Advanced Networks: UKF Trading Company Network Design Report
VerifiedAdded on 2021/06/17
|19
|3431
|43
Report
AI Summary
This report details the advanced network design proposed for UKF Trading Company, a financial organization expanding its operations. The report begins with an overview of the business requirements, including performance, availability, flexibility, and manageability goals. It then presents a logical design, including a network diagram and IP addressing scheme. The core of the report focuses on the Layer 3 architecture, breaking down the network into core, access, and distribution layers. It further details the protocols and devices used, including Ethernet, PPP, IP, EIGRP, TCP, OSPF, switches, routers, network cables, and firewalls. The report emphasizes security measures, such as intrusion prevention and detection systems, port security, access control lists, and protocol filtering. The objective is to provide a flexible, manageable, and secure network infrastructure to support the company's growth.

Running head: ADVANCED NETWORKS
Advanced Networks
Name of the Student
Name of the University
Author’s Note
Advanced Networks
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
ADVANCED NETWORKS
Table of Contents
Part 1 – Design...........................................................................................................................2
1. Discussing the network model and the business requirement............................................2
1.1. Background of the organization..................................................................................2
1.2. Goals and Objectives of the Project............................................................................2
2. Logical Design...................................................................................................................3
3. Associated Design Documents...........................................................................................5
Part 2 – Report...........................................................................................................................7
Introduction............................................................................................................................7
Layer 3 architecture................................................................................................................7
Protocols and Devices..........................................................................................................10
Protocols...........................................................................................................................10
Network Hardware Devices.............................................................................................11
Backup Solution...................................................................................................................13
Intrusion Prevention System................................................................................................13
Intrusion detection system....................................................................................................13
Port Security.........................................................................................................................14
Access control List...............................................................................................................14
Protocol Filtering.................................................................................................................14
Conclusion............................................................................................................................15
Bibliography.............................................................................................................................16
ADVANCED NETWORKS
Table of Contents
Part 1 – Design...........................................................................................................................2
1. Discussing the network model and the business requirement............................................2
1.1. Background of the organization..................................................................................2
1.2. Goals and Objectives of the Project............................................................................2
2. Logical Design...................................................................................................................3
3. Associated Design Documents...........................................................................................5
Part 2 – Report...........................................................................................................................7
Introduction............................................................................................................................7
Layer 3 architecture................................................................................................................7
Protocols and Devices..........................................................................................................10
Protocols...........................................................................................................................10
Network Hardware Devices.............................................................................................11
Backup Solution...................................................................................................................13
Intrusion Prevention System................................................................................................13
Intrusion detection system....................................................................................................13
Port Security.........................................................................................................................14
Access control List...............................................................................................................14
Protocol Filtering.................................................................................................................14
Conclusion............................................................................................................................15
Bibliography.............................................................................................................................16

2
ADVANCED NETWORKS
Part 1 – Design
1. Discussing the network model and the business requirement
1.1. Background of the organization
UKF Trading Company is a financial organization with its base in Birmingham,
Manchester and Edinburgh. There are different business organization that gets their service
from UKF Trading and the company have the requirement to expand their current network in
order to serve the growing needs of their customers. For the expansion of the organization the
company needs to relocate the headquarter to a large space and design a network to connect
all the workspace of the new building. Thus a new network design is needed according to the
layout of the building and a network design is proposed for the organization for meeting the
tender invitation.
1.2. Goals and Objectives of the Project
Performance – The UKF Trading Company network should be developed for the
measurement of the service quality and the performance of the network is measured
depending on the bandwidth, throughput, latency, error rate and jitter in the network. The
network downtime should be minimum and it should be available to the user all the time.
Backup of the network should be created for the reducing the recovery time and increasing
the performance of the network.
Availability – The network device should be connected with each other using
redundant link such that if one of the link fails the data packets can reach the destination
address using the mirror link. It also eliminates the congestion in the network and reduces the
rate of error and latency. The use of separate channel for the different departments increases
ADVANCED NETWORKS
Part 1 – Design
1. Discussing the network model and the business requirement
1.1. Background of the organization
UKF Trading Company is a financial organization with its base in Birmingham,
Manchester and Edinburgh. There are different business organization that gets their service
from UKF Trading and the company have the requirement to expand their current network in
order to serve the growing needs of their customers. For the expansion of the organization the
company needs to relocate the headquarter to a large space and design a network to connect
all the workspace of the new building. Thus a new network design is needed according to the
layout of the building and a network design is proposed for the organization for meeting the
tender invitation.
