Amazon EC2: Comprehensive Analysis of Security, Risks, and Controls
VerifiedAdded on 2022/11/26
|13
|2756
|393
Report
AI Summary
This report provides a comprehensive overview of Amazon Elastic Compute Cloud (EC2), a core service within Amazon Web Services (AWS). The report begins with a summary of Amazon EC2, highlighting its evolution as a pioneer in cloud computing and its advantages, such as elasticity and scalability. It then delves into the assets of EC2, emphasizing its ability to create and manage virtual machine instances efficiently. The report also covers the cryptography used in Amazon EC2, along with an analysis of potential threats and vulnerabilities associated with the service, including privacy concerns, traffic outages, and regulatory compliance issues. Furthermore, the report examines the security objectives, controls, and risk evaluation processes within EC2, including features like elastic IP addresses and CloudWatch. The report concludes by emphasizing EC2's potential for organizations seeking cloud computing solutions and its ability to provide developers with the tools necessary to build resilient and fail-safe applications.

Amazon Elastic Compute Cloud (Amazon EC2)
Student’s name
Institution Affiliation(s)
Student’s name
Institution Affiliation(s)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Summary of Amazon EC2............................................................................................................................2
Assets..........................................................................................................................................................3
Cryptography used in Amazon EC2..........................................................................................................4
Threats........................................................................................................................................................5
Vulnerabilities..............................................................................................................................................6
Security objectives.......................................................................................................................................7
Controls.......................................................................................................................................................8
Risk Evaluation............................................................................................................................................9
Conclusions................................................................................................................................................10
References.................................................................................................................................................11
Summary of Amazon EC2............................................................................................................................2
Assets..........................................................................................................................................................3
Cryptography used in Amazon EC2..........................................................................................................4
Threats........................................................................................................................................................5
Vulnerabilities..............................................................................................................................................6
Security objectives.......................................................................................................................................7
Controls.......................................................................................................................................................8
Risk Evaluation............................................................................................................................................9
Conclusions................................................................................................................................................10
References.................................................................................................................................................11

Summary of Amazon EC2
In 2002, Amazon initiated cloud computing in Beta form through Amazon Web Services
(AWS). Being the first player in this field, Amazon is proud to be called or considered a pioneer
in cloud computing. When the management at Amazon found that they had an extensive
Information System infrastructure for their purposes, they introduced the commercial process of
sharing its IS infrastructure to other firms. “Think of it this way: Amazon has spent a lot of time
and money setting up a multitude of servers to service its popular website, and is making those
vast hardware and software resources available for all developers to use” (Meyer, 2015). Initial
Beta phase was run using Microsoft Windows Server as well as Microsoft SQL Server. Then, it
got extended to other operating systems like Linux and Open Solaris. In 2006, it formally
extended its Amazon’s Cloud commercial services in the form AWS which hosted various
applications for other business. “Since early 2006, Amazon Web Services (AWS) has provided
companies of all sizes with an infrastructure web services platform in the cloud. With AWS, you
can requisition compute power, storage, and other services–gaining access to a suite of elastic IT
infrastructure services as your business demands them” (Meyer, 2015).
With the excellent response for AWS, Amazon launched Amazon EC2 (Elastic Compute
Cloud) and Amazon S3 (Simple Storage Service) as part of AWS and also to balance the existing
AWS services. Originally Amazon started providing only storage services through S3, but later it
developed its cloud computing service by comprising both storage options as well as software
applications. From this background, we can understand that Amazon is a pioneer in cloud
computing, has developed its services through strong and quality research and development
process. By using Amazon’s EC2, clients can make use of various software applications at any
time. Those software applications can be utilized for running various business simulations, to
In 2002, Amazon initiated cloud computing in Beta form through Amazon Web Services
(AWS). Being the first player in this field, Amazon is proud to be called or considered a pioneer
in cloud computing. When the management at Amazon found that they had an extensive
Information System infrastructure for their purposes, they introduced the commercial process of
sharing its IS infrastructure to other firms. “Think of it this way: Amazon has spent a lot of time
and money setting up a multitude of servers to service its popular website, and is making those
vast hardware and software resources available for all developers to use” (Meyer, 2015). Initial
Beta phase was run using Microsoft Windows Server as well as Microsoft SQL Server. Then, it
got extended to other operating systems like Linux and Open Solaris. In 2006, it formally
extended its Amazon’s Cloud commercial services in the form AWS which hosted various
applications for other business. “Since early 2006, Amazon Web Services (AWS) has provided
companies of all sizes with an infrastructure web services platform in the cloud. With AWS, you
can requisition compute power, storage, and other services–gaining access to a suite of elastic IT
infrastructure services as your business demands them” (Meyer, 2015).
