Advanced Network Management, Design and Security for YG
VerifiedAdded on 2023/05/29
|18
|4115
|318
Report
AI Summary
This report provides a comprehensive network solution for the Yotsuba Group (YG), focusing on replacing their outdated network and expanding their headquarters. It begins with requirement gathering and assumptions, detailing user needs and network scope. A detailed network proposal is presented, including device selection (Cisco ASA 5506 Firewall, Cisco 2811 Series Router, Cisco 3560 and 2960 switches, Cisco WRT300N Wireless Router, and Cisco 7960 IP Phones), physical topology, wiring, and device placement. The report includes an addressing scheme, justifying the design choices for efficient network communication and security. A network policy outlines user access and security protocols, while a section on network security threats and solutions identifies potential vulnerabilities like DoS attacks and identity spoofing, offering mitigation strategies. The document also covers network design strategies, risk identification, and a disaster management and contingency plan to ensure network uptime and performance. This solution focuses on creating a secure, efficient, and scalable network infrastructure for the Yotsuba Group.

Running head: ADVANCED NETWORK MANAGEMENT AND DESIGN
Advanced Network Management and Design
Name of the Student
Name of the University
Author’s Note
Advanced Network Management and Design
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
ADVANCED NETWORK MANAGEMENT AND DESIGN
Table of Contents
1. Introduction............................................................................................................................2
2. Requirement gathering and assumptions...............................................................................2
3. Network Proposal...................................................................................................................4
3.1. Device selection..............................................................................................................4
3.2. Physical Topology...........................................................................................................5
3.3. Wiring and device placement..........................................................................................5
4. Addressing Scheme................................................................................................................5
4.1. Justification of the design................................................................................................9
5. Network Policy.....................................................................................................................10
6. Network security Threats and solution................................................................................10
7. Network design strategies and plans....................................................................................12
8. Identification of potential risk..............................................................................................13
9. Disaster management and contingency plan........................................................................13
Bibliography.............................................................................................................................15
ADVANCED NETWORK MANAGEMENT AND DESIGN
Table of Contents
1. Introduction............................................................................................................................2
2. Requirement gathering and assumptions...............................................................................2
3. Network Proposal...................................................................................................................4
3.1. Device selection..............................................................................................................4
3.2. Physical Topology...........................................................................................................5
3.3. Wiring and device placement..........................................................................................5
4. Addressing Scheme................................................................................................................5
4.1. Justification of the design................................................................................................9
5. Network Policy.....................................................................................................................10
6. Network security Threats and solution................................................................................10
7. Network design strategies and plans....................................................................................12
8. Identification of potential risk..............................................................................................13
9. Disaster management and contingency plan........................................................................13
Bibliography.............................................................................................................................15

2
ADVANCED NETWORK MANAGEMENT AND DESIGN
1. Introduction
The network solution is developed for the Yotsuba Group (YG) for rep the old
network and expanding the companies headquarter in the new building. The company
currently faced different problems with their old network as they found the performance of
the network deteriorated and increase in the number of security incidents. The report is
created for the development of the requirement analysis and assuming the network device and
the wiring that is needed to be made for development of the network framework. A proposal
for the network is attached with the report including the network device, network topology
and wiring and placement of the network device and server for creating a secure network
infrastructure for the organization.
An addressing scheme is also prepared that would be needed for configuring the
network device interface. The number of users should be identified and a network policy is
developed for the management of the usage of the device and allowing or restricting them to
access the core network components. The network security threats acting on the network and
their solution is also documented in the report. Strategy that can be used for mitigating the
risk is given in the report that would help the increase the uptime of the network and provide
the best performance for the organization.
2. Requirement gathering and assumptions
For the development of the network solution the requirement of the network should be
identified on the terms of number of users using the network and the area needed to be
covered by the network. The security requirement and the number of subnets required for the
development of the network is needed to be identified for increasing the efficiency of the
network. The building floor plan should be analysed for the placement of the device and the
develop the cabling plan for connecting the network device and increasing the efficiency of
ADVANCED NETWORK MANAGEMENT AND DESIGN
1. Introduction
The network solution is developed for the Yotsuba Group (YG) for rep the old
network and expanding the companies headquarter in the new building. The company
currently faced different problems with their old network as they found the performance of
the network deteriorated and increase in the number of security incidents. The report is
created for the development of the requirement analysis and assuming the network device and
the wiring that is needed to be made for development of the network framework. A proposal
for the network is attached with the report including the network device, network topology
and wiring and placement of the network device and server for creating a secure network
infrastructure for the organization.
An addressing scheme is also prepared that would be needed for configuring the
network device interface. The number of users should be identified and a network policy is
developed for the management of the usage of the device and allowing or restricting them to
access the core network components. The network security threats acting on the network and
their solution is also documented in the report. Strategy that can be used for mitigating the
risk is given in the report that would help the increase the uptime of the network and provide
the best performance for the organization.
2. Requirement gathering and assumptions
For the development of the network solution the requirement of the network should be
identified on the terms of number of users using the network and the area needed to be
covered by the network. The security requirement and the number of subnets required for the
development of the network is needed to be identified for increasing the efficiency of the
network. The building floor plan should be analysed for the placement of the device and the
develop the cabling plan for connecting the network device and increasing the efficiency of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
ADVANCED NETWORK MANAGEMENT AND DESIGN
the network. The old network is analysed for finding the flaws in the network and incorporate
the network for increasing the compatibility of the network and secure it from the external
agents.
