Advanced Network Security: Cryptography, Access Control, Firewalls, and Wireless Network Security
VerifiedAdded on 2023/06/11
|11
|1783
|206
AI Summary
This article covers advanced network security topics such as cryptography, access control, firewalls, and wireless network security. It includes practical exercises and recommendations for securing organizational networks. The article also provides references for further reading.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Advanced Network Security
Name:
Register Id:
Guide:
Name:
Register Id:
Guide:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Question 1: Cryptographic Operations with Open SSL.....................................................................................................1
Question 2: HTTPS and Certificates................................................................................................................................. 1
Question 3: Access Control............................................................................................................................................... 4
Question 4: Firewalls........................................................................................................................................................ 5
Question 5: Wireless Network Security............................................................................................................................. 7
References........................................................................................................................................................................ 9
Question 1: Cryptographic Operations with Open SSL.....................................................................................................1
Question 2: HTTPS and Certificates................................................................................................................................. 1
Question 3: Access Control............................................................................................................................................... 4
Question 4: Firewalls........................................................................................................................................................ 5
Question 5: Wireless Network Security............................................................................................................................. 7
References........................................................................................................................................................................ 9

Question 1: Cryptographic Operations with Open SSL
Answer:
The Open SSL is used for performing the cryptographic operations (Cems.uwe.ac.uk,
2018). It operation performed are listed below:
a) The commands are recorded.
b) RSA key pair are generated.
c) User public key is extracted.
d) New message is created.
e) Created message file is signed.
f) 128 bit random value is generated.
g) Message file is encrypted.
h) Using RAS algorithms, even encrypt the key text file.
The files are attached below (Raymii.org, 2018).
Question 2: HTTPS and Certificates
Answer:
Virtual network is used for learning about HTTPS and certificate. The following
operations are performed:
1) Create topology 4 in the virtual network.
2) Deploy a website.
3) Setup the web server in order to support HTTPS.
4) Capture the traffic from web server.
5) HTTPS connection is analyze and tested.
To receive the certificate authority, the setup of web server is used, where the activities such as,
generating the Signing Request and Sending the certificate signing request is involved
(Krisjordan.com, 2018).
1
Answer:
The Open SSL is used for performing the cryptographic operations (Cems.uwe.ac.uk,
2018). It operation performed are listed below:
a) The commands are recorded.
b) RSA key pair are generated.
c) User public key is extracted.
d) New message is created.
e) Created message file is signed.
f) 128 bit random value is generated.
g) Message file is encrypted.
h) Using RAS algorithms, even encrypt the key text file.
The files are attached below (Raymii.org, 2018).
Question 2: HTTPS and Certificates
Answer:
Virtual network is used for learning about HTTPS and certificate. The following
operations are performed:
1) Create topology 4 in the virtual network.
2) Deploy a website.
3) Setup the web server in order to support HTTPS.
4) Capture the traffic from web server.
5) HTTPS connection is analyze and tested.
To receive the certificate authority, the setup of web server is used, where the activities such as,
generating the Signing Request and Sending the certificate signing request is involved
(Krisjordan.com, 2018).
1

a) Answer:
Setup web server files are attached below.
b) Answer:
Figure: Message Sequence Diagram
c) Answer:
2
Setup web server files are attached below.
