Assignment on Analysis of Protocols with Wireshark
VerifiedAdded on 2022/09/25
|8
|1194
|17
Assignment
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: COIT20262
COIT20262
Name of the Student
Name of the University
Author Note
COIT20262
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
1COIT20262
Question 1. Analysis of Protocols with Wireshark
Part (a)
Netcat.pcap file submitted on Moodle. These are not included in this report
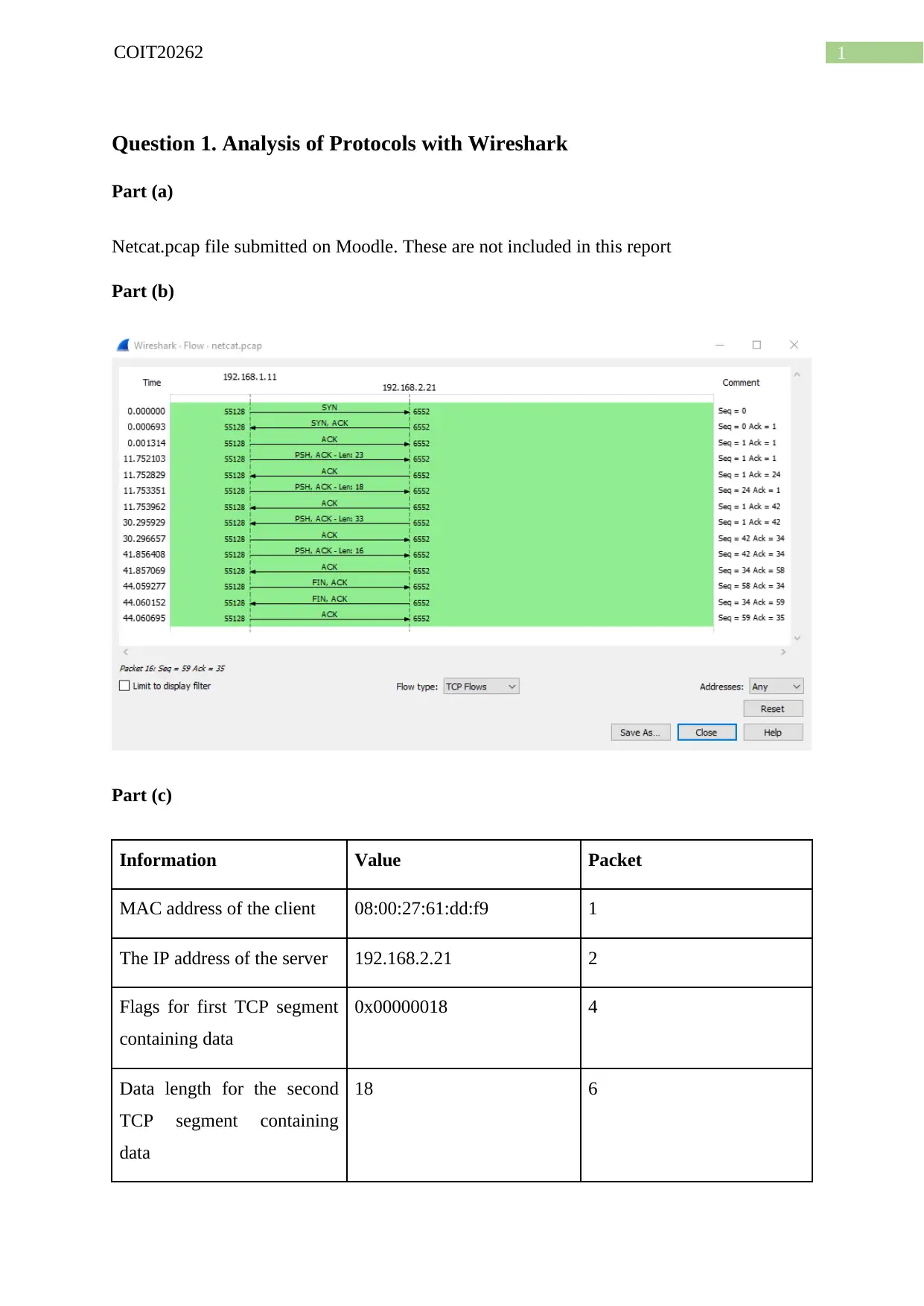
Part (b)
Part (c)
Information Value Packet
MAC address of the client 08:00:27:61:dd:f9 1
The IP address of the server 192.168.2.21 2
Flags for first TCP segment
containing data
0x00000018 4
Data length for the second
TCP segment containing
data
18 6
Question 1. Analysis of Protocols with Wireshark
Part (a)
Netcat.pcap file submitted on Moodle. These are not included in this report
Part (b)
Part (c)
Information Value Packet
MAC address of the client 08:00:27:61:dd:f9 1
The IP address of the server 192.168.2.21 2
Flags for first TCP segment
containing data
0x00000018 4
Data length for the second
TCP segment containing
data
18 6

2COIT20262
Absolute sequence number
of 1st TCP segment sent by
server that contains data
1 8
Question 2. Web Application Attacks
Part (a)
SQL injection is a weakness of web security that permits an attacker to obstruct with the
queries that an application makes to the databases. It usually permits an attacker to see the
data that they cannot recover. This can consists of data belonging to other users.
