University Network Security: Analysis and Implementation Report
VerifiedAdded on 2020/04/01
|15
|2051
|45
Homework Assignment
AI Summary
This assignment provides a comprehensive analysis of advanced network security concepts. It begins with a network diagram and firewall rules, detailing their implementation and purpose. The assignment delves into WiFi security, explaining WPA/WPA2, antenna configurations, RADIUS authentication, and rogue AP detection. It then explores access control, including the structure and security of password files. The use of HTTPS and certificates is examined, including how certificates are obtained and verified. Finally, the assignment addresses internet privacy, discussing web proxies, VPNs, and the Tor network. The student demonstrates a strong understanding of network security principles and their practical application.

Running head: ADVANCED NETWORK SECURITY
Advanced Network Security
Name of the Student
Name of the University
Author’s Note
Advanced Network Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
ADVANCED NETWORK SECURITY
Table of Contents
Question 1. Firewalls...........................................................................................................2
Question 2. WiFi Security...................................................................................................3
Question 3. Access Control.................................................................................................5
Question 4. HTTPS and Certificates...................................................................................9
Question 5. Internet Privacy..............................................................................................11
Bibliography......................................................................................................................13
ADVANCED NETWORK SECURITY
Table of Contents
Question 1. Firewalls...........................................................................................................2
Question 2. WiFi Security...................................................................................................3
Question 3. Access Control.................................................................................................5
Question 4. HTTPS and Certificates...................................................................................9
Question 5. Internet Privacy..............................................................................................11
Bibliography......................................................................................................................13
2
ADVANCED NETWORK SECURITY
Question 1. Firewalls
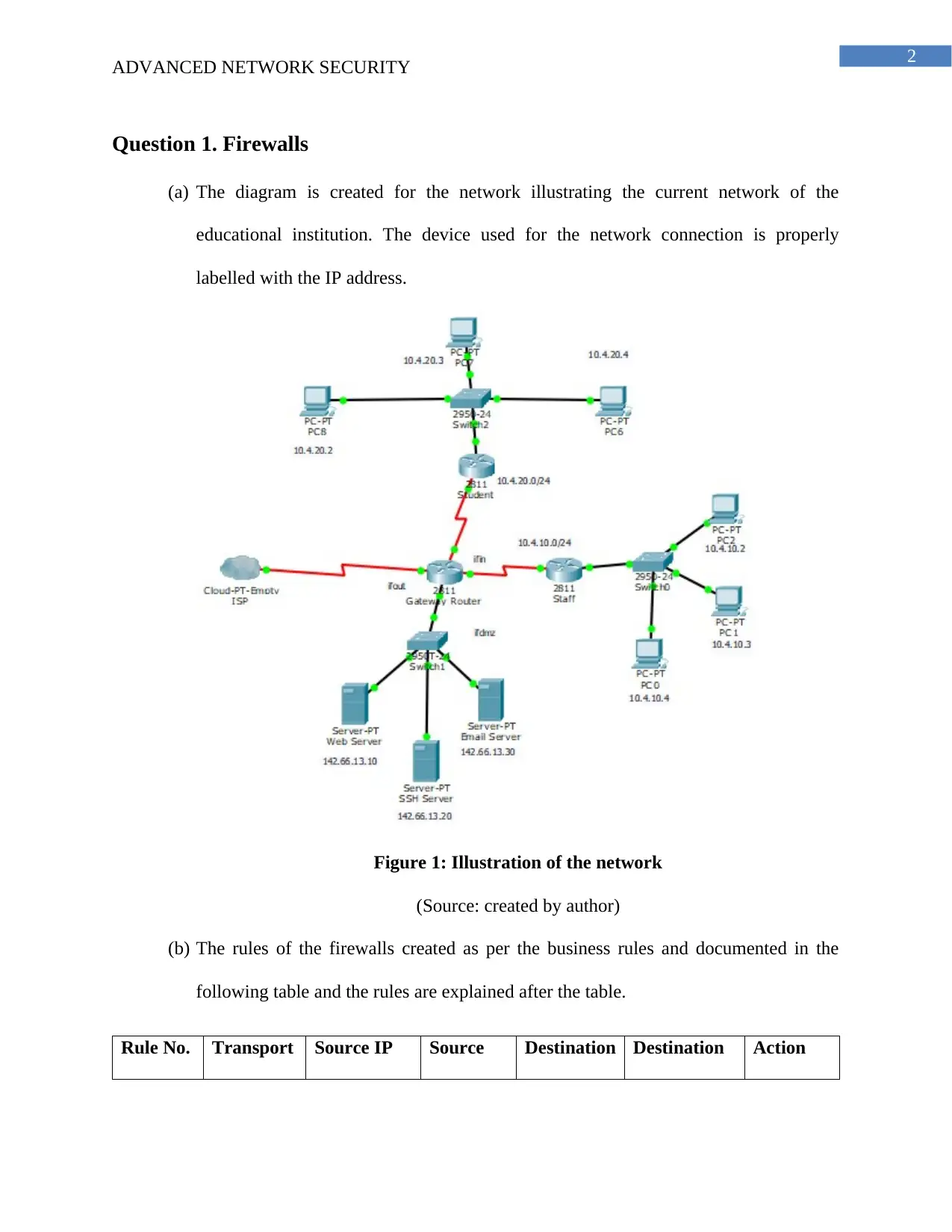
(a) The diagram is created for the network illustrating the current network of the
educational institution. The device used for the network connection is properly
labelled with the IP address.
