BYOD Risk Assessment Task 1: Critical Components 2 2 Cyber Security Name of University Author
VerifiedAdded on 2022/10/18
|15
|2429
|149
AI Summary
Qualitative Risk assessment of the Information System 4 Task 2: Certificate based Authentication System 5 2.1. Organization Information System: Critical Components This section of the report aims in evaluation of the key processes of the information system of an organization that is the key information assets of the organization. The information related to total number of CBA users per year and the client details The above data indicates the most valuable assets of the Southern Cross University (SCU). The information related to total number of CBA users per year and the client
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CYBER SECURITY
Cyber Security
Name of Student
Name of University
Author Note
Cyber Security
Name of Student
Name of University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1CYBER SECURITY
Table of Contents
Task 1: BYOD Risk Assessment.........................................................................................2
1.1. Organization Information System: Critical Components.........................................2
1.2. Threats of BYOD Policy..........................................................................................2
1.3. Potential Vulnerabilities of Asset.............................................................................3
1.4. Qualitative Risk assessment of the Information System..........................................4
Task 2: Certificate based Authentication System................................................................5
2.1. Working Process: Pros and Cons..............................................................................5
2.2. Comparison between certificate and Password based authentication.......................6
2.2.1. Features for combating threats from BYOD policy..........................................6
Task 3: Anti-Phishing Guideline.........................................................................................8
3.1. Identification of the electronic Phishing messages...................................................8
3.2. Example of Phishing.................................................................................................9
3.3. Phishing Handling Instructions...............................................................................11
References..........................................................................................................................13
Table of Contents
Task 1: BYOD Risk Assessment.........................................................................................2
1.1. Organization Information System: Critical Components.........................................2
1.2. Threats of BYOD Policy..........................................................................................2
1.3. Potential Vulnerabilities of Asset.............................................................................3
1.4. Qualitative Risk assessment of the Information System..........................................4
Task 2: Certificate based Authentication System................................................................5
2.1. Working Process: Pros and Cons..............................................................................5
2.2. Comparison between certificate and Password based authentication.......................6
2.2.1. Features for combating threats from BYOD policy..........................................6
Task 3: Anti-Phishing Guideline.........................................................................................8
3.1. Identification of the electronic Phishing messages...................................................8
3.2. Example of Phishing.................................................................................................9
3.3. Phishing Handling Instructions...............................................................................11
References..........................................................................................................................13

2CYBER SECURITY
Task 1: BYOD Risk Assessment
1.1. Organization Information System: Critical Components
This section of the report aims in evaluation of the key processes of the information
system of an organization that is the key information assets of the organization. The information
assets of Southern Cross University are listed as below-
1. Personal data of the staffs and students of the University is one of the information
assets of the organization (Shumate & Ketel, 2014)
2. The annual financial data of the organization is another is another key asset of the
Southern Cross University
3. The information about the human resources.
4. The existing proprietary software system of the organization
5. The information related to total number of admissions per year and the client details
The above data indicates the most valuable assets of the Southern Cross University
(SCU). These information are vital for normal operation of the business and therefore, these
information may be subjected to risk of data theft.
1.2. Threats of BYOD Policy
The BYOD policy that is implemented in the SCU provides the staffs of the organization,
the facility of working with their own devices. However, there are certain threats linked with the
proposed BYOD policy which are listed as follows-
Task 1: BYOD Risk Assessment
1.1. Organization Information System: Critical Components
This section of the report aims in evaluation of the key processes of the information
system of an organization that is the key information assets of the organization. The information
assets of Southern Cross University are listed as below-
1. Personal data of the staffs and students of the University is one of the information
assets of the organization (Shumate & Ketel, 2014)
2. The annual financial data of the organization is another is another key asset of the
Southern Cross University
3. The information about the human resources.
4. The existing proprietary software system of the organization
5. The information related to total number of admissions per year and the client details
The above data indicates the most valuable assets of the Southern Cross University
(SCU). These information are vital for normal operation of the business and therefore, these
information may be subjected to risk of data theft.
1.2. Threats of BYOD Policy
The BYOD policy that is implemented in the SCU provides the staffs of the organization,
the facility of working with their own devices. However, there are certain threats linked with the
proposed BYOD policy which are listed as follows-

3CYBER SECURITY
1. The personal devices used by the staffs of the organization might get stolen thus
risking the confidential information of the University.
2. There is generally no password protection in the personal devises and thus the devices
can easily get compromised in an event of theft or hacking (Olalere et al., 2015).
3. The device might make use of public internet without encryption of the data related to
University thus, increasing the chances of data hack.
4. Even after the employee leaves the organization, there are high chances of the data
being stored in the device thus, risking the confidentiality of the data.
