COIT20262 Advanced Network Security: Protocol Analysis, Cryptography
VerifiedAdded on 2023/06/13
|12
|1899
|262
Homework Assignment
AI Summary
This assignment solution for COIT20262 Advanced Network Security covers several key areas. It includes an analysis of network protocols using Wireshark, identifying MAC addresses, server IP addresses, and TCP segment flags. The solution also delves into web application attacks, specifically SQL injection, explaining the attack mechanism, prevention techniques, and vulnerabilities in the MyUni website. Furthermore, it explores cryptography concepts, detailing symmetric key encryption, full disk encryption, and file-based encryption, along with considerations for backing up file servers using cloud storage. Finally, the assignment researches trojan downloads, discussing the motivations of malicious users, examples of malware distribution, and the role of file hashes, digests, and digital signatures in secure downloads, concluding with recommendations for software developers and users to ensure secure software distribution and download practices. Desklib offers a wealth of similar solved assignments and study resources for students.

Running head: COIT20262 - ADVANCED NETWORK SECURITY
COIT20262 - Advanced Network Security
Name of the Student
Student ID: 12052743
Name of the University
Author’s Note
COIT20262 - Advanced Network Security
Name of the Student
Student ID: 12052743
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
COIT20262 - ADVANCED NETWORK SECURITY
Table of Contents
Question 1. Analysis of Protocols with Wireshark..........................................................................2
Question 2. Web Application Attacks.............................................................................................3
Question 3. Cryptography Concepts................................................................................................6
Question 4. Trojan Downloads Research........................................................................................8
Bibliography..................................................................................................................................10
COIT20262 - ADVANCED NETWORK SECURITY
Table of Contents
Question 1. Analysis of Protocols with Wireshark..........................................................................2
Question 2. Web Application Attacks.............................................................................................3
Question 3. Cryptography Concepts................................................................................................6
Question 4. Trojan Downloads Research........................................................................................8