Figure 1: Illustration of the network
(Source: created by author)
(b) The rules of the firewalls created as per the business rules and documented in the
following table and the rules are explained after the table.
Rule No. Transport Source IP Source Destination Destination Action
ADVANCED NETWORK SECURITY
Question 1. Firewalls
(a) The diagram is created for the network illustrating the current network of the
educational institution. The device used for the network connection is properly
labelled with the IP address.
Figure 1: Illustration of the network
(Source: created by author)
(b) The rules of the firewalls created as per the business rules and documented in the
following table and the rules are explained after the table.
Rule No. Transport Source IP Source Destination Destination Action
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
ADVANCED NETWORK SECURITY
Port Port IP
1 TCP Any 143 143 142.66.13.10 Deny
2 TCP Any 1433 1433 142.66.13.30 Allow
3 TCP Any 1023 Any 142.66.13.20 Deny
4 TCP 10.4.10.0 –
10.4.10.255
143 143 142.66.13.10 Allow
5 TCP 142.66.13.10 1023 Any 142.66.13.30 Allow
6 TCP 142.66.13.30 1023 Any 142.66.13.20 Allow
7 TCP 10.40.10.2 1234 1234 10.4.10.4 Allow
8 TCP 10.40.20.2 1234 1234 10.40.10.3 Allow
9 TCP 10.40.10.3 1234 1234 Any Deny
(c) The default policy of the firewall can be created using the iptables and –L can be used
for the chain input accept policy and set the forwarding rules in the firewall. The –A
can be used for accepting the policy and application in the specified port dropping or
accepting the data packets in the network.
Question 2. WiFi Security
(a) WPA or wifi protected access is used in the wireless network for increasing the
security of the network solution and restrict the unauthorized users to connect with
the network. There is another version of WPA that is WPA2 and it came into play
since 2003 as a replacement of the WEP. TKIP is used as an encryption algorithm for
WPA and a 128 bit key is generated for prevention of the different types of attacks.
(b) Antennas, transmit power and AP positioning for controlling the radio range
ADVANCED NETWORK SECURITY
Port Port IP
1 TCP Any 143 143 142.66.13.10 Deny
2 TCP Any 1433 1433 142.66.13.30 Allow
3 TCP Any 1023 Any 142.66.13.20 Deny
4 TCP 10.4.10.0 –
10.4.10.255
143 143 142.66.13.10 Allow
5 TCP 142.66.13.10 1023 Any 142.66.13.30 Allow
6 TCP 142.66.13.30 1023 Any 142.66.13.20 Allow
7 TCP 10.40.10.2 1234 1234 10.4.10.4 Allow
8 TCP 10.40.20.2 1234 1234 10.40.10.3 Allow
9 TCP 10.40.10.3 1234 1234 Any Deny
(c) The default policy of the firewall can be created using the iptables and –L can be used
for the chain input accept policy and set the forwarding rules in the firewall. The –A
can be used for accepting the policy and application in the specified port dropping or
accepting the data packets in the network.
Question 2. WiFi Security
(a) WPA or wifi protected access is used in the wireless network for increasing the
security of the network solution and restrict the unauthorized users to connect with
the network. There is another version of WPA that is WPA2 and it came into play
since 2003 as a replacement of the WEP. TKIP is used as an encryption algorithm for
WPA and a 128 bit key is generated for prevention of the different types of attacks.
(b) Antennas, transmit power and AP positioning for controlling the radio range
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
ADVANCED NETWORK SECURITY
The antennas are used in the wireless networks for generation of wireless signals and
it acts as an extension of the radio. There are different factors that can affect the range
of the antennas and it mainly depends on the amount of energy entering into the
antenna. When the radio energy are passed the transmit power is required to be
controlled and it should control the gain of the signal and increase the efficiency of
the wireless radio network.