1.3. Potential Vulnerabilities of Asset
The potential vulnerability of each information asset in consideration to the identified
threats are indicated as follows-
1. The personal information of students and personal information of the staffs of the
University might be at the risk of data threat as there is no password protection to the personal
device of a user.
2. The annual financial data of the organization is at risk of data theft as the personal
devices might connect to the public internet (French, Guo & Shim, 2014).
3. The information of the human resources might be at risk if an employee leaves the
organization.
4. The details of the software might be at risk if the device gets stolen.
1. The personal devices used by the staffs of the organization might get stolen thus
risking the confidential information of the University.
2. There is generally no password protection in the personal devises and thus the devices
can easily get compromised in an event of theft or hacking (Olalere et al., 2015).
3. The device might make use of public internet without encryption of the data related to
University thus, increasing the chances of data hack.
4. Even after the employee leaves the organization, there are high chances of the data
being stored in the device thus, risking the confidentiality of the data.
1.3. Potential Vulnerabilities of Asset
The potential vulnerability of each information asset in consideration to the identified
threats are indicated as follows-
1. The personal information of students and personal information of the staffs of the
University might be at the risk of data threat as there is no password protection to the personal
device of a user.
2. The annual financial data of the organization is at risk of data theft as the personal
devices might connect to the public internet (French, Guo & Shim, 2014).
3. The information of the human resources might be at risk if an employee leaves the
organization.
4. The details of the software might be at risk if the device gets stolen.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4CYBER SECURITY
5. The information about the total admission per year might be at risk if the device is
compromised by the attackers.
1.4. Qualitative Risk assessment of the Information System
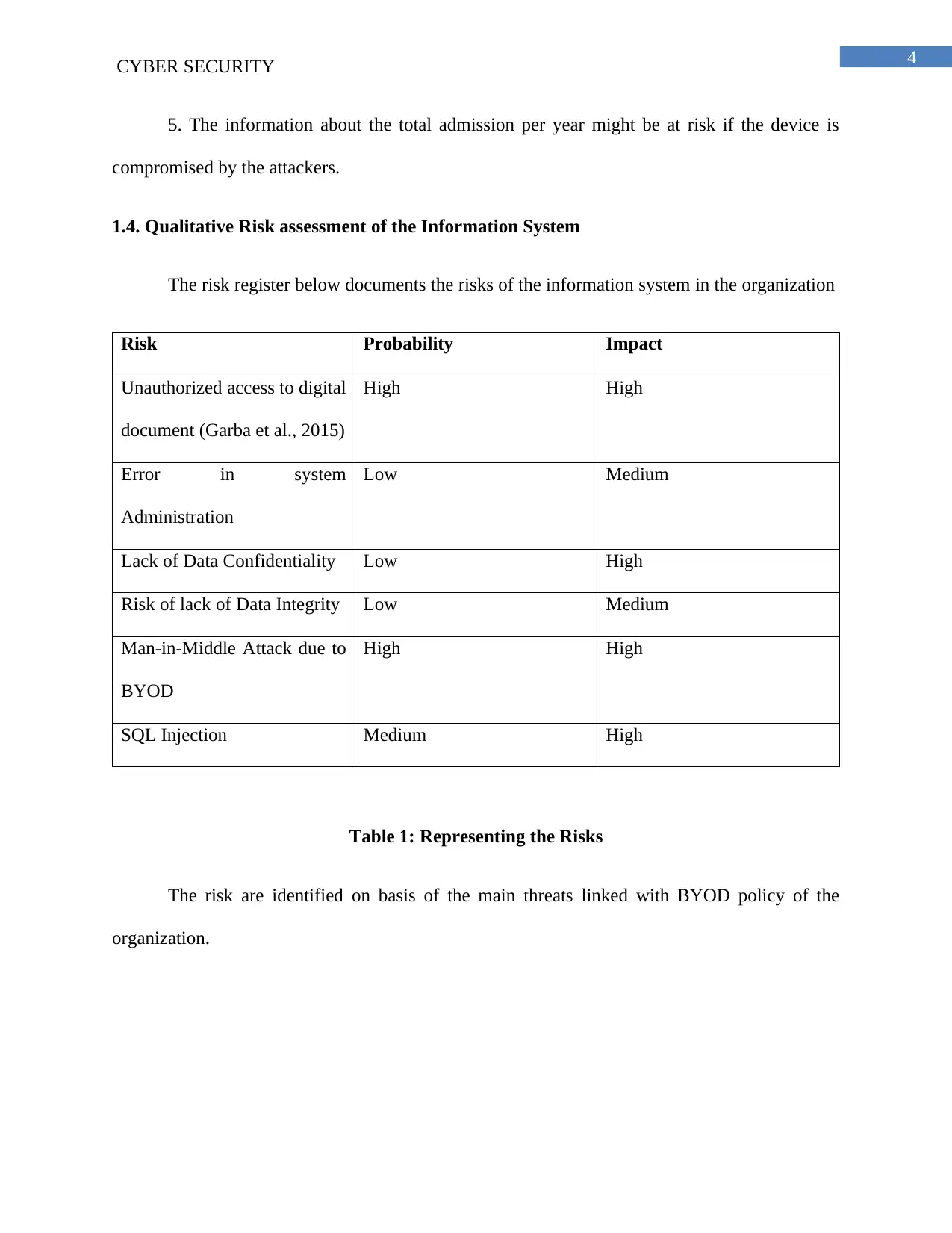
The risk register below documents the risks of the information system in the organization
Risk Probability Impact
Unauthorized access to digital
document (Garba et al., 2015)
High High
Error in system
Administration
Low Medium
Lack of Data Confidentiality Low High
Risk of lack of Data Integrity Low Medium
Man-in-Middle Attack due to
BYOD
High High
SQL Injection Medium High
Table 1: Representing the Risks
The risk are identified on basis of the main threats linked with BYOD policy of the
organization.
