Applied Communications: Network Case Projects & Solutions Analysis
VerifiedAdded on 2023/04/21
|13
|3246
|440
Case Study
AI Summary
This document presents solutions to a series of case projects in applied communications, addressing various networking challenges. The projects cover topics such as choosing between peer-to-peer and server-based networks for a growing company, upgrading a 50-computer network experiencing performance issues, and mitigating broadcast traffic in a LAN using extended star topology. Additional cases explore optimizing network efficiency for an older tech corporation, connecting two offices with fiber optic cables, configuring DHCP for dynamic IP address assignment, determining subnet masks for corporate consumers, and troubleshooting network connectivity issues based on the OSI model. Furthermore, the document offers solutions for enhancing network performance using high-level modems and local area networks.
APPLIED COMMUNICATIONS
0
Applied communications
0
Applied communications
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
APPLIED COMMUNICATIONS
1
Case Project 1-1 p49
Networking gadgets is an information technology company that provide the
networking services to their consumers and currently, total 8 employees are working in
this organization. In future, they will hire 10 more individuals to improve their
productivity for which they can adopt the server-based network to control and manage
their works. It is one of the best approaches to manage and backup their project files
because they provide the accessibility to those employees that are working on a project
(Akyildiz, Lee, Wang, Luo, & Chou, 2016). It has the potential to enhance the security
and privacy of their data or information files and it also provides the central control
process which is the very best approach to share files rather than storing them on every
machine. A recent study observed that to control and manage the 15 employees by
peer-to peer network is more difficult as compared to server based network and many
largest business industries are using this technique in their computer networks.
Therefore, networking gadgets should adopt server based network to reduce the
complexity and handle employee’s details for project files (Ozdemir, & Xiao, 2009). In
last two years, the rate of server based network has increased by 44% because of their
several benefits like very easy to design and implement, low power consumption; more
secure rather than peer to peer networks and improve the performance of
communication system (Peterson, & Davie, 2007).
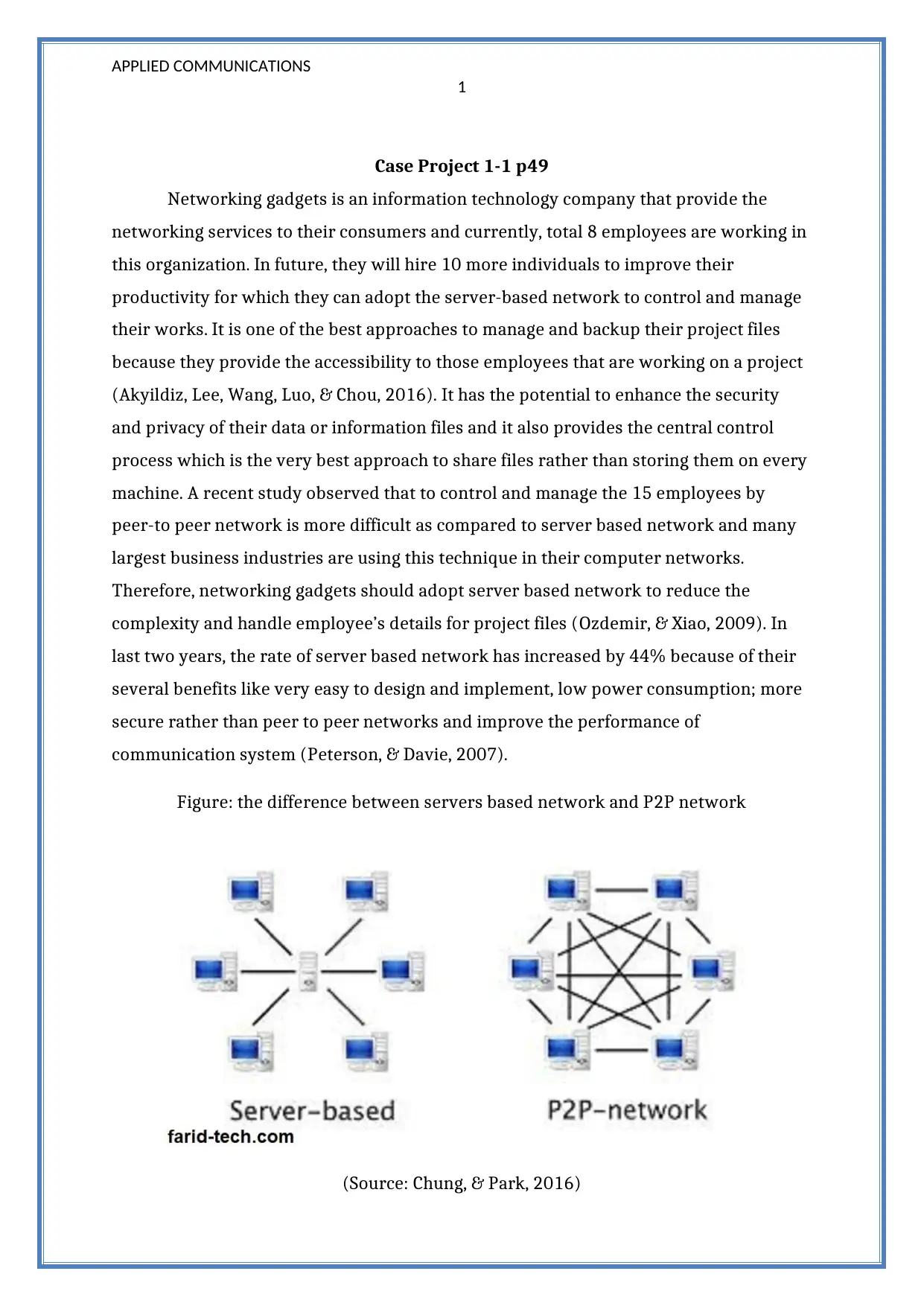
Figure: the difference between servers based network and P2P network
(Source: Chung, & Park, 2016)
1
Case Project 1-1 p49
Networking gadgets is an information technology company that provide the
networking services to their consumers and currently, total 8 employees are working in
this organization. In future, they will hire 10 more individuals to improve their
productivity for which they can adopt the server-based network to control and manage
their works. It is one of the best approaches to manage and backup their project files
because they provide the accessibility to those employees that are working on a project
(Akyildiz, Lee, Wang, Luo, & Chou, 2016). It has the potential to enhance the security
and privacy of their data or information files and it also provides the central control
process which is the very best approach to share files rather than storing them on every
machine. A recent study observed that to control and manage the 15 employees by
peer-to peer network is more difficult as compared to server based network and many
largest business industries are using this technique in their computer networks.
