COIT20262 Advanced Network Security: Cryptography, HTTPS, and More
VerifiedAdded on 2023/06/11
|10
|1404
|169
Homework Assignment
AI Summary
This assignment solution delves into advanced network security concepts, covering cryptographic operations using OpenSSL, HTTPS and certificate analysis, Linux access control mechanisms, firewall configurations, and wireless network security recommendations. It includes practical exercises such as generating RSA key pairs, signing messages, setting up web servers with HTTPS, and analyzing network traffic. The solution also provides insights into firewall rules for TCP traffic, security features for wireless access points, and suggestions for securing a wireless network in a business environment. Supporting files, including configuration files, diagrams, and captured network traffic, are referenced throughout the document. Desklib provides similar solved assignments and study tools for students.

Advanced Network Security
NAME:
REGISTER ID:
GUIDE:
SUBMISSION DATE:
NAME:
REGISTER ID:
GUIDE:
SUBMISSION DATE:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Cryptographic Operations with Open SSL..............................................................................................................1
2. HTTPS and Certificates........................................................................................................................................... 1
3. Access Control......................................................................................................................................................... 4
4. Firewalls.................................................................................................................................................................. 4
5. Wireless Network Security....................................................................................................................................... 6
References........................................................................................................................................................................ 7
1. Cryptographic Operations with Open SSL..............................................................................................................1
2. HTTPS and Certificates........................................................................................................................................... 1
3. Access Control......................................................................................................................................................... 4
4. Firewalls.................................................................................................................................................................. 4
5. Wireless Network Security....................................................................................................................................... 6
References........................................................................................................................................................................ 7

1. Cryptographic Operations with Open SSL
The cryptographic operation is performed using Open SSL as follows (Sawant et al., 2017):
1) Recording the commands.
2) Generating the RSA key pair.
3) Creating a new message or a plain text.
4) Extracting user public key.
5) Signing the created message file.
6) Generating 128 bit random values.
7) Encrypting the key text file with the help of RAS algorithm.
8) Encrypting the message file.
All the files are zipped and attached below.
2. HTTPS and Certificates
For studying about HTTPs and certificate, the virtual network is utilized, as it executes the below
listed operations:
1) In the virtual network, it creates four topologies.
2) It setups the web server for assisting HTTPS.
3) It deploys the website.
4) It captures traffic from the web server.
5) It analyzes and tests HTTPS connections.
For obtaining the certificate authority, the web server setup is utilized, which encompasses the
activities like- Generating the Signing Request and Sending the certificate signing request.
a) Answer:
1
The cryptographic operation is performed using Open SSL as follows (Sawant et al., 2017):
1) Recording the commands.
2) Generating the RSA key pair.
3) Creating a new message or a plain text.
4) Extracting user public key.
5) Signing the created message file.
6) Generating 128 bit random values.
7) Encrypting the key text file with the help of RAS algorithm.
8) Encrypting the message file.
All the files are zipped and attached below.
2. HTTPS and Certificates
For studying about HTTPs and certificate, the virtual network is utilized, as it executes the below
listed operations:
1) In the virtual network, it creates four topologies.
2) It setups the web server for assisting HTTPS.
3) It deploys the website.
4) It captures traffic from the web server.
5) It analyzes and tests HTTPS connections.
For obtaining the certificate authority, the web server setup is utilized, which encompasses the
activities like- Generating the Signing Request and Sending the certificate signing request.
a) Answer:
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
The supporting setup web server files are attached as a zipped file (Lin, Tsudik and Wang,
2011).
