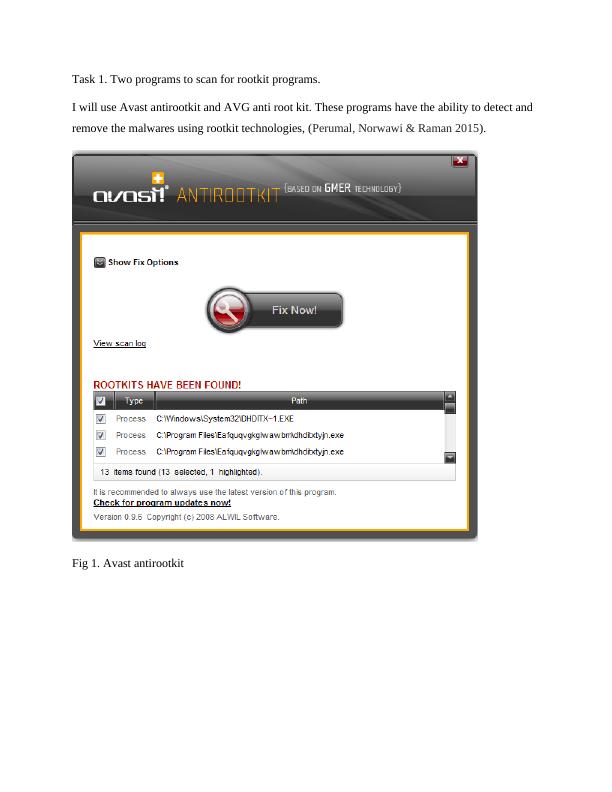
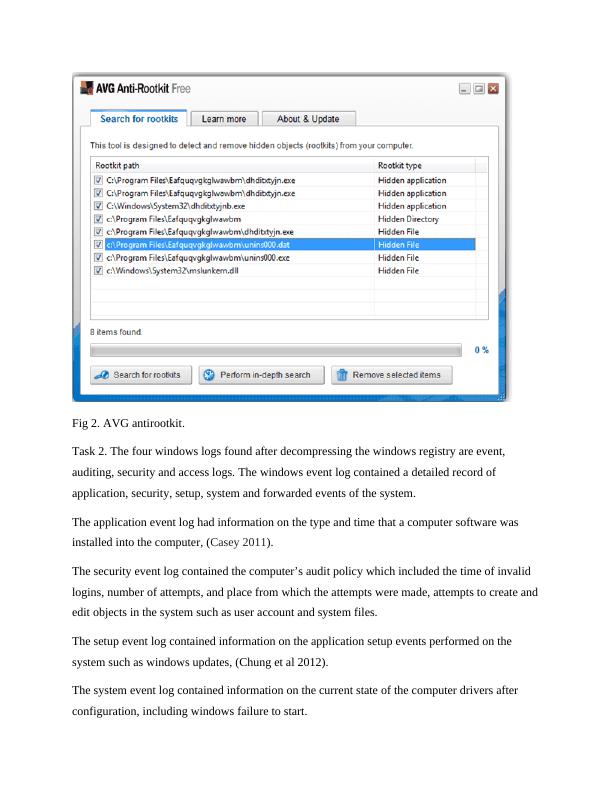
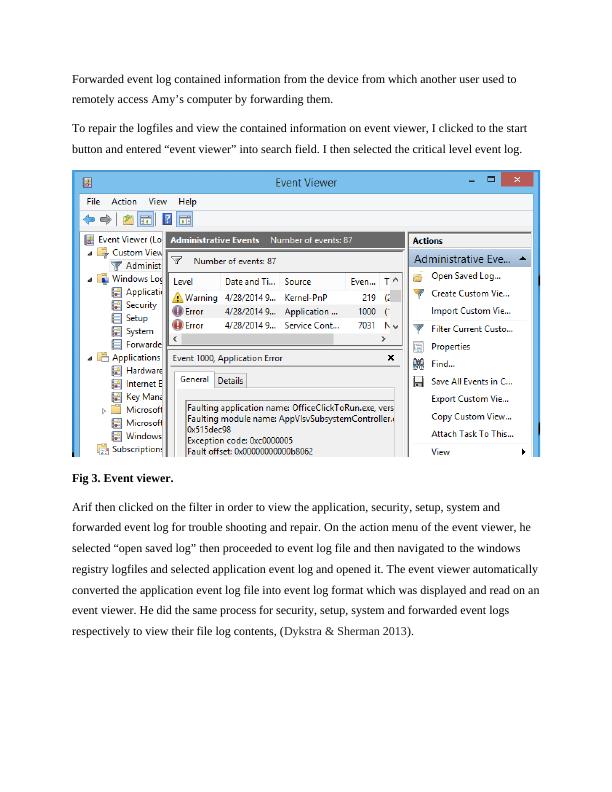
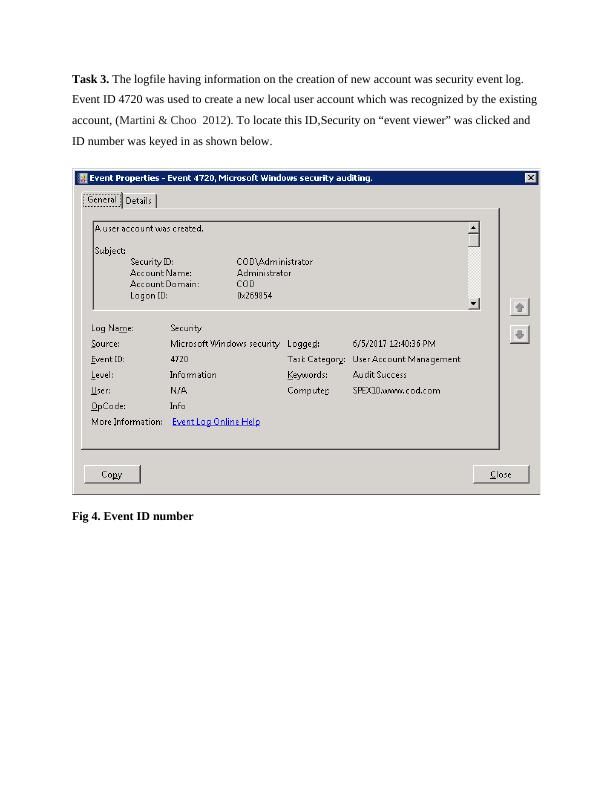
SIT703: Advanced Digital Forensics - Case Investigation Report
35 Pages2867 Words282 Views
Added on 2023-06-07
About This Document
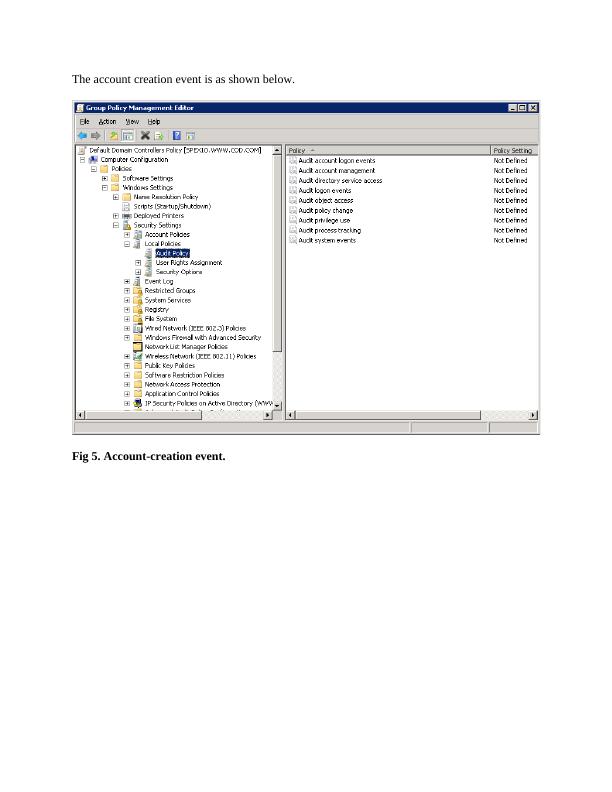
This case investigation report discusses unauthorized computer access, password cracking, and log files to track events and rectify the problem. It also covers programs to scan for rootkit programs, windows logs, cracking passwords, and more. The report is for SIT703: Advanced Digital Forensics course.
SIT703: Advanced Digital Forensics - Case Investigation Report
Added on 2023-06-07
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Assignment of Digital Forensics
|18
|1528
|292
Open Vulnerability Assessment System (OpenVAS)
|9
|1326
|180
Advanced Digital Forensics Investigation | Desklib
|31
|1904
|361
Audit Policy and Security Guidelines for Rouge Company
|5
|973
|230
Security Issues in Networking
|6
|1229
|54
Enhancing Network Security for NextGard: Best Practices and Recommendations
|11
|2582
|64