Bibliography..................................................................................................................................10
2
COIT20262 - ADVANCED NETWORK SECURITY
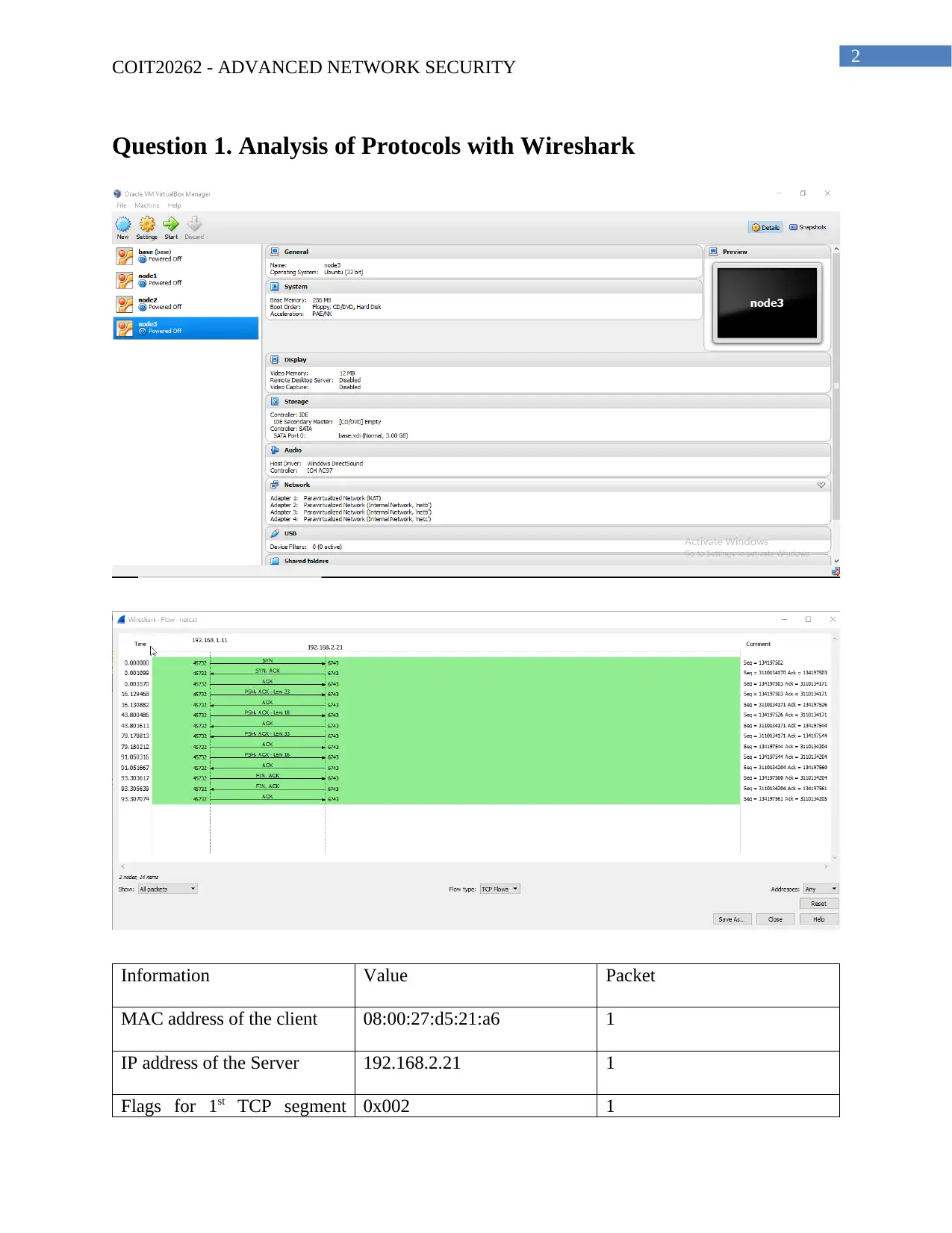
Question 1. Analysis of Protocols with Wireshark
Information Value Packet
MAC address of the client 08:00:27:d5:21:a6 1
IP address of the Server 192.168.2.21 1
Flags for 1st TCP segment 0x002 1
COIT20262 - ADVANCED NETWORK SECURITY
Question 1. Analysis of Protocols with Wireshark
Information Value Packet
MAC address of the client 08:00:27:d5:21:a6 1
IP address of the Server 192.168.2.21 1
Flags for 1st TCP segment 0x002 1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
COIT20262 - ADVANCED NETWORK SECURITY
containing data
Length of data for 2nd TCP
segment containing data
40bytes 2
Absolute sequence number of
the 1st TCP
134197502 1
Question 2. Web Application Attacks
2.1. Explanation of SQL Injection Attacks –
In this type of attacks malicious SQL codes are used by the attacker and for manipulating the
database for the own benefit. The SQL attacks includes the successful access of the unauthorized
views of the list of users, deletion or modification of tables and gaining the administrative rights
on the database. SQL statements are used for the modification of the database for example:
“SELECT ItemName, ItemDescription
FROM Items
WHERE ItemNumber = 999 OR 1=1”
2.2. The two general approaches that can be used for the avoidance of the SQL injection attacks
are given below:
i. The user input should not be trusted and it should be considered as malicious until it is proved
to be trusted.
ii. The input string should be validated on the server end for neutralizing the risk of malicious
commands used by the hacker.
COIT20262 - ADVANCED NETWORK SECURITY
containing data
Length of data for 2nd TCP
segment containing data
40bytes 2
Absolute sequence number of
the 1st TCP
134197502 1
Question 2. Web Application Attacks
2.1. Explanation of SQL Injection Attacks –
In this type of attacks malicious SQL codes are used by the attacker and for manipulating the
database for the own benefit. The SQL attacks includes the successful access of the unauthorized
views of the list of users, deletion or modification of tables and gaining the administrative rights
on the database. SQL statements are used for the modification of the database for example:
“SELECT ItemName, ItemDescription
FROM Items
WHERE ItemNumber = 999 OR 1=1”
2.2. The two general approaches that can be used for the avoidance of the SQL injection attacks
are given below:
i. The user input should not be trusted and it should be considered as malicious until it is proved
to be trusted.