With the excellent response for AWS, Amazon launched Amazon EC2 (Elastic Compute
Cloud) and Amazon S3 (Simple Storage Service) as part of AWS and also to balance the existing
AWS services. Originally Amazon started providing only storage services through S3, but later it
developed its cloud computing service by comprising both storage options as well as software
applications. From this background, we can understand that Amazon is a pioneer in cloud
computing, has developed its services through strong and quality research and development
process. By using Amazon’s EC2, clients can make use of various software applications at any
time. Those software applications can be utilized for running various business simulations, to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

carry out programming languages, web hosting, and others. “EC2 enables scalable deployment
of applications by letting customers request a set number of virtual machines, onto which they
can load any application of their choice” (Kokkinos, Varvarigou, Kretsis, Soumplis, &
Varvarigos, 2015). EC2 can provide scalable deployment of software applications through which
clients can boot and load an Amazon Machine Image, thereby creating a virtual machine. This
process is called an "instance."
Assets
Named as EC2 with E denoting Elasticity, the main attribute of Amazon’s EC2 is
‘Elasticity’ by which its users can create instances, increase its usage, and the same time end the
“instances,” whenever they want. During their peak times in business, they might need additional
usage of software and other applications. The elasticity feature in EC2 allows the business clients
to increase their usage or access to the cloud services by paying extra rental charges whenever
required. Importantly all these are done in quick time. “Amazon EC2 reduces the time required
to obtain and boot new server instances to minutes, allowing you to quickly scale capacity, both
up and down, as your computing requirements change” (Kokkinos et al., 2015). Thus, the main
advantage that firms enjoy is that they can initiate or end your server ‘instances’ very quickly at
your convenience and based on your needs.
EC2 offers a comprehensive environment consisting of a memory, processor, and
preconfigured software. Amazon EC2 offers developers effective tools to construct applications
that can deter failure and differentiate themselves from standard failure cases. EC2’s scalability
occurs on a pay-as-you-go basis within a few minutes. This, therefore, minimizes the duration it
takes to acquire and boot the serve to mere minutes. This enables the user speedily scale capacity
to scale up or down according to the changes in computing needs. EC2 transforms the economies
of applications by letting customers request a set number of virtual machines, onto which they
can load any application of their choice” (Kokkinos, Varvarigou, Kretsis, Soumplis, &
Varvarigos, 2015). EC2 can provide scalable deployment of software applications through which
clients can boot and load an Amazon Machine Image, thereby creating a virtual machine. This
process is called an "instance."
Assets
Named as EC2 with E denoting Elasticity, the main attribute of Amazon’s EC2 is
‘Elasticity’ by which its users can create instances, increase its usage, and the same time end the
“instances,” whenever they want. During their peak times in business, they might need additional
usage of software and other applications. The elasticity feature in EC2 allows the business clients
to increase their usage or access to the cloud services by paying extra rental charges whenever
required. Importantly all these are done in quick time. “Amazon EC2 reduces the time required
to obtain and boot new server instances to minutes, allowing you to quickly scale capacity, both
up and down, as your computing requirements change” (Kokkinos et al., 2015). Thus, the main
advantage that firms enjoy is that they can initiate or end your server ‘instances’ very quickly at
your convenience and based on your needs.
EC2 offers a comprehensive environment consisting of a memory, processor, and
preconfigured software. Amazon EC2 offers developers effective tools to construct applications
that can deter failure and differentiate themselves from standard failure cases. EC2’s scalability
occurs on a pay-as-you-go basis within a few minutes. This, therefore, minimizes the duration it
takes to acquire and boot the serve to mere minutes. This enables the user speedily scale capacity
to scale up or down according to the changes in computing needs. EC2 transforms the economies
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
inherent in computing by enabling the user to pay only for the capacity utilized (Madhyastha et
al., 2017).