The transmit power depends on the polarization, gain of the antenna and attenuation.
There are different types of antennas such as the Omni directional antennas, point to
point and directional antennas. If there is more attenuation then the transmit power is
required to meet the loss of signal.
The access point is also required to be placed in the proper location for covering the
whole area and the selection of the antenna is essential for increasing the security of
the network. Proper encryption is required to be used in the access point for
restricting it from unauthorized access.
(c) RADIUS authentication
It is used for centralized authentication of the wireless network and AAA protocol is
used for authentication of the servers. The RADIUS protocol is utilized by the ISP for
management of the internal and the external networks. Two types of packets are used
by the RADIUS for the management of the access of the authentication, accounting
and authorization.
(d) Manually detecting the rogue Aps
For detecting the rogue access point the risk associated with the wireless network is
required to be analyzed and the vulnerability of the network is required to be noted.
ADVANCED NETWORK SECURITY
The antennas are used in the wireless networks for generation of wireless signals and
it acts as an extension of the radio. There are different factors that can affect the range
of the antennas and it mainly depends on the amount of energy entering into the
antenna. When the radio energy are passed the transmit power is required to be
controlled and it should control the gain of the signal and increase the efficiency of
the wireless radio network.
The transmit power depends on the polarization, gain of the antenna and attenuation.
There are different types of antennas such as the Omni directional antennas, point to
point and directional antennas. If there is more attenuation then the transmit power is
required to meet the loss of signal.
The access point is also required to be placed in the proper location for covering the
whole area and the selection of the antenna is essential for increasing the security of
the network. Proper encryption is required to be used in the access point for
restricting it from unauthorized access.
(c) RADIUS authentication
It is used for centralized authentication of the wireless network and AAA protocol is
used for authentication of the servers. The RADIUS protocol is utilized by the ISP for
management of the internal and the external networks. Two types of packets are used
by the RADIUS for the management of the access of the authentication, accounting
and authorization.
(d) Manually detecting the rogue Aps