b) Answer:
Figure: Message Sequence Diagram
c) Answer:
2
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
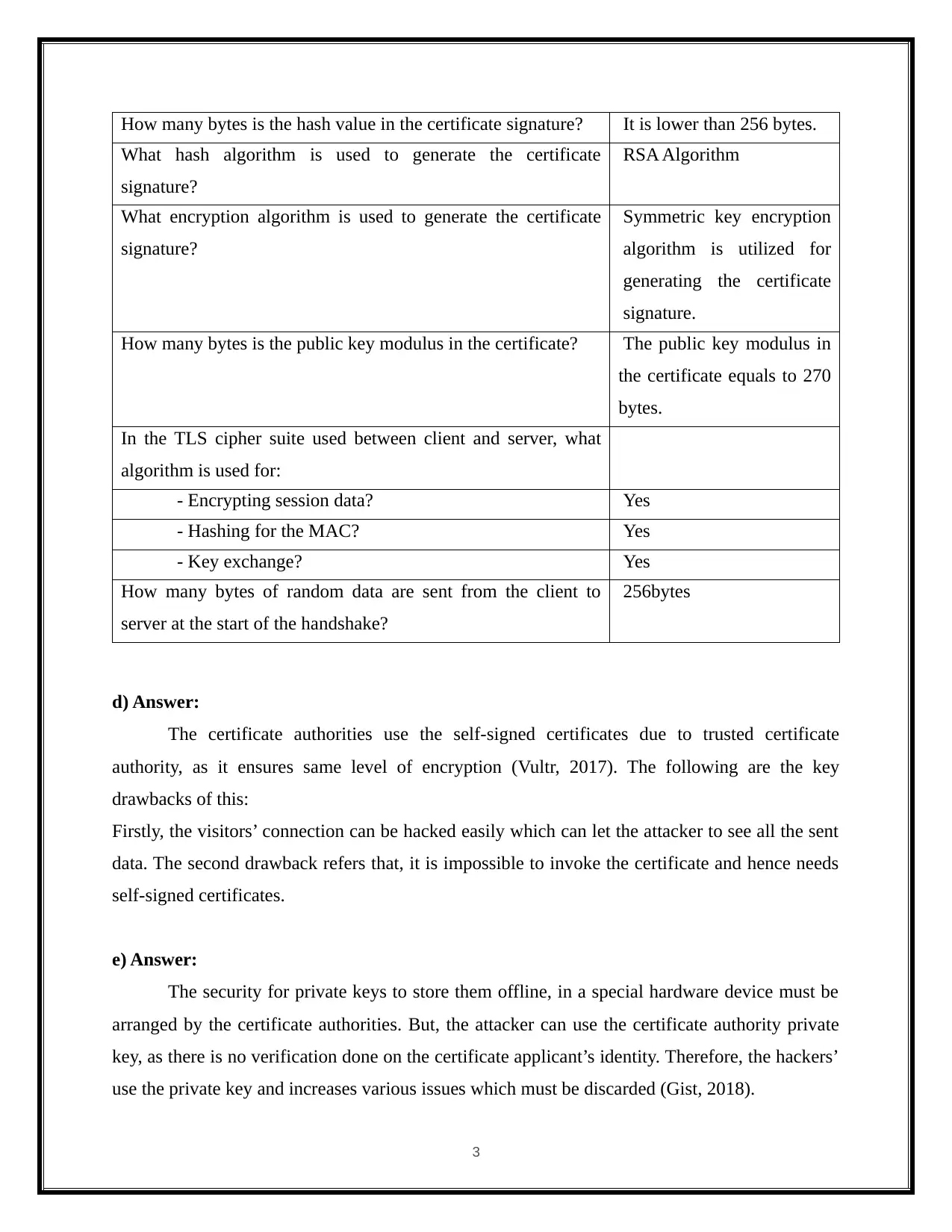
How many bytes is the hash value in the certificate signature? It is lower than 256 bytes.
What hash algorithm is used to generate the certificate
signature?
RSA Algorithm
What encryption algorithm is used to generate the certificate
signature?
Symmetric key encryption
algorithm is utilized for
generating the certificate
signature.
How many bytes is the public key modulus in the certificate? The public key modulus in
the certificate equals to 270
bytes.
In the TLS cipher suite used between client and server, what
algorithm is used for:
- Encrypting session data? Yes
- Hashing for the MAC? Yes
- Key exchange? Yes
How many bytes of random data are sent from the client to
server at the start of the handshake?
256bytes
d) Answer:
The certificate authorities use the self-signed certificates due to trusted certificate
authority, as it ensures same level of encryption (Vultr, 2017). The following are the key
drawbacks of this:
Firstly, the visitors’ connection can be hacked easily which can let the attacker to see all the sent
data. The second drawback refers that, it is impossible to invoke the certificate and hence needs
self-signed certificates.
e) Answer:
The security for private keys to store them offline, in a special hardware device must be
arranged by the certificate authorities. But, the attacker can use the certificate authority private
key, as there is no verification done on the certificate applicant’s identity. Therefore, the hackers’
use the private key and increases various issues which must be discarded (Gist, 2018).
