MBC Firm: Mobile Security, Linux Server Auditing Analysis
VerifiedAdded on 2023/01/11
|11
|2676
|85
Report
AI Summary
This report provides a comprehensive security and risk assessment for MBC, a broadcasting firm that allows employees to use their own mobile devices. It identifies various mobile security threats, including application-based threats like spyware, malware, and vulnerable applications, as well as web-based threats such as drive-by downloads and phishing scams. The report details security protection techniques and mitigation strategies, including the formulation of precise policies, fragmentation of information, encryption, and the use of security software. It also demonstrates how MBC can ensure web service availability using Apache Cassandra and discusses the influence of employees on information security, highlighting risks from within and cybersecurity incidents. Furthermore, the report illustrates Linux server auditing tools, such as Nagios and Fluentd, and provides commands for creating directories and users in a Linux environment, offering practical insights into server management and security practices. The report emphasizes the importance of proactive security measures to protect MBC's network and sensitive information.

Applied Project
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction.................................................................................................................................................3
Task 1..........................................................................................................................................................3
Specify types of threats within mobile devices and vulnerability to destruction and abuse.....................3
Security protection techniques and mitigation of risks within mobile devices.........................................4
Demonstrate how firm ensure availability of web service using Apache.................................................5
Influence of employees of information security.......................................................................................6
Illustrate Linux server auditing tools along with ways through which they can be used by MBC...........7
Task 2..........................................................................................................................................................8
Conception of two directories in Linux...................................................................................................8
Illustrate ways for creating three users....................................................................................................9
Conclusion.................................................................................................................................................10
References.................................................................................................................................................11
Introduction.................................................................................................................................................3
Task 1..........................................................................................................................................................3
Specify types of threats within mobile devices and vulnerability to destruction and abuse.....................3
Security protection techniques and mitigation of risks within mobile devices.........................................4
Demonstrate how firm ensure availability of web service using Apache.................................................5
Influence of employees of information security.......................................................................................6
Illustrate Linux server auditing tools along with ways through which they can be used by MBC...........7
Task 2..........................................................................................................................................................8
Conception of two directories in Linux...................................................................................................8
Illustrate ways for creating three users....................................................................................................9
Conclusion.................................................................................................................................................10
References.................................................................................................................................................11

Introduction
The assessment which comprises of recognizing risks within firm, technologies utilized
by them along with processes for verification that whether all the controls are in place for
safeguarding system against security threats is referred to as security and risk assessment. Here,
emphasis is laid on preventing applications from any kind of defects and associated
vulnerabilities (Arora and Gigras, 2020). For understanding security aspects that are being
experienced by firms, MBC is taken into consideration that is a broadcasting firm who has given
their employees with permission to make use of their own devices like mobile phones. This
report gives an insight into security aspects, vulnerabilities and ways in which they can be
mitigated. In addition to this, availability of servers will also be analyzed along with impact on
security policies by employees and distinct auditing tools are also mentioned.
Task 1
Specify types of threats within mobile devices and vulnerability to destruction and abuse
Viruses and spyware creates influence on laptop and PC’s similarly there are various threats
which create an impact on mobile phones. The risk that creates an influence on organization on
the whole as well as their network is referred to as security threat. Two major reasons are there
for these risks, physical (stealing of devices) and non-physical risks (virus attacks, ransomware,
malware, Trojan horse, etc.). The mobile security threats which can impact overall network of
MBC firm are illustrated below:
Application based threats: People usually download apps which seems appealing to them
and it is always not necessary that they are from authorized persons. This denotes that
applications do not illustrate whether they have ransomware or any other vulnerability within
them for conducting illegal activities (Brashear, 2020). In context of MBC, as employee’s makes
use of mobile phones and WiFi access of firm is being utilized, this denotes that one wrong app
can make entire network vulnerable. Some application threats are mentioned beneath:
Spyware: This is responsible for utilizing or collection of sensitive information of users
without their approval and even knowledge that some irrelevant activities are being
conducted within their devices. Basically, information which is being attacked is in the
messages, contact list, browser history, photographs, etc.
