ITC595 Information Security: Security Fundamentals - Assessment Report
VerifiedAdded on 2024/05/21
|11
|1831
|55
Homework Assignment
AI Summary
This document presents a student's solution to an Information Security assignment, focusing on security fundamentals. It covers various aspects of ATM security, including integrity, confidentiality, and availability requirements. The solution delves into calculating PIN possibilities with broken keys, discusses reluctance towards biometrics due to error management, cost, and accuracy, and analyzes scenarios where false negatives outweigh false positives. Furthermore, it demonstrates ciphertext decryption using the Vigenere cipher and Caesar cipher techniques. The document provides detailed explanations and examples to enhance understanding of information security concepts. Desklib offers this and many other solved assignments and past papers for students.

Arun Kumar Kalleda 11618961
ITC595: Information security
Assessment 2
Security Fundamental
Student Name: Arun Kumar Kalleda
Student ID: 11618961
1
ITC595: Information security
Assessment 2
Security Fundamental
Student Name: Arun Kumar Kalleda
Student ID: 11618961
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Arun Kumar Kalleda 11618961
Contents
Part 1:....................................................................................................................................................3
Part 2:....................................................................................................................................................4
Part 3:....................................................................................................................................................5
Part 4:....................................................................................................................................................6
Part 5:....................................................................................................................................................7
References...........................................................................................................................................11
2
Contents
Part 1:....................................................................................................................................................3
Part 2:....................................................................................................................................................4
Part 3:....................................................................................................................................................5
Part 4:....................................................................................................................................................6
Part 5:....................................................................................................................................................7
References...........................................................................................................................................11
2

Arun Kumar Kalleda 11618961
Part 1:
Under given is a brief detailing about the major requirements of ATM’s integrity,
confidentiality and availability.
Integrity requirement: Though the ATM’s are considered to be the safest, fastest and most
reliable way to transact money but there exist many threats which are needed to be solved
by improving few parameters of operations, the major one is integrity. To eradicate the
following issues integrity needs to be implemented. (Wingfield, 2016)
Unauthorized user access.
Information loss.
Abnormal message push’s on smartphones.
The major reason to avail integrity of automated teller machine is to allow only
authenticated and authorized users to operate the machine in order to avoid data breaching
and malfunctioning.
The degree of importance in the functionality provision and management is quite high in the
ATM system as in it multiuser access to different accounts is available to the data
transparency management also needs to be controlled. In case of failures availability
management of ATM gets less in the count.
Confidentiality: Multiple users need to operate their accounts through ATM’s, thus for
securing each individual data confidentiality maintenance is a necessity. Supporting
techniques in case of confidentiality management are authentication, biometry, and
encryption. Confidentiality means privacy state maintenance. This is achieved using pin
codes for operations like withdrawal and deposit. Using pin codes for individual account
access helps to avoid hacker access (Vonnegut, 2016).
Possible issues are:
Spoofing is the biggest threat which is eradicated using confidentiality as in these
third-party attacks the individual account data.
Availability:
In this users are availed several features and functionalities under automated teller machine
to enhance the workflow quality of the system. Reason to achieve this is fulfilling the money
availability throughout the system so that no issues have to be faced at user end in any case.
Nonrepudiation is another matter of fact linked with ATM, as not even a single user can
deny that he/she hasn’t accessed the account if done, every activity is recorded (Atrey,
2017).
3
Part 1:
Under given is a brief detailing about the major requirements of ATM’s integrity,
confidentiality and availability.
Integrity requirement: Though the ATM’s are considered to be the safest, fastest and most
reliable way to transact money but there exist many threats which are needed to be solved
by improving few parameters of operations, the major one is integrity. To eradicate the
following issues integrity needs to be implemented. (Wingfield, 2016)
Unauthorized user access.
Information loss.
Abnormal message push’s on smartphones.
The major reason to avail integrity of automated teller machine is to allow only
authenticated and authorized users to operate the machine in order to avoid data breaching
and malfunctioning.
The degree of importance in the functionality provision and management is quite high in the
ATM system as in it multiuser access to different accounts is available to the data
transparency management also needs to be controlled. In case of failures availability
management of ATM gets less in the count.