5. The information about the total admission per year might be at risk if the device is
compromised by the attackers.
1.4. Qualitative Risk assessment of the Information System
The risk register below documents the risks of the information system in the organization
Risk Probability Impact
Unauthorized access to digital
document (Garba et al., 2015)
High High
Error in system
Administration
Low Medium
Lack of Data Confidentiality Low High
Risk of lack of Data Integrity Low Medium
Man-in-Middle Attack due to
BYOD
High High
SQL Injection Medium High
Table 1: Representing the Risks
The risk are identified on basis of the main threats linked with BYOD policy of the
organization.
5CYBER SECURITY
Task 2: Certificate based Authentication System
2.1. Working Process: Pros and Cons
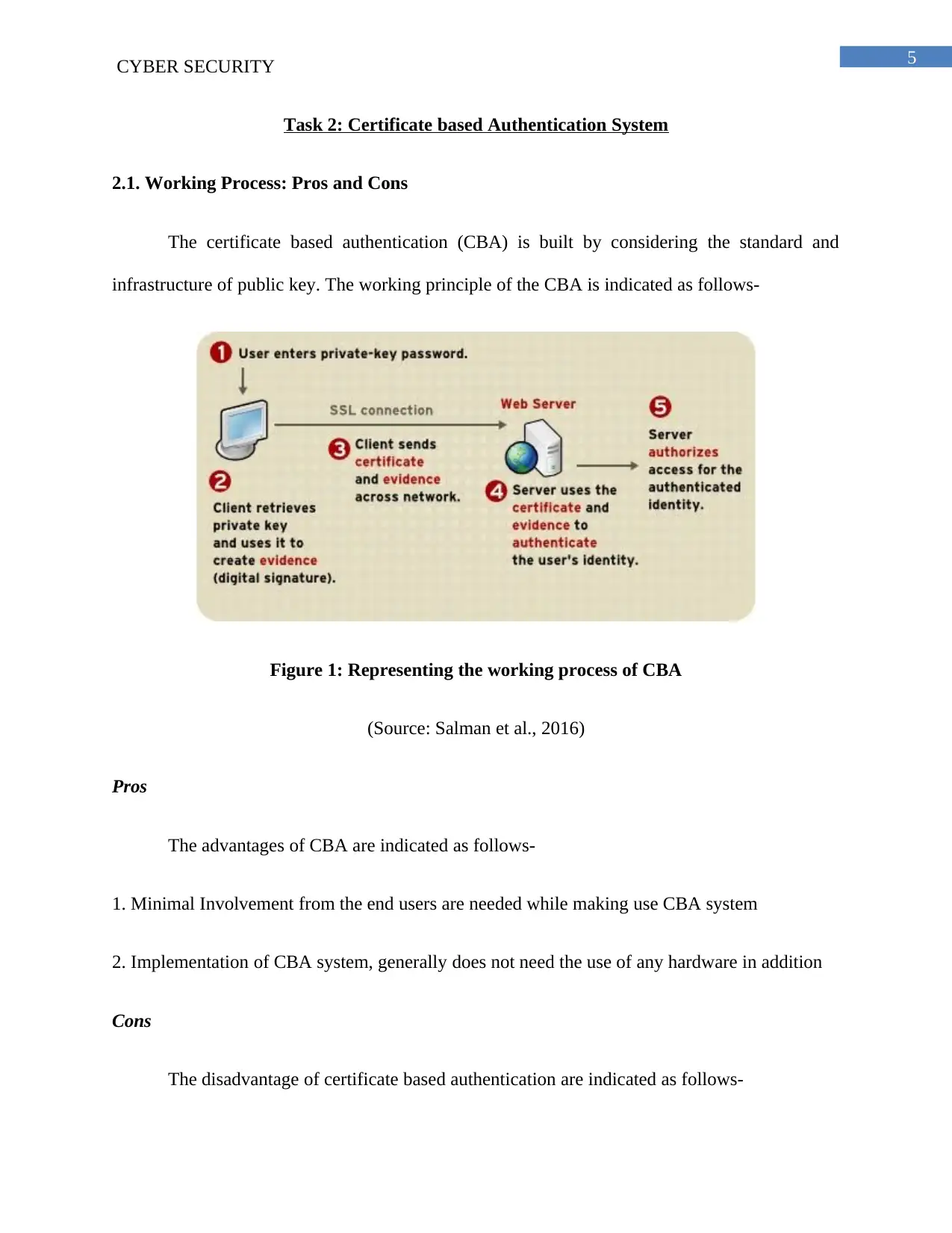
The certificate based authentication (CBA) is built by considering the standard and
infrastructure of public key. The working principle of the CBA is indicated as follows-
Figure 1: Representing the working process of CBA
(Source: Salman et al., 2016)
Pros
The advantages of CBA are indicated as follows-
1. Minimal Involvement from the end users are needed while making use CBA system
2. Implementation of CBA system, generally does not need the use of any hardware in addition