Therefore, networking gadgets should adopt server based network to reduce the
complexity and handle employee’s details for project files (Ozdemir, & Xiao, 2009). In
last two years, the rate of server based network has increased by 44% because of their
several benefits like very easy to design and implement, low power consumption; more
secure rather than peer to peer networks and improve the performance of
communication system (Peterson, & Davie, 2007).
Figure: the difference between servers based network and P2P network
(Source: Chung, & Park, 2016)

APPLIED COMMUNICATIONS
2
Case Project 2-1 p91
To increase the data speed of a network which is connected with the 50
computers the combination of routers and switches can be used because both have
potential to enhance the internet speed by 56 Mbps. The main server and one computer
system are connected with the router to control and manage the data speed between
these computer devices (Akyildiz, Wang, & Lin, 2015). The router is a type of
networking system which transfers data packets between the computer networks and
routes the traffic signals from one network to another. One router is sufficient to handle
the internet speed between 50 computers and it is interconnected with two more data
lines. Two 24 port network switches can be used to connect two more devices with each
other and it transfers data at the data link layer of the OSI model. The management team
should design and implement a central server which can control and manage the
incoming or outgoing transmissions. Moreover, the networks hubs can be upgraded to
handle the 1000 Mb per second data speed and company should adopt the security tools
to avoid bugs and traffic signals from networks like firewall, encryption and so on. The
recent investigation identified that the router is the very common network which is
used by many companies to enhance the internet speed and connect numbers of the
computer system at a time.
Figure: connection of routers and switches with a computer network
2
Case Project 2-1 p91
To increase the data speed of a network which is connected with the 50
computers the combination of routers and switches can be used because both have
potential to enhance the internet speed by 56 Mbps. The main server and one computer
system are connected with the router to control and manage the data speed between
these computer devices (Akyildiz, Wang, & Lin, 2015). The router is a type of
networking system which transfers data packets between the computer networks and
routes the traffic signals from one network to another. One router is sufficient to handle
the internet speed between 50 computers and it is interconnected with two more data
lines. Two 24 port network switches can be used to connect two more devices with each
other and it transfers data at the data link layer of the OSI model. The management team
should design and implement a central server which can control and manage the
incoming or outgoing transmissions. Moreover, the networks hubs can be upgraded to
handle the 1000 Mb per second data speed and company should adopt the security tools
to avoid bugs and traffic signals from networks like firewall, encryption and so on. The
recent investigation identified that the router is the very common network which is
used by many companies to enhance the internet speed and connect numbers of the
computer system at a time.
Figure: connection of routers and switches with a computer network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
APPLIED COMMUNICATIONS
3
Case Project 2-2 p91
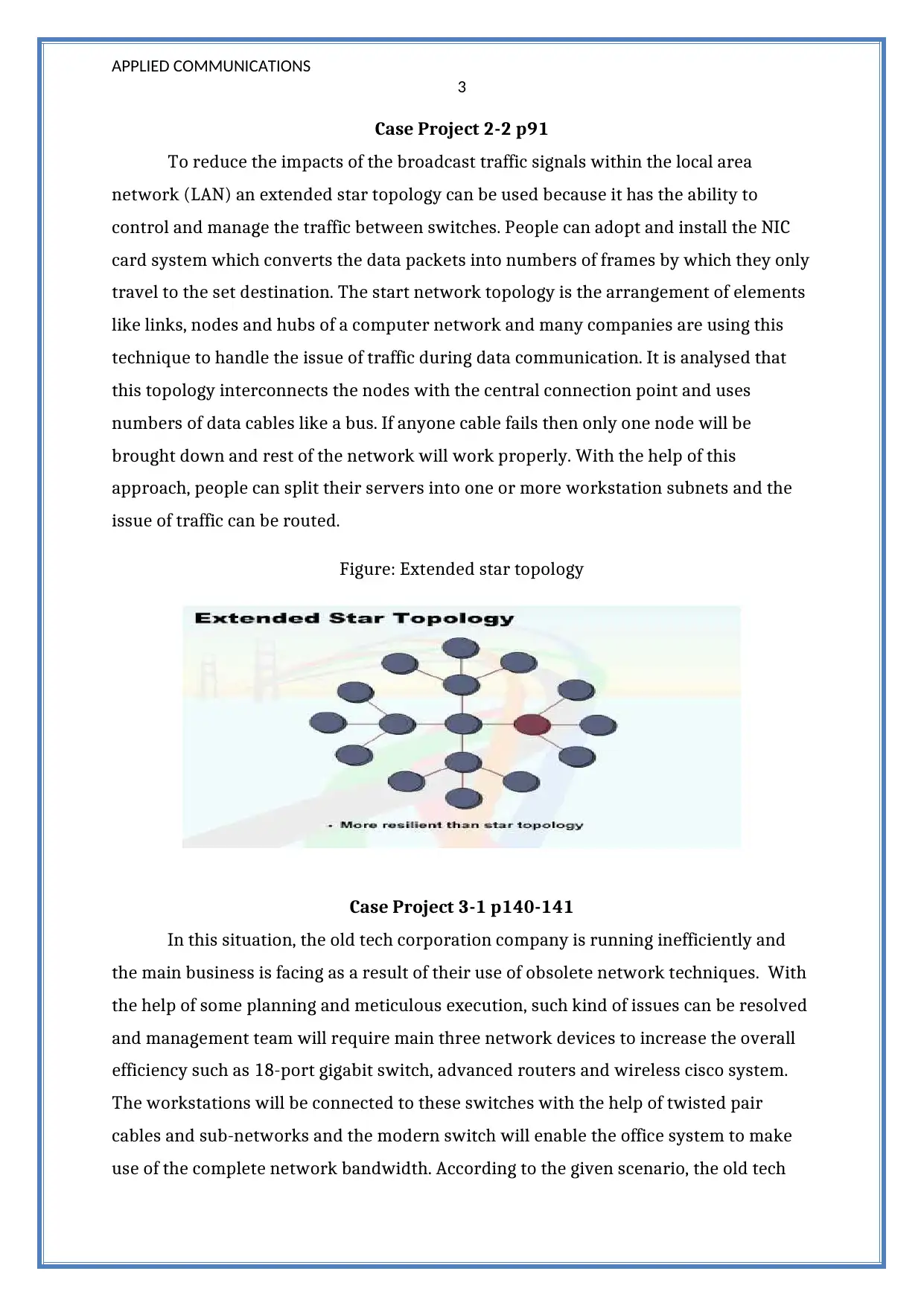
To reduce the impacts of the broadcast traffic signals within the local area
network (LAN) an extended star topology can be used because it has the ability to
control and manage the traffic between switches. People can adopt and install the NIC
card system which converts the data packets into numbers of frames by which they only
travel to the set destination. The start network topology is the arrangement of elements
like links, nodes and hubs of a computer network and many companies are using this
technique to handle the issue of traffic during data communication. It is analysed that
this topology interconnects the nodes with the central connection point and uses
numbers of data cables like a bus. If anyone cable fails then only one node will be
brought down and rest of the network will work properly. With the help of this
approach, people can split their servers into one or more workstation subnets and the
issue of traffic can be routed.
Figure: Extended star topology
Case Project 3-1 p140-141
In this situation, the old tech corporation company is running inefficiently and
the main business is facing as a result of their use of obsolete network techniques. With
the help of some planning and meticulous execution, such kind of issues can be resolved