Confidentiality: Multiple users need to operate their accounts through ATM’s, thus for
securing each individual data confidentiality maintenance is a necessity. Supporting
techniques in case of confidentiality management are authentication, biometry, and
encryption. Confidentiality means privacy state maintenance. This is achieved using pin
codes for operations like withdrawal and deposit. Using pin codes for individual account
access helps to avoid hacker access (Vonnegut, 2016).
Possible issues are:
Spoofing is the biggest threat which is eradicated using confidentiality as in these
third-party attacks the individual account data.
Availability:
In this users are availed several features and functionalities under automated teller machine
to enhance the workflow quality of the system. Reason to achieve this is fulfilling the money
availability throughout the system so that no issues have to be faced at user end in any case.
Nonrepudiation is another matter of fact linked with ATM, as not even a single user can
deny that he/she hasn’t accessed the account if done, every activity is recorded (Atrey,
2017).
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Arun Kumar Kalleda 11618961
Part 2:
Under given is a complete calculation of maximum pin numbers possible to enter for
accurately discovering the actual pin of the customer on the hackers ends.
Presenting case 1: In case one, the zero digits are broken from the number key panel of
automated teller machine. Due to this obviously, the respected user would not be able to
use zero key digits out of the number panel present on ATM machine.
As the ATM pin consists four place values so the left part is five other values. Possible
combinations for the pin development can be the one I have listed below. These are
basically to be filled with the leftover place values.
First Value: 5 Second Value: 5 Third Value: 5 Forth Value: 5
Resulting Value: 5 x 5 x 5 x 5= 625
Presenting case 2: In a situation, if that zero digit key not being broken through the
respective user then the possibility raises such that chances are reduced by value one which
means all present four zeros are not the actual password for which the complete process is
going on. In this scenario possible cases are:
Resulting Value: 5 x 5 x 5 x 5 minus one = 624
Preceding all the above-mentioned steps more than three or four times according to the
fixed number of counts, there exist chances of automated machine teller card blocking
chances for 24 hours. Secondly, all the mentioned details are completely taken in reference
from bank-based real scenarios.
4
Part 2:
Under given is a complete calculation of maximum pin numbers possible to enter for
accurately discovering the actual pin of the customer on the hackers ends.
Presenting case 1: In case one, the zero digits are broken from the number key panel of
automated teller machine. Due to this obviously, the respected user would not be able to
use zero key digits out of the number panel present on ATM machine.
As the ATM pin consists four place values so the left part is five other values. Possible
combinations for the pin development can be the one I have listed below. These are
basically to be filled with the leftover place values.
First Value: 5 Second Value: 5 Third Value: 5 Forth Value: 5
Resulting Value: 5 x 5 x 5 x 5= 625
Presenting case 2: In a situation, if that zero digit key not being broken through the
respective user then the possibility raises such that chances are reduced by value one which
means all present four zeros are not the actual password for which the complete process is
going on. In this scenario possible cases are:
Resulting Value: 5 x 5 x 5 x 5 minus one = 624
Preceding all the above-mentioned steps more than three or four times according to the
fixed number of counts, there exist chances of automated machine teller card blocking
chances for 24 hours. Secondly, all the mentioned details are completely taken in reference
from bank-based real scenarios.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Arun Kumar Kalleda 11618961
Part 3:
Below are the three major reasons due to which people show reluctance towards biometrics
as an authentication system.
Error management: In biometric system, customers face faults and errors in getting
recognized due to system server issues majorly. Errors faced are two types,
Technical: System server issues.
Other issues: Minor Injuries and cuts in fingers cause recognition issues.
Solution to these issues is again the Gabor image filtration or simply customer can go for
some other authorization and authentication technique.
Less Feasible in terms of cost: Customer class is always attracted towards the best at least,
best is the quality and least in terms of money. Though this system is not that feasible in
terms of price yes, compared to rest of the authentications systems biometric proves to be
the most widely used one as it offers several features. Features are.
User data need not be stored, just a key scan is done if using cards or recognitions
are done that too face and finger vein based.
No requirement to share personal details.
Helps to avoid spoofing, third-party attacks on accounts.
But a machine based trust is required as all the customer data has ultimately been stored in
the machine only. Several other methods based on security are considered to safe
authentication and authorization part also.