1.2. Goals and Objectives of the Project
Performance – The UKF Trading Company network should be developed for the
measurement of the service quality and the performance of the network is measured
depending on the bandwidth, throughput, latency, error rate and jitter in the network. The
network downtime should be minimum and it should be available to the user all the time.
Backup of the network should be created for the reducing the recovery time and increasing
the performance of the network.
Availability – The network device should be connected with each other using
redundant link such that if one of the link fails the data packets can reach the destination
address using the mirror link. It also eliminates the congestion in the network and reduces the
rate of error and latency. The use of separate channel for the different departments increases
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
ADVANCED NETWORKS
the availability of the network resources and the servers should be configured with
virtualization for balancing the loads and serve the needs of the clients.
Flexibility – Different options should be available to the user for the expansion of the
network and reduce the failure point for the development of the network framework. The
network should be tested for analysis in the errors in the configuration and the business
policy should be evaluated for the configuration of the network device. The network should
be flexible such that it can be expanded according to the growth of the organization and there
should be no performance issues for maintaining high latency.
Manageability – The network administrator is responsible for the management of the
network performance and the problems in the network should be identified for mitigation of
the risk associated with the development of the network. The throughput of the network
should be optimized for allowing the user to get the best output from the network. Different
Vlans are used for the management of the departments and divide the communication channel
for transferring of data packets. The VLAN management is important for the management of
the data traffic and enabling control on the flow of traffic in the network.
2. Logical Design
The logical diagram of the network is prepared for the AMY networks including all
the details such as the list of the network device and the IP address used for the configuration
of the interface of the device. The UKF trading servers are located in different geographical
location such as Manchester, Edinburgh and Birmingham and it is serves the needs of the
regional offices.
ADVANCED NETWORKS
the availability of the network resources and the servers should be configured with
virtualization for balancing the loads and serve the needs of the clients.
Flexibility – Different options should be available to the user for the expansion of the
network and reduce the failure point for the development of the network framework. The
network should be tested for analysis in the errors in the configuration and the business
policy should be evaluated for the configuration of the network device. The network should
be flexible such that it can be expanded according to the growth of the organization and there
should be no performance issues for maintaining high latency.
Manageability – The network administrator is responsible for the management of the
network performance and the problems in the network should be identified for mitigation of
the risk associated with the development of the network. The throughput of the network
should be optimized for allowing the user to get the best output from the network. Different
Vlans are used for the management of the departments and divide the communication channel
for transferring of data packets. The VLAN management is important for the management of
the data traffic and enabling control on the flow of traffic in the network.
2. Logical Design
The logical diagram of the network is prepared for the AMY networks including all
the details such as the list of the network device and the IP address used for the configuration
of the interface of the device. The UKF trading servers are located in different geographical
location such as Manchester, Edinburgh and Birmingham and it is serves the needs of the
regional offices.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
ADVANCED NETWORKS
Figure 1: logical Diagram of then UKF Network
(Source: Created by author)
There is an expected growth in the current business and the current network
framework does not meets the expansion of the network. Thus the current network needs to
be modified and should be aligned with the current needs of the organization according to the
building floor plan and design the network according to the layout of the building. An
invitation of the tender is proposed by the UKF trading company for the creation of the
design of the network. The goals and objectives of the project should be analysed for the
development of the network. The network should be designed for making it flexible and
increasing the manageability of the network.
ADVANCED NETWORKS
Figure 1: logical Diagram of then UKF Network
(Source: Created by author)
There is an expected growth in the current business and the current network
framework does not meets the expansion of the network. Thus the current network needs to
be modified and should be aligned with the current needs of the organization according to the
building floor plan and design the network according to the layout of the building. An
invitation of the tender is proposed by the UKF trading company for the creation of the
design of the network. The goals and objectives of the project should be analysed for the
development of the network. The network should be designed for making it flexible and
increasing the manageability of the network.
