CS 335 Computer Network Assignment Solutions: Detailed Analysis
VerifiedAdded on 2022/08/25
|6
|1494
|24
Homework Assignment
AI Summary
This document contains detailed solutions to a CS 335 computer network assignment. The solutions cover a range of topics, including the effectiveness of parity checks in detecting errors, the limitations of the Stop-and-Wait protocol in satellite communication, and the determination of an appropriate subnet mask for a given IP address and subnet requirements. The document also differentiates between link-state and distance vector routing protocols, analyzes the role of specific IP fields (Identifier, Don't Fragment, and Time to Live) across different network entities, explains datagram fragmentation and reassembly, calculates Ethernet fragment sizes, determines packet transmission rates, and analyzes the buffer space needed for fragment reassembly. Finally, it explains Address Resolution Protocol (ARP) and performs a bandwidth calculation to determine window size.

Solution 1
A single parity check code is used in ASCII, characters are represented by 7 bits, as well as the
eighth bit is the parity bit. A straightforward equality check code can distinguish all single-piece
blunders. You can likewise recognize numerous mistakes just if the all out numbest of
information unit blunders is odd.
Solution 2
For the Stop-as well as-Wait protocol, after the frame is sent, the transmitter waits for an
acknowledgement from the receiver before sending the next frame. This protocol works
efficiently for frames with a propagation time that is shorter than the transmission time of the
frames.
Solution 3
The given IP address belongs to Class C network.
The default subnet mask of class C is 255.255.255.0
As we want four subnets to use, we can borrow two bit from the host bits in the given IP address
the new net mask would be 255.255.255.192 remaining host bits = 26 = 32
Since, the maximum number of hosts that exist per subnet will be 25. So the 255.255.255.192
subnet mask fulfills our requirement. It creates four subnets as well as 32 hosts per network.
Hence the subnet mask used by administrator would be = 255.255.255.192
Solution 4
Please find below the difference between the Distance Vector as well as Link State Routing
Distance Vector
· The Distance Vector directing convention depends on the Bellma and Ford calculations.
· The Distance Vector directing convention isn't versatile, for instance, RIP underpins 16
bounces and IGRP bolsters up to 100 jumps.
A single parity check code is used in ASCII, characters are represented by 7 bits, as well as the
eighth bit is the parity bit. A straightforward equality check code can distinguish all single-piece
blunders. You can likewise recognize numerous mistakes just if the all out numbest of
information unit blunders is odd.
Solution 2
For the Stop-as well as-Wait protocol, after the frame is sent, the transmitter waits for an
acknowledgement from the receiver before sending the next frame. This protocol works
efficiently for frames with a propagation time that is shorter than the transmission time of the
frames.
Solution 3
The given IP address belongs to Class C network.
The default subnet mask of class C is 255.255.255.0
As we want four subnets to use, we can borrow two bit from the host bits in the given IP address
the new net mask would be 255.255.255.192 remaining host bits = 26 = 32
Since, the maximum number of hosts that exist per subnet will be 25. So the 255.255.255.192
subnet mask fulfills our requirement. It creates four subnets as well as 32 hosts per network.
Hence the subnet mask used by administrator would be = 255.255.255.192
Solution 4
Please find below the difference between the Distance Vector as well as Link State Routing
Distance Vector
· The Distance Vector directing convention depends on the Bellma and Ford calculations.
· The Distance Vector directing convention isn't versatile, for instance, RIP underpins 16
bounces and IGRP bolsters up to 100 jumps.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Link State
· The connection state steering convention depends on the Dijkstra calculation.
· The connection state steering convention is truly adaptable and underpins endless bounces.
Solution 5
The IP entity in the source may need the identification as well as don't-fragment parameters as
well as it may not require the time-to-live parameter. The identifier as well as don’t fragment
identifier is used in fragmentation. The identification field (ID) is used to identify datagram
fragments for reassembly as well as the don’t fragment identifier indicates whether IP can
fragment data or not. Since the sender sets some time-to-live value, the IP source entity need not
look at the TTL parameter.
The IP entities of the intermediate routers need to examine the Time-to-live, Identifier as well as
don't-fragment parameters. ID as well as Don't-fragment parameters are to be examined if
fragmentation is desired, as well as TTL is to be examined since every module that processes a
datagram must decrease the TTL by at least one.
Solution 6
Datagram fragmentation:
• The datagram fragmentation is the process to divide the data packet into small ones when the
data packets are larger than the maximum length of a particular system.
Reassembly:
• Reassembly is a process of reassembling the pieces of packets into original packets in the
receiving system.