For gathering the requirement the interaction of the user with the network is needed to
be understand and the resources and the services essential for the network should be listed.
Information about the external and internal access of the services and the resources should
also be identified from the existing old network because without the knowledge about the
users accessing the network resources some of the requirement can be overlooked. A network
design should be designed based on the requirement and shared with the organization for its
approval. For the identification of the potential users the users should be grouped such as:
Filed office and branch staffs
Remote users
Suppliers. Partners and Vendors
Customers
Board members
The user access should be added by configuring the server connected in the network
such that the identity of the user is managed and the network resources are kept secured. The
network project should be based on the business goals of the organization and the business
managers should perform a feasibility analysis on the project for the identification of the
contribution of the project on the growth of the organization. The technical requirement of
the network should be defined for establishing the scope of the project and improving the
scalability, availability and performance of the network. It also helps in simplification of the
support and management. The network equipment needed for the development of the project
ADVANCED NETWORK MANAGEMENT AND DESIGN
the network. The old network is analysed for finding the flaws in the network and incorporate
the network for increasing the compatibility of the network and secure it from the external
agents.
For gathering the requirement the interaction of the user with the network is needed to
be understand and the resources and the services essential for the network should be listed.
Information about the external and internal access of the services and the resources should
also be identified from the existing old network because without the knowledge about the
users accessing the network resources some of the requirement can be overlooked. A network
design should be designed based on the requirement and shared with the organization for its
approval. For the identification of the potential users the users should be grouped such as:
Filed office and branch staffs
Remote users
Suppliers. Partners and Vendors
Customers
Board members
The user access should be added by configuring the server connected in the network
such that the identity of the user is managed and the network resources are kept secured. The
network project should be based on the business goals of the organization and the business
managers should perform a feasibility analysis on the project for the identification of the
contribution of the project on the growth of the organization. The technical requirement of
the network should be defined for establishing the scope of the project and improving the
