An Empirical Study of VPNs for IoT Devices (BSC301)
VerifiedAdded on 2022/12/19
|25
|6293
|1
Project
AI Summary
This project plan outlines an empirical study comparing various VPN technologies (OpenVPN, ZeroTier, Tinc, and Wireguard) for resource-constrained IoT devices. The study aims to evaluate the subjective setup complexity and security of each VPN option, as well as their objective performance metrics, including CPU usage, memory usage, and packet overhead. The research will involve setting up VPN servers in the cloud (Microsoft Azure) and clients using Murdoch University's resources. The project encompasses problem statement, literature review, research aims, research design, project scope, time management, communication, risk management, and human resource management plans. The plan also includes a team contract and roles, culminating in a conclusion and appendices with references and a glossary. The goal is to determine the suitability of modern VPN protocols for IoT devices, considering their limited resources and increasing security needs.

An Empirical Study of VPN Options for Resource-Constrained IoT Devices
BSC301: Applied Research Skills In ICT
ICT Project Plan
Semester 1, 2019
Group: David_1
Supervisor:
Dr David Murray
Group members:
Michael Schwenger 33087838
Daniel Alberts 32969931
Enrique Getino Reboso 33163823
Khalid Bin Walid Baeisa 32490882
Patrick Nkhata 33254798
Robert Edmonds 33110938
Abstract: In this study, we will be comparing the different VPN technologies for resource-
constrained IoT devices. We will be looking at: OpenVPN, ZeroTier, Tinc and Wireguard to
compare the subjective setup complexity and security, as well as the objective CPU, Memory
and packet overheads of each option.
1
BSC301: Applied Research Skills In ICT
ICT Project Plan
Semester 1, 2019
Group: David_1
Supervisor:
Dr David Murray
Group members:
Michael Schwenger 33087838
Daniel Alberts 32969931
Enrique Getino Reboso 33163823
Khalid Bin Walid Baeisa 32490882
Patrick Nkhata 33254798
Robert Edmonds 33110938
Abstract: In this study, we will be comparing the different VPN technologies for resource-
constrained IoT devices. We will be looking at: OpenVPN, ZeroTier, Tinc and Wireguard to
compare the subjective setup complexity and security, as well as the objective CPU, Memory
and packet overheads of each option.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Summary of Project 3
Problem Statement 3
Literature Review 3
Research Aims and Research Questions 4
Research Design 5
Overview 5
Hardware Requirements 5
Software Requirements 5
Special Resources Required 5
Data Collection 6
Project Scope Management 7
Project Time Management 10
Discussion of the Work Breakdown Structure 12
Project Communications Management 13
Communications plan 13
Project information storage 17
Project Risk Management 18
Project Human Resources Management 19
Project roles and responsibilities 19
Procedures to resolve conflicts within the team 19
Conclusion 19
Appendices 20
Glossary 20
References 20
Team Contract 21
Team Roles 22
ICT301 Group Declaration Sheet 23
2
Summary of Project 3
Problem Statement 3
Literature Review 3
Research Aims and Research Questions 4
Research Design 5
Overview 5
Hardware Requirements 5
Software Requirements 5
Special Resources Required 5
Data Collection 6
Project Scope Management 7
Project Time Management 10
Discussion of the Work Breakdown Structure 12
Project Communications Management 13
Communications plan 13
Project information storage 17
Project Risk Management 18
Project Human Resources Management 19
Project roles and responsibilities 19
Procedures to resolve conflicts within the team 19
Conclusion 19
Appendices 20
Glossary 20
References 20
Team Contract 21
Team Roles 22
ICT301 Group Declaration Sheet 23
2

Summary of Project
The objective of this project is to state if the new VPN protocols are suitable to be used on
resource-constraint hardware from IoT devices. It will be compared against other VPN
products and it will be measured through metrics like response time and throughput. The
VPN servers will be hosted in the cloud, Microsoft Azure, while we locally run the clients
using Murdoch University’s resources.
Problem Statement
The number of IoT devices and security requirements, when it comes to network connections
is increasing. A large number of end users are willingly using VPN connections on a daily
basis, not only for business but also for private use. The need for securing these connections
grows side to side with the concern for privacy. These IoT devices need to enhance their
security in order to make them more attractive to the end user.
The actual VPN services have powerful tools and protocols to protect the security of the
connections. But on the other hand, the software to provide these levels of security are
resource intensive and require hardware that many of the IoT devices cannot provide, at this
moment, in order to run a VPN service smoothly.
Literature Review
IoT devices are more present than ever. All these devices are designed to be connected not
only to our home or office network but also, to public hotspots. The mobility that some of
them provide makes them really handy when it comes to access internet from anywhere in the
world, but, what about the security and the privacy of those connections?
It has been stated that these technologies are vulnerable to replay, man-in-the-middle and
denial-of-service attacks. To prevent man-in-the-middle attacks all communication between
the client and gateway should be over an encrypted VPN/IPsec tunnel. This solution is only
suitable for those IoT devices that have the necessary computational and storage capabilities
to gather the required data and run the necessary software, including VPN. Additionally
highly sensitive data should be encrypted within the tunnel, though this can take a
computational and speed hit on both the gateway and client device. Also, control system
gateways with sufficient compute power can also be used with modern IoT client devices to
help manage the security challenges of the remote access control (Michael W. Condry,
Catherine Blackadar Nelson, 2016).
Resource constraint in IOT devices are an important drawbacks for securing these network.
