Advanced Network Security Assignment: Protocols and Techniques
VerifiedAdded on 2020/03/16
|19
|3116
|36
Homework Assignment
AI Summary
This assignment delves into the realm of advanced network security, covering a range of critical topics. It begins with an exploration of firewalls, examining IP Tables and default policies. The assignment then moves on to WiFi security, analyzing WPA, its advantages, and disadvantages, followed by a discussion of RADIUS authentication and its benefits and drawbacks, concluding with manual detection of rogue access points. The assignment proceeds to examine access control, focusing on password security, including hashing and salt techniques. Next, it delves into HTTPS and certificates, explaining client certificates, server certificates, and digital signatures. Finally, the assignment addresses internet privacy, detailing web proxies, TOR, and VPNs, including their advantages, disadvantages, and potential security implications, and includes a diagram of addresses learned by malicious users using these techniques.
Advanced Network Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Question 1: Firewall................................................................................................2
Question 2. WiFi Security.......................................................................................4
Question 3. Access Control.....................................................................................7
Question 4. HTTPS and Certificates.....................................................................8
Question 5. Internet Privacy.................................................................................10
References..............................................................................................................16
1
Question 1: Firewall................................................................................................2
Question 2. WiFi Security.......................................................................................4
Question 3. Access Control.....................................................................................7
Question 4. HTTPS and Certificates.....................................................................8
Question 5. Internet Privacy.................................................................................10
References..............................................................................................................16
1
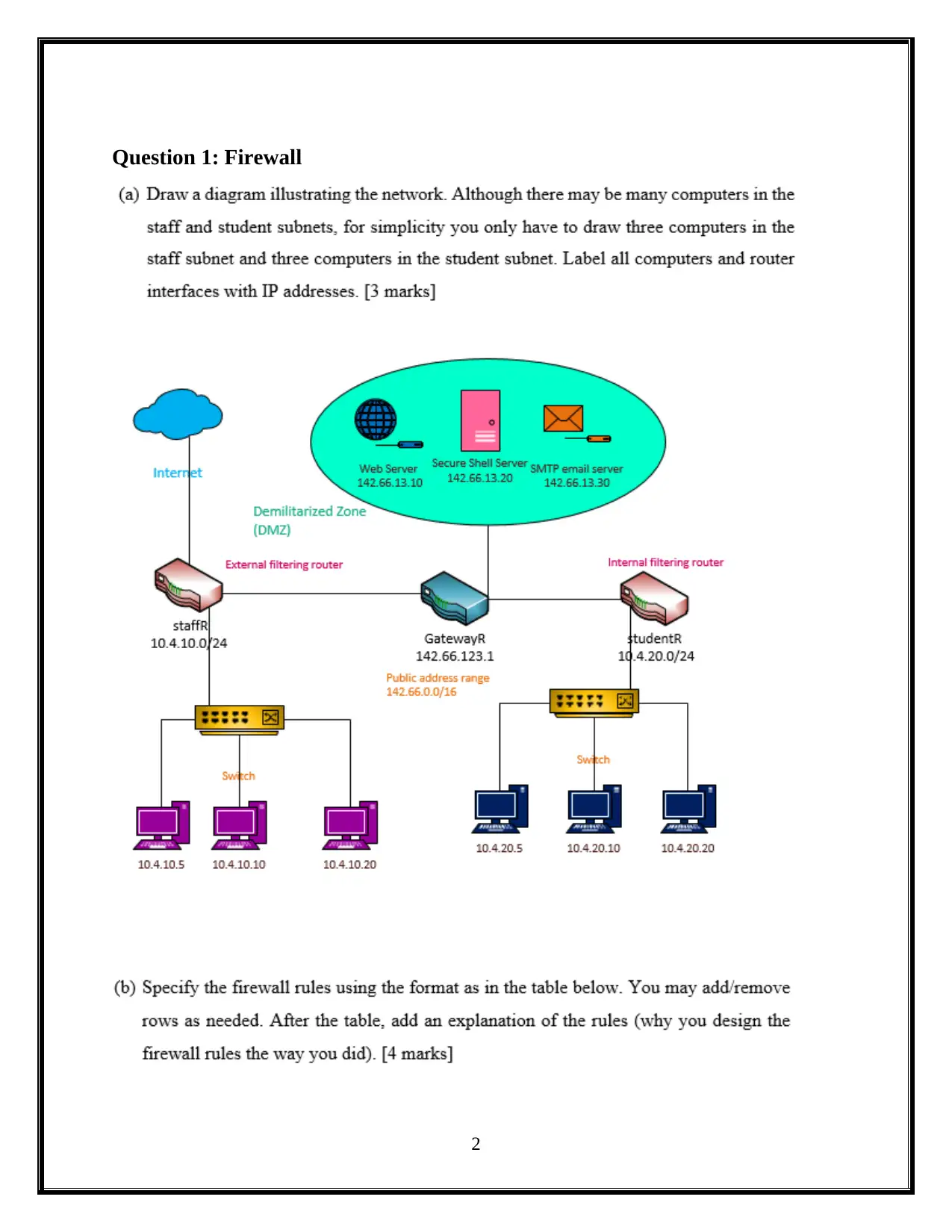
Question 1: Firewall
2
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IP Tables - firewall software
IP Tables are the modules that are mainly used to interrelate the command outlines in
order to refer as well as fix the firewall rubrics in the form of table (Mankell and Segerberg,
2012) Mills, D. (n.d.). Firewall..
