Security Analysis: Threats and Mitigation for CentOS Linux & Apache
VerifiedAdded on 2023/06/11
|21
|3232
|291
Report
AI Summary
This report provides a detailed security analysis of a textile industry's open-source HTTP server running Apache 2.0 on CentOS. It identifies key threats to the CentOS Linux server, including Apache version exposure, denial-of-service attacks, and unauthorized access to configuration files. The analysis extends to threats against the Apache web server, such as vulnerabilities exploited through tools like Nmap and Nessus, insider attacks, and liabilities related to SSH access and protocol versions. Mitigation strategies are proposed for each identified threat, including configuring firewall policies, implementing intrusion detection and prevention systems, and securing Apache web server configurations. The report also outlines a testing plan to validate the effectiveness of the implemented security measures, emphasizing the importance of proactive security measures to protect the system against potential cyberattacks. Desklib offers similar solved assignments and AI based study tools to help students.

Table of Contents
1. Design Analysis..................................................................................................................................2
2. Threats towards Centos Linux Server.............................................................................................4
3. Threats towards the Apache web servers........................................................................................7
4. Threats towards the network..........................................................................................................16
5. Firewall Policies and IPS / IDS Policies.........................................................................................18
6. Apache Web Server Configuration Summary...............................................................................19
7. Testing Plan......................................................................................................................................20
8. Conclusion........................................................................................................................................20
References................................................................................................................................................21
1
1. Design Analysis..................................................................................................................................2
2. Threats towards Centos Linux Server.............................................................................................4
3. Threats towards the Apache web servers........................................................................................7
4. Threats towards the network..........................................................................................................16
5. Firewall Policies and IPS / IDS Policies.........................................................................................18
6. Apache Web Server Configuration Summary...............................................................................19
7. Testing Plan......................................................................................................................................20
8. Conclusion........................................................................................................................................20
References................................................................................................................................................21
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Design Analysis
One textile industry named "Wear it on" recently launched the open source HTTP server.
That has the Apache 2.0 with Cent OS servers (Mallett, 2014). These process was done by the
trainee who doesn’t have the good sound of awareness on the network security and network
servers. While he testing the server he found that a TCP scanning performed. It was noticed after
the establishment of connection with internet. The report was all about the study of the
administration process carried out by the industry. Also the major threats for the Cent OS will be
recognized in this project. The reorganization only not enough, we have to take corrective
actions against the problem causes. Then only we can able to ensure the safety of the system
against threats.
ModSecurity is a web appilication firewall (Ristic, 2009) (Albanese and Sonnenreich,
2004) (Cole et al., 2009. This software was available as zero cost. Because it was open-source
software. During the initial stage of the product people can use this software for security purpose
with HTTP module. Because of its features which is expanded to almost all internet based
applications as well as software packages similar to NGINX, IIS etc. Huge no of developers are
there in the project development. But the same time a strict governing policies are formed for the
safety purpose. These policies are known as “Sec Rules”. This software was added in the web-
server as a plugin. Some situation this also used as a Proxy-server. This software consists of the
subsequent processes. They are listed below (Lockhart, 2004) (Knipp and Danielyan, 2002).
Monitor system security
Controlling the permission for assessing the system
Security testing purpose
Reorganization of the masking-server
Maintain the up-loading as well as down-loading size
HTTP security
Appraising system properties
2
One textile industry named "Wear it on" recently launched the open source HTTP server.
That has the Apache 2.0 with Cent OS servers (Mallett, 2014). These process was done by the
trainee who doesn’t have the good sound of awareness on the network security and network
servers. While he testing the server he found that a TCP scanning performed. It was noticed after
the establishment of connection with internet. The report was all about the study of the
administration process carried out by the industry. Also the major threats for the Cent OS will be
recognized in this project. The reorganization only not enough, we have to take corrective
actions against the problem causes. Then only we can able to ensure the safety of the system
against threats.
ModSecurity is a web appilication firewall (Ristic, 2009) (Albanese and Sonnenreich,
2004) (Cole et al., 2009. This software was available as zero cost. Because it was open-source
software. During the initial stage of the product people can use this software for security purpose
with HTTP module. Because of its features which is expanded to almost all internet based
applications as well as software packages similar to NGINX, IIS etc. Huge no of developers are
there in the project development. But the same time a strict governing policies are formed for the
safety purpose. These policies are known as “Sec Rules”. This software was added in the web-
server as a plugin. Some situation this also used as a Proxy-server. This software consists of the
subsequent processes. They are listed below (Lockhart, 2004) (Knipp and Danielyan, 2002).