Hence, the challenge is to device such a solution that does not require huge computing
resources and computing power, but still delivers an efficient solution for device security.
Nowadays, the amount of IoT devices capable of running VPN software without having their
performance affected is still low. It is in this situation where lighter VPN protocols like
Wireguard can make a huge difference. WireGuard weights in at around 4,000 lines of code.
3
The objective of this project is to state if the new VPN protocols are suitable to be used on
resource-constraint hardware from IoT devices. It will be compared against other VPN
products and it will be measured through metrics like response time and throughput. The
VPN servers will be hosted in the cloud, Microsoft Azure, while we locally run the clients
using Murdoch University’s resources.
Problem Statement
The number of IoT devices and security requirements, when it comes to network connections
is increasing. A large number of end users are willingly using VPN connections on a daily
basis, not only for business but also for private use. The need for securing these connections
grows side to side with the concern for privacy. These IoT devices need to enhance their
security in order to make them more attractive to the end user.
The actual VPN services have powerful tools and protocols to protect the security of the
connections. But on the other hand, the software to provide these levels of security are
resource intensive and require hardware that many of the IoT devices cannot provide, at this
moment, in order to run a VPN service smoothly.
Literature Review
IoT devices are more present than ever. All these devices are designed to be connected not
only to our home or office network but also, to public hotspots. The mobility that some of
them provide makes them really handy when it comes to access internet from anywhere in the
world, but, what about the security and the privacy of those connections?
It has been stated that these technologies are vulnerable to replay, man-in-the-middle and
denial-of-service attacks. To prevent man-in-the-middle attacks all communication between
the client and gateway should be over an encrypted VPN/IPsec tunnel. This solution is only
suitable for those IoT devices that have the necessary computational and storage capabilities
to gather the required data and run the necessary software, including VPN. Additionally
highly sensitive data should be encrypted within the tunnel, though this can take a
computational and speed hit on both the gateway and client device. Also, control system
gateways with sufficient compute power can also be used with modern IoT client devices to
help manage the security challenges of the remote access control (Michael W. Condry,
Catherine Blackadar Nelson, 2016).
Resource constraint in IOT devices are an important drawbacks for securing these network.
Hence, the challenge is to device such a solution that does not require huge computing
resources and computing power, but still delivers an efficient solution for device security.
Nowadays, the amount of IoT devices capable of running VPN software without having their
performance affected is still low. It is in this situation where lighter VPN protocols like
Wireguard can make a huge difference. WireGuard weights in at around 4,000 lines of code.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Compared to the 600,000 lines of code of OpenVPN + OpenSSL or the 400,000 lines of code
for XFRM+StrongSwan for an IPSEC VPN (Jim Salter, 2018).
So far, this new protocol (Wireguard) has been released for Linux, Android and iOS based
devices, although the developers warn anyone willing to install it, that this protocol is still
under development. Versions for Windows clients have not been released yet.
This is a significant challenge for making these services available for everyone as windows is
still the dominant and most preferred OS that is considered by most of the enterprises
(Schurgot, Shinberg and Greenwald 2015). However, in terms of flexibility and security,
developers and security experts often prefer Linux. Hence, the authors also suggest
considering Linux for better software options and customization, which is required when
designing security solutions for IOT devices, where resource constraint is an important issue.
Other protocols like IPsec or SSL also use to have some disadvantages. For IPsec, it was
noted that existing implementations were hardly compatible with each other and often
required some manual configuration. It was also stated that most IPsec solutions for setting up a
VPN required third-party hardware and/or software and on top of that, in order to access an IPsec
VPN, a given endpoint must had an IPsec client application installed (Chang et al. 2015).
In regards to SSL, almost every device in the world was equipped with the necessary software to
connect to a SSL VPN. This protocol would allow more precise access control (Shif et al. 2018).
In fact, operation at the transport layer would allow VPN tunnels to be allocated to specific
applications rather to an specific machine (or often to an entire LAN). This way, users on SSL
VPN connections can only access the applications that they are configured to access rather than
an entire network.
In an IoT environment, devices are often targeted due to the ease of exploiting these devices.
Hence, securing devices in an IoT environment is an important criterion. IoT devices often do not
integrate standard security protocols, which makes these vulnerable. Distributed denial of
services or DDoS is an important security threat for IoT network. As IoT devices do not have
standard protection of antivirus software due to the limitation in device architecture (Bonetto et
al. 2012). Hence, protection at the network level is required and this is where VPN has an
important role in securing IoT devices as it provides encryption of data that is communicated over
a network through these devices. As data is encrypted, it enhances the security of the system at
this makes it difficult for others to access this data without proper authorization.
When data is sent from particular IoT devices, it does not instantly send to the destination
devices. During this season, it is possible to interpret this data if it is not secured with proper
security measures. One recommended process that is suggested by this article is to ensure data
encryption throughout this entire season of data transfer. When an IoT device is connected with a
VPN network, each traffic that comes in and goes out of this device is secured and encrypted.
Hence, according to the authors, even if someone makes a try to interpret traffic of network, it is
not virtually possible for them.
Although IoT devices are secured when the network is connected with a VPN, it requires
effective configuration. Without the proper configuration of the IoT network with VPN, it is not
possible to ensure proper security that it offers. Hence, proper configuration according to the
authors is an important requirement when considering VPN for securing IoT devices with this
technology (Kuusijärvi et al. 2016). The authors have suggested a desktop client for managing
this configuration. The reason as suggested in the article is that it is easy to use and effective as
well.