Default Policies
IP Tables contains the pre-defined chains. It is also named as the Default Policies. There
are 3 default policies. These Default Policies are tested against with the IP packets and a decision
is prepared to agree or deny the overall process.
3
IP Tables are the modules that are mainly used to interrelate the command outlines in
order to refer as well as fix the firewall rubrics in the form of table (Mankell and Segerberg,
2012) Mills, D. (n.d.). Firewall..
Default Policies
IP Tables contains the pre-defined chains. It is also named as the Default Policies. There
are 3 default policies. These Default Policies are tested against with the IP packets and a decision
is prepared to agree or deny the overall process.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Two common Default Policies
i. INPUT
ii. OUTPUT
INPUT
In the INPUT default policy, all the IP packets are intended to have their endpoint to the
host system.
OUTPUT
In the INPUT default policy, all the IP packets are intended to have their source from the
host system. The one more main default policy is FORWARD default policy.
Tradeoffs among the policies
Trade off or balance measure among the default policies is accepted out using the
FORWARD default policy and the IP packets namely ACCEPT AND DROP.
Question 2. WiFi Security
Answer
(a)Wi-Fi Protected Access (WPA)
Wi-Fi Protected Access is one of the security standard for the users of computing devices
equipped with the help of Wi-Fi. It is very stronger encryption algorithm which is produced by
the networking industry to modify the problems that is associated with the WEP (Laurent-
Maknavicius and Chaouchi, 2008). It enhanced upon and exchanged the unique Wi-Fi safety
standard, Wired Equivalent Privacy (WEP). The devices are linked to a WPA encrypted wireless
network, which can uses the rent keys that are dynamically altered for the communication
purpose.
4
i. INPUT
ii. OUTPUT
INPUT
In the INPUT default policy, all the IP packets are intended to have their endpoint to the
host system.
OUTPUT
In the INPUT default policy, all the IP packets are intended to have their source from the
host system. The one more main default policy is FORWARD default policy.
Tradeoffs among the policies
Trade off or balance measure among the default policies is accepted out using the
FORWARD default policy and the IP packets namely ACCEPT AND DROP.
Question 2. WiFi Security
Answer
(a)Wi-Fi Protected Access (WPA)
Wi-Fi Protected Access is one of the security standard for the users of computing devices
equipped with the help of Wi-Fi. It is very stronger encryption algorithm which is produced by
the networking industry to modify the problems that is associated with the WEP (Laurent-
Maknavicius and Chaouchi, 2008). It enhanced upon and exchanged the unique Wi-Fi safety
standard, Wired Equivalent Privacy (WEP). The devices are linked to a WPA encrypted wireless
network, which can uses the rent keys that are dynamically altered for the communication
purpose.
4

If any request rises to alter the global key, WPA will spontaneously promote the new
security key to each and every devices on the same network without taking to manually variation
them (Aissi, Dabbous and Prasad, 2006).
Disadvantages
i. Incompatibility with the legacy hardware
ii. Increase the data packet size which leads to the longer transmission (Milliken, Selis and
Marshall, 2013).
Radio cell size is generally controlled by the transmitted power level of the wireless
device and controls interference among the radio cells. The extreme transmit power is restricted
according to regulatory region. An improper mixture of transmit power level and the antenna
increase the result in corresponding isotropic emitted power that surpasses the amount permitted
per regulatory domain.