3
What hash algorithm is used to generate the certificate
signature?
RSA Algorithm
What encryption algorithm is used to generate the certificate
signature?
Symmetric key encryption
algorithm is utilized for
generating the certificate
signature.
How many bytes is the public key modulus in the certificate? The public key modulus in
the certificate equals to 270
bytes.
In the TLS cipher suite used between client and server, what
algorithm is used for:
- Encrypting session data? Yes
- Hashing for the MAC? Yes
- Key exchange? Yes
How many bytes of random data are sent from the client to
server at the start of the handshake?
256bytes
d) Answer:
The certificate authorities use the self-signed certificates due to trusted certificate
authority, as it ensures same level of encryption (Vultr, 2017). The following are the key
drawbacks of this:
Firstly, the visitors’ connection can be hacked easily which can let the attacker to see all the sent
data. The second drawback refers that, it is impossible to invoke the certificate and hence needs
self-signed certificates.
e) Answer:
The security for private keys to store them offline, in a special hardware device must be
arranged by the certificate authorities. But, the attacker can use the certificate authority private
key, as there is no verification done on the certificate applicant’s identity. Therefore, the hackers’
use the private key and increases various issues which must be discarded (Gist, 2018).
3

Question 3: Access Control
Virtual network is utilized for studying the Linux access control and passwords, where
the following operations are performed:
a) Create new topology.
b) Create five new users.
c) Create password.
d) Create two new groups.
e) Create files and directories.
f) Provide necessary access control and rules.
g) At last, test the access control.
a) Answer
Necessary files are attached below.
b) Answer
The practice is that, the Linux distribution is stores user information in /etc/passwd and it
contains the following:
a) User login
b) Optional comment field
c) Unique numerical user id
d) Encrypted password information
e) Numerical group id.
But, in /etc/passwd the encrypted password is not stored like actually stored in the
following: /etc/shadow file. Even, the password which is encrypted is also stored in /etc/passwd,
which just the super user can read (Sandilands.info, 2018).
c) Answer
4
Virtual network is utilized for studying the Linux access control and passwords, where
the following operations are performed:
a) Create new topology.
b) Create five new users.
c) Create password.
d) Create two new groups.
e) Create files and directories.
f) Provide necessary access control and rules.
g) At last, test the access control.
a) Answer
Necessary files are attached below.
b) Answer
The practice is that, the Linux distribution is stores user information in /etc/passwd and it
contains the following:
a) User login
b) Optional comment field
c) Unique numerical user id
d) Encrypted password information
e) Numerical group id.
But, in /etc/passwd the encrypted password is not stored like actually stored in the
following: /etc/shadow file. Even, the password which is encrypted is also stored in /etc/passwd,
which just the super user can read (Sandilands.info, 2018).
c) Answer
4
The access control contains four types, where the most common access control on Linux
refers to Role based access control and mandatory based access control.
The strictest access control refers to mandatory based access control, which uses
hierarchical approach for controlling the access of the resources/ IT enforced MAC environment
access for each of the resource objects. Moreover, the settings help to control, which the system
administrator has defined. The role based access control is used to approach the real world
method to structure the access control. The organization, the computer systems are assigned
based on the job function of the user. Additionally, permissions are assigned for the specific roles
in the organization.