The assessment which comprises of recognizing risks within firm, technologies utilized
by them along with processes for verification that whether all the controls are in place for
safeguarding system against security threats is referred to as security and risk assessment. Here,
emphasis is laid on preventing applications from any kind of defects and associated
vulnerabilities (Arora and Gigras, 2020). For understanding security aspects that are being
experienced by firms, MBC is taken into consideration that is a broadcasting firm who has given
their employees with permission to make use of their own devices like mobile phones. This
report gives an insight into security aspects, vulnerabilities and ways in which they can be
mitigated. In addition to this, availability of servers will also be analyzed along with impact on
security policies by employees and distinct auditing tools are also mentioned.
Task 1
Specify types of threats within mobile devices and vulnerability to destruction and abuse
Viruses and spyware creates influence on laptop and PC’s similarly there are various threats
which create an impact on mobile phones. The risk that creates an influence on organization on
the whole as well as their network is referred to as security threat. Two major reasons are there
for these risks, physical (stealing of devices) and non-physical risks (virus attacks, ransomware,
malware, Trojan horse, etc.). The mobile security threats which can impact overall network of
MBC firm are illustrated below:
Application based threats: People usually download apps which seems appealing to them
and it is always not necessary that they are from authorized persons. This denotes that
applications do not illustrate whether they have ransomware or any other vulnerability within
them for conducting illegal activities (Brashear, 2020). In context of MBC, as employee’s makes
use of mobile phones and WiFi access of firm is being utilized, this denotes that one wrong app
can make entire network vulnerable. Some application threats are mentioned beneath:
Spyware: This is responsible for utilizing or collection of sensitive information of users
without their approval and even knowledge that some irrelevant activities are being
conducted within their devices. Basically, information which is being attacked is in the
messages, contact list, browser history, photographs, etc.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Vulnerable applications: There are wide range of applications which have flaws within
them, it leads to exploitation of devices through which harmful activities are conducted.
Vulnerabilities assist attacker for furnishing access to private information. Malware: It denotes software that is responsible for conducting malicious operations
when they are being installed in mobile devices. They will make changes like sending
messages which will create an impact on their mobile phone bills, providing access to
third person to their accounts like Gmail or any other credential information stored within
them (Chopra and Chaudhary, 2020). This will be carried out without permission from
the user.
Web based threats: Mobile devices are mostly connected with internet for having access
to web services. Due to this different issues will be encountered by them in their mobile devices,
some of them are mentioned beneath:
Drive by downloads: It is liable for downloading applications automatically without
consent from mobile device owner. This is done when user visits the web page and it is
not essential they are being prompted to certain actions. Phishing scams: Facebook, text messages, email, instagram and Twitter is used to send
links for website. These links have been developed for tricking the users into their
webpage where they will enter their credentials and intruder will have those details (Ellis,
Hertig and Metscher, 2020). These are being used by them for carrying out
unauthenticated activities.
Security protection techniques and mitigation of risks within mobile devices
There are various organization that allow their employees to make use of mobile devices in the
working area. Some is done by MBC but they need to ensure that relevant strong policies and
security measures have been taken up by them to ensure that details about their network are not
accessed by third party or intruders. The reason behind this is that the threat associated with this
is very high as it is clear from above section (Hubbard, 2020). The methods that can be used by
MBC to ensure security of their operations are mentioned beneath:
Formulate of precise policies: When MBC allows mobile phones within working
structure, then need to ensure that adequate security policies have been developed. This
them, it leads to exploitation of devices through which harmful activities are conducted.
Vulnerabilities assist attacker for furnishing access to private information. Malware: It denotes software that is responsible for conducting malicious operations
when they are being installed in mobile devices. They will make changes like sending
messages which will create an impact on their mobile phone bills, providing access to
third person to their accounts like Gmail or any other credential information stored within
them (Chopra and Chaudhary, 2020). This will be carried out without permission from
the user.
Web based threats: Mobile devices are mostly connected with internet for having access
to web services. Due to this different issues will be encountered by them in their mobile devices,
some of them are mentioned beneath:
Drive by downloads: It is liable for downloading applications automatically without
consent from mobile device owner. This is done when user visits the web page and it is
not essential they are being prompted to certain actions. Phishing scams: Facebook, text messages, email, instagram and Twitter is used to send
links for website. These links have been developed for tricking the users into their
webpage where they will enter their credentials and intruder will have those details (Ellis,
Hertig and Metscher, 2020). These are being used by them for carrying out
unauthenticated activities.