and management team will require main three network devices to increase the overall
efficiency such as 18-port gigabit switch, advanced routers and wireless cisco system.
The workstations will be connected to these switches with the help of twisted pair
cables and sub-networks and the modern switch will enable the office system to make
use of the complete network bandwidth. According to the given scenario, the old tech
3
Case Project 2-2 p91
To reduce the impacts of the broadcast traffic signals within the local area
network (LAN) an extended star topology can be used because it has the ability to
control and manage the traffic between switches. People can adopt and install the NIC
card system which converts the data packets into numbers of frames by which they only
travel to the set destination. The start network topology is the arrangement of elements
like links, nodes and hubs of a computer network and many companies are using this
technique to handle the issue of traffic during data communication. It is analysed that
this topology interconnects the nodes with the central connection point and uses
numbers of data cables like a bus. If anyone cable fails then only one node will be
brought down and rest of the network will work properly. With the help of this
approach, people can split their servers into one or more workstation subnets and the
issue of traffic can be routed.
Figure: Extended star topology
Case Project 3-1 p140-141
In this situation, the old tech corporation company is running inefficiently and
the main business is facing as a result of their use of obsolete network techniques. With
the help of some planning and meticulous execution, such kind of issues can be resolved
and management team will require main three network devices to increase the overall
efficiency such as 18-port gigabit switch, advanced routers and wireless cisco system.
The workstations will be connected to these switches with the help of twisted pair
cables and sub-networks and the modern switch will enable the office system to make
use of the complete network bandwidth. According to the given scenario, the old tech
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

APPLIED COMMUNICATIONS
4
will develop 5 more workstations for which they require to interconnect their computer
networks with each other (Ali, Sivaraman, Radford, & Jha, 2015). The wireless
technology can be adopted for increasing the efficiency of the communication system
and IT team can install a cisco system WRVS4400N wireless system and security
routers in the ceiling of the old tech. all wireless networks and system are connected
with the 18-port switch and will interconnect with the workstations wirelessly. To
complete the configuration of this wireless system they can adopt and install the
network interface cards in every machine. To complete the computer network, the
manger can configure every manufacturing computer to identify and interconnect with
the wireless router by generating a second sub-network and broadcast system. To solve
the difficulty of cabling they can adopt the wireless local area networks and
technologies like Wi-Fi, Zigbee, Z-wave and many more.
Figure: cisco system WRVS4400N wireless system
(Source: Wood, Ramakrishnan, Hwang, Liu, & Zhang, 2015)
Case Project 4-2 p186
To interconnect two offices in different buildings the XYZ Corporation can use
the fibre optic cable because it has the potential to send and receive the data over long
distance. It is observed that fibre optic cable is more reliable and secure as compared to
the twisted pair cable and many information and communication technology companies
are using these cables for data communication purpose. The main drawback of twisted
pair cable is that it cannot be used for long distance communication for which XYS
Company can adopt the fibre optic cable to connect their offices. There are many
4
will develop 5 more workstations for which they require to interconnect their computer
networks with each other (Ali, Sivaraman, Radford, & Jha, 2015). The wireless
technology can be adopted for increasing the efficiency of the communication system
and IT team can install a cisco system WRVS4400N wireless system and security
routers in the ceiling of the old tech. all wireless networks and system are connected
with the 18-port switch and will interconnect with the workstations wirelessly. To
complete the configuration of this wireless system they can adopt and install the
network interface cards in every machine. To complete the computer network, the
manger can configure every manufacturing computer to identify and interconnect with
the wireless router by generating a second sub-network and broadcast system. To solve
the difficulty of cabling they can adopt the wireless local area networks and
technologies like Wi-Fi, Zigbee, Z-wave and many more.
