IEEE Report: CIDC Scheme for V2V Safety Message Broadcast Design
VerifiedAdded on 2023/01/16
|16
|6208
|54
Report
AI Summary
This paper introduces a Contention Intensity based Distributed Coordination (CIDC) scheme designed for the secure broadcasting of information in vehicular communication. Leveraging the high-frequency and periodic nature of safety messages, the CIDC's application-layer design enables each vehicle to estimate channel contention in a distributed manner. This contention information informs the MAC layer design, allowing vehicles to employ a superior channel access strategy compared to 802.11p by deterministically selecting the initial back-off counter. The CIDC model is analyzed to derive key performance indicators like packet collision probability and contention delay. The study demonstrates the CIDC's effectiveness, showing a significant reduction in collision probabilities and contention delay compared to 802.11p, with minor communication and computation overhead. Simulation results validate the CIDC's performance under various contention estimation scenarios, addressing practical concerns like vehicle mobility.

Abstract
This paper, proposes contention intensity established distribution coordination structure intended
for plan for broadcasted information safely. Through using of high-frequency as well as
periodical characteristics of broadcasting message safely, the layer application designing for the
contention intensity design coordination (CIDC) gives ability every vehicle will estimation
contention intensity channel instantaneously within complete distribution manner. Using the
information contention magnitude, the MAC layer designing of the CIDC permits vehicles give
access channel approach which is better when compared with 802.11p.It happens as a result of
the CIDC selection of the initial counter back-off or every packet determined, for instance,
basing on contention magnitude as an alternative of the random selection. The CIDC proposed is
molded, as well as major performing displays in relations of probability of the collision packet as
well as mean contention delay is reached. It can be illustrated that change proposed in the
starting choice of counter results for model system that are absolutely diverse beginning the
model of classic Markovic chain. Furthermore, the CIDC proposal is whole distributed as well as
being compatible with 802.11p can gain both considerable lesser collision probabilities in
addition to a slight contention in contrast by 802.11p virtually a relative cheaper price of a minor
communications as well as extra computations. The Far-reaching simulation outcomes show the
CIDC effectiveness in both erroneous and accurate contention estimate circumstances.
Key words: Message broadcast safety, MAC design, DSRC, 802.11p, linked vehicles
1. Introduction
Vehicle-to-vehicle (V2V) communication is
the mains of which the linked device of the
future age intellectual transportation
structures .The application links the
vehicles, with integrated automatic drives is
likely to decrease traffic calamities as well
as economic loses by the communication
combination of the consisting of V2V and
vehicle to the infrastructure (V2I) thus
promoting awareness ability to the
surrounding environment and activities at all
vehicles. Efforts are being made for
deployment of connected vehicles (CV), and
standards of have been designed. (Kan
Zheng, 2016)The tests of Dedicated Short
range Communication (DSRC) have been
made to enable V2V as well as V2I
communications.
The standards of DSRC accepts seven
channels for instance one channel dedicated
for control, while the six channels are set for
applications which does not need safety. The
IEEE 802.11pstandards covers the physical
layer as well as the DSRC with its MAC
layer designing. The IEEE 1609 standards
stack gives address MAC, network also
transport layers. The IEEE 1609 as well as
IEEE 802.11p together they form the access
which is wireless within a vehicular
environments principles while SAE J2735
outlines the information that is usually used
This paper, proposes contention intensity established distribution coordination structure intended
for plan for broadcasted information safely. Through using of high-frequency as well as
periodical characteristics of broadcasting message safely, the layer application designing for the
contention intensity design coordination (CIDC) gives ability every vehicle will estimation
contention intensity channel instantaneously within complete distribution manner. Using the
information contention magnitude, the MAC layer designing of the CIDC permits vehicles give
access channel approach which is better when compared with 802.11p.It happens as a result of
the CIDC selection of the initial counter back-off or every packet determined, for instance,
basing on contention magnitude as an alternative of the random selection. The CIDC proposed is
molded, as well as major performing displays in relations of probability of the collision packet as
well as mean contention delay is reached. It can be illustrated that change proposed in the
starting choice of counter results for model system that are absolutely diverse beginning the
model of classic Markovic chain. Furthermore, the CIDC proposal is whole distributed as well as
being compatible with 802.11p can gain both considerable lesser collision probabilities in
addition to a slight contention in contrast by 802.11p virtually a relative cheaper price of a minor
communications as well as extra computations. The Far-reaching simulation outcomes show the
CIDC effectiveness in both erroneous and accurate contention estimate circumstances.
Key words: Message broadcast safety, MAC design, DSRC, 802.11p, linked vehicles
1. Introduction
Vehicle-to-vehicle (V2V) communication is
the mains of which the linked device of the
future age intellectual transportation
structures .The application links the
vehicles, with integrated automatic drives is
likely to decrease traffic calamities as well
as economic loses by the communication
combination of the consisting of V2V and
vehicle to the infrastructure (V2I) thus
promoting awareness ability to the
surrounding environment and activities at all
vehicles. Efforts are being made for
deployment of connected vehicles (CV), and
standards of have been designed. (Kan
Zheng, 2016)The tests of Dedicated Short
range Communication (DSRC) have been
made to enable V2V as well as V2I
communications.
The standards of DSRC accepts seven
channels for instance one channel dedicated
for control, while the six channels are set for
applications which does not need safety. The
IEEE 802.11pstandards covers the physical
layer as well as the DSRC with its MAC
layer designing. The IEEE 1609 standards
stack gives address MAC, network also
transport layers. The IEEE 1609 as well as
IEEE 802.11p together they form the access
which is wireless within a vehicular
environments principles while SAE J2735
outlines the information that is usually used
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

in the layer of application. (Stephan Olariu,
2009)
In the event of communicating of V2V for
CV uses, the vital element is the message
safety broadcasting. This type of broadcast
goes hand in hand by corresponding to the
Basic Safety Messages within the SAE
J25735 standards in the united states or
CAM in the ITS standards for the
European telecommunication principles
organization. The messages security are
periodicals, single-hop and carrier safety
associated vehicle facts status such as their
acceleration, speed, location as well as
direction. By the broadcasting of the vehicle
safety information, vehicles will be aware of
one another’s status, thus traffic accidents
are minimized due to the effect of message
conveying that requires to be exchanged at
hyper frequency. (Christoph Sommer, 2015)
This high frequency gives the message
safety of broadcasting the main load of
traffic data within control channel of DSRC.
Consequently the broadcasting the message
safely is important in V2V communication
relationship of both significance as well as
significant and its traffic data volume.
