whole procedure of
authorization is controlled by an administrator in a private cloud.
Confidentiality
Confidentiality, in cloud computing, plays a crucial role most specifically in the
aspect of maintaining jurisdiction over the data owned by different
organizations, posited across several distributed databases. It is imperative
and mandatory to implement this in a public cloud, especially as a
consequence of the public cloud’s relatively porous accessibility. This
process, of ensuring that the data (which are accessed on a virtual basis) of
the users are protected, and kept confidential, gives room for the enforcement
of information security protocols and guidelines at varying, multiple strata of
cloud applications.
Integrity
The integrity proviso is embedded in the application of required diligence in
the cloud domain, oftentimes in the process of accessing data. As a result,
ACID (atomicity, consistency, isolation and durability) as important features of
the cloud’s data undoubtedly, should be enforced – and rigidly if need be –
across all the delivery models of cloud computing services.
Non-repudiation
authorization is controlled by an administrator in a private cloud.
Confidentiality
Confidentiality, in cloud computing, plays a crucial role most specifically in the
aspect of maintaining jurisdiction over the data owned by different
organizations, posited across several distributed databases. It is imperative
and mandatory to implement this in a public cloud, especially as a
consequence of the public cloud’s relatively porous accessibility. This
process, of ensuring that the data (which are accessed on a virtual basis) of
the users are protected, and kept confidential, gives room for the enforcement
of information security protocols and guidelines at varying, multiple strata of
cloud applications.
Integrity
The integrity proviso is embedded in the application of required diligence in
the cloud domain, oftentimes in the process of accessing data. As a result,
ACID (atomicity, consistency, isolation and durability) as important features of
the cloud’s data undoubtedly, should be enforced – and rigidly if need be –
across all the delivery models of cloud computing services.
Non-repudiation
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

In cloud computing, non repudiation could be gotten through the application of
orthodox e-commerce protocols for maintenance of security, and token
provisioning to data transmission about cloud applications, take for instance
timestamps, digital signatures and services centered on the provision of
confirmation receipts – this functions via digital receipting of messages
transmitted, to validate the data being sent/received.
Availability
Amongst the very crucial sine quibus non of information security, the issue of
availability bears mentioning for the reason that it is a core element to be
considered in making decisions as to whether the services of private, hybrid
or public cloud vendors would be employed; this extends to the form of
delivery models applied also.
The Service Level Agreement trumps all other documents in terms of
preponderance, as it accentuates the trepidation of availability as regards
cloud services and the resources thereof, between the client and the service
provider of the cloud infrastructure.
Privacy
On the basis of legal compliance, and user trust, privacy stands as a crucial
issue that requires a great degree of concern and attention to be paid to it, at
each and every level/phase that the design passes through. For software
orthodox e-commerce protocols for maintenance of security, and token
provisioning to data transmission about cloud applications, take for instance
timestamps, digital signatures and services centered on the provision of
confirmation receipts – this functions via digital receipting of messages
transmitted, to validate the data being sent/received.
Availability
Amongst the very crucial sine quibus non of information security, the issue of
availability bears mentioning for the reason that it is a core element to be
considered in making decisions as to whether the services of private, hybrid
or public cloud vendors would be employed; this extends to the form of
delivery models applied also.
The Service Level Agreement trumps all other documents in terms of
preponderance, as it accentuates the trepidation of availability as regards
cloud services and the resources thereof, between the client and the service
provider of the cloud infrastructure.
Privacy
On the basis of legal compliance, and user trust, privacy stands as a crucial
issue that requires a great degree of concern and attention to be paid to it, at
each and every level/phase that the design passes through. For software

engineers, however, the core quagmire with which they are faced lies in
finding a means to create designs for cloud services in a manner that ensures
that it is in accordance with the substantive legal protocols and rules, and at
the same time reduce privacy risk.
Listed below are some recommendations for Testers, cloud system
designers, architects and developers [15].
To begin with, the personal information of users and clients transmitted
across and stored on the cloud should be minimized.
Again, the credentials and sensitive information of the users stored on the
cloud should be safeguarded and kept from illegitimate access by third
parties.
Also, the cloud users should be afforded maximized control of the services
available on the cloud infrastructure. Users should be given the liberty to
make choices of their own.
At all times, specifications and restrictions should be attached to the reasons
for which data is being used.
Ultimately, it is imperative that the cloud service provider request for feedback
from its clients as per the performance, security, with the major highs and
lows, as well as the very flaws to be picked out in the architecture.
Identity and Access Management
finding a means to create designs for cloud services in a manner that ensures
that it is in accordance with the substantive legal protocols and rules, and at
the same time reduce privacy risk.
Listed below are some recommendations for Testers, cloud system
designers, architects and developers [15].
To begin with, the personal information of users and clients transmitted
across and stored on the cloud should be minimized.
Again, the credentials and sensitive information of the users stored on the
cloud should be safeguarded and kept from illegitimate access by third
parties.
Also, the cloud users should be afforded maximized control of the services
available on the cloud infrastructure. Users should be given the liberty to
make choices of their own.