Part (b)
The two ways by which SQL injection can be mitigated are as follows:
Firewall: A web application firewall can be implemented in order to filter the data those
are malicious. Good firewalls will have a sequence of regulations and rules and it is easier
to add new rules whenever required. A web application firewall can useful to give some
protection against weaknesses before patching is done
Use of proper privileges: the database should not be connected using an admin level
privilege. Utilising a restricted access account is safer and it can restrict the hacker to
attack using a SQL injection
Part (c)
The SQL injection is possible for the website because of poor programming of the developer
who developed the website. The website permits SQL injection and it is usually carried out
by setting a demo system of grading. It is created in SQL for permitting SQL injection attack.
Absolute sequence number
of 1st TCP segment sent by
server that contains data
1 8
Question 2. Web Application Attacks
Part (a)
SQL injection is a weakness of web security that permits an attacker to obstruct with the
queries that an application makes to the databases. It usually permits an attacker to see the
data that they cannot recover. This can consists of data belonging to other users.
Part (b)
The two ways by which SQL injection can be mitigated are as follows:
Firewall: A web application firewall can be implemented in order to filter the data those
are malicious. Good firewalls will have a sequence of regulations and rules and it is easier
to add new rules whenever required. A web application firewall can useful to give some
protection against weaknesses before patching is done
Use of proper privileges: the database should not be connected using an admin level
privilege. Utilising a restricted access account is safer and it can restrict the hacker to
attack using a SQL injection
Part (c)
The SQL injection is possible for the website because of poor programming of the developer
who developed the website. The website permits SQL injection and it is usually carried out
by setting a demo system of grading. It is created in SQL for permitting SQL injection attack.