Therefore the V2V protocol communication
must be integrated wide designing to give
aid for the reliable message safely
broadcasting.
Generally, design of the protocol for V2V
communication encounters a major change:
improved performances are normally gained
due to overhead cost. The message safely
broadcasted; actually 802.11p experiences a
high probability collision within high load
network. Hence, the 802.11p also majority
built workings on it can deliberate by way of
intended; can create the potential
improvement for overheads which are
minimal. Some other literature workings
will be discussed in detail in section II,
objective is obtain a sufficient performance
improved more coordinated cost and
overheads which are large.
The work objective is to make a structure for
message safely broadcasted; can improve
the performances enough in comparison
with 802.11p at the overhead small cost. For
achieving the target, the unique
characteristics of the message safety
broadcast are exploited e.g. periodicity, high
frequency message, and identical format,
and make our designs basing on the
characteristics. The work contributions are
as follows. In the first place, the novel
proposal contention intensity basing
distributing coordination (CIDC) plan to
better performance of the message
broadcasted. The design proposed is whole
distribution as well in compatibility of
802.11p, characterized by minor
communication, also extra computation, also
obtaining enough improved performances
when comparing 802.11p.Secondly, CIDC
proposal is molded as well as featured, and
know how concerning delay of contention
and packet collision are available. Effects
analyzed for contention delay as well
collision probability of the CIDC is made. It
shows apparently minor adjustment of
802.11p of MAC through CIDC proposal to
diverse model system and diverse basic
effect collision of packet in comparison
802.11p.Thirdly, proposed CIDC
performances is shown using wide
simulations. The probability of collision and
mean CIDC delay are in comparison to
2009)
In the event of communicating of V2V for
CV uses, the vital element is the message
safety broadcasting. This type of broadcast
goes hand in hand by corresponding to the
Basic Safety Messages within the SAE
J25735 standards in the united states or
CAM in the ITS standards for the
European telecommunication principles
organization. The messages security are
periodicals, single-hop and carrier safety
associated vehicle facts status such as their
acceleration, speed, location as well as
direction. By the broadcasting of the vehicle
safety information, vehicles will be aware of
one another’s status, thus traffic accidents
are minimized due to the effect of message
conveying that requires to be exchanged at
hyper frequency. (Christoph Sommer, 2015)
This high frequency gives the message
safety of broadcasting the main load of
traffic data within control channel of DSRC.
Consequently the broadcasting the message
safely is important in V2V communication
relationship of both significance as well as
significant and its traffic data volume.
Therefore the V2V protocol communication
must be integrated wide designing to give
aid for the reliable message safely
broadcasting.
Generally, design of the protocol for V2V
communication encounters a major change:
improved performances are normally gained
due to overhead cost. The message safely
broadcasted; actually 802.11p experiences a
high probability collision within high load
network. Hence, the 802.11p also majority
built workings on it can deliberate by way of
intended; can create the potential
improvement for overheads which are
minimal. Some other literature workings
will be discussed in detail in section II,
objective is obtain a sufficient performance
improved more coordinated cost and
overheads which are large.
The work objective is to make a structure for
message safely broadcasted; can improve
the performances enough in comparison
with 802.11p at the overhead small cost. For
achieving the target, the unique
characteristics of the message safety
broadcast are exploited e.g. periodicity, high
frequency message, and identical format,
and make our designs basing on the
characteristics. The work contributions are
as follows. In the first place, the novel
proposal contention intensity basing
distributing coordination (CIDC) plan to
better performance of the message
broadcasted. The design proposed is whole
distribution as well in compatibility of
802.11p, characterized by minor
communication, also extra computation, also
obtaining enough improved performances
when comparing 802.11p.Secondly, CIDC
proposal is molded as well as featured, and
know how concerning delay of contention
and packet collision are available. Effects
analyzed for contention delay as well
collision probability of the CIDC is made. It
shows apparently minor adjustment of
802.11p of MAC through CIDC proposal to
diverse model system and diverse basic
effect collision of packet in comparison
802.11p.Thirdly, proposed CIDC
performances is shown using wide
simulations. The probability of collision and
mean CIDC delay are in comparison to

effects which are analyzed and of 802.11p
MAC which is demonstrated CIDC can
significantly decreasing average contention
delay and collision probability in a variety
of vehicle density in comparison to 802.11p
MAC faults are presented to account for the
mobility of the vehicle and other practical
concerns. This part assesses the available
working with message safely broadcasted in
the V2V communications reviewing
literature. (Huang, 2009) We group the
working into two groups basing on 802.11p
relationship.
First class works emphases the analysis
performance protocol of 802.11p, which
some studies make proposals of a variety of
adaptation parameter schemes for
optimizing the performance of 802.11p.The
analyzing of the performance of the
802.11p, can be obtained. The deriving
analysis performance considerations of
vehicle mobility and performance boost
proposal basing on accepting the
information transmission power, frequency
and size of window of contetion. The works
above are based the 802.11p parameters
aimed to achieve improved performances
while a distributed structure is sustained and
overhead is small. (Huaqun, 2009)
Although, the parameter adaptation
approach based may face practice
limitations. For example when adapting the
frequency of the message is not a feasible
option always on frequency of the message
application safety support can be moreover
rigid to be practically adjusted. The
adaptation of the size of window in
contention, it brings in mainly a trade-off
between the performance delay as well as
the performance collision rather than
developing both of them. There are some
works of research being developed on
802.11p which do not have adaption base
parameter. The channel access deterministic
for message safety broadcast was proposed
basing on protocol sequences. (Naja,
2013)Development of application layer
design basing on offsetting randomly in
epoch BSM choice towards a better one
performance of layer of MAC of 802.11p if
the information frequency is not compliant.
In recognition of the limitation performance
of 802.11p within high load network, the
works of the second class aims for new
protocols development rather than refining
the 802.11p. Variety MAC protocols
proposals for vehicular communications,
consisting both centralized and distributed
and equally contention- based as well as
designs in contention-free. The proposal of
distribution on time division multiple access
(TDMA)-basing protocol of MAC in the bi-
directional flow of traffic for equipped
vehicles with two transceivers. (Michel
Terré, 2013)This type of protocol decreases
collision probability, also improvement
throughput in comparison to 802.11p
For the TDMA basing MAC is short of
scalability to the vehicle number
respectively. The slot sharing TDMA with
MAC basis was designed. The distributed
cooperation proposal on MAC basis was
proposed by. This is at which clusters as
well as header cooperation form is injected
into the packet so the vehicle can make
decisions to aid others. (Vij, 2010)The
centralized TDMA on MAC basis proposal
in that a roadside unit (RSU) is required to
manage the vehicle communication. The
TDMA with MAC based was also proposed
MAC which is demonstrated CIDC can
significantly decreasing average contention
delay and collision probability in a variety
of vehicle density in comparison to 802.11p
MAC faults are presented to account for the
mobility of the vehicle and other practical
concerns. This part assesses the available
working with message safely broadcasted in
the V2V communications reviewing
literature. (Huang, 2009) We group the
working into two groups basing on 802.11p
relationship.