Figure: cisco system WRVS4400N wireless system
(Source: Wood, Ramakrishnan, Hwang, Liu, & Zhang, 2015)
Case Project 4-2 p186
To interconnect two offices in different buildings the XYZ Corporation can use
the fibre optic cable because it has the potential to send and receive the data over long
distance. It is observed that fibre optic cable is more reliable and secure as compared to
the twisted pair cable and many information and communication technology companies
are using these cables for data communication purpose. The main drawback of twisted
pair cable is that it cannot be used for long distance communication for which XYS
Company can adopt the fibre optic cable to connect their offices. There are many

APPLIED COMMUNICATIONS
5
researchers investigated on this topic and they analysed that to transfer information
through fibre optic cable is more easy and secure because signal travel in the form of
light which cannot be easily hacked. Point A is true because Ethernet has an attenuation
distance of 100m maximum by which it cannot go far enough. Point C is true because
the ground potential can cause EMI or RFI by which company cannot connect their both
companies if they use twisted pair cables. D is also true because fibre-optic cables are
capable to provide the TERA bits per second data speed.
Figure: Fibre optic cable
(Jousset, et al., 2016)
Case Project 5-2 p235
We can install and configure the DHCP process which will help to assign the
dynamic internet protocol address and DNS server information related to the printers
and workstations. DHCP is defined as the dynamic host configuration protocol which is
used to provide the IP address to any peripheral device or node. It is evaluated that in
the network of DHCP the IPv4 can be used and configured at the time of installation
which can help to configure the 25 workstations through a single network protocol.
People can adopt the IPv6 network protocol to increase the efficiency and performance
of their dynamic IP address system. After the installation and configuration of DHCP
network, we are able to control and manage the events, services, workstations and
sources that are related to the servers (Akyildiz, Melodia, and Chowdhury, 2007).
5
researchers investigated on this topic and they analysed that to transfer information
through fibre optic cable is more easy and secure because signal travel in the form of
light which cannot be easily hacked. Point A is true because Ethernet has an attenuation
distance of 100m maximum by which it cannot go far enough. Point C is true because
the ground potential can cause EMI or RFI by which company cannot connect their both
companies if they use twisted pair cables. D is also true because fibre-optic cables are
capable to provide the TERA bits per second data speed.
Figure: Fibre optic cable
(Jousset, et al., 2016)
Case Project 5-2 p235
We can install and configure the DHCP process which will help to assign the
dynamic internet protocol address and DNS server information related to the printers
and workstations. DHCP is defined as the dynamic host configuration protocol which is
used to provide the IP address to any peripheral device or node. It is evaluated that in
the network of DHCP the IPv4 can be used and configured at the time of installation
which can help to configure the 25 workstations through a single network protocol.
People can adopt the IPv6 network protocol to increase the efficiency and performance
of their dynamic IP address system. After the installation and configuration of DHCP
network, we are able to control and manage the events, services, workstations and
sources that are related to the servers (Akyildiz, Melodia, and Chowdhury, 2007).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

APPLIED COMMUNICATIONS
6
Moreover, people can adopt three IP reservations with the help of MAC technique of the
network printer that will help to assign the same IP address to three printers. In last
two years, the issue of configuration has increased by 34% and many small and large
business sectors are facing such issue but now DHCP changed the way of
communication and provide a platform to configure the number of workstation and
networks by assigning a dynamic IP address. The main advantage identified by the
researcher is that DHCP can manage the configuration related issue automatically which
reduce the difficulties and complexity in a computer system (Alemdar, & Ersoy, 2010).
