COIT20262 Advanced Network Security: Protocol Analysis & Attacks
VerifiedAdded on 2023/06/13
|12
|1957
|154
Homework Assignment
AI Summary
This document presents a comprehensive solution to an assignment on Advanced Network Security. It includes a Wireshark protocol analysis, focusing on packet information value, MAC addresses, IP addresses, TCP flags, and data lengths. The solution further discusses web application attacks, particularly SQL injection, detailing prevention methods and vulnerabilities in web applications. Cryptography concepts, including symmetric key encryption, file-based encryption, and cloud storage security risks, are explored. The document also covers Trojan download research, examining motivations, real-world examples, the role of file hashes and digital signatures, software distribution methods, and user recommendations for safe software downloads. Desklib provides a platform for students to access similar solved assignments and resources.

Running head: ADVANCED NETWORK SECURITY
Advanced Network Security
Name of the Student
Name of the University
Author’s Note
Advanced Network Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
ADVANCED NETWORK SECURITY
Table of Contents
Answer to Question 1: Analysis of Wireshark with Protocol..........................................................2
Answer to Question 2: Web Application Attacks............................................................................3
Answer to Question 3: Cryptography Concepts..............................................................................6
Answer to Question 4: Trojan Download Research........................................................................7
Bibliography..................................................................................................................................10
ADVANCED NETWORK SECURITY
Table of Contents
Answer to Question 1: Analysis of Wireshark with Protocol..........................................................2
Answer to Question 2: Web Application Attacks............................................................................3
Answer to Question 3: Cryptography Concepts..............................................................................6
Answer to Question 4: Trojan Download Research........................................................................7
Bibliography..................................................................................................................................10

2
ADVANCED NETWORK SECURITY
Answer to Question 1: Analysis of Wireshark with Protocol
a.
b.
c.
Information Value Packet
MAC address of the client 08:00:27:49:99:e2 3
IP address of the Server 192.168.2.21 3
Flags for 1st TCP segment
containing data
0x002 4
Length of data for 2nd TCP
segment containing data
1460 bytes 4
Absolute sequence number of 2824361535 4
ADVANCED NETWORK SECURITY
Answer to Question 1: Analysis of Wireshark with Protocol
a.
b.
c.
Information Value Packet
MAC address of the client 08:00:27:49:99:e2 3
IP address of the Server 192.168.2.21 3
Flags for 1st TCP segment
containing data
0x002 4
Length of data for 2nd TCP
segment containing data
1460 bytes 4
Absolute sequence number of 2824361535 4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
ADVANCED NETWORK SECURITY
the 1st TCP
Answer to Question 2: Web Application Attacks
a. The SQL injection attack is done on a system by using malicious SQL codes it can be utilized
by the hacker to modify the database contents for their own benefits. A successful SQL attack is
used for getting the access of the user details and it can be modified using similar SQL statement.
The following example is given for modification of a database table using the SQL query:
“SELECT CourseID, CourseName
FROM Course
WHERE StudentID = 999 OR 1=1”
b. There are different approaches that can be used for the prevention of the SQL injection attacks
and they are given below:
The inputs from the users should be validated and considered as a malicious input until it
is verified to be trusted
On the server side a validation should be applied for reducing the risk of the execution of
the malicious commands from the hacker.
c. The MyUni Web site deployed on node 4 have is that the session for the logged in users never
expires and it can be used by the hacker to gain the access of the database by injecting malicious
SQL codes in the system.
ADVANCED NETWORK SECURITY
the 1st TCP
Answer to Question 2: Web Application Attacks
a. The SQL injection attack is done on a system by using malicious SQL codes it can be utilized
by the hacker to modify the database contents for their own benefits. A successful SQL attack is
used for getting the access of the user details and it can be modified using similar SQL statement.