Cryptography used in Amazon EC2
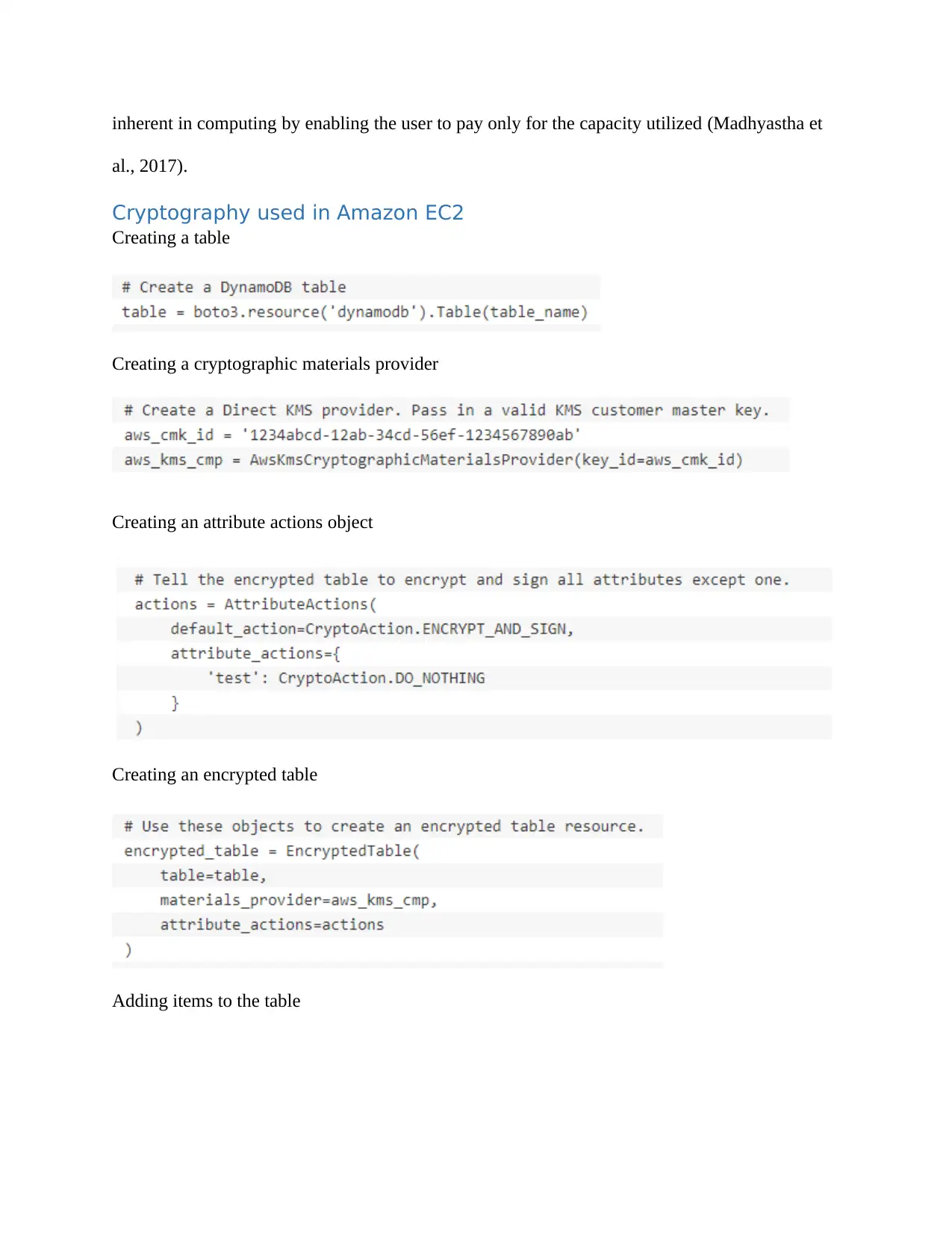
Creating a table
Creating a cryptographic materials provider
Creating an attribute actions object
Creating an encrypted table
Adding items to the table
al., 2017).