3COIT20262
If the website is logged-in as student, the attack can be carried out in order to see the grades
and the subject of other students by utilising a query of SQL.
Part (d)
The attacker with the username [12037777] has to login into his account that is developed in
the database. In order to see the grades of other students, the attacker have to put the script to
“its335' OR '1'='1” in place of code of the course and then the website will return all the
codes and the grades of the students.
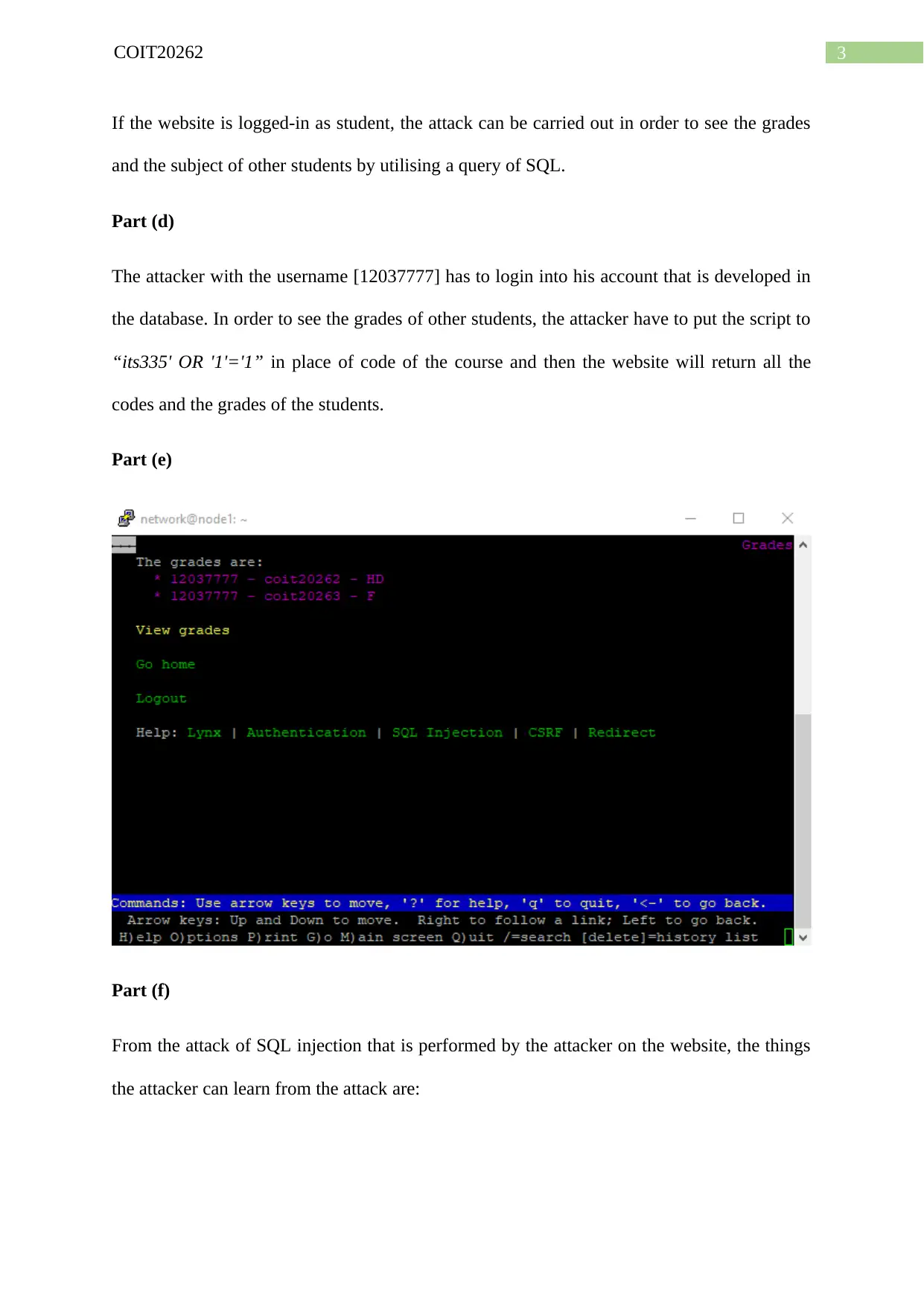
Part (e)
Part (f)
From the attack of SQL injection that is performed by the attacker on the website, the things
the attacker can learn from the attack are:
If the website is logged-in as student, the attack can be carried out in order to see the grades
and the subject of other students by utilising a query of SQL.
Part (d)
The attacker with the username [12037777] has to login into his account that is developed in
the database. In order to see the grades of other students, the attacker have to put the script to
“its335' OR '1'='1” in place of code of the course and then the website will return all the
codes and the grades of the students.
Part (e)
Part (f)
From the attack of SQL injection that is performed by the attacker on the website, the things
the attacker can learn from the attack are:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4COIT20262
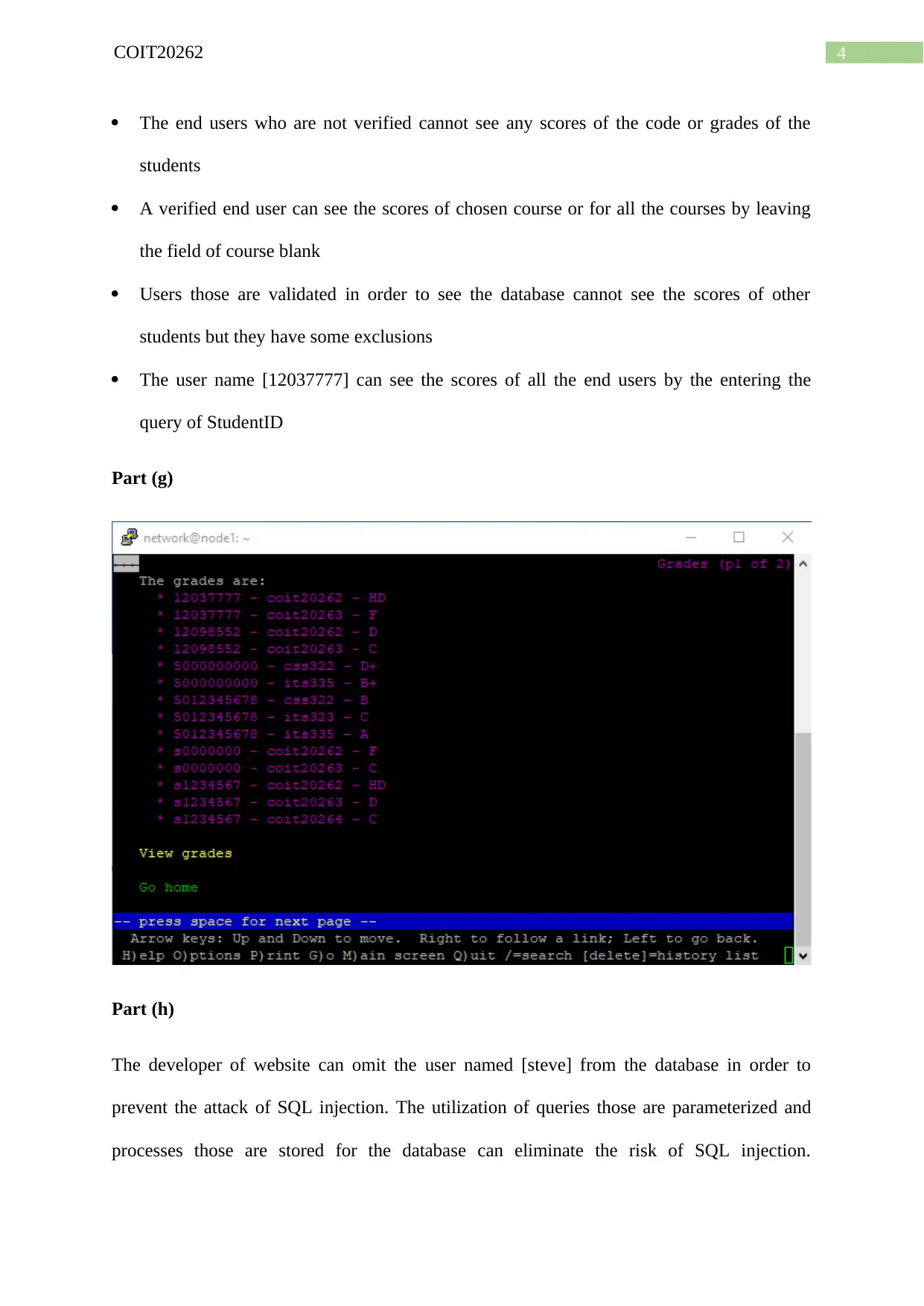
The end users who are not verified cannot see any scores of the code or grades of the
students
A verified end user can see the scores of chosen course or for all the courses by leaving
the field of course blank
Users those are validated in order to see the database cannot see the scores of other
students but they have some exclusions
The user name [12037777] can see the scores of all the end users by the entering the
query of StudentID
Part (g)
Part (h)
The developer of website can omit the user named [steve] from the database in order to
prevent the attack of SQL injection. The utilization of queries those are parameterized and
processes those are stored for the database can eliminate the risk of SQL injection.
