Advanced Network Security: Cookie Stealing Attack, Cryptography, Ransomware Research
VerifiedAdded on 2023/06/10
|10
|1527
|359
AI Summary
Learn about cookie stealing attack, cryptography, and ransomware research in advanced network security. This article covers the technical details of ransomware, recommendations to prevent ransomware, and issues of security in cryptography. It also includes a step-by-step guide to perform cookie stealing attack using virtnet. Subject: Network Security, Course Code: NA, Course Name: NA, College/University: NA.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

advanced network security
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
1. Cookie Stealing Attack................................................................................................................2
2. Cryptography...............................................................................................................................5
3. Ransomware Research................................................................................................................7
References............................................................................................................................................9
1
1. Cookie Stealing Attack................................................................................................................2
2. Cryptography...............................................................................................................................5
3. Ransomware Research................................................................................................................7
References............................................................................................................................................9
1

1. Cookie Stealing Attack
Here we will use virtnet to perform the cookie stealing attack. To perform cooking
stealing attack by following the below steps.
• Create topology 7 in virtnet
• Add a new normal student user
• Add a new malicious student user
• Test the existing users.
• Capture the cookies by using tcpdump.
• For capturing the packet with the help of malicious student user, perform Masquerade
attack.
• To masquerade as a normal student user, cookie stealing attack must be performed.
• Normal users’ password is captured and recorded.
• On node 3, the packet is captured.
The captured packets are attached below (Huang, 2014).
Part (a)
Pcap file is attached here.
Part (b)
Pcap file is attached here.
2
Here we will use virtnet to perform the cookie stealing attack. To perform cooking
stealing attack by following the below steps.
• Create topology 7 in virtnet
• Add a new normal student user
• Add a new malicious student user
• Test the existing users.
• Capture the cookies by using tcpdump.
• For capturing the packet with the help of malicious student user, perform Masquerade
attack.
• To masquerade as a normal student user, cookie stealing attack must be performed.
• Normal users’ password is captured and recorded.
• On node 3, the packet is captured.
