Security Evaluation of Amazon Web Services (AWS) - Report
VerifiedAdded on 2023/03/21
|10
|2101
|84
Report
AI Summary
This report provides a comprehensive security evaluation of Amazon Web Services (AWS). The study begins with an introduction to information system security and highlights the importance of security measures. The report then identifies AWS assets, including organizational databases, networks, and hardware devices, and discusses potential security threats such as hacking, malware attacks, and denial-of-service attacks. It delves into AWS vulnerabilities, emphasizing the shared responsibility model for security, and details penetration testing, password snooping, SQL injection, and cross-site scripting (XSS) attempts to identify weaknesses. The report also outlines Amazon's security objectives and the vulnerability controls implemented. The evaluation includes a security evaluation matrix that assesses the likelihood and impact of vulnerabilities, along with proposed control measures. The report concludes by summarizing the key findings, emphasizing the importance of robust security measures and continuous monitoring to prevent data breaches and ensure the stability of the AWS platform. The evaluation utilized tools such as sqlmap and Wireshark to test vulnerabilities. The report also discusses the effectiveness of AWS's incident response and customer support in addressing security concerns.

Amazon Web Services security evaluation
Name
Institution
Professor
Course
Date
Name
Institution
Professor
Course
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction...............................................................................................................................................3
AWS Assets................................................................................................................................................4
AWS Security threats................................................................................................................................4
Amazon Web Service vulnerabilities.......................................................................................................4
Amazon security objectives.......................................................................................................................6
AWS vulnerability controls......................................................................................................................7
Security evaluation matrix........................................................................................................................8
Conclusion..................................................................................................................................................9
Bibliography............................................................................................................................................10
Introduction...............................................................................................................................................3
AWS Assets................................................................................................................................................4
AWS Security threats................................................................................................................................4
Amazon Web Service vulnerabilities.......................................................................................................4
Amazon security objectives.......................................................................................................................6
AWS vulnerability controls......................................................................................................................7
Security evaluation matrix........................................................................................................................8
Conclusion..................................................................................................................................................9
Bibliography............................................................................................................................................10

Introduction
Information system security has been a great challenge in today’s technology world due
to lack of proper security measures. To make sure organizational data remains secure, some
protection techniques and measures should be adopted by the subjected organization. Some of
the measures are users, organization and service provider related. In this regard, it can be
observed that the security of an information system involves several entities with different roles
to play. Since each information system or product have different requirements that have to be
met, the paper would focus on Amazon Web Services (AWS) as a product (Micro 2013, pp. 5-6).
Security evaluation would be based on several scenarios such as subjecting AWS platform to
stress testing. The security testing and analysis on AWS would also be done through penetration
testing by evaluating if some vulnerabilities exist. Sqlmap and Wireshark are some of the best
tools which would be used to perform security checks, perform database injections and subject
available resources to stress. On the same note, cross-site scripting (XSS) would be done to try
and extract confidential information such as login from novice users. Finally, the free account
would be created in the AWS platform and try to compromise the AWS application console. In
this case, the vulnerability checks would be focused on poor user accounts protection which can
be advanced later to AWS console. The system security evaluation offers an opportunity to
perform prior analysis on security risks that specific information system might be exposed to.
The goal of the study would be to assess security measures and techniques which can be used to
compromise organizational operations.
Information system security has been a great challenge in today’s technology world due
to lack of proper security measures. To make sure organizational data remains secure, some
protection techniques and measures should be adopted by the subjected organization. Some of
the measures are users, organization and service provider related. In this regard, it can be
observed that the security of an information system involves several entities with different roles
to play. Since each information system or product have different requirements that have to be
met, the paper would focus on Amazon Web Services (AWS) as a product (Micro 2013, pp. 5-6).