Cons
The disadvantage of certificate based authentication are indicated as follows-
Task 2: Certificate based Authentication System
2.1. Working Process: Pros and Cons
The certificate based authentication (CBA) is built by considering the standard and
infrastructure of public key. The working principle of the CBA is indicated as follows-
Figure 1: Representing the working process of CBA
(Source: Salman et al., 2016)
Pros
The advantages of CBA are indicated as follows-
1. Minimal Involvement from the end users are needed while making use CBA system
2. Implementation of CBA system, generally does not need the use of any hardware in addition
Cons
The disadvantage of certificate based authentication are indicated as follows-
6CYBER SECURITY
1. The main disadvantage is that this type of authentication requires the use of public key
infrastructure
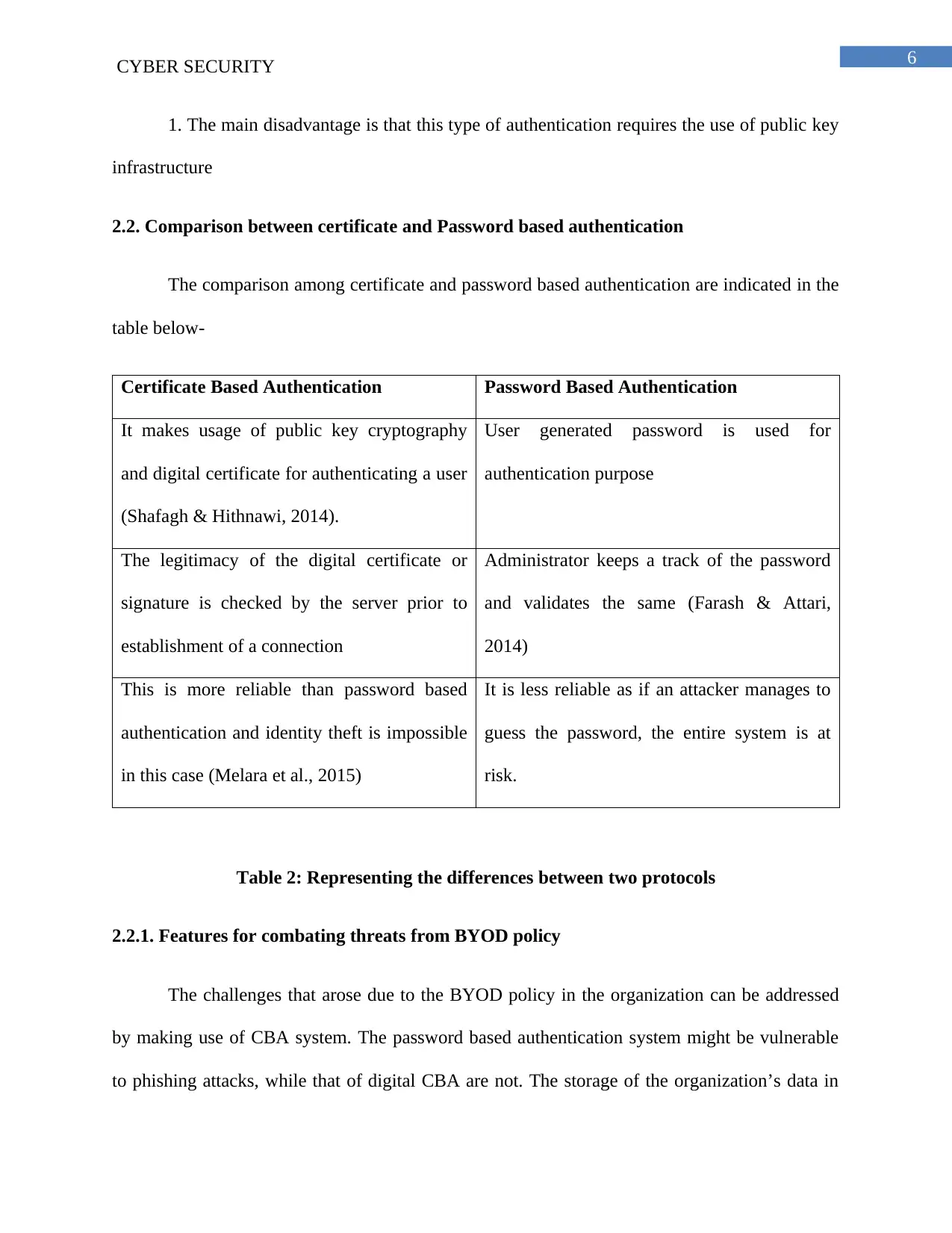
2.2. Comparison between certificate and Password based authentication
The comparison among certificate and password based authentication are indicated in the
table below-
Certificate Based Authentication Password Based Authentication
It makes usage of public key cryptography
and digital certificate for authenticating a user
(Shafagh & Hithnawi, 2014).