The captured packets are attached below (Huang, 2014).
Part (a)
Pcap file is attached here.
Part (b)
Pcap file is attached here.
2
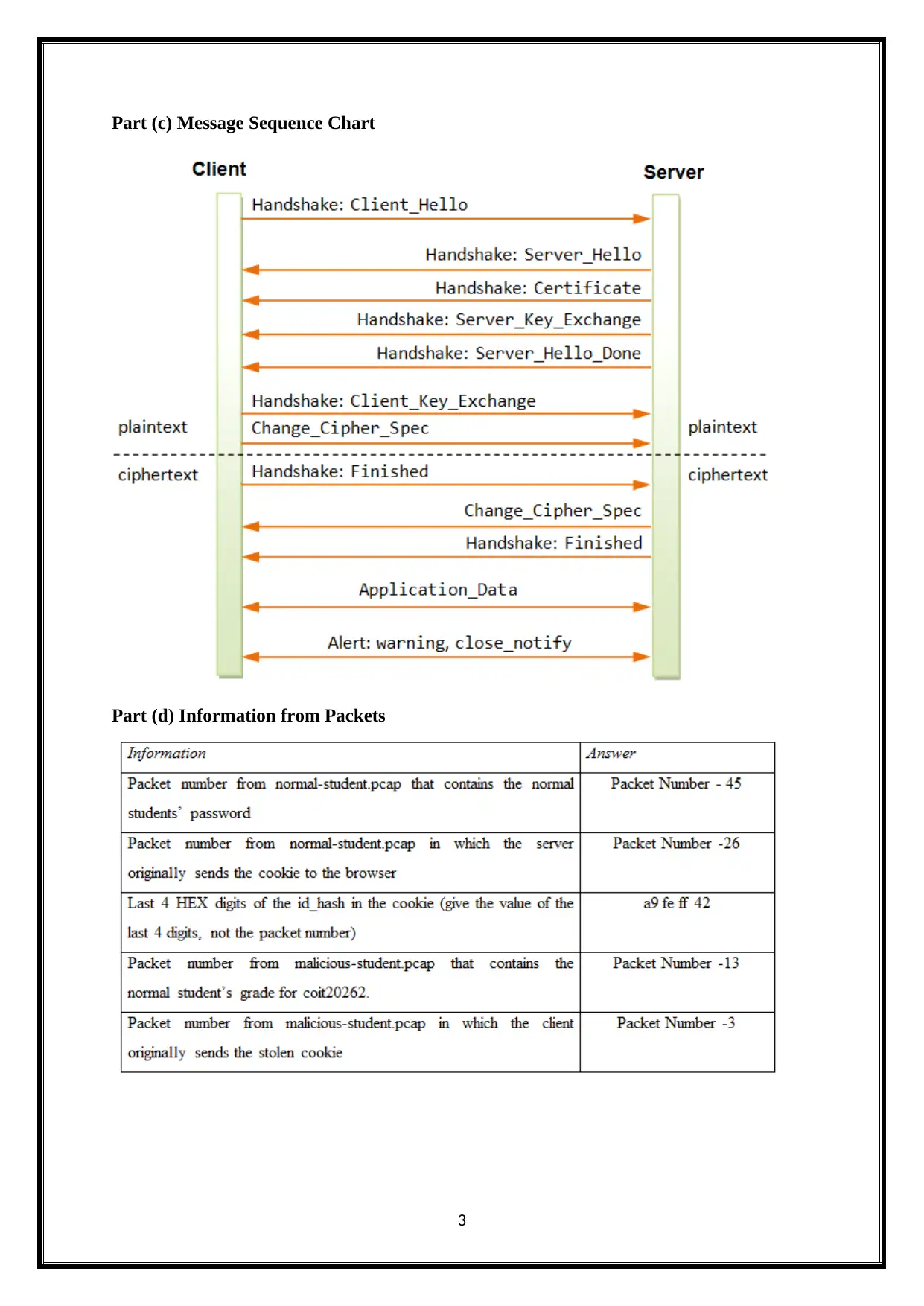
Part (c) Message Sequence Chart
Part (d) Information from Packets
3
Part (d) Information from Packets
3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Part (e)
In order to calculate the ID hash of the id that is used in the Merkle Tree, one needs to
SHA hash the whole id message as defined in the Protocol Specification wiki page twice.
Part (f)
Hash function are very helpful and show up in all data security applications. A hash
function refers to a mathematical function which changes when there is numerical
information approval in other packed numerical esteem. Then, the hash function contribution
is of a subjective length, but still it yields dependably on the established length. The hash
function contains various objectives, other than cryptography. The practical applications
incorporate message integrity checks, validation, digital signatures, as well as different data
security applications (Kotenko, 2012).
Part (g)
If a weakness is found in the hash function which considers two records in to account,
for having exact same process. The capacity is broken cryptographically, such that the
computerized fingerprints which are created could be manufactured and results in less trust
worthy. For instance, the attackers can make a rogue software program for refresh which
could be acknowledged as well as executed with a refresh system that ensures to give
confirmation to refresh, by checking the computerized marks.
Part (h)
From the browser to server, if a normal student user sends the password as a plaintext,
it creates insecurity. So, we need to use the hash function for storing the passwords. Due to
this, it requires the members to have passwords that are stronger. This can be achieved with
the enforcement of mixed characters, minimum lengths, and digital along with special
characters.
Part (i)
Cookies creation
Generally, the browser stores the cookie and it is sent on a request, which is made to
the exact same server within a cookie HTTP header.
Set-Cookie: <cookie-name>=<cookie-value>
Cookies in the web browser
First, go and check "Chrome Developer Tools"
Select Menu → then select "Tools" → and next select "Developer Tools".
4
In order to calculate the ID hash of the id that is used in the Merkle Tree, one needs to
SHA hash the whole id message as defined in the Protocol Specification wiki page twice.
Part (f)
Hash function are very helpful and show up in all data security applications. A hash
function refers to a mathematical function which changes when there is numerical
information approval in other packed numerical esteem. Then, the hash function contribution
is of a subjective length, but still it yields dependably on the established length. The hash
function contains various objectives, other than cryptography. The practical applications
incorporate message integrity checks, validation, digital signatures, as well as different data
security applications (Kotenko, 2012).