Question 4: Firewalls
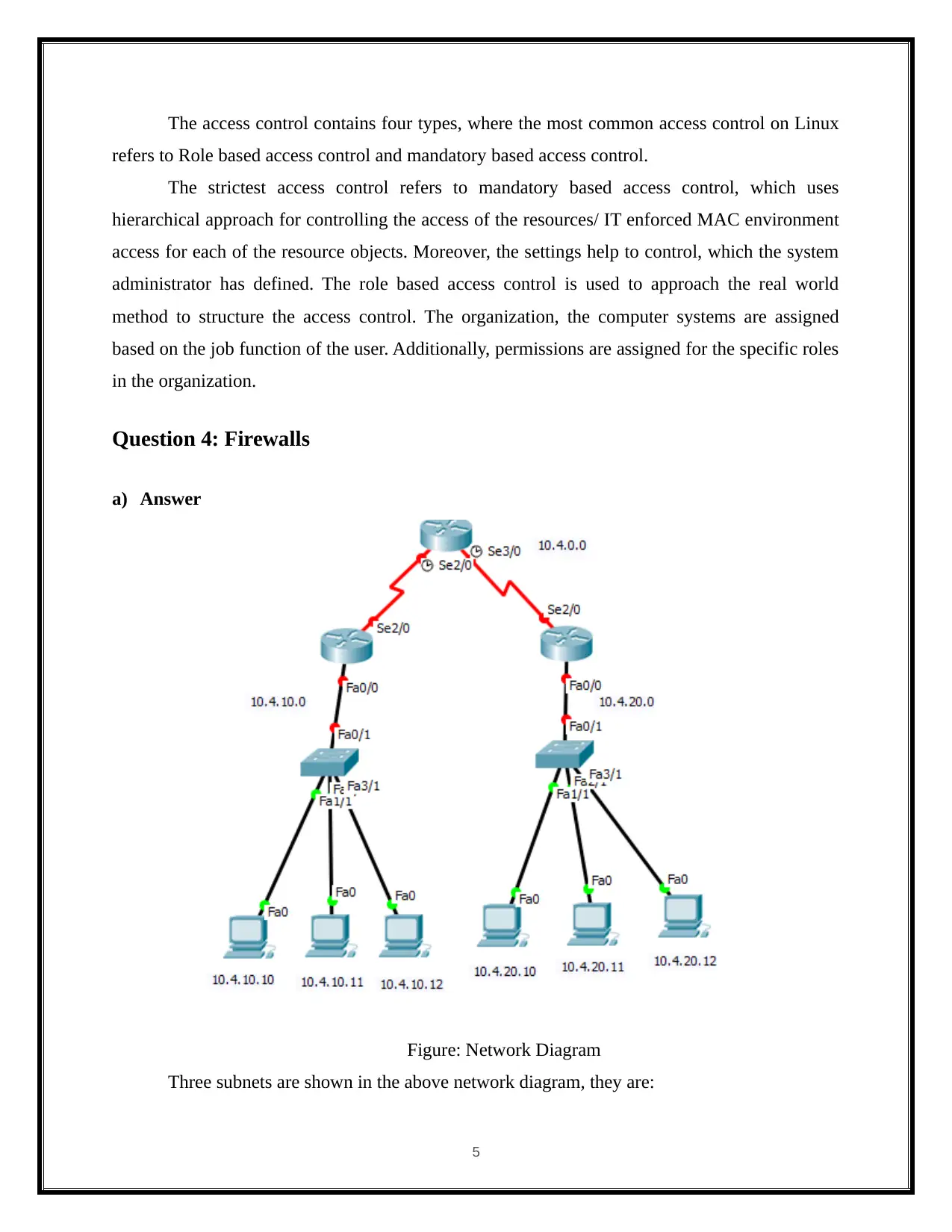
a) Answer
Figure: Network Diagram
Three subnets are shown in the above network diagram, they are:
5
refers to Role based access control and mandatory based access control.
The strictest access control refers to mandatory based access control, which uses
hierarchical approach for controlling the access of the resources/ IT enforced MAC environment
access for each of the resource objects. Moreover, the settings help to control, which the system
administrator has defined. The role based access control is used to approach the real world
method to structure the access control. The organization, the computer systems are assigned
based on the job function of the user. Additionally, permissions are assigned for the specific roles
in the organization.