First class works emphases the analysis
performance protocol of 802.11p, which
some studies make proposals of a variety of
adaptation parameter schemes for
optimizing the performance of 802.11p.The
analyzing of the performance of the
802.11p, can be obtained. The deriving
analysis performance considerations of
vehicle mobility and performance boost
proposal basing on accepting the
information transmission power, frequency
and size of window of contetion. The works
above are based the 802.11p parameters
aimed to achieve improved performances
while a distributed structure is sustained and
overhead is small. (Huaqun, 2009)
Although, the parameter adaptation
approach based may face practice
limitations. For example when adapting the
frequency of the message is not a feasible
option always on frequency of the message
application safety support can be moreover
rigid to be practically adjusted. The
adaptation of the size of window in
contention, it brings in mainly a trade-off
between the performance delay as well as
the performance collision rather than
developing both of them. There are some
works of research being developed on
802.11p which do not have adaption base
parameter. The channel access deterministic
for message safety broadcast was proposed
basing on protocol sequences. (Naja,
2013)Development of application layer
design basing on offsetting randomly in
epoch BSM choice towards a better one
performance of layer of MAC of 802.11p if
the information frequency is not compliant.
In recognition of the limitation performance
of 802.11p within high load network, the
works of the second class aims for new
protocols development rather than refining
the 802.11p. Variety MAC protocols
proposals for vehicular communications,
consisting both centralized and distributed
and equally contention- based as well as
designs in contention-free. The proposal of
distribution on time division multiple access
(TDMA)-basing protocol of MAC in the bi-
directional flow of traffic for equipped
vehicles with two transceivers. (Michel
Terré, 2013)This type of protocol decreases
collision probability, also improvement
throughput in comparison to 802.11p
For the TDMA basing MAC is short of
scalability to the vehicle number
respectively. The slot sharing TDMA with
MAC basis was designed. The distributed
cooperation proposal on MAC basis was
proposed by. This is at which clusters as
well as header cooperation form is injected
into the packet so the vehicle can make
decisions to aid others. (Vij, 2010)The
centralized TDMA on MAC basis proposal
in that a roadside unit (RSU) is required to
manage the vehicle communication. The
TDMA with MAC based was also proposed
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

for messages broadcast relaying. For the
case where channels available are multiple
and every vehicle has to have two radio
heads, as the frequency hopping MAC
based. The proposal on adaptive control
MAC explanation that can switch
between802.11p as well as TDMA basing
MAC reliant on the load of the network. A
periodical broadcast study with a basing on
a geolocation access in LTE V2X .It can
deduced that research works aim to obtain
an important improvement performance at
large overhead cost required for effecting an
efficient network coordination. This type of
work can be grouped into first class.
Nevertheless, rather than of incorporating
parameters in the 802.11p, the aim is to
attain a significant improved performance
by using unique features of the message
safety broadcast and making the designs
consequently.
2. The Design Proposal
The CIDC proposal uses three feature of
messages safely broadcasted like the Table I
summary.
Firstly, while frequency information can
cause congestion, vehicles are enabled to
update information on their environment
timely.
Features Implications
High frequency
messages
Timely information
n update
Mobility not a
concern
Periodicals Messages arrival in
regular intervals
Uniform size and
format
Transmission
duration regularity
Table I:
Furthermore, high frequency message shows
that the effect of mobility of the vehicle in
the limitation message cycle duration .Thus,
the effect of mobility on topology of the
network of the vehicle within several cycles
of messages can be abandoned.
Secondly, as messages safety are periodical,
here is a pattern which is regular regarding
arrival of the messages instants of every
vehicle by message exchange. Observations
like that can be used to better the access of
the vehicle channel strategy. Third, due to
messages safety being with a uniform size
and format, here is a regular pattern
concerning transmission packet duration that
can be used in the design and modelling of
the protocol (Ju Ren, 2018). It must be
distinguished that CIDC is steadfast to the
driven timely message safety broadcasted.
While, other kinds of messages are not
included, the design proposed can be in use
as a building factor in a protocol which is
comprehensive which consists all kinds of
V2V communications. An example of a
protocol may accept CIDC for broadcasting
on the DSRC channel of control and
802.11p for additional service
communication channels.
Assumptions Made
Given assumptions were made basing on the
messages safety:
When high frequency is given of a
message safely broadcasted (i .e.
λ=22 messages per second), the
varying of neighbor vehicle set
case where channels available are multiple
and every vehicle has to have two radio
heads, as the frequency hopping MAC
based. The proposal on adaptive control
MAC explanation that can switch
between802.11p as well as TDMA basing
MAC reliant on the load of the network. A
periodical broadcast study with a basing on
a geolocation access in LTE V2X .It can
deduced that research works aim to obtain
an important improvement performance at
large overhead cost required for effecting an
efficient network coordination. This type of
work can be grouped into first class.
Nevertheless, rather than of incorporating
parameters in the 802.11p, the aim is to
attain a significant improved performance
by using unique features of the message
safety broadcast and making the designs
consequently.
2. The Design Proposal
The CIDC proposal uses three feature of
messages safely broadcasted like the Table I
summary.
Firstly, while frequency information can
cause congestion, vehicles are enabled to
update information on their environment
timely.
Features Implications
High frequency
messages
Timely information
n update
Mobility not a
concern
Periodicals Messages arrival in
regular intervals
Uniform size and
format
Transmission
duration regularity
Table I:
Furthermore, high frequency message shows
that the effect of mobility of the vehicle in
the limitation message cycle duration .Thus,
the effect of mobility on topology of the
network of the vehicle within several cycles
of messages can be abandoned.
Secondly, as messages safety are periodical,
here is a pattern which is regular regarding
arrival of the messages instants of every
vehicle by message exchange. Observations
like that can be used to better the access of
the vehicle channel strategy. Third, due to
messages safety being with a uniform size
and format, here is a regular pattern
concerning transmission packet duration that
can be used in the design and modelling of
the protocol (Ju Ren, 2018). It must be
distinguished that CIDC is steadfast to the
driven timely message safety broadcasted.