Monitor system security
Controlling the permission for assessing the system
Security testing purpose
Reorganization of the masking-server
Maintain the up-loading as well as down-loading size
HTTP security
Appraising system properties
2

In networks it is essential to monitor the security and in the network it is consider as a
single part and it is used to gather the data and used to analyze them. And also it analyze the
attacks and make a safety for that networks.
In the system access control measurement is essential in the network and it had many
devices to the control and access to the system. And access network could be Ethernet and fiber
optic networks.
Security testing is used to describe about the tools for detect the vulnerable kind of
software. And in the testing the attitude of system has notified and positive things also explored
through this testing.
HTTP security is known as the secure concern of that rules and it use to add the
constraints for the security purpose. And it had additional letter as s and that seems to be the
meaning of security. If the security is not sure to provide the network but more webpages using
that protocol and it makes the text given by the user as plain text. And it is vary from normal
protocol and in that web pages analyze the messages through this protocol. And the system
security has their properties to make a process as perfectly.
The design setup is shown above. An apache based webserver is configured. Mod
security is installed in the webserver which can act as firewalls. Snort, Nessus and Fire starter are
installed. Honeyd also installed. The following IPs are selected.
1.Attacker (IP Address :192.168.1.2)
2.Web server(IP Address:192.168.1.1)
3.Honeyd(IP Address:192.168.100.100, alias:192.168.1.101, 192.168.1.102)
The threat analysis are done as follows.
3
single part and it is used to gather the data and used to analyze them. And also it analyze the
attacks and make a safety for that networks.
In the system access control measurement is essential in the network and it had many
devices to the control and access to the system. And access network could be Ethernet and fiber
optic networks.
Security testing is used to describe about the tools for detect the vulnerable kind of
software. And in the testing the attitude of system has notified and positive things also explored
through this testing.
HTTP security is known as the secure concern of that rules and it use to add the
constraints for the security purpose. And it had additional letter as s and that seems to be the
meaning of security. If the security is not sure to provide the network but more webpages using
that protocol and it makes the text given by the user as plain text. And it is vary from normal
protocol and in that web pages analyze the messages through this protocol. And the system
security has their properties to make a process as perfectly.
The design setup is shown above. An apache based webserver is configured. Mod
security is installed in the webserver which can act as firewalls. Snort, Nessus and Fire starter are
installed. Honeyd also installed. The following IPs are selected.
1.Attacker (IP Address :192.168.1.2)
2.Web server(IP Address:192.168.1.1)
3.Honeyd(IP Address:192.168.100.100, alias:192.168.1.101, 192.168.1.102)
The threat analysis are done as follows.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2. Threats towards Centos Linux Server
1.1 Apache version number
In the digital world the webservers easily attacked by the attackers. They simply hack the
server by the use of special codes. They do this activity when they know the details about the
apache of the webserver. Cyber-attacks are highly dangerous. Because these attacks are the
reason for the data stealing, etc. So we must protect the apache version details. So we should
disable the server-signature and token details. In the below figure the apache version details are
showed for the deep understanding. And in the below screenshot the server tokens and the details
are listed and these details according to the server as apache and that tokens such as major and
minor and kind of operating system. And the version of apache is notified in each terms and the
operating system may be the UNIX.
The following two lines should be added in apache2.conf and httpd.conf
ServerToens Prod
ServerSignature Off
1.2 Many connections
When the hacker sends lot of web requests the webserver will craash without handling multiple
requests.
MITIGATION
Max connections will be defined in the httpd.conf settings. Usually 256 is the limit.
4
1.1 Apache version number
In the digital world the webservers easily attacked by the attackers. They simply hack the
server by the use of special codes. They do this activity when they know the details about the
apache of the webserver. Cyber-attacks are highly dangerous. Because these attacks are the
reason for the data stealing, etc. So we must protect the apache version details. So we should
disable the server-signature and token details. In the below figure the apache version details are
showed for the deep understanding. And in the below screenshot the server tokens and the details
are listed and these details according to the server as apache and that tokens such as major and
minor and kind of operating system. And the version of apache is notified in each terms and the
operating system may be the UNIX.
The following two lines should be added in apache2.conf and httpd.conf
ServerToens Prod
ServerSignature Off
1.2 Many connections
When the hacker sends lot of web requests the webserver will craash without handling multiple
requests.