Case Project 6-1 p288
For this requirement, the new subnet mask is 255.255.255.240 which will help meet
the requirements of the consumers and also satisfy the IP requirements of 16 corporate
consumers which need between 10 and 14 addresses each. It is described that a
network address is a physical address which uniquely distinguishes computer devices
over a communication network (Liu, Gao, Wang, & Wang, 2015). With the help of this
technique, people can identify any network device or node and it involves few elements
like IP address, MAC and host address. The first four sub-network addresses are given
below:
197.14.88.0
197.14.88.16
197.14.88.32
197.14.88.48
Case Project 7-1 p317-318
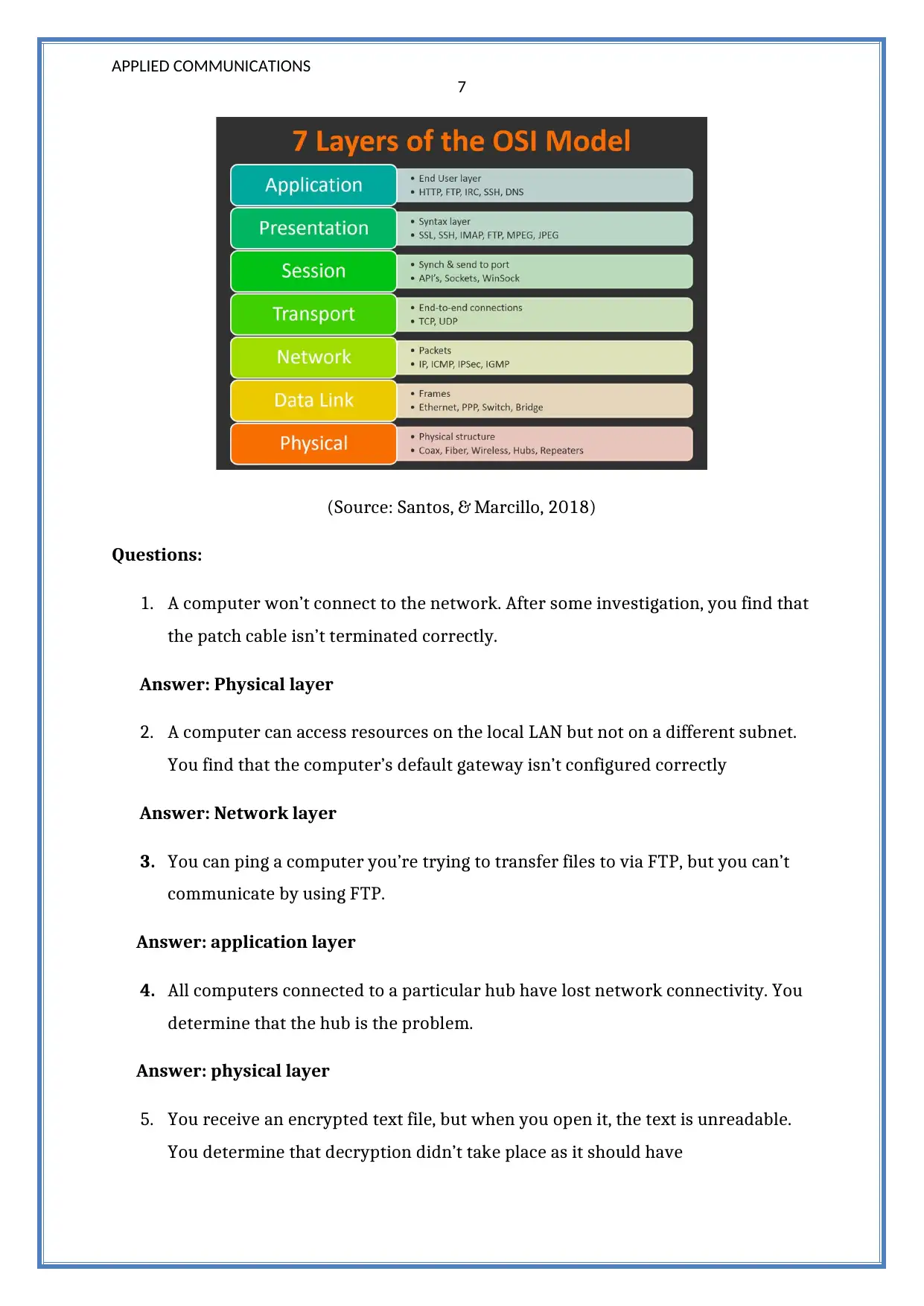
The OSI model is defined as a conceptual model which characterizes and
standardizes the communication functions of a communication system. It consists of
main seven layers, for example, application, presentation, session, transport, network
layer, data link and physical layer. Mainly, it is used in the computer networks for
troubleshooting purpose and it has the capability to isolate the problem on a specific
software module (Yan, Şekercioğlu, & Narayanan, 2010).
Figure: Layers of the OSI model
6
Moreover, people can adopt three IP reservations with the help of MAC technique of the
network printer that will help to assign the same IP address to three printers. In last
two years, the issue of configuration has increased by 34% and many small and large
business sectors are facing such issue but now DHCP changed the way of
communication and provide a platform to configure the number of workstation and
networks by assigning a dynamic IP address. The main advantage identified by the
researcher is that DHCP can manage the configuration related issue automatically which
reduce the difficulties and complexity in a computer system (Alemdar, & Ersoy, 2010).
Case Project 6-1 p288
For this requirement, the new subnet mask is 255.255.255.240 which will help meet
the requirements of the consumers and also satisfy the IP requirements of 16 corporate
consumers which need between 10 and 14 addresses each. It is described that a
network address is a physical address which uniquely distinguishes computer devices
over a communication network (Liu, Gao, Wang, & Wang, 2015). With the help of this
technique, people can identify any network device or node and it involves few elements
like IP address, MAC and host address. The first four sub-network addresses are given
below:
197.14.88.0
197.14.88.16
197.14.88.32
197.14.88.48
Case Project 7-1 p317-318
The OSI model is defined as a conceptual model which characterizes and
standardizes the communication functions of a communication system. It consists of
main seven layers, for example, application, presentation, session, transport, network
layer, data link and physical layer. Mainly, it is used in the computer networks for
troubleshooting purpose and it has the capability to isolate the problem on a specific
software module (Yan, Şekercioğlu, & Narayanan, 2010).
Figure: Layers of the OSI model
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
APPLIED COMMUNICATIONS
7
(Source: Santos, & Marcillo, 2018)
Questions:
1. A computer won’t connect to the network. After some investigation, you find that
the patch cable isn’t terminated correctly.
Answer: Physical layer
2. A computer can access resources on the local LAN but not on a different subnet.
You find that the computer’s default gateway isn’t configured correctly
Answer: Network layer
3. You can ping a computer you’re trying to transfer files to via FTP, but you can’t
communicate by using FTP.
Answer: application layer
4. All computers connected to a particular hub have lost network connectivity. You
determine that the hub is the problem.
Answer: physical layer
5. You receive an encrypted text file, but when you open it, the text is unreadable.
You determine that decryption didn’t take place as it should have
7
(Source: Santos, & Marcillo, 2018)
Questions:
1. A computer won’t connect to the network. After some investigation, you find that
the patch cable isn’t terminated correctly.
Answer: Physical layer
2. A computer can access resources on the local LAN but not on a different subnet.
You find that the computer’s default gateway isn’t configured correctly
Answer: Network layer
3. You can ping a computer you’re trying to transfer files to via FTP, but you can’t
communicate by using FTP.