The following example is given for modification of a database table using the SQL query:
“SELECT CourseID, CourseName
FROM Course
WHERE StudentID = 999 OR 1=1”
b. There are different approaches that can be used for the prevention of the SQL injection attacks
and they are given below:
The inputs from the users should be validated and considered as a malicious input until it
is verified to be trusted
On the server side a validation should be applied for reducing the risk of the execution of
the malicious commands from the hacker.
c. The MyUni Web site deployed on node 4 have is that the session for the logged in users never
expires and it can be used by the hacker to gain the access of the database by injecting malicious
SQL codes in the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
ADVANCED NETWORK SECURITY
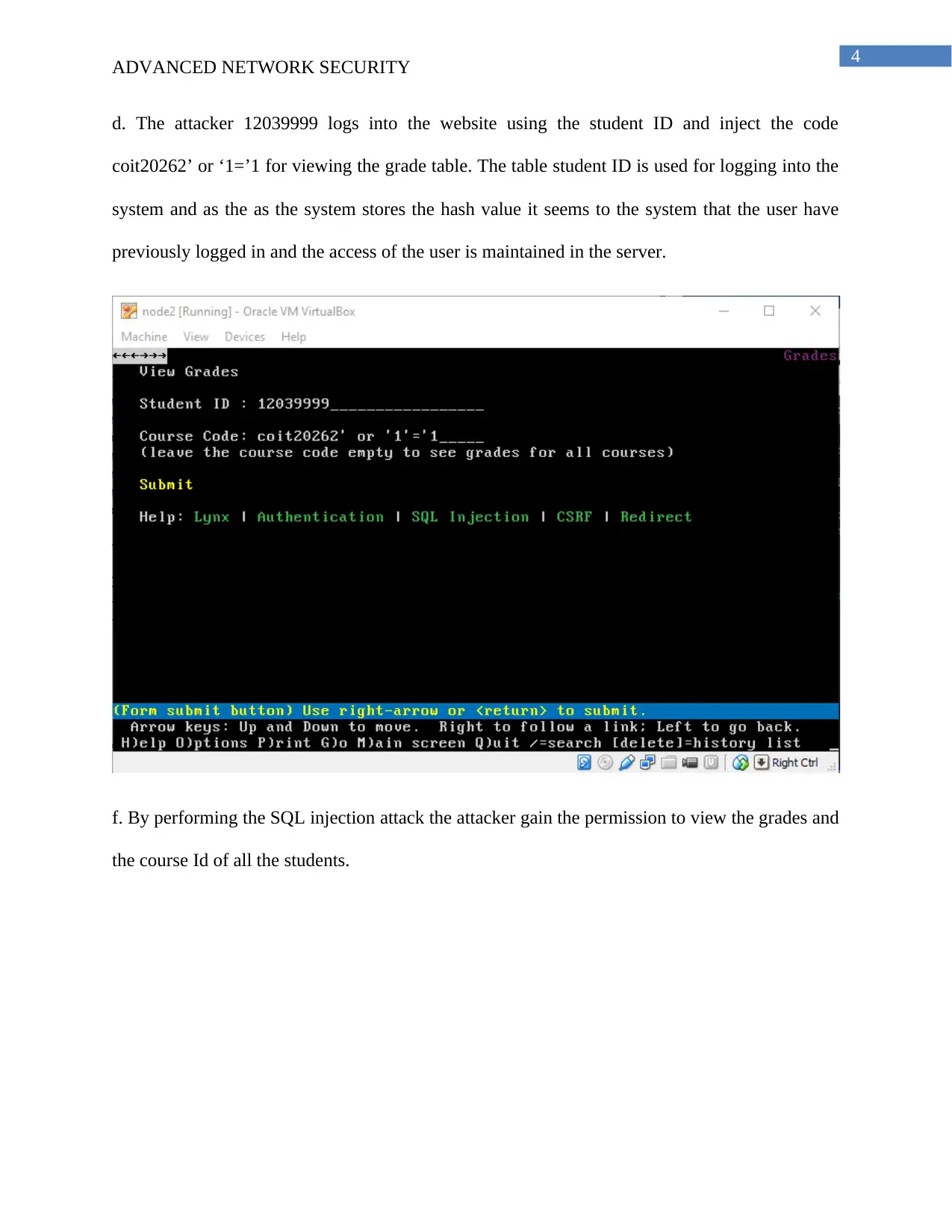
d. The attacker 12039999 logs into the website using the student ID and inject the code
coit20262’ or ‘1=’1 for viewing the grade table. The table student ID is used for logging into the
system and as the as the system stores the hash value it seems to the system that the user have
previously logged in and the access of the user is maintained in the server.