Cryptography used in Amazon EC2
Creating a table
Creating a cryptographic materials provider
Creating an attribute actions object
Creating an encrypted table
Adding items to the table
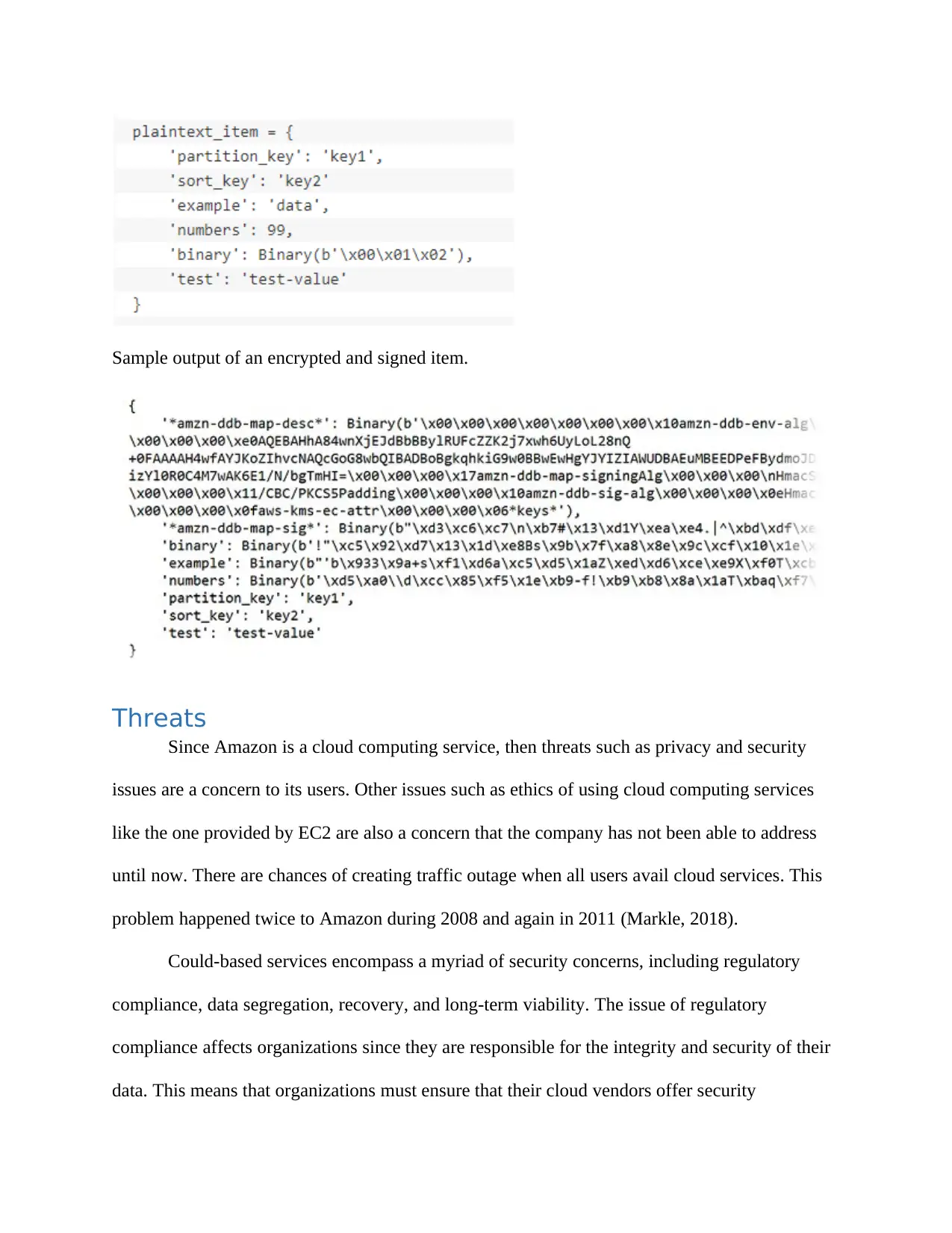
Sample output of an encrypted and signed item.
Threats
Since Amazon is a cloud computing service, then threats such as privacy and security
issues are a concern to its users. Other issues such as ethics of using cloud computing services
like the one provided by EC2 are also a concern that the company has not been able to address
until now. There are chances of creating traffic outage when all users avail cloud services. This
problem happened twice to Amazon during 2008 and again in 2011 (Markle, 2018).
Could-based services encompass a myriad of security concerns, including regulatory
compliance, data segregation, recovery, and long-term viability. The issue of regulatory
compliance affects organizations since they are responsible for the integrity and security of their
data. This means that organizations must ensure that their cloud vendors offer security
Threats
Since Amazon is a cloud computing service, then threats such as privacy and security
issues are a concern to its users. Other issues such as ethics of using cloud computing services
like the one provided by EC2 are also a concern that the company has not been able to address
until now. There are chances of creating traffic outage when all users avail cloud services. This
problem happened twice to Amazon during 2008 and again in 2011 (Markle, 2018).
Could-based services encompass a myriad of security concerns, including regulatory
compliance, data segregation, recovery, and long-term viability. The issue of regulatory
compliance affects organizations since they are responsible for the integrity and security of their
data. This means that organizations must ensure that their cloud vendors offer security
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

certifications and external audits. The issue of data segregation occurs since most times, data and
information from different organizations coexist within one cloud. Sometimes there is no clear
segregation of this information (Markle, 2018). Numerous encryption techniques are needed to
ensure the delineation of this information. With regard to the issue of recovery, there is a need
for vendors to provide specified plans of action applicable in case of calamities. Comprehensive
disaster recovery plans are vital to easing recovery. Another major security concern is that of
long-term viability, especially with regard to the vendor. Vendors chosen should possess
valuable experience and viability in matters of cloud computing. Effective methodologies for
maintaining cloud security include the layered approach (Markle, 2018).