ii. The input string should be validated on the server end for neutralizing the risk of malicious
commands used by the hacker.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
COIT20262 - ADVANCED NETWORK SECURITY
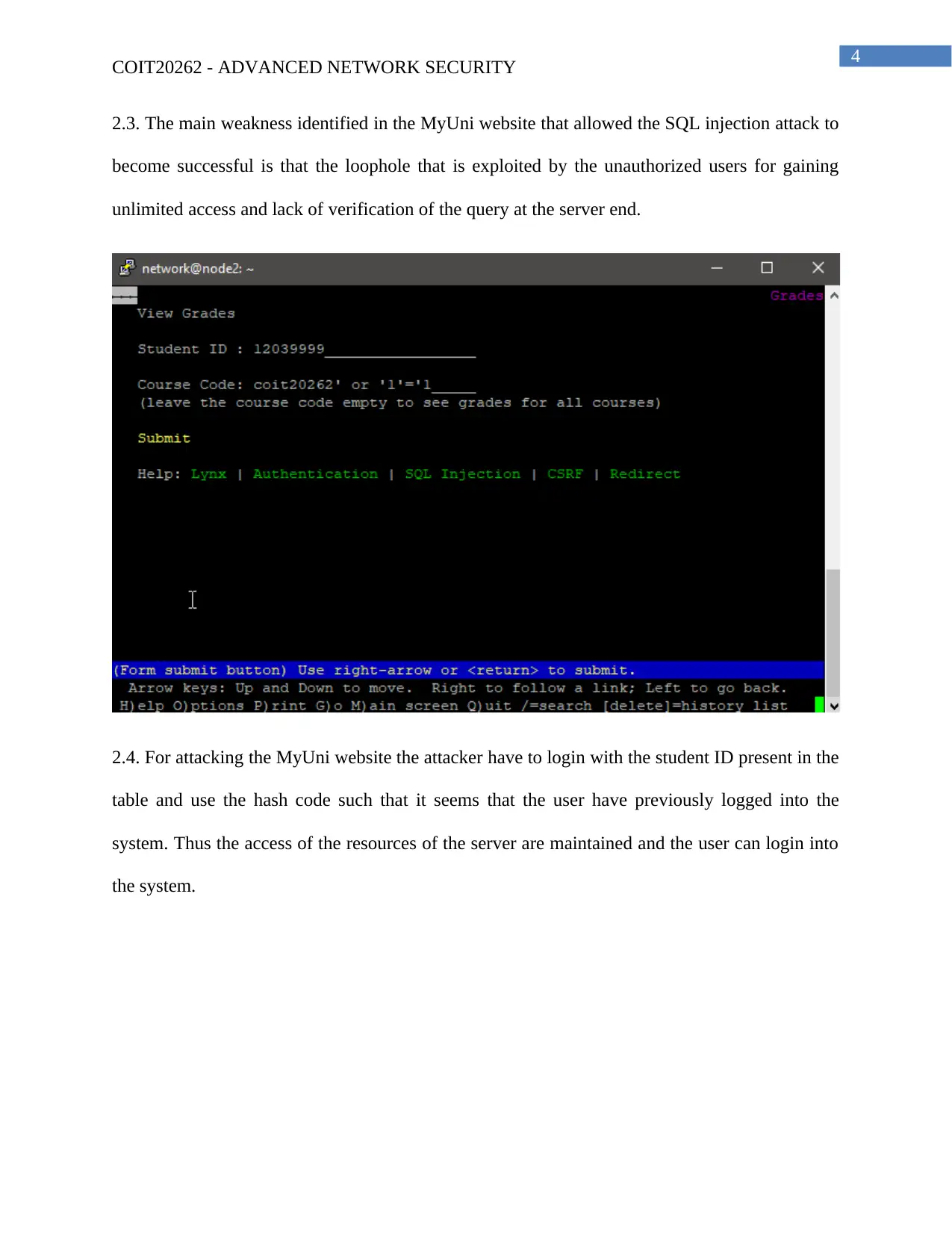
2.3. The main weakness identified in the MyUni website that allowed the SQL injection attack to
become successful is that the loophole that is exploited by the unauthorized users for gaining
unlimited access and lack of verification of the query at the server end.
2.4. For attacking the MyUni website the attacker have to login with the student ID present in the
table and use the hash code such that it seems that the user have previously logged into the
system. Thus the access of the resources of the server are maintained and the user can login into
the system.
COIT20262 - ADVANCED NETWORK SECURITY
2.3. The main weakness identified in the MyUni website that allowed the SQL injection attack to
become successful is that the loophole that is exploited by the unauthorized users for gaining
unlimited access and lack of verification of the query at the server end.
2.4. For attacking the MyUni website the attacker have to login with the student ID present in the
table and use the hash code such that it seems that the user have previously logged into the
system. Thus the access of the resources of the server are maintained and the user can login into
the system.