MITIGATION
Max connections will be defined in the httpd.conf settings. Usually 256 is the limit.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.3 DoS attack
One kind of cyber-attack carried out by the cyber-criminal. The main objective of
the attack was to cause the severe damage to the server. For this attack the attacker must check
the active status of the server. If the safety features are in the disabled condition, the attacker
easily crash the entire server. He needs to restart a system. That was achieved by the simple five
steps. For a band width a huge no of attacks are carried out. If the system has the heavy traffic,
the control was not possible. That is the positive parameter to the attacker. Using this flaw the
attacker can easily attacks the server. DOS attack means Denial of Service attack. Normally two
different types of attacks are used in the DOS attack. The first one is flooding service or crashing
service. And the next one is service to crash. Sometimes the system receives two much of traffic
in the server, then the floods attack is occur. The flood attack is broadly classified into three
different types.
Buffer overflow attack
ICMP flood
SYN flood
Buffer overflow attacks- one of the most famous attacks, it based on the concept of the
network address receive more traffic than the programmers are easily building the system for
handle this situation. It also determines the bugs in certain applications are networks.
ICMP flood- the spoofed packets are used for send the packets to the misconfigured
network. And also it ping the every target computer network. All the above operations are done
5
One kind of cyber-attack carried out by the cyber-criminal. The main objective of
the attack was to cause the severe damage to the server. For this attack the attacker must check
the active status of the server. If the safety features are in the disabled condition, the attacker
easily crash the entire server. He needs to restart a system. That was achieved by the simple five
steps. For a band width a huge no of attacks are carried out. If the system has the heavy traffic,
the control was not possible. That is the positive parameter to the attacker. Using this flaw the
attacker can easily attacks the server. DOS attack means Denial of Service attack. Normally two
different types of attacks are used in the DOS attack. The first one is flooding service or crashing
service. And the next one is service to crash. Sometimes the system receives two much of traffic
in the server, then the floods attack is occur. The flood attack is broadly classified into three
different types.
Buffer overflow attack
ICMP flood
SYN flood
Buffer overflow attacks- one of the most famous attacks, it based on the concept of the
network address receive more traffic than the programmers are easily building the system for
handle this situation. It also determines the bugs in certain applications are networks.
ICMP flood- the spoofed packets are used for send the packets to the misconfigured
network. And also it ping the every target computer network. All the above operations are done
5

in one specific machine. To amplify the traffic, it triggered by the network. ICMP flood attack is
also known as smurf attack or ping of death.
SYN floods- it not support the handshake process but it send the connection request to a
server. All the open ports are saturated and no legitimates are available.
MITIGATION -SIZE OF LIMIT REQUEST
Here the no of HTTP request need to reduced. That reduces the controlling of the traffic
of the web server. The size probably set minimum by manually. We can perform the action by
change the configuration of the directory. The code was showed in the below.
LimitRequestBody 512000 #set the limit to 512 MB
1.4 DISTRIBUTED DENIAL OF SERVICE ATTACK (DDoS)
It is also the attacking process carried out to crash the server. Here the group of
computers are formed to attack the server. All the computers are affected by the Trojans.
Mitigation
Normally the file attack is solved by the changing of time and in that two sectors is there. One
is timeout in that web server should have to complete the work within the time. SO for that issue
we can make a time ass too long before it could be loss. And each webserver has own time for
the process but the default time for this server is 300 seconds. And another one is represented as
take a time is alive and in this the web server need to wait for the request when the connection
getting end and it has the default time as 5 seconds.
Unnecessary modules
In the Linux server the function of the server get installed as default in the process of installing
apache in kind of operating system. To avoid the unwanted modules we can do switch of the
symbol in the line. For this action the server have to restart.
1.5 Access to httpd.conf
This file controlls everything in the web server. The direction and the functionality can affected
by this configuration file. The file permissions shoudld be set in such a way that hacker can not
access this file.
6
also known as smurf attack or ping of death.
SYN floods- it not support the handshake process but it send the connection request to a
server. All the open ports are saturated and no legitimates are available.
MITIGATION -SIZE OF LIMIT REQUEST
Here the no of HTTP request need to reduced. That reduces the controlling of the traffic
of the web server. The size probably set minimum by manually. We can perform the action by
change the configuration of the directory. The code was showed in the below.
LimitRequestBody 512000 #set the limit to 512 MB
1.4 DISTRIBUTED DENIAL OF SERVICE ATTACK (DDoS)
It is also the attacking process carried out to crash the server. Here the group of
computers are formed to attack the server. All the computers are affected by the Trojans.