For connecting the IoT network with VPN, the authors have suggested for VPN router. I fact the
authors have not recommended desktop client for this purpose as according to the authors desktop
clients have own set limitation and it often oversimplifies the configuration that affects the
4
for XFRM+StrongSwan for an IPSEC VPN (Jim Salter, 2018).
So far, this new protocol (Wireguard) has been released for Linux, Android and iOS based
devices, although the developers warn anyone willing to install it, that this protocol is still
under development. Versions for Windows clients have not been released yet.
This is a significant challenge for making these services available for everyone as windows is
still the dominant and most preferred OS that is considered by most of the enterprises
(Schurgot, Shinberg and Greenwald 2015). However, in terms of flexibility and security,
developers and security experts often prefer Linux. Hence, the authors also suggest
considering Linux for better software options and customization, which is required when
designing security solutions for IOT devices, where resource constraint is an important issue.
Other protocols like IPsec or SSL also use to have some disadvantages. For IPsec, it was
noted that existing implementations were hardly compatible with each other and often
required some manual configuration. It was also stated that most IPsec solutions for setting up a
VPN required third-party hardware and/or software and on top of that, in order to access an IPsec
VPN, a given endpoint must had an IPsec client application installed (Chang et al. 2015).
In regards to SSL, almost every device in the world was equipped with the necessary software to
connect to a SSL VPN. This protocol would allow more precise access control (Shif et al. 2018).
In fact, operation at the transport layer would allow VPN tunnels to be allocated to specific
applications rather to an specific machine (or often to an entire LAN). This way, users on SSL
VPN connections can only access the applications that they are configured to access rather than
an entire network.
In an IoT environment, devices are often targeted due to the ease of exploiting these devices.
Hence, securing devices in an IoT environment is an important criterion. IoT devices often do not
integrate standard security protocols, which makes these vulnerable. Distributed denial of
services or DDoS is an important security threat for IoT network. As IoT devices do not have
standard protection of antivirus software due to the limitation in device architecture (Bonetto et
al. 2012). Hence, protection at the network level is required and this is where VPN has an
important role in securing IoT devices as it provides encryption of data that is communicated over
a network through these devices. As data is encrypted, it enhances the security of the system at
this makes it difficult for others to access this data without proper authorization.
When data is sent from particular IoT devices, it does not instantly send to the destination
devices. During this season, it is possible to interpret this data if it is not secured with proper
security measures. One recommended process that is suggested by this article is to ensure data
encryption throughout this entire season of data transfer. When an IoT device is connected with a
VPN network, each traffic that comes in and goes out of this device is secured and encrypted.
Hence, according to the authors, even if someone makes a try to interpret traffic of network, it is
not virtually possible for them.
Although IoT devices are secured when the network is connected with a VPN, it requires
effective configuration. Without the proper configuration of the IoT network with VPN, it is not
possible to ensure proper security that it offers. Hence, proper configuration according to the
authors is an important requirement when considering VPN for securing IoT devices with this
technology (Kuusijärvi et al. 2016). The authors have suggested a desktop client for managing
this configuration. The reason as suggested in the article is that it is easy to use and effective as
well.
For connecting the IoT network with VPN, the authors have suggested for VPN router. I fact the
authors have not recommended desktop client for this purpose as according to the authors desktop
clients have own set limitation and it often oversimplifies the configuration that affects the
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

security of VPN. One of the main benefits of connecting the IoT network through the VPN router
is that only configuration of the router with VPN is required. Every devices that are connected to
the network through this router is secured and protection of VPN id ensured for each device.
Hence this effective and cost-effective solution.
Although VPN router provides a way and cost-effective solution for IoT device configuration
with the network, the security of the devices is still dependent on the VPN service provider. Now
the organisation might find it difficult to select the appropriate vendor for VPN service, but the
organisation should always choose a VPN service provider based on their popularity in the
market and expertise in this field.
Some VPN service provider tracks the IP address of their client, which includes destination IP
address too. This means that such vendors have complete knowledge of client activity and this
information might be shared to third parties without the permission of the client. This will
definitely affect the security of the IoT devices. Hence, the authors suggest checking if VPN
providers have a strict measure regarding no-logs policy (Xu et al. 2014). If the vendor does not
ensure this, who is providing VPN services, it is better to avoid that vendor. Otherwise, there will
be an issue in securing these devices because when service provider compromise in security it is
extremely difficult to ensure security for these devices.
As IoT devices are still not standardized, security for these devices lacks proper infrastructure,
which makes the security of these devices a complex process to manage properly. As IoT devices
are being implemented into the various application from smart cart to smart city, challenges of
security are even significant and innovation is the only way to develop a robust and secured
infrastructure to deploy IoT devices properly for implementing various smart applications that
increased productivity and efficiency various activities in which these applications are considered
(Kharchenko et al. 2016). VPN might be considered as an effective solution as of now, but as
sophisticated procedures are being applied for cybercrime, it is also required to increase the
security of VPN devices.
There are various advantages of VPN. It helps to restrict illegal access to the network, which is
the first process to hack a network and illegally access network data (Jha and Sunil 2014).
Another advantage of VPN is that it is cost effective which is a major requirement, especially
when considering security applications in an organizational context.However, while selecting a
VPN for IoT security, it is important to analyze various drawbacks that are associated with this
technology. Although encryption of VPN provides security to IoT devices, it slows the rate of
data transfer over the network, which is a significant drawback of this technology. When there is
high traffic on the network, service is affected and the reliability of the system becomes an issue.