Datagram fragmentation as well as reassembly in wrong order data arrival:
• The fragmented datagram arrives as intact as well as then it has the possibility for wrong order
of datagram arrival.
· The connection state steering convention depends on the Dijkstra calculation.
· The connection state steering convention is truly adaptable and underpins endless bounces.
Solution 5
The IP entity in the source may need the identification as well as don't-fragment parameters as
well as it may not require the time-to-live parameter. The identifier as well as don’t fragment
identifier is used in fragmentation. The identification field (ID) is used to identify datagram
fragments for reassembly as well as the don’t fragment identifier indicates whether IP can
fragment data or not. Since the sender sets some time-to-live value, the IP source entity need not
look at the TTL parameter.
The IP entities of the intermediate routers need to examine the Time-to-live, Identifier as well as
don't-fragment parameters. ID as well as Don't-fragment parameters are to be examined if
fragmentation is desired, as well as TTL is to be examined since every module that processes a
datagram must decrease the TTL by at least one.
Solution 6
Datagram fragmentation:
• The datagram fragmentation is the process to divide the data packet into small ones when the
data packets are larger than the maximum length of a particular system.
Reassembly:
• Reassembly is a process of reassembling the pieces of packets into original packets in the
receiving system.
Datagram fragmentation as well as reassembly in wrong order data arrival:
• The fragmented datagram arrives as intact as well as then it has the possibility for wrong order
of datagram arrival.

• Even though the datagram arrives in wrong order, the TCP (Transmission Control Protocol)
should be prepared to reassemble the parts of a message in proper order.
Solution 7
Consider a 4480-octet datagram.
The maximum payload of an Ethernet = 1500 octets.
The datagram has 20 octets of IP header. Then, the remaining bytes of the datagram are 4480-20
= 4460 octets.
The datagram of the Ethernet has 20 octets of IP header. Then, the remaining bytes of the
datagram of the Ethernet is 1500-20 = 1480 octets.
Therefore, the data of 1480 octets can transfer through the Ethernet at a time.
Now, fragment the 4460-octet diagram to get each fragment of data 1480-octet.
Let the number of fragments is 3 as well as each of 1480 octets.
Then, the total octets of the fragments are 3x1480 = 4440 octets.
The remaining octets of the datagram can be a fragment of data (4460 – 4440) = 20 octets.
Therefore, to transmit the data through the Ethernet, it requires 4 fragments. Three fragments of
data 1480 each as well as the fourth fragment of data of sum of the remaining octets of the
datagram as well as octets of the IP header. That is 20+20 = 40 octets.
Let the 4 fragments are Fragment 1, Fragment 2, Fragment 3, as well as Fragment 4.
The length of the first three fragments is 1480 octets as well as the length of the fourth fragment
is 40 octets.
The Offset of a fragment is multiple of 8 octets. Therefore, the offset of the fragment is 1480/8 =
185.
The data transmission starts with an offset of 0. Then, the offsets of the fragments will as below:
should be prepared to reassemble the parts of a message in proper order.
Solution 7
Consider a 4480-octet datagram.
The maximum payload of an Ethernet = 1500 octets.
The datagram has 20 octets of IP header. Then, the remaining bytes of the datagram are 4480-20
= 4460 octets.
The datagram of the Ethernet has 20 octets of IP header. Then, the remaining bytes of the
datagram of the Ethernet is 1500-20 = 1480 octets.
Therefore, the data of 1480 octets can transfer through the Ethernet at a time.
Now, fragment the 4460-octet diagram to get each fragment of data 1480-octet.
Let the number of fragments is 3 as well as each of 1480 octets.
Then, the total octets of the fragments are 3x1480 = 4440 octets.
The remaining octets of the datagram can be a fragment of data (4460 – 4440) = 20 octets.
Therefore, to transmit the data through the Ethernet, it requires 4 fragments. Three fragments of
data 1480 each as well as the fourth fragment of data of sum of the remaining octets of the
datagram as well as octets of the IP header. That is 20+20 = 40 octets.
Let the 4 fragments are Fragment 1, Fragment 2, Fragment 3, as well as Fragment 4.
The length of the first three fragments is 1480 octets as well as the length of the fourth fragment
is 40 octets.
The Offset of a fragment is multiple of 8 octets. Therefore, the offset of the fragment is 1480/8 =
185.