Question 4: Firewalls
a) Answer
Figure: Network Diagram
Three subnets are shown in the above network diagram, they are:
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
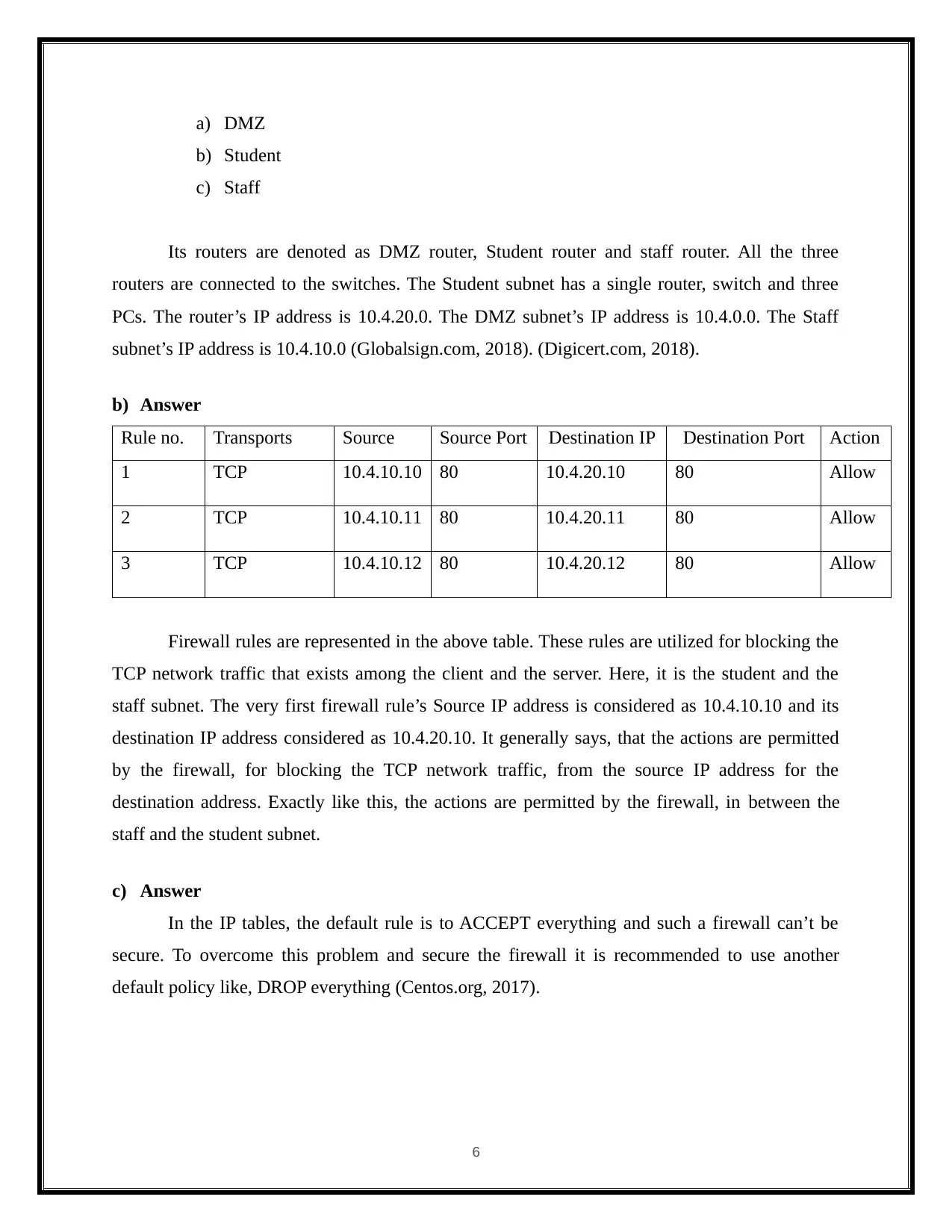
a) DMZ
b) Student
c) Staff
Its routers are denoted as DMZ router, Student router and staff router. All the three
routers are connected to the switches. The Student subnet has a single router, switch and three
PCs. The router’s IP address is 10.4.20.0. The DMZ subnet’s IP address is 10.4.0.0. The Staff
subnet’s IP address is 10.4.10.0 (Globalsign.com, 2018). (Digicert.com, 2018).
b) Answer
Rule no. Transports Source
IPs
Source Port Destination IP Destination Port Action
1 TCP 10.4.10.10 80 10.4.20.10 80 Allow
2 TCP 10.4.10.11 80 10.4.20.11 80 Allow
3 TCP 10.4.10.12 80 10.4.20.12 80 Allow
Firewall rules are represented in the above table. These rules are utilized for blocking the
TCP network traffic that exists among the client and the server. Here, it is the student and the
staff subnet. The very first firewall rule’s Source IP address is considered as 10.4.10.10 and its
destination IP address considered as 10.4.20.10. It generally says, that the actions are permitted
by the firewall, for blocking the TCP network traffic, from the source IP address for the
destination address. Exactly like this, the actions are permitted by the firewall, in between the
staff and the student subnet.
c) Answer
In the IP tables, the default rule is to ACCEPT everything and such a firewall can’t be
secure. To overcome this problem and secure the firewall it is recommended to use another
default policy like, DROP everything (Centos.org, 2017).