Security evaluation would be based on several scenarios such as subjecting AWS platform to
stress testing. The security testing and analysis on AWS would also be done through penetration
testing by evaluating if some vulnerabilities exist. Sqlmap and Wireshark are some of the best
tools which would be used to perform security checks, perform database injections and subject
available resources to stress. On the same note, cross-site scripting (XSS) would be done to try
and extract confidential information such as login from novice users. Finally, the free account
would be created in the AWS platform and try to compromise the AWS application console. In
this case, the vulnerability checks would be focused on poor user accounts protection which can
be advanced later to AWS console. The system security evaluation offers an opportunity to
perform prior analysis on security risks that specific information system might be exposed to.
The goal of the study would be to assess security measures and techniques which can be used to
compromise organizational operations.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

AWS Assets
Amazon Web Services supports many business entities which depends on it to run its
daily operations. Some of the assets that can be adversely affected by insecure AWS are;
organizational database, Network and hardware devices such as computers, routers and sensors.
The database is the key to any organizational operations and failure to secure data may render
organizational operations unreliable (Micro 2013, pp. 5). Next, the network supports all online
operations and sharing of data within and outside the organization. Its security should be
guaranteed for successful business operations. Finally, hardware devices such as computers
should be accorded necessary security prevention by securing them with strong ant malware.
AWS Security threats
Some of the threats that can affect Amazon business operations are; Hacking, malware
attacks, unsecured web interfaces and Denial of services (DoS) (Micro 2013, pp. 2). Hacking can
be done by either internal or external entities with vested interests such as competitors and
experts doing it for a hobby. Malware infection is also performed by third parties through the
sharing of data or employees injecting infected disks intentionally. Unsecured web interfaces are
caused by developers failing to adhere to secure design principles. These threats have a higher
magnitude of impacts on service delivery because the attacker on one of the service or assets
results to operational issues.
Amazon Web Service vulnerabilities
Amazon Web services have set up its infrastructure framework in such a way that it
remains the responsibility of all stakeholders to secure its infrastructure. It is important to note
that system security cannot be a task dedicated to a single entity. The AWS being an
infrastructure that supports different services in use by various entities, making the sole
responsibility of each of the service provider cannot guarantee the required security. It is from
Amazon Web Services supports many business entities which depends on it to run its
daily operations. Some of the assets that can be adversely affected by insecure AWS are;
organizational database, Network and hardware devices such as computers, routers and sensors.
The database is the key to any organizational operations and failure to secure data may render
organizational operations unreliable (Micro 2013, pp. 5). Next, the network supports all online
operations and sharing of data within and outside the organization. Its security should be
guaranteed for successful business operations. Finally, hardware devices such as computers
should be accorded necessary security prevention by securing them with strong ant malware.
AWS Security threats
Some of the threats that can affect Amazon business operations are; Hacking, malware
attacks, unsecured web interfaces and Denial of services (DoS) (Micro 2013, pp. 2). Hacking can
be done by either internal or external entities with vested interests such as competitors and
experts doing it for a hobby. Malware infection is also performed by third parties through the
sharing of data or employees injecting infected disks intentionally. Unsecured web interfaces are
caused by developers failing to adhere to secure design principles. These threats have a higher
magnitude of impacts on service delivery because the attacker on one of the service or assets
results to operational issues.