scalability, availability and performance of the network. It also helps in simplification of the
support and management. The network equipment needed for the development of the project
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
ADVANCED NETWORK MANAGEMENT AND DESIGN
should be listed and the protocols that are needed for establishing the goals of the
organization should be identified for the implementation of the network services.
The following assumptions are made for the development of the network solution and
are given below:
For the configuration of the network multiple VLANs would be created with
the name of the department and the DHCP protocol should be used for the
allocation of the IP address to the device.
The users using the network would be have knowledge of using the network
and aware with the security policy of the organization.
The password of the wireless access point would be available only with the
organizational staffs
3. Network Proposal
3.1. Device selection
For the development of the network solution the following device are needed such as:
Cisco ASA 5506 Firewall x 2
Cisco 2811 Series Router x 1
Cisco 3560 24 PS Layer 3 Switch x1
Cisco 2960 24TT switch x 9
Cisco WRT300N Wireless Router x 1
Cisco 7960 IP Phone x max. 480
PC x max. 480
ADVANCED NETWORK MANAGEMENT AND DESIGN
should be listed and the protocols that are needed for establishing the goals of the
organization should be identified for the implementation of the network services.
The following assumptions are made for the development of the network solution and
are given below:
For the configuration of the network multiple VLANs would be created with
the name of the department and the DHCP protocol should be used for the
allocation of the IP address to the device.
The users using the network would be have knowledge of using the network
and aware with the security policy of the organization.
The password of the wireless access point would be available only with the
organizational staffs
3. Network Proposal
3.1. Device selection
For the development of the network solution the following device are needed such as:
Cisco ASA 5506 Firewall x 2
Cisco 2811 Series Router x 1
Cisco 3560 24 PS Layer 3 Switch x1
Cisco 2960 24TT switch x 9
Cisco WRT300N Wireless Router x 1
Cisco 7960 IP Phone x max. 480
PC x max. 480
5
ADVANCED NETWORK MANAGEMENT AND DESIGN
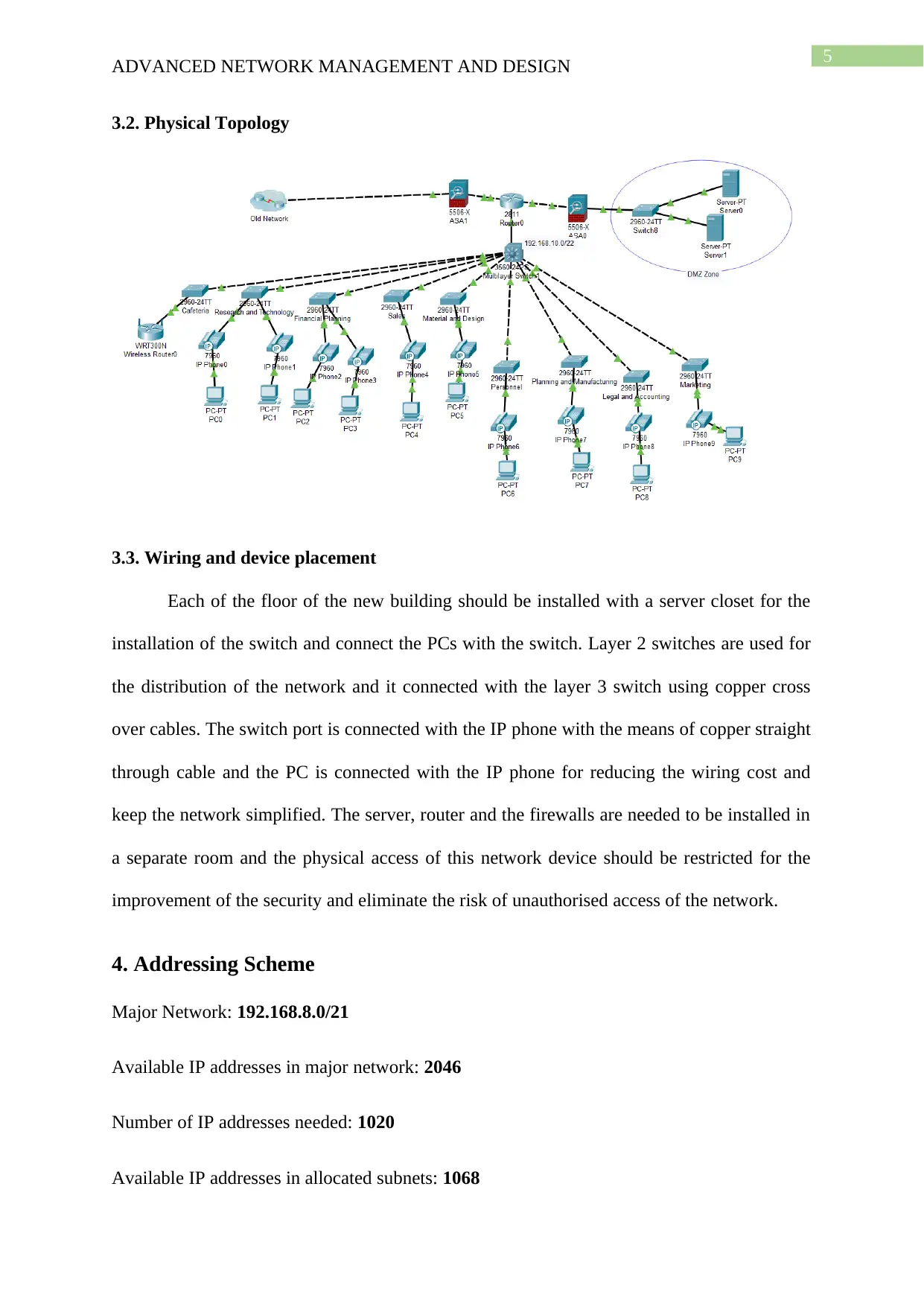
3.2. Physical Topology
3.3. Wiring and device placement
Each of the floor of the new building should be installed with a server closet for the
installation of the switch and connect the PCs with the switch. Layer 2 switches are used for
the distribution of the network and it connected with the layer 3 switch using copper cross
over cables. The switch port is connected with the IP phone with the means of copper straight
through cable and the PC is connected with the IP phone for reducing the wiring cost and
keep the network simplified. The server, router and the firewalls are needed to be installed in