5
ADVANCED NETWORKS
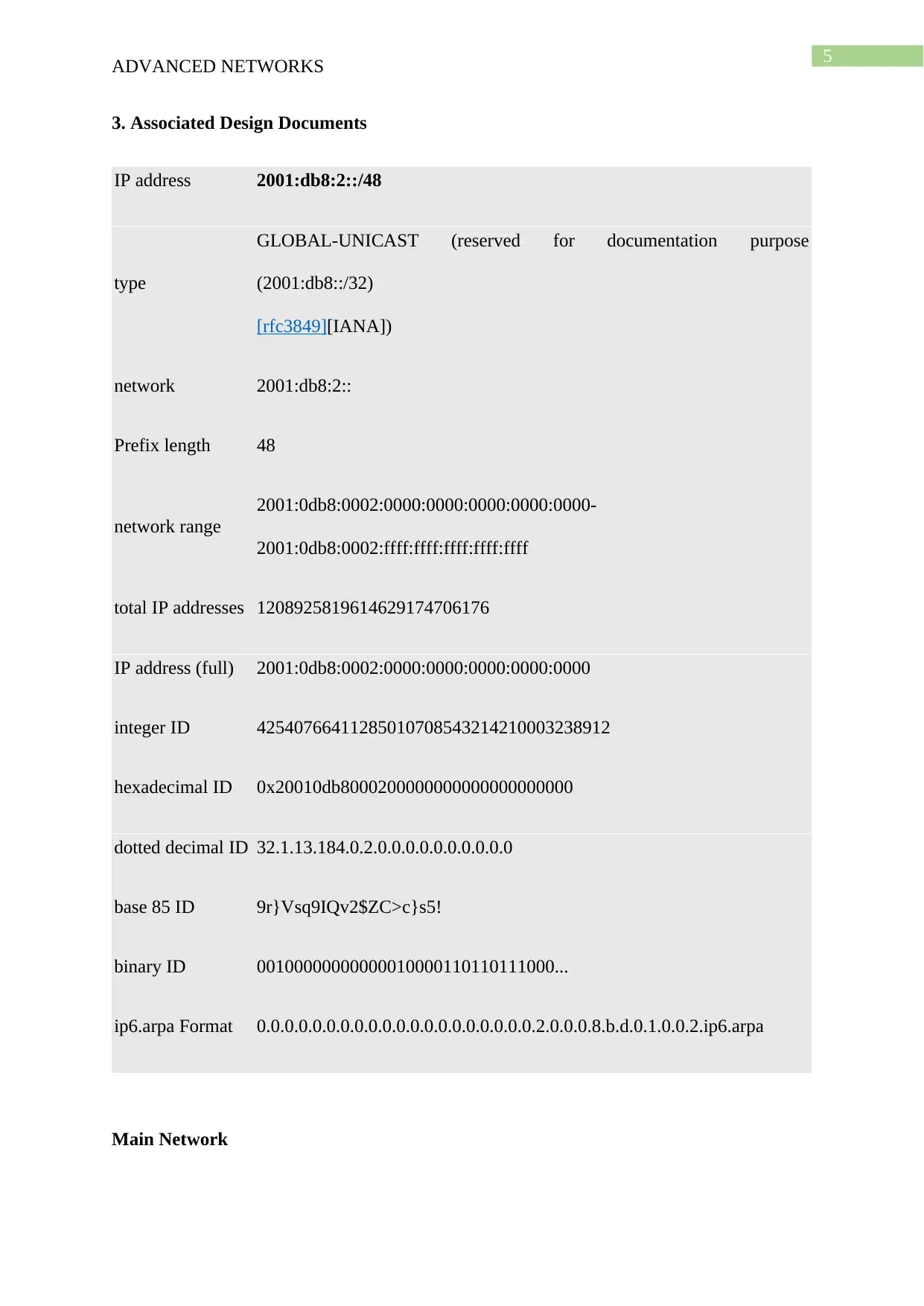
3. Associated Design Documents
IP address 2001:db8:2::/48
type
GLOBAL-UNICAST (reserved for documentation purpose
(2001:db8::/32)
[rfc3849][IANA])
network 2001:db8:2::
Prefix length 48
network range
2001:0db8:0002:0000:0000:0000:0000:0000-
2001:0db8:0002:ffff:ffff:ffff:ffff:ffff
total IP addresses 1208925819614629174706176
IP address (full) 2001:0db8:0002:0000:0000:0000:0000:0000
integer ID 42540766411285010708543214210003238912
hexadecimal ID 0x20010db8000200000000000000000000
dotted decimal ID 32.1.13.184.0.2.0.0.0.0.0.0.0.0.0.0
base 85 ID 9r}Vsq9IQv2$ZC>c}s5!
binary ID 00100000000000010000110110111000...