5
COIT20262 - ADVANCED NETWORK SECURITY
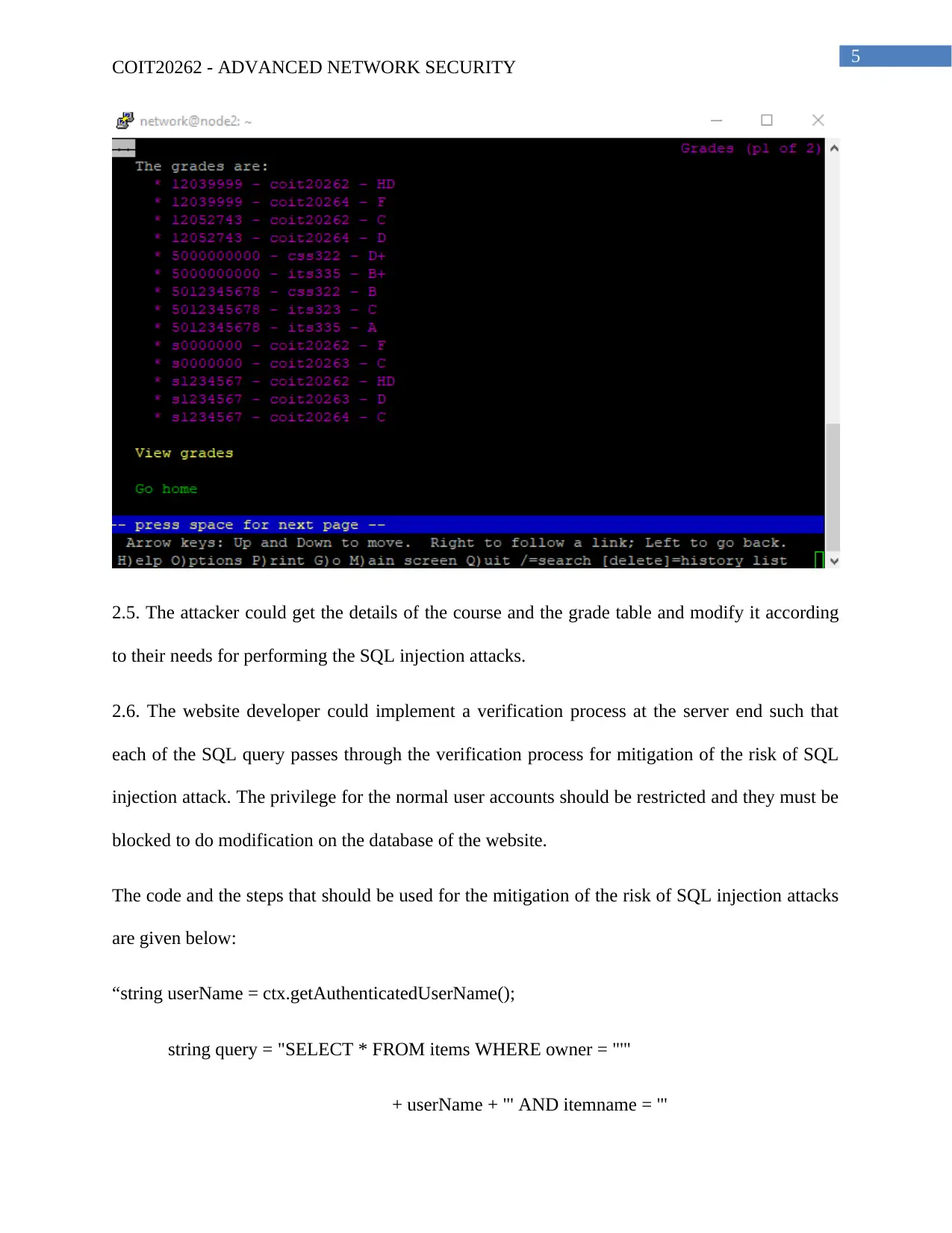
2.5. The attacker could get the details of the course and the grade table and modify it according
to their needs for performing the SQL injection attacks.
2.6. The website developer could implement a verification process at the server end such that
each of the SQL query passes through the verification process for mitigation of the risk of SQL
injection attack. The privilege for the normal user accounts should be restricted and they must be
blocked to do modification on the database of the website.