Part (g)
If a weakness is found in the hash function which considers two records in to account,
for having exact same process. The capacity is broken cryptographically, such that the
computerized fingerprints which are created could be manufactured and results in less trust
worthy. For instance, the attackers can make a rogue software program for refresh which
could be acknowledged as well as executed with a refresh system that ensures to give
confirmation to refresh, by checking the computerized marks.
Part (h)
From the browser to server, if a normal student user sends the password as a plaintext,
it creates insecurity. So, we need to use the hash function for storing the passwords. Due to
this, it requires the members to have passwords that are stronger. This can be achieved with
the enforcement of mixed characters, minimum lengths, and digital along with special
characters.
Part (i)
Cookies creation
Generally, the browser stores the cookie and it is sent on a request, which is made to
the exact same server within a cookie HTTP header.
Set-Cookie: <cookie-name>=<cookie-value>
Cookies in the web browser
First, go and check "Chrome Developer Tools"
Select Menu → then select "Tools" → and next select "Developer Tools".
4
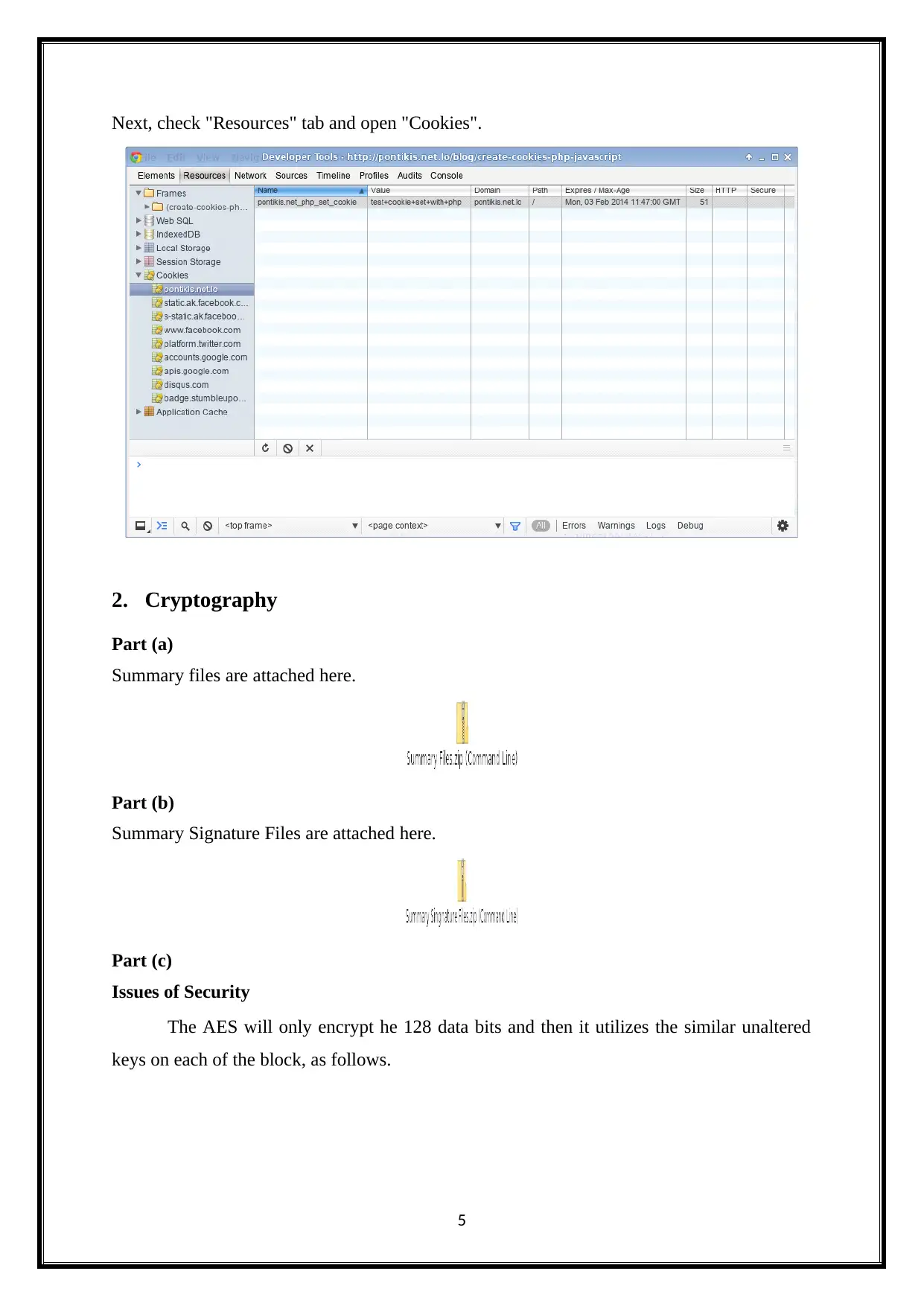
Next, check "Resources" tab and open "Cookies".