While, other kinds of messages are not
included, the design proposed can be in use
as a building factor in a protocol which is
comprehensive which consists all kinds of
V2V communications. An example of a
protocol may accept CIDC for broadcasting
on the DSRC channel of control and
802.11p for additional service
communication channels.
Assumptions Made
Given assumptions were made basing on the
messages safety:
When high frequency is given of a
message safely broadcasted (i .e.
λ=22 messages per second), the
varying of neighbor vehicle set
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

because of vehicle mobility is
insignificant during the period of
several messages.
Vehicle i is with distinctive off set
which is random σi uniformly and
independently drawn from
coordinates [0, 1/λ].This prohibits
the messages arrival and contending
from different vehicles for access of
the channel at the same time. The σi
offset may be static for every vehicle
or by energizing at every frequency
μ like that of μ˂˂λ. Meanwhile, the
σi of every vehicle perpetual for
substantial message cycles number.
A message safety can obsolete;
replace an available message security
which has not been sent.
Vehicles are capable of real-time
processing of data, which is
significant of giving application
security.
For facilitation of the analysis as well as
modelling, given assumptions are
applied:
Messages with safety have same
size, especially the message
transmission duration and DCF
Interfram
Figure 1: shows intensity contention
estimation
DIFS (space) usually thought to be of
multiples time duration slot e.g. TTx +
TDIFS = KTs, where TTx, TDIFS, Ts are
the message transmission lengths. (Hannes
Hartenstein, 2010)The length of DIFS and
slot time length in the space separately.
3. The Contention Intensity
Design Coordination (CIDC)
The intensity contention term is a number of
messages securities which can either
transmitting or waiting to access the channel
within a certain time instant. The CIDC is
made of two sections. Part one is intensity
contention estimation, within layer of
application which operate facilitation of data
exchange within vehicles to make
estimations of the channel of intensity
contention. The second section being the
strategy of accessing, designing of MAC
layer made on the space of 802.11p MAC
yet has modification for the use of intensity
contention information. (Yuanguo Bi, 2017)
Application layer designing is as given:
Vehicle i will include that one
offset σi in the messages
security.
Vehicle i will extract its offset σi
for {j,|j ≠i} of vehicles within the
array from the messages security.
Vehicle i do estimations for the
intensity contention instants
whenever a new security packet
arises at its layer of MAC.
insignificant during the period of
several messages.
Vehicle i is with distinctive off set
which is random σi uniformly and
independently drawn from
coordinates [0, 1/λ].This prohibits
the messages arrival and contending
from different vehicles for access of
the channel at the same time. The σi
offset may be static for every vehicle
or by energizing at every frequency
μ like that of μ˂˂λ. Meanwhile, the
σi of every vehicle perpetual for
substantial message cycles number.
A message safety can obsolete;
replace an available message security
which has not been sent.
Vehicles are capable of real-time
processing of data, which is
significant of giving application
security.
For facilitation of the analysis as well as
modelling, given assumptions are
applied:
Messages with safety have same
size, especially the message
transmission duration and DCF
Interfram
Figure 1: shows intensity contention
estimation
DIFS (space) usually thought to be of
multiples time duration slot e.g. TTx +
TDIFS = KTs, where TTx, TDIFS, Ts are
the message transmission lengths. (Hannes
Hartenstein, 2010)The length of DIFS and
slot time length in the space separately.
3. The Contention Intensity
Design Coordination (CIDC)
The intensity contention term is a number of
messages securities which can either
transmitting or waiting to access the channel
within a certain time instant. The CIDC is
made of two sections. Part one is intensity
contention estimation, within layer of
application which operate facilitation of data
exchange within vehicles to make
estimations of the channel of intensity
contention. The second section being the
strategy of accessing, designing of MAC
layer made on the space of 802.11p MAC
yet has modification for the use of intensity
contention information. (Yuanguo Bi, 2017)
Application layer designing is as given:
Vehicle i will include that one
offset σi in the messages
security.
Vehicle i will extract its offset σi
for {j,|j ≠i} of vehicles within the
array from the messages security.
Vehicle i do estimations for the
intensity contention instants
whenever a new security packet
arises at its layer of MAC.

The contention intensity estimates are
shown in fig 1.It is showing ten vehicles in
the give examples within a communication
range from one another, illustrated in Fig. 1.
bottom. Vehicle 1 is used as an illustration
as shown in Fig. 1 top part. The vehicle 1
keeps the timeline also instantaneously
marks every vehicle in within the range of
communication that generate message safety
basing messages security received in the
preceded cycles. (André-Luc Beylot, 2013)
Whenever the message safety is received
from the vehicle neighboring, the equivalent
mark is usually altered to illustrated the
message is not contending for accessing of
the channel. Then the generated messages
by neighbors also not received in intervals
from the start of this messages cycle, which
is marked as to, until the current time instant
is labelled as tc, all are contending for
access of the channel. By counting the
messages number will give the instant
intensity contention, that is 3 for the
illustration shown in Fig .1 which can be
align all the vehicles. For instance when the
starting can be found basing time of the
GPS.
Figure: intensity contention estimation also
start back-off counter purpose within CIDC
For each vehicle can have all the entire
required information of the vehicles
communicating with it and activities of the
vehicle. (Stephan Olariu, 2009)
4. The Formulation of CIDC
For the formulating the model system, the
given definitions also the denotations are
first introduced. The symbols list applied in
the paper of research is shown in Table II.
Mini-slot and slot is the counter of
back off duration which the packet is
fixed. A mini-slot is time duration
length Ts. When the channel remains
idle, a slot will involve one mini-slot.
A slot has otherwise usually one K
mini-slot. Consequently, Sk = {1}
when slot k is idle; Sk ={1,...,K}
when slot k being busy
Relative and absolute slot index:
normally is an index in relation to
the starting of the implementation
protocol.
The relative slot is the index in
relation to the existing absolute
index i.e. k in Figs. 2(a) as well as
2(b) is an whereas 1, 2 ... afterwards
the “+” being relative slot indexes
also can have translation to k + 1, k
+ 2, k+3... Within absolute slot
index.
shown in fig 1.It is showing ten vehicles in
the give examples within a communication
range from one another, illustrated in Fig. 1.
bottom. Vehicle 1 is used as an illustration
as shown in Fig. 1 top part. The vehicle 1
keeps the timeline also instantaneously
marks every vehicle in within the range of
communication that generate message safety
basing messages security received in the
preceded cycles. (André-Luc Beylot, 2013)
Whenever the message safety is received
from the vehicle neighboring, the equivalent
mark is usually altered to illustrated the
message is not contending for accessing of
the channel. Then the generated messages
by neighbors also not received in intervals
from the start of this messages cycle, which
is marked as to, until the current time instant
is labelled as tc, all are contending for
access of the channel. By counting the
messages number will give the instant
intensity contention, that is 3 for the
illustration shown in Fig .1 which can be
align all the vehicles. For instance when the
starting can be found basing time of the
GPS.