At all times, specifications and restrictions should be attached to the reasons
for which data is being used.
Ultimately, it is imperative that the cloud service provider request for feedback
from its clients as per the performance, security, with the major highs and
lows, as well as the very flaws to be picked out in the architecture.
Identity and Access Management

Having a formidable, federated framework in place for identity management,
and strategy internal to the firm, sits at the very central axis of determining is
the organization is to thrive in the aspect of managing identities. Employing
the use of a cloud-oriented Identity as a service providers could prove to be
instrumental in the procedure of outsourcing certain capabilities of identity
management, as well as in the facilitation of federated identity management
with cloud service providers [16].
Security Governance
It is suggested that a committee saddled with the task of manning security be
inaugurated; the committee would aim to make the provision of guidance on
security initiatives, and how they conform with business and IT gambits, a
focal point. It is required of the committee to unambiguously lay out the
functions and tasks of the security team and other sects connected in one
way or the other to the performance of information security roles.
Network Security
Since times past, the true purpose for which cloud computing platforms were
created have been deviated from, as is evidenced in the planting of malware
which is afterwards used a tool to transmit spam, and ultimately, compromise
crucial information; also, in the exploitation of the processing power of cloud
infrastructure to crack passwords via the aid of brute force attacks or in the
concealment of command and control (C&C servers) servers which serve as
a control station for botnets.
and strategy internal to the firm, sits at the very central axis of determining is
the organization is to thrive in the aspect of managing identities. Employing
the use of a cloud-oriented Identity as a service providers could prove to be
instrumental in the procedure of outsourcing certain capabilities of identity
management, as well as in the facilitation of federated identity management
with cloud service providers [16].
Security Governance
It is suggested that a committee saddled with the task of manning security be
inaugurated; the committee would aim to make the provision of guidance on
security initiatives, and how they conform with business and IT gambits, a
focal point. It is required of the committee to unambiguously lay out the
functions and tasks of the security team and other sects connected in one
way or the other to the performance of information security roles.
Network Security
Since times past, the true purpose for which cloud computing platforms were
created have been deviated from, as is evidenced in the planting of malware
which is afterwards used a tool to transmit spam, and ultimately, compromise
crucial information; also, in the exploitation of the processing power of cloud
infrastructure to crack passwords via the aid of brute force attacks or in the
concealment of command and control (C&C servers) servers which serve as
a control station for botnets.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Each CSP ought to adopt efficacious security initiatives to create a shield to
protect against network-based attacks; in so doing, prospective attacks of the
same nature could be forestalled, and the misuse of resources addressed, as
well.
Virtual machine security
Physical servers, in the cloud working space, are merged with multiple
machine instances on virtualized servers.
Data center security teams’ capacity is not limited to the replication of typical
security controls for the data center, as a whole to ensure security of the
virtual machines; as their capabilities also extend to the rendering of advices
and suggestions to their customers, on the subject of how the machines could
be set up for migration onto a cloud environment in compliance with due
course.
Data Security
Generation, data storage, data usage, distribution, and obliteration of data all
exist as the component stages of data life cycle.
The phases of which the data cycle is comprised, in entirety, should be
supported by each CSP with the suitable mechanisms. NAS, SAN, Object
Storage, to mention but a few are storage technology used to store data.
However, all the said storage technologies share a certain mutual feature; in
that multiple, distinct customers are to share a sole, general data repository.
protect against network-based attacks; in so doing, prospective attacks of the
same nature could be forestalled, and the misuse of resources addressed, as
well.
Virtual machine security
Physical servers, in the cloud working space, are merged with multiple
machine instances on virtualized servers.
Data center security teams’ capacity is not limited to the replication of typical
security controls for the data center, as a whole to ensure security of the
virtual machines; as their capabilities also extend to the rendering of advices
and suggestions to their customers, on the subject of how the machines could
be set up for migration onto a cloud environment in compliance with due
course.
Data Security
Generation, data storage, data usage, distribution, and obliteration of data all
exist as the component stages of data life cycle.
The phases of which the data cycle is comprised, in entirety, should be
supported by each CSP with the suitable mechanisms. NAS, SAN, Object
Storage, to mention but a few are storage technology used to store data.
However, all the said storage technologies share a certain mutual feature; in
that multiple, distinct customers are to share a sole, general data repository.

In this sort of configuration, for the fact that the procedure of securely
separating the data of customers is of the essence, it should, hence be
ensured. As a case in point, with SaaS, customer data is, under normal
conditions, stored in a common table.
To create a typicality between the customers, a supposed Tenant ID is
employed. In the event that the web application (also referred to as shared
application in some cases) is not programmed with security as a paramount
objective, a customer has the opportunity to apply an SQL injection, in order
to access – albeit in an authorized manner – the data of a separate customer,
manipulate said data, or wipe it off completely. In order to preclude such
occurrences, the required and necessary initiatives for security should be set
in motion.
separating the data of customers is of the essence, it should, hence be
ensured. As a case in point, with SaaS, customer data is, under normal
conditions, stored in a common table.