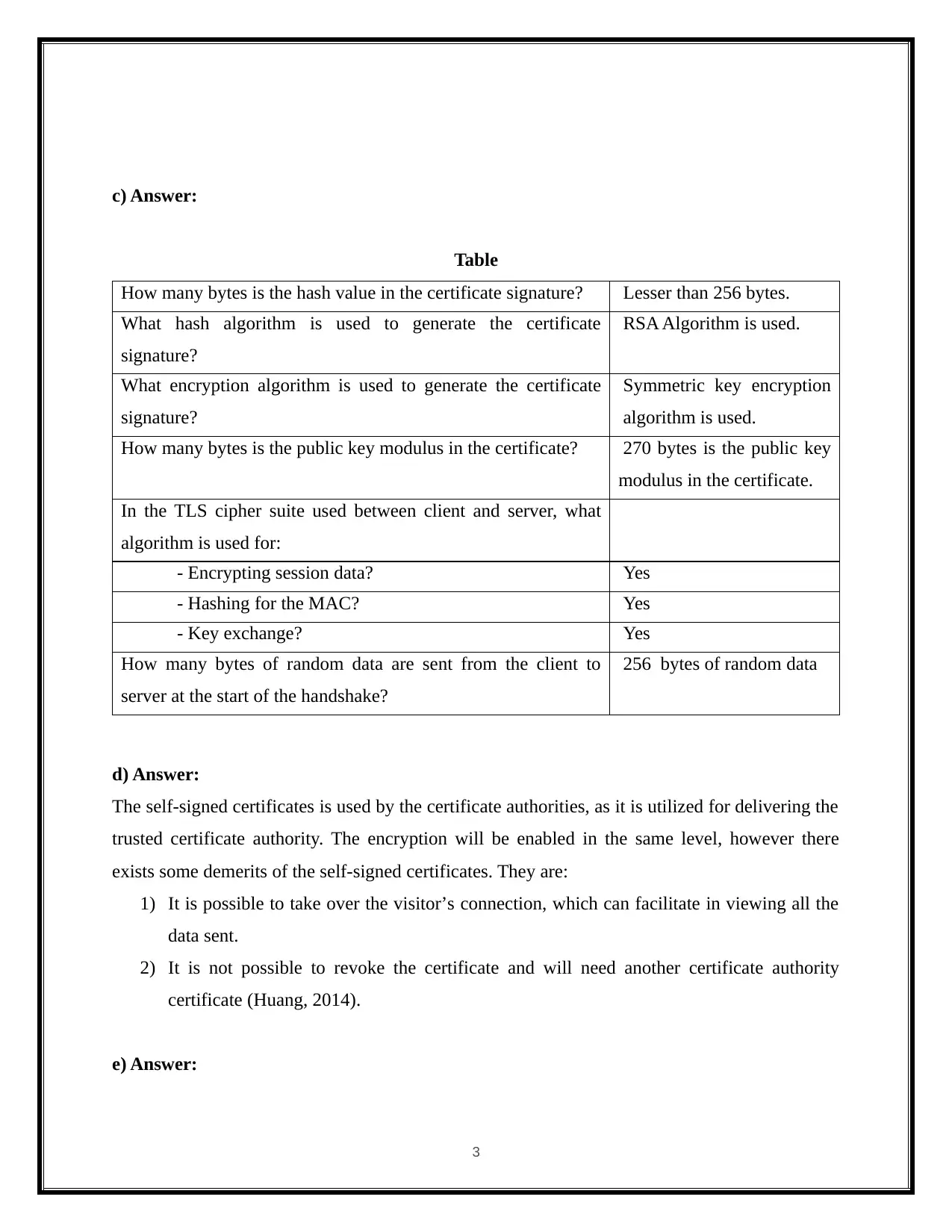
b) Message Sequence Diagram
Figure: Message Sequence Diagram
2
2011).
b) Message Sequence Diagram
Figure: Message Sequence Diagram
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
c) Answer:
Table
How many bytes is the hash value in the certificate signature? Lesser than 256 bytes.
What hash algorithm is used to generate the certificate
signature?
RSA Algorithm is used.
What encryption algorithm is used to generate the certificate
signature?
Symmetric key encryption
algorithm is used.
How many bytes is the public key modulus in the certificate? 270 bytes is the public key
modulus in the certificate.
In the TLS cipher suite used between client and server, what
algorithm is used for:
- Encrypting session data? Yes
- Hashing for the MAC? Yes
- Key exchange? Yes
How many bytes of random data are sent from the client to
server at the start of the handshake?