2. Cryptography
Part (a)
Summary files are attached here.
Part (b)
Summary Signature Files are attached here.
Part (c)
Issues of Security
The AES will only encrypt he 128 data bits and then it utilizes the similar unaltered
keys on each of the block, as follows.
5
2. Cryptography
Part (a)
Summary files are attached here.
Part (b)
Summary Signature Files are attached here.
Part (c)
Issues of Security
The AES will only encrypt he 128 data bits and then it utilizes the similar unaltered
keys on each of the block, as follows.
5
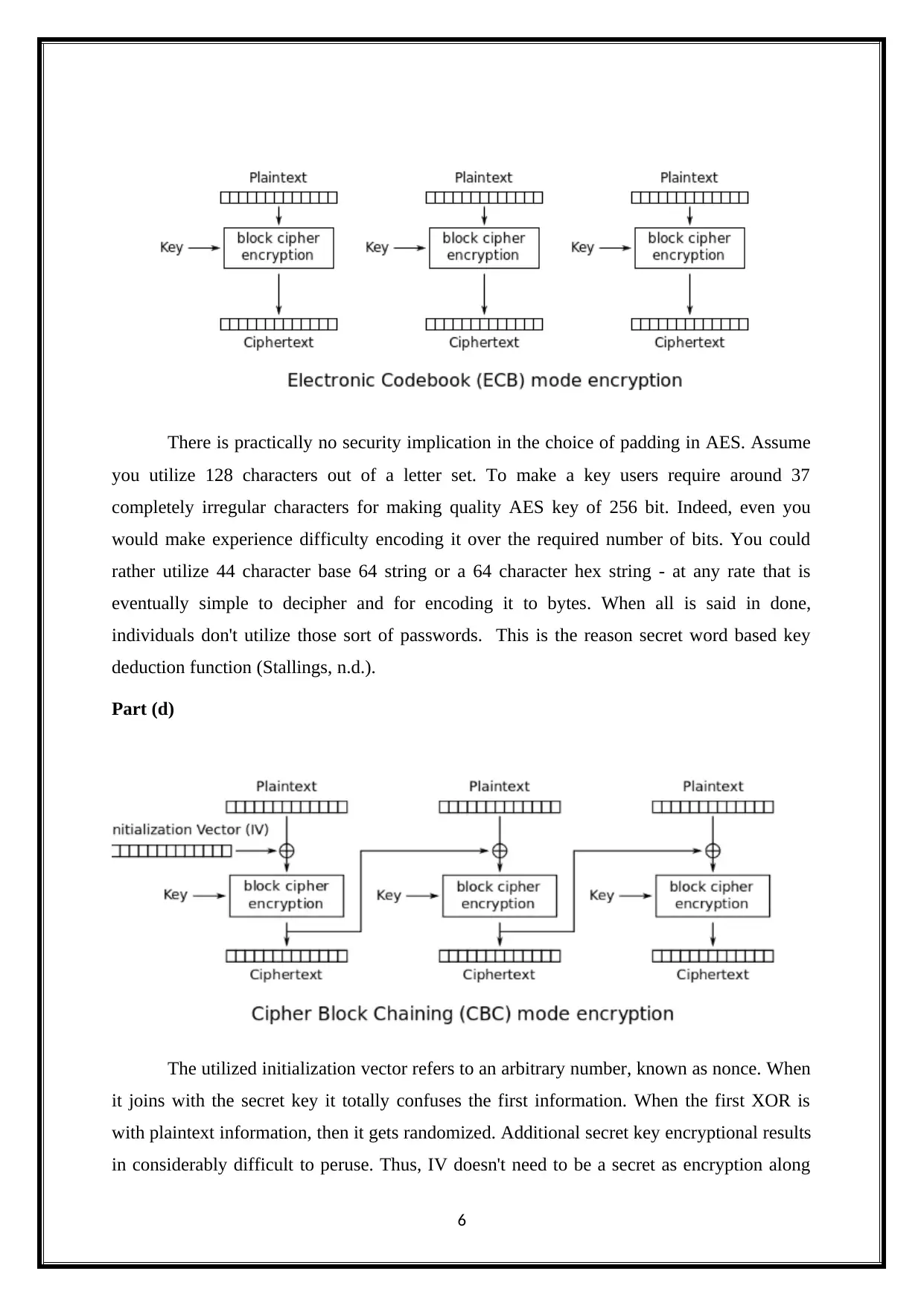
There is practically no security implication in the choice of padding in AES. Assume
you utilize 128 characters out of a letter set. To make a key users require around 37
completely irregular characters for making quality AES key of 256 bit. Indeed, even you
would make experience difficulty encoding it over the required number of bits. You could
rather utilize 44 character base 64 string or a 64 character hex string - at any rate that is
eventually simple to decipher and for encoding it to bytes. When all is said in done,
individuals don't utilize those sort of passwords. This is the reason secret word based key
deduction function (Stallings, n.d.).
Part (d)
The utilized initialization vector refers to an arbitrary number, known as nonce. When
it joins with the secret key it totally confuses the first information. When the first XOR is
with plaintext information, then it gets randomized. Additional secret key encryptional results
in considerably difficult to peruse. Thus, IV doesn't need to be a secret as encryption along
6
you utilize 128 characters out of a letter set. To make a key users require around 37
completely irregular characters for making quality AES key of 256 bit. Indeed, even you
would make experience difficulty encoding it over the required number of bits. You could
rather utilize 44 character base 64 string or a 64 character hex string - at any rate that is
eventually simple to decipher and for encoding it to bytes. When all is said in done,
individuals don't utilize those sort of passwords. This is the reason secret word based key
deduction function (Stallings, n.d.).
Part (d)
The utilized initialization vector refers to an arbitrary number, known as nonce. When
it joins with the secret key it totally confuses the first information. When the first XOR is
with plaintext information, then it gets randomized. Additional secret key encryptional results