Security protection techniques and mitigation of risks within mobile devices
There are various organization that allow their employees to make use of mobile devices in the
working area. Some is done by MBC but they need to ensure that relevant strong policies and
security measures have been taken up by them to ensure that details about their network are not
accessed by third party or intruders. The reason behind this is that the threat associated with this
is very high as it is clear from above section (Hubbard, 2020). The methods that can be used by
MBC to ensure security of their operations are mentioned beneath:
Formulate of precise policies: When MBC allows mobile phones within working
structure, then need to ensure that adequate security policies have been developed. This
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

must involve mandatory security settings, acceptable usage, adequate anti-theft measures,
etc. Along with this, activities which are being carried out within the network must be
monitored (PHONE SECURITY: 20 WAYS TO SECURE YOUR MOBILE PHONE,
2020).
Fragment information and applications on enterprise devices: Here, mobile device
users will be fragmented with respect to roles they have to carry out. This will aid MBC
to ensure that if device of one user has been attacked then only few devices within that
network will be accessed and not all (Janssen, 2020). Furthermore, unauthorized
applications will also not be installed in all the devices.
Encrypt and diminish visibility of devices: In case any of the mobile devices have been
compromised then information must not be accessed easily by intruder. This will prevent
mobile devices to be an entry point for attackers into MBC’s network. For this, they can
make use of identity & access management system.
Install security software in mobile devices: This implies primary as well as crucial
countermeasures which can be taken by MBC firm for allowing mobile. Security team
must consider those devices as any other hardware which is present within the working
premises.
Update mobile with security patches: Employees need to make sure that there devices
are up to date. The mobile devices furnish information related with updates for resolving
security threats or any kind of vulnerability (Wolf and Serpanos, 2020). This renders
adequate performance and security features.
Demonstrate how firm ensure availability of web service using Apache.
Linux is open source software which provides easy access to services. When Apache
(Linux web server) will be used by MBC then they will be able to create new threads which are
being concurrently associated. Apache is liable for supporting enhanced range of features that are
being executed as a separate module. The standardized medium that is utilized for propagating
communication among client as well as server applications on World Wide Web is referred to as
web server. MBC can make use of Apache Cassandra as this denotes availability above
consistency that will aid them to make sure that they render high availability to their users (Arora
and Gigras, 2020). Aspects associated with are specified beneath:
etc. Along with this, activities which are being carried out within the network must be
monitored (PHONE SECURITY: 20 WAYS TO SECURE YOUR MOBILE PHONE,
2020).
Fragment information and applications on enterprise devices: Here, mobile device
users will be fragmented with respect to roles they have to carry out. This will aid MBC
to ensure that if device of one user has been attacked then only few devices within that
network will be accessed and not all (Janssen, 2020). Furthermore, unauthorized
applications will also not be installed in all the devices.
Encrypt and diminish visibility of devices: In case any of the mobile devices have been
compromised then information must not be accessed easily by intruder. This will prevent
mobile devices to be an entry point for attackers into MBC’s network. For this, they can
make use of identity & access management system.
Install security software in mobile devices: This implies primary as well as crucial
countermeasures which can be taken by MBC firm for allowing mobile. Security team
must consider those devices as any other hardware which is present within the working
premises.
Update mobile with security patches: Employees need to make sure that there devices
are up to date. The mobile devices furnish information related with updates for resolving
security threats or any kind of vulnerability (Wolf and Serpanos, 2020). This renders
adequate performance and security features.
Demonstrate how firm ensure availability of web service using Apache.