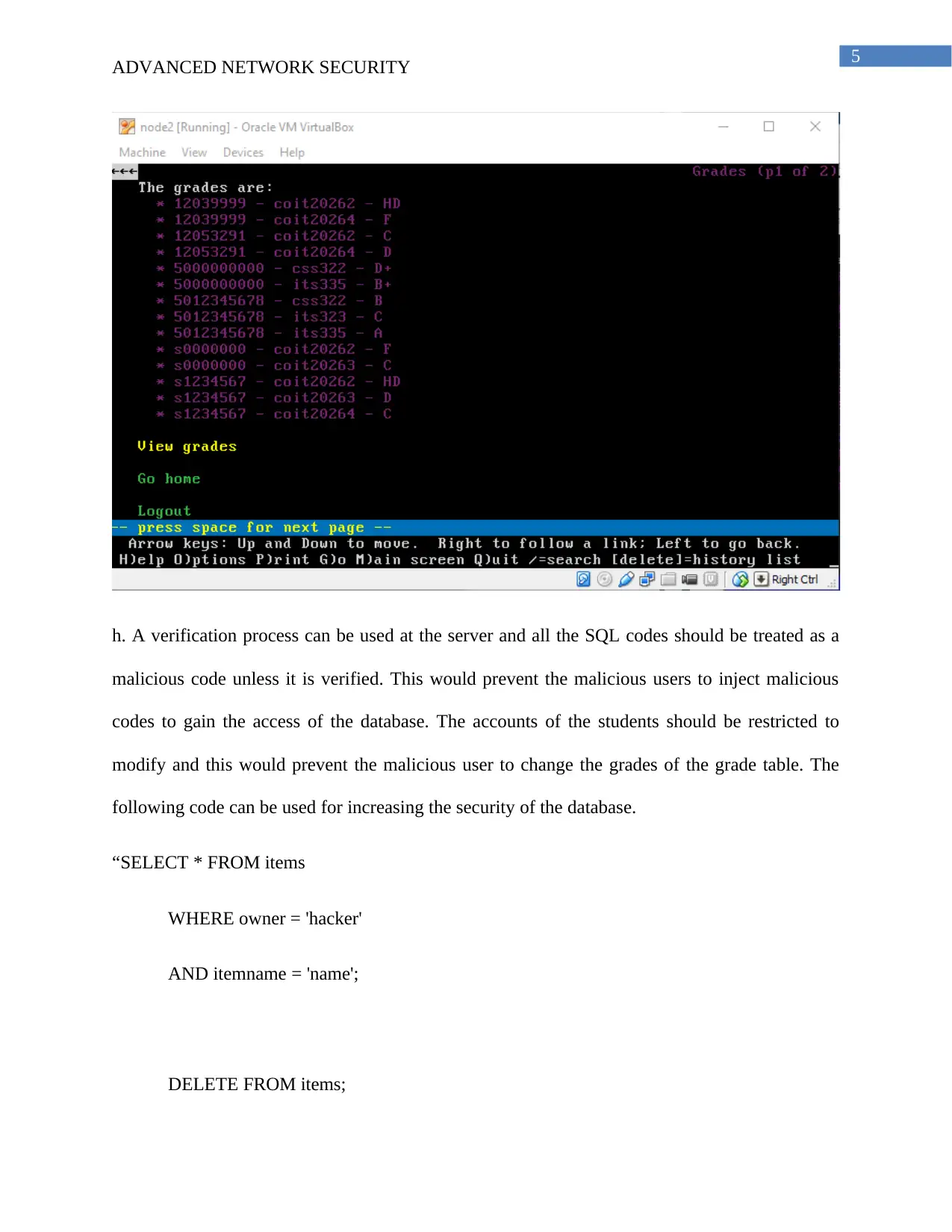
f. By performing the SQL injection attack the attacker gain the permission to view the grades and
the course Id of all the students.
ADVANCED NETWORK SECURITY
d. The attacker 12039999 logs into the website using the student ID and inject the code
coit20262’ or ‘1=’1 for viewing the grade table. The table student ID is used for logging into the
system and as the as the system stores the hash value it seems to the system that the user have
previously logged in and the access of the user is maintained in the server.
f. By performing the SQL injection attack the attacker gain the permission to view the grades and
the course Id of all the students.
5
ADVANCED NETWORK SECURITY
h. A verification process can be used at the server and all the SQL codes should be treated as a
malicious code unless it is verified. This would prevent the malicious users to inject malicious
codes to gain the access of the database. The accounts of the students should be restricted to
modify and this would prevent the malicious user to change the grades of the grade table. The
following code can be used for increasing the security of the database.