in considerably difficult to peruse. Thus, IV doesn't need to be a secret as encryption along
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

with a secret key provides the necessary secret. Additionally, the information within the
scrambled document cannot be speculated in AES-CBC. Because, it carries out numerous
encryption rounds.
3. Ransomware Research
Overview of Ransomware
Ransomware refers to a type of malware which keeps the clients safe from getting to
their framework or individual records and requests free segment with a specific end goal to
recapture. There exists some different methods using which the ransomware could taint the
victim's computer. Today, the unique and popular method is through malicious spam/
malspam, which are spread through email. The malicious programming or malware such as
Ransomware refers to a program, which once it gets the control over the user’s computer,
then it can cause various threats, especially rejecting the user access to all their information
present in the computer. For the victim, the attacker sends a request of payment which
promises to re-establish their access to their own information.
How ransomware functions
Generally, several vectors ransomware exists which could get to a computer. Phishing
spam connections is the uniquely identified conveyance frameworks, which are delivered to
the victims by means of email. If the victim opens tis mail or downloads the file then, the
hackers can easily have control on the computer of the victim. This especially happens when
they have worked in social building devices which traps the clients into permitting
authoritative access. In some sorts of malware, the attacker might refer to be the law
implementation office, which is closing the computer of the victim. Due to the presence of
pilfered programming. Be that as it may, most attacks don't waste time with this
misrepresentation. Similarly, there is a variety named as leak ware or doxware, where the
attacker incapacitates to plug delicate information on the victim's hard drive except if a
payoff is paid. But, since identifying and discarding such type of data is an exceptionally
precarious suggestion for the attackers, encryption ransomware is the highly identified
method. Another well-known method is malvertising. Malvertising, or malicious promoting,
is the utilization of web based publicizing for dispersing the malware with next to the
required zero client cooperation. Regularly, that malware refers to ransomware.