a separate room and the physical access of this network device should be restricted for the
improvement of the security and eliminate the risk of unauthorised access of the network.
4. Addressing Scheme
Major Network: 192.168.8.0/21
Available IP addresses in major network: 2046
Number of IP addresses needed: 1020
Available IP addresses in allocated subnets: 1068
ADVANCED NETWORK MANAGEMENT AND DESIGN
3.2. Physical Topology
3.3. Wiring and device placement
Each of the floor of the new building should be installed with a server closet for the
installation of the switch and connect the PCs with the switch. Layer 2 switches are used for
the distribution of the network and it connected with the layer 3 switch using copper cross
over cables. The switch port is connected with the IP phone with the means of copper straight
through cable and the PC is connected with the IP phone for reducing the wiring cost and
keep the network simplified. The server, router and the firewalls are needed to be installed in
a separate room and the physical access of this network device should be restricted for the
improvement of the security and eliminate the risk of unauthorised access of the network.
4. Addressing Scheme
Major Network: 192.168.8.0/21
Available IP addresses in major network: 2046
Number of IP addresses needed: 1020
Available IP addresses in allocated subnets: 1068
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
ADVANCED NETWORK MANAGEMENT AND DESIGN
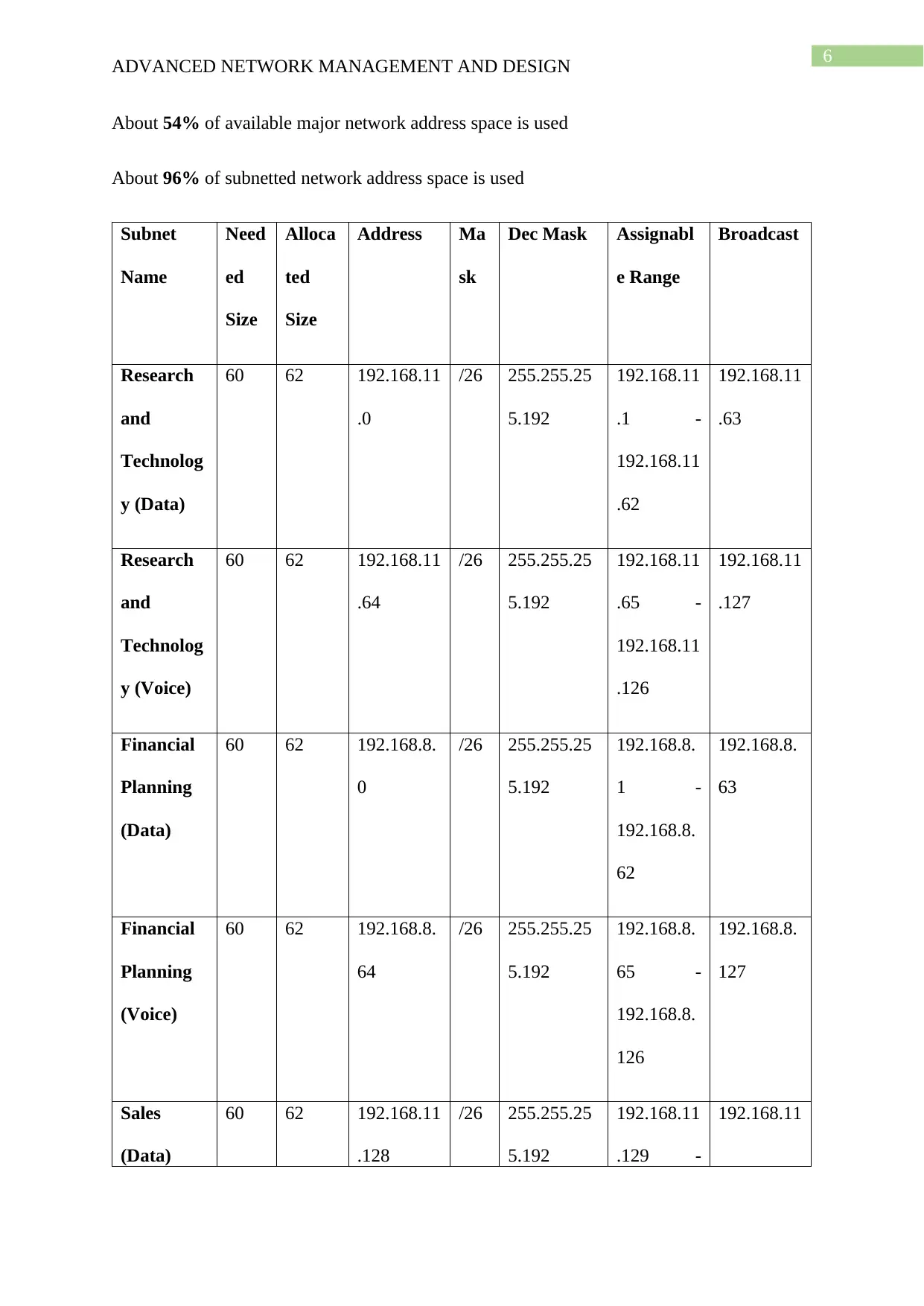
About 54% of available major network address space is used
About 96% of subnetted network address space is used
Subnet
Name
Need
ed
Size
Alloca
ted
Size
Address Ma
sk
Dec Mask Assignabl
e Range
Broadcast
Research
and
Technolog
y (Data)
60 62 192.168.11
.0
/26 255.255.25
5.192
192.168.11
.1 -
192.168.11
.62
192.168.11
.63
Research
and
Technolog
y (Voice)
60 62 192.168.11
.64
/26 255.255.25
5.192
192.168.11
.65 -
192.168.11
.126
192.168.11
.127
Financial
Planning
(Data)
60 62 192.168.8.
0
/26 255.255.25
5.192
192.168.8.
1 -
192.168.8.
62
192.168.8.
63
Financial
Planning
(Voice)
60 62 192.168.8.
64
/26 255.255.25
5.192
192.168.8.
65 -
192.168.8.
126
192.168.8.
127
Sales
(Data)
60 62 192.168.11
.128
/26 255.255.25
5.192
192.168.11
.129 -
192.168.11
ADVANCED NETWORK MANAGEMENT AND DESIGN
About 54% of available major network address space is used
About 96% of subnetted network address space is used
Subnet
Name
Need
ed
Size
Alloca
ted
Size
Address Ma
sk
Dec Mask Assignabl
e Range
Broadcast
Research
and
Technolog
y (Data)
60 62 192.168.11
.0
/26 255.255.25
5.192
192.168.11
.1 -
192.168.11
.62
192.168.11
.63
Research
and
Technolog
y (Voice)
60 62 192.168.11
.64
/26 255.255.25
5.192
192.168.11
.65 -
192.168.11
.126
192.168.11
.127
Financial
Planning
(Data)
60 62 192.168.8.
0
/26 255.255.25
5.192
192.168.8.
1 -
192.168.8.
62
192.168.8.
63
Financial
Planning
(Voice)
60 62 192.168.8.
64
/26 255.255.25
5.192
192.168.8.
65 -
192.168.8.
126
192.168.8.