Feasibility can be countered opting loan system for the geographical area wherever the
facility is required. (Moeller, 2017)
Accuracy: Biometric systems are very convenient to use but customer class faces an issue
of accuracy in biometric. The first example is sometimes it happens while getting the finger
recognized position issues occur that result in denial of service if tried more than the fixed
counts.
Solution to eradicate this issue is the application of Gabor image filters and sensors in the
biometric system to save the enhanced view of the recognized body part. (Biometrics, 2016)
5
Part 3:
Below are the three major reasons due to which people show reluctance towards biometrics
as an authentication system.
Error management: In biometric system, customers face faults and errors in getting
recognized due to system server issues majorly. Errors faced are two types,
Technical: System server issues.
Other issues: Minor Injuries and cuts in fingers cause recognition issues.
Solution to these issues is again the Gabor image filtration or simply customer can go for
some other authorization and authentication technique.
Less Feasible in terms of cost: Customer class is always attracted towards the best at least,
best is the quality and least in terms of money. Though this system is not that feasible in
terms of price yes, compared to rest of the authentications systems biometric proves to be
the most widely used one as it offers several features. Features are.
User data need not be stored, just a key scan is done if using cards or recognitions
are done that too face and finger vein based.
No requirement to share personal details.
Helps to avoid spoofing, third-party attacks on accounts.
But a machine based trust is required as all the customer data has ultimately been stored in
the machine only. Several other methods based on security are considered to safe
authentication and authorization part also.
Feasibility can be countered opting loan system for the geographical area wherever the
facility is required. (Moeller, 2017)
Accuracy: Biometric systems are very convenient to use but customer class faces an issue
of accuracy in biometric. The first example is sometimes it happens while getting the finger
recognized position issues occur that result in denial of service if tried more than the fixed
counts.
Solution to eradicate this issue is the application of Gabor image filters and sensors in the
biometric system to save the enhanced view of the recognized body part. (Biometrics, 2016)
5

Arun Kumar Kalleda 11618961
Part 4:
Under given are the two basic circumstances where false positives make fewer concerns
then false positives.
Scenario 1: Situation if a person being an authorized genuine customer or user but the
biometric system of respected area fails to recognize the one due to less enhanced vision
capture during sensing stage and not authenticating the user, it can cause serious issue as
here only the false negative circumstances are leading more serious than that of positive
one.
Scenario 2: In a remote health tele monitoring system if a patient is not willing to reach the
hospital for getting the reports and through biometric system in phone he can access the
same but the biometric authenticating system fails to recognize the user in emergency case,
this has also the ability to create false negative circumstances than positive ones.
6
Part 4:
Under given are the two basic circumstances where false positives make fewer concerns
then false positives.
Scenario 1: Situation if a person being an authorized genuine customer or user but the
biometric system of respected area fails to recognize the one due to less enhanced vision
capture during sensing stage and not authenticating the user, it can cause serious issue as
here only the false negative circumstances are leading more serious than that of positive
one.
Scenario 2: In a remote health tele monitoring system if a patient is not willing to reach the
hospital for getting the reports and through biometric system in phone he can access the
same but the biometric authenticating system fails to recognize the user in emergency case,
this has also the ability to create false negative circumstances than positive ones.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Arun Kumar Kalleda 11618961
Part 5:
Ciphertext provided: NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
Though here the need is to convert one phase plain text to the ciphertext given above has
implemented substitution methodology for a step by step encryption and decryption. Type
of cipher taken into consideration is known as Vigenere cipher.