Amazon Web Service vulnerabilities
Amazon Web services have set up its infrastructure framework in such a way that it
remains the responsibility of all stakeholders to secure its infrastructure. It is important to note
that system security cannot be a task dedicated to a single entity. The AWS being an
infrastructure that supports different services in use by various entities, making the sole
responsibility of each of the service provider cannot guarantee the required security. It is from
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

distribution of the security responsibilities that hackers try to evaluate vulnerabilities that system
users have left open without their knowledge. Under shared responsibilities, Amazon keeps
vigilant over the security of its applications but it is the responsibility of the system owner to
make sure all security configurations are done. When attacking the system, system vulnerabilities
would majorly evaluate the concept of shared responsibility because it is obvious that shared
resources have so many loopholes. It is understood that Amazon has set guidelines and
requirements for creating strong authentication but many system users would end up using
obvious passwords that can be easily guessed. During system security vulnerability testing,
password snooping has been one of the major criteria that was intensively evaluated. Through
eavesdropping by capturing transmitted packets, it was possible to observe that Amazon has
secured its application through data encryption. To customers who create weak passwords, it was
possible to analyze available usernames and try to guess the possibility of getting the right
password through multiple combinations. The password vulnerability was tested by creating a
free account with Amazon platform and requested a friend to change the password. Being aware
of the username, password search was done by trying the possible combination of possible
passwords. Though password cracking was unsuccessful, it was observable that weak password
such as using individual names as well as relatives can be a security threat.
Additionally, vulnerability evaluation of the Amazon platform has been done by
analyzing development and configuration loopholes which included scanning to check the nature
of protection done. Vulnerability check was done through the use of tools such as sqlmap and
data packets analysis captured through the use of Wireshark. The combination of these tools was
quite useful because it was possible to subject the Amazon platform under SQL injection. As an
attacker, it was possible to observe that combination of sqlmap and Wireshark gave promising
users have left open without their knowledge. Under shared responsibilities, Amazon keeps
vigilant over the security of its applications but it is the responsibility of the system owner to
make sure all security configurations are done. When attacking the system, system vulnerabilities
would majorly evaluate the concept of shared responsibility because it is obvious that shared
resources have so many loopholes. It is understood that Amazon has set guidelines and
requirements for creating strong authentication but many system users would end up using
obvious passwords that can be easily guessed. During system security vulnerability testing,
password snooping has been one of the major criteria that was intensively evaluated. Through
eavesdropping by capturing transmitted packets, it was possible to observe that Amazon has
secured its application through data encryption. To customers who create weak passwords, it was
possible to analyze available usernames and try to guess the possibility of getting the right
password through multiple combinations. The password vulnerability was tested by creating a
free account with Amazon platform and requested a friend to change the password. Being aware
of the username, password search was done by trying the possible combination of possible
passwords. Though password cracking was unsuccessful, it was observable that weak password
such as using individual names as well as relatives can be a security threat.
Additionally, vulnerability evaluation of the Amazon platform has been done by
analyzing development and configuration loopholes which included scanning to check the nature
of protection done. Vulnerability check was done through the use of tools such as sqlmap and
data packets analysis captured through the use of Wireshark. The combination of these tools was
quite useful because it was possible to subject the Amazon platform under SQL injection. As an
attacker, it was possible to observe that combination of sqlmap and Wireshark gave promising

results. It was very impressive to see tools being used to suppress the AWS by inducing stress on
the system. Stress testing was done by initiating multiple result requests simultaneously. Both
stress testing and SQL injection were done at the user level and AWS console level login. By
inducing stress on to the system, it was possible to over-utilize resources that are required by
other users which might have caused Denial of Services (DoS). Stress was evaluated by
subjecting the system under immense request from Linux based attacker while trying to access
the same infrastructure from a windows based computer as novice users. The slowness in gaining
access to an individual created a free account was a clear indication that the AWS server was
receiving many requests that before. After ending the stress testing process, system testing access
was done and it was fine. In this regard, it was observed that the system can be subjected to
intense spam request by inducing undesirable resource requests which result in DoS. As the
system was under induced stress testing, SQL injection was being done by scanning continuously
on any open port directed to available databases. Besides, programming loopholes were being
tested by trying to check the feasibility of escape and special characters being unhandled at the
exception level.