Vulnerabilities
Amazon EC2 provides developers with the tools which have great importance in
maintaining their cloud storage. Cloud computing has enabled people in organizations who are
distantly separated can access, share, and process information from their remote locations. Cloud
computing also enables users who have little knowledge about the system to use it to its full
capacity. The Amazon EC2 service has the ability to detect security threats from applications and
remove them. This feature has enabled the Amazon EC2 program to compete favorably and
stand out of the rest (Saha, 2014). EC2 allows the IS of the clients to manage its instances (to
create or to terminate) by calculating the capability and the needs of the system. That is, as is
mentioned earlier, it automatically scales up and down according to the usage of the clients. In
addition, using this scaling feature, simple applications can be handled with easily accessible
schedule-based (e.g., time-of-the-day) and rule-based (e.g., time-of-the-day) auto-scaling
methods.
information from different organizations coexist within one cloud. Sometimes there is no clear
segregation of this information (Markle, 2018). Numerous encryption techniques are needed to
ensure the delineation of this information. With regard to the issue of recovery, there is a need
for vendors to provide specified plans of action applicable in case of calamities. Comprehensive
disaster recovery plans are vital to easing recovery. Another major security concern is that of
long-term viability, especially with regard to the vendor. Vendors chosen should possess
valuable experience and viability in matters of cloud computing. Effective methodologies for
maintaining cloud security include the layered approach (Markle, 2018).
Vulnerabilities
Amazon EC2 provides developers with the tools which have great importance in
maintaining their cloud storage. Cloud computing has enabled people in organizations who are
distantly separated can access, share, and process information from their remote locations. Cloud
computing also enables users who have little knowledge about the system to use it to its full
capacity. The Amazon EC2 service has the ability to detect security threats from applications and
remove them. This feature has enabled the Amazon EC2 program to compete favorably and
stand out of the rest (Saha, 2014). EC2 allows the IS of the clients to manage its instances (to
create or to terminate) by calculating the capability and the needs of the system. That is, as is
mentioned earlier, it automatically scales up and down according to the usage of the clients. In
addition, using this scaling feature, simple applications can be handled with easily accessible
schedule-based (e.g., time-of-the-day) and rule-based (e.g., time-of-the-day) auto-scaling
methods.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Recently, Amazon has added more control to this auto-scaling feature from start to the
termination of the instances. That is, this control feature can aid the users to “hold your newly
launched instances in a pending state while you perform actions on them, such as installing
software, before they are added to your Auto Scaling group and become in service.” On the same
lines, when instances are terminating, “you can temporarily stop the termination from
investigating the cause or retrieving logs from an instance before it terminates” (Agmon, Ben,
Schuster, & Tsafrir, 2013).
Security objectives
The main key feature of Amazon’s EC2 is its elastic IP addresses. That is, EC2’s elastic
IP address is not connected with any virtual machine instance. Instead, it is connected with the
client or user account that creates an instance. This gives an advantage over other static IP
address in the data centers. To explain, when a client or user connects with a cloud host, the user
can map an elastic IP address and can connect to any virtual machine instance. This can be
carried out without any help of the network administrator, and the user does not have to wait for
the DNS to authenticate this new connection. The connection lasts until it is deleted openly, but
the IP address will remain with the account even when there is no connection with the cloud. The
advantage of this feature is that it can actualize a quick connection to the cloud without major
impediments (Agmon et al., 2013).
CloudWatch is another feature of EC2 which make the service an effective one for its
clients. CloudWatch is a monitoring service inside EC2 which is used to collect and track clients’
resources consumption. It monitors resource consumption, such as CPU, networks, and disks.
“You can use Amazon CloudWatch to collect and track metrics, collect and monitor log files,
and set alarms” Clients can also get metrics and other details from Amazon CloudWatch by
termination of the instances. That is, this control feature can aid the users to “hold your newly
launched instances in a pending state while you perform actions on them, such as installing
software, before they are added to your Auto Scaling group and become in service.” On the same
lines, when instances are terminating, “you can temporarily stop the termination from
investigating the cause or retrieving logs from an instance before it terminates” (Agmon, Ben,
Schuster, & Tsafrir, 2013).
Security objectives
The main key feature of Amazon’s EC2 is its elastic IP addresses. That is, EC2’s elastic
IP address is not connected with any virtual machine instance. Instead, it is connected with the
client or user account that creates an instance. This gives an advantage over other static IP
address in the data centers. To explain, when a client or user connects with a cloud host, the user
can map an elastic IP address and can connect to any virtual machine instance. This can be
carried out without any help of the network administrator, and the user does not have to wait for
the DNS to authenticate this new connection. The connection lasts until it is deleted openly, but
the IP address will remain with the account even when there is no connection with the cloud. The
advantage of this feature is that it can actualize a quick connection to the cloud without major
impediments (Agmon et al., 2013).