The code and the steps that should be used for the mitigation of the risk of SQL injection attacks
are given below:
“string userName = ctx.getAuthenticatedUserName();
string query = "SELECT * FROM items WHERE owner = "'"
+ userName + "' AND itemname = '"
COIT20262 - ADVANCED NETWORK SECURITY
2.5. The attacker could get the details of the course and the grade table and modify it according
to their needs for performing the SQL injection attacks.
2.6. The website developer could implement a verification process at the server end such that
each of the SQL query passes through the verification process for mitigation of the risk of SQL
injection attack. The privilege for the normal user accounts should be restricted and they must be
blocked to do modification on the database of the website.
The code and the steps that should be used for the mitigation of the risk of SQL injection attacks
are given below:
“string userName = ctx.getAuthenticatedUserName();
string query = "SELECT * FROM items WHERE owner = "'"
+ userName + "' AND itemname = '"
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
COIT20262 - ADVANCED NETWORK SECURITY
+ ItemName.Text + "'";
sda = new SqlDataAdapter(query, conn);
DataTable dt = new DataTable();
sda.Fill(dt);
SELECT * FROM items
WHERE owner =
AND itemname = ;
SELECT * FROM items
WHERE owner = 'wiley'
AND itemname = 'name' OR 'a'='a';
SELECT * FROM items;”
Question 3. Cryptography Concepts
3.1. Description of the working of the Symmetric key encryption –
The symmetric key encryption system works by sharing a single key for the encryption and
decryption of a message. It is faster and simple but the main problem arises for remote
communication because the key needs to shred securely between the users. It works on files and
disk by encrypting the contents with a key and generate a hash value. The key is required for the
decryption of the files and access it.
COIT20262 - ADVANCED NETWORK SECURITY
+ ItemName.Text + "'";
sda = new SqlDataAdapter(query, conn);
DataTable dt = new DataTable();
sda.Fill(dt);
SELECT * FROM items
WHERE owner =
AND itemname = ;
SELECT * FROM items
WHERE owner = 'wiley'
AND itemname = 'name' OR 'a'='a';
SELECT * FROM items;”
Question 3. Cryptography Concepts
3.1. Description of the working of the Symmetric key encryption –
The symmetric key encryption system works by sharing a single key for the encryption and
decryption of a message. It is faster and simple but the main problem arises for remote
communication because the key needs to shred securely between the users. It works on files and
disk by encrypting the contents with a key and generate a hash value. The key is required for the
decryption of the files and access it.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
COIT20262 - ADVANCED NETWORK SECURITY
3.2. In the full disk encryption the data residing in the hard disk is encrypted with a key and it
provides no protection against the authorized users such as the administrators and it is used for
encrypting the data base of the datacenters.
The file based encryption technique is applied for encrypting different files with different keys
and it provides control of the access of data depending on the roles. The users can be divided into
different levels for providing them authorization to access different files. It is ideally suited for
all environment and it is more secure than the full disk encryption technique.
3.3. Backing up the file server using the cloud storage is an ideal option for the organization
because there are different cloud services and security options provided by the cloud vendors.
The security should be chosen wisely for securing the organizational data from illegal access.
There are different threats acting during moving the files to the backup server and it should be
taken for securing the backup. During the transmission of the data to the cloud server precaution
against sniffing, electronic theft and physical theft should be considered. Moreover moving the
data in the cloud server increases its scalability and makes it available to the users from remote
location. The data moved to the cloud platform can be encrypted for resolving the issues of
unauthorized access.
Question 4. Trojan Downloads Research
4.1. The main motivation and the goals of the malicious users is to take the partial or full control
of the targeted host. As an example off the malicious attack the change of the author name of a
word document may be a cause of the malicious software. More over adware and spyware can be
used by an attacker to monitor the activity of the user. The software developer can be affected by
COIT20262 - ADVANCED NETWORK SECURITY
3.2. In the full disk encryption the data residing in the hard disk is encrypted with a key and it
provides no protection against the authorized users such as the administrators and it is used for
encrypting the data base of the datacenters.
The file based encryption technique is applied for encrypting different files with different keys
and it provides control of the access of data depending on the roles. The users can be divided into
different levels for providing them authorization to access different files. It is ideally suited for
all environment and it is more secure than the full disk encryption technique.
3.3. Backing up the file server using the cloud storage is an ideal option for the organization
because there are different cloud services and security options provided by the cloud vendors.