ip6.arpa Format 0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.0.0.8.b.d.0.1.0.0.2.ip6.arpa
Main Network
ADVANCED NETWORKS
3. Associated Design Documents
IP address 2001:db8:2::/48
type
GLOBAL-UNICAST (reserved for documentation purpose
(2001:db8::/32)
[rfc3849][IANA])
network 2001:db8:2::
Prefix length 48
network range
2001:0db8:0002:0000:0000:0000:0000:0000-
2001:0db8:0002:ffff:ffff:ffff:ffff:ffff
total IP addresses 1208925819614629174706176
IP address (full) 2001:0db8:0002:0000:0000:0000:0000:0000
integer ID 42540766411285010708543214210003238912
hexadecimal ID 0x20010db8000200000000000000000000
dotted decimal ID 32.1.13.184.0.2.0.0.0.0.0.0.0.0.0.0
base 85 ID 9r}Vsq9IQv2$ZC>c}s5!
binary ID 00100000000000010000110110111000...
ip6.arpa Format 0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.0.0.8.b.d.0.1.0.0.2.ip6.arpa
Main Network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
ADVANCED NETWORKS
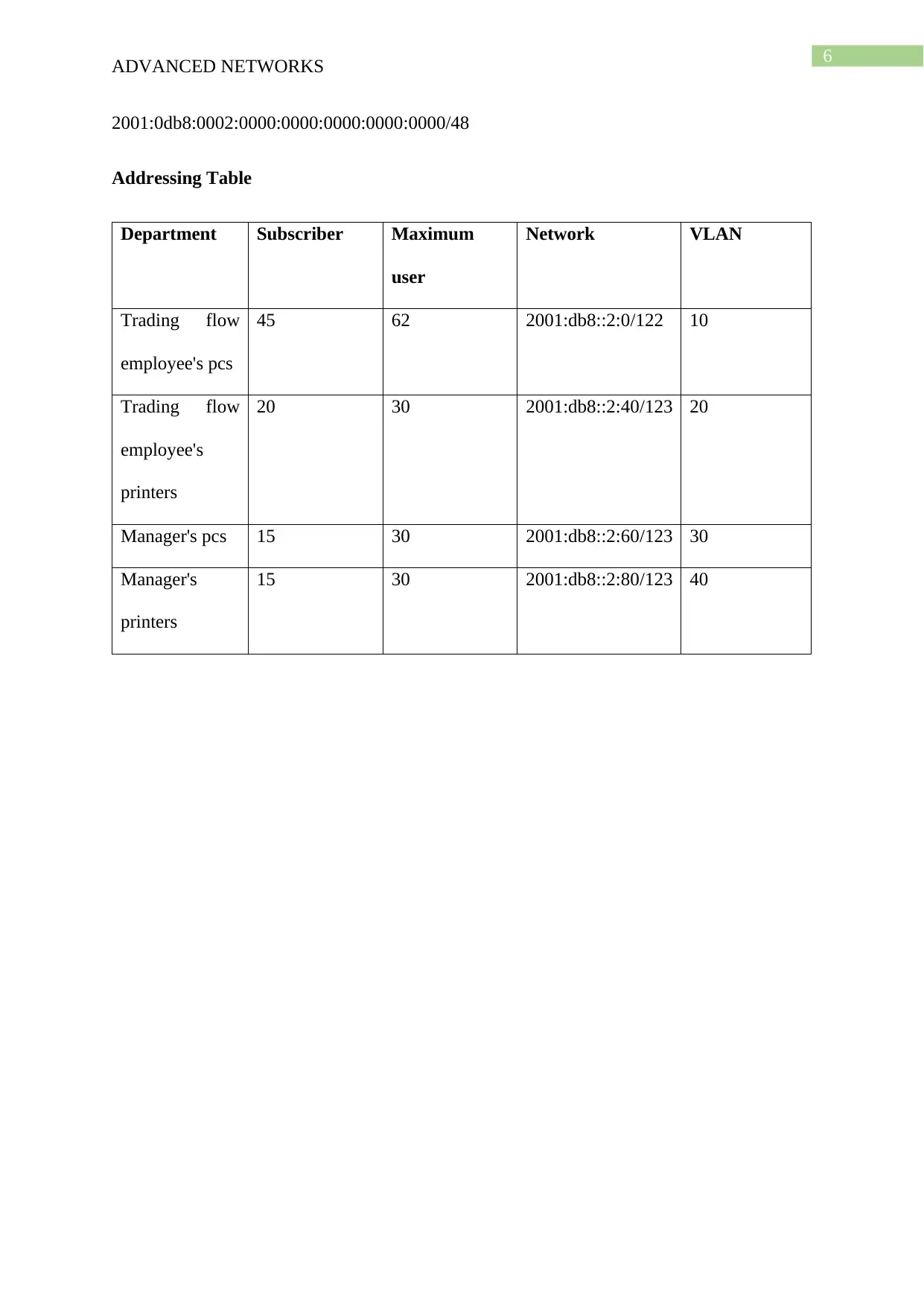
2001:0db8:0002:0000:0000:0000:0000:0000/48
Addressing Table
Department Subscriber Maximum
user
Network VLAN
Trading flow
employee's pcs
45 62 2001:db8::2:0/122 10
Trading flow
employee's
printers
20 30 2001:db8::2:40/123 20
Manager's pcs 15 30 2001:db8::2:60/123 30
Manager's
printers
15 30 2001:db8::2:80/123 40
ADVANCED NETWORKS
2001:0db8:0002:0000:0000:0000:0000:0000/48
Addressing Table
Department Subscriber Maximum
user
Network VLAN
Trading flow