6
b) Student
c) Staff
Its routers are denoted as DMZ router, Student router and staff router. All the three
routers are connected to the switches. The Student subnet has a single router, switch and three
PCs. The router’s IP address is 10.4.20.0. The DMZ subnet’s IP address is 10.4.0.0. The Staff
subnet’s IP address is 10.4.10.0 (Globalsign.com, 2018). (Digicert.com, 2018).
b) Answer
Rule no. Transports Source
IPs
Source Port Destination IP Destination Port Action
1 TCP 10.4.10.10 80 10.4.20.10 80 Allow
2 TCP 10.4.10.11 80 10.4.20.11 80 Allow
3 TCP 10.4.10.12 80 10.4.20.12 80 Allow
Firewall rules are represented in the above table. These rules are utilized for blocking the
TCP network traffic that exists among the client and the server. Here, it is the student and the
staff subnet. The very first firewall rule’s Source IP address is considered as 10.4.10.10 and its
destination IP address considered as 10.4.20.10. It generally says, that the actions are permitted
by the firewall, for blocking the TCP network traffic, from the source IP address for the
destination address. Exactly like this, the actions are permitted by the firewall, in between the
staff and the student subnet.
c) Answer
In the IP tables, the default rule is to ACCEPT everything and such a firewall can’t be
secure. To overcome this problem and secure the firewall it is recommended to use another
default policy like, DROP everything (Centos.org, 2017).
6

Question 5: Wireless Network Security
A small sized company which contains 50 employees has planned to move into a new
building. Advice is asked from the consultant who is hired for only providing recommendation
on securing the network of this small company.
a) Answer
To have a secure organizational network, the following are recommended:
1) Secure the organization wireless router and its access point administration
interface.
2) Enable WPA encryption in placing of WEP.
3) Use MAC filtering for Access control
4) Reduce WLAN transmitter Power.
5) Disable the option of remote administration.
b) Answer
It is recommended by the consultant that the D - Link wireless access point must be
selected, as it provides network connectivity solution for both the small and medium sized
businesses. D - Link refers to the corporate name of manufacturer which designs networking,
voice and data communications, digital and broadband solutions. It enables the users to connect
with more devices on a single internet. Hence, it supports small company IT admins. It easily
extends the business network and provides enough connection ports.
c) Answer
The security features for D – Link includes:
a) High performance connectivity
7
A small sized company which contains 50 employees has planned to move into a new
building. Advice is asked from the consultant who is hired for only providing recommendation
on securing the network of this small company.
a) Answer
To have a secure organizational network, the following are recommended:
1) Secure the organization wireless router and its access point administration
interface.
2) Enable WPA encryption in placing of WEP.
3) Use MAC filtering for Access control
4) Reduce WLAN transmitter Power.
5) Disable the option of remote administration.
b) Answer
It is recommended by the consultant that the D - Link wireless access point must be
selected, as it provides network connectivity solution for both the small and medium sized
businesses. D - Link refers to the corporate name of manufacturer which designs networking,
voice and data communications, digital and broadband solutions. It enables the users to connect
with more devices on a single internet. Hence, it supports small company IT admins. It easily
extends the business network and provides enough connection ports.
c) Answer
The security features for D – Link includes:
a) High performance connectivity
7

b) Traffic control
c) Quality of the services.
d) Filtering of MAC address
e) Partition of WLAN.
f) ARP spoofing prevention
g) Web redirection
h) Protection with respect to network access.
i) Internal RADIUS server
j) Robust security
All this allows the network administrators to define multiple levels of network access depending
on the needs of an individual client.