The data transmission starts with an offset of 0. Then, the offsets of the fragments will as below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
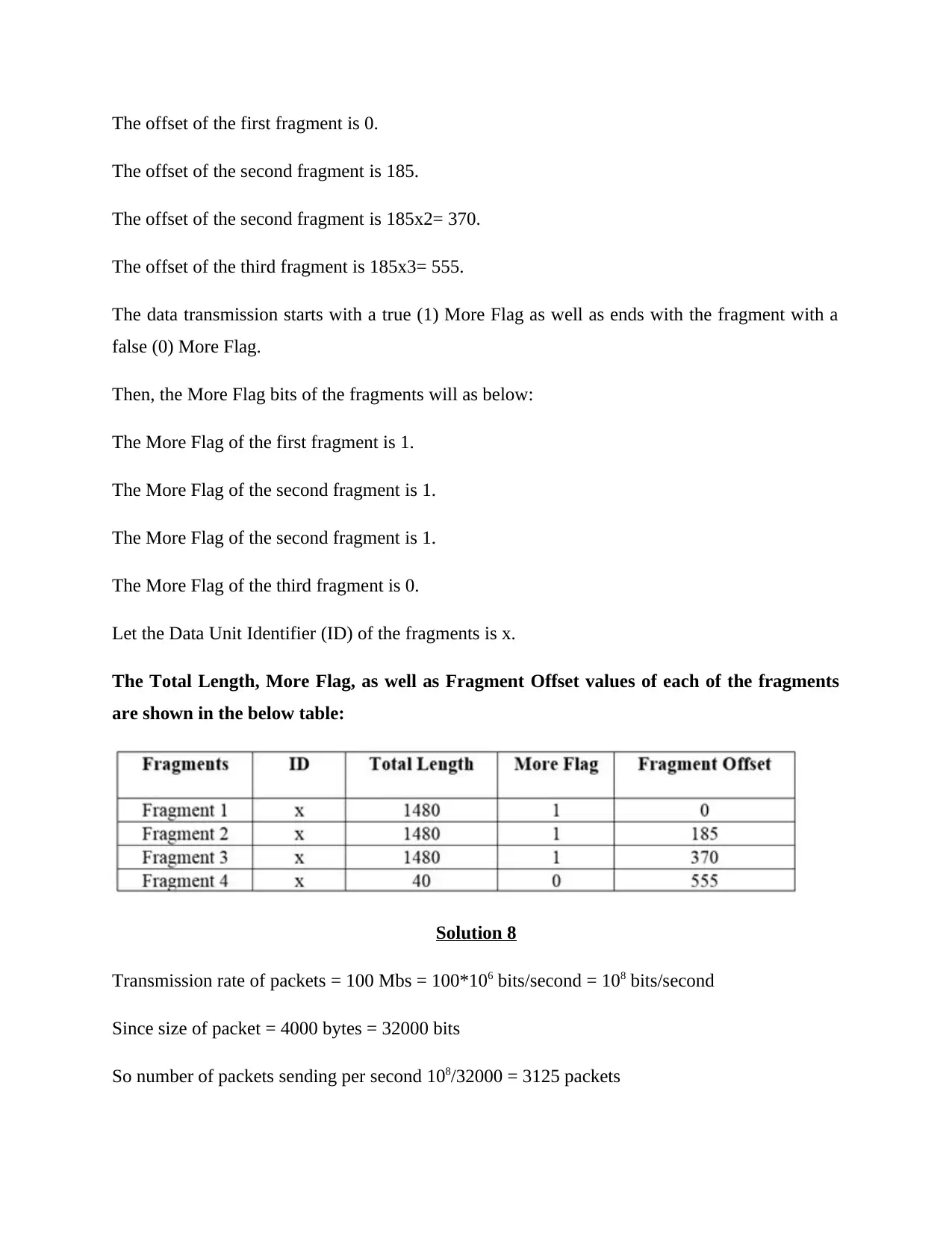
The offset of the first fragment is 0.
The offset of the second fragment is 185.
The offset of the second fragment is 185x2= 370.
The offset of the third fragment is 185x3= 555.
The data transmission starts with a true (1) More Flag as well as ends with the fragment with a
false (0) More Flag.
Then, the More Flag bits of the fragments will as below:
The More Flag of the first fragment is 1.
The More Flag of the second fragment is 1.
The More Flag of the second fragment is 1.
The More Flag of the third fragment is 0.
Let the Data Unit Identifier (ID) of the fragments is x.
The Total Length, More Flag, as well as Fragment Offset values of each of the fragments
are shown in the below table:
Solution 8
Transmission rate of packets = 100 Mbs = 100*106 bits/second = 108 bits/second
Since size of packet = 4000 bytes = 32000 bits
So number of packets sending per second 108/32000 = 3125 packets
The offset of the second fragment is 185.
The offset of the second fragment is 185x2= 370.
The offset of the third fragment is 185x3= 555.