Technical Details of Ransomware
There are a couple of principle ransomware type which are normally observed at present:
7
scrambled document cannot be speculated in AES-CBC. Because, it carries out numerous
encryption rounds.
3. Ransomware Research
Overview of Ransomware
Ransomware refers to a type of malware which keeps the clients safe from getting to
their framework or individual records and requests free segment with a specific end goal to
recapture. There exists some different methods using which the ransomware could taint the
victim's computer. Today, the unique and popular method is through malicious spam/
malspam, which are spread through email. The malicious programming or malware such as
Ransomware refers to a program, which once it gets the control over the user’s computer,
then it can cause various threats, especially rejecting the user access to all their information
present in the computer. For the victim, the attacker sends a request of payment which
promises to re-establish their access to their own information.
How ransomware functions
Generally, several vectors ransomware exists which could get to a computer. Phishing
spam connections is the uniquely identified conveyance frameworks, which are delivered to
the victims by means of email. If the victim opens tis mail or downloads the file then, the
hackers can easily have control on the computer of the victim. This especially happens when
they have worked in social building devices which traps the clients into permitting
authoritative access. In some sorts of malware, the attacker might refer to be the law
implementation office, which is closing the computer of the victim. Due to the presence of
pilfered programming. Be that as it may, most attacks don't waste time with this
misrepresentation. Similarly, there is a variety named as leak ware or doxware, where the
attacker incapacitates to plug delicate information on the victim's hard drive except if a
payoff is paid. But, since identifying and discarding such type of data is an exceptionally
precarious suggestion for the attackers, encryption ransomware is the highly identified
method. Another well-known method is malvertising. Malvertising, or malicious promoting,
is the utilization of web based publicizing for dispersing the malware with next to the
required zero client cooperation. Regularly, that malware refers to ransomware.
Technical Details of Ransomware
There are a couple of principle ransomware type which are normally observed at present:
7

• On a computer, Crypto-ransomware encodes the records, it 'scrambles' the document
substance, such that the client won’t reach it without the presence of a decoding key
which can accurately 'unscramble' it.
• "Police-themed" ransomware endeavours for covering the activities by seeming, by
all accounts, to be a notice from a neighbourhood rule authorization specialist,
apparently to possess materials that are wrongfully downloaded, obscene or generally
booty.
Recommendations
Four Recommendations for prevent the ransomware. These are,
• Ensure that the user's Operating system is up dated, this guarantees to have lower
vulnerabilities and secures from any misusing.
• Make sure no software is installed or don’t provide any administrative privileges
except if you are aware of what actually it is and what it could do.
• Install antivirus programs that helps to discriminate any malicious activities such as
ransomware as they arrive, and during the time of programming. In any
circumstances, this avoids execution of any unapproved applications.
• Next, often back up all the documents, automatically. This will decrease the level of
harm.
8
substance, such that the client won’t reach it without the presence of a decoding key
which can accurately 'unscramble' it.
• "Police-themed" ransomware endeavours for covering the activities by seeming, by
all accounts, to be a notice from a neighbourhood rule authorization specialist,
apparently to possess materials that are wrongfully downloaded, obscene or generally
booty.
Recommendations
Four Recommendations for prevent the ransomware. These are,
• Ensure that the user's Operating system is up dated, this guarantees to have lower
vulnerabilities and secures from any misusing.
• Make sure no software is installed or don’t provide any administrative privileges
except if you are aware of what actually it is and what it could do.
• Install antivirus programs that helps to discriminate any malicious activities such as
ransomware as they arrive, and during the time of programming. In any
circumstances, this avoids execution of any unapproved applications.
• Next, often back up all the documents, automatically. This will decrease the level of
harm.
8

References
Huang, S. (2014). Network security. [Place of publication not identified]: Springer.
Kotenko, I. (2012). Computer network security. Berlin: Springer.
Stallings, W. (n.d.). Cryptography and network security.
9
Huang, S. (2014). Network security. [Place of publication not identified]: Springer.
Kotenko, I. (2012). Computer network security. Berlin: Springer.
Stallings, W. (n.d.). Cryptography and network security.
9
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