“SELECT * FROM items
WHERE owner = 'hacker'
AND itemname = 'name';
DELETE FROM items;
ADVANCED NETWORK SECURITY
h. A verification process can be used at the server and all the SQL codes should be treated as a
malicious code unless it is verified. This would prevent the malicious users to inject malicious
codes to gain the access of the database. The accounts of the students should be restricted to
modify and this would prevent the malicious user to change the grades of the grade table. The
following code can be used for increasing the security of the database.
“SELECT * FROM items
WHERE owner = 'hacker'
AND itemname = 'name';
DELETE FROM items;
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
ADVANCED NETWORK SECURITY
--'
SELECT * FROM items
WHERE owner = 'hacker'
AND itemname = 'name';
DELETE FROM items;
SELECT * FROM items WHERE 'a'='a';
”
procedure get_item (
itm_cv IN OUT ItmCurTyp,
usr in varchar2,
itm in varchar2)
is
open itm_cv for ' SELECT * FROM items WHERE ' ||
'owner = '''|| usr ||
' AND itemname = ''' || itm || '''';
end get_item;”
ADVANCED NETWORK SECURITY
--'
SELECT * FROM items
WHERE owner = 'hacker'
AND itemname = 'name';
DELETE FROM items;
SELECT * FROM items WHERE 'a'='a';
”
procedure get_item (
itm_cv IN OUT ItmCurTyp,
usr in varchar2,
itm in varchar2)
is
open itm_cv for ' SELECT * FROM items WHERE ' ||
'owner = '''|| usr ||
' AND itemname = ''' || itm || '''';
end get_item;”
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
ADVANCED NETWORK SECURITY
Answer to Question 3: Cryptography Concepts
a. The symmetric key encryption uses a single key for encryption and decryption of a file or
message sent over the network or stored locally. The major problem of the single key encryption
is that the key needs to be shared externally to the client for decryption of the package and the
sharing should be done securely for maintaining the security of the package. The contents of the
files or the disk is encrypted with a key and a hash value is generated.
b. There are different type of encryption techniques such as file based encryption and full disk
encryption. In case of full disk encryption the whole hard disk is encrypted with a key and it is
accessible to the authorized users such as the administrator and thus it provides no protection
against the internal agents. In the file based encryption the files are encrypted with different keys
and different users can be provides access to different files. It can be used for any situation and is
more secure and flexible than the full disk encryption technology.
c. The current files and database of the organization can be backed up using the cloud storage
options but there are different risk associated with the security provided by the cloud platform.
The cloud vendor provides different level of service and selection of the service is important for
the implementation of the cloud storage. There is risk of data loss and data hijacking because the
data can be access be by ant third party users during the migration of the data into the cloud
servers. The company should take precaution such as encrypting the data during its transfer for
protecting it from theft and modification. The public clouds are vulnerable to the users and
storage of the information in the public cloud servers may be accessed by the hacker using the
CSRF attacks. It can cause the company to lock down with their service.
ADVANCED NETWORK SECURITY
Answer to Question 3: Cryptography Concepts
a. The symmetric key encryption uses a single key for encryption and decryption of a file or
message sent over the network or stored locally. The major problem of the single key encryption
is that the key needs to be shared externally to the client for decryption of the package and the
sharing should be done securely for maintaining the security of the package. The contents of the
files or the disk is encrypted with a key and a hash value is generated.
b. There are different type of encryption techniques such as file based encryption and full disk
encryption. In case of full disk encryption the whole hard disk is encrypted with a key and it is
accessible to the authorized users such as the administrator and thus it provides no protection
against the internal agents. In the file based encryption the files are encrypted with different keys
and different users can be provides access to different files. It can be used for any situation and is
more secure and flexible than the full disk encryption technology.
c. The current files and database of the organization can be backed up using the cloud storage
options but there are different risk associated with the security provided by the cloud platform.
The cloud vendor provides different level of service and selection of the service is important for
the implementation of the cloud storage. There is risk of data loss and data hijacking because the
data can be access be by ant third party users during the migration of the data into the cloud
servers. The company should take precaution such as encrypting the data during its transfer for
protecting it from theft and modification. The public clouds are vulnerable to the users and
storage of the information in the public cloud servers may be accessed by the hacker using the
CSRF attacks. It can cause the company to lock down with their service.

