Ransomware Attack Analysis & Prevention
VerifiedAdded on 2020/03/23
|8
|1503
|237
AI Summary
This assignment analyzes a ransomware attack that targeted Motherboards and More Pty Ltd., detailing the attack's impact, financial losses, and informational consequences. It examines the vulnerability factors within the organization and proposes effective control measures to mitigate future attacks. The analysis emphasizes the importance of implementing robust antivirus software, maintaining regular system updates, practicing safe email habits, and establishing comprehensive data backup systems.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: ACCOUNTING INFORMATION SYSTEM
Accounting Information System
Name of the Student
Name of the University
Author Note
Accounting Information System
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
ACCOUNTING INFORMATION SYSTEM
Executive summary
This report deals with the discussion about the recent outbreak of the ransom ware attack.
The organization chosen for the completion of this report is the Motherboards and More Pty
Ltd. The CFO of the organization has asked to produce a brief review of the revenue cycle,
which the company follows for the products and has requested to provide a recommendation
for the organization, which would help them to combat the ransom ware attack. The report
contains a description of the revenue cycle followed by the organization, the drawbacks,
which the current system has and the recommendation for the ransom ware attacks.
ACCOUNTING INFORMATION SYSTEM
Executive summary
This report deals with the discussion about the recent outbreak of the ransom ware attack.
The organization chosen for the completion of this report is the Motherboards and More Pty
Ltd. The CFO of the organization has asked to produce a brief review of the revenue cycle,
which the company follows for the products and has requested to provide a recommendation
for the organization, which would help them to combat the ransom ware attack. The report
contains a description of the revenue cycle followed by the organization, the drawbacks,
which the current system has and the recommendation for the ransom ware attacks.

2
ACCOUNTING INFORMATION SYSTEM
Table of Contents
Introduction................................................................................................................................3
Overview of the revenue cycle...................................................................................................3
Threat identification...................................................................................................................4
Ransom ware - attack overview.................................................................................................5
Appropriate controlling measures..............................................................................................6
Conclusion..................................................................................................................................6
Recommendation........................................................................................................................6
References..................................................................................................................................7
ACCOUNTING INFORMATION SYSTEM
Table of Contents
Introduction................................................................................................................................3
Overview of the revenue cycle...................................................................................................3
Threat identification...................................................................................................................4
Ransom ware - attack overview.................................................................................................5
Appropriate controlling measures..............................................................................................6
Conclusion..................................................................................................................................6
Recommendation........................................................................................................................6
References..................................................................................................................................7

3
CUSTOMERS TAKE ORDER CUSTOMER
ACCOUNTING INFORMATION SYSTEM
Introduction
Ransom ware virus had recently started a worldwide chaotic outbreak in May of 2017.
The warehouse drawbacks and the recommendation for the threats and the ransom ware
attacks on how to combat them have compiled in this report for the CFO of Motherboards
and More Pty Ltd also discussing about the revenue cycle that is being followed.
Overview of the revenue cycle
The organization, Motherboards, and More Pty Ltd is a medium size organization,
which produces motherboards, microchips, repairing procedures and graphics cards for the
continent of Australia. The organization has its offices in the central city building and the
other departments are situated in the outskirts of Australia (Wells & Bravender, 2016). The
revenue cycle of the company follows a pattern discussed as follows:
The customer after visiting the website of the organization searches for the product,
which he or she wishes to buy. After choosing the product, the customer requests for the
product to be delivered. The orders are completed on a credit basis. The orders are placed and
invoices are created which is then forwarded to the warehouse for the completion of the
procedure (Harris & Kaplan, 2015). The invoices are checked in an alphabetical manner and
the orders come in from twenty different sources ant the outgoing deliveries are more than
that. When an item is found to be missing in the warehouse the workers log the information
in a logbook along with the tag and the inventory record is updated. The item once lout for
the customer can track delivery (Sittig & Singh, 2016). Once the item has been delivered to
the customer the review and the company, which would help the other customers visiting the
website to learn about the quality of the products, takes the feedback.
CUSTOMERS TAKE ORDER CUSTOMER
ACCOUNTING INFORMATION SYSTEM
Introduction
Ransom ware virus had recently started a worldwide chaotic outbreak in May of 2017.
The warehouse drawbacks and the recommendation for the threats and the ransom ware
attacks on how to combat them have compiled in this report for the CFO of Motherboards
and More Pty Ltd also discussing about the revenue cycle that is being followed.
