Ask a question from expert
Privacy and Security System | Assignment
22 Pages8571 Words378 Views
Added on 2019-09-25
Privacy and Security System | Assignment
Added on 2019-09-25
BookmarkShareRelated Documents
Assessment item 1Privacy and Security Reflectionvalue- 10%Due Date:25-Jul-2018Length:Approx. 3000 wordsTaskThis assignment is designed to get you to reflect on your personal approach and feelings on information security and privacy.Read:Lau, Y. (2015). Cybercrime in cloud: Risks and responses in Hong Kong, Singapore. In Ko, R., & Choo, K.(Eds.). (2015). The Cloud Security Ecosystem: Technical, Legal, Business andManagement Issues. Waltham, MA: Syngress.This chapter discusses some of the approaches to cybercrime that are taken by both the Hong Kong and Singapore governments. But, any approach to cybercrime comes with risks to information security and privacy.Tasks:Assume that an Australian State Government has reviewed the Singapore Government’s Smart Nation Plan and has decided to implement their own Smart State Plan. This will initially consist of a network of smart sensors and cameras at traffic lights, bus stops, rubbish bins, etc. in their CBD to monitor citizens behaviour and address street crime.1. Discuss what you see as the personal and ethical implications for your privacy of the proposed Government’s Smart Sensor Network by looking at:a. The types or categories of people affected by this proposal,b. What behavioural changes you might expect to see from normal citizens,c. Would you expect to see changes in individual behaviours, such as choice of activities, changes in time schedules, etc.The next part of the Government’s plan is to deploy a Smart WiFi Network which will consist of a series of sensor boxes to act as WiFi hotspots throughout the city. This would allow the introduction of a heterogeneous network where smart phones and other devices could seamless switch between mobile data and WiFi.2. Discuss what you see as the personal and ethical implications for your privacy of the proposed Government’s Smart WiFi Network by looking at:

a. The types or categories of people affected by this proposal,b. What behavioural changes you might expect to see from normal citizens using their mobile devices in the CBD,c. Would you expect to see changes in individual behaviours, such as choice of activities, changes in time schedules, etc.d. What are the implications for you If you had sensitive information on your mobile device that you did not want to share?The Smart State Plan will also enrol all citizens with a Digital Identity to ensure that they can correctly be identified and access services provided by the state both electronically and physically.3. If you were visiting the State Capital after the Smart State Plan has rolled out, do you thinkthat the use of a digital identity would assist you to maintain your privacy while using your mobile phone or devices during your visit? Discuss the reasons for your answer. 4. What steps do you think that you could take to ensure the security and privacy of your digital identity while