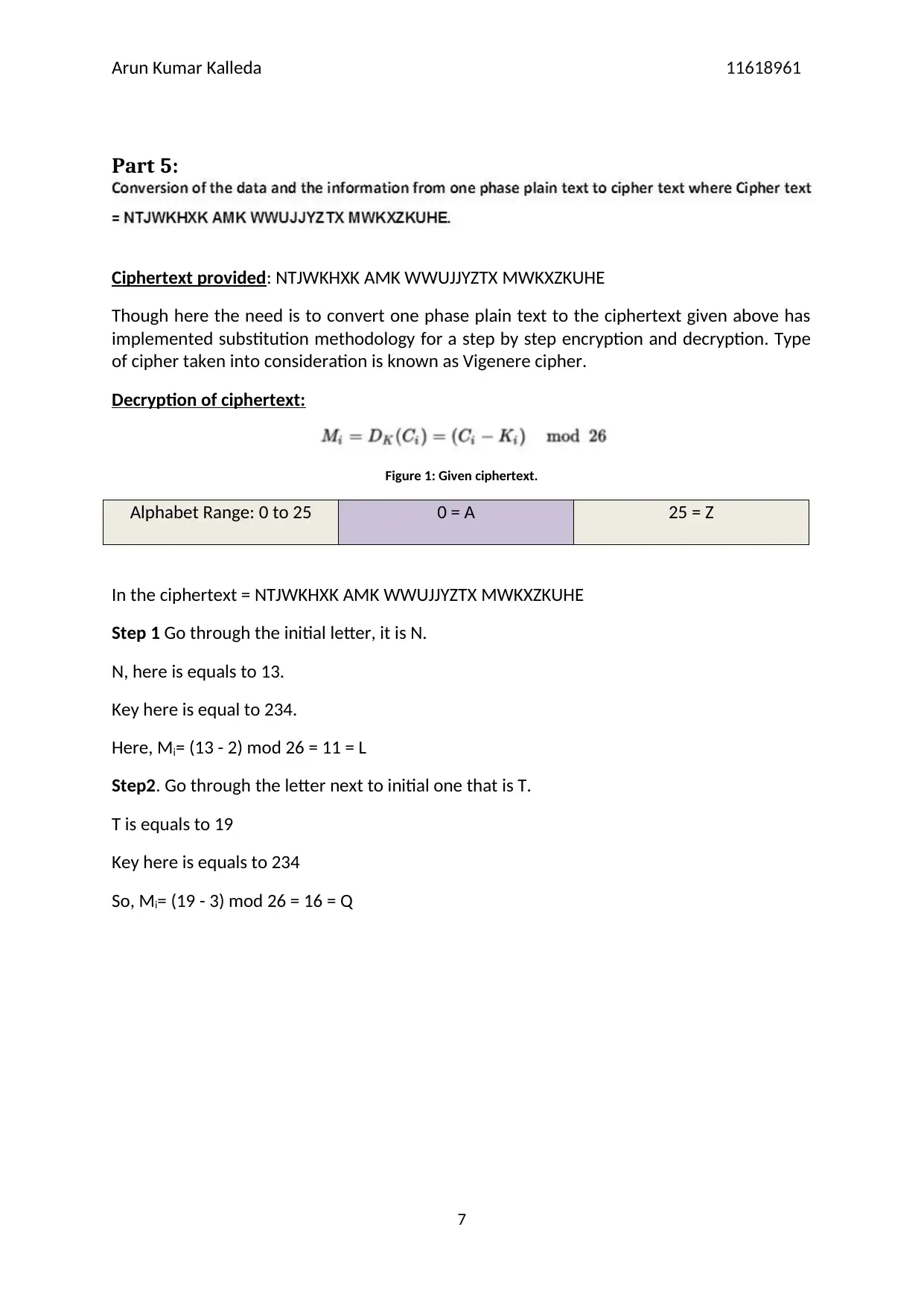
Decryption of ciphertext:
Figure 1: Given ciphertext.
Alphabet Range: 0 to 25 0 = A 25 = Z
In the ciphertext = NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
Step 1 Go through the initial letter, it is N.
N, here is equals to 13.
Key here is equal to 234.
Here, Mi= (13 - 2) mod 26 = 11 = L
Step2. Go through the letter next to initial one that is T.
T is equals to 19
Key here is equals to 234
So, Mi= (19 - 3) mod 26 = 16 = Q
7
Part 5:
Ciphertext provided: NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
Though here the need is to convert one phase plain text to the ciphertext given above has
implemented substitution methodology for a step by step encryption and decryption. Type
of cipher taken into consideration is known as Vigenere cipher.
Decryption of ciphertext:
Figure 1: Given ciphertext.
Alphabet Range: 0 to 25 0 = A 25 = Z
In the ciphertext = NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
Step 1 Go through the initial letter, it is N.
N, here is equals to 13.
Key here is equal to 234.
Here, Mi= (13 - 2) mod 26 = 11 = L
Step2. Go through the letter next to initial one that is T.