However, SSL technology only works for Web-based applications so they do not always provide
native access to all network resources (Ricardo Bonetto, Nicola Bui, Vishwas Lakkundi, Alexis
Olivereau, Alexandru Serbanati, Michele Rossi, 2012).These two protocols are widely used
nowadays on VPN services, but the amount of configuration and resources that both of them
require, may make them not suitable for resource-constrained devices.
In conclusion, IoT devices are being integrated into our lives as technology progresses. The
need for data protection on these devices is becoming a larger concern as the devices are
handling increasing amounts of sensitive data which could conflict with user privacy (Ali
and Ali 2018). Because of the low computational and storage power that these devices have,
WireGuard could be considered as the best available option for the near future. The protocol
follows the philosophy ‘the simpler, the better: simple public keys, simple network interface,
simple configuration, etc’. The contrast between WireGuard, OpenVPN/IPsec and Tinc is
really noticeable when it comes to high-resource hardware tests. Further testing needs to be
done to conclude how they might perform under low-resource hardware devices. However
the literature available about VPN services used in IoT devices is somewhat limited due to
the fact that the technology evolves quicker than the publishing of papers.
5
is that only configuration of the router with VPN is required. Every devices that are connected to
the network through this router is secured and protection of VPN id ensured for each device.
Hence this effective and cost-effective solution.
Although VPN router provides a way and cost-effective solution for IoT device configuration
with the network, the security of the devices is still dependent on the VPN service provider. Now
the organisation might find it difficult to select the appropriate vendor for VPN service, but the
organisation should always choose a VPN service provider based on their popularity in the
market and expertise in this field.
Some VPN service provider tracks the IP address of their client, which includes destination IP
address too. This means that such vendors have complete knowledge of client activity and this
information might be shared to third parties without the permission of the client. This will
definitely affect the security of the IoT devices. Hence, the authors suggest checking if VPN
providers have a strict measure regarding no-logs policy (Xu et al. 2014). If the vendor does not
ensure this, who is providing VPN services, it is better to avoid that vendor. Otherwise, there will
be an issue in securing these devices because when service provider compromise in security it is
extremely difficult to ensure security for these devices.
As IoT devices are still not standardized, security for these devices lacks proper infrastructure,
which makes the security of these devices a complex process to manage properly. As IoT devices
are being implemented into the various application from smart cart to smart city, challenges of
security are even significant and innovation is the only way to develop a robust and secured
infrastructure to deploy IoT devices properly for implementing various smart applications that
increased productivity and efficiency various activities in which these applications are considered
(Kharchenko et al. 2016). VPN might be considered as an effective solution as of now, but as
sophisticated procedures are being applied for cybercrime, it is also required to increase the
security of VPN devices.
There are various advantages of VPN. It helps to restrict illegal access to the network, which is
the first process to hack a network and illegally access network data (Jha and Sunil 2014).
Another advantage of VPN is that it is cost effective which is a major requirement, especially
when considering security applications in an organizational context.However, while selecting a
VPN for IoT security, it is important to analyze various drawbacks that are associated with this
technology. Although encryption of VPN provides security to IoT devices, it slows the rate of
data transfer over the network, which is a significant drawback of this technology. When there is
high traffic on the network, service is affected and the reliability of the system becomes an issue.
However, SSL technology only works for Web-based applications so they do not always provide
native access to all network resources (Ricardo Bonetto, Nicola Bui, Vishwas Lakkundi, Alexis
Olivereau, Alexandru Serbanati, Michele Rossi, 2012).These two protocols are widely used
nowadays on VPN services, but the amount of configuration and resources that both of them
require, may make them not suitable for resource-constrained devices.
In conclusion, IoT devices are being integrated into our lives as technology progresses. The
need for data protection on these devices is becoming a larger concern as the devices are
handling increasing amounts of sensitive data which could conflict with user privacy (Ali
and Ali 2018). Because of the low computational and storage power that these devices have,
WireGuard could be considered as the best available option for the near future. The protocol
follows the philosophy ‘the simpler, the better: simple public keys, simple network interface,
simple configuration, etc’. The contrast between WireGuard, OpenVPN/IPsec and Tinc is
really noticeable when it comes to high-resource hardware tests. Further testing needs to be
done to conclude how they might perform under low-resource hardware devices. However
the literature available about VPN services used in IoT devices is somewhat limited due to
the fact that the technology evolves quicker than the publishing of papers.
5

6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Research Aims and Research Questions
We are trying to find out whether WireGuard can be the next standard protocol for VPN
connections as it is a lighter protocol than the actual standard ones so it would not require as
much resources as the ones which are now being used.
- Is Wireguard actually able to reduce the resource consumption on devices it has been
implemented on in VPN connections?
- Is there a considerable difference in the performance of these protocols when
hardware isn’t a factor?
- What metrics are relevant to testing ones performance?
- How heavily does hardware throttling affect a VPNs performance?
- Are there any VPN solutions that are viable solutions to be placed on IoT devices?
Research Design
Overview
The research will be carried out using Microsoft Azure to facilitate the hosting of all the VPN
products’ servers. This provides a consistent, cloud based, target that won't be subject to
NAT, bandwidth shaping and other networking features that can skew the results of our tests.