256 bytes of random data
d) Answer:
The self-signed certificates is used by the certificate authorities, as it is utilized for delivering the
trusted certificate authority. The encryption will be enabled in the same level, however there
exists some demerits of the self-signed certificates. They are:
1) It is possible to take over the visitor’s connection, which can facilitate in viewing all the
data sent.
2) It is not possible to revoke the certificate and will need another certificate authority
certificate (Huang, 2014).
e) Answer:
3
Table
How many bytes is the hash value in the certificate signature? Lesser than 256 bytes.
What hash algorithm is used to generate the certificate
signature?
RSA Algorithm is used.
What encryption algorithm is used to generate the certificate
signature?
Symmetric key encryption
algorithm is used.
How many bytes is the public key modulus in the certificate? 270 bytes is the public key
modulus in the certificate.
In the TLS cipher suite used between client and server, what
algorithm is used for:
- Encrypting session data? Yes
- Hashing for the MAC? Yes
- Key exchange? Yes
How many bytes of random data are sent from the client to
server at the start of the handshake?
256 bytes of random data
d) Answer:
The self-signed certificates is used by the certificate authorities, as it is utilized for delivering the
trusted certificate authority. The encryption will be enabled in the same level, however there
exists some demerits of the self-signed certificates. They are:
1) It is possible to take over the visitor’s connection, which can facilitate in viewing all the
data sent.
2) It is not possible to revoke the certificate and will need another certificate authority
certificate (Huang, 2014).
e) Answer:
3
It is necessary that the certificate authorities should provide security for the private key. It is
possible when the private keys are stored offline with the help of special hardware devices. At
times it is observed that the hackers are making use of the certificate authority private, as it fails
to identify and verify the certificate applicant.
3. Access Control
To study the Linux access control and passwords, the virtual network is used.
a) Answer
All the files are zipped and attached as follows.
b) Answer
As usual, the information of the user are stored by the Linux distribution in, /etc/passwd, which
comprises of user login, unique numerical user id, optional comment field, numerical group id
and encrypted password information. The exception is that, the encrypted password will never be
stored here, instead it will be stored in /etc/shadow file, and the encrypted password will be
stored in /etc/passwd, which only the super user can read (Sardana, 2011).
c) Answer
Four types of access controls are available.
The mandatory based access control is the strictest of all level of controls. Hierarchical approach
is used to control the resource access. The role based access control is utilised for taking a real
world approach for structuring the access control. The computer system belong depending on the
user’s job function in the organization.
4. Firewalls
a) Answer
4
possible when the private keys are stored offline with the help of special hardware devices. At
times it is observed that the hackers are making use of the certificate authority private, as it fails
to identify and verify the certificate applicant.
3. Access Control
To study the Linux access control and passwords, the virtual network is used.
a) Answer
All the files are zipped and attached as follows.
b) Answer
As usual, the information of the user are stored by the Linux distribution in, /etc/passwd, which
comprises of user login, unique numerical user id, optional comment field, numerical group id
and encrypted password information. The exception is that, the encrypted password will never be
stored here, instead it will be stored in /etc/shadow file, and the encrypted password will be
stored in /etc/passwd, which only the super user can read (Sardana, 2011).
c) Answer
Four types of access controls are available.
The mandatory based access control is the strictest of all level of controls. Hierarchical approach
is used to control the resource access. The role based access control is utilised for taking a real
world approach for structuring the access control. The computer system belong depending on the
user’s job function in the organization.