User generated password is used for
authentication purpose
The legitimacy of the digital certificate or
signature is checked by the server prior to
establishment of a connection
Administrator keeps a track of the password
and validates the same (Farash & Attari,
2014)
This is more reliable than password based
authentication and identity theft is impossible
in this case (Melara et al., 2015)
It is less reliable as if an attacker manages to
guess the password, the entire system is at
risk.
Table 2: Representing the differences between two protocols
2.2.1. Features for combating threats from BYOD policy
The challenges that arose due to the BYOD policy in the organization can be addressed
by making use of CBA system. The password based authentication system might be vulnerable
to phishing attacks, while that of digital CBA are not. The storage of the organization’s data in
1. The main disadvantage is that this type of authentication requires the use of public key
infrastructure
2.2. Comparison between certificate and Password based authentication
The comparison among certificate and password based authentication are indicated in the
table below-
Certificate Based Authentication Password Based Authentication
It makes usage of public key cryptography
and digital certificate for authenticating a user
(Shafagh & Hithnawi, 2014).
User generated password is used for
authentication purpose
The legitimacy of the digital certificate or
signature is checked by the server prior to
establishment of a connection
Administrator keeps a track of the password
and validates the same (Farash & Attari,
2014)
This is more reliable than password based
authentication and identity theft is impossible
in this case (Melara et al., 2015)
It is less reliable as if an attacker manages to
guess the password, the entire system is at
risk.
Table 2: Representing the differences between two protocols
2.2.1. Features for combating threats from BYOD policy
The challenges that arose due to the BYOD policy in the organization can be addressed
by making use of CBA system. The password based authentication system might be vulnerable
to phishing attacks, while that of digital CBA are not. The storage of the organization’s data in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY
the personal computer of the user is needed to be prohibited. The feature of validating the
identity of the user on basis of the digital signature or the digital certificate generated can help in
addressing the issues that can be faced because of the BYOD policy.
the personal computer of the user is needed to be prohibited. The feature of validating the
identity of the user on basis of the digital signature or the digital certificate generated can help in
addressing the issues that can be faced because of the BYOD policy.

8CYBER SECURITY
Task 3: Anti-Phishing Guideline
The aim of this section of the report is to identify the different types of messages that can
be termed as phishing message. This step becomes essential to design and develop phishing
handling instructions for the staffs of the organization.
3.1. Identification of the electronic Phishing messages
The phishing messages mainly aims in entrapping the victims into paying money to the
attackers. Thus the phishing messages are sent in form of gift card request, request for payroll
diversion while certain other messages requests for direct bank transfer (Suganya, 2016). These
messages although resembles the messages sent from valid sources, most of the phishing
messages contains malicious links that aims in soliciting money from the users or soliciting the
personal information of the users including the details of their credit cards.
The distinctive characteristics of a phishing message is indicated as follows-
1. The phishing emails always appear as an important notice or urgent update giving
alerts which are deceptive. The subject line of such emails might contain various numeric
characters or letters so that those mails can easily bypass the spamming filters.
2. Phishing emails mainly contains messages that sound attractive and not threatening.
3. Phishing emails mainly consists of forged sender’s address to make the emails appear
to be coming from the valid sources (Qabajeh, Thabtah & Chiclana, 2018)
4. The Phishing emails usually contains the hyperlink that directs the recipients to the
fraudulent website which are not genuine links.
Task 3: Anti-Phishing Guideline
The aim of this section of the report is to identify the different types of messages that can
be termed as phishing message. This step becomes essential to design and develop phishing
handling instructions for the staffs of the organization.