But will also be far enough away, to provide usable results. The clients that we will use are
the Murdoch university lab computers as they have overly strong hardware and networking
facilities for the tests that we will be performing. The overperforming hardware allows for
any bottlenecks in the protocols to not be misconstrued as hardware limitations.
Hardware Requirements
The main physical requirement, to perform reasonable testing, is the geographic separation of
the clients and servers. This provides us with testing results that are not so small, that
comparisons will not be able to be made. The computers that will be used to run both servers
and clients, need to be over specd to not allow any bottlenecks that could hinder the results.
This allows us to test the protocols as fairly as possible as some VPN product requirements
are higher than others. After testing the protocols we will then test how well they perform in a
low resource device. This will be done at first with the use of throttling certain hardware
(CPU, RAM, etc) to simulate low resource IoT devices. After we have tested the protocols
and have true test data, we will then throttle the hardware to simulate low resource IoT
devices. This allows us to test how well different VPN products are able to deal with low
resources, as well as testing to see if those VPNs can even run on the hardware.
Another physical requirement for the stretch goal of testing these vpn technologies on
raspberry pies. This would allow for testing to be performed on the most similar hardware to
IoT devices. But this is a stretch goal and the likelihood of implementing this testing needs to
be evaluated at a later date.
7
We are trying to find out whether WireGuard can be the next standard protocol for VPN
connections as it is a lighter protocol than the actual standard ones so it would not require as
much resources as the ones which are now being used.
- Is Wireguard actually able to reduce the resource consumption on devices it has been
implemented on in VPN connections?
- Is there a considerable difference in the performance of these protocols when
hardware isn’t a factor?
- What metrics are relevant to testing ones performance?
- How heavily does hardware throttling affect a VPNs performance?
- Are there any VPN solutions that are viable solutions to be placed on IoT devices?
Research Design
Overview
The research will be carried out using Microsoft Azure to facilitate the hosting of all the VPN
products’ servers. This provides a consistent, cloud based, target that won't be subject to
NAT, bandwidth shaping and other networking features that can skew the results of our tests.
But will also be far enough away, to provide usable results. The clients that we will use are
the Murdoch university lab computers as they have overly strong hardware and networking
facilities for the tests that we will be performing. The overperforming hardware allows for
any bottlenecks in the protocols to not be misconstrued as hardware limitations.
Hardware Requirements
The main physical requirement, to perform reasonable testing, is the geographic separation of
the clients and servers. This provides us with testing results that are not so small, that
comparisons will not be able to be made. The computers that will be used to run both servers
and clients, need to be over specd to not allow any bottlenecks that could hinder the results.
This allows us to test the protocols as fairly as possible as some VPN product requirements
are higher than others. After testing the protocols we will then test how well they perform in a
low resource device. This will be done at first with the use of throttling certain hardware
(CPU, RAM, etc) to simulate low resource IoT devices. After we have tested the protocols
and have true test data, we will then throttle the hardware to simulate low resource IoT
devices. This allows us to test how well different VPN products are able to deal with low
resources, as well as testing to see if those VPNs can even run on the hardware.
Another physical requirement for the stretch goal of testing these vpn technologies on
raspberry pies. This would allow for testing to be performed on the most similar hardware to
IoT devices. But this is a stretch goal and the likelihood of implementing this testing needs to
be evaluated at a later date.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Software Requirements
The primary software requirements to this project is the use of these VPN products.We will
be mainly testing Wireguard, OpenVPN and Tinc, with regards to time constraints. As most
of these products are free or have free versions available to the public, getting this software is
no challenge.
Due to wireguard being only supported on linux, we shall be testing all of these products on a
linux distribution. As most group members will be installing these servers to get familiar with
the products. No specific distribution has been chosen, as the differences in the distributions
can be another performance metric as well as create a check as to if the distribution is
throttling the protocol.
Special Resources Required
Microsoft Azure will be required to perform these tests, as it provides us with the ability to
host our servers in the cloud. This allows us to have response times that are more realistic and
not so small that you cannot give a comparison. As Microsoft Azure is proprietary, we will
have to pay for this service. But because we are registered students at Murdoch University,
we will have $30 of credit per person. The pricing of VMs on Azure range from $0.011/hour
to $0.173, which makes the $30 credit last about a month. Which provides plenty of testing
time.
The last special resource, which is for the stretch goal, is the use of a raspberry pie. This
allows us to test the protocols on specific hardware that is the closest to IoT devices. They
will be resourced through Dr David Murray (Supervisor) but this is however a stretch goal
and will be determined with time and how well the testing on Azure goes.
Data Collection
The methods of data collection as well as the data that we will collecting will likely change.
This is due to how difficult it is to provide a one-to-one comparison of these VPN products.
As some use different protocols, more or less extra features and even the code/runtime being
able to be optimized in a short period of time. Due to all of these variables the methods and
tools, that will be utilized to collect data, will be subject to change.
The nature of the data collected will be performance metrics of the servers and clients as the
connections are made and data is transferred. The two initial baseline metrics will be the
initial connection response time as well as throughput that each protocol can provide. These
tests will be performed with hardware that has an abundance of resources available to them.
After this we will look at hardware utilization, CPU cycles and other metrics.Finally, with
each VPNs’ baseline performance maped, we will then test how low resource hardware
affects each protocols performance. Some of the questions we hope to answer are. Is there a
considerable difference in the performance of these protocols when hardware isn’t a factor?
What metrics are relevant to testing ones performance? How heavily does hardware throttling
affect a VPNs performance? Are there any VPN solutions that are viable solutions to be
placed on IoT devices?