To create a typicality between the customers, a supposed Tenant ID is
employed. In the event that the web application (also referred to as shared
application in some cases) is not programmed with security as a paramount
objective, a customer has the opportunity to apply an SQL injection, in order
to access – albeit in an authorized manner – the data of a separate customer,
manipulate said data, or wipe it off completely. In order to preclude such
occurrences, the required and necessary initiatives for security should be set
in motion.
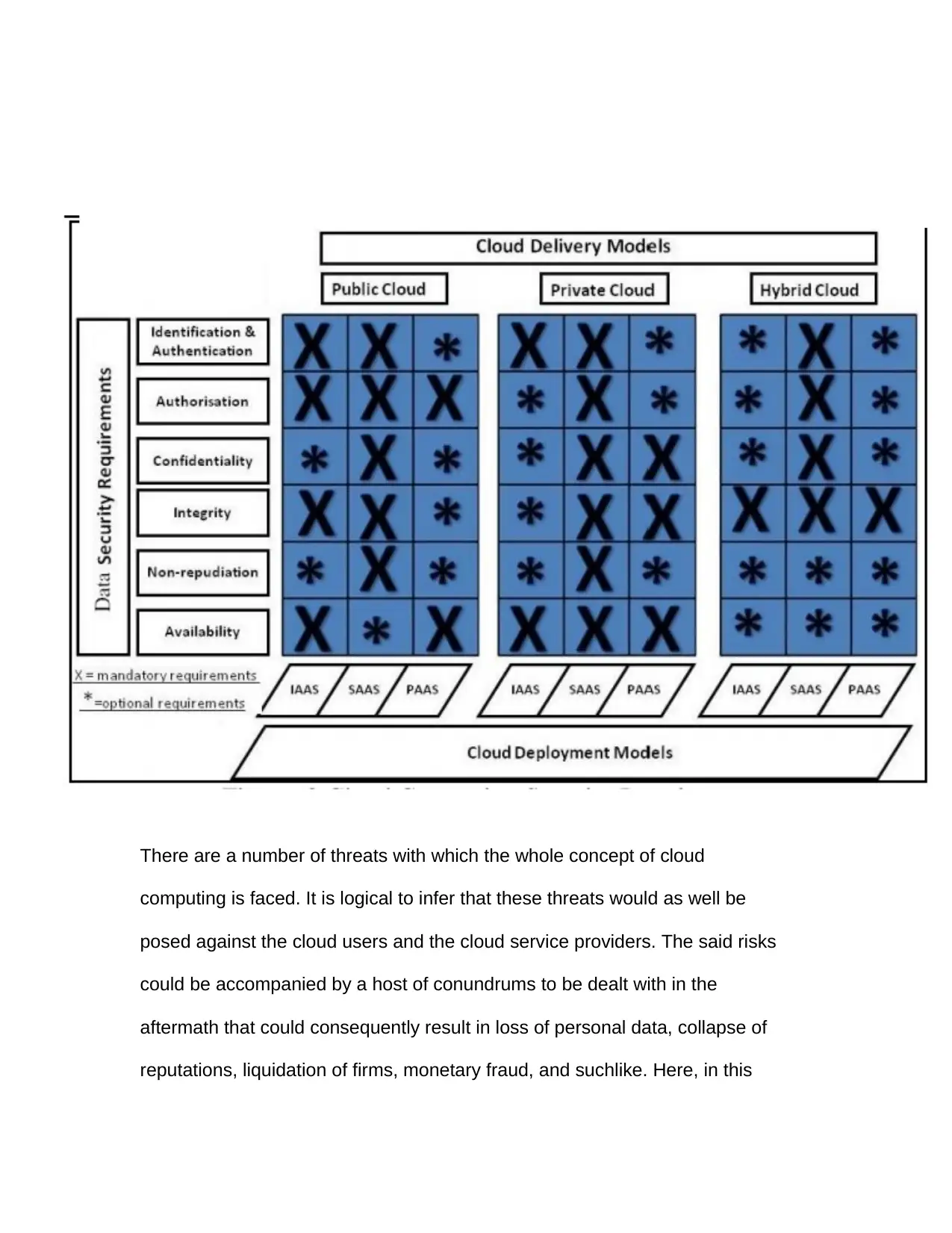
There are a number of threats with which the whole concept of cloud
computing is faced. It is logical to infer that these threats would as well be
posed against the cloud users and the cloud service providers. The said risks
could be accompanied by a host of conundrums to be dealt with in the
aftermath that could consequently result in loss of personal data, collapse of
reputations, liquidation of firms, monetary fraud, and suchlike. Here, in this
computing is faced. It is logical to infer that these threats would as well be
posed against the cloud users and the cloud service providers. The said risks
could be accompanied by a host of conundrums to be dealt with in the
aftermath that could consequently result in loss of personal data, collapse of
reputations, liquidation of firms, monetary fraud, and suchlike. Here, in this
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

study, quite a number of these threats would be looked into and discussed
and possible solutions proffered.
Unethical and malicious application of Cloud Computing and services.