Figure: intensity contention estimation also
start back-off counter purpose within CIDC
For each vehicle can have all the entire
required information of the vehicles
communicating with it and activities of the
vehicle. (Stephan Olariu, 2009)
4. The Formulation of CIDC
For the formulating the model system, the
given definitions also the denotations are
first introduced. The symbols list applied in
the paper of research is shown in Table II.
Mini-slot and slot is the counter of
back off duration which the packet is
fixed. A mini-slot is time duration
length Ts. When the channel remains
idle, a slot will involve one mini-slot.
A slot has otherwise usually one K
mini-slot. Consequently, Sk = {1}
when slot k is idle; Sk ={1,...,K}
when slot k being busy
Relative and absolute slot index:
normally is an index in relation to
the starting of the implementation
protocol.
The relative slot is the index in
relation to the existing absolute
index i.e. k in Figs. 2(a) as well as
2(b) is an whereas 1, 2 ... afterwards
the “+” being relative slot indexes
also can have translation to k + 1, k
+ 2, k+3... Within absolute slot
index.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Designate the packet numbers competing for
access of the channel measured from the
start of slot k by way of c(k). By making
h(k) = 1 as well as h(k) = 0 represents
happenings that slot k is busy also idle,
seperately. (Ning Lu, 2014)
Representing the packet numbers reached in
a minislot k[s] is measured at termination of
the mini-slot as well as the packet numbers
attained in slot k measured at the close of
slot such as nI(k[s]) also nI(k), separately. It
should be noted that h(k) = 1 if when only if
no (k) > 0. A system executing the CIDC
usually directed through the subsequent
rules:
Where, represent the process that gives the
significance of the right hand side
expressions to the variables on the left hand
side.
Given equation (1a): describes the
variation in the intensity contention
afterwards at slot.
Given equation (1b): describes the
projected first counter back-off
selection rule basing on the intensity
contention.
At Equations (1c) as well as (1d)
shows the outcome of the back-off
counter selection on the status
system within an impending time
instant e.g., the channel can be busy
afterwards e(k[s]) slots also with one
extra packet can be sent to equivalent
slot
Additional variables of interest are the
counter back-off maximum amongst all the
competing measured packets; the first slot k,
represented as bmax (k).
The extreme counter back-off is ruled by the
given rule:
From equations (1) & (2); can be manifested
when the beginning counter back-off
selection basing on the intensity contention
within CIDC is of important effects on the
system model (Sungwook, 2017)
5. Analysis performance
access of the channel measured from the
start of slot k by way of c(k). By making
h(k) = 1 as well as h(k) = 0 represents
happenings that slot k is busy also idle,
seperately. (Ning Lu, 2014)
Representing the packet numbers reached in
a minislot k[s] is measured at termination of
the mini-slot as well as the packet numbers
attained in slot k measured at the close of
slot such as nI(k[s]) also nI(k), separately. It
should be noted that h(k) = 1 if when only if
no (k) > 0. A system executing the CIDC
usually directed through the subsequent
rules:
Where, represent the process that gives the
significance of the right hand side
expressions to the variables on the left hand
side.
Given equation (1a): describes the
variation in the intensity contention
afterwards at slot.
Given equation (1b): describes the
projected first counter back-off
selection rule basing on the intensity
contention.
At Equations (1c) as well as (1d)
shows the outcome of the back-off
counter selection on the status
system within an impending time
instant e.g., the channel can be busy
afterwards e(k[s]) slots also with one
extra packet can be sent to equivalent
slot
Additional variables of interest are the
counter back-off maximum amongst all the
competing measured packets; the first slot k,
represented as bmax (k).
The extreme counter back-off is ruled by the
given rule:
From equations (1) & (2); can be manifested
when the beginning counter back-off
selection basing on the intensity contention
within CIDC is of important effects on the
system model (Sungwook, 2017)
5. Analysis performance
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The CIDC proposal has two intuitive
characteristics. First, a collision packet will
only occur in some slots: Therefore a
collision will only occur at s k + 2M, k +
3M
Figure 3: two CIDC illustration features
Secondly, collision of the packets can only
occur if has been reduction in the intensity
contention c(k). If the packet numbers
competing for accessing the channel is
continuous or gradually rising, a collision
will not occur. Being at Step (i) for there is
existence of two packets by continuing
back-off counters at b1 = 0 ; b2 = 2,
separately, the early counter back-off
counter of the received new packet,
represented with e3 that is moved to 9. On
Step (ii) for instance, that is two slots from
Step (i), then packet equivalent to a b2
counter back-off has been transferred, also
the packet through a b2 counter back-off is
conducting as b2 has decreased to zero. The
residual packet counter back-off with the
early e3 back-off counter, represented by b3,
being at 7. Afterwards extra slot, e.g., On
Step (iii), different packet reaches also
moves its early counter back-off e4 to 6
meanwhile, only one remaining packet
competing for the access of the channel.
Unluckily, the back-off counters of the
current packet, e.g., b3, and reduces to 6
within the slot. This results a collision which
will occur in 6 slots. While step (iv), extra
packet reaches also setting its early counter
back-off e5 to 9 which can be witnessed as
the intensity contention having been
reducing after Steps (i) until afore Step (iii),
which makes the collision of packets a
possibility. By the difference, the contention
intensity rises amid Step (iii) as well as Step
(iv), and hence the fresh packet reaching
Step (iv) will not face a collision. Then,
system will portray the set via (1) in detail
(IEEE Operations Center, 2001)
6. Slot Packet Ratio
Being a perspective network parameter,
packet to slot ratio is presented now to
denote the concurrently number competing
packets within the slot numbers that can
provide the counter back-off for these
competing packets. For 802.11p MAC, the
packet to slot refers to the packet numbers in
the permanent range [0, W-1] which is
distributed by W, and W is window of
contention. The CIDC lacks the window of
contention also when packet numbers as
well as a series of their back-off counters
change over a given time. (Altoaimy, 2016)
characteristics. First, a collision packet will
only occur in some slots: Therefore a
collision will only occur at s k + 2M, k +
3M
Figure 3: two CIDC illustration features
Secondly, collision of the packets can only
occur if has been reduction in the intensity
contention c(k). If the packet numbers
competing for accessing the channel is
continuous or gradually rising, a collision
will not occur. Being at Step (i) for there is
existence of two packets by continuing
back-off counters at b1 = 0 ; b2 = 2,
separately, the early counter back-off
counter of the received new packet,
represented with e3 that is moved to 9. On
Step (ii) for instance, that is two slots from
Step (i), then packet equivalent to a b2
counter back-off has been transferred, also
the packet through a b2 counter back-off is
conducting as b2 has decreased to zero. The
residual packet counter back-off with the
early e3 back-off counter, represented by b3,
being at 7. Afterwards extra slot, e.g., On
Step (iii), different packet reaches also
moves its early counter back-off e4 to 6
meanwhile, only one remaining packet
competing for the access of the channel.