employee's pcs
45 62 2001:db8::2:0/122 10
Trading flow
employee's
printers
20 30 2001:db8::2:40/123 20
Manager's pcs 15 30 2001:db8::2:60/123 30
Manager's
printers
15 30 2001:db8::2:80/123 40
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
ADVANCED NETWORKS
Part 2 – Report
Introduction
The report describes the logical design that is created for designing the framework of
the trading floor. The architecture and the protocols used for the configuration of the network
is analysed and documented for the management of the network. There are different security
measures that are used for the development of the network and prevent the external users to
access the internal components of the network.
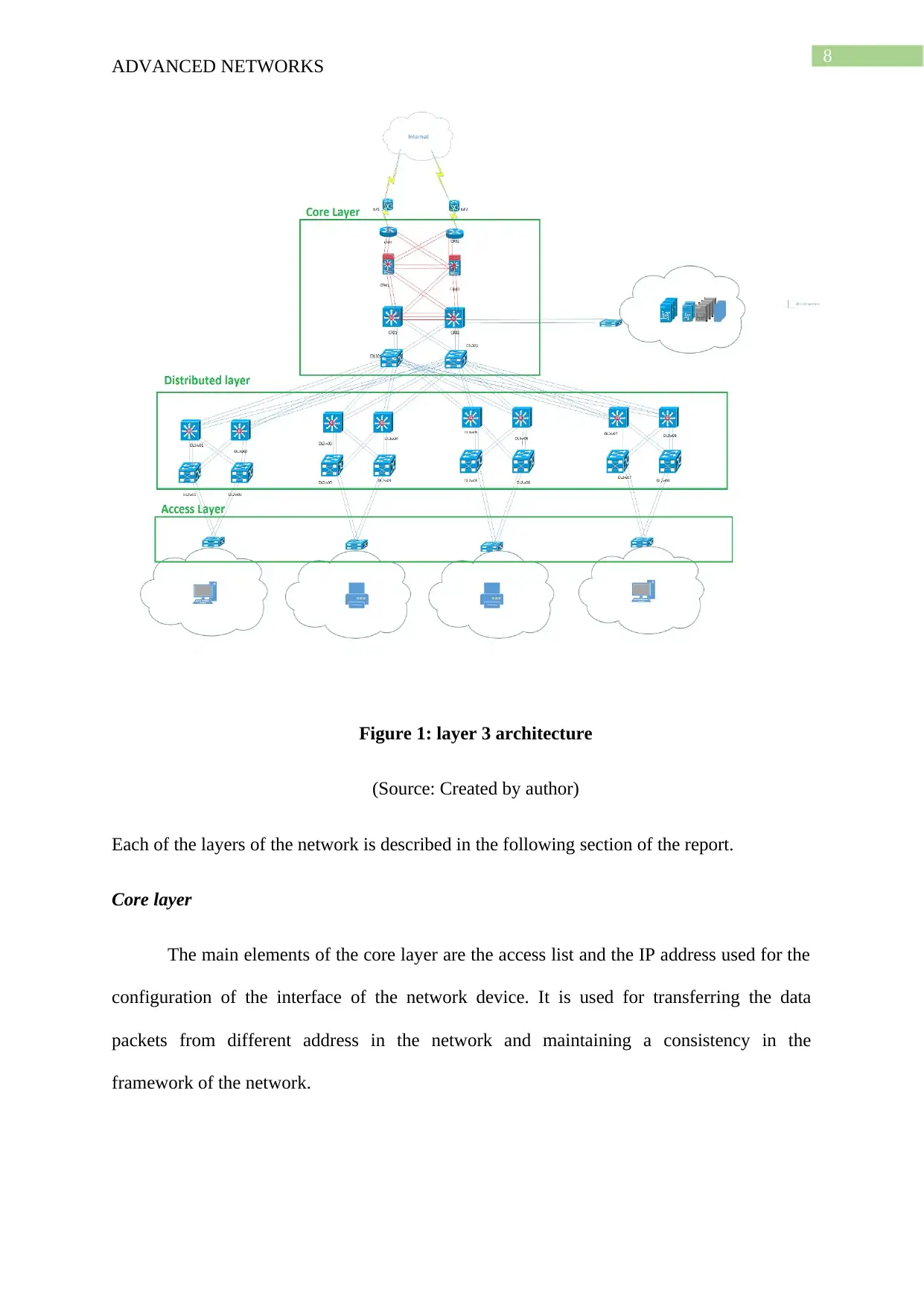
Layer 3 architecture
For the development of the network framework the network is divided into smaller
segments that can be managed for the development of the network. The problems and the
barriers faced for the development of the network should be identified for eliminating the
errors and management of the development of the network framework. The business goals
and the technical needs is analysed and the solution is developed following the cisco SAFE
architecture for dividing the layers into the following such as:
Core
Access and
Distribution layer.
ADVANCED NETWORKS
Part 2 – Report
Introduction
The report describes the logical design that is created for designing the framework of