127
Sales
(Data)
60 62 192.168.11
.128
/26 255.255.25
5.192
192.168.11
.129 -
192.168.11
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
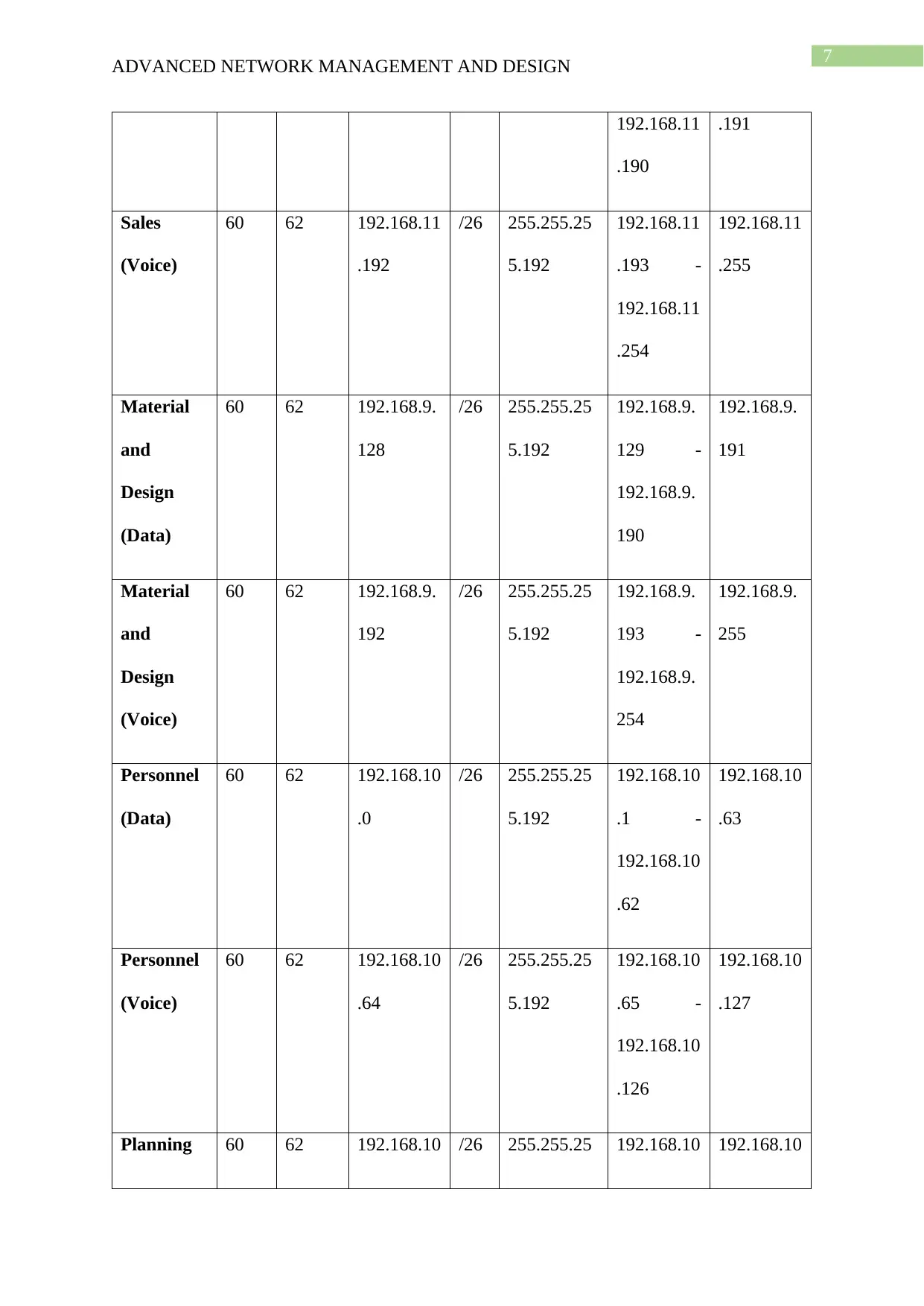
ADVANCED NETWORK MANAGEMENT AND DESIGN
192.168.11
.190
.191
Sales
(Voice)
60 62 192.168.11
.192
/26 255.255.25
5.192
192.168.11
.193 -
192.168.11
.254
192.168.11
.255
Material
and
Design
(Data)
60 62 192.168.9.
128
/26 255.255.25
5.192
192.168.9.
129 -
192.168.9.
190
192.168.9.
191
Material
and
Design
(Voice)
60 62 192.168.9.
192
/26 255.255.25
5.192
192.168.9.
193 -
192.168.9.
254
192.168.9.
255
Personnel
(Data)
60 62 192.168.10
.0
/26 255.255.25
5.192
192.168.10
.1 -
192.168.10
.62
192.168.10
.63
Personnel
(Voice)
60 62 192.168.10
.64
/26 255.255.25
5.192
192.168.10
.65 -
192.168.10
.126
192.168.10
.127
Planning 60 62 192.168.10 /26 255.255.25 192.168.10 192.168.10
ADVANCED NETWORK MANAGEMENT AND DESIGN
192.168.11
.190
.191
Sales
(Voice)
60 62 192.168.11
.192
/26 255.255.25
5.192
192.168.11
.193 -
192.168.11
.254
192.168.11
.255
Material
and
Design
(Data)
60 62 192.168.9.
128
/26 255.255.25
5.192
192.168.9.
129 -
192.168.9.
190
192.168.9.
191
Material
and
Design
(Voice)
60 62 192.168.9.
192
/26 255.255.25
5.192
192.168.9.
193 -
192.168.9.
254
192.168.9.