Linux is open source software which provides easy access to services. When Apache
(Linux web server) will be used by MBC then they will be able to create new threads which are
being concurrently associated. Apache is liable for supporting enhanced range of features that are
being executed as a separate module. The standardized medium that is utilized for propagating
communication among client as well as server applications on World Wide Web is referred to as
web server. MBC can make use of Apache Cassandra as this denotes availability above
consistency that will aid them to make sure that they render high availability to their users (Arora
and Gigras, 2020). Aspects associated with are specified beneath:

Data availability by replicas: Cassandra is liable for creating multiple copies within
different clusters. It is done to make sure that even if one node is not responding then data
can be retrieved from other nodes without any issues. Cassandra furnishes information to
their users but it is up to date or not it cannot be ensured as sometimes server is
temporarily down.
Tunable consistency through Cassandra: To acknowledge issues faced in above
mentioned point, tunable consistency is preserved. In case write and read operations are
being conducted, user can depict the consistency level (Brashear, 2020). Quorum is used
for illustrating high consistency. As replicas have been created, the one which has been
updated at last can be provided to user as per their needs.
It will aid MBC to make sure that their services are available with high consistency through
the usage of Apache Cassandra. Furthermore, for firm can make use of different steps through
which they can amplify availability of web services.
Influence of employees of information security.
Within a firm, employees are there critical assets but they also make their operations
vulnerable. As per the analysis it has been identified that MBC can face enhanced risk from their
employees, they are mentioned below:
Risk from within: It occurs when employees of organization are careless or do not have
adequate knowledge related with security concerns. They act as biggest armor towards
cyberattack which takes place within the firm (Chopra and Chaudhary, 2020). The reason
behind this is that mobile devices are lost then by making use of credentials of employees crucial
information of firm can be stolen which may hamper overall operations of organization.
Cybersecurity incidents due to employees: Inappropriate data is being sent by employees
through usage of firms Wi-Fi in case intruder get access to their mobile devices then entire
network can be tracked which can create a worse impact on organization as all their activities can
be monitored. Along with this they also put sensitive information on system without any security
measures either carelessly or accidently (The Human Factor in IT Security: How Employees
are Making Businesses Vulnerable from Within. 2020). This is caused due to inadequate
training given to them.
different clusters. It is done to make sure that even if one node is not responding then data
can be retrieved from other nodes without any issues. Cassandra furnishes information to
their users but it is up to date or not it cannot be ensured as sometimes server is
temporarily down.
Tunable consistency through Cassandra: To acknowledge issues faced in above
mentioned point, tunable consistency is preserved. In case write and read operations are
being conducted, user can depict the consistency level (Brashear, 2020). Quorum is used
for illustrating high consistency. As replicas have been created, the one which has been
updated at last can be provided to user as per their needs.
It will aid MBC to make sure that their services are available with high consistency through
the usage of Apache Cassandra. Furthermore, for firm can make use of different steps through
which they can amplify availability of web services.
Influence of employees of information security.
Within a firm, employees are there critical assets but they also make their operations
vulnerable. As per the analysis it has been identified that MBC can face enhanced risk from their
employees, they are mentioned below:
Risk from within: It occurs when employees of organization are careless or do not have
adequate knowledge related with security concerns. They act as biggest armor towards
cyberattack which takes place within the firm (Chopra and Chaudhary, 2020). The reason
behind this is that mobile devices are lost then by making use of credentials of employees crucial
information of firm can be stolen which may hamper overall operations of organization.
Cybersecurity incidents due to employees: Inappropriate data is being sent by employees
through usage of firms Wi-Fi in case intruder get access to their mobile devices then entire
network can be tracked which can create a worse impact on organization as all their activities can
be monitored. Along with this they also put sensitive information on system without any security
measures either carelessly or accidently (The Human Factor in IT Security: How Employees
are Making Businesses Vulnerable from Within. 2020). This is caused due to inadequate
training given to them.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Illustration 1: Security event experienced
There are different risks that are being faced by organization but cyber attacks like Trojan
horse, virus, hardware theft, etc. creates an adverse impact as they alter information, deletes it or
make their use for carrying out unauthorized activities (Ellis, Hertig and Metscher, 2020). MBC
must carry out mandatory training for all the employees so that they can have idea about impact
that is being created by their activities and how they can be prevented before it creates worst
impact.
Illustrate Linux server auditing tools along with ways through which they can be used by MBC.