The misuse and application of cloud computing and its services with
malicious intent at heart sits at the pinnacle of threats acknowledged by the
CSA. Using a straightforward example to demonstrate this, botnets are
utilized in the activity of spreading spam and malware. Take for example, the
attackers can infiltrate a public cloud, and devise an approach to upload
malware to hundreds, or thousands of computers and exploit the great
capabilities of the cloud infrastructure, and direct an attack towards other
machines.
The CSA however recommends that, to tackle this issue - in terms of
alleviation, that is, as it cannot be completely eradicated - the initial
procedures of registration and validation be made more rigid, monitoring of
public blacklists for an individual's network blocks and that the traffic on the
customer network be closely investigated.
Insecurity in Application Programming Interfaces
With the fact that software interfaces or APIs are contrivances that facilitate
customers' interaction with the services made available on the cloud
established, it is quite logical to infer that they be guarded with extremely
secure and strict authentication, access control, encryption and activity
and possible solutions proffered.
Unethical and malicious application of Cloud Computing and services.
The misuse and application of cloud computing and its services with
malicious intent at heart sits at the pinnacle of threats acknowledged by the
CSA. Using a straightforward example to demonstrate this, botnets are
utilized in the activity of spreading spam and malware. Take for example, the
attackers can infiltrate a public cloud, and devise an approach to upload
malware to hundreds, or thousands of computers and exploit the great
capabilities of the cloud infrastructure, and direct an attack towards other
machines.
The CSA however recommends that, to tackle this issue - in terms of
alleviation, that is, as it cannot be completely eradicated - the initial
procedures of registration and validation be made more rigid, monitoring of
public blacklists for an individual's network blocks and that the traffic on the
customer network be closely investigated.
Insecurity in Application Programming Interfaces
With the fact that software interfaces or APIs are contrivances that facilitate
customers' interaction with the services made available on the cloud
established, it is quite logical to infer that they be guarded with extremely
secure and strict authentication, access control, encryption and activity

monitoring mechanisms, with greater emphasis placed upon them when third
parties begin to build upon their infrastructure.
To curb this threat, the CSA suggests that the security models used by cloud
provider interfaces are properly analyzed. Again, it is recommended that clear
comprehension of the dependency chain with which the API is affiliated is
attained. On a final note, robust authentication and access controls should be
enforced, in simultaneity with encrypted transmission.
Malicious Insiders
The relevance of this threat (of the malicious insiders) cannot be downplayed,
as a vast majority of cloud service providers do not make known their modus
operandi with hiring/employment of personnel, how they are granted
admittance to the assets, or the manner in which they are being watched. In
this scenario, transparency is crucial in the process of working towards a
secure cloud offering, as well as compliance reporting and breach notification.
To assuage this risk, the CSA proposes that an austere supply chain
management be implemented, and that expansive assessments of the
suppliers be carried out. Also, under legal contracts, prerequisites for human
resource should be specified; in the general information security and
management practices, transparency should be held imperative, along with
compliance reporting.
parties begin to build upon their infrastructure.
To curb this threat, the CSA suggests that the security models used by cloud
provider interfaces are properly analyzed. Again, it is recommended that clear
comprehension of the dependency chain with which the API is affiliated is
attained. On a final note, robust authentication and access controls should be
enforced, in simultaneity with encrypted transmission.
Malicious Insiders
The relevance of this threat (of the malicious insiders) cannot be downplayed,
as a vast majority of cloud service providers do not make known their modus
operandi with hiring/employment of personnel, how they are granted
admittance to the assets, or the manner in which they are being watched. In
this scenario, transparency is crucial in the process of working towards a
secure cloud offering, as well as compliance reporting and breach notification.
To assuage this risk, the CSA proposes that an austere supply chain
management be implemented, and that expansive assessments of the
suppliers be carried out. Also, under legal contracts, prerequisites for human
resource should be specified; in the general information security and
management practices, transparency should be held imperative, along with
compliance reporting.

Shared Technology Vulnerabilities
The concept of sharing infrastructure is deeply ingrained in the operational
activities of IaaS providers. The clients of the IaaS providers are not afforded
with the luxury of having infrastructure split apart individually, as the
architecture upon which the infrastructure is based was not designed in such
way. Nevertheless, to see to it that the customers do not infringe upon each
other's privacy, it is of the essence to supervise, and firm
compartmentalization is also required.
The CSA advises that the environment of the cloud be scanned for
unsolicited, unauthorized modifications and activity. Service Level
Agreements also should be implemented for patching and the remediation of
exposure and susceptibility to threats.
Also, it is proposed that administrative access and operations are provided
with consolidated authentication and access control.
Loss of data
Data is, at all times, susceptible to theft, or loss by a multiplicity of means.
These might include, but are not limited to, the loss of data due to absence of
backup after deletion, misplacement of encryption key or by unpermitted
access. Several organizations ponder upon this issue seriously, as they are in
danger of tarnishing their reputation, and are also required by legal protocol to
ensure the safety of data.