8
The primary software requirements to this project is the use of these VPN products.We will
be mainly testing Wireguard, OpenVPN and Tinc, with regards to time constraints. As most
of these products are free or have free versions available to the public, getting this software is
no challenge.
Due to wireguard being only supported on linux, we shall be testing all of these products on a
linux distribution. As most group members will be installing these servers to get familiar with
the products. No specific distribution has been chosen, as the differences in the distributions
can be another performance metric as well as create a check as to if the distribution is
throttling the protocol.
Special Resources Required
Microsoft Azure will be required to perform these tests, as it provides us with the ability to
host our servers in the cloud. This allows us to have response times that are more realistic and
not so small that you cannot give a comparison. As Microsoft Azure is proprietary, we will
have to pay for this service. But because we are registered students at Murdoch University,
we will have $30 of credit per person. The pricing of VMs on Azure range from $0.011/hour
to $0.173, which makes the $30 credit last about a month. Which provides plenty of testing
time.
The last special resource, which is for the stretch goal, is the use of a raspberry pie. This
allows us to test the protocols on specific hardware that is the closest to IoT devices. They
will be resourced through Dr David Murray (Supervisor) but this is however a stretch goal
and will be determined with time and how well the testing on Azure goes.
Data Collection
The methods of data collection as well as the data that we will collecting will likely change.
This is due to how difficult it is to provide a one-to-one comparison of these VPN products.
As some use different protocols, more or less extra features and even the code/runtime being
able to be optimized in a short period of time. Due to all of these variables the methods and
tools, that will be utilized to collect data, will be subject to change.
The nature of the data collected will be performance metrics of the servers and clients as the
connections are made and data is transferred. The two initial baseline metrics will be the
initial connection response time as well as throughput that each protocol can provide. These
tests will be performed with hardware that has an abundance of resources available to them.
After this we will look at hardware utilization, CPU cycles and other metrics.Finally, with
each VPNs’ baseline performance maped, we will then test how low resource hardware
affects each protocols performance. Some of the questions we hope to answer are. Is there a
considerable difference in the performance of these protocols when hardware isn’t a factor?
What metrics are relevant to testing ones performance? How heavily does hardware throttling
affect a VPNs performance? Are there any VPN solutions that are viable solutions to be
placed on IoT devices?
8
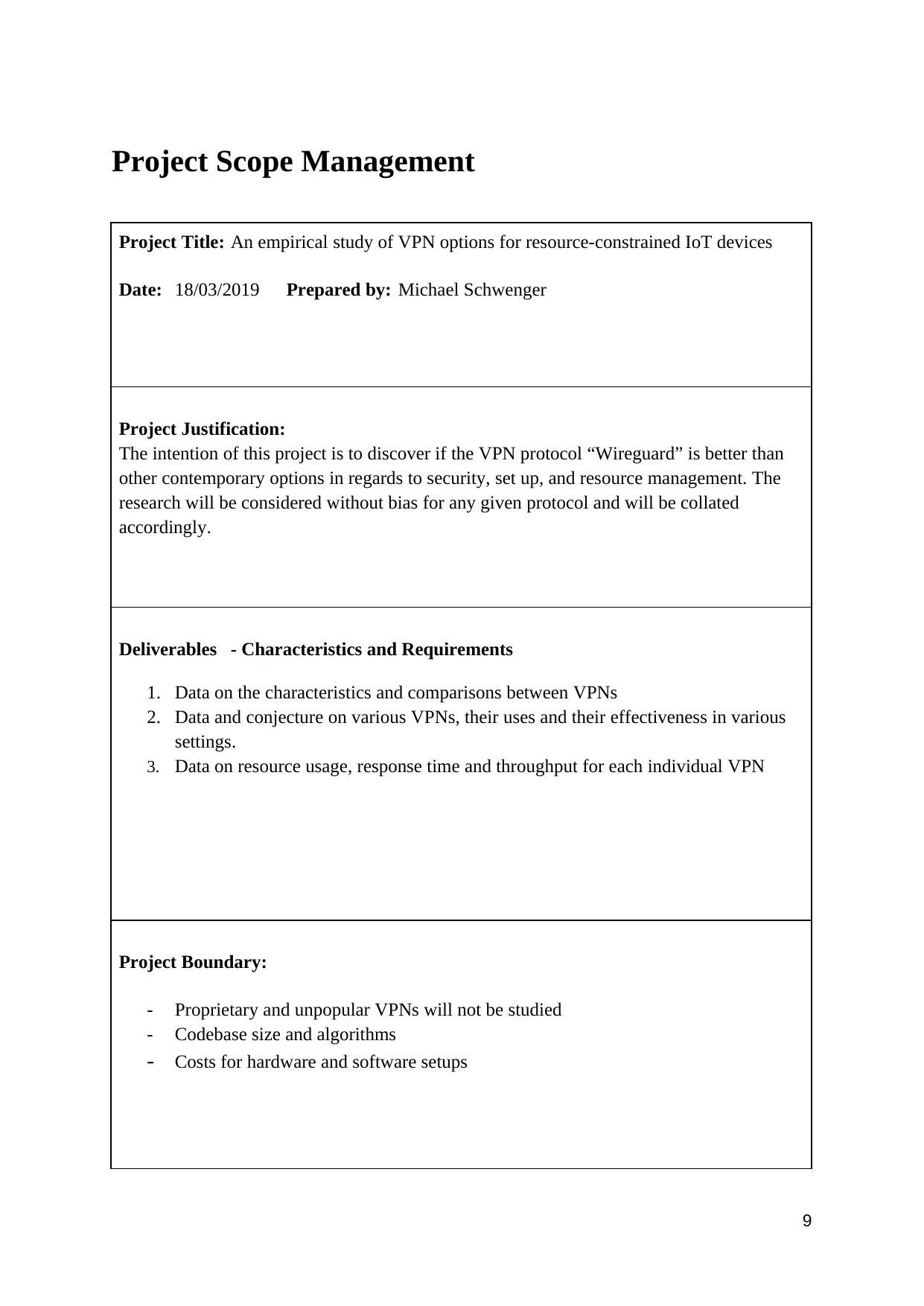
Project Scope Management
Project Title: An empirical study of VPN options for resource-constrained IoT devices
Date: 18/03/2019 Prepared by: Michael Schwenger
Project Justification:
The intention of this project is to discover if the VPN protocol “Wireguard” is better than
other contemporary options in regards to security, set up, and resource management. The
research will be considered without bias for any given protocol and will be collated
accordingly.