255
Personnel
(Data)
60 62 192.168.10
.0
/26 255.255.25
5.192
192.168.10
.1 -
192.168.10
.62
192.168.10
.63
Personnel
(Voice)
60 62 192.168.10
.64
/26 255.255.25
5.192
192.168.10
.65 -
192.168.10
.126
192.168.10
.127
Planning 60 62 192.168.10 /26 255.255.25 192.168.10 192.168.10
8
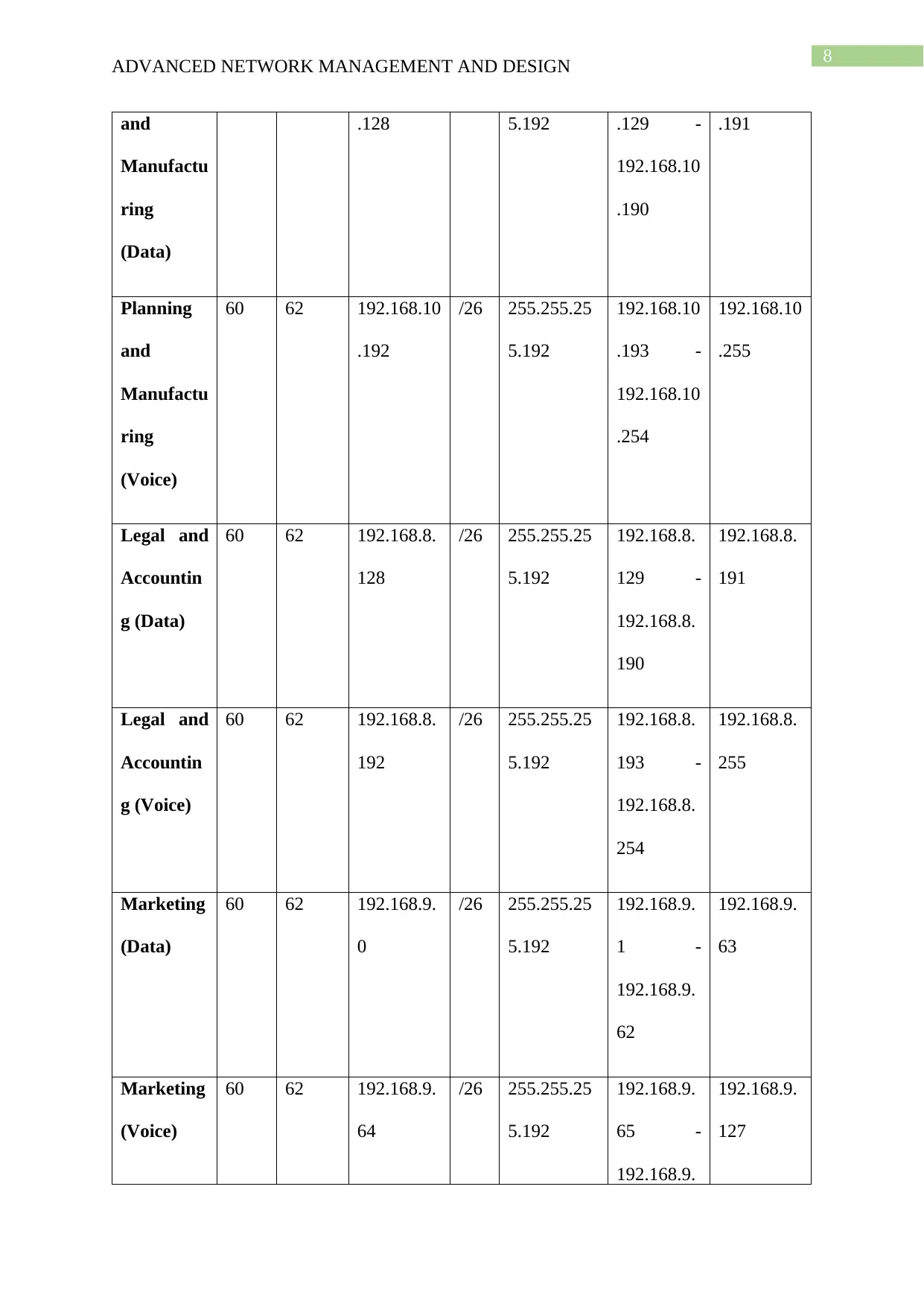
ADVANCED NETWORK MANAGEMENT AND DESIGN
and
Manufactu
ring
(Data)
.128 5.192 .129 -
192.168.10
.190
.191
Planning
and
Manufactu
ring
(Voice)
60 62 192.168.10
.192
/26 255.255.25
5.192
192.168.10
.193 -
192.168.10
.254
192.168.10
.255
Legal and
Accountin
g (Data)
60 62 192.168.8.
128
/26 255.255.25
5.192
192.168.8.
129 -
192.168.8.
190
192.168.8.
191
Legal and
Accountin
g (Voice)
60 62 192.168.8.
192
/26 255.255.25
5.192
192.168.8.
193 -
192.168.8.
254
192.168.8.
255
Marketing
(Data)
60 62 192.168.9.
0
/26 255.255.25
5.192
192.168.9.
1 -
192.168.9.
62
192.168.9.
63
Marketing
(Voice)
60 62 192.168.9.
64
/26 255.255.25
5.192
192.168.9.
65 -
192.168.9.
192.168.9.
127
ADVANCED NETWORK MANAGEMENT AND DESIGN
and
Manufactu
ring
(Data)
.128 5.192 .129 -
192.168.10
.190
.191
Planning
and
Manufactu
ring
(Voice)
60 62 192.168.10
.192
/26 255.255.25
5.192
192.168.10
.193 -
192.168.10
.254
192.168.10
.255
Legal and
Accountin
g (Data)
60 62 192.168.8.
128
/26 255.255.25
5.192
192.168.8.
129 -
192.168.8.
190
192.168.8.
191
Legal and
Accountin
g (Voice)
60 62 192.168.8.
192
/26 255.255.25
5.192
192.168.8.
193 -
192.168.8.
254
192.168.8.
255
Marketing
(Data)
60 62 192.168.9.
0
/26 255.255.25
5.192
192.168.9.
1 -
192.168.9.
62
192.168.9.
63
Marketing
(Voice)
60 62 192.168.9.
64
/26 255.255.25
5.192
192.168.9.
65 -
192.168.9.
192.168.9.