Unluckily, the back-off counters of the
current packet, e.g., b3, and reduces to 6
within the slot. This results a collision which
will occur in 6 slots. While step (iv), extra
packet reaches also setting its early counter
back-off e5 to 9 which can be witnessed as
the intensity contention having been
reducing after Steps (i) until afore Step (iii),
which makes the collision of packets a
possibility. By the difference, the contention
intensity rises amid Step (iii) as well as Step
(iv), and hence the fresh packet reaching
Step (iv) will not face a collision. Then,
system will portray the set via (1) in detail
(IEEE Operations Center, 2001)
6. Slot Packet Ratio
Being a perspective network parameter,
packet to slot ratio is presented now to
denote the concurrently number competing
packets within the slot numbers that can
provide the counter back-off for these
competing packets. For 802.11p MAC, the
packet to slot refers to the packet numbers in
the permanent range [0, W-1] which is
distributed by W, and W is window of
contention. The CIDC lacks the window of
contention also when packet numbers as
well as a series of their back-off counters
change over a given time. (Altoaimy, 2016)

For description of the series of the conters
back-off, the virtue entrance point ey (k[s])
at any given mini-slot is shown as:
Where ev (k[s]) is the point of entry if a
packet likely to reach mini-slot ks is also
hence is well-defined for some k[s] (By
contrast, e(k[s]) is only well-defined at k[s]
if nI(k[s]) > 0).
The measured ratio packet to slot at the
mini-slot k[s] ends is given as:
The definition above describes the average
packet numbers per slot, that depending on
N and λ. whereas the parameter M protocol
is also anticipated to have an effect on the
packet-to-slot ratio, that effect is not directly
established on the equation (4). The given
lemma illustrates that the outcome of M
befits manifest as the system nears
saturation. (Cavalcanti, 2014)
Lemma 1: The packet to slot ratio υ(k[s]) is
confined by 1/M in CIDC. It can be easily
illustrated which the 1/M busy ratio is a
confine that cannot be obtained. (Mao,
2017)Given M, N, also λ, when anticipated
value at υ(k[s])in a stable state, represented
as υs, is set by given lemma.
Lemma 2: When N, M, as well as λ, the
estimated ratio of a packet to slot is in a
stable state in the following equation:
Where Pck (0) represents probability of c(k)
being a value 0 and ns is the anticipated
packet number in the busy slot, e.g, the
anticipated no value (k) for equation (1a).
N represents the vehicles number that can
result to saturation satisfaction.
The estimated packet numbers per busy slot,
e.g. ns˃1 because the packet collision
probability. Precisely is linked to the
probability which l packet can collide within
one slot, represented Pl col, over the given
equation:
When neglecting the circumstances at which
over two packets collide, Pcol befits P2 col also
the equation above decreases to
7. Intensity and Delay
Contention
The contention intensity can be described by
the transition matrix probability of c(k) of
one-slot. (Syed Faraz Hasan, 2013)
Definitely, given c(k), the given
circumstances of c(k + 1) that is a
possibility:
back-off, the virtue entrance point ey (k[s])
at any given mini-slot is shown as:
Where ev (k[s]) is the point of entry if a
packet likely to reach mini-slot ks is also
hence is well-defined for some k[s] (By
contrast, e(k[s]) is only well-defined at k[s]
if nI(k[s]) > 0).
The measured ratio packet to slot at the
mini-slot k[s] ends is given as:
The definition above describes the average
packet numbers per slot, that depending on
N and λ. whereas the parameter M protocol
is also anticipated to have an effect on the
packet-to-slot ratio, that effect is not directly
established on the equation (4). The given
lemma illustrates that the outcome of M
befits manifest as the system nears
saturation. (Cavalcanti, 2014)
Lemma 1: The packet to slot ratio υ(k[s]) is
confined by 1/M in CIDC. It can be easily
illustrated which the 1/M busy ratio is a
confine that cannot be obtained. (Mao,
2017)Given M, N, also λ, when anticipated
value at υ(k[s])in a stable state, represented
as υs, is set by given lemma.
Lemma 2: When N, M, as well as λ, the
estimated ratio of a packet to slot is in a
stable state in the following equation:
Where Pck (0) represents probability of c(k)
being a value 0 and ns is the anticipated
packet number in the busy slot, e.g, the
anticipated no value (k) for equation (1a).
N represents the vehicles number that can
result to saturation satisfaction.
The estimated packet numbers per busy slot,
e.g. ns˃1 because the packet collision
probability. Precisely is linked to the
probability which l packet can collide within
one slot, represented Pl col, over the given
equation:
When neglecting the circumstances at which
over two packets collide, Pcol befits P2 col also
the equation above decreases to
7. Intensity and Delay
Contention
The contention intensity can be described by
the transition matrix probability of c(k) of
one-slot. (Syed Faraz Hasan, 2013)
Definitely, given c(k), the given
circumstances of c(k + 1) that is a
possibility:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

i) For the kth slot is busy also there
is nα (k) onsets in the slot k,
therefore c(k + 1) = c(k) + nα (k)
− no (k)
ii) For the kth slot is busy also there
is no onsets in the slot k,
therefore c(k + 1) = c(k) − no (k)
iii) for the kth slot is idle also there is
nβ (k) onsets in the slot k, c(k +
1) = c(k) + nβ (k)
iv) for the kth slot is idle as well as
there is no onset in the slot k, c(k
+ 1) = c(k)
Contemplate an incident at which packets
c(k) = j in slot k as well as c(k + 1) = i
packets inside slot k + 1. Representing
probabilities of that at incident shown that
slot k is idle also busy as PI k+1,k (i, j) as
well as P B k+1,k (i, j), correspondingly.