The data transmission starts with a true (1) More Flag as well as ends with the fragment with a
false (0) More Flag.
Then, the More Flag bits of the fragments will as below:
The More Flag of the first fragment is 1.
The More Flag of the second fragment is 1.
The More Flag of the second fragment is 1.
The More Flag of the third fragment is 0.
Let the Data Unit Identifier (ID) of the fragments is x.
The Total Length, More Flag, as well as Fragment Offset values of each of the fragments
are shown in the below table:
Solution 8
Transmission rate of packets = 100 Mbs = 100*106 bits/second = 108 bits/second
Since size of packet = 4000 bytes = 32000 bits
So number of packets sending per second 108/32000 = 3125 packets
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Since each packet is decomposed to 4 fragments, hence number of fragments sended per second
= 3125*4 = 13000 fragments per second
Now since among 13000 fragments are sended per second as well as every 100 such packets are
discarded.
Since in 5 seconds, there will be 13000*5 = 65000 fragments sended over, out of which 100*5 =
500 fragments are discarded.
Hence number of fragments arrived at host in 5 seconds = 65000 - 500 = 64500 fragments.
So buffer space should be sufficient to accommodate 64500 fragments each of size 1000 bytes.
Hence amount of buffer space needed = 64500*1000 bytes = 64500000 bytes
Solution 9
Address resolution protocol (ARP):
· The system interface card in the information connect layer doesn't perceive the Internet
Protocol (IP) address.
· ARP is a convention used to determine this issue by giving an IP address at the system layer to
get the Ethernet address of a machine in the system.
· subsequently, administration demands are not just used to process demands from the upper
layer of the vehicle layer, yet in addition gave to the lower layer of the system that is the
information interface layer.
Hence, ARP is a piece of the system layer and not part of the information interface layer offers
types of assistance to the vehicle layer.
Solution 10
Given data:
Bandwidth = 64 kbps =64×1024 bps
Data frames = 512 bytes
= 3125*4 = 13000 fragments per second
Now since among 13000 fragments are sended per second as well as every 100 such packets are
discarded.
Since in 5 seconds, there will be 13000*5 = 65000 fragments sended over, out of which 100*5 =
500 fragments are discarded.
Hence number of fragments arrived at host in 5 seconds = 65000 - 500 = 64500 fragments.
So buffer space should be sufficient to accommodate 64500 fragments each of size 1000 bytes.
Hence amount of buffer space needed = 64500*1000 bytes = 64500000 bytes
Solution 9
Address resolution protocol (ARP):
· The system interface card in the information connect layer doesn't perceive the Internet
Protocol (IP) address.
· ARP is a convention used to determine this issue by giving an IP address at the system layer to
get the Ethernet address of a machine in the system.
· subsequently, administration demands are not just used to process demands from the upper
layer of the vehicle layer, yet in addition gave to the lower layer of the system that is the
information interface layer.
Hence, ARP is a piece of the system layer and not part of the information interface layer offers
types of assistance to the vehicle layer.
Solution 10
Given data:
Bandwidth = 64 kbps =64×1024 bps
Data frames = 512 bytes

Propagation Time (tp) =270 ms
Transmission time (Tt) = Frame length (Data size transmit)/Bandwidth
Frame length (l) = 512×8
l = 4096 bits
Transmission time (Tt) = l/ BW
= 4096/64*1024
= 625 m.sec
Window size = 1+2a
Where
a= Propagation time (Tp)/ Transmission time Tt
Window size = 1+2(270/625)
= 1+2(0.432)
Window size = 1.864 =2
Solution 11
If it exceeds the speed of light in a vacuum the it will no longer be a reasonable design. The
velocity of light (the velocity of the photon of the physical object) is not constant. There is no
complete vacuum because there is material and field! (Not to mention virtual particles. By the
way, if the virtual particles are broken, they emit energy, so they are short-lived, not normal, but
no such radiation!)
Transmission time (Tt) = Frame length (Data size transmit)/Bandwidth
Frame length (l) = 512×8
l = 4096 bits
Transmission time (Tt) = l/ BW
= 4096/64*1024
= 625 m.sec
Window size = 1+2a
Where
a= Propagation time (Tp)/ Transmission time Tt
Window size = 1+2(270/625)
= 1+2(0.432)
Window size = 1.864 =2
Solution 11
If it exceeds the speed of light in a vacuum the it will no longer be a reasonable design. The
velocity of light (the velocity of the photon of the physical object) is not constant. There is no
complete vacuum because there is material and field! (Not to mention virtual particles. By the
way, if the virtual particles are broken, they emit energy, so they are short-lived, not normal, but
no such radiation!)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.