Mitigation
Normally the file attack is solved by the changing of time and in that two sectors is there. One
is timeout in that web server should have to complete the work within the time. SO for that issue
we can make a time ass too long before it could be loss. And each webserver has own time for
the process but the default time for this server is 300 seconds. And another one is represented as
take a time is alive and in this the web server need to wait for the request when the connection
getting end and it has the default time as 5 seconds.
Unnecessary modules
In the Linux server the function of the server get installed as default in the process of installing
apache in kind of operating system. To avoid the unwanted modules we can do switch of the
symbol in the line. For this action the server have to restart.
1.5 Access to httpd.conf
This file controlls everything in the web server. The direction and the functionality can affected
by this configuration file. The file permissions shoudld be set in such a way that hacker can not
access this file.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
chattr +i /usr/local/apache2/conf/httpd.conf
Is the command prompt for disabling the httpd.conf file.
3. Threats towards the Apache web servers
3.1 First starter utilization
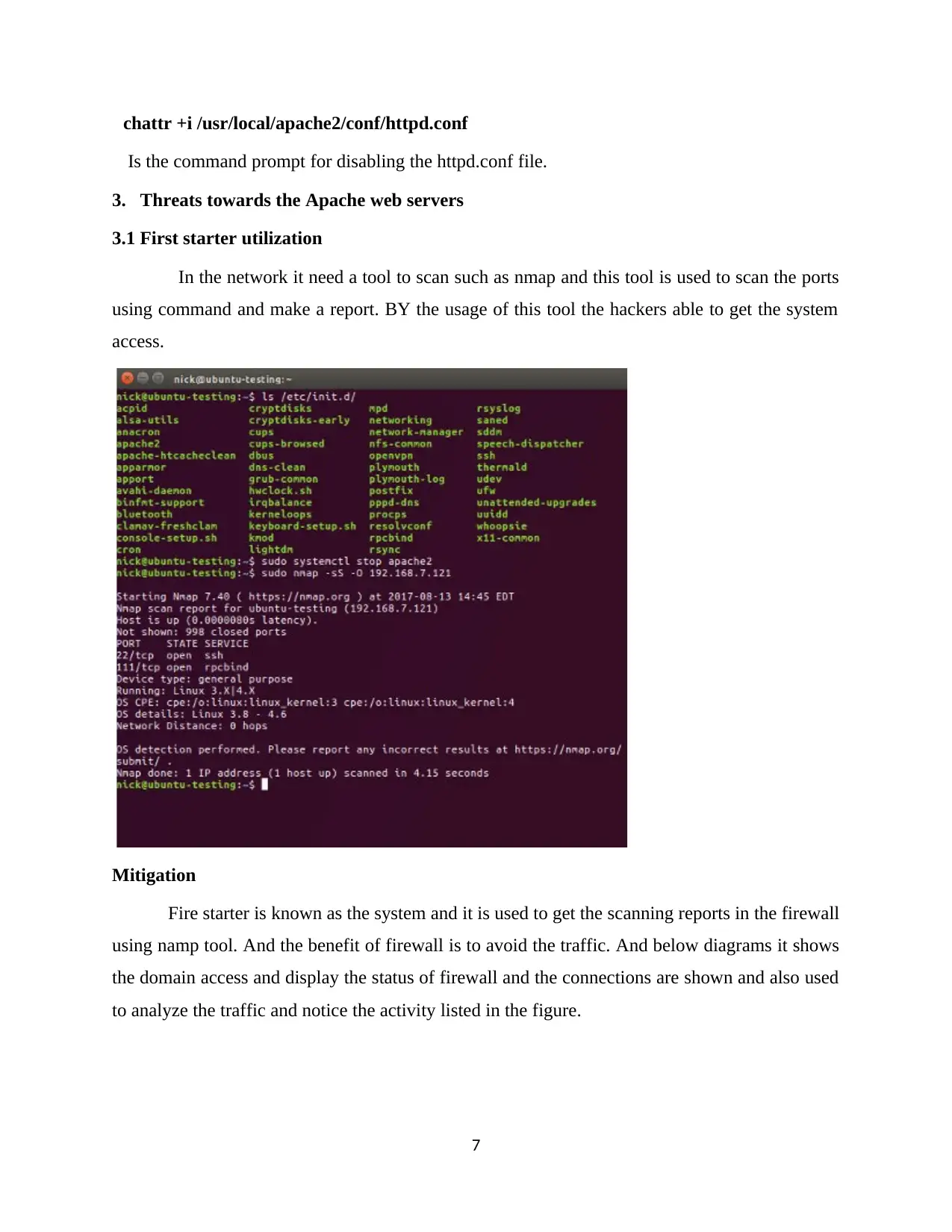
In the network it need a tool to scan such as nmap and this tool is used to scan the ports
using command and make a report. BY the usage of this tool the hackers able to get the system
access.
Mitigation
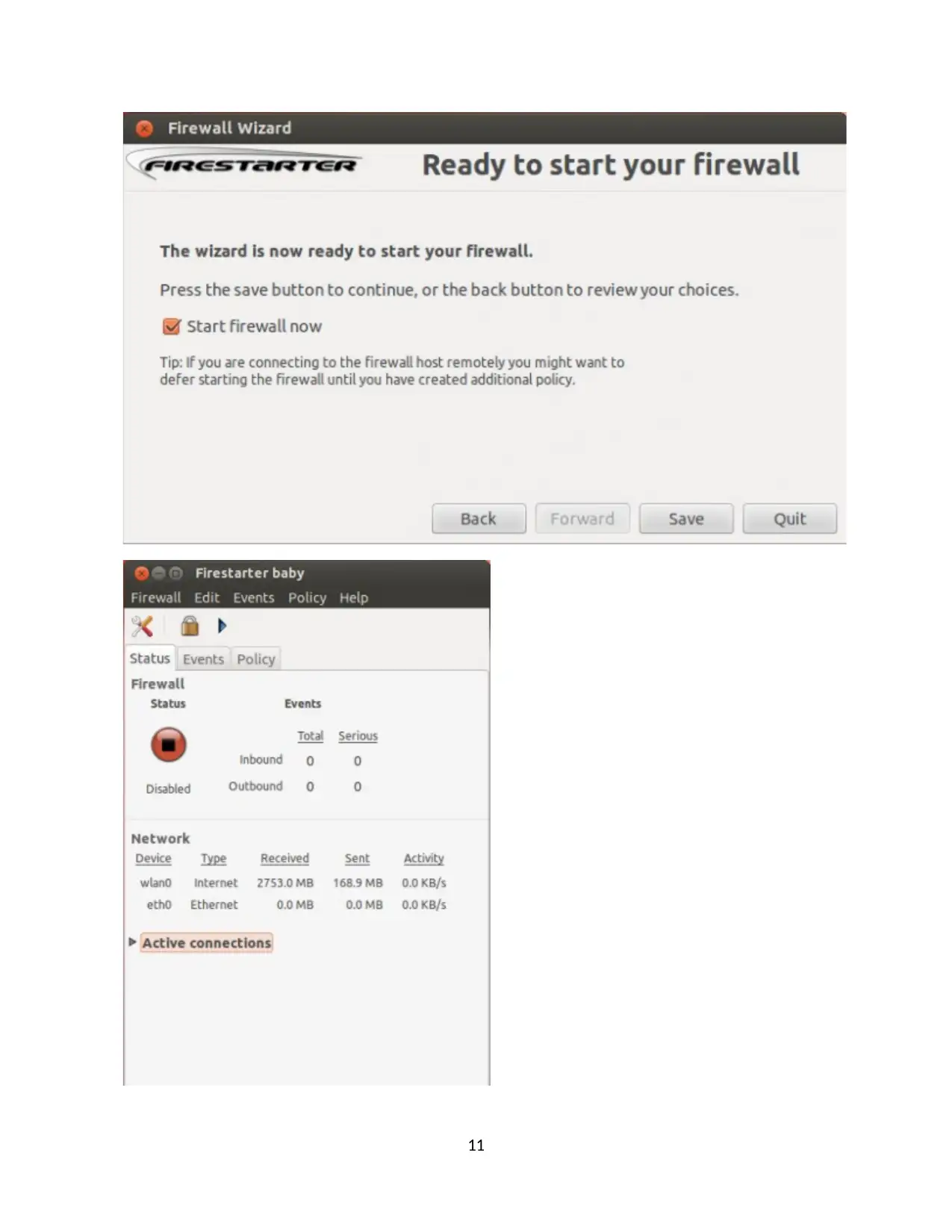
Fire starter is known as the system and it is used to get the scanning reports in the firewall
using namp tool. And the benefit of firewall is to avoid the traffic. And below diagrams it shows
the domain access and display the status of firewall and the connections are shown and also used
to analyze the traffic and notice the activity listed in the figure.
7
Is the command prompt for disabling the httpd.conf file.