Answer: application layer
4. All computers connected to a particular hub have lost network connectivity. You
determine that the hub is the problem.
Answer: physical layer
5. You receive an encrypted text file, but when you open it, the text is unreadable.
You determine that decryption didn’t take place as it should have

APPLIED COMMUNICATIONS
8
Answer: presentation layer
6. You check some statistics generated by a network-monitoring program and
discover that an abnormally high number of CRC errors were detected
Answer: link layer
7. One of your servers has been exhibiting sluggish network performance. You use
a network monitoring program to try to evaluate the problem. You find
considerable TCP retries occurring because the server is being overwhelmed by
data, and packets are being discarded
Answer: network layer
8. A user is trying to connect to another computer, but the logon attempt is
continually rejected
Answer: Session layer
9. You try to access a Linux server to share files by using NFS. You can
communicate with the server, but the shared files don’t appear to be available
Answer: application layer
10. You inspect a computer that can’t communicate with other computers. You find
that IPv6 instead of IPv4 is installed on that computer
Answer: network layer
Case Project 8-1 p366
For the given scenario the high level modems can be used because it has the
potential to improve the performance of the network system. With the help of this
system CNT books can control and manage the 300 workstations and 10 networks at a
time and they can share projects from one network to another (Kreutz, et al., 2015). To
interconnect all these workstations with Servers Company can adopt the local area
network due to their several advantages such as more efficient, faster speed, and very
secure (Atzori, Iera, Morabito, & Nitti, 2012). According to my opinion management
team can adopt the configure ports and VLANs for this design because both systems
8
Answer: presentation layer
6. You check some statistics generated by a network-monitoring program and
discover that an abnormally high number of CRC errors were detected
Answer: link layer
7. One of your servers has been exhibiting sluggish network performance. You use
a network monitoring program to try to evaluate the problem. You find
considerable TCP retries occurring because the server is being overwhelmed by
data, and packets are being discarded
Answer: network layer
8. A user is trying to connect to another computer, but the logon attempt is
continually rejected
Answer: Session layer
9. You try to access a Linux server to share files by using NFS. You can
communicate with the server, but the shared files don’t appear to be available
Answer: application layer
10. You inspect a computer that can’t communicate with other computers. You find
that IPv6 instead of IPv4 is installed on that computer
Answer: network layer
Case Project 8-1 p366
For the given scenario the high level modems can be used because it has the
potential to improve the performance of the network system. With the help of this
system CNT books can control and manage the 300 workstations and 10 networks at a
time and they can share projects from one network to another (Kreutz, et al., 2015). To
interconnect all these workstations with Servers Company can adopt the local area
network due to their several advantages such as more efficient, faster speed, and very
secure (Atzori, Iera, Morabito, & Nitti, 2012). According to my opinion management
team can adopt the configure ports and VLANs for this design because both systems
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
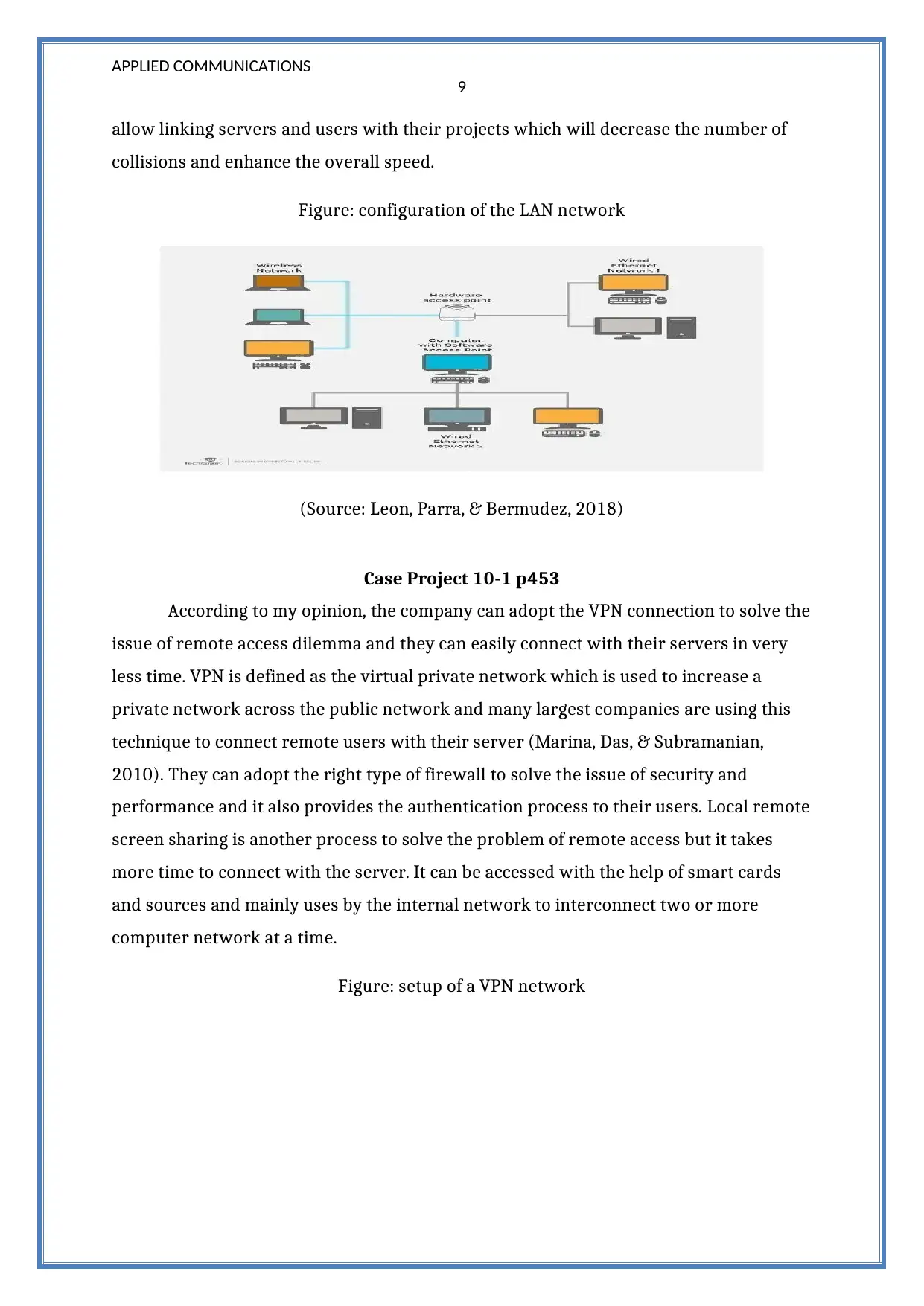
APPLIED COMMUNICATIONS
9
allow linking servers and users with their projects which will decrease the number of
collisions and enhance the overall speed.
