Article Analysis: “Towards a System for Complex Analysis of Security Events in Large-Scale Networks”
VerifiedAdded on 2022/08/16
|17
|981
|20
Presentation
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Authors: Andrey Sapegin , David Jaeger, Feng Cheng, Christoph
Meinel
ARTICLE ANALYSIS: “TOWARDS A
SYSTEM FOR COMPLEX
ANALYSIS OF
SECURITY EVENTS IN LARGE-
SCALE NETWORKS”
Meinel
ARTICLE ANALYSIS: “TOWARDS A
SYSTEM FOR COMPLEX
ANALYSIS OF
SECURITY EVENTS IN LARGE-
SCALE NETWORKS”
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1. INTRODUCTION:
• Approximately after twenty years of development, current SIEM or
Security Information and Event Management, there are problems with
normalization of the data sources that are heterogeneous in nature.
Further, there are various fake positive warnings and prolonged times
particularly under large-scale networks under huge amounts of different
security events.
• The following study deals with the review of the given article that deals
with the present system related to complex assessment regarding
different security events present under large-scale networks.
• Approximately after twenty years of development, current SIEM or
Security Information and Event Management, there are problems with
normalization of the data sources that are heterogeneous in nature.
Further, there are various fake positive warnings and prolonged times
particularly under large-scale networks under huge amounts of different
security events.
• The following study deals with the review of the given article that deals
with the present system related to complex assessment regarding
different security events present under large-scale networks.

2. BACKGROUND OF THE STUDY:
• The SIEM or the innovation of “Security Information and Event
Management” systems is seen to be coming out during late 90s for
regulating and then centralize managing of security of various data flows
under enterprise network.
• The article demonstrates the prototypes of SIEM systems combining most
novel type of technologies related to data analysis and processing and
then evaluates detailed concerns.
• The SIEM or the innovation of “Security Information and Event
Management” systems is seen to be coming out during late 90s for
regulating and then centralize managing of security of various data flows
under enterprise network.
• The article demonstrates the prototypes of SIEM systems combining most
novel type of technologies related to data analysis and processing and
then evaluates detailed concerns.

3. CONTRIBUTIONS OF THE PRESET WORK:
• There has been every log messages that are found to be coming to the
system has been converted from the heterogeneous origins to a unique
format.
• Analysis module of that system has deployed an innovative hybrid
approach towards effective security analytics.
• Novel algorithm has been proposed that s helpful for the unsupervised
anomaly findings.
• There has been every log messages that are found to be coming to the
system has been converted from the heterogeneous origins to a unique
format.
• Analysis module of that system has deployed an innovative hybrid
approach towards effective security analytics.
• Novel algorithm has been proposed that s helpful for the unsupervised
anomaly findings.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4. UNDERSTANDING ISSUES WITH CURRENT SIEM
SYSTEMS AND METHODS TO DETECT ANOMALY:
• Firstly, heterogeneous kinds of data generates various issues.
• Secondly, there are problems regarding Big Data or high data volumes.
• Thirdly, most of SIEM systems are on market deploying solely the
signature-based approach originating from the IDSs.
SYSTEMS AND METHODS TO DETECT ANOMALY:
• Firstly, heterogeneous kinds of data generates various issues.
• Secondly, there are problems regarding Big Data or high data volumes.
• Thirdly, most of SIEM systems are on market deploying solely the
signature-based approach originating from the IDSs.

5. DISCUSSION ON ANALYTICS OF REAL
EVENT AND MONITORING THE SYSTEM:
• Here, the specific system has been supporting an effective collection of
different types of security events originating from various sources.
• This involves the GNU/Linux and various hosts of Windows, controller of
domains and additional Log management systems and SIEM.
EVENT AND MONITORING THE SYSTEM:
• Here, the specific system has been supporting an effective collection of
different types of security events originating from various sources.
• This involves the GNU/Linux and various hosts of Windows, controller of
domains and additional Log management systems and SIEM.

6. ANALYTICAL ABILITIES OF REAMS:
• The signatures are implemented prior the persistence of data to
database.
• As the normalized logs are there in the database, the anomaly and query-
based analytics are implemented to retrieve much more data from the
information.
• The signatures are implemented prior the persistence of data to
database.
• As the normalized logs are there in the database, the anomaly and query-
based analytics are implemented to retrieve much more data from the
information.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7. KDD CUP 1999 DATA AND
REALWINDOWS EVENT DATASET:
• The primary data for the research came from a huge multinational
organization.
• This comprised of the Windows Events from various Domain Controllers
and ArcSight.
REALWINDOWS EVENT DATASET:
• The primary data for the research came from a huge multinational
organization.
• This comprised of the Windows Events from various Domain Controllers
and ArcSight.