The AP can uses the Omni directional and di-pole antenna for the communication
purpose. By altering the transmit power, the access point of the radio range is altered. The radio
range of the WI-FI is rely on the antenna power gain. To control the radio range, only one
antenna should be used in the network (Wright, 2000).
(c)RADIUS Authentication
The RADIUS (Remote Authentication Dial In User Service) protocol was initially well-
defined to allow the centralized authentication, access control and authorization for point to point
process (PPP) and SLIP dial up sessions like these prepared to dial up internet service provider
(ISP). In its place of need every NAS (network access server) to develop a list of authorized
login id and passwords. The Remote Authentication Dial In User Service access the request are
passed to AAA server and authentication server. Once the user will connects, then the network
access server transmits the RADIUS access request message to authentication, authorization and
accounting server (AAA server), relaying information such as login id and passwords, type of
port, identity of NAS and message authenticator. All of these Remote Authentication Dial In
User Service messages are passed by User Datagram Protocol which provides a sequence
number, message type, Authenticator, length, and sequence of Attribute-Value sets. When the
user need to connect to Wi-Fi network with RADIUS certification, devices establishes the
5
security key to each and every devices on the same network without taking to manually variation
them (Aissi, Dabbous and Prasad, 2006).
Disadvantages
i. Incompatibility with the legacy hardware
ii. Increase the data packet size which leads to the longer transmission (Milliken, Selis and
Marshall, 2013).
Radio cell size is generally controlled by the transmitted power level of the wireless
device and controls interference among the radio cells. The extreme transmit power is restricted
according to regulatory region. An improper mixture of transmit power level and the antenna
increase the result in corresponding isotropic emitted power that surpasses the amount permitted
per regulatory domain.
The AP can uses the Omni directional and di-pole antenna for the communication
purpose. By altering the transmit power, the access point of the radio range is altered. The radio
range of the WI-FI is rely on the antenna power gain. To control the radio range, only one
antenna should be used in the network (Wright, 2000).
(c)RADIUS Authentication
The RADIUS (Remote Authentication Dial In User Service) protocol was initially well-
defined to allow the centralized authentication, access control and authorization for point to point
process (PPP) and SLIP dial up sessions like these prepared to dial up internet service provider
(ISP). In its place of need every NAS (network access server) to develop a list of authorized
login id and passwords. The Remote Authentication Dial In User Service access the request are
passed to AAA server and authentication server. Once the user will connects, then the network
access server transmits the RADIUS access request message to authentication, authorization and
accounting server (AAA server), relaying information such as login id and passwords, type of
port, identity of NAS and message authenticator. All of these Remote Authentication Dial In
User Service messages are passed by User Datagram Protocol which provides a sequence
number, message type, Authenticator, length, and sequence of Attribute-Value sets. When the
user need to connect to Wi-Fi network with RADIUS certification, devices establishes the
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

communication with access points and request the access to network. The access point carried
out the request to RADIUS server that returns a recommendation request back to user through
the access points.
Advantages
1. A wide range of implementation choices
The RADIUS will be implemented as a dedicated on premise server, with help of purchased
RADIUS server software or open source such as free RADIUS. Many network devices and
server operating systems have RADIUS built in, so that does not require the additional software
and hardware id needed.
2. individualized authentication
Each and every user is assigned different credential for accessing the Wi-Fi network.
3. synchronization with active directory
The device could not set up so the user network directory passwords are needs to authenticate on
Wi-Fi network, enabling one sign on for users.
Disadvantage
It uses User Data Protocol for information sharing among the NAS and the
authentication server only the password is encoded and all the information are directed in a text
format that is vulnerable to eavesdropping attacks.
(d)Manual detection of rouge APs
A rouge access point (AP) is an unauthorized access points which is plugged underwired
side of network. The Aruba operating system provides the rouge access point’s detection
functionality accessible in base OS. Formerly the Aruba operating system could categorize the
access points as a rouge and constantly provide it, the operating system should detect the access
points, detect any base station that related to it, and detect the wired system with that challenges
to interconnect.
Advantages
1. The benefits are lower time-to-detection. When the monitor mode Access Points s are
additionally configured with Adaptive Internet Service Provider, a wide range of over-
the-air dangers and attacks will be detected.
2. Many data attackers have taken advantage of unobserved rogue access points in
initiatives to not only get free Internet access, but also to view the private information.
6
out the request to RADIUS server that returns a recommendation request back to user through
the access points.