The concept of sharing infrastructure is deeply ingrained in the operational
activities of IaaS providers. The clients of the IaaS providers are not afforded
with the luxury of having infrastructure split apart individually, as the
architecture upon which the infrastructure is based was not designed in such
way. Nevertheless, to see to it that the customers do not infringe upon each
other's privacy, it is of the essence to supervise, and firm
compartmentalization is also required.
The CSA advises that the environment of the cloud be scanned for
unsolicited, unauthorized modifications and activity. Service Level
Agreements also should be implemented for patching and the remediation of
exposure and susceptibility to threats.
Also, it is proposed that administrative access and operations are provided
with consolidated authentication and access control.
Loss of data
Data is, at all times, susceptible to theft, or loss by a multiplicity of means.
These might include, but are not limited to, the loss of data due to absence of
backup after deletion, misplacement of encryption key or by unpermitted
access. Several organizations ponder upon this issue seriously, as they are in
danger of tarnishing their reputation, and are also required by legal protocol to
ensure the safety of data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Propositions rendered by the CSA as avenues to palliate the havoc caused
by the threat include implementation of tough API access control, encryption,
and protection of data being transmitted, contractual specification of the
service provider to provide frameworks for backup and retention of data.
Enforcement of strong key generation protocol on the clients; and provision of
an option to include two-factor authentication.
Service, Account and Traffic hijacking.
Here, cloud users should be cognizant of the threat of service, traffic and
account hijacking as it could result in total jeopardy of personal Information
and credentials, as well as tainting of reputations. The threats are fashioned
in form of phishing and spam campaigns, man-in-the-middle attacks and
denial of service attacks and suchlike.
The CSA recommends that the sharing of account credentials amongst users
and services is prohibited; also the implementation of proactive supervision to
find out unauthorized activity at the initial stage.
Incompetence in the Security of Cloud service providers
If there is failure on the part of the Service provider in incorporating
formidable, strong security measures in the infrastructure of the cloud
beforehand, then the data of clients and cloud users is extremely susceptible
to being compromised. For this reason, security of the provider is highly
significant.
by the threat include implementation of tough API access control, encryption,
and protection of data being transmitted, contractual specification of the
service provider to provide frameworks for backup and retention of data.
Enforcement of strong key generation protocol on the clients; and provision of
an option to include two-factor authentication.
Service, Account and Traffic hijacking.
Here, cloud users should be cognizant of the threat of service, traffic and
account hijacking as it could result in total jeopardy of personal Information
and credentials, as well as tainting of reputations. The threats are fashioned
in form of phishing and spam campaigns, man-in-the-middle attacks and
denial of service attacks and suchlike.
The CSA recommends that the sharing of account credentials amongst users
and services is prohibited; also the implementation of proactive supervision to
find out unauthorized activity at the initial stage.
Incompetence in the Security of Cloud service providers
If there is failure on the part of the Service provider in incorporating
formidable, strong security measures in the infrastructure of the cloud
beforehand, then the data of clients and cloud users is extremely susceptible
to being compromised. For this reason, security of the provider is highly
significant.

Attacks orchestrated by other clients
In the occurrence of dilapidation of structures set in place as barriers between
customers, a customer with malicious intent can gain access to other
customers data and tamper with or manipulate their data and applications.
Problems of availability and trustworthiness
Hitherto, the cloud can only be accessed by way of the internet; this makes
internet reliability and availability and essential point of reference.
Issues of Legality and Regulation
A vast number of questions have been raised, bordering on the legal and
regulatory jurisdiction of transmitted data, due to the virtual and global nature
of cloud computing.
Breach of Perimeter security model
A lot of organizations employ a perimeter security model integrated with rigid
security within and about the perimeter of the firm’s network. Without any
form of doubt, the cloud exists outside the perimeter of enterprise control, but
it will then store critical data and applications.
Integration of Provider and Customer Security Systems
It is required of the cloud service providers that they integrate with the
systems already in place, so as to preclude the happening of reverting to the
archaic methodology of manual provisioning and uncoordinated response.
In the occurrence of dilapidation of structures set in place as barriers between
customers, a customer with malicious intent can gain access to other
customers data and tamper with or manipulate their data and applications.
Problems of availability and trustworthiness
Hitherto, the cloud can only be accessed by way of the internet; this makes
internet reliability and availability and essential point of reference.
Issues of Legality and Regulation
A vast number of questions have been raised, bordering on the legal and
regulatory jurisdiction of transmitted data, due to the virtual and global nature
of cloud computing.
Breach of Perimeter security model
A lot of organizations employ a perimeter security model integrated with rigid
security within and about the perimeter of the firm’s network. Without any
form of doubt, the cloud exists outside the perimeter of enterprise control, but
it will then store critical data and applications.
Integration of Provider and Customer Security Systems
It is required of the cloud service providers that they integrate with the
systems already in place, so as to preclude the happening of reverting to the
archaic methodology of manual provisioning and uncoordinated response.