the trading floor. The architecture and the protocols used for the configuration of the network
is analysed and documented for the management of the network. There are different security
measures that are used for the development of the network and prevent the external users to
access the internal components of the network.
Layer 3 architecture
For the development of the network framework the network is divided into smaller
segments that can be managed for the development of the network. The problems and the
barriers faced for the development of the network should be identified for eliminating the
errors and management of the development of the network framework. The business goals
and the technical needs is analysed and the solution is developed following the cisco SAFE
architecture for dividing the layers into the following such as:
Core
Access and
Distribution layer.
8
ADVANCED NETWORKS
Figure 1: layer 3 architecture
(Source: Created by author)
Each of the layers of the network is described in the following section of the report.
Core layer
The main elements of the core layer are the access list and the IP address used for the
configuration of the interface of the network device. It is used for transferring the data
packets from different address in the network and maintaining a consistency in the
framework of the network.
ADVANCED NETWORKS
Figure 1: layer 3 architecture
(Source: Created by author)
Each of the layers of the network is described in the following section of the report.
Core layer
The main elements of the core layer are the access list and the IP address used for the
configuration of the interface of the network device. It is used for transferring the data
packets from different address in the network and maintaining a consistency in the
framework of the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
ADVANCED NETWORKS
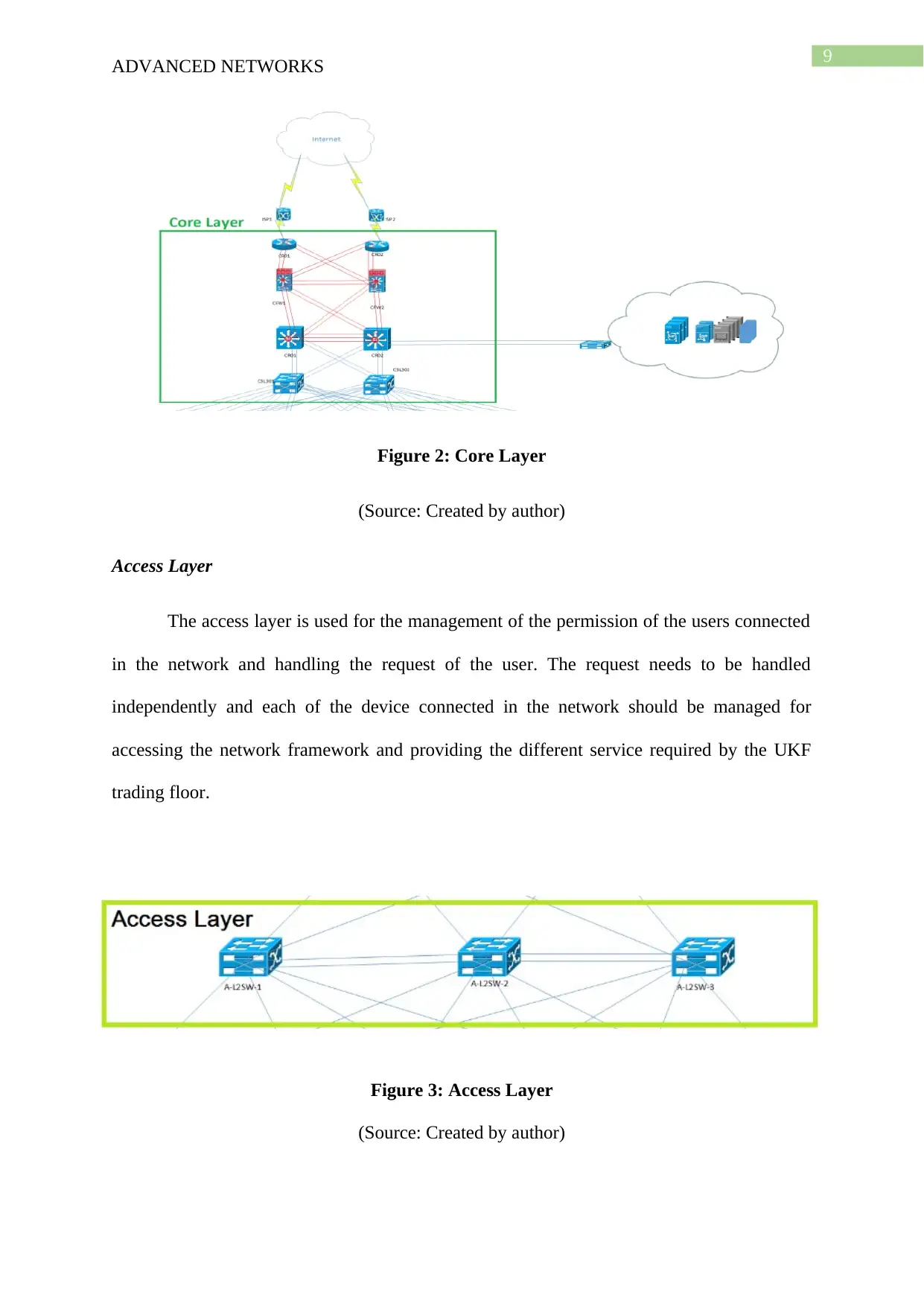
Figure 2: Core Layer
(Source: Created by author)
Access Layer
The access layer is used for the management of the permission of the users connected
in the network and handling the request of the user. The request needs to be handled
independently and each of the device connected in the network should be managed for
accessing the network framework and providing the different service required by the UKF
trading floor.
Figure 3: Access Layer
(Source: Created by author)
ADVANCED NETWORKS
Figure 2: Core Layer
(Source: Created by author)
Access Layer
The access layer is used for the management of the permission of the users connected
in the network and handling the request of the user. The request needs to be handled
independently and each of the device connected in the network should be managed for
accessing the network framework and providing the different service required by the UKF
trading floor.