8. FINDING AND CATEGORIZATION OF
SUSPICIOUS HAPPENINGS IN THE
INFORMATION:
• This can be understood from the following table:
SUSPICIOUS HAPPENINGS IN THE
INFORMATION:
• This can be understood from the following table:
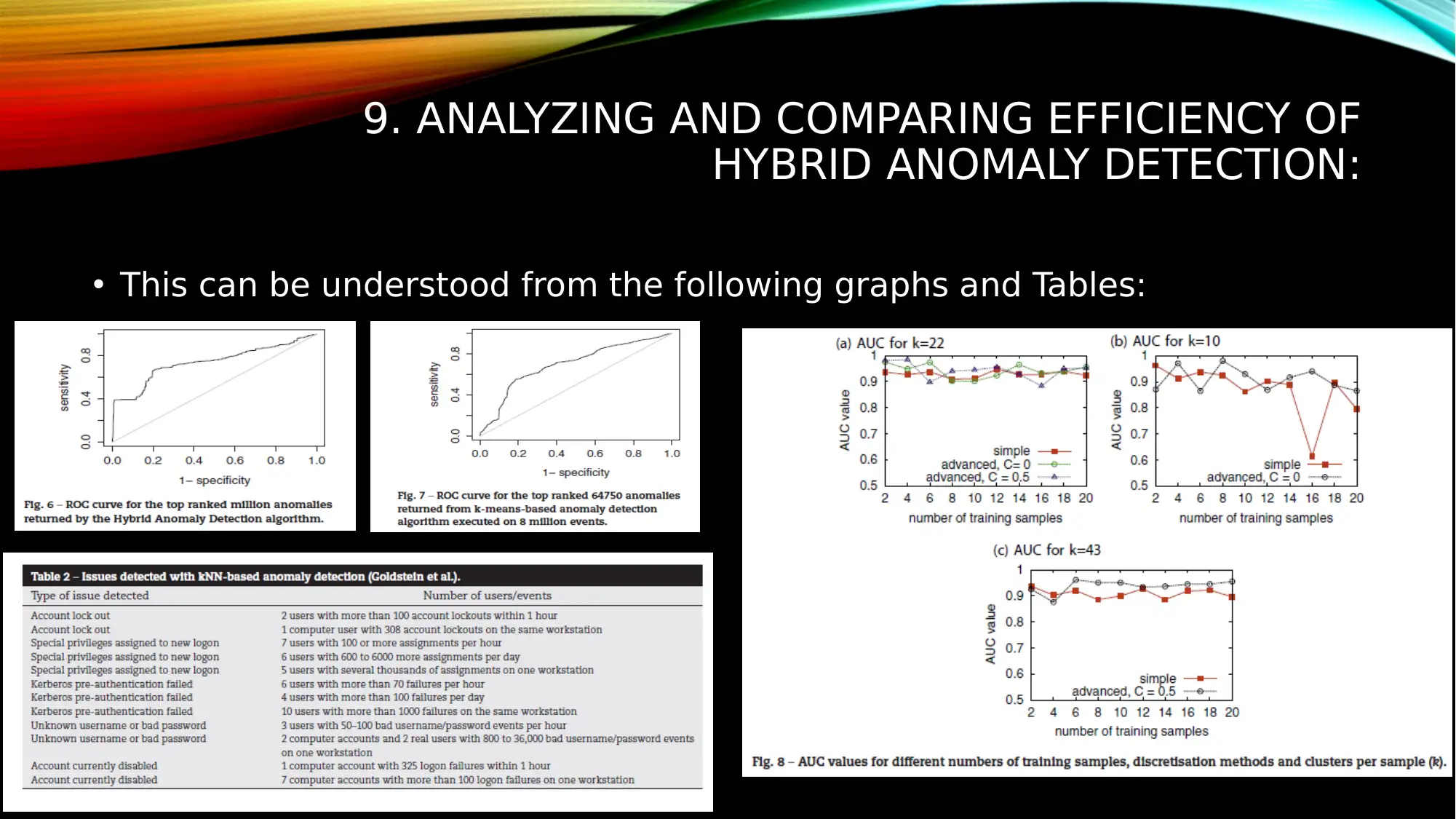
9. ANALYZING AND COMPARING EFFICIENCY OF
HYBRID ANOMALY DETECTION:
• This can be understood from the following graphs and Tables:
HYBRID ANOMALY DETECTION:
• This can be understood from the following graphs and Tables:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10. DETECTION PROCESS OF MALICIOUS
ACTIVITY:
The system has applied the hybrid approach using three distinct kinds of
assessments.
• Unsupervised anomaly detection
• Queries
• Signatures
ACTIVITY:
The system has applied the hybrid approach using three distinct kinds of
assessments.
• Unsupervised anomaly detection
• Queries
• Signatures

11. RECOMMENDATIONS TO USE RANKED
OUTCOMES
• Apart from the anomaly detection, the signatures and queries of
information sources for operator of SIEM system apart from standard
method to assess output of anomaly-based module of detection.
OUTCOMES
• Apart from the anomaly detection, the signatures and queries of
information sources for operator of SIEM system apart from standard
method to assess output of anomaly-based module of detection.