Amazon security objectives
The goal of Amazon is to offer secure and stable services to all its customers. To achieve
its goals, Amazon has come up with a security framework to secure its infrastructure. It is the
responsibility of every Amazon service consumer to secure the infrastructure with strong
authentication credentials. The next security requirements from the customers' are to report any
suspected security breach to the Amazon security team. The last security requirement is for
Amazon to monitor any security issue and report it to the customer.
the system. Stress testing was done by initiating multiple result requests simultaneously. Both
stress testing and SQL injection were done at the user level and AWS console level login. By
inducing stress on to the system, it was possible to over-utilize resources that are required by
other users which might have caused Denial of Services (DoS). Stress was evaluated by
subjecting the system under immense request from Linux based attacker while trying to access
the same infrastructure from a windows based computer as novice users. The slowness in gaining
access to an individual created a free account was a clear indication that the AWS server was
receiving many requests that before. After ending the stress testing process, system testing access
was done and it was fine. In this regard, it was observed that the system can be subjected to
intense spam request by inducing undesirable resource requests which result in DoS. As the
system was under induced stress testing, SQL injection was being done by scanning continuously
on any open port directed to available databases. Besides, programming loopholes were being
tested by trying to check the feasibility of escape and special characters being unhandled at the
exception level.
Amazon security objectives
The goal of Amazon is to offer secure and stable services to all its customers. To achieve
its goals, Amazon has come up with a security framework to secure its infrastructure. It is the
responsibility of every Amazon service consumer to secure the infrastructure with strong
authentication credentials. The next security requirements from the customers' are to report any
suspected security breach to the Amazon security team. The last security requirement is for
Amazon to monitor any security issue and report it to the customer.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

AWS vulnerability controls
During security evaluation on penetration and stress testing, it was observable that our
requested were being terminated immaturely. This was obvious that our connection to the system
was being watched and where necessary terminated. If the service provider does not monitor
system operations, it can be compromised which might result in DoS to the actual system users.
This was a clear indication that failure by the Amazon to keep track of the security operations, its
services might be interrupted to cause substantial business impact to the Amazon. On the same
note, it was observed that after XSS interrogation, some system users responded immediately but
changed their mind. Some of the details shared could not work as they pop out an error that
password had been changed a moment ago. This was a clear indication that some system users
had detected some form of fraud and had act immediately before the worst could happen. It was
also presumed that some system users reported the instance to Amazon. Important to note is that
Amazon does not allow integration of its platform with other third-party applications. The final
security measures observed from AWS security evaluation was customer involvement on
instances where customer raise complain. To test the Amazon response effectiveness, a
complaint was filed with the support desk and within a short time, the feedback was received
through a call and mail. After a couple of minutes, they called again to confirm if the system had
stabilized. It was observed that Amazon takes the security of its infrastructure and data privacy
very seriously.
During security evaluation on penetration and stress testing, it was observable that our
requested were being terminated immaturely. This was obvious that our connection to the system
was being watched and where necessary terminated. If the service provider does not monitor
system operations, it can be compromised which might result in DoS to the actual system users.