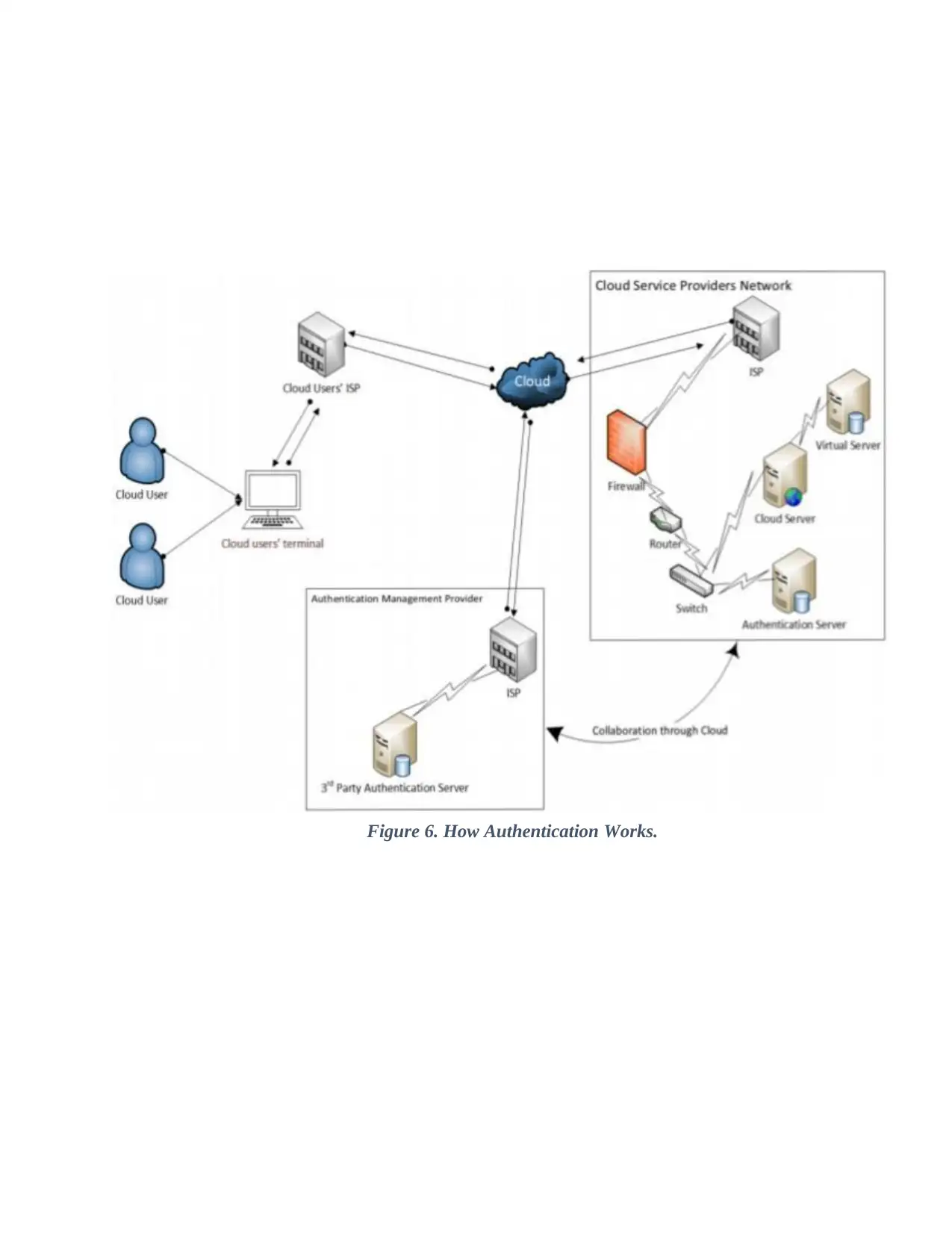
Figure 6. How Authentication Works.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CONCLUSION
It is a well-known fact that cloud computing has now been utilized by a host of
individuals and organizations across various sectors and industries. This
means that data flow has also increased in correspondence, deviating from
what could be obtained in former times. As such, inherent security concerns
are raised; this implies that there is a need to dynamically make upgrades to
the framework of the security base of cloud computing. As observed from the
study, the efforts toward ensuring that the cloud computing sphere is safer to
operate in have been bolstered. Nonetheless, there is still much work to be
done; more researches to be conducted to see to it that this goal is realized.
As the scope of cloud computing – and the business world alike – is
broadening ever rapidly across many fields, research focus should be
directed towards creating improvements in the technologies and processes
utilized in cloud security architecture.
It is a well-known fact that cloud computing has now been utilized by a host of
individuals and organizations across various sectors and industries. This
means that data flow has also increased in correspondence, deviating from
what could be obtained in former times. As such, inherent security concerns
are raised; this implies that there is a need to dynamically make upgrades to
the framework of the security base of cloud computing. As observed from the
study, the efforts toward ensuring that the cloud computing sphere is safer to
operate in have been bolstered. Nonetheless, there is still much work to be
done; more researches to be conducted to see to it that this goal is realized.
As the scope of cloud computing – and the business world alike – is
broadening ever rapidly across many fields, research focus should be
directed towards creating improvements in the technologies and processes
utilized in cloud security architecture.