3. Threats towards the Apache web servers
3.1 First starter utilization
In the network it need a tool to scan such as nmap and this tool is used to scan the ports
using command and make a report. BY the usage of this tool the hackers able to get the system
access.
Mitigation
Fire starter is known as the system and it is used to get the scanning reports in the firewall
using namp tool. And the benefit of firewall is to avoid the traffic. And below diagrams it shows
the domain access and display the status of firewall and the connections are shown and also used
to analyze the traffic and notice the activity listed in the figure.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
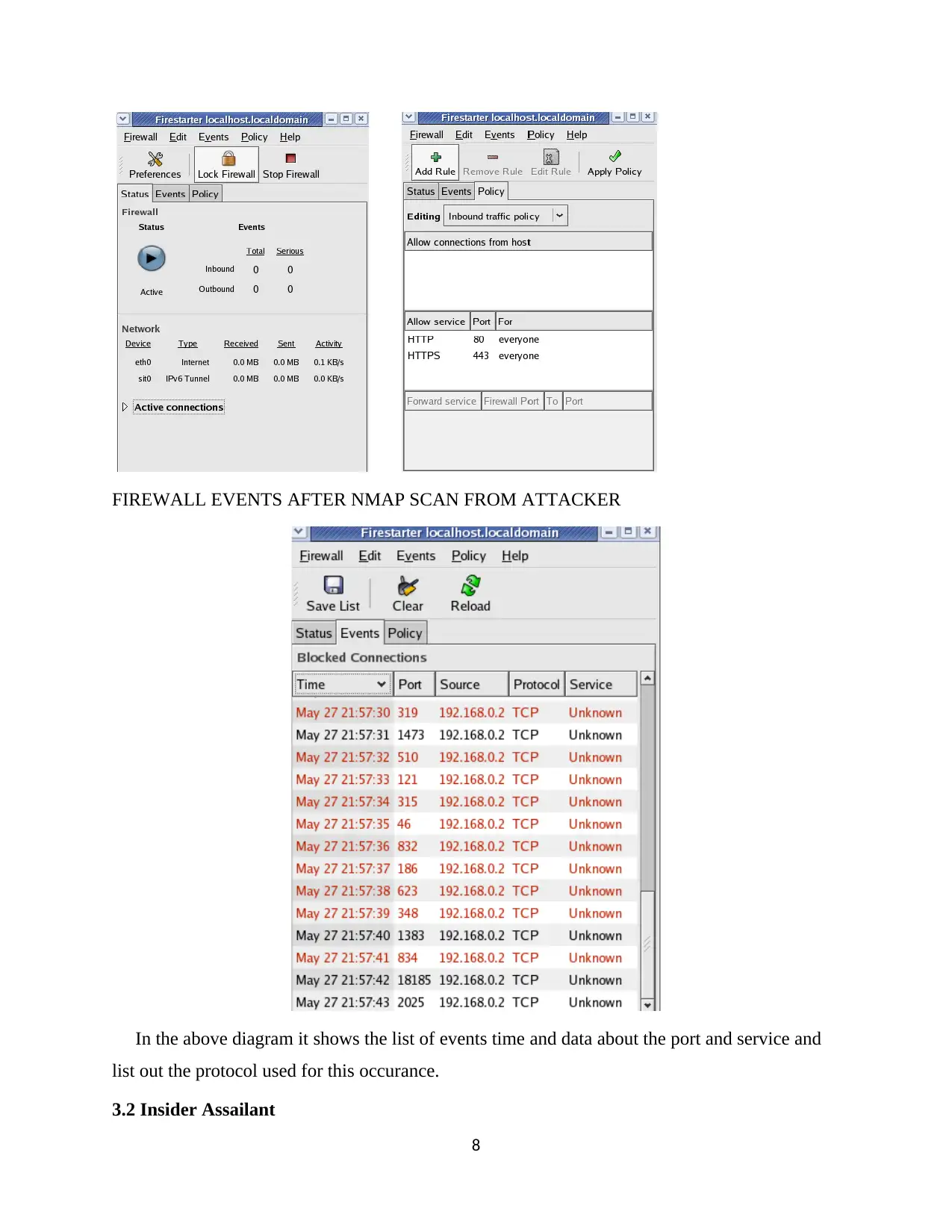
FIREWALL EVENTS AFTER NMAP SCAN FROM ATTACKER
In the above diagram it shows the list of events time and data about the port and service and
list out the protocol used for this occurance.
3.2 Insider Assailant
8
In the above diagram it shows the list of events time and data about the port and service and
list out the protocol used for this occurance.