T is equals to 19
Key here is equals to 234
So, Mi= (19 - 3) mod 26 = 16 = Q
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Arun Kumar Kalleda 11618961
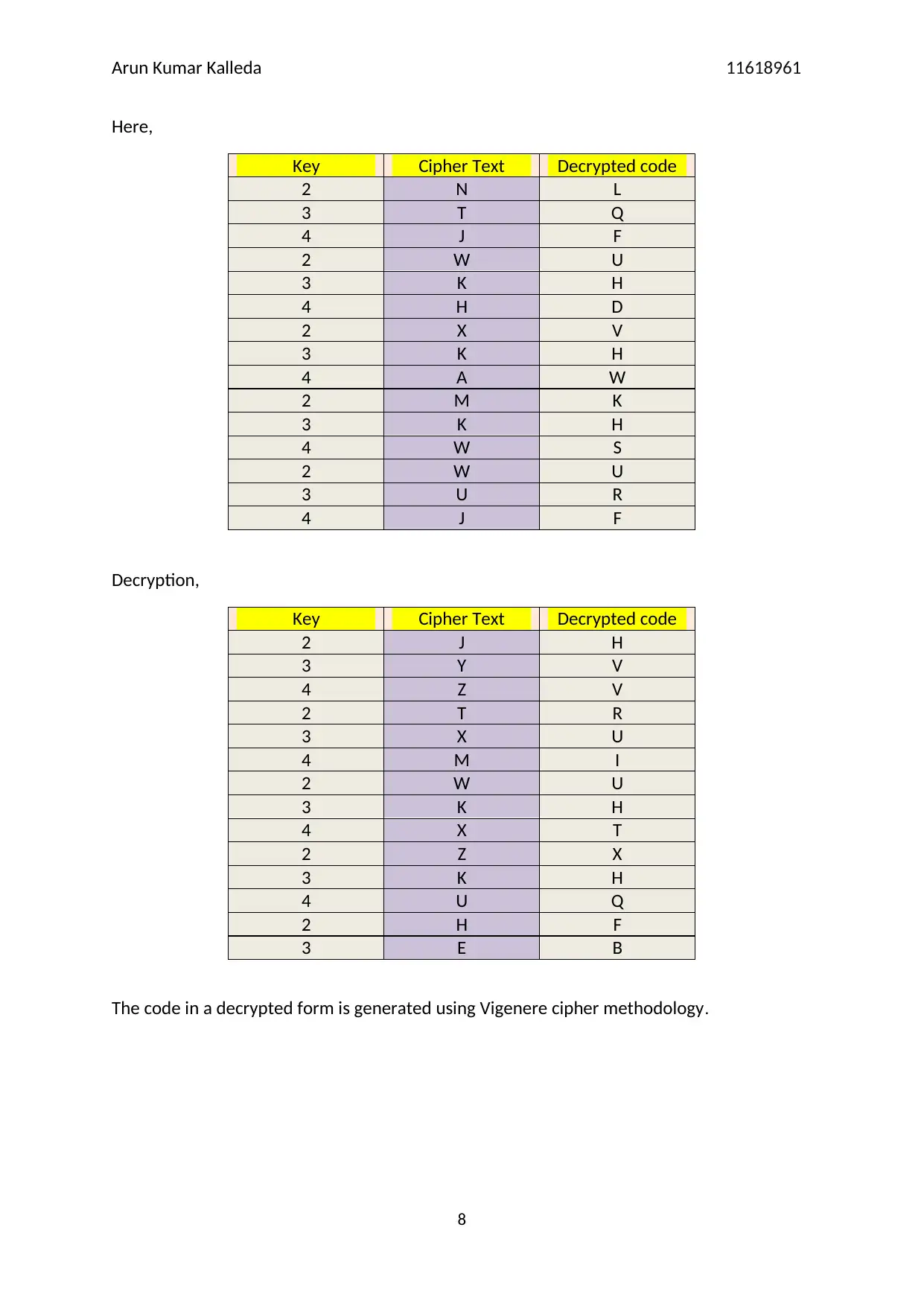
Here,
Key Cipher Text Decrypted code
2 N L
3 T Q
4 J F
2 W U
3 K H
4 H D
2 X V
3 K H
4 A W
2 M K
3 K H
4 W S
2 W U
3 U R
4 J F
Decryption,
Key Cipher Text Decrypted code
2 J H
3 Y V
4 Z V
2 T R
3 X U
4 M I
2 W U
3 K H
4 X T
2 Z X
3 K H
4 U Q
2 H F
3 E B
The code in a decrypted form is generated using Vigenere cipher methodology.