8
c) Quality of the services.
d) Filtering of MAC address
e) Partition of WLAN.
f) ARP spoofing prevention
g) Web redirection
h) Protection with respect to network access.
i) Internal RADIUS server
j) Robust security
All this allows the network administrators to define multiple levels of network access depending
on the needs of an individual client.
8
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

References
Cems.uwe.ac.uk. (2018). Introduction to the openssl command tool. [online] Available at:
http://www.cems.uwe.ac.uk/~irjohnso/coursenotes/uwe/SSLworksheet.pdf [Accessed 1 Jun.
2018].
Digicert.com. (2018). CSR Creation (Create Certificate Signing Request). [online] Available at:
https://www.digicert.com/csr-creation.htm [Accessed 1 Jun. 2018].
Gist. (2018). How to generate & use private keys using the OpenSSL command line tool. [online]
Available at: https://gist.github.com/briansmith/2ee42439923d8e65a266994d0f70180b
[Accessed 1 Jun. 2018].
Globalsign.com. (2018). SSL Basics: What is a Certificate Signing Request (CSR)?. [online]
Available at: https://www.globalsign.com/en/blog/what-is-a-certificate-signing-request-csr/
[Accessed 1 Jun. 2018].
Krisjordan.com. (2018). Encryption with RSA Key Pairs - Kris Jordan. [online] Available at:
http://krisjordan.com/essays/encrypting-with-rsa-key-pairs [Accessed 25 May 2018].
Raymii.org. (2018). Encrypt and decrypt files to public keys via the OpenSSL Command Line -
Raymii.org. [online] Available at:
https://raymii.org/s/tutorials/Encrypt_and_decrypt_files_to_public_keys_via_the_OpenSSL_Co
mmand_Line.html [Accessed 25 May 2018].
Sandilands.info. (2018). Testing HTTPS and Certificates with Apache, OpenSSL and tcpdump in
a Virtual Network. [online] Available at: https://sandilands.info/sgordon/https-and-certificates-
with-apache-openssl-tcpdump [Accessed 25 May 2018].
Vultr. (2017). Vultr: High Performance SSD Cloud.. [online] Available at:
https://www.vultr.com/docs/configure-apache-with-select-signed-tls-ssl-certificate-on-ubuntu-
16-04 [Accessed 1 Jun. 2018].
9
Cems.uwe.ac.uk. (2018). Introduction to the openssl command tool. [online] Available at:
http://www.cems.uwe.ac.uk/~irjohnso/coursenotes/uwe/SSLworksheet.pdf [Accessed 1 Jun.
2018].
Digicert.com. (2018). CSR Creation (Create Certificate Signing Request). [online] Available at:
https://www.digicert.com/csr-creation.htm [Accessed 1 Jun. 2018].
Gist. (2018). How to generate & use private keys using the OpenSSL command line tool. [online]
Available at: https://gist.github.com/briansmith/2ee42439923d8e65a266994d0f70180b
[Accessed 1 Jun. 2018].
Globalsign.com. (2018). SSL Basics: What is a Certificate Signing Request (CSR)?. [online]
Available at: https://www.globalsign.com/en/blog/what-is-a-certificate-signing-request-csr/
[Accessed 1 Jun. 2018].
Krisjordan.com. (2018). Encryption with RSA Key Pairs - Kris Jordan. [online] Available at:
http://krisjordan.com/essays/encrypting-with-rsa-key-pairs [Accessed 25 May 2018].
Raymii.org. (2018). Encrypt and decrypt files to public keys via the OpenSSL Command Line -
Raymii.org. [online] Available at:
https://raymii.org/s/tutorials/Encrypt_and_decrypt_files_to_public_keys_via_the_OpenSSL_Co
mmand_Line.html [Accessed 25 May 2018].
Sandilands.info. (2018). Testing HTTPS and Certificates with Apache, OpenSSL and tcpdump in
a Virtual Network. [online] Available at: https://sandilands.info/sgordon/https-and-certificates-
with-apache-openssl-tcpdump [Accessed 25 May 2018].
Vultr. (2017). Vultr: High Performance SSD Cloud.. [online] Available at:
https://www.vultr.com/docs/configure-apache-with-select-signed-tls-ssl-certificate-on-ubuntu-
16-04 [Accessed 1 Jun. 2018].
9
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