The security should be chosen wisely for securing the organizational data from illegal access.
There are different threats acting during moving the files to the backup server and it should be
taken for securing the backup. During the transmission of the data to the cloud server precaution
against sniffing, electronic theft and physical theft should be considered. Moreover moving the
data in the cloud server increases its scalability and makes it available to the users from remote
location. The data moved to the cloud platform can be encrypted for resolving the issues of
unauthorized access.
Question 4. Trojan Downloads Research
4.1. The main motivation and the goals of the malicious users is to take the partial or full control
of the targeted host. As an example off the malicious attack the change of the author name of a
word document may be a cause of the malicious software. More over adware and spyware can be
used by an attacker to monitor the activity of the user. The software developer can be affected by

8
COIT20262 - ADVANCED NETWORK SECURITY
the malicious users by changing the codes of a program or deleting or embed codes in the
application developed to spread the virus.
4.2. Two example of malware that is distributed by the reputable sources are the browser plugin
of the adobe flash player and the adobe reader. This is because sometimes the installation of the
new version of the plugin does not removes the older version and it can be used by the malicious
used to cause buffer overrun and not allowing the new data to be accommodated.
4.3. The file hash, digests and the digital signature plays a significant role for securely download
a file from the web. The hash is appended with the message and sent to the receiver such the
receiver can find the alternation (if any) by comparing the hash value. In case of the man in the
middle attack the hash value can be altered and regenerated such that the user cannot find the
difference between the altered messages. The verification of the file is done using the message
digest and the digital signature is applied for checking the authenticity and the integrity of the
file or the message sent over the network.
The file hash and message digest technique is vulnerable to the man in the middle attack
because the well-known hash algorithm such as MD3 and SHA1 are used and the man in the
middle can easily alter and regenerate the message for disguising the users. Moreover there are
limitation to digital certificate this is because of their compatibility and sharing of the digital
certificate is a complex task.
4.4. For the distribution of the software the software developers are provided the following
recommendations such as:
The source code must be compiled to form a single executable file that can be downloaded form
the internet.
COIT20262 - ADVANCED NETWORK SECURITY
the malicious users by changing the codes of a program or deleting or embed codes in the
application developed to spread the virus.
4.2. Two example of malware that is distributed by the reputable sources are the browser plugin
of the adobe flash player and the adobe reader. This is because sometimes the installation of the
new version of the plugin does not removes the older version and it can be used by the malicious
used to cause buffer overrun and not allowing the new data to be accommodated.
4.3. The file hash, digests and the digital signature plays a significant role for securely download
a file from the web. The hash is appended with the message and sent to the receiver such the
receiver can find the alternation (if any) by comparing the hash value. In case of the man in the
middle attack the hash value can be altered and regenerated such that the user cannot find the
difference between the altered messages. The verification of the file is done using the message
digest and the digital signature is applied for checking the authenticity and the integrity of the
file or the message sent over the network.
The file hash and message digest technique is vulnerable to the man in the middle attack
because the well-known hash algorithm such as MD3 and SHA1 are used and the man in the
middle can easily alter and regenerate the message for disguising the users. Moreover there are
limitation to digital certificate this is because of their compatibility and sharing of the digital
certificate is a complex task.
4.4. For the distribution of the software the software developers are provided the following
recommendations such as:
The source code must be compiled to form a single executable file that can be downloaded form
the internet.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
COIT20262 - ADVANCED NETWORK SECURITY
Different software distribution tools can be used such as LANDesk management suite for the
windows, OS X and Linux software distribution.
4.5. For downloading the software the following recommendations are made such as:
Safest and cleanest website should be used for downloading the software application for
avoiding the risk of malware installation in the system.
Virtual machines must be used for testing the software because if malware is found it
cannot affect the primary PC and its resources.
COIT20262 - ADVANCED NETWORK SECURITY
Different software distribution tools can be used such as LANDesk management suite for the
windows, OS X and Linux software distribution.
4.5. For downloading the software the following recommendations are made such as:
Safest and cleanest website should be used for downloading the software application for
avoiding the risk of malware installation in the system.
Virtual machines must be used for testing the software because if malware is found it
cannot affect the primary PC and its resources.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
COIT20262 - ADVANCED NETWORK SECURITY
Bibliography
Acemoglu, D., Malekian, A. and Ozdaglar, A., 2016. Network security and contagion. Journal
of Economic Theory, 166, pp.536-585.