8
Here,
Key Cipher Text Decrypted code
2 N L
3 T Q
4 J F
2 W U
3 K H
4 H D
2 X V
3 K H
4 A W
2 M K
3 K H
4 W S
2 W U
3 U R
4 J F
Decryption,
Key Cipher Text Decrypted code
2 J H
3 Y V
4 Z V
2 T R
3 X U
4 M I
2 W U
3 K H
4 X T
2 Z X
3 K H
4 U Q
2 H F
3 E B
The code in a decrypted form is generated using Vigenere cipher methodology.
8
Arun Kumar Kalleda 11618961
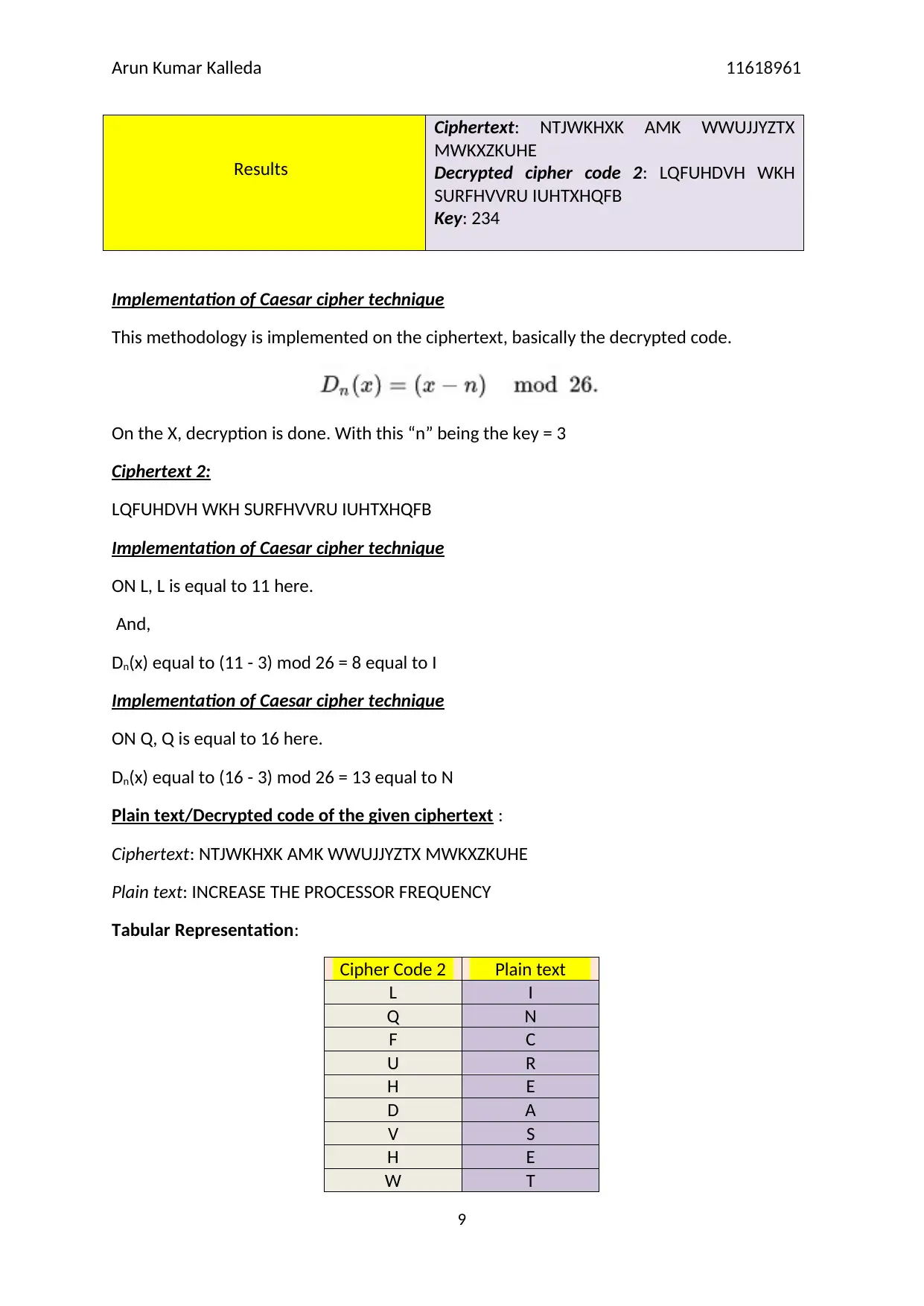
Results
Ciphertext: NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE
Decrypted cipher code 2: LQFUHDVH WKH
SURFHVVRU IUHTXHQFB
Key: 234
Implementation of Caesar cipher technique
This methodology is implemented on the ciphertext, basically the decrypted code.