Disregard the probability exceeding 1 packet
received in the same mini-slot. Therefore, PI
k+1,k (i, j) also P B k+1,k (i, j) with i, j ∈
{1,...,N} as follows
And
Where
Meanwhile a busy slot through probability
υs, the whole probability one-slot
changeover matrix of c(k) is as follows in by
Represented Pcs = [P(c(0)), ..P(c(N))]T as
per the given vector of the stable-stage
probability of c(k), k = 0,...,N. Then Pcs
fulfils
Thus, Pc s is a null space within Pk+1, k − I.
The anticipated intensity contention total
slots, i.e., anticipated c(k) represented as cs,
also its relationship of mean packet delay is
as N, λ, also M as more are brought out
through the subsequent theorem.
Theorem 1: The mean contention intensity
cs also the mean total packet delays fix on
CIDC can be resolved from the given
equations:
The do total packet delay and it is the
duration time from the packet instant is
received to the instant when the packet
transmission completes. The dc is the delay
contention, being the duration time between
is nα (k) onsets in the slot k,
therefore c(k + 1) = c(k) + nα (k)
− no (k)
ii) For the kth slot is busy also there
is no onsets in the slot k,
therefore c(k + 1) = c(k) − no (k)
iii) for the kth slot is idle also there is
nβ (k) onsets in the slot k, c(k +
1) = c(k) + nβ (k)
iv) for the kth slot is idle as well as
there is no onset in the slot k, c(k
+ 1) = c(k)
Contemplate an incident at which packets
c(k) = j in slot k as well as c(k + 1) = i
packets inside slot k + 1. Representing
probabilities of that at incident shown that
slot k is idle also busy as PI k+1,k (i, j) as
well as P B k+1,k (i, j), correspondingly.
Disregard the probability exceeding 1 packet
received in the same mini-slot. Therefore, PI
k+1,k (i, j) also P B k+1,k (i, j) with i, j ∈
{1,...,N} as follows
And
Where
Meanwhile a busy slot through probability
υs, the whole probability one-slot
changeover matrix of c(k) is as follows in by
Represented Pcs = [P(c(0)), ..P(c(N))]T as
per the given vector of the stable-stage
probability of c(k), k = 0,...,N. Then Pcs
fulfils
Thus, Pc s is a null space within Pk+1, k − I.
The anticipated intensity contention total
slots, i.e., anticipated c(k) represented as cs,
also its relationship of mean packet delay is
as N, λ, also M as more are brought out
through the subsequent theorem.
Theorem 1: The mean contention intensity
cs also the mean total packet delays fix on
CIDC can be resolved from the given
equations:
The do total packet delay and it is the
duration time from the packet instant is
received to the instant when the packet
transmission completes. The dc is the delay
contention, being the duration time between
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the instant that a packet is received as well
as the instant when the transmission packet
starts. The relationship within the two delay
metrics is as follows:
Lemma 3: The N-small and N-large
estimates of the anticipate number of
competing packets cs, represented as cL s and
cH s separately, is as follows:
8. Collision Probability and
Conditions
In this part, the instant probability
collision is first analyzed. Next, the
higher targeting of collision probability
is derivative in the closed form.
Contemplate the occurrence which
packet B, that reaches at the minis-lot
k2[s2], collides through packet A, that
reaches at mini-slot k1[s1], at k1 < k2.
Let α = k2 − k1. Supposing β busy slots
in the intermission [k1[s1], k2[s2]), in
which τ packets are transferred.
Designate the packet number arriving in
the intermission [k1[s1], k2[s2]] as η.
(Danda B. Rawat, 2017).
Lemma 4: Packets A as well as B can collide
if also only if
Lemma 4 proves aforesaid feature of
duration with extra transfers than is
important; a collision to occur (as illustrated
in Fig. 3(b)).
The probability collision of the forward
given α and c1 can be written as follows:
where c’1 = c1 − 2 also Pk2 A denotes the
probability of at least one onset incident
happening in slot k2.
Owing to the autonomous rise features of
the arbitrary arrival procedure, the
transmission number as well as arrivals in
the α slots can be deliberated as per
independent e.g.
where Pα T (i)as well as Pα A (j) represent
probabilities that of i packets are transmitted
also that of j packets reach in the α slots,
separately.
By expressing β = α/M. The total collision
probability is
Theorem 2: The mean collision probability
of the CIDC, presumptuous as the system is
not outside saturation, is upper enclosed by
as the instant when the transmission packet
starts. The relationship within the two delay
metrics is as follows:
Lemma 3: The N-small and N-large
estimates of the anticipate number of
competing packets cs, represented as cL s and
cH s separately, is as follows:
8. Collision Probability and
Conditions
In this part, the instant probability
collision is first analyzed. Next, the
higher targeting of collision probability
is derivative in the closed form.
Contemplate the occurrence which
packet B, that reaches at the minis-lot
k2[s2], collides through packet A, that
reaches at mini-slot k1[s1], at k1 < k2.
Let α = k2 − k1. Supposing β busy slots
in the intermission [k1[s1], k2[s2]), in
which τ packets are transferred.
Designate the packet number arriving in
the intermission [k1[s1], k2[s2]] as η.
(Danda B. Rawat, 2017).
Lemma 4: Packets A as well as B can collide
if also only if
Lemma 4 proves aforesaid feature of
duration with extra transfers than is
important; a collision to occur (as illustrated
in Fig. 3(b)).
The probability collision of the forward
given α and c1 can be written as follows:
where c’1 = c1 − 2 also Pk2 A denotes the
probability of at least one onset incident
happening in slot k2.
Owing to the autonomous rise features of
the arbitrary arrival procedure, the
transmission number as well as arrivals in
the α slots can be deliberated as per
independent e.g.
where Pα T (i)as well as Pα A (j) represent
probabilities that of i packets are transmitted
also that of j packets reach in the α slots,
separately.