For detecting the rogue access point the risk associated with the wireless network is
required to be analyzed and the vulnerability of the network is required to be noted.
5
ADVANCED NETWORK SECURITY
The security measures that can be applied for increasing the security of the network is
required to be evaluated for increasing the flexibility of the network. The access point
that are connected with the wired network is required to be secured from
unauthorized access to reduce the risk of susceptible attacks.
Question 3. Access Control
ADVANCED NETWORK SECURITY
The security measures that can be applied for increasing the security of the network is
required to be evaluated for increasing the flexibility of the network. The access point
that are connected with the wired network is required to be secured from
unauthorized access to reduce the risk of susceptible attacks.
Question 3. Access Control
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
ADVANCED NETWORK SECURITY
ADVANCED NETWORK SECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
ADVANCED NETWORK SECURITY
ADVANCED NETWORK SECURITY
8
ADVANCED NETWORK SECURITY
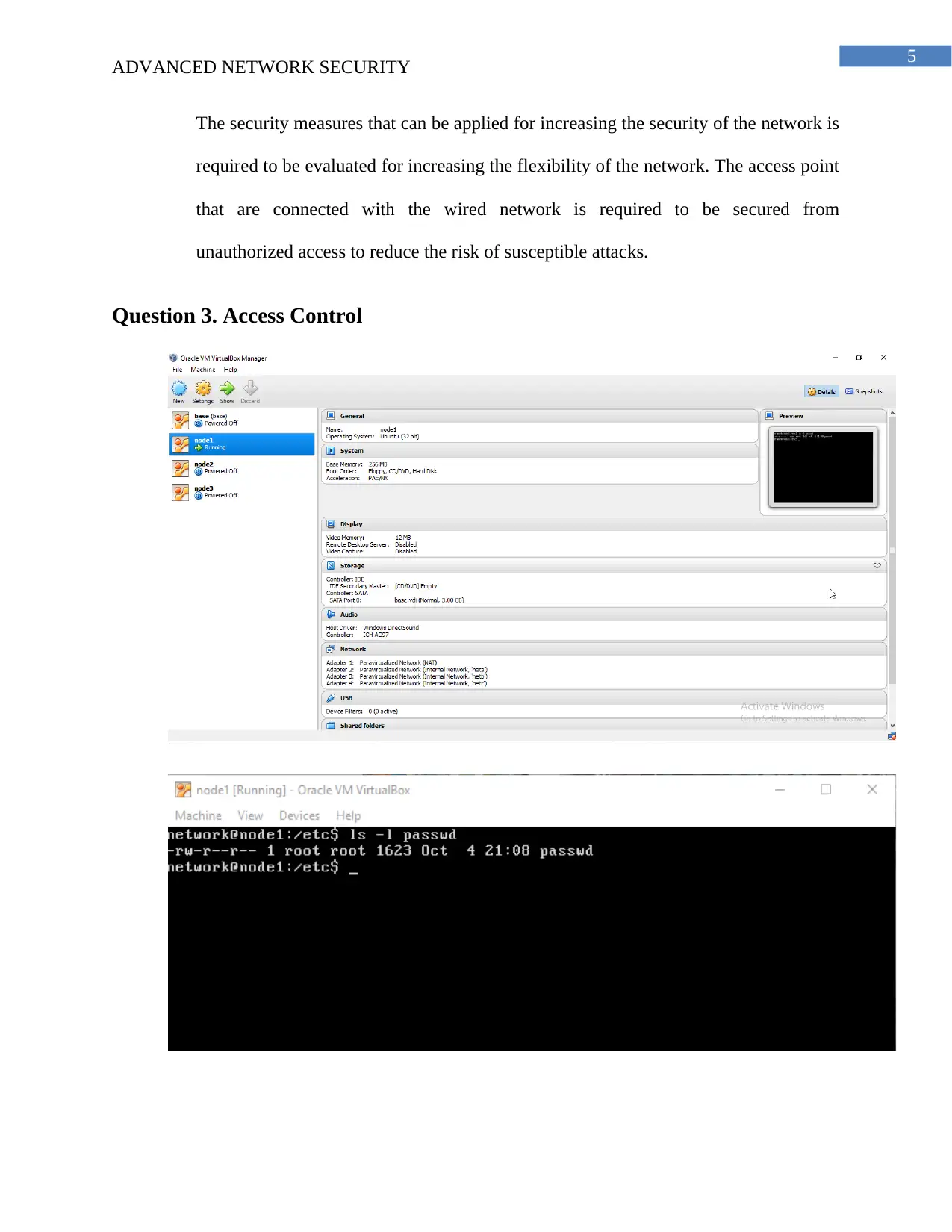
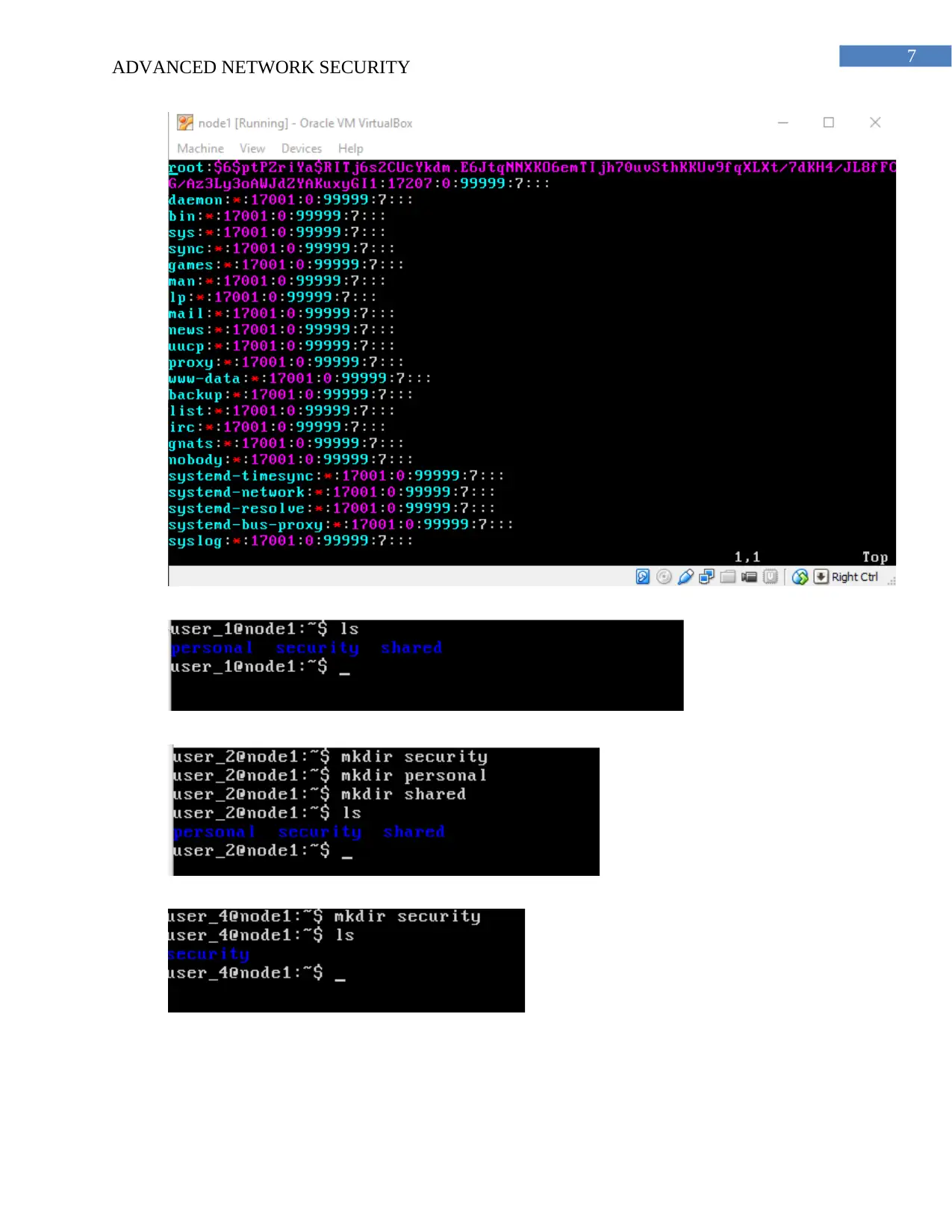
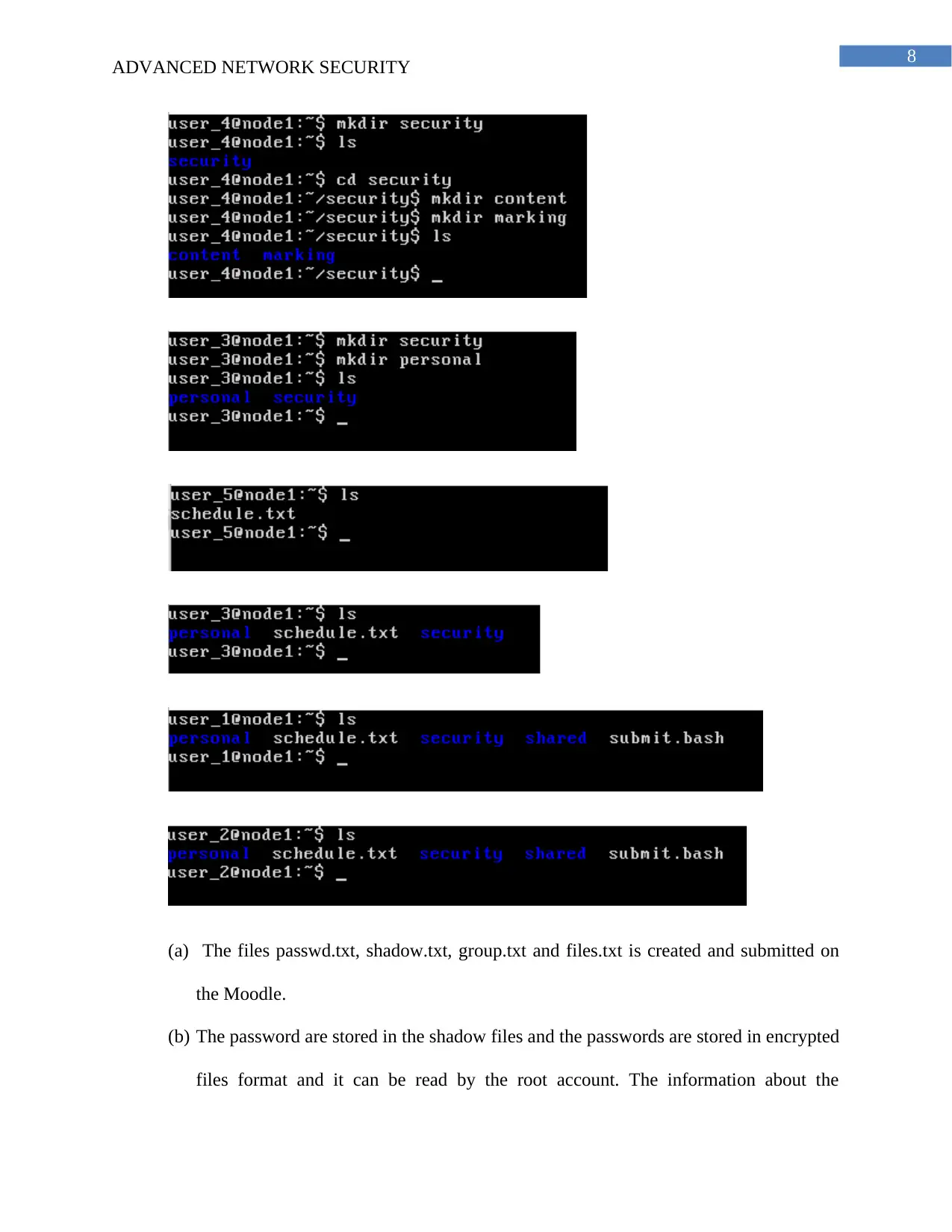
(a) The files passwd.txt, shadow.txt, group.txt and files.txt is created and submitted on
the Moodle.