REFERENCES
Petre, R. (2012). Data mining in Cloud Computing. Database Systems
Journal, 3(3), 67-71.
Ogigau-Neamtiu, F. (2012). Cloud Computing Security Issues. Journal of
Defense Resource Management, 3(2), 141-148.
Singh, S. and Jangwal, T. (2012). Cost breakdown of Public Cloud Computing
and Private Cloud Computing and Security Issues. International Journal of
Computer Science & Information Technology, 4(2), 17-31.
Bisong, A. and Rahman, S.S.M. (2011). An Overview of the Security
Concerns in Enterprise Cloud Computing. International Journal of Network
Security & Its Applications, 3(1), 30-45. doi:10.5121/ijnsa.2011.3103
Rashmi, Sahoo, G. and Mehfuz, S. (2013). Securing Software as a Service
Model of Cloud Computing: Issues and Solutions. International Journal on
Cloud Computing: Services and Architecture, 3(4), 1-11. Doi:
10.5121/ijccsa.2013.3401
Petre, R. (2012). Data mining in Cloud Computing. Database Systems
Journal, 3(3), 67-71.
Ogigau-Neamtiu, F. (2012). Cloud Computing Security Issues. Journal of
Defense Resource Management, 3(2), 141-148.
Singh, S. and Jangwal, T. (2012). Cost breakdown of Public Cloud Computing
and Private Cloud Computing and Security Issues. International Journal of
Computer Science & Information Technology, 4(2), 17-31.
Bisong, A. and Rahman, S.S.M. (2011). An Overview of the Security
Concerns in Enterprise Cloud Computing. International Journal of Network
Security & Its Applications, 3(1), 30-45. doi:10.5121/ijnsa.2011.3103
Rashmi, Sahoo, G. and Mehfuz, S. (2013). Securing Software as a Service
Model of Cloud Computing: Issues and Solutions. International Journal on
Cloud Computing: Services and Architecture, 3(4), 1-11. Doi:
10.5121/ijccsa.2013.3401

Qaisar, S. and Khawaja, K.F. (2012). Cloud Computing: Network/Security
Threats and Countermeasures. Interdisciplinary Journal of Contemporary
Research in Business, 3(9), 1323-1329.
Kuyoro, S.O., Ibikunle, F. and Awodele, O. (2011). Cloud Computing Security
Issues and
Challenges. International Journal of Computer Networks, 3(5), 247-255.
Suresh, K.S. and Prasad, K.V. (2012). Security Issues and Security
Algorithms in Cloud Computing.
International Journal of Advanced Research in Computer Science and
Software Engineering, 2(10),
110-114.
Youssef, A.E. (2012). Exploring Cloud Computing Services and Applications.
Journal of Emerging
Trends in Computing and Information Sciences, 3(6), 838-847.
Subashini, S., & Kavitha, V. (2011). A survey on security issues in service
delivery models of cloud computing. Journal of Network and Computer
Applications, 34(1), 1- 11.
R. Woolley and D. Fletcher “The Hybrid Cloud: Bringing Cloud-Based IT
Services to State Government October 4, 2009” Department of Technology
Services.
Threats and Countermeasures. Interdisciplinary Journal of Contemporary
Research in Business, 3(9), 1323-1329.
Kuyoro, S.O., Ibikunle, F. and Awodele, O. (2011). Cloud Computing Security
Issues and
Challenges. International Journal of Computer Networks, 3(5), 247-255.
Suresh, K.S. and Prasad, K.V. (2012). Security Issues and Security
Algorithms in Cloud Computing.
International Journal of Advanced Research in Computer Science and
Software Engineering, 2(10),
110-114.
Youssef, A.E. (2012). Exploring Cloud Computing Services and Applications.
Journal of Emerging
Trends in Computing and Information Sciences, 3(6), 838-847.
Subashini, S., & Kavitha, V. (2011). A survey on security issues in service
delivery models of cloud computing. Journal of Network and Computer
Applications, 34(1), 1- 11.
R. Woolley and D. Fletcher “The Hybrid Cloud: Bringing Cloud-Based IT
Services to State Government October 4, 2009” Department of Technology
Services.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

T. kraska “Building Database Applications in the Cloud” Swiss federal institute
of technology Zurich 2010
Global Netoptex Incorporated , 2009, Demystifying the cloud. Important
opportunities, crucial choices, http://www.gni.com , pp 4-14, viewed 13
December 2009.
R. Neisse, D. Holling, and A. Pretschner, “Implementing trust in cloud
infrastructures,” in Proceedings of the 11th IEEE/ACM International
Symposium on Cluster, Cloud and Grid Computing (CCGrid ’11), pp. 524–
533, IEEE Computer Society, May 2011.
R. Yeluri, E. Castro-Leon, R. R. Harmon, and J. Greene,“Building trust and
compliance in the cloud for services,” in Proceedings of the Annual SRII
Global Conference (SRII ’12), pp. 379–390, San Jose, Calif, USA, July 2012.