Figure: configuration of the LAN network
(Source: Leon, Parra, & Bermudez, 2018)
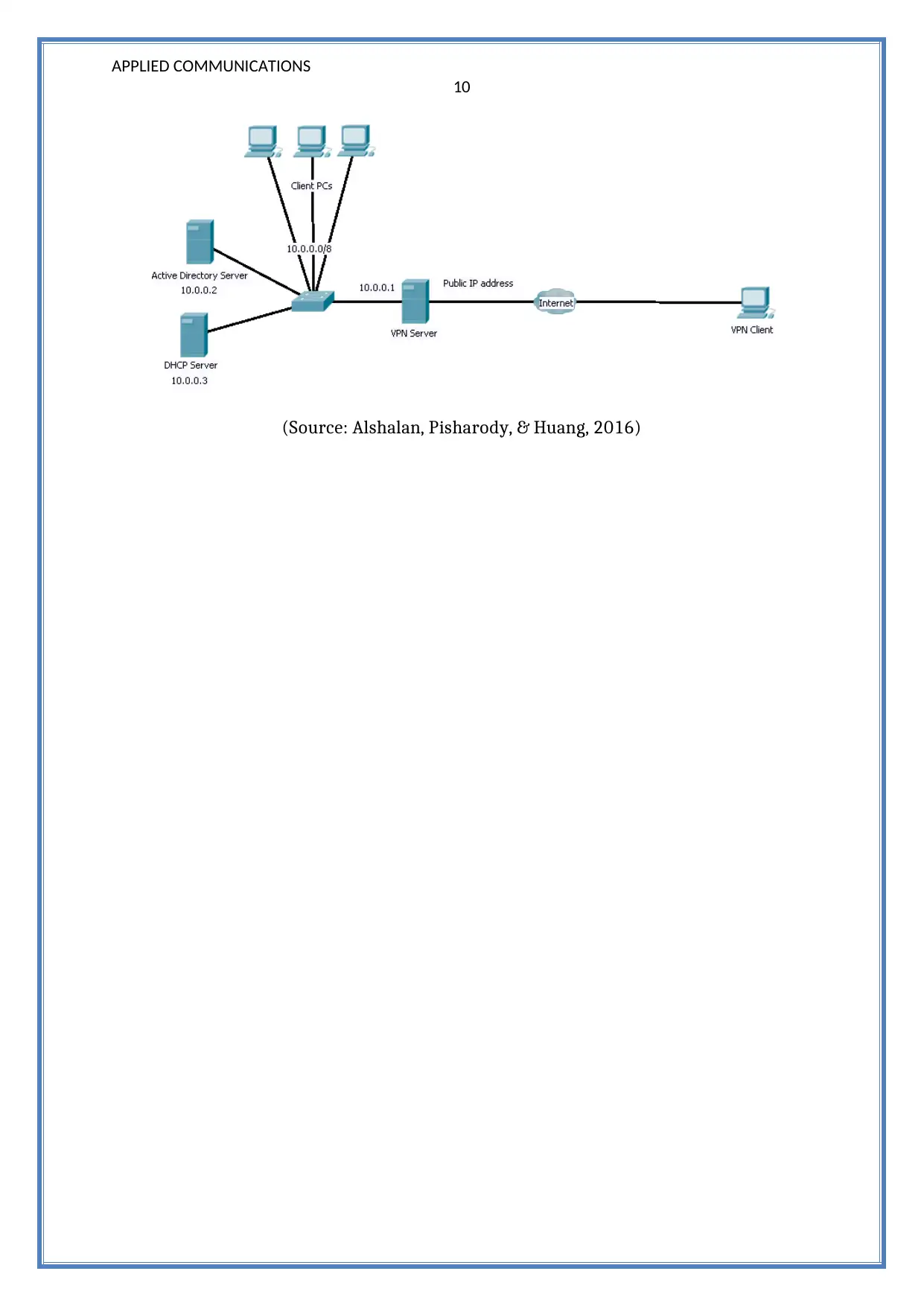
Case Project 10-1 p453
According to my opinion, the company can adopt the VPN connection to solve the
issue of remote access dilemma and they can easily connect with their servers in very
less time. VPN is defined as the virtual private network which is used to increase a
private network across the public network and many largest companies are using this
technique to connect remote users with their server (Marina, Das, & Subramanian,
2010). They can adopt the right type of firewall to solve the issue of security and
performance and it also provides the authentication process to their users. Local remote
screen sharing is another process to solve the problem of remote access but it takes
more time to connect with the server. It can be accessed with the help of smart cards
and sources and mainly uses by the internal network to interconnect two or more
computer network at a time.