CloudWatch is another feature of EC2 which make the service an effective one for its
clients. CloudWatch is a monitoring service inside EC2 which is used to collect and track clients’
resources consumption. It monitors resource consumption, such as CPU, networks, and disks.
“You can use Amazon CloudWatch to collect and track metrics, collect and monitor log files,
and set alarms” Clients can also get metrics and other details from Amazon CloudWatch by

accessing command line tools and through Web API’s (Fusaro, Patil, Gafni, Wall, & Tonellato,
2011). It is obvious that this feature is helpful to monitor the organizational level resource
utilization, applications performance, and the instances created from the client side. In addition,
the metrics collected through CloudWatch can enable the auto-scaling feature to automatically
create or eliminate EC2 instances, thereby helping the clients to carry out their tasks, including
their increased tasks without any stoppages.
Controls
Amazon EC2 provides complete control of the system as if it were on-premise by
allowing users to obtain and configure the capacity of their systems with a lot of ease.
Acquisition and booting a new server through Amazon EC2 has been simplified, providing a
quick means of either increasing or decreasing capacity depending on system requirements. This
is a highly scalable system which provides developers with tools to build resilient fail-safe
mechanisms. Its elasticity and simplicity allows for an easy way to manage instances both old
and recently acquired. Amazon EC2 gives complete control to its end user by providing root
access to its applications. Amazon EC2 storage can store and retrieve data of any amount, from
any web-based system at any particular time, making it extremely efficient and highly
manageable.
2011). It is obvious that this feature is helpful to monitor the organizational level resource
utilization, applications performance, and the instances created from the client side. In addition,
the metrics collected through CloudWatch can enable the auto-scaling feature to automatically
create or eliminate EC2 instances, thereby helping the clients to carry out their tasks, including
their increased tasks without any stoppages.
Controls
Amazon EC2 provides complete control of the system as if it were on-premise by
allowing users to obtain and configure the capacity of their systems with a lot of ease.
Acquisition and booting a new server through Amazon EC2 has been simplified, providing a
quick means of either increasing or decreasing capacity depending on system requirements. This
is a highly scalable system which provides developers with tools to build resilient fail-safe
mechanisms. Its elasticity and simplicity allows for an easy way to manage instances both old
and recently acquired. Amazon EC2 gives complete control to its end user by providing root
access to its applications. Amazon EC2 storage can store and retrieve data of any amount, from
any web-based system at any particular time, making it extremely efficient and highly
manageable.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
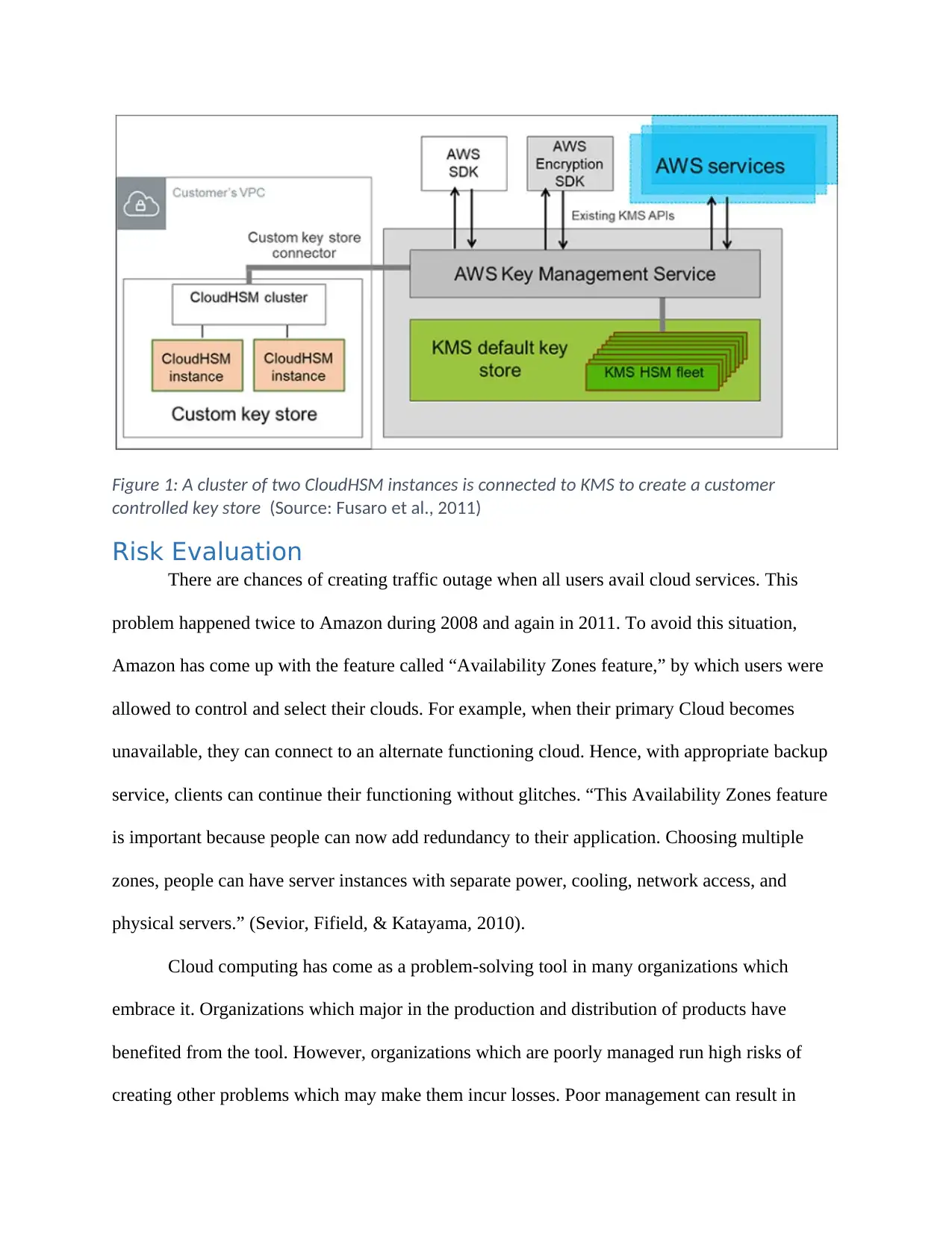
Figure 1: A cluster of two CloudHSM instances is connected to KMS to create a customer
controlled key store (Source: Fusaro et al., 2011)
Risk Evaluation
There are chances of creating traffic outage when all users avail cloud services. This
problem happened twice to Amazon during 2008 and again in 2011. To avoid this situation,
Amazon has come up with the feature called “Availability Zones feature,” by which users were