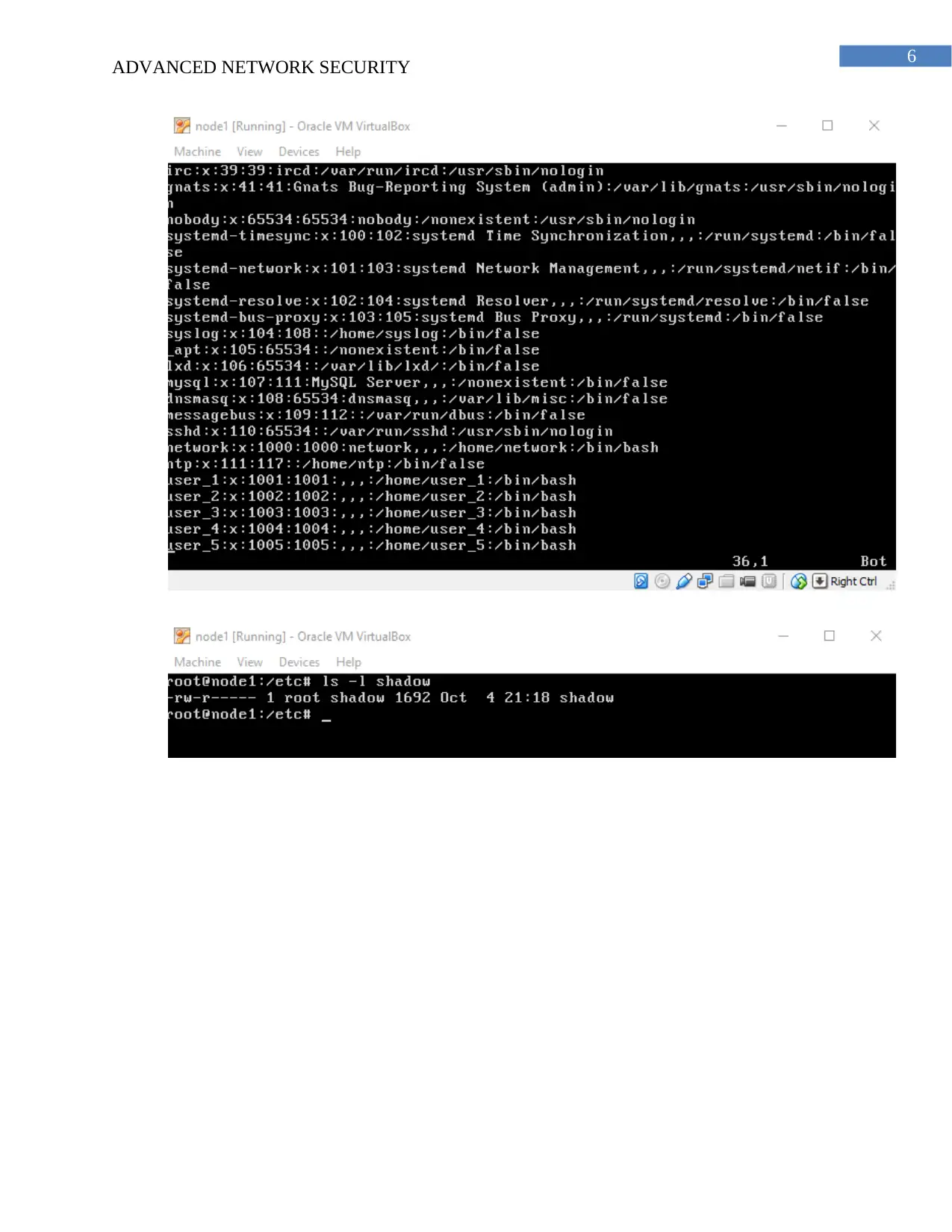
(b) The password are stored in the shadow files and the passwords are stored in encrypted
files format and it can be read by the root account. The information about the
ADVANCED NETWORK SECURITY
(a) The files passwd.txt, shadow.txt, group.txt and files.txt is created and submitted on
the Moodle.