By expressing β = α/M. The total collision
probability is
Theorem 2: The mean collision probability
of the CIDC, presumptuous as the system is
not outside saturation, is upper enclosed by
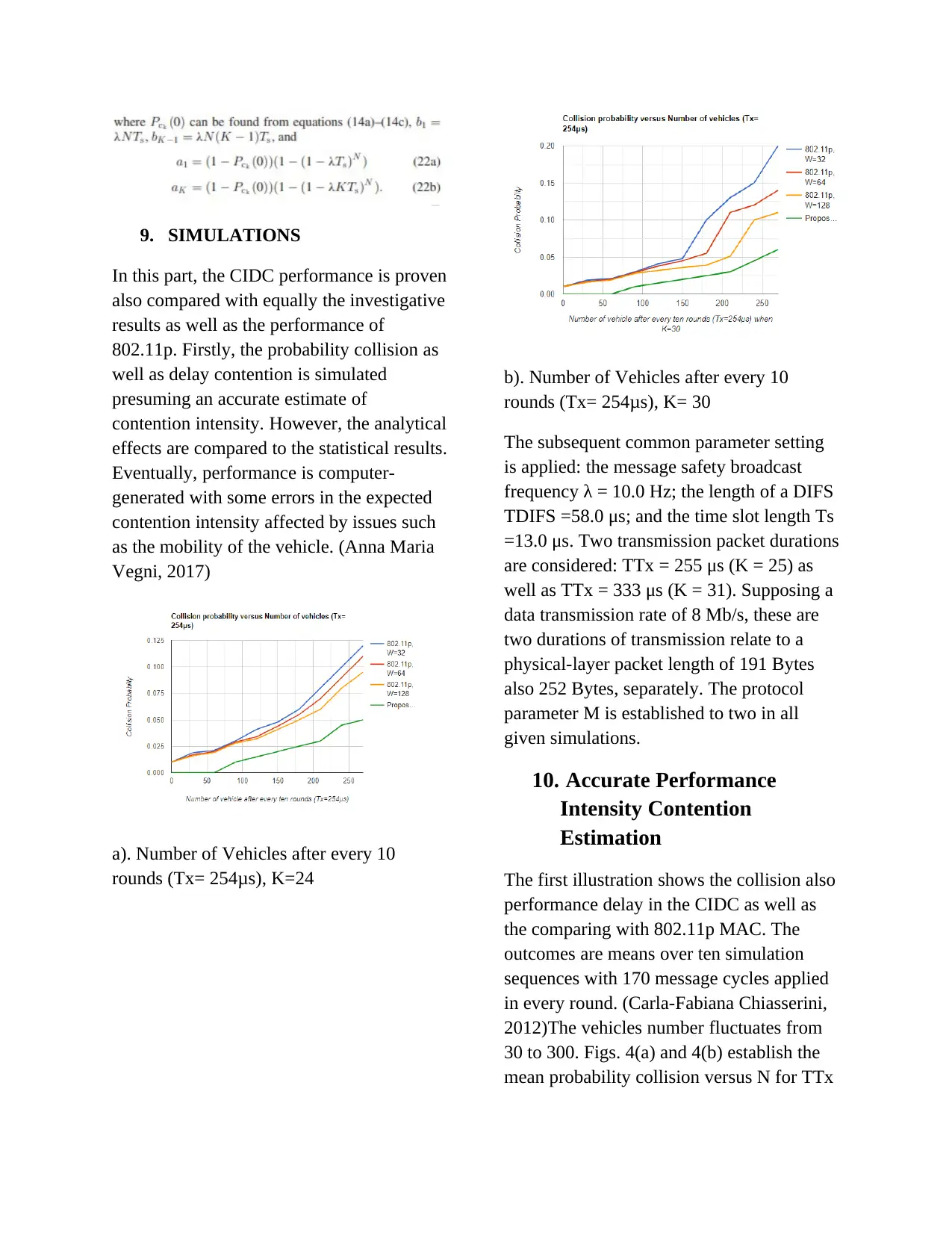
9. SIMULATIONS
In this part, the CIDC performance is proven
also compared with equally the investigative
results as well as the performance of
802.11p. Firstly, the probability collision as
well as delay contention is simulated
presuming an accurate estimate of
contention intensity. However, the analytical
effects are compared to the statistical results.
Eventually, performance is computer-
generated with some errors in the expected
contention intensity affected by issues such
as the mobility of the vehicle. (Anna Maria
Vegni, 2017)
a). Number of Vehicles after every 10
rounds (Tx= 254μs), K=24
b). Number of Vehicles after every 10
rounds (Tx= 254μs), K= 30
The subsequent common parameter setting
is applied: the message safety broadcast
frequency λ = 10.0 Hz; the length of a DIFS
TDIFS =58.0 μs; and the time slot length Ts
=13.0 μs. Two transmission packet durations
are considered: TTx = 255 μs (K = 25) as
well as TTx = 333 μs (K = 31). Supposing a
data transmission rate of 8 Mb/s, these are
two durations of transmission relate to a
physical-layer packet length of 191 Bytes
also 252 Bytes, separately. The protocol
parameter M is established to two in all
given simulations.
10. Accurate Performance
Intensity Contention
Estimation
The first illustration shows the collision also
performance delay in the CIDC as well as
the comparing with 802.11p MAC. The
outcomes are means over ten simulation
sequences with 170 message cycles applied
in every round. (Carla-Fabiana Chiasserini,
2012)The vehicles number fluctuates from
30 to 300. Figs. 4(a) and 4(b) establish the
mean probability collision versus N for TTx
In this part, the CIDC performance is proven
also compared with equally the investigative
results as well as the performance of
802.11p. Firstly, the probability collision as
well as delay contention is simulated
presuming an accurate estimate of
contention intensity. However, the analytical
effects are compared to the statistical results.
Eventually, performance is computer-
generated with some errors in the expected
contention intensity affected by issues such
as the mobility of the vehicle. (Anna Maria
Vegni, 2017)
a). Number of Vehicles after every 10
rounds (Tx= 254μs), K=24
b). Number of Vehicles after every 10
rounds (Tx= 254μs), K= 30
The subsequent common parameter setting
is applied: the message safety broadcast
frequency λ = 10.0 Hz; the length of a DIFS
TDIFS =58.0 μs; and the time slot length Ts
=13.0 μs. Two transmission packet durations
are considered: TTx = 255 μs (K = 25) as
well as TTx = 333 μs (K = 31). Supposing a
data transmission rate of 8 Mb/s, these are
two durations of transmission relate to a
physical-layer packet length of 191 Bytes
also 252 Bytes, separately. The protocol
parameter M is established to two in all
given simulations.
10. Accurate Performance
Intensity Contention
Estimation
The first illustration shows the collision also
performance delay in the CIDC as well as
the comparing with 802.11p MAC. The
outcomes are means over ten simulation
sequences with 170 message cycles applied
in every round. (Carla-Fabiana Chiasserini,
2012)The vehicles number fluctuates from
30 to 300. Figs. 4(a) and 4(b) establish the
mean probability collision versus N for TTx
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