Advantages
1. A wide range of implementation choices
The RADIUS will be implemented as a dedicated on premise server, with help of purchased
RADIUS server software or open source such as free RADIUS. Many network devices and
server operating systems have RADIUS built in, so that does not require the additional software
and hardware id needed.
2. individualized authentication
Each and every user is assigned different credential for accessing the Wi-Fi network.
3. synchronization with active directory
The device could not set up so the user network directory passwords are needs to authenticate on
Wi-Fi network, enabling one sign on for users.
Disadvantage
It uses User Data Protocol for information sharing among the NAS and the
authentication server only the password is encoded and all the information are directed in a text
format that is vulnerable to eavesdropping attacks.
(d)Manual detection of rouge APs
A rouge access point (AP) is an unauthorized access points which is plugged underwired
side of network. The Aruba operating system provides the rouge access point’s detection
functionality accessible in base OS. Formerly the Aruba operating system could categorize the
access points as a rouge and constantly provide it, the operating system should detect the access
points, detect any base station that related to it, and detect the wired system with that challenges
to interconnect.
Advantages
1. The benefits are lower time-to-detection. When the monitor mode Access Points s are
additionally configured with Adaptive Internet Service Provider, a wide range of over-
the-air dangers and attacks will be detected.
2. Many data attackers have taken advantage of unobserved rogue access points in
initiatives to not only get free Internet access, but also to view the private information.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Disadvantage
Radio Frequency scanning needs more time and it is boring, that detect the rogue Access
Point only, when scanning is processed. RF scanning technique is also do influence on the
costing and also it is not so accurate and effective.
Question 3. Access Control
The password and user name information is stored at the database in the organization website. It
is stored in the encrypted form,that is hash format with salt. Because the hacker uses the random
table to find out the password in the database even the password is in the form of hash values.
The passwords is divided into two types. That is administratively assigned and another
one is not administratively assigned. In case of the secure passwords that are not administratively
assigned, the system fails to identify that 2 user have used the same passwords. The passwords
are kept in Hash table with in the file or a database. The password length, combination of special
characters, use of capital and small letter can makes the passwords difficult and the hash value of
the difficult passwords. And these passwords are hard to track (Zhang et al., 2004). This is the
7
Radio Frequency scanning needs more time and it is boring, that detect the rogue Access
Point only, when scanning is processed. RF scanning technique is also do influence on the
costing and also it is not so accurate and effective.
Question 3. Access Control
The password and user name information is stored at the database in the organization website. It
is stored in the encrypted form,that is hash format with salt. Because the hacker uses the random
table to find out the password in the database even the password is in the form of hash values.
The passwords is divided into two types. That is administratively assigned and another
one is not administratively assigned. In case of the secure passwords that are not administratively
assigned, the system fails to identify that 2 user have used the same passwords. The passwords
are kept in Hash table with in the file or a database. The password length, combination of special
characters, use of capital and small letter can makes the passwords difficult and the hash value of
the difficult passwords. And these passwords are hard to track (Zhang et al., 2004). This is the
7

important reason why even after a cruel attack, the hacker was not able to hack the strong
passwords.
The password is stored in the hash of a salted form. The long random salt is combined with the
users password, after the combined process the hash value is calculated for the combined
password and salt. This value is stored in the website database.so it made difficult for the
malicious user.
Question 4. HTTPS and Certificates
Each client have their own certificate, it is called as client certificate. For the purpose of
authenticating so that the client for using the server certificate, client certificate is sent to the
server (Instantssl.com, 2017). HTTP protocol provides a link that could connect the server and
the client. Digital server certificate is essential to create a HTTP (Blackstone and Lewis, 2007).
The server certificate id verification is made by the codes assistance, these codes are
called as response codes. 1XX, 2XX, 3XX, 4XX AND 5XX are some of the response code that
is provide by the server certificate. These codes has a number of sub codes in it, each sub code is
responsible for different type of responses.
8
passwords.
The password is stored in the hash of a salted form. The long random salt is combined with the
users password, after the combined process the hash value is calculated for the combined
password and salt. This value is stored in the website database.so it made difficult for the
malicious user.
Question 4. HTTPS and Certificates
Each client have their own certificate, it is called as client certificate. For the purpose of
authenticating so that the client for using the server certificate, client certificate is sent to the
server (Instantssl.com, 2017). HTTP protocol provides a link that could connect the server and
the client. Digital server certificate is essential to create a HTTP (Blackstone and Lewis, 2007).