(b) The password are stored in the shadow files and the passwords are stored in encrypted
files format and it can be read by the root account. The information about the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
ADVANCED NETWORK SECURITY
password are stored in the shadow file and other information are stored in the passwd
file. The file format used for the storage of the password and the shadow file is .txt.
Each of the fields of the shadow and the password files are separated using a colon
and are case sensitive.
(c) The administrator cannot distinguish the passwords of the different users because the
passwords are stored in encrypted format and thus the same passwords cannot be
distinguished.
(d) If the passwd.txt file is accessible to the malicious user it can be used because all the
information are stored in encrypted and cipher text is used for the encryption. 128 bit
encryption is used for the encryption of the password and for recovering the password
and the user name the key is also required.
Question 4. HTTPS and Certificates
ADVANCED NETWORK SECURITY
password are stored in the shadow file and other information are stored in the passwd
file. The file format used for the storage of the password and the shadow file is .txt.
Each of the fields of the shadow and the password files are separated using a colon
and are case sensitive.
(c) The administrator cannot distinguish the passwords of the different users because the
passwords are stored in encrypted format and thus the same passwords cannot be
distinguished.
(d) If the passwd.txt file is accessible to the malicious user it can be used because all the
information are stored in encrypted and cipher text is used for the encryption. 128 bit
encryption is used for the encryption of the password and for recovering the password
and the user name the key is also required.
Question 4. HTTPS and Certificates
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
ADVANCED NETWORK SECURITY
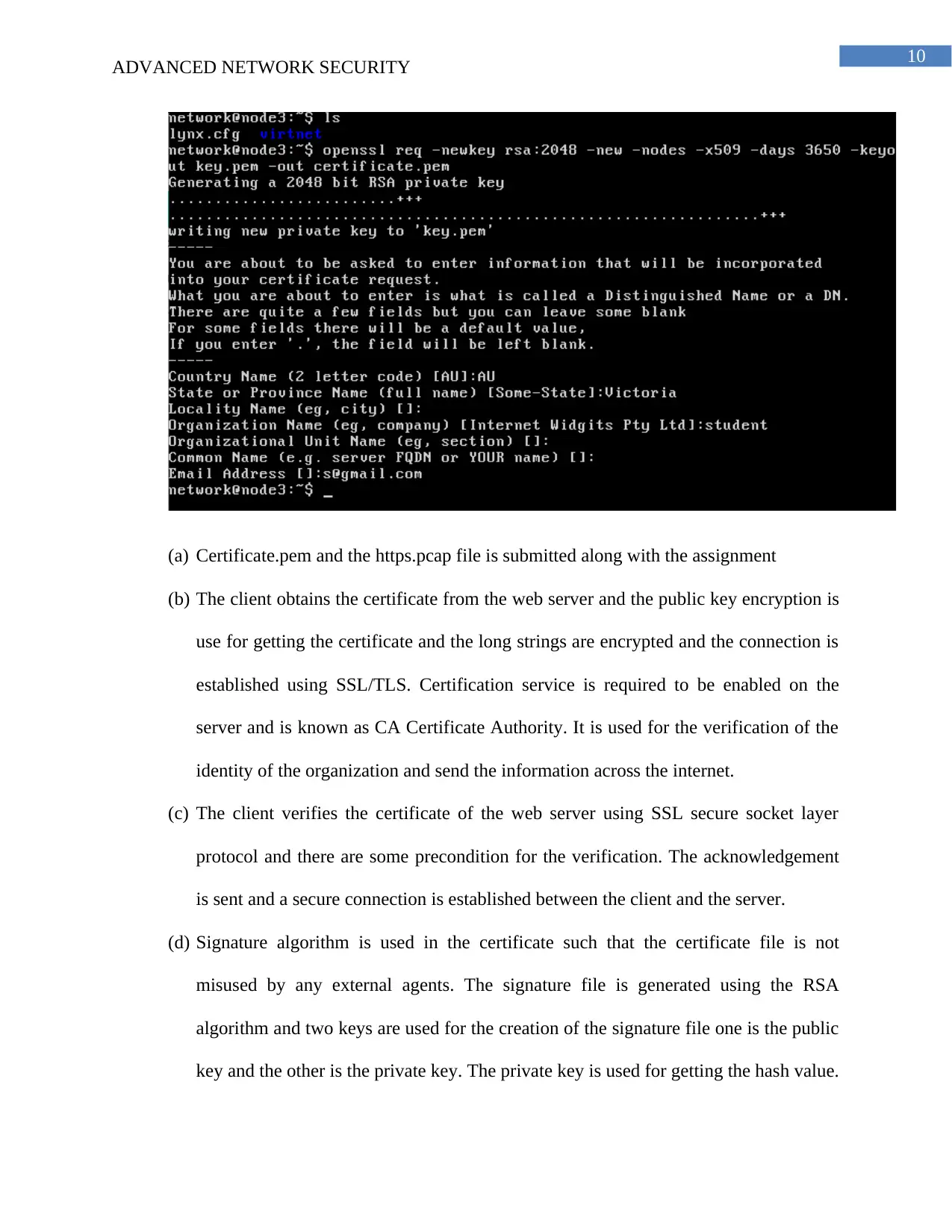
(a) Certificate.pem and the https.pcap file is submitted along with the assignment
(b) The client obtains the certificate from the web server and the public key encryption is
use for getting the certificate and the long strings are encrypted and the connection is
established using SSL/TLS. Certification service is required to be enabled on the
server and is known as CA Certificate Authority. It is used for the verification of the
identity of the organization and send the information across the internet.