12. IMPROVEMENT OF PRIOR TASKS:
• Implementing negative binomial model
• Developing an efficient novel hybrid approach that has been assimilating
the smart vector-space model.
• Implementing negative binomial model
• Developing an efficient novel hybrid approach that has been assimilating
the smart vector-space model.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13. WAYS TO AVOID LONG TIME OF
COMPUTATION:
• Smaller cluster and samples are build separately to create the ensemble of
the various SVM models. This lies on the helpful concept vectors of the
different identified clusters.
• Here, eight samples from 100,000 events are considered. Moreover, every
body for the phase of training is used, that covers just 6.5% of the overall
dataset.
• Nevertheless the aim is never to find every anomalies.
• It has intended to the return of utmost types of suspicious activities
originating from data for any operator of the present SIEM system. The
algorithm suggested is largely scalable in nature and can be parallelised
further for gaining greater coverage. This is on the dataset through training
data.
COMPUTATION:
• Smaller cluster and samples are build separately to create the ensemble of
the various SVM models. This lies on the helpful concept vectors of the
different identified clusters.
• Here, eight samples from 100,000 events are considered. Moreover, every
body for the phase of training is used, that covers just 6.5% of the overall
dataset.
• Nevertheless the aim is never to find every anomalies.
• It has intended to the return of utmost types of suspicious activities
originating from data for any operator of the present SIEM system. The
algorithm suggested is largely scalable in nature and can be parallelised
further for gaining greater coverage. This is on the dataset through training
data.

14. TESTING OF THE SYSTEM:
• The system is tested on real dataset originating from huge multinational organization.
• Here, different problems under the data are identified through deploying the three
measures like anomaly detection, queries and signatures. Performance of algorithms
and architecture permitted to assess one hundred sixty million log messages.
• It has covered a three month time in few days. As a comparison is made with the
present approaches towards anomaly detection, the suggested Hybrid Anomaly
Detection generates various relevant outcomes.
• It never needs to feature the re-processing and working quicker than different other
types of solutions.
• Deployment of the algorithm suggested on KDD Cup 1999 data has taken place. This
has also proved the efficiency. Besides, the algorithm has been capable of assessing
any sort of information. This includes the textual fields and also constant numerical
values. This is due to enhanced feature of the discretisation measures.
• The system is tested on real dataset originating from huge multinational organization.
• Here, different problems under the data are identified through deploying the three
measures like anomaly detection, queries and signatures. Performance of algorithms
and architecture permitted to assess one hundred sixty million log messages.
• It has covered a three month time in few days. As a comparison is made with the
present approaches towards anomaly detection, the suggested Hybrid Anomaly
Detection generates various relevant outcomes.
• It never needs to feature the re-processing and working quicker than different other
types of solutions.
• Deployment of the algorithm suggested on KDD Cup 1999 data has taken place. This
has also proved the efficiency. Besides, the algorithm has been capable of assessing
any sort of information. This includes the textual fields and also constant numerical
values. This is due to enhanced feature of the discretisation measures.

15. CONCLUSION:
• In this way, both algorithms and architectures utilized in the SIEM system
prototype has been largely relevant for the analysis of security of Big
Data. It could also be implemented also to huge networks of enterprises.
This is assure that the finding of malicious activities traced under log
measures.
• In this way, both algorithms and architectures utilized in the SIEM system
prototype has been largely relevant for the analysis of security of Big
Data. It could also be implemented also to huge networks of enterprises.
This is assure that the finding of malicious activities traced under log
measures.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

REFERENCE:
Sapegin, A., Jaeger, D., Cheng, F. and Meinel, C., 2017. Towards a system
for complex analysis of security events in large-scale networks. Computers
& Security, 67, pp.16-34.
Sapegin, A., Jaeger, D., Cheng, F. and Meinel, C., 2017. Towards a system
for complex analysis of security events in large-scale networks. Computers
& Security, 67, pp.16-34.
1 out of 17
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.