3.2 Insider Assailant
8
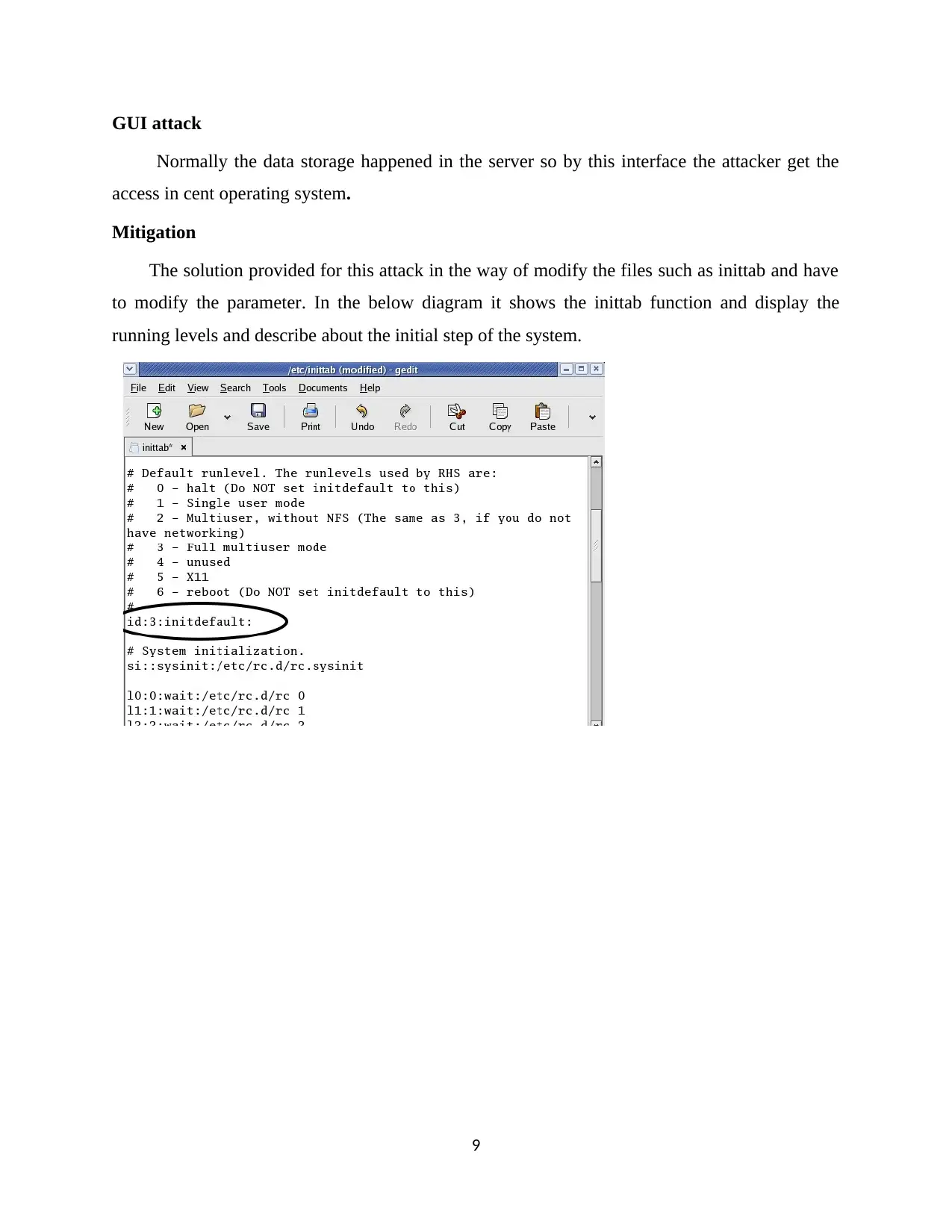
GUI attack
Normally the data storage happened in the server so by this interface the attacker get the
access in cent operating system.
Mitigation
The solution provided for this attack in the way of modify the files such as inittab and have
to modify the parameter. In the below diagram it shows the inittab function and display the
running levels and describe about the initial step of the system.
9
Normally the data storage happened in the server so by this interface the attacker get the
access in cent operating system.