4. Firewalls
a) Answer
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
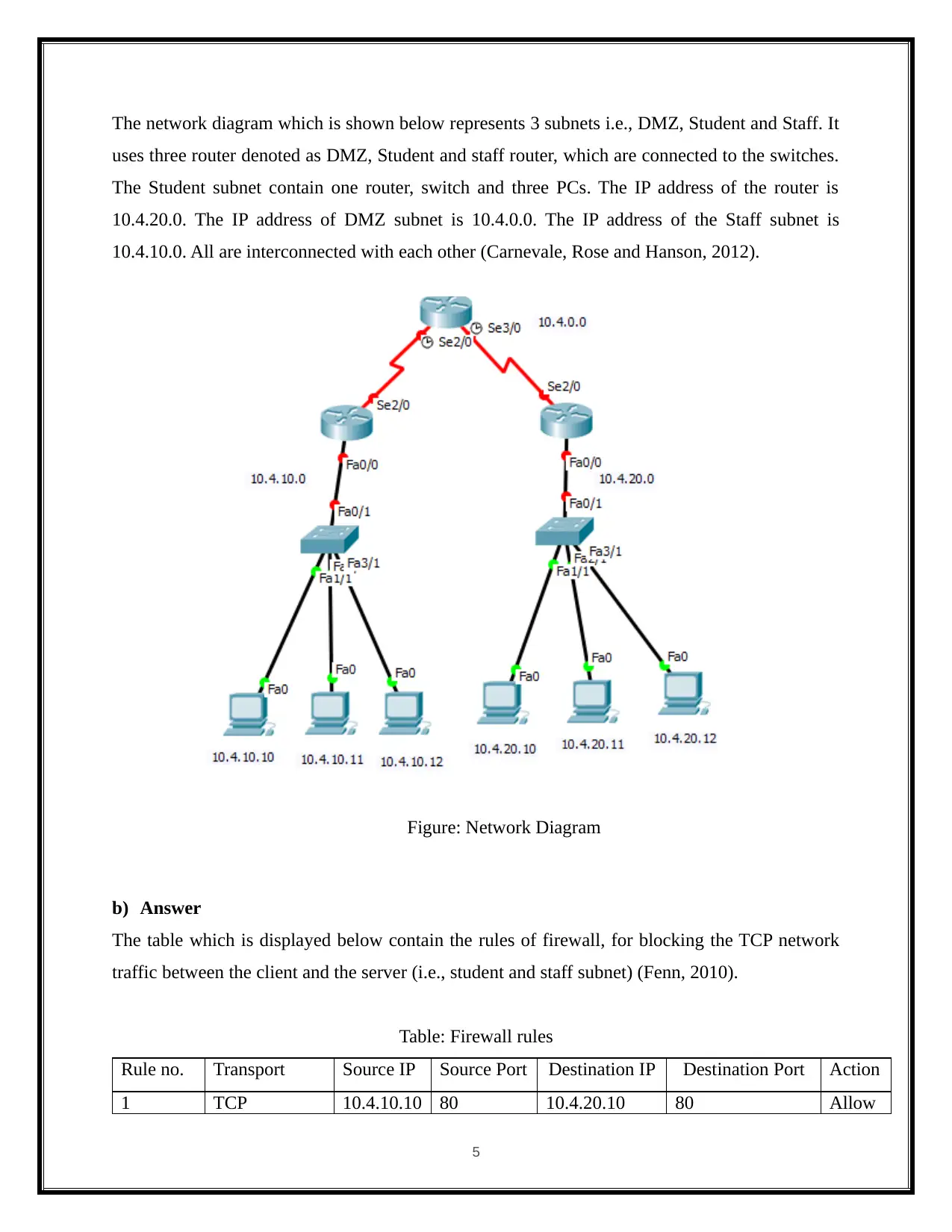
The network diagram which is shown below represents 3 subnets i.e., DMZ, Student and Staff. It
uses three router denoted as DMZ, Student and staff router, which are connected to the switches.
The Student subnet contain one router, switch and three PCs. The IP address of the router is
10.4.20.0. The IP address of DMZ subnet is 10.4.0.0. The IP address of the Staff subnet is
10.4.10.0. All are interconnected with each other (Carnevale, Rose and Hanson, 2012).
Figure: Network Diagram
b) Answer
The table which is displayed below contain the rules of firewall, for blocking the TCP network
traffic between the client and the server (i.e., student and staff subnet) (Fenn, 2010).
Table: Firewall rules
Rule no. Transport Source IP Source Port Destination IP Destination Port Action
1 TCP 10.4.10.10 80 10.4.20.10 80 Allow
5
uses three router denoted as DMZ, Student and staff router, which are connected to the switches.