8
ADVANCED NETWORK SECURITY
Answer to Question 4: Trojan Download Research
a. The motivation and goals of the malicious users is to control the targeted system partially or
modify the information or data in the system. For example, the author name or digital signature
of a file can be changed by the malware. The current activity of the users can also be monitored
with the implementation of the malware and spyware. The malware can affect the software
developer because it can be used by the malicious users to add extra codes and cause the
developed software to malfunction. The Trojan virus are used for disguising the users for
accessing the resources and gain the access.
b. As an example of real Trojan or malware distributed using reputable sources are
download.com and old version of adobe flash player plugin. The download.com is a free source
to download software and it causes installation of more software accidentally and this may
contain Trojan or spigots that can be used for getting the access of the computer. The extension
or plugins installed in a browser can also be a malware and it can cause buffer overrun such that
new data cannot be accommodated and results in denial of service.
c. The file hashes, digest or digital signature have an important role in securing downloads but it
have some limitations that should be overcome for increasing the security of the files. A hash
code can be appended with the message sent to the client and the value is compared at the other
end for finding the alternation made in the packet. The message can be affected by man in the
middle attack, where a duplicate hash value can be generated such that no difference can be
found in the altered message. Message digest is used for maintaining the integrity of the data and
finding the alteration to protect the data. The digital signature is embedded in the file for
checking the authenticity of the user and finding the owner of the file.
ADVANCED NETWORK SECURITY
Answer to Question 4: Trojan Download Research
a. The motivation and goals of the malicious users is to control the targeted system partially or
modify the information or data in the system. For example, the author name or digital signature
of a file can be changed by the malware. The current activity of the users can also be monitored
with the implementation of the malware and spyware. The malware can affect the software
developer because it can be used by the malicious users to add extra codes and cause the
developed software to malfunction. The Trojan virus are used for disguising the users for
accessing the resources and gain the access.
b. As an example of real Trojan or malware distributed using reputable sources are
download.com and old version of adobe flash player plugin. The download.com is a free source
to download software and it causes installation of more software accidentally and this may
contain Trojan or spigots that can be used for getting the access of the computer. The extension
or plugins installed in a browser can also be a malware and it can cause buffer overrun such that
new data cannot be accommodated and results in denial of service.
c. The file hashes, digest or digital signature have an important role in securing downloads but it
have some limitations that should be overcome for increasing the security of the files. A hash
code can be appended with the message sent to the client and the value is compared at the other
end for finding the alternation made in the packet. The message can be affected by man in the
middle attack, where a duplicate hash value can be generated such that no difference can be
found in the altered message. Message digest is used for maintaining the integrity of the data and
finding the alteration to protect the data. The digital signature is embedded in the file for
checking the authenticity of the user and finding the owner of the file.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
ADVANCED NETWORK SECURITY
MD3 and SHA1 algorithm are used for generation of the hash value and it can also be
used by the malicious users for generating the hash value and disguising the user. It is a complex
task to share the digital certificate and it may not be compatible with each other and thus it
cannot be used for verification.
d. The software can be distributed by the software developer by compiling the source code into a
executable file format and uploading in the internet server for making it available to the users to
download. There are different software management tools such as LANDesk management suite
available for Linux, Windows and OS X for the distribution of the software.
e. The users should follow the following recommendations for downloading the software
application such as:
Using clean and safe website for downloading the software and follow the rating of the
application for downloading it.
Using virtual machine for testing a new software and it protects the machine from
malware, spyware and adware because it does not have a direct impact on the physical
machine.
ADVANCED NETWORK SECURITY
MD3 and SHA1 algorithm are used for generation of the hash value and it can also be
used by the malicious users for generating the hash value and disguising the user. It is a complex
task to share the digital certificate and it may not be compatible with each other and thus it
cannot be used for verification.
d. The software can be distributed by the software developer by compiling the source code into a
executable file format and uploading in the internet server for making it available to the users to
download. There are different software management tools such as LANDesk management suite
available for Linux, Windows and OS X for the distribution of the software.
e. The users should follow the following recommendations for downloading the software
application such as:
Using clean and safe website for downloading the software and follow the rating of the
application for downloading it.
Using virtual machine for testing a new software and it protects the machine from
malware, spyware and adware because it does not have a direct impact on the physical
machine.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
ADVANCED NETWORK SECURITY
Bibliography
Acemoglu, D., Malekian, A. and Ozdaglar, A., 2016. Network security and contagion. Journal
of Economic Theory, 166, pp.536-585.