Figure 3: Access Layer
(Source: Created by author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
ADVANCED NETWORKS
ADVANCED NETWORKS
11
ADVANCED NETWORKS
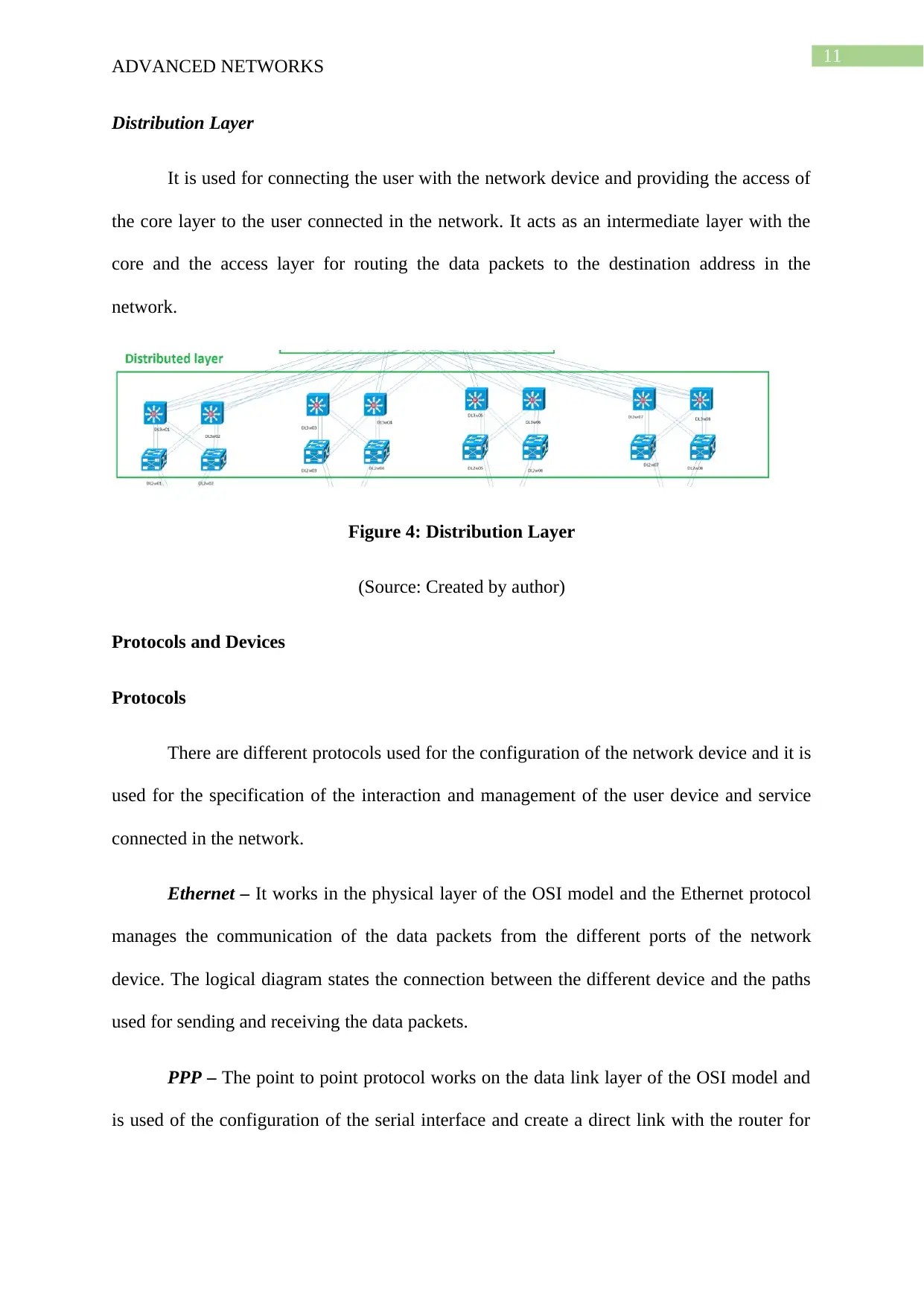
Distribution Layer
It is used for connecting the user with the network device and providing the access of
the core layer to the user connected in the network. It acts as an intermediate layer with the
core and the access layer for routing the data packets to the destination address in the
network.
Figure 4: Distribution Layer
(Source: Created by author)
Protocols and Devices
Protocols
There are different protocols used for the configuration of the network device and it is
used for the specification of the interaction and management of the user device and service
connected in the network.
Ethernet – It works in the physical layer of the OSI model and the Ethernet protocol
manages the communication of the data packets from the different ports of the network
device. The logical diagram states the connection between the different device and the paths
used for sending and receiving the data packets.
PPP – The point to point protocol works on the data link layer of the OSI model and
is used of the configuration of the serial interface and create a direct link with the router for
ADVANCED NETWORKS
Distribution Layer
It is used for connecting the user with the network device and providing the access of
the core layer to the user connected in the network. It acts as an intermediate layer with the
core and the access layer for routing the data packets to the destination address in the
network.
Figure 4: Distribution Layer
(Source: Created by author)
Protocols and Devices
Protocols
There are different protocols used for the configuration of the network device and it is
used for the specification of the interaction and management of the user device and service
connected in the network.
Ethernet – It works in the physical layer of the OSI model and the Ethernet protocol
manages the communication of the data packets from the different ports of the network
device. The logical diagram states the connection between the different device and the paths
used for sending and receiving the data packets.
PPP – The point to point protocol works on the data link layer of the OSI model and
is used of the configuration of the serial interface and create a direct link with the router for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