Overview of the revenue cycle
The organization, Motherboards, and More Pty Ltd is a medium size organization,
which produces motherboards, microchips, repairing procedures and graphics cards for the
continent of Australia. The organization has its offices in the central city building and the
other departments are situated in the outskirts of Australia (Wells & Bravender, 2016). The
revenue cycle of the company follows a pattern discussed as follows:
The customer after visiting the website of the organization searches for the product,
which he or she wishes to buy. After choosing the product, the customer requests for the
product to be delivered. The orders are completed on a credit basis. The orders are placed and
invoices are created which is then forwarded to the warehouse for the completion of the
procedure (Harris & Kaplan, 2015). The invoices are checked in an alphabetical manner and
the orders come in from twenty different sources ant the outgoing deliveries are more than
that. When an item is found to be missing in the warehouse the workers log the information
in a logbook along with the tag and the inventory record is updated. The item once lout for
the customer can track delivery (Sittig & Singh, 2016). Once the item has been delivered to
the customer the review and the company, which would help the other customers visiting the
website to learn about the quality of the products, takes the feedback.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
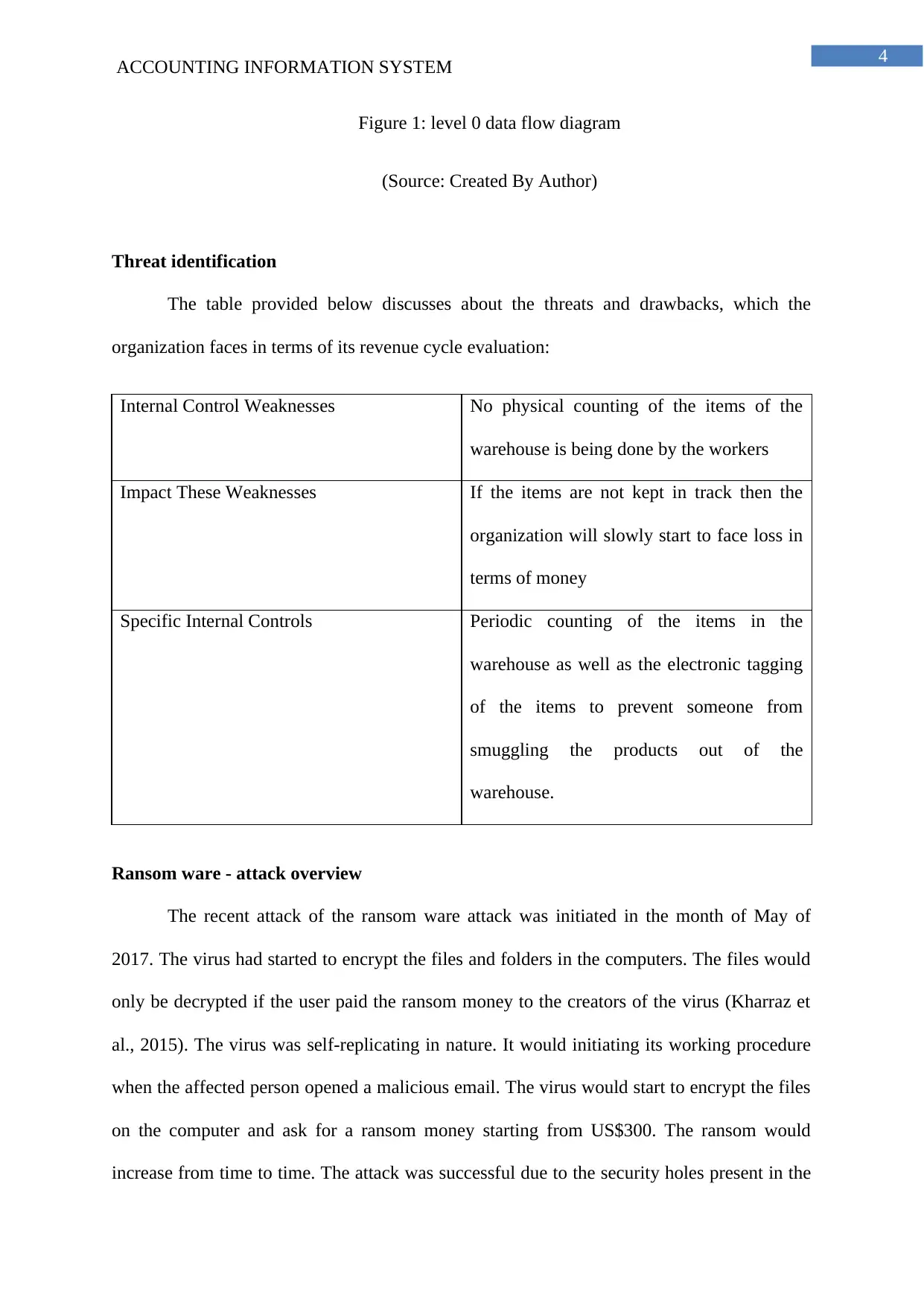
4
ACCOUNTING INFORMATION SYSTEM
Figure 1: level 0 data flow diagram
(Source: Created By Author)
Threat identification
The table provided below discusses about the threats and drawbacks, which the
organization faces in terms of its revenue cycle evaluation:
Internal Control Weaknesses No physical counting of the items of the
warehouse is being done by the workers
Impact These Weaknesses If the items are not kept in track then the
organization will slowly start to face loss in
terms of money
Specific Internal Controls Periodic counting of the items in the
warehouse as well as the electronic tagging
of the items to prevent someone from
smuggling the products out of the
warehouse.