The end users who are not verified cannot see any scores of the code or grades of the
students
A verified end user can see the scores of chosen course or for all the courses by leaving
the field of course blank
Users those are validated in order to see the database cannot see the scores of other
students but they have some exclusions
The user name [12037777] can see the scores of all the end users by the entering the
query of StudentID
Part (g)
Part (h)
The developer of website can omit the user named [steve] from the database in order to
prevent the attack of SQL injection. The utilization of queries those are parameterized and
processes those are stored for the database can eliminate the risk of SQL injection.

5COIT20262
Appropriate privileges are important as it can restrict the access of the hackers. The access to
the website must be limited.
Question 3. Cryptography Concepts
Part (a)
The algorithm is weak against the attack of brute force as it has keys those are weak, the size
of block is of 64 bits, and that is small. The algorithm can be easily cracked as the algorithm
has short keys
Part (b)
In order to overcome the problem of the algorithm, the algorithm can be applied three times
for every block of data. The size of key of the cipher of the algorithm is 56 bits and the
increase in the power of computation has led to the attack of brute force (Nisbet and Kim
2016). The use of algorithm 3 times can maximize the size of key and safeguard against the
attack of brute force and there is no requirement in order to design a new algorithm of block
cipher
Question 4. Network Attacks Research
Part (a)
The artificial intelligence attacks are caused due to algorithms of artificial intelligence and
they are different from the traditional cyber attacks that utilise bugs. Utilising the artificial
intelligence attack, the attackers can manipulate the systems to modify their behaviour in
order to serve a goal those are malicious (Khurana et al 2019). There are five areas those are
affected by the AI attacks consisting of content filters, enforcement of law, military, civil
society and the task those are based on humans.