Figure: setup of a VPN network
9
allow linking servers and users with their projects which will decrease the number of
collisions and enhance the overall speed.
Figure: configuration of the LAN network
(Source: Leon, Parra, & Bermudez, 2018)
Case Project 10-1 p453
According to my opinion, the company can adopt the VPN connection to solve the
issue of remote access dilemma and they can easily connect with their servers in very
less time. VPN is defined as the virtual private network which is used to increase a
private network across the public network and many largest companies are using this
technique to connect remote users with their server (Marina, Das, & Subramanian,
2010). They can adopt the right type of firewall to solve the issue of security and
performance and it also provides the authentication process to their users. Local remote
screen sharing is another process to solve the problem of remote access but it takes
more time to connect with the server. It can be accessed with the help of smart cards
and sources and mainly uses by the internal network to interconnect two or more
computer network at a time.
Figure: setup of a VPN network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
APPLIED COMMUNICATIONS
10
(Source: Alshalan, Pisharody, & Huang, 2016)
10
(Source: Alshalan, Pisharody, & Huang, 2016)

APPLIED COMMUNICATIONS
11
References
Akyildiz, I. F., Lee, A., Wang, P., Luo, M., & Chou, W. (2016). Research challenges for
traffic engineering in software defined networks. IEEE Network, 30(3), 52-58.
Akyildiz, I. F., Wang, P., & Lin, S. C. (2015). SoftAir: A software defined networking
architecture for 5G wireless systems. Computer Networks, 85, 1-18.
Akyildiz, I.F., Melodia, T. and Chowdhury, K.R., 2007. A survey on wireless multimedia
sensor networks. Computer networks, 51(4), pp.921-960.
Alemdar, H., & Ersoy, C. (2010). Wireless sensor networks for healthcare: A
survey. Computer networks, 54(15), 2688-2710.
Ali, S. T., Sivaraman, V., Radford, A., & Jha, S. (2015). A Survey of Securing Networks
Using Software Defined Networking. IEEE Trans. Reliability, 64(3), 1086-1097.
Alshalan, A., Pisharody, S., & Huang, D. (2016). A survey of mobile VPN
technologies. IEEE Communications Surveys & Tutorials, 18(2), 1177-1196.
Atzori, L., Iera, A., Morabito, G., & Nitti, M. (2012). The social internet of things (siot)–
when social networks meet the internet of things: Concept, architecture and
network characterization. Computer networks, 56(16), 3594-3608.
Chung, K., & Park, R. C. (2016). P2P cloud network services for IoT based disaster
situations information. Peer-to-Peer Networking and Applications, 9(3), 566-577.
Jousset, P., Reinsch, T., Ryberg, T., Blanck, H., Clarke, A., Aghayev, R., ... & Krawczyk, C. M.
(2018). Dynamic strain determination using fibre-optic cables allows imaging of
seismological and structural features. Nature communications, 9(1), 2509.
Kreutz, D., Ramos, F. M., Verissimo, P. E., Rothenberg, C. E., Azodolmolky, S., & Uhlig, S.
(2015). Software-defined networking: A comprehensive survey. Proceedings of
the IEEE, 103(1), 14-76.
Leon, A. F. H., Parra, O. J. S., & Bermudez, G. M. T. (2018). LAN-WAN-LAN end-to-end
Network Simulation with NS2. International Journal of Applied Engineering
Research, 13(17), 13136-13140.
11
References
Akyildiz, I. F., Lee, A., Wang, P., Luo, M., & Chou, W. (2016). Research challenges for
traffic engineering in software defined networks. IEEE Network, 30(3), 52-58.
Akyildiz, I. F., Wang, P., & Lin, S. C. (2015). SoftAir: A software defined networking
architecture for 5G wireless systems. Computer Networks, 85, 1-18.
Akyildiz, I.F., Melodia, T. and Chowdhury, K.R., 2007. A survey on wireless multimedia
sensor networks. Computer networks, 51(4), pp.921-960.
Alemdar, H., & Ersoy, C. (2010). Wireless sensor networks for healthcare: A
survey. Computer networks, 54(15), 2688-2710.
Ali, S. T., Sivaraman, V., Radford, A., & Jha, S. (2015). A Survey of Securing Networks
Using Software Defined Networking. IEEE Trans. Reliability, 64(3), 1086-1097.
Alshalan, A., Pisharody, S., & Huang, D. (2016). A survey of mobile VPN
technologies. IEEE Communications Surveys & Tutorials, 18(2), 1177-1196.
Atzori, L., Iera, A., Morabito, G., & Nitti, M. (2012). The social internet of things (siot)–
when social networks meet the internet of things: Concept, architecture and
network characterization. Computer networks, 56(16), 3594-3608.
Chung, K., & Park, R. C. (2016). P2P cloud network services for IoT based disaster
situations information. Peer-to-Peer Networking and Applications, 9(3), 566-577.
Jousset, P., Reinsch, T., Ryberg, T., Blanck, H., Clarke, A., Aghayev, R., ... & Krawczyk, C. M.
(2018). Dynamic strain determination using fibre-optic cables allows imaging of
seismological and structural features. Nature communications, 9(1), 2509.
Kreutz, D., Ramos, F. M., Verissimo, P. E., Rothenberg, C. E., Azodolmolky, S., & Uhlig, S.
(2015). Software-defined networking: A comprehensive survey. Proceedings of
the IEEE, 103(1), 14-76.
Leon, A. F. H., Parra, O. J. S., & Bermudez, G. M. T. (2018). LAN-WAN-LAN end-to-end
Network Simulation with NS2. International Journal of Applied Engineering
Research, 13(17), 13136-13140.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