Ransom ware - attack overview
The recent attack of the ransom ware attack was initiated in the month of May of
2017. The virus had started to encrypt the files and folders in the computers. The files would
only be decrypted if the user paid the ransom money to the creators of the virus (Kharraz et
al., 2015). The virus was self-replicating in nature. It would initiating its working procedure
when the affected person opened a malicious email. The virus would start to encrypt the files
on the computer and ask for a ransom money starting from US$300. The ransom would
increase from time to time. The attack was successful due to the security holes present in the
ACCOUNTING INFORMATION SYSTEM
Figure 1: level 0 data flow diagram
(Source: Created By Author)
Threat identification
The table provided below discusses about the threats and drawbacks, which the
organization faces in terms of its revenue cycle evaluation:
Internal Control Weaknesses No physical counting of the items of the
warehouse is being done by the workers
Impact These Weaknesses If the items are not kept in track then the
organization will slowly start to face loss in
terms of money
Specific Internal Controls Periodic counting of the items in the
warehouse as well as the electronic tagging
of the items to prevent someone from
smuggling the products out of the
warehouse.
Ransom ware - attack overview
The recent attack of the ransom ware attack was initiated in the month of May of
2017. The virus had started to encrypt the files and folders in the computers. The files would
only be decrypted if the user paid the ransom money to the creators of the virus (Kharraz et
al., 2015). The virus was self-replicating in nature. It would initiating its working procedure
when the affected person opened a malicious email. The virus would start to encrypt the files
on the computer and ask for a ransom money starting from US$300. The ransom would
increase from time to time. The attack was successful due to the security holes present in the

5
ACCOUNTING INFORMATION SYSTEM
windows operating system. When the Microsoft officials were asked about the security holes,
they said that they had found the drawbacks from long ago and had published the respective
updates for them. Majority of the users had switched the updates option of the windows
center off which made the updates not to reach the computers (Collier, 2017). Moreover,
many of the computers affected were using an obsolete version of the windows operating
system (Mohurle & Patil, 2017). The highest casualty level was in the hospitals and clinics in
England. The ransom exorcists were able to extort a total amount of $57,000 from 99
counties.
Appropriate controlling measures
The best appropriate measures that could be taken up by the organization would be to
install an effective antivirus along with an anti ransom ware virus software. The software
would be able to determine any kind of ransom ware attack on the system and stop the virus
from initiating the attack (Gupta & Tripathi, 2017). Keeping a backup of all the data that is
essential for the company should be kept safe in a remote located server. The mails, which
come into the system, should be checked before opening then or clicking on the links that
might redirect the user to a location on the internet from where the virus would be
downloaded into the system. The main problem due to which the attack was initiated was not
installing the latest updates. The computer of the company should always be kept up to date
at all times (Pope, 2016).
Conclusion
To conclude this report, it can be said that the recent attack of the ransom ware attack
has produced many loss in terms of financial as well as from the information point of view.
The study of the organization, Motherboards and More Pty Ltd has provided a detailed report
ACCOUNTING INFORMATION SYSTEM
windows operating system. When the Microsoft officials were asked about the security holes,
they said that they had found the drawbacks from long ago and had published the respective
updates for them. Majority of the users had switched the updates option of the windows
center off which made the updates not to reach the computers (Collier, 2017). Moreover,
many of the computers affected were using an obsolete version of the windows operating
system (Mohurle & Patil, 2017). The highest casualty level was in the hospitals and clinics in
England. The ransom exorcists were able to extort a total amount of $57,000 from 99
counties.