On the X, decryption is done. With this “n” being the key = 3
Ciphertext 2:
LQFUHDVH WKH SURFHVVRU IUHTXHQFB
Implementation of Caesar cipher technique
ON L, L is equal to 11 here.
And,
Dn(x) equal to (11 - 3) mod 26 = 8 equal to I
Implementation of Caesar cipher technique
ON Q, Q is equal to 16 here.
Dn(x) equal to (16 - 3) mod 26 = 13 equal to N
Plain text/Decrypted code of the given ciphertext :
Ciphertext: NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
Plain text: INCREASE THE PROCESSOR FREQUENCY
Tabular Representation:
Cipher Code 2 Plain text
L I
Q N
F C
U R
H E
D A
V S
H E
W T
9
Results
Ciphertext: NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE
Decrypted cipher code 2: LQFUHDVH WKH
SURFHVVRU IUHTXHQFB
Key: 234
Implementation of Caesar cipher technique
This methodology is implemented on the ciphertext, basically the decrypted code.
On the X, decryption is done. With this “n” being the key = 3
Ciphertext 2:
LQFUHDVH WKH SURFHVVRU IUHTXHQFB
Implementation of Caesar cipher technique
ON L, L is equal to 11 here.
And,
Dn(x) equal to (11 - 3) mod 26 = 8 equal to I
Implementation of Caesar cipher technique
ON Q, Q is equal to 16 here.
Dn(x) equal to (16 - 3) mod 26 = 13 equal to N
Plain text/Decrypted code of the given ciphertext :
Ciphertext: NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
Plain text: INCREASE THE PROCESSOR FREQUENCY
Tabular Representation:
Cipher Code 2 Plain text
L I
Q N
F C
U R
H E
D A
V S
H E
W T
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Arun Kumar Kalleda 11618961
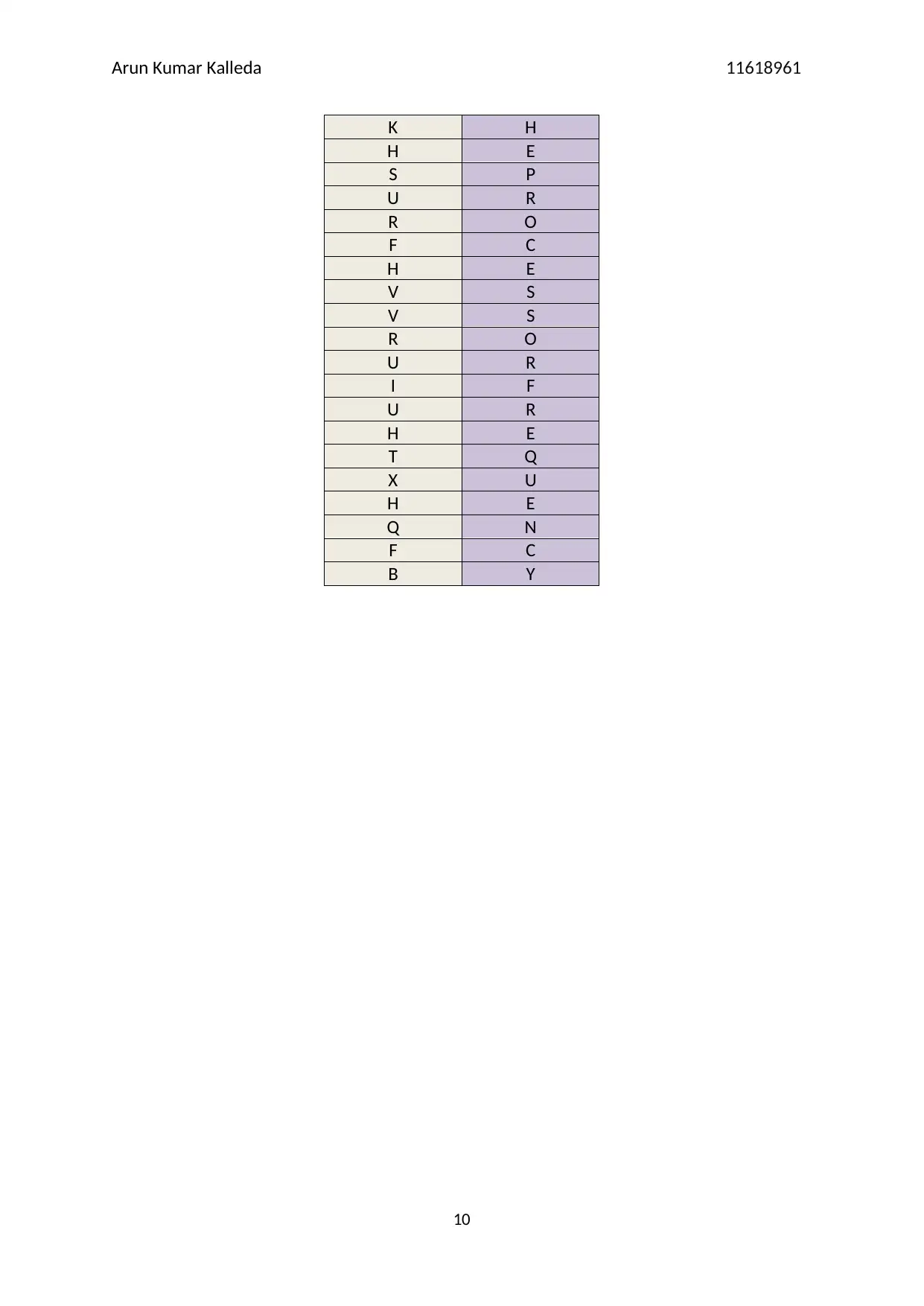
K H
H E
S P
U R
R O
F C
H E
V S
V S
R O
U R
I F
U R