Auditing is crucial for ensuring that complete security is being maintained within
operations carried out by firm. In context of MBC, they have opted to make use of different
monitoring tools for making sure that they have adequate knowledge about activities conducted
within the network. They are as:
Nagios: This is open source tool which is being utilised for managing log data which will
assists MBC in gathering of data by furnishing adequate information to system
administrators as well as this can be used to monitor security of their local networks
(Janssen, 2020).
Fluentd: As firm have different departments who carry out different operations and they
are directly or indirectly associated with each other. This implies that there has to be
There are different risks that are being faced by organization but cyber attacks like Trojan
horse, virus, hardware theft, etc. creates an adverse impact as they alter information, deletes it or
make their use for carrying out unauthorized activities (Ellis, Hertig and Metscher, 2020). MBC
must carry out mandatory training for all the employees so that they can have idea about impact
that is being created by their activities and how they can be prevented before it creates worst
impact.
Illustrate Linux server auditing tools along with ways through which they can be used by MBC.
Auditing is crucial for ensuring that complete security is being maintained within
operations carried out by firm. In context of MBC, they have opted to make use of different
monitoring tools for making sure that they have adequate knowledge about activities conducted
within the network. They are as:
Nagios: This is open source tool which is being utilised for managing log data which will
assists MBC in gathering of data by furnishing adequate information to system
administrators as well as this can be used to monitor security of their local networks
(Janssen, 2020).
Fluentd: As firm have different departments who carry out different operations and they
are directly or indirectly associated with each other. This implies that there has to be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

centralized system which will also aid to monitor entire performance. Fluentd will
provide firm with robust solution for collecting information as well as organize it by
making use of different pipelines (Hubbard, 2020). Through this, MBC can extend data in
all their application and will also minimize effort for carrying out analysis.
There are many other tools such as Linux Dash which is being used for monitoring linux
server performance, Wireshark, etc.
Task 2
Conception of two directories in Linux
This part illustrates commands which will be utilized for creating two directories in
directory named SBM4304, they are shown beneath:
i. Create a directory named SBM4304
mkdir SBM4304
ii. Change the directory to SBM4304 from root directory
cd SBM4304
iii. Create two directories with name StudentID1 and StudentID2 in SBM4304 directory