The server certificate id verification is made by the codes assistance, these codes are
called as response codes. 1XX, 2XX, 3XX, 4XX AND 5XX are some of the response code that
is provide by the server certificate. These codes has a number of sub codes in it, each sub code is
responsible for different type of responses.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
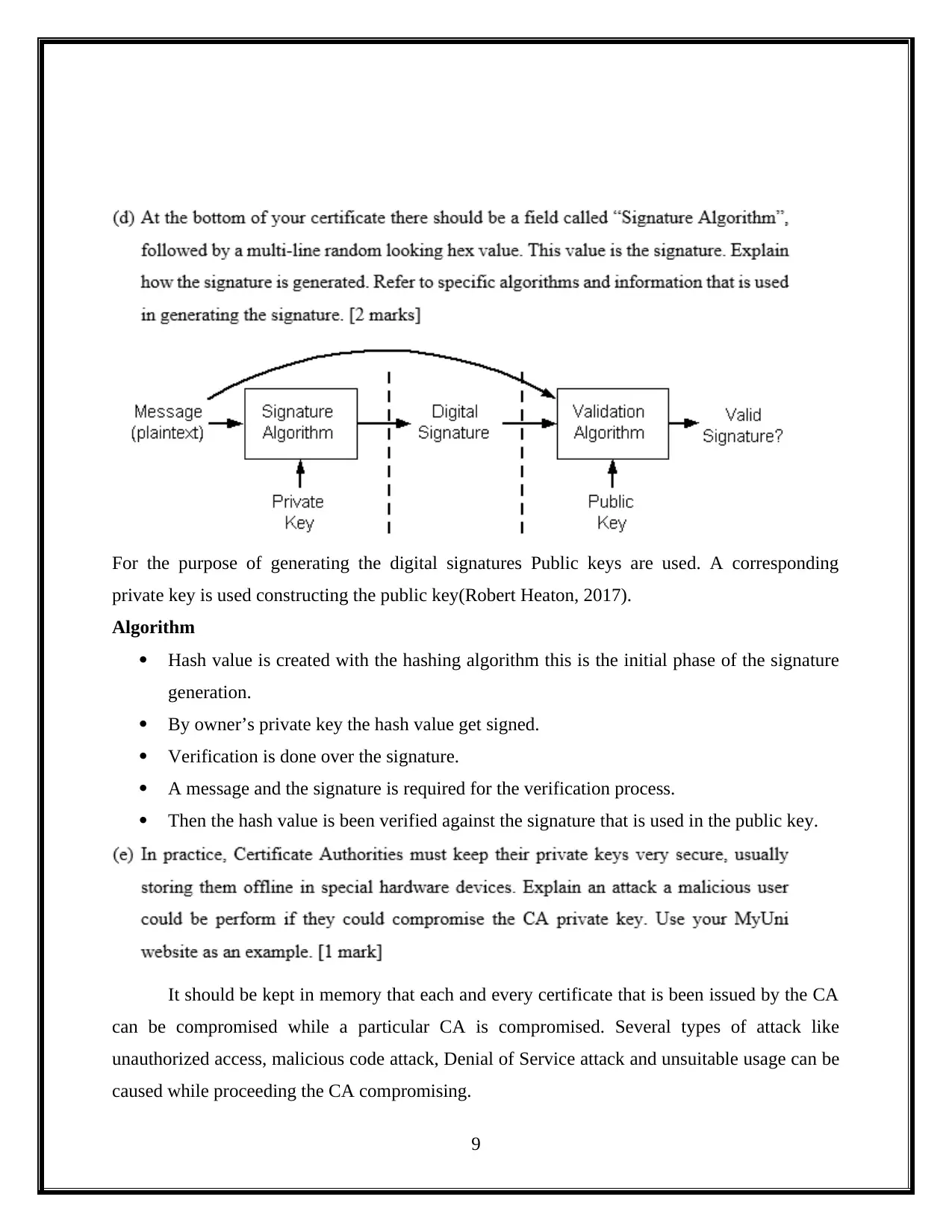
For the purpose of generating the digital signatures Public keys are used. A corresponding
private key is used constructing the public key(Robert Heaton, 2017).
Algorithm
Hash value is created with the hashing algorithm this is the initial phase of the signature
generation.
By owner’s private key the hash value get signed.
Verification is done over the signature.
A message and the signature is required for the verification process.
Then the hash value is been verified against the signature that is used in the public key.