3.1. Identification of the electronic Phishing messages
The phishing messages mainly aims in entrapping the victims into paying money to the
attackers. Thus the phishing messages are sent in form of gift card request, request for payroll
diversion while certain other messages requests for direct bank transfer (Suganya, 2016). These
messages although resembles the messages sent from valid sources, most of the phishing
messages contains malicious links that aims in soliciting money from the users or soliciting the
personal information of the users including the details of their credit cards.
The distinctive characteristics of a phishing message is indicated as follows-
1. The phishing emails always appear as an important notice or urgent update giving
alerts which are deceptive. The subject line of such emails might contain various numeric
characters or letters so that those mails can easily bypass the spamming filters.
2. Phishing emails mainly contains messages that sound attractive and not threatening.
3. Phishing emails mainly consists of forged sender’s address to make the emails appear
to be coming from the valid sources (Qabajeh, Thabtah & Chiclana, 2018)
4. The Phishing emails usually contains the hyperlink that directs the recipients to the
fraudulent website which are not genuine links.
9CYBER SECURITY
5. Phishing mails generally contains a form or similar links for the recipient for filling in
the personal or financial data, which the user needs to fill and submit (Chaudhry, Chaudhry &
Rittenhouse, 2016).
The above points indicate the process of identification of the electronic phishing
messages.
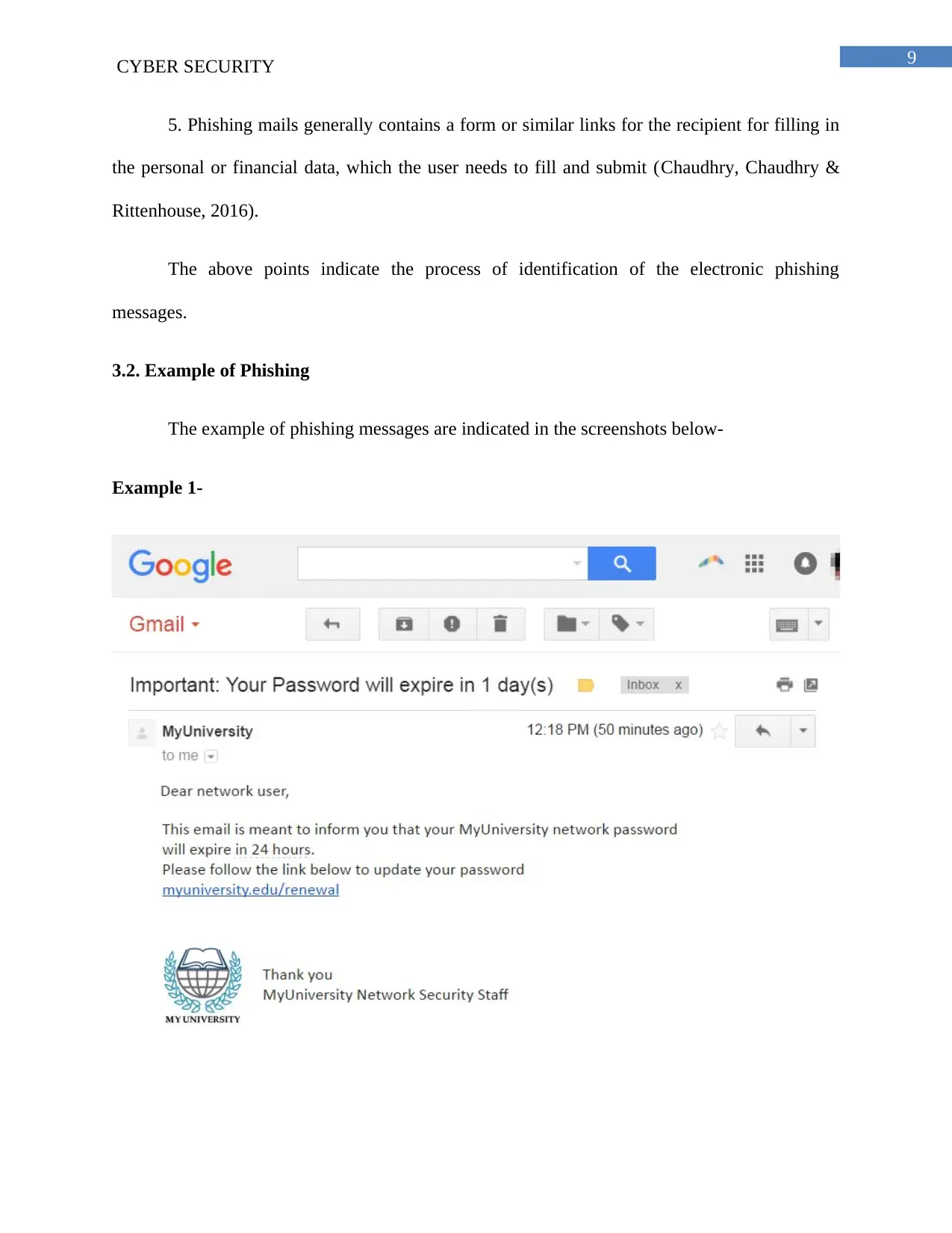
3.2. Example of Phishing
The example of phishing messages are indicated in the screenshots below-
Example 1-
5. Phishing mails generally contains a form or similar links for the recipient for filling in
the personal or financial data, which the user needs to fill and submit (Chaudhry, Chaudhry &
Rittenhouse, 2016).