mkdir StudentID1
mkdir StudentID2
iv. For checking whether directories have been created or not
ls
v. Change directory to root
cd ls –l
vi. To check permissions of directories
ls –l
vii. For changing pernissions of SBM4304 for giving complete access
provide firm with robust solution for collecting information as well as organize it by
making use of different pipelines (Hubbard, 2020). Through this, MBC can extend data in
all their application and will also minimize effort for carrying out analysis.
There are many other tools such as Linux Dash which is being used for monitoring linux
server performance, Wireshark, etc.
Task 2
Conception of two directories in Linux
This part illustrates commands which will be utilized for creating two directories in
directory named SBM4304, they are shown beneath:
i. Create a directory named SBM4304
mkdir SBM4304
ii. Change the directory to SBM4304 from root directory
cd SBM4304
iii. Create two directories with name StudentID1 and StudentID2 in SBM4304 directory
mkdir StudentID1
mkdir StudentID2
iv. For checking whether directories have been created or not
ls
v. Change directory to root
cd ls –l
vi. To check permissions of directories
ls –l
vii. For changing pernissions of SBM4304 for giving complete access
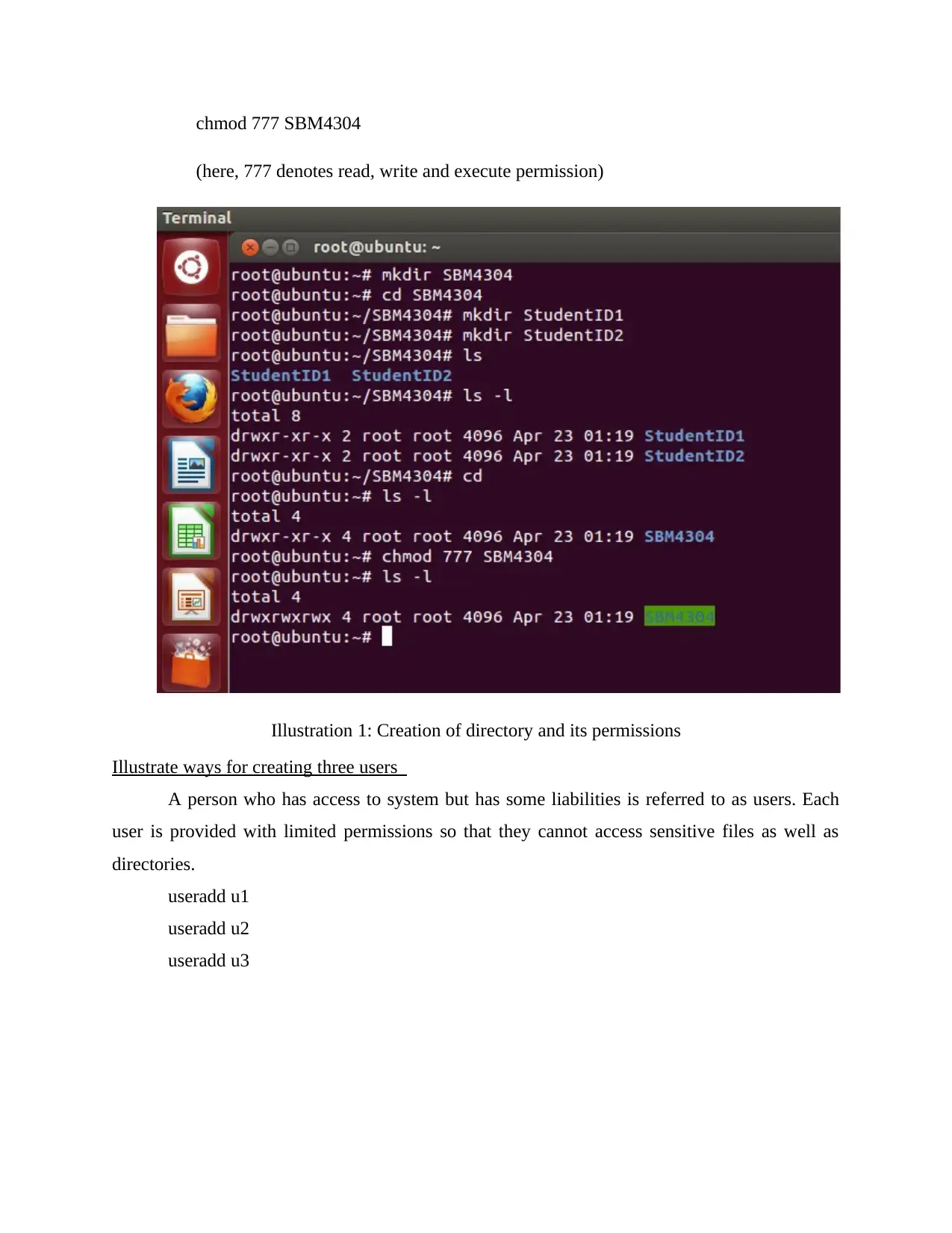
chmod 777 SBM4304
(here, 777 denotes read, write and execute permission)
Illustration 1: Creation of directory and its permissions
Illustrate ways for creating three users
A person who has access to system but has some liabilities is referred to as users. Each
user is provided with limited permissions so that they cannot access sensitive files as well as
directories.
useradd u1
useradd u2
useradd u3
(here, 777 denotes read, write and execute permission)
Illustration 1: Creation of directory and its permissions
Illustrate ways for creating three users
A person who has access to system but has some liabilities is referred to as users. Each
user is provided with limited permissions so that they cannot access sensitive files as well as
directories.
useradd u1
useradd u2
useradd u3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Illustration 2: Users
Conclusion
From above, it has been identified that, process that is associated with making use of
information technology for delivering different services by taking assessing and mitigating risks
for maintenance of integrity, confidentiality and availability is referred to as security and risk
management. There are wide ranges of threats which can hamper mobile devices and even steal
information present within them, it is essential for firms to formulate adequate procedures by
which attacks can be controlled or completely eradicated. Furthermore, firm need to ensure that
services furnished by them can be accessed by users thereby ensuring that their web servers are
available. Moreover auditing tools can be used to monitor performance of their servers.