It should be kept in memory that each and every certificate that is been issued by the CA
can be compromised while a particular CA is compromised. Several types of attack like
unauthorized access, malicious code attack, Denial of Service attack and unsuitable usage can be
caused while proceeding the CA compromising.
9
private key is used constructing the public key(Robert Heaton, 2017).
Algorithm
Hash value is created with the hashing algorithm this is the initial phase of the signature
generation.
By owner’s private key the hash value get signed.
Verification is done over the signature.
A message and the signature is required for the verification process.
Then the hash value is been verified against the signature that is used in the public key.
It should be kept in memory that each and every certificate that is been issued by the CA
can be compromised while a particular CA is compromised. Several types of attack like
unauthorized access, malicious code attack, Denial of Service attack and unsuitable usage can be
caused while proceeding the CA compromising.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Question 5. Internet Privacy
1. An explanation of the technique
Web proxy
Web proxies are used to change the IP addresses during the process of browsing. By
using this, one could change the IP addresses in quick and easy way (Levmore and Nussbaum,
2012). It is portable one. Because it doesn’t need any additional software installation and
computer network setting modification. It provides the web pages. It serves as a search engine. It
provides SSL security for Web (Harvard Gazette, 2017). It is used for encrypting process. It
encrypts the communication between the proxy and user. It is common to the some type proxy
such as advertisement removal, user agent masking and cookie management. Its cache could be
used for all users.
TOR
TOR stands for The Onion Router. It is an administration. It is provided for using the
internet with security. With the help of TOR, IP addresses is removed the locals. It provide the
access for clients to interface the system by enabling the immediate association (Kasser, 2000).
10
1. An explanation of the technique
Web proxy
Web proxies are used to change the IP addresses during the process of browsing. By
using this, one could change the IP addresses in quick and easy way (Levmore and Nussbaum,
2012). It is portable one. Because it doesn’t need any additional software installation and
computer network setting modification. It provides the web pages. It serves as a search engine. It
provides SSL security for Web (Harvard Gazette, 2017). It is used for encrypting process. It
encrypts the communication between the proxy and user. It is common to the some type proxy
such as advertisement removal, user agent masking and cookie management. Its cache could be
used for all users.
TOR
TOR stands for The Onion Router. It is an administration. It is provided for using the
internet with security. With the help of TOR, IP addresses is removed the locals. It provide the
access for clients to interface the system by enabling the immediate association (Kasser, 2000).
10

VPN
The abbreviation of VPN is Virtual Private Network. It has the encryption tool. By using
the encryption tool, the internet users protect their information or data. The content restrictions
problem is removed by the VPN. In the VPN, the user has ability to enable the sports streams,
chat on forums and download the music. The blocked data or information in the web could be
accessed by the internet user with the help of VPN. The users access the internet from the VPN
server, because the VPN connections are provided to the VPN server. The VPN connections are
also used at mobile, laptops and desktop. Several types of VPN are there. The VPN is separated
based on the protocol, security and scope. Types of VPN Protocols PPTP, SSTP, OPEN VPN,
IKENv2 and L2TP/IPsec. To avoid the content blocks during the browsing, the IP addresses are
changed. The VPN is used to change the IP address. It is also helpful to reduce IP bans across the
web (Cis-india.org, 2017).
Benefits of VPN
1. It provides secure connection
2. Private access is provided by the VPN
3. It has high speed bandwidth.
4. It has the ability to choose location according to the need of user.
5. It has perfect Usability.
11
The abbreviation of VPN is Virtual Private Network. It has the encryption tool. By using
the encryption tool, the internet users protect their information or data. The content restrictions
problem is removed by the VPN. In the VPN, the user has ability to enable the sports streams,
chat on forums and download the music. The blocked data or information in the web could be
accessed by the internet user with the help of VPN. The users access the internet from the VPN
server, because the VPN connections are provided to the VPN server. The VPN connections are
also used at mobile, laptops and desktop. Several types of VPN are there. The VPN is separated
based on the protocol, security and scope. Types of VPN Protocols PPTP, SSTP, OPEN VPN,
IKENv2 and L2TP/IPsec. To avoid the content blocks during the browsing, the IP addresses are
changed. The VPN is used to change the IP address. It is also helpful to reduce IP bans across the
web (Cis-india.org, 2017).
Benefits of VPN
1. It provides secure connection
2. Private access is provided by the VPN
3. It has high speed bandwidth.
4. It has the ability to choose location according to the need of user.
5. It has perfect Usability.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