(c) The client verifies the certificate of the web server using SSL secure socket layer
protocol and there are some precondition for the verification. The acknowledgement
is sent and a secure connection is established between the client and the server.
(d) Signature algorithm is used in the certificate such that the certificate file is not
misused by any external agents. The signature file is generated using the RSA
algorithm and two keys are used for the creation of the signature file one is the public
key and the other is the private key. The private key is used for getting the hash value.
ADVANCED NETWORK SECURITY
(a) Certificate.pem and the https.pcap file is submitted along with the assignment
(b) The client obtains the certificate from the web server and the public key encryption is
use for getting the certificate and the long strings are encrypted and the connection is
established using SSL/TLS. Certification service is required to be enabled on the
server and is known as CA Certificate Authority. It is used for the verification of the
identity of the organization and send the information across the internet.
(c) The client verifies the certificate of the web server using SSL secure socket layer
protocol and there are some precondition for the verification. The acknowledgement
is sent and a secure connection is established between the client and the server.
(d) Signature algorithm is used in the certificate such that the certificate file is not
misused by any external agents. The signature file is generated using the RSA
algorithm and two keys are used for the creation of the signature file one is the public
key and the other is the private key. The private key is used for getting the hash value.

11
ADVANCED NETWORK SECURITY
(e) The information stored in the servers are encrypted using the RSA algorithm and it
uses two keys and if the private key is available to the malicious user it can be used
for decryption and thee security of the network would be compromised. For example
the certificate generated for the MyUni website it is used for the establishment of a
secure connection between the nodes.
Question 5. Internet Privacy
(a) Web Proxies
The web proxies are used for accessing a website and it acts as a middleman between the
user and the website. It can be used such that the information of the user are not disclosed
to the client. The user information are masked and acts as a shield for hiding the presence
of the users. There are different proxy servers available online such as anonymouse.org,
tor that can be used as a web proxy and anonymous browsing on the internet.
(b) VPNs
The virtual private system helps the sender and the collector to send and get information
using an open system safely. Here the customer sends information to the server by means
of n number of switches and distinctive ways can be utilized for achieving the goal
address and vpn can be utilized for securing the channel of correspondence and
expanding the effectiveness of the system arrangement. A point to point association is set
up and distinctive intermediary servers are utilized for the assurance of the personality
ADVANCED NETWORK SECURITY
(e) The information stored in the servers are encrypted using the RSA algorithm and it
uses two keys and if the private key is available to the malicious user it can be used
for decryption and thee security of the network would be compromised. For example
the certificate generated for the MyUni website it is used for the establishment of a
secure connection between the nodes.
Question 5. Internet Privacy
(a) Web Proxies
The web proxies are used for accessing a website and it acts as a middleman between the
user and the website. It can be used such that the information of the user are not disclosed
to the client. The user information are masked and acts as a shield for hiding the presence
of the users. There are different proxy servers available online such as anonymouse.org,
tor that can be used as a web proxy and anonymous browsing on the internet.
(b) VPNs
The virtual private system helps the sender and the collector to send and get information
using an open system safely. Here the customer sends information to the server by means
of n number of switches and distinctive ways can be utilized for achieving the goal
address and vpn can be utilized for securing the channel of correspondence and
expanding the effectiveness of the system arrangement. A point to point association is set
up and distinctive intermediary servers are utilized for the assurance of the personality
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