The Student subnet contain one router, switch and three PCs. The IP address of the router is
10.4.20.0. The IP address of DMZ subnet is 10.4.0.0. The IP address of the Staff subnet is
10.4.10.0. All are interconnected with each other (Carnevale, Rose and Hanson, 2012).
Figure: Network Diagram
b) Answer
The table which is displayed below contain the rules of firewall, for blocking the TCP network
traffic between the client and the server (i.e., student and staff subnet) (Fenn, 2010).
Table: Firewall rules
Rule no. Transport Source IP Source Port Destination IP Destination Port Action
1 TCP 10.4.10.10 80 10.4.20.10 80 Allow
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
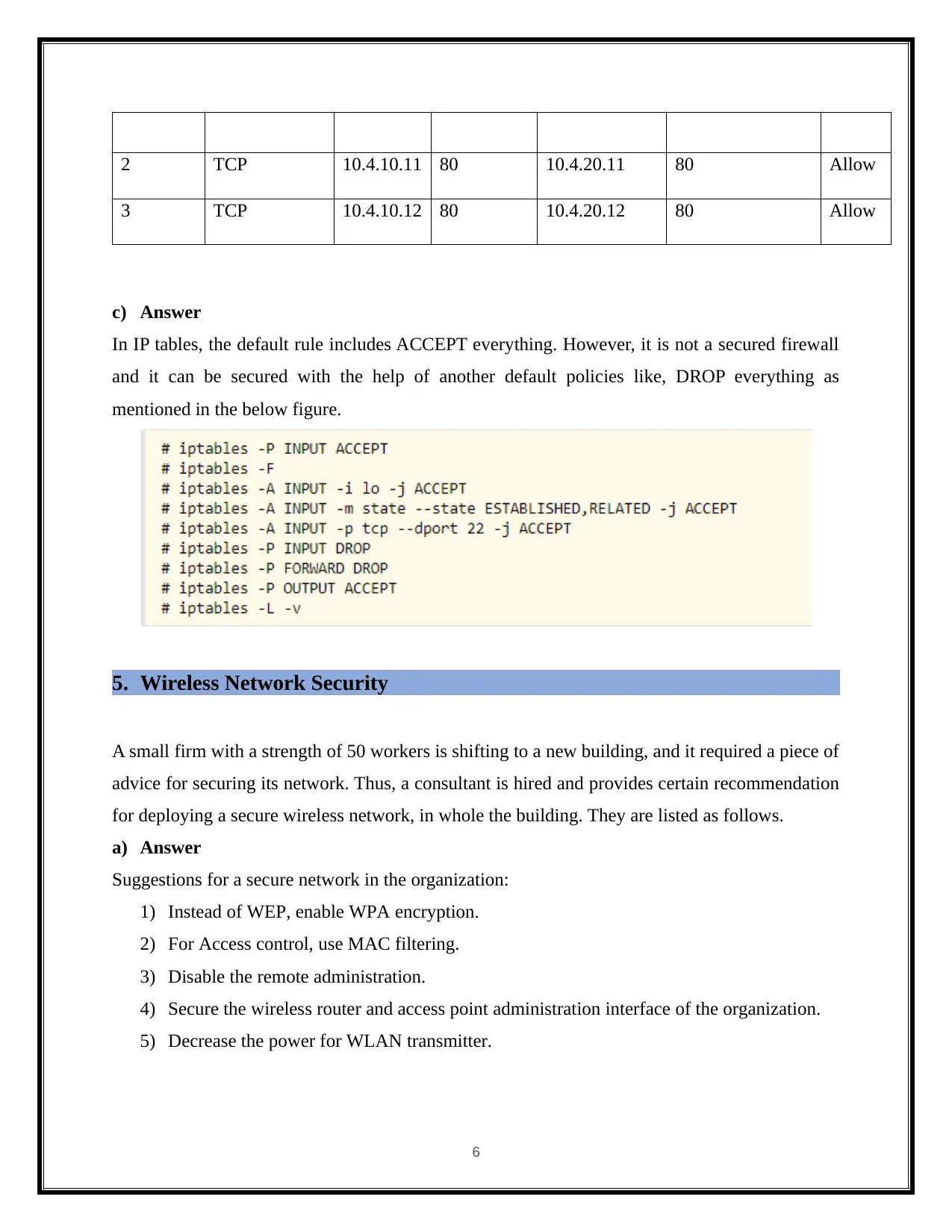
2 TCP 10.4.10.11 80 10.4.20.11 80 Allow
3 TCP 10.4.10.12 80 10.4.20.12 80 Allow
c) Answer
In IP tables, the default rule includes ACCEPT everything. However, it is not a secured firewall
and it can be secured with the help of another default policies like, DROP everything as
mentioned in the below figure.