Anwar, R.W., Bakhtiari, M., Zainal, A., Abdullah, A.H. and Qureshi, K.N., 2014. Security issues
and attacks in wireless sensor network. World Applied Sciences Journal, 30(10), pp.1224-1227.
Jang, H., Jeong, J., Kim, H. and Park, J.S., 2015, March. A survey on interfaces to network
security functions in network virtualization. In Advanced Information Networking and
Applications Workshops (WAINA), 2015 IEEE 29th International Conference on (pp. 160-163).
IEEE.
JOSEPH. PHILLIPS, P.M.P., CBAP, I. and PMP, C., 2018. PMP PROJECT MANAGEMENT
PROFESSIONAL STUDY GUIDE. McGraw-Hill Education.
Joshi, M.R. and Karkade, R.A., 2015. Network security with cryptography. International
Journal of Computer Science and Mobile Computing” IJCSMCVol, 4, pp.201-204.
Kizza, J.M., 2017. Guide to computer network security. Springer.
Loo, J., Mauri, J.L. and Ortiz, J.H. eds., 2016. Mobile ad hoc networks: current status and future
trends. CRC Press.
Moon, C.S. and Kim, S.H., 2014. A study on the integrated security system based real-time
network packet deep inspection. International Journal of Security and Its Applications, 8(1),
pp.113-122.
ADVANCED NETWORK SECURITY
Bibliography
Acemoglu, D., Malekian, A. and Ozdaglar, A., 2016. Network security and contagion. Journal
of Economic Theory, 166, pp.536-585.
Anwar, R.W., Bakhtiari, M., Zainal, A., Abdullah, A.H. and Qureshi, K.N., 2014. Security issues
and attacks in wireless sensor network. World Applied Sciences Journal, 30(10), pp.1224-1227.
Jang, H., Jeong, J., Kim, H. and Park, J.S., 2015, March. A survey on interfaces to network
security functions in network virtualization. In Advanced Information Networking and
Applications Workshops (WAINA), 2015 IEEE 29th International Conference on (pp. 160-163).
IEEE.
JOSEPH. PHILLIPS, P.M.P., CBAP, I. and PMP, C., 2018. PMP PROJECT MANAGEMENT
PROFESSIONAL STUDY GUIDE. McGraw-Hill Education.
Joshi, M.R. and Karkade, R.A., 2015. Network security with cryptography. International
Journal of Computer Science and Mobile Computing” IJCSMCVol, 4, pp.201-204.
Kizza, J.M., 2017. Guide to computer network security. Springer.
Loo, J., Mauri, J.L. and Ortiz, J.H. eds., 2016. Mobile ad hoc networks: current status and future
trends. CRC Press.
Moon, C.S. and Kim, S.H., 2014. A study on the integrated security system based real-time
network packet deep inspection. International Journal of Security and Its Applications, 8(1),
pp.113-122.

11
ADVANCED NETWORK SECURITY
Pathan, A.S.K. ed., 2016. Security of self-organizing networks: MANET, WSN, WMN, VANET.
CRC press.
Pawar, M.V. and Anuradha, J., 2015. Network security and types of attacks in
network. Procedia Computer Science, 48, pp.503-506.
Perlman, R., Kaufman, C. and Speciner, M., 2016. Network security: private communication in a
public world. Pearson Education India.
Yan, F., Jian-Wen, Y. and Lin, C., 2015, June. Computer Network Security and Technology
Research. In Measuring Technology and Mechatronics Automation (ICMTMA), 2015 Seventh
International Conference on (pp. 293-296). IEEE.
ADVANCED NETWORK SECURITY
Pathan, A.S.K. ed., 2016. Security of self-organizing networks: MANET, WSN, WMN, VANET.
CRC press.
Pawar, M.V. and Anuradha, J., 2015. Network security and types of attacks in
network. Procedia Computer Science, 48, pp.503-506.
Perlman, R., Kaufman, C. and Speciner, M., 2016. Network security: private communication in a
public world. Pearson Education India.
Yan, F., Jian-Wen, Y. and Lin, C., 2015, June. Computer Network Security and Technology
Research. In Measuring Technology and Mechatronics Automation (ICMTMA), 2015 Seventh
International Conference on (pp. 293-296). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