Mitigation
The solution provided for this attack in the way of modify the files such as inittab and have
to modify the parameter. In the below diagram it shows the inittab function and display the
running levels and describe about the initial step of the system.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
11
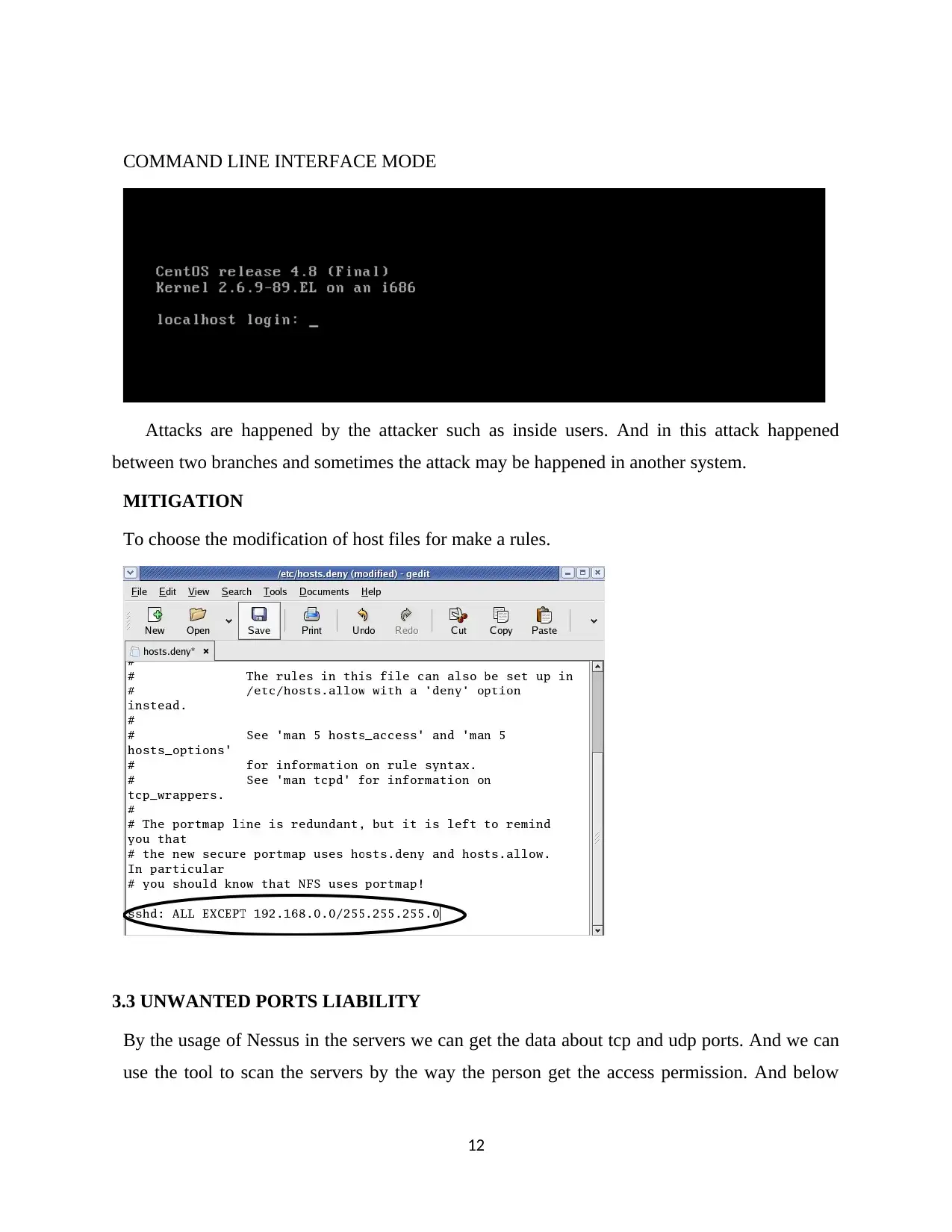
COMMAND LINE INTERFACE MODE
Attacks are happened by the attacker such as inside users. And in this attack happened
between two branches and sometimes the attack may be happened in another system.
MITIGATION
To choose the modification of host files for make a rules.
3.3 UNWANTED PORTS LIABILITY
By the usage of Nessus in the servers we can get the data about tcp and udp ports. And we can
use the tool to scan the servers by the way the person get the access permission. And below
12
Attacks are happened by the attacker such as inside users. And in this attack happened
between two branches and sometimes the attack may be happened in another system.
MITIGATION
To choose the modification of host files for make a rules.
3.3 UNWANTED PORTS LIABILITY
By the usage of Nessus in the servers we can get the data about tcp and udp ports. And we can
use the tool to scan the servers by the way the person get the access permission. And below
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