5. Wireless Network Security
A small firm with a strength of 50 workers is shifting to a new building, and it required a piece of
advice for securing its network. Thus, a consultant is hired and provides certain recommendation
for deploying a secure wireless network, in whole the building. They are listed as follows.
a) Answer
Suggestions for a secure network in the organization:
1) Instead of WEP, enable WPA encryption.
2) For Access control, use MAC filtering.
3) Disable the remote administration.
4) Secure the wireless router and access point administration interface of the organization.
5) Decrease the power for WLAN transmitter.
6
3 TCP 10.4.10.12 80 10.4.20.12 80 Allow
c) Answer
In IP tables, the default rule includes ACCEPT everything. However, it is not a secured firewall
and it can be secured with the help of another default policies like, DROP everything as
mentioned in the below figure.
5. Wireless Network Security
A small firm with a strength of 50 workers is shifting to a new building, and it required a piece of
advice for securing its network. Thus, a consultant is hired and provides certain recommendation
for deploying a secure wireless network, in whole the building. They are listed as follows.
a) Answer
Suggestions for a secure network in the organization:
1) Instead of WEP, enable WPA encryption.
2) For Access control, use MAC filtering.
3) Disable the remote administration.
4) Secure the wireless router and access point administration interface of the organization.
5) Decrease the power for WLAN transmitter.
6

b) Answer
It is suggested by the consultant, to select the D - Link wireless access point. As, it is utilized for
providing the network connectivity solution for the business of small and medium size. The D -
Link is the corporate name of the manufacturer and is designed with networking, digital and
broadband solutions, voice and data communications.
c) Answer
For D – Link, the security features are listed below:
1) Robust security
2) MAC address filtering
3) ARP spoofing prevention
4) WLAN partition
5) Web redirection
6) Internal RADIUS server
7) Network access protection
7
It is suggested by the consultant, to select the D - Link wireless access point. As, it is utilized for
providing the network connectivity solution for the business of small and medium size. The D -
Link is the corporate name of the manufacturer and is designed with networking, digital and
broadband solutions, voice and data communications.
c) Answer
For D – Link, the security features are listed below:
1) Robust security
2) MAC address filtering
3) ARP spoofing prevention
4) WLAN partition
5) Web redirection
6) Internal RADIUS server
7) Network access protection
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Carnevale, A., Rose, S. and Hanson, A. (2012). Certificates. Washington, D.C.: Georgetown
University, Center on Education and the Workforce.
Fenn, D. (2010). Access control. Teddington, Richmond Upon Thames [England]: Key Note Ltd.
Huang, S. (2014). Network security. [Place of publication not identified]: Springer.
Lin, D., Tsudik, G. and Wang, X. (2011). Cryptology and network security. Berlin: Springer.
Sardana, S. (2011). Handbook on C++ language. New Delhi: Firewal Media.
Sawant, U., Pelz, O., Hobson, J. and Leemans, W. (2017). Linux. Birmingham: Packt Publishing.
8
Carnevale, A., Rose, S. and Hanson, A. (2012). Certificates. Washington, D.C.: Georgetown
University, Center on Education and the Workforce.
Fenn, D. (2010). Access control. Teddington, Richmond Upon Thames [England]: Key Note Ltd.
Huang, S. (2014). Network security. [Place of publication not identified]: Springer.
Lin, D., Tsudik, G. and Wang, X. (2011). Cryptology and network security. Berlin: Springer.
Sardana, S. (2011). Handbook on C++ language. New Delhi: Firewal Media.
Sawant, U., Pelz, O., Hobson, J. and Leemans, W. (2017). Linux. Birmingham: Packt Publishing.
8
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