Conclusion
From above, it has been identified that, process that is associated with making use of
information technology for delivering different services by taking assessing and mitigating risks
for maintenance of integrity, confidentiality and availability is referred to as security and risk
management. There are wide ranges of threats which can hamper mobile devices and even steal
information present within them, it is essential for firms to formulate adequate procedures by
which attacks can be controlled or completely eradicated. Furthermore, firm need to ensure that
services furnished by them can be accessed by users thereby ensuring that their web servers are
available. Moreover auditing tools can be used to monitor performance of their servers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Books and Journal
Arora, M. and Gigras, Y., 2020. Security, Privacy, Forensics Analysis for Smartphones.
In Forensic Investigations and Risk Management in Mobile and Wireless
Communications (pp. 1-25). IGI Global.
Brashear, J.P., 2020. Managing Risk to Critical Infrastructures, Their Interdependencies, and the
Region They Serve: A Risk Management Process. In Optimizing Community
Infrastructure (pp. 41-67). Butterworth-Heinemann.
Chopra, A. and Chaudhary, M., 2020. Risk Management Approach. In Implementing an
Information Security Management System (pp. 77-102). Apress, Berkeley, CA.
Ellis, J., Hertig, C.A. and Metscher, R., 2020. Concepts and Evolution of Asset Protection and
Security. In The Professional Protection Officer (pp. 3-18). Butterworth-Heinemann.
Hubbard, D.W., 2020. The failure of risk management: Why it's broken and how to fix it. John
Wiley & Sons.
Janssen, S.A.M., 2020. Capturing Agents in Security Models: Agent-based Security Risk
Management using Causal Discovery.
Wolf, M. and Serpanos, D., 2020. Safety and Security Design Processes. In Safe and Secure
Cyber-Physical Systems and Internet-of-Things Systems (pp. 11-33). Springer, Cham.
Online
PHONE SECURITY: 20 WAYS TO SECURE YOUR MOBILE PHONE. 2020. [Online].
Available through: <https://preyproject.com/blog/en/phone-security-20-ways-to-secure-
your-mobile-phone/>.
The Human Factor in IT Security: How Employees are Making Businesses Vulnerable from
Within. 2020. [Online]. Available through: <https://www.kaspersky.com/blog/the-
human-factor-in-it-security/>.
Books and Journal
Arora, M. and Gigras, Y., 2020. Security, Privacy, Forensics Analysis for Smartphones.
In Forensic Investigations and Risk Management in Mobile and Wireless
Communications (pp. 1-25). IGI Global.
Brashear, J.P., 2020. Managing Risk to Critical Infrastructures, Their Interdependencies, and the
Region They Serve: A Risk Management Process. In Optimizing Community
Infrastructure (pp. 41-67). Butterworth-Heinemann.
Chopra, A. and Chaudhary, M., 2020. Risk Management Approach. In Implementing an
Information Security Management System (pp. 77-102). Apress, Berkeley, CA.
Ellis, J., Hertig, C.A. and Metscher, R., 2020. Concepts and Evolution of Asset Protection and
Security. In The Professional Protection Officer (pp. 3-18). Butterworth-Heinemann.
Hubbard, D.W., 2020. The failure of risk management: Why it's broken and how to fix it. John
Wiley & Sons.
Janssen, S.A.M., 2020. Capturing Agents in Security Models: Agent-based Security Risk
Management using Causal Discovery.
Wolf, M. and Serpanos, D., 2020. Safety and Security Design Processes. In Safe and Secure
Cyber-Physical Systems and Internet-of-Things Systems (pp. 11-33). Springer, Cham.
Online
PHONE SECURITY: 20 WAYS TO SECURE YOUR MOBILE PHONE. 2020. [Online].
Available through: <https://preyproject.com/blog/en/phone-security-20-ways-to-secure-
your-mobile-phone/>.
The Human Factor in IT Security: How Employees are Making Businesses Vulnerable from
Within. 2020. [Online]. Available through: <https://www.kaspersky.com/blog/the-
human-factor-in-it-security/>.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