127
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
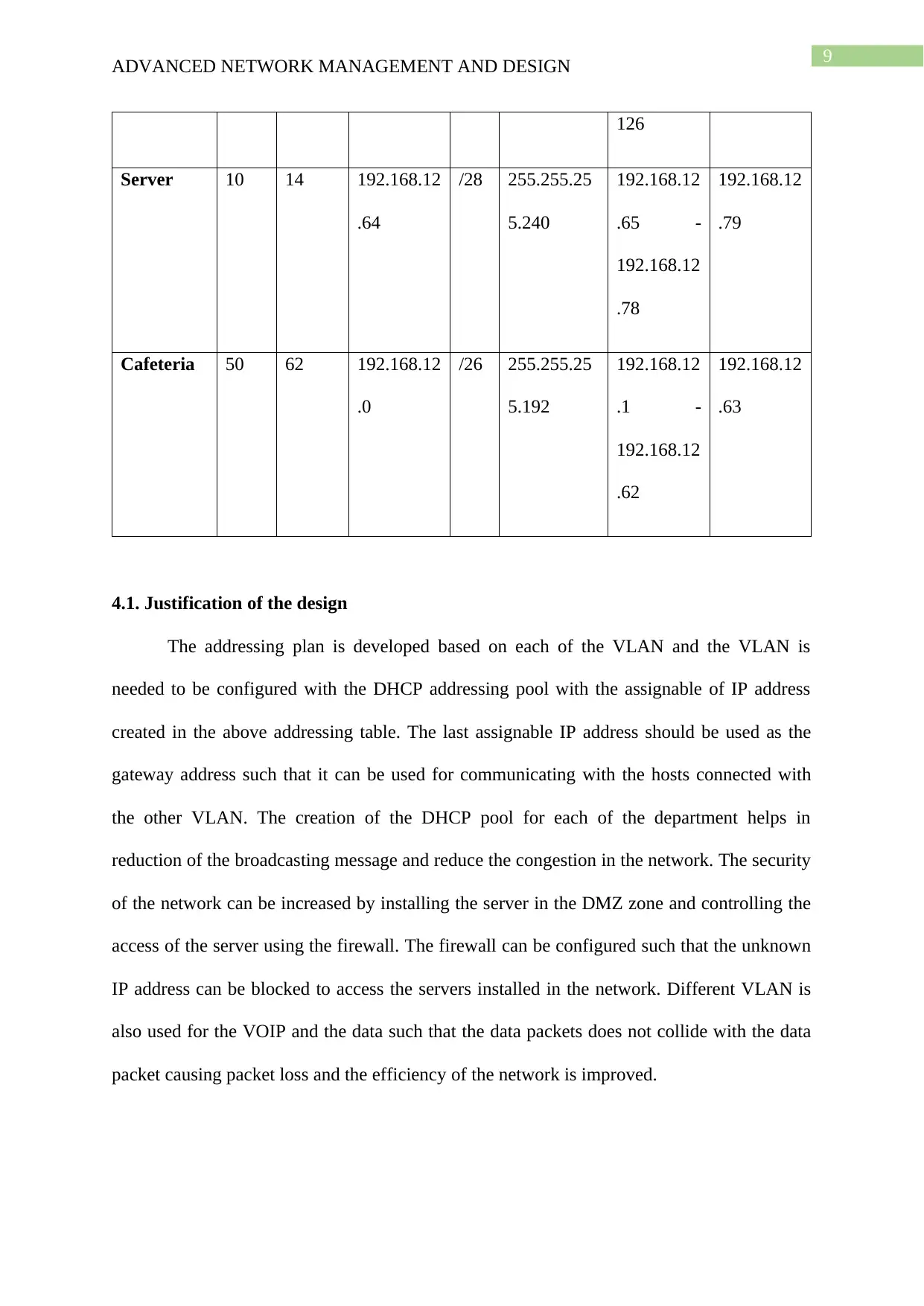
9
ADVANCED NETWORK MANAGEMENT AND DESIGN
126
Server 10 14 192.168.12
.64
/28 255.255.25
5.240
192.168.12
.65 -
192.168.12
.78
192.168.12
.79
Cafeteria 50 62 192.168.12
.0
/26 255.255.25
5.192
192.168.12
.1 -
192.168.12
.62
192.168.12
.63
4.1. Justification of the design
The addressing plan is developed based on each of the VLAN and the VLAN is
needed to be configured with the DHCP addressing pool with the assignable of IP address
created in the above addressing table. The last assignable IP address should be used as the
gateway address such that it can be used for communicating with the hosts connected with
the other VLAN. The creation of the DHCP pool for each of the department helps in
reduction of the broadcasting message and reduce the congestion in the network. The security
of the network can be increased by installing the server in the DMZ zone and controlling the
access of the server using the firewall. The firewall can be configured such that the unknown
IP address can be blocked to access the servers installed in the network. Different VLAN is
also used for the VOIP and the data such that the data packets does not collide with the data
packet causing packet loss and the efficiency of the network is improved.