Part (b)
Appropriate privileges are important as it can restrict the access of the hackers. The access to
the website must be limited.
Question 3. Cryptography Concepts
Part (a)
The algorithm is weak against the attack of brute force as it has keys those are weak, the size
of block is of 64 bits, and that is small. The algorithm can be easily cracked as the algorithm
has short keys
Part (b)
In order to overcome the problem of the algorithm, the algorithm can be applied three times
for every block of data. The size of key of the cipher of the algorithm is 56 bits and the
increase in the power of computation has led to the attack of brute force (Nisbet and Kim
2016). The use of algorithm 3 times can maximize the size of key and safeguard against the
attack of brute force and there is no requirement in order to design a new algorithm of block
cipher
Question 4. Network Attacks Research
Part (a)
The artificial intelligence attacks are caused due to algorithms of artificial intelligence and
they are different from the traditional cyber attacks that utilise bugs. Utilising the artificial
intelligence attack, the attackers can manipulate the systems to modify their behaviour in
order to serve a goal those are malicious (Khurana et al 2019). There are five areas those are
affected by the AI attacks consisting of content filters, enforcement of law, military, civil
society and the task those are based on humans.
Part (b)

6COIT20262
The three examples of AI based network attacks are as follows:
TaskRabbit: The marketplace that is used by the labourers and clients faced a huge cyber
breach in the month of April. The hackers attacked the website and the investigation was
unable to trace them. The data of the users was compromised including their numbers and
details of bank accounts.
Nokia: The IoT botnet was responsible for malware infections in Nokia. It was found that
malware has infected various systems of crypto-currency. The botnets of AI look for
weakness in devices and they exploit the devices in order to steal data from the devices
Instagram: The Instagram one of the popular social networking sites was attacked by AI
powered attacks. Various users were logged out of their accounts and the attackers changed
their personal information. In the month of November, a bug influenced Instagram and that
have led to breach in their data. The passwords of the users were compromised in this attack.
Part (c)
The strategies of defence that can be used for the prevention of AI attacks are as follows:
The AI attacks can be prevented by utilisation of various security tools
Deployment of configuration and restriction
The three examples of AI based network attacks are as follows:
TaskRabbit: The marketplace that is used by the labourers and clients faced a huge cyber
breach in the month of April. The hackers attacked the website and the investigation was
unable to trace them. The data of the users was compromised including their numbers and
details of bank accounts.
Nokia: The IoT botnet was responsible for malware infections in Nokia. It was found that
malware has infected various systems of crypto-currency. The botnets of AI look for
weakness in devices and they exploit the devices in order to steal data from the devices
Instagram: The Instagram one of the popular social networking sites was attacked by AI
powered attacks. Various users were logged out of their accounts and the attackers changed
their personal information. In the month of November, a bug influenced Instagram and that
have led to breach in their data. The passwords of the users were compromised in this attack.
Part (c)
The strategies of defence that can be used for the prevention of AI attacks are as follows:
The AI attacks can be prevented by utilisation of various security tools
Deployment of configuration and restriction
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7COIT20262
References
Nisbet, A. and Kim, M., 2016. An analysis of chosen alarm code pin numbers & their
weakness against a modified brute force attack.
Khurana, N., Mittal, S., Piplai, A. and Joshi, A., 2019, October. Preventing Poisoning Attacks
on AI based Threat Intelligence Systems. In 2019 IEEE 29th International Workshop on
Machine Learning for Signal Processing (MLSP) (pp. 1-6). IEEE.
References
Nisbet, A. and Kim, M., 2016. An analysis of chosen alarm code pin numbers & their
weakness against a modified brute force attack.
Khurana, N., Mittal, S., Piplai, A. and Joshi, A., 2019, October. Preventing Poisoning Attacks
on AI based Threat Intelligence Systems. In 2019 IEEE 29th International Workshop on
Machine Learning for Signal Processing (MLSP) (pp. 1-6). IEEE.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