The above points indicate the process of identification of the electronic phishing
messages.
3.2. Example of Phishing
The example of phishing messages are indicated in the screenshots below-
Example 1-
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10CYBER SECURITY
The above figure illustrates a common scam for phishing attacks. It contains a link and on
clicking the link the user is readdressed to a fake page myuniversity.edurenewal.com that looks
exactly same as the original renewal page. For renewal of the password the victim is prompted to
provide the old password. On entering the same, the attacker who is monitoring the site, takes
over the original password to get access resulting in a reflected XSS attack, which in turn gives
the criminal an access to the Network of the University.
Example 2-
The above screenshot is another example of phishing email. A phishing email is generally
sent from an illegitimate email address.
Example 3:
The above figure illustrates a common scam for phishing attacks. It contains a link and on
clicking the link the user is readdressed to a fake page myuniversity.edurenewal.com that looks
exactly same as the original renewal page. For renewal of the password the victim is prompted to
provide the old password. On entering the same, the attacker who is monitoring the site, takes
over the original password to get access resulting in a reflected XSS attack, which in turn gives
the criminal an access to the Network of the University.
Example 2-
The above screenshot is another example of phishing email. A phishing email is generally
sent from an illegitimate email address.
Example 3:

11CYBER SECURITY
The above figure is an example of spam email that contain a vague link. Also, the
important note mentioned at the end of the email itself indicates that it is a spam.
3.3. Phishing Handling Instructions
The above section provides an idea of the phishing emails that a user might receive.
Therefore, it is necessary to develop a guideline for the staffs of the organization with which they
can easily combat the threats linked with phishing emails (Wright et al., 2014). These
instructions will help the staffs to easily recognize a phishing attack and will help in minimizing
the threats of phishing.
1. All the staffs should ensure that the network of the organization is deployed with a spam filter
that is capable of detecting the viruses or blank senders in an email. Furthermore, the staffs to
ascertain that all the systems are updated with the current and latest security patches.
The above figure is an example of spam email that contain a vague link. Also, the
important note mentioned at the end of the email itself indicates that it is a spam.
3.3. Phishing Handling Instructions
The above section provides an idea of the phishing emails that a user might receive.
Therefore, it is necessary to develop a guideline for the staffs of the organization with which they
can easily combat the threats linked with phishing emails (Wright et al., 2014). These
instructions will help the staffs to easily recognize a phishing attack and will help in minimizing
the threats of phishing.
1. All the staffs should ensure that the network of the organization is deployed with a spam filter
that is capable of detecting the viruses or blank senders in an email. Furthermore, the staffs to
ascertain that all the systems are updated with the current and latest security patches.

12CYBER SECURITY
2. One of the easiest way of detecting spam email involves detection of malicious links. Email
from valid sources never asks for personal details. The user can hover over any hyperlink that is
sent over email to see the actual address (Aleroud & Zhou, 2017). If it is seen that the address is
fake the user should refrain from clicking that link.
3. The emails that are not relevant to the organization or the user should be left unattended.
4. Emails saying that the user has own free gifts, lottery or prizes should be left unattended.
2. One of the easiest way of detecting spam email involves detection of malicious links. Email
from valid sources never asks for personal details. The user can hover over any hyperlink that is
sent over email to see the actual address (Aleroud & Zhou, 2017). If it is seen that the address is
fake the user should refrain from clicking that link.
3. The emails that are not relevant to the organization or the user should be left unattended.
4. Emails saying that the user has own free gifts, lottery or prizes should be left unattended.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13CYBER SECURITY
References
Aleroud, A., & Zhou, L. (2017). Phishing environments, techniques, and countermeasures: A
survey. Computers & Security, 68, 160-196.
Chaudhry, J. A., Chaudhry, S. A., & Rittenhouse, R. G. (2016). Phishing attacks and
defenses. International Journal of Security and Its Applications, 10(1), 247-256.
Farash, M. S., & Attari, M. A. (2014). An efficient client–client password-based authentication
scheme with provable security. The Journal of Supercomputing, 70(2), 1002-1022.