allowed to control and select their clouds. For example, when their primary Cloud becomes
unavailable, they can connect to an alternate functioning cloud. Hence, with appropriate backup
service, clients can continue their functioning without glitches. “This Availability Zones feature
is important because people can now add redundancy to their application. Choosing multiple
zones, people can have server instances with separate power, cooling, network access, and
physical servers.” (Sevior, Fifield, & Katayama, 2010).
Cloud computing has come as a problem-solving tool in many organizations which
embrace it. Organizations which major in the production and distribution of products have
benefited from the tool. However, organizations which are poorly managed run high risks of
creating other problems which may make them incur losses. Poor management can result in
controlled key store (Source: Fusaro et al., 2011)
Risk Evaluation
There are chances of creating traffic outage when all users avail cloud services. This
problem happened twice to Amazon during 2008 and again in 2011. To avoid this situation,
Amazon has come up with the feature called “Availability Zones feature,” by which users were
allowed to control and select their clouds. For example, when their primary Cloud becomes
unavailable, they can connect to an alternate functioning cloud. Hence, with appropriate backup
service, clients can continue their functioning without glitches. “This Availability Zones feature
is important because people can now add redundancy to their application. Choosing multiple
zones, people can have server instances with separate power, cooling, network access, and
physical servers.” (Sevior, Fifield, & Katayama, 2010).
Cloud computing has come as a problem-solving tool in many organizations which
embrace it. Organizations which major in the production and distribution of products have
benefited from the tool. However, organizations which are poorly managed run high risks of
creating other problems which may make them incur losses. Poor management can result in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

excessive energy usage, which will make the organization risk incurring a loss. Businesses are
also required to uphold ethical standards of professionalism while using cloud computing. The
effective management of cloud networking in an organization help ascertain sustainable
environment, which is necessary for future generations (Wong & Goscinski, 2012).
Conclusions
Based on the above analysis of Amazon’s EC2, its effective features, and its favorable
comparison with other cloud providers, it is obvious that EC2 can be the best product for
organizations that are looking to use cloud computing services. Amazon Elastic Compute Cloud
is a service that helps one to configure cloud computing capacity with minimal difficulties. The
service developed by Amazon helps developers easily set up cloud computing services that will
benefit their needs and be in a position to manage it well. Since the inception of cloud
computing, users have known its benefits, and this has been noted by an increase in usage. The
Amazon EC2 is an effective application when the user modifies the application to suit their
organization functions. The services provided by Amazon EC2 are inexpensive and easy to use
and compete favorably in the market space
also required to uphold ethical standards of professionalism while using cloud computing. The
effective management of cloud networking in an organization help ascertain sustainable
environment, which is necessary for future generations (Wong & Goscinski, 2012).