This was a clear indication that failure by the Amazon to keep track of the security operations, its
services might be interrupted to cause substantial business impact to the Amazon. On the same
note, it was observed that after XSS interrogation, some system users responded immediately but
changed their mind. Some of the details shared could not work as they pop out an error that
password had been changed a moment ago. This was a clear indication that some system users
had detected some form of fraud and had act immediately before the worst could happen. It was
also presumed that some system users reported the instance to Amazon. Important to note is that
Amazon does not allow integration of its platform with other third-party applications. The final
security measures observed from AWS security evaluation was customer involvement on
instances where customer raise complain. To test the Amazon response effectiveness, a
complaint was filed with the support desk and within a short time, the feedback was received
through a call and mail. After a couple of minutes, they called again to confirm if the system had
stabilized. It was observed that Amazon takes the security of its infrastructure and data privacy
very seriously.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
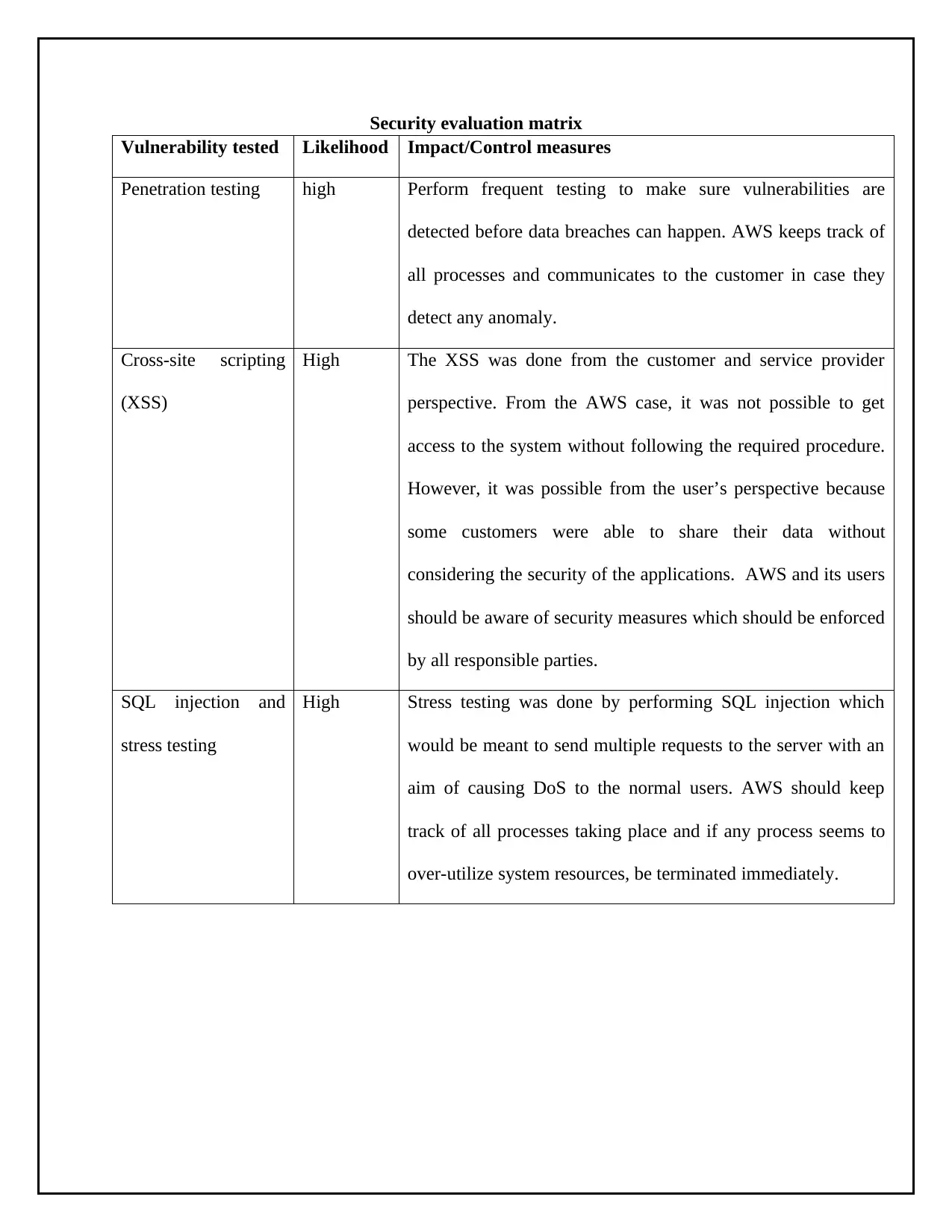
Security evaluation matrix
Vulnerability tested Likelihood Impact/Control measures
Penetration testing high Perform frequent testing to make sure vulnerabilities are
detected before data breaches can happen. AWS keeps track of
all processes and communicates to the customer in case they
detect any anomaly.