French, A. M., Guo, C., & Shim, J. P. (2014). Current status, issues, and future of bring your
own device (BYOD). Communications of the Association for Information Systems, 35(1),
10.
Garba, A. B., Armarego, J., Murray, D., & Kenworthy, W. (2015). Review of the information
security and privacy challenges in Bring Your Own Device (BYOD)
environments. Journal of Information privacy and security, 11(1), 38-54.
Melara, M. S., Blankstein, A., Bonneau, J., Felten, E. W., & Freedman, M. J. (2015).
{CONIKS}: Bringing Key Transparency to End Users. In 24th {USENIX} Security
Symposium ({USENIX} Security 15) (pp. 383-398).
Olalere, M., Abdullah, M. T., Mahmod, R., & Abdullah, A. (2015). A review of bring your own
device on security issues. Sage Open, 5(2), 2158244015580372.
Qabajeh, I., Thabtah, F., & Chiclana, F. (2018). A recent review of conventional vs. automated
cybersecurity anti-phishing techniques. Computer Science Review, 29, 44-55.
References
Aleroud, A., & Zhou, L. (2017). Phishing environments, techniques, and countermeasures: A
survey. Computers & Security, 68, 160-196.
Chaudhry, J. A., Chaudhry, S. A., & Rittenhouse, R. G. (2016). Phishing attacks and
defenses. International Journal of Security and Its Applications, 10(1), 247-256.
Farash, M. S., & Attari, M. A. (2014). An efficient client–client password-based authentication
scheme with provable security. The Journal of Supercomputing, 70(2), 1002-1022.
French, A. M., Guo, C., & Shim, J. P. (2014). Current status, issues, and future of bring your
own device (BYOD). Communications of the Association for Information Systems, 35(1),
10.
Garba, A. B., Armarego, J., Murray, D., & Kenworthy, W. (2015). Review of the information
security and privacy challenges in Bring Your Own Device (BYOD)
environments. Journal of Information privacy and security, 11(1), 38-54.
Melara, M. S., Blankstein, A., Bonneau, J., Felten, E. W., & Freedman, M. J. (2015).
{CONIKS}: Bringing Key Transparency to End Users. In 24th {USENIX} Security
Symposium ({USENIX} Security 15) (pp. 383-398).
Olalere, M., Abdullah, M. T., Mahmod, R., & Abdullah, A. (2015). A review of bring your own
device on security issues. Sage Open, 5(2), 2158244015580372.
Qabajeh, I., Thabtah, F., & Chiclana, F. (2018). A recent review of conventional vs. automated
cybersecurity anti-phishing techniques. Computer Science Review, 29, 44-55.

14CYBER SECURITY
Salman, O., Abdallah, S., Elhajj, I. H., Chehab, A., & Kayssi, A. (2016, June). Identity-based
authentication scheme for the internet of things. In 2016 IEEE Symposium on Computers
and Communication (ISCC) (pp. 1109-1111). IEEE.
Shafagh, H., & Hithnawi, A. (2014, May). Security comes first, a public-key cryptography
framework for the internet of things. In 2014 IEEE International Conference on
Distributed Computing in Sensor Systems (pp. 135-136). IEEE.
Shumate, T., & Ketel, M. (2014, March). Bring your own device: benefits, risks and control
techniques. In Ieee Southeastcon 2014 (pp. 1-6). IEEE.
Suganya, V. (2016). A review on phishing attacks and various anti phishing
techniques. International Journal of Computer Applications, 139(1), 20-23.
Wright, R. T., Jensen, M. L., Thatcher, J. B., Dinger, M., & Marett, K. (2014). Research note—
influence techniques in phishing attacks: an examination of vulnerability and
resistance. Information systems research, 25(2), 385-400.
Salman, O., Abdallah, S., Elhajj, I. H., Chehab, A., & Kayssi, A. (2016, June). Identity-based
authentication scheme for the internet of things. In 2016 IEEE Symposium on Computers
and Communication (ISCC) (pp. 1109-1111). IEEE.
Shafagh, H., & Hithnawi, A. (2014, May). Security comes first, a public-key cryptography
framework for the internet of things. In 2014 IEEE International Conference on
Distributed Computing in Sensor Systems (pp. 135-136). IEEE.
Shumate, T., & Ketel, M. (2014, March). Bring your own device: benefits, risks and control
techniques. In Ieee Southeastcon 2014 (pp. 1-6). IEEE.
Suganya, V. (2016). A review on phishing attacks and various anti phishing
techniques. International Journal of Computer Applications, 139(1), 20-23.
Wright, R. T., Jensen, M. L., Thatcher, J. B., Dinger, M., & Marett, K. (2014). Research note—
influence techniques in phishing attacks: an examination of vulnerability and
resistance. Information systems research, 25(2), 385-400.
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