Conclusions
Based on the above analysis of Amazon’s EC2, its effective features, and its favorable
comparison with other cloud providers, it is obvious that EC2 can be the best product for
organizations that are looking to use cloud computing services. Amazon Elastic Compute Cloud
is a service that helps one to configure cloud computing capacity with minimal difficulties. The
service developed by Amazon helps developers easily set up cloud computing services that will
benefit their needs and be in a position to manage it well. Since the inception of cloud
computing, users have known its benefits, and this has been noted by an increase in usage. The
Amazon EC2 is an effective application when the user modifies the application to suit their
organization functions. The services provided by Amazon EC2 are inexpensive and easy to use
and compete favorably in the market space

References
Agmon, O., Ben, M., Schuster, A., & Tsafrir, D. (2013). Deconstructing Amazon EC2 Spot
Instance Pricing. ACM Trans. Econ. Comput., 1(3), 16:1–16:20.
https://doi.org/10.1145/2509413.2509416
Fusaro, V. A., Patil, P., Gafni, E., Wall, D. P., & Tonellato, P. J. (2011). Biomedical Cloud
Computing With Amazon Web Services. PLoS Computational Biology, 7(8).
https://doi.org/10.1371/journal.pcbi.1002147
Kokkinos, P., Varvarigou, T. A., Kretsis, A., Soumplis, P., & Varvarigos, E. A. (2015). SuMo:
Analysis and Optimization of Amazon EC2 Instances. Journal of Grid Computing, 13(2),
255–274. https://doi.org/10.1007/s10723-014-9311-x
Madhyastha, T. M., Koh, N., Day, T. K. M., Hernández-Fernández, M., Kelley, A., Peterson, D.
J., … Grabowski, T. J. (2017). Running Neuroimaging Applications on Amazon Web
Services: How, When, and at What Cost? Frontiers in Neuroinformatics, 11.
https://doi.org/10.3389/fninf.2017.00063
Markle, L. (2018, August 13). Media coverage: Amazon AWS cloud computing partnership with
19 LA community colleges. Retrieved May 25, 2019, from Los Angeles County
Economic Development Corporation website: https://laedc.org/2018/08/13/media-
amazon-cloud-computing-colleges/
Meyer, R. (2015, April 23). The Unbelievable Power of Amazon Web Services. Retrieved May
25, 2019, from The Atlantic website:
https://www.theatlantic.com/technology/archive/2015/04/the-unbelievable-power-of-
amazon-web-services/391281/
Agmon, O., Ben, M., Schuster, A., & Tsafrir, D. (2013). Deconstructing Amazon EC2 Spot
Instance Pricing. ACM Trans. Econ. Comput., 1(3), 16:1–16:20.
https://doi.org/10.1145/2509413.2509416
Fusaro, V. A., Patil, P., Gafni, E., Wall, D. P., & Tonellato, P. J. (2011). Biomedical Cloud
Computing With Amazon Web Services. PLoS Computational Biology, 7(8).
https://doi.org/10.1371/journal.pcbi.1002147
Kokkinos, P., Varvarigou, T. A., Kretsis, A., Soumplis, P., & Varvarigos, E. A. (2015). SuMo:
Analysis and Optimization of Amazon EC2 Instances. Journal of Grid Computing, 13(2),
255–274. https://doi.org/10.1007/s10723-014-9311-x
Madhyastha, T. M., Koh, N., Day, T. K. M., Hernández-Fernández, M., Kelley, A., Peterson, D.
J., … Grabowski, T. J. (2017). Running Neuroimaging Applications on Amazon Web
Services: How, When, and at What Cost? Frontiers in Neuroinformatics, 11.
https://doi.org/10.3389/fninf.2017.00063
Markle, L. (2018, August 13). Media coverage: Amazon AWS cloud computing partnership with
19 LA community colleges. Retrieved May 25, 2019, from Los Angeles County
Economic Development Corporation website: https://laedc.org/2018/08/13/media-
amazon-cloud-computing-colleges/
Meyer, R. (2015, April 23). The Unbelievable Power of Amazon Web Services. Retrieved May
25, 2019, from The Atlantic website:
https://www.theatlantic.com/technology/archive/2015/04/the-unbelievable-power-of-
amazon-web-services/391281/
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