Anwar, R.W., Bakhtiari, M., Zainal, A., Abdullah, A.H. and Qureshi, K.N., 2014. Security issues
and attacks in wireless sensor network. World Applied Sciences Journal, 30(10), pp.1224-1227.
Jang, H., Jeong, J., Kim, H. and Park, J.S., 2015, March. A survey on interfaces to network
security functions in network virtualization. In Advanced Information Networking and
Applications Workshops (WAINA), 2015 IEEE 29th International Conference on (pp. 160-163).
IEEE.
JOSEPH. PHILLIPS, P.M.P., CBAP, I. and PMP, C., 2018. PMP PROJECT MANAGEMENT
PROFESSIONAL STUDY GUIDE. McGraw-Hill Education.
Joshi, M.R. and Karkade, R.A., 2015. Network security with cryptography. International
Journal of Computer Science and Mobile Computing” IJCSMCVol, 4, pp.201-204.
Kizza, J.M., 2017. Guide to computer network security. Springer.
Loo, J., Mauri, J.L. and Ortiz, J.H. eds., 2016. Mobile ad hoc networks: current status and future
trends. CRC Press.
Moon, C.S. and Kim, S.H., 2014. A study on the integrated security system based real-time
network packet deep inspection. International Journal of Security and Its Applications, 8(1),
pp.113-122.
COIT20262 - ADVANCED NETWORK SECURITY
Bibliography
Acemoglu, D., Malekian, A. and Ozdaglar, A., 2016. Network security and contagion. Journal
of Economic Theory, 166, pp.536-585.
Anwar, R.W., Bakhtiari, M., Zainal, A., Abdullah, A.H. and Qureshi, K.N., 2014. Security issues
and attacks in wireless sensor network. World Applied Sciences Journal, 30(10), pp.1224-1227.
Jang, H., Jeong, J., Kim, H. and Park, J.S., 2015, March. A survey on interfaces to network
security functions in network virtualization. In Advanced Information Networking and
Applications Workshops (WAINA), 2015 IEEE 29th International Conference on (pp. 160-163).
IEEE.
JOSEPH. PHILLIPS, P.M.P., CBAP, I. and PMP, C., 2018. PMP PROJECT MANAGEMENT
PROFESSIONAL STUDY GUIDE. McGraw-Hill Education.
Joshi, M.R. and Karkade, R.A., 2015. Network security with cryptography. International
Journal of Computer Science and Mobile Computing” IJCSMCVol, 4, pp.201-204.
Kizza, J.M., 2017. Guide to computer network security. Springer.
Loo, J., Mauri, J.L. and Ortiz, J.H. eds., 2016. Mobile ad hoc networks: current status and future
trends. CRC Press.
Moon, C.S. and Kim, S.H., 2014. A study on the integrated security system based real-time
network packet deep inspection. International Journal of Security and Its Applications, 8(1),
pp.113-122.

11
COIT20262 - ADVANCED NETWORK SECURITY
Pathan, A.S.K. ed., 2016. Security of self-organizing networks: MANET, WSN, WMN, VANET.
CRC press.
Pawar, M.V. and Anuradha, J., 2015. Network security and types of attacks in
network. Procedia Computer Science, 48, pp.503-506.
Perlman, R., Kaufman, C. and Speciner, M., 2016. Network security: private communication in a
public world. Pearson Education India.
Yan, F., Jian-Wen, Y. and Lin, C., 2015, June. Computer Network Security and Technology
Research. In Measuring Technology and Mechatronics Automation (ICMTMA), 2015 Seventh
International Conference on (pp. 293-296). IEEE.
COIT20262 - ADVANCED NETWORK SECURITY
Pathan, A.S.K. ed., 2016. Security of self-organizing networks: MANET, WSN, WMN, VANET.
CRC press.
Pawar, M.V. and Anuradha, J., 2015. Network security and types of attacks in
network. Procedia Computer Science, 48, pp.503-506.
Perlman, R., Kaufman, C. and Speciner, M., 2016. Network security: private communication in a
public world. Pearson Education India.
Yan, F., Jian-Wen, Y. and Lin, C., 2015, June. Computer Network Security and Technology
Research. In Measuring Technology and Mechatronics Automation (ICMTMA), 2015 Seventh
International Conference on (pp. 293-296). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