H E
T Q
X U
H E
Q N
F C
B Y
10
K H
H E
S P
U R
R O
F C
H E
V S
V S
R O
U R
I F
U R
H E
T Q
X U
H E
Q N
F C
B Y
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Arun Kumar Kalleda 11618961
References
Erden, M. (2016). Advantages and Disadvantages of Biometric Authentication SESTEK
Blog. SESTEK. Retrieved from http://www.sestek.com/2016/11/advantages-
disadvantages-biometric-authentication/
The conversation (2017). How secure are today's ATMs? 5 questions answered. The
Conversation. Retrieved from https://theconversation.com/how-secure-are-todays-
atms-5-questions-answered-79618
Vonnegut, S. (2016). The Importance of Database Security and Integrity. Checkmarx.
Retrieved from https://www.checkmarx.com/2016/06/24/20160624the-importance-
of-database-security-and-integrity/
Wingfield, T. (2016). Securing Tomorrow. McAfee Blogs. Retrieved from
https://securingtomorrow.mcafee
11
References
Erden, M. (2016). Advantages and Disadvantages of Biometric Authentication SESTEK
Blog. SESTEK. Retrieved from http://www.sestek.com/2016/11/advantages-
disadvantages-biometric-authentication/
The conversation (2017). How secure are today's ATMs? 5 questions answered. The
Conversation. Retrieved from https://theconversation.com/how-secure-are-todays-
atms-5-questions-answered-79618
Vonnegut, S. (2016). The Importance of Database Security and Integrity. Checkmarx.
Retrieved from https://www.checkmarx.com/2016/06/24/20160624the-importance-
of-database-security-and-integrity/
Wingfield, T. (2016). Securing Tomorrow. McAfee Blogs. Retrieved from
https://securingtomorrow.mcafee
11
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.