Cross-site scripting
(XSS)
High The XSS was done from the customer and service provider
perspective. From the AWS case, it was not possible to get
access to the system without following the required procedure.
However, it was possible from the user’s perspective because
some customers were able to share their data without
considering the security of the applications. AWS and its users
should be aware of security measures which should be enforced
by all responsible parties.
SQL injection and
stress testing
High Stress testing was done by performing SQL injection which
would be meant to send multiple requests to the server with an
aim of causing DoS to the normal users. AWS should keep
track of all processes taking place and if any process seems to
over-utilize system resources, be terminated immediately.
Vulnerability tested Likelihood Impact/Control measures
Penetration testing high Perform frequent testing to make sure vulnerabilities are
detected before data breaches can happen. AWS keeps track of
all processes and communicates to the customer in case they
detect any anomaly.
Cross-site scripting
(XSS)
High The XSS was done from the customer and service provider
perspective. From the AWS case, it was not possible to get
access to the system without following the required procedure.
However, it was possible from the user’s perspective because
some customers were able to share their data without
considering the security of the applications. AWS and its users
should be aware of security measures which should be enforced
by all responsible parties.
SQL injection and
stress testing
High Stress testing was done by performing SQL injection which
would be meant to send multiple requests to the server with an
aim of causing DoS to the normal users. AWS should keep
track of all processes taking place and if any process seems to
over-utilize system resources, be terminated immediately.

Conclusion
Technology infrastructure requires the best security measures and close monitoring to
make sure data breaches does not have devastating effects if it occurs. The main goal was to
evaluate the Amazon We service security level, infrastructure techniques applied and incidence
response when reported by customers or when observed by the Amazon security team. The
evaluation was based on penetration testing, password cracking and cross-site scripting.
Vulnerability testing was done through the use of tools such as sqlmap and Wireshark. Sqlmap
was used to test for vulnerability such as open ports and subjecting system under stress by
inducing unnecessary resource requests. Through stress testing, it was possible to observe
multiple requests being generated by sqlmap while at the same time SQL injection into the
available database being scanned. Though no database was detected due to security protection,
vulnerability scanning runs successfully inducing server with so many requests that made
services somehow unavailable. Stress testing was meant to make resources unavailable which in
turn would cause DoS to the actual system users. Cross-site scripting was attempted on both user
and Amazon support by trying to trick subjected parties to share system login credentials which
were meant to make unauthorized access to customers' data. In this regard, it would be important
to point out that Amazon security has been given the required security and it is difficult to gain
access to either customer or amazon console with proper authentication.
Technology infrastructure requires the best security measures and close monitoring to
make sure data breaches does not have devastating effects if it occurs. The main goal was to
evaluate the Amazon We service security level, infrastructure techniques applied and incidence
response when reported by customers or when observed by the Amazon security team. The
evaluation was based on penetration testing, password cracking and cross-site scripting.
Vulnerability testing was done through the use of tools such as sqlmap and Wireshark. Sqlmap
was used to test for vulnerability such as open ports and subjecting system under stress by
inducing unnecessary resource requests. Through stress testing, it was possible to observe
multiple requests being generated by sqlmap while at the same time SQL injection into the
available database being scanned. Though no database was detected due to security protection,
vulnerability scanning runs successfully inducing server with so many requests that made
services somehow unavailable. Stress testing was meant to make resources unavailable which in
turn would cause DoS to the actual system users. Cross-site scripting was attempted on both user
and Amazon support by trying to trick subjected parties to share system login credentials which
were meant to make unauthorized access to customers' data. In this regard, it would be important
to point out that Amazon security has been given the required security and it is difficult to gain
access to either customer or amazon console with proper authentication.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Bibliography
Micro, T., 2013. Best Practices for Security and Compliance with Amazon Web Services. White
Paper, 1-11.
Micro, T., 2013. Best Practices for Security and Compliance with Amazon Web Services. White
Paper, 1-11.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