ADVANCED NETWORK MANAGEMENT AND DESIGN
126
Server 10 14 192.168.12
.64
/28 255.255.25
5.240
192.168.12
.65 -
192.168.12
.78
192.168.12
.79
Cafeteria 50 62 192.168.12
.0
/26 255.255.25
5.192
192.168.12
.1 -
192.168.12
.62
192.168.12
.63
4.1. Justification of the design
The addressing plan is developed based on each of the VLAN and the VLAN is
needed to be configured with the DHCP addressing pool with the assignable of IP address
created in the above addressing table. The last assignable IP address should be used as the
gateway address such that it can be used for communicating with the hosts connected with
the other VLAN. The creation of the DHCP pool for each of the department helps in
reduction of the broadcasting message and reduce the congestion in the network. The security
of the network can be increased by installing the server in the DMZ zone and controlling the
access of the server using the firewall. The firewall can be configured such that the unknown
IP address can be blocked to access the servers installed in the network. Different VLAN is
also used for the VOIP and the data such that the data packets does not collide with the data
packet causing packet loss and the efficiency of the network is improved.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
ADVANCED NETWORK MANAGEMENT AND DESIGN
5. Network Policy
The network security policy should be created for the development of the new
network solution. The problems in the old network is analysed and the network is
troubleshooted for development of the policy. The policy is developed for controlling the
usage of the network and keep the malicious users outside the network such that they can not
cause any damage to the resources of the network. The policy is developed for outlining the
procedures and principles that should be followed by the user while accessing the network
(Dacier et al. 2017). It acts as a guideline for the user for managing, monitoring and
maintaining the security of the network designed for the organization. The network security
policy should consists of the following elements:
Legal procedure and rules for accessing the network
Management and governance of the internet and web
Implementation of the security procedures and configuration of the access
control list
Creation of privilege or role based policy for authorization and authentication
of the service provided to the user
6. Network security Threats and solution
There are different security threats acting on the network and they are needed to be
identified for the development of a secure network solution.
Denial of Service attack – In this attack the users connected in the network are denied
to reach the resource by overloading the resource with numerous requests (Jung, Ahn and Ko
2014). This type of attack is common and proper security measures should be taken for
mitigating the risk of DoS attack.
ADVANCED NETWORK MANAGEMENT AND DESIGN
5. Network Policy
The network security policy should be created for the development of the new
network solution. The problems in the old network is analysed and the network is
troubleshooted for development of the policy. The policy is developed for controlling the
usage of the network and keep the malicious users outside the network such that they can not
cause any damage to the resources of the network. The policy is developed for outlining the
procedures and principles that should be followed by the user while accessing the network
(Dacier et al. 2017). It acts as a guideline for the user for managing, monitoring and
maintaining the security of the network designed for the organization. The network security
policy should consists of the following elements:
Legal procedure and rules for accessing the network
Management and governance of the internet and web
Implementation of the security procedures and configuration of the access
control list
Creation of privilege or role based policy for authorization and authentication
of the service provided to the user
6. Network security Threats and solution
There are different security threats acting on the network and they are needed to be
identified for the development of a secure network solution.
Denial of Service attack – In this attack the users connected in the network are denied
to reach the resource by overloading the resource with numerous requests (Jung, Ahn and Ko
2014). This type of attack is common and proper security measures should be taken for
mitigating the risk of DoS attack.

11
ADVANCED NETWORK MANAGEMENT AND DESIGN
Brute force attack – It is used for getting the password of the system with the
application of trial and error mechanism. Once getting the server the intruder can get the
access of the system and the sensitive information about the organization.
Identity Spoofing – The user can use the IP address of a host connected in the
network for altering the data packet and appear as a regular host or the source address for
performing illegal activity.
Browser attack – The main target of this attack are the end users using the browser
and spreading to the whole organizational network (Pierce 2016). Malware can be
downloaded from the sites as fake update of software and infect the system.
SSL TLS attack – This attack is used for intercepting the data transmitted between the
hosts connected in the network. The unencrypted message can be accessed by the attacker
compromising the security of the network.
There are different technology that can be used for mitigation of the security issues
such as:
Penetration Test – In this test the network solution created for the organization is
needed to be hacked with the involvement of friendly hacker for the identification of the
vulnerability of the proposed system. The IT professional hired uses the same technique as
the hacker for the exploitation of the network and identification of the security issue.
Intrusion Detection – In this system the suspicious activity of the user can be
identified by tracking the unauthorised access of the user. For the examination of the
intrusion a malware scan is performed and the general network activity of the user is
reviewed. The vulnerability of the network is checked along with the illegal program installed
in different systems (Jackson et al. 2014). A monitoring is done on the file settings and other
activity of the user for detection of the malicious user.
ADVANCED NETWORK MANAGEMENT AND DESIGN
Brute force attack – It is used for getting the password of the system with the
application of trial and error mechanism. Once getting the server the intruder can get the
access of the system and the sensitive information about the organization.
Identity Spoofing – The user can use the IP address of a host connected in the
network for altering the data packet and appear as a regular host or the source address for
performing illegal activity.
Browser attack – The main target of this attack are the end users using the browser
and spreading to the whole organizational network (Pierce 2016). Malware can be
downloaded from the sites as fake update of software and infect the system.
SSL TLS attack – This attack is used for intercepting the data transmitted between the
hosts connected in the network. The unencrypted message can be accessed by the attacker
compromising the security of the network.
There are different technology that can be used for mitigation of the security issues
such as:
Penetration Test – In this test the network solution created for the organization is
needed to be hacked with the involvement of friendly hacker for the identification of the
vulnerability of the proposed system. The IT professional hired uses the same technique as
the hacker for the exploitation of the network and identification of the security issue.
Intrusion Detection – In this system the suspicious activity of the user can be
identified by tracking the unauthorised access of the user. For the examination of the
intrusion a malware scan is performed and the general network activity of the user is
reviewed. The vulnerability of the network is checked along with the illegal program installed
in different systems (Jackson et al. 2014). A monitoring is done on the file settings and other
activity of the user for detection of the malicious user.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