Appropriate controlling measures
The best appropriate measures that could be taken up by the organization would be to
install an effective antivirus along with an anti ransom ware virus software. The software
would be able to determine any kind of ransom ware attack on the system and stop the virus
from initiating the attack (Gupta & Tripathi, 2017). Keeping a backup of all the data that is
essential for the company should be kept safe in a remote located server. The mails, which
come into the system, should be checked before opening then or clicking on the links that
might redirect the user to a location on the internet from where the virus would be
downloaded into the system. The main problem due to which the attack was initiated was not
installing the latest updates. The computer of the company should always be kept up to date
at all times (Pope, 2016).
Conclusion
To conclude this report, it can be said that the recent attack of the ransom ware attack
has produced many loss in terms of financial as well as from the information point of view.
The study of the organization, Motherboards and More Pty Ltd has provided a detailed report

6
ACCOUNTING INFORMATION SYSTEM
of the drawbacks in the warehouse of the organization and the recommendation for the
ransom ware attack.
Recommendation
From the above report, it can be said that the basic drawback of the warehouse is the
inability of the company to keep a track of the items that it has in store. This can be overcome
by the use of appropriate tagging system and along with a daily monitoring system, which
would compare the stock items with the inventory list. Tagging the items with an electronic
tag would help the warehouse officials are notified when an item is being taken out of the
location without the officials knowing.
References
Collier, R. (2017). NHS ransom ware attack spreads worldwide.
Gupta, G., & Tripathi, K. (2017). STUDY ON RANSOM WARE ATTACK AND ITS
PREVENTION. International Education and Research Journal, 3(5).
Harris, M. T., & Kaplan, D. (2015). The Revenue Cycle. In The Complete Business Guide for
a Successful Medical Practice (pp. 107-119). Springer International Publishing.
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L., & Kirda, E. (2015, July). Cutting the
gordian knot: A look under the hood of ransom ware attacks. In International
Conference on Detection of Intrusions and Malware, and Vulnerability
Assessment (pp. 3-24). Springer, Cham.
Mohurle, S., & Patil, M. (2017). A brief study of Wannacry Threat: Ransom ware Attack
2017. International Journal, 8(5).
ACCOUNTING INFORMATION SYSTEM
of the drawbacks in the warehouse of the organization and the recommendation for the
ransom ware attack.
Recommendation
From the above report, it can be said that the basic drawback of the warehouse is the
inability of the company to keep a track of the items that it has in store. This can be overcome
by the use of appropriate tagging system and along with a daily monitoring system, which
would compare the stock items with the inventory list. Tagging the items with an electronic
tag would help the warehouse officials are notified when an item is being taken out of the
location without the officials knowing.
References
Collier, R. (2017). NHS ransom ware attack spreads worldwide.
Gupta, G., & Tripathi, K. (2017). STUDY ON RANSOM WARE ATTACK AND ITS
PREVENTION. International Education and Research Journal, 3(5).
Harris, M. T., & Kaplan, D. (2015). The Revenue Cycle. In The Complete Business Guide for
a Successful Medical Practice (pp. 107-119). Springer International Publishing.
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L., & Kirda, E. (2015, July). Cutting the
gordian knot: A look under the hood of ransom ware attacks. In International
Conference on Detection of Intrusions and Malware, and Vulnerability
Assessment (pp. 3-24). Springer, Cham.
Mohurle, S., & Patil, M. (2017). A brief study of Wannacry Threat: Ransom ware Attack
2017. International Journal, 8(5).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
ACCOUNTING INFORMATION SYSTEM
Pope, J. (2016). Ransom ware: Minimizing the Risks. Innovations in clinical
neuroscience, 13(11-12), 37.
Sittig, D. F., & Singh, H. (2016). A socio-technical approach to preventing, mitigating, and
recovering from ransom ware attacks. Applied clinical informatics, 7(2), 624.
Wells, S. T., & Bravender, R. (2016). Improving employee engagement in the revenue
cycle. Healthcare Financial Management, 70(10), 36-39.
ACCOUNTING INFORMATION SYSTEM
Pope, J. (2016). Ransom ware: Minimizing the Risks. Innovations in clinical
neuroscience, 13(11-12), 37.
Sittig, D. F., & Singh, H. (2016). A socio-technical approach to preventing, mitigating, and
recovering from ransom ware attacks. Applied clinical informatics, 7(2), 624.
Wells, S. T., & Bravender, R. (2016). Improving employee engagement in the revenue
cycle. Healthcare Financial Management, 70(10), 36-39.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