Deliverables - Characteristics and Requirements
1. Data on the characteristics and comparisons between VPNs
2. Data and conjecture on various VPNs, their uses and their effectiveness in various
settings.
3. Data on resource usage, response time and throughput for each individual VPN
Project Boundary:
- Proprietary and unpopular VPNs will not be studied
- Codebase size and algorithms
- Costs for hardware and software setups
9
Project Title: An empirical study of VPN options for resource-constrained IoT devices
Date: 18/03/2019 Prepared by: Michael Schwenger
Project Justification:
The intention of this project is to discover if the VPN protocol “Wireguard” is better than
other contemporary options in regards to security, set up, and resource management. The
research will be considered without bias for any given protocol and will be collated
accordingly.
Deliverables - Characteristics and Requirements
1. Data on the characteristics and comparisons between VPNs
2. Data and conjecture on various VPNs, their uses and their effectiveness in various
settings.
3. Data on resource usage, response time and throughput for each individual VPN
Project Boundary:
- Proprietary and unpopular VPNs will not be studied
- Codebase size and algorithms
- Costs for hardware and software setups
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Constraints and Assumptions:
- We are constrained by hardware and software limits on student budgets
- We can not use VPNs that cost money or are outside of our capabilities to
effectively use and test
10
- We are constrained by hardware and software limits on student budgets
- We can not use VPNs that cost money or are outside of our capabilities to
effectively use and test
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
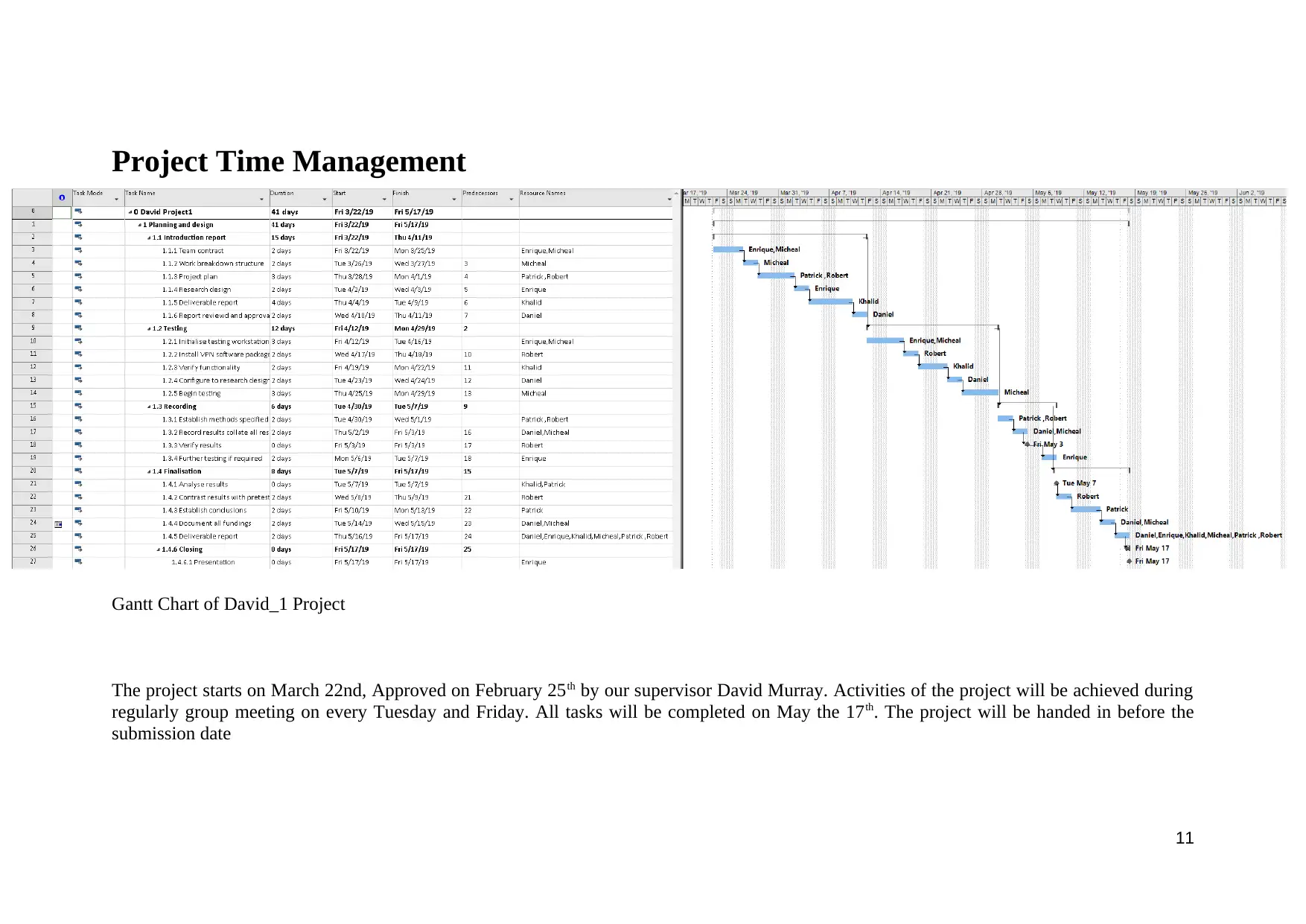
Project Time Management
Gantt Chart of David_1 Project
The project starts on March 22nd, Approved on February 25th by our supervisor David Murray. Activities of the project will be achieved during
regularly group meeting on every Tuesday and Friday. All tasks will be completed on May the 17th. The project will be handed in before the
submission date
11
Gantt Chart of David_1 Project
The project starts on March 22nd, Approved on February 25th by our supervisor David Murray. Activities of the project will be achieved during
regularly group meeting on every Tuesday and Friday. All tasks will be completed on May the 17th. The project will be handed in before the
submission date
11
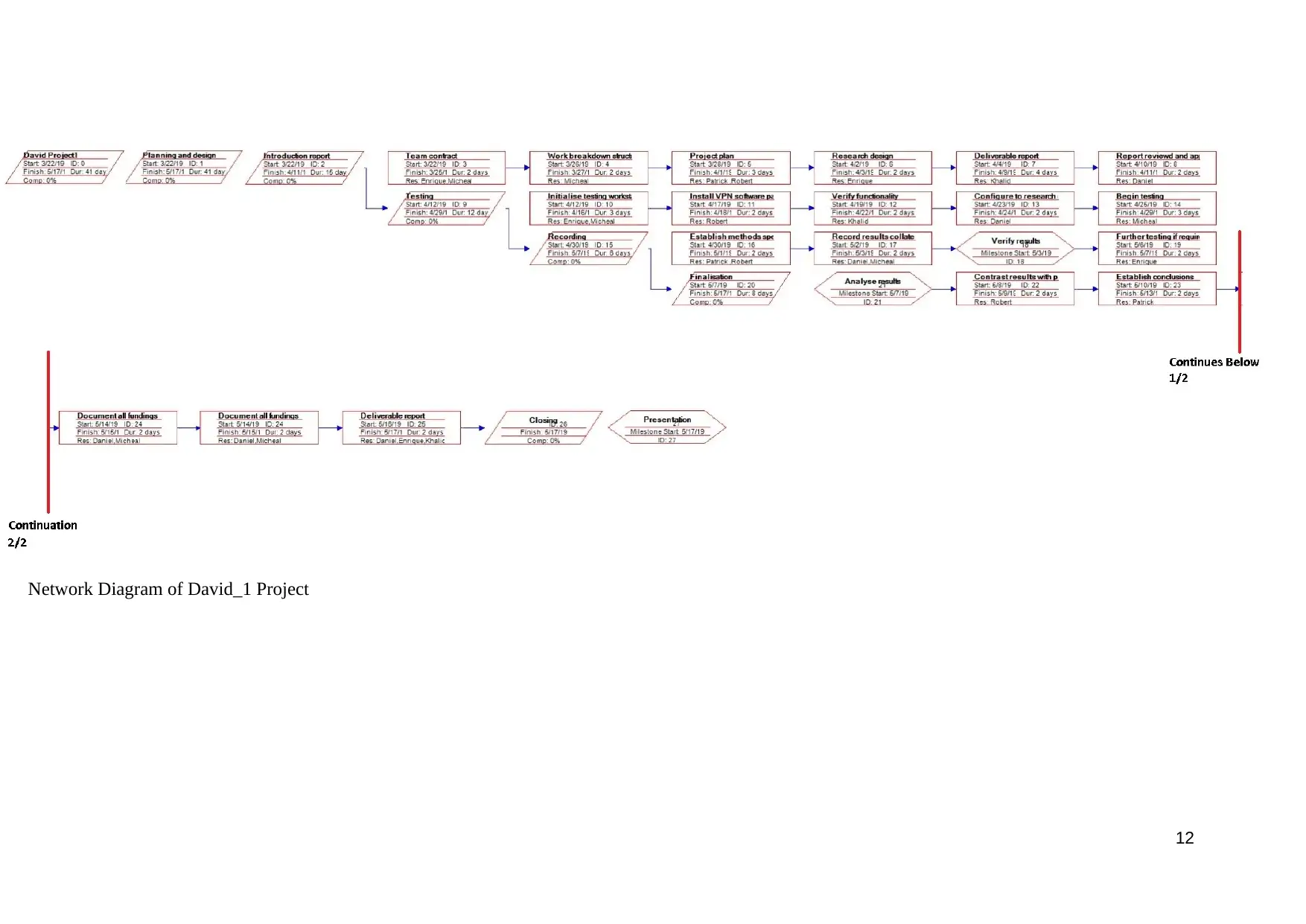
Network Diagram of David_1 Project
12
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