A. Squicciarini, S. Sundareswaran, and D. Lin, “Preventing information
leakage fromindexing in the cloud,” in Proceedings of the 3rd IEEE
International Conference on Cloud Computing (CLOUD ’10), pp. 188–195,
July 2010.
of technology Zurich 2010
Global Netoptex Incorporated , 2009, Demystifying the cloud. Important
opportunities, crucial choices, http://www.gni.com , pp 4-14, viewed 13
December 2009.
R. Neisse, D. Holling, and A. Pretschner, “Implementing trust in cloud
infrastructures,” in Proceedings of the 11th IEEE/ACM International
Symposium on Cluster, Cloud and Grid Computing (CCGrid ’11), pp. 524–
533, IEEE Computer Society, May 2011.
R. Yeluri, E. Castro-Leon, R. R. Harmon, and J. Greene,“Building trust and
compliance in the cloud for services,” in Proceedings of the Annual SRII
Global Conference (SRII ’12), pp. 379–390, San Jose, Calif, USA, July 2012.
A. Squicciarini, S. Sundareswaran, and D. Lin, “Preventing information
leakage fromindexing in the cloud,” in Proceedings of the 3rd IEEE
International Conference on Cloud Computing (CLOUD ’10), pp. 188–195,
July 2010.

K. Hwang and D. Li, “Trusted cloud computing with secure resources and
data coloring,” IEEE Internet Computing, vol. 14, no. 5, pp. 14–22, 2010.
A. Behl, “Emerging security challenges in cloud computing: an insight to cloud
security challenges and their mitigation,” in Proceedings of the World
Congress on Information and Communication Technologies (WICT ’11), pp.
217–222, IEEE, December 2011.
Z. Shen, L. Li, F. Yan, and X. Wu, “Cloud computing system based on trusted
computing platform,” in Proceedings of the International Conference on
Intelligent Computation Technology and Automation (ICICTA ’10), vol. 1, pp.
942–945, IEEE, May 2010.
D. Chen and H. Zhao, “Data security and privacy protection issues in cloud
computing,” in Proceeding of the International Conference on Computer
Science and Electronics Engineering (ICCSEE '12), vol. 1, pp. 647–
651,Hangzhou, China,March 2012.
Khorshed, T.M., Ali, A.B.M.S., and Wasimi, S.A. (2012). A survey on gaps,
threat remediation challenges and some thoughts for proactive attack
detection in cloud computing. Future Generation Computer Systems 28: 833–
851. doi:10.1016/j.future.2012.01.006
data coloring,” IEEE Internet Computing, vol. 14, no. 5, pp. 14–22, 2010.
A. Behl, “Emerging security challenges in cloud computing: an insight to cloud
security challenges and their mitigation,” in Proceedings of the World
Congress on Information and Communication Technologies (WICT ’11), pp.
217–222, IEEE, December 2011.
Z. Shen, L. Li, F. Yan, and X. Wu, “Cloud computing system based on trusted
computing platform,” in Proceedings of the International Conference on
Intelligent Computation Technology and Automation (ICICTA ’10), vol. 1, pp.
942–945, IEEE, May 2010.
D. Chen and H. Zhao, “Data security and privacy protection issues in cloud
computing,” in Proceeding of the International Conference on Computer
Science and Electronics Engineering (ICCSEE '12), vol. 1, pp. 647–
651,Hangzhou, China,March 2012.
Khorshed, T.M., Ali, A.B.M.S., and Wasimi, S.A. (2012). A survey on gaps,
threat remediation challenges and some thoughts for proactive attack
detection in cloud computing. Future Generation Computer Systems 28: 833–
851. doi:10.1016/j.future.2012.01.006

Ahmed, M., and Hossain, M.A. (2014). Cloud computing and security issues
in the cloud. International Journal of Network Security & Its Applications
(IJNSA), 6(1): 25-36. DOI: 10.5121/ijnsa.2014.6103 25.
King, N.J. and Raja, V.T. (2012). Protecting the privacy and security of
sensitive customer data in the cloud. Computer Law and Security Reviews,
28: 308-319.
D. (2011). Internet cloud security: The illusion of inclusion. Information
Security. Technical Report 16: 102-107. doi:10.1016/j.istr.2011.08.005
Joint, A. and Baker, E. (2011). Knowing the past to understand the present 1
e issues in the contracting for cloud based services. Computer Law &
Security Review 27: 407- 415. doi:10.1016/j.clsr.2011.05.002
in the cloud. International Journal of Network Security & Its Applications
(IJNSA), 6(1): 25-36. DOI: 10.5121/ijnsa.2014.6103 25.
King, N.J. and Raja, V.T. (2012). Protecting the privacy and security of
sensitive customer data in the cloud. Computer Law and Security Reviews,
28: 308-319.
D. (2011). Internet cloud security: The illusion of inclusion. Information
Security. Technical Report 16: 102-107. doi:10.1016/j.istr.2011.08.005
Joint, A. and Baker, E. (2011). Knowing the past to understand the present 1
e issues in the contracting for cloud based services. Computer Law &
Security Review 27: 407- 415. doi:10.1016/j.clsr.2011.05.002
1 out of 52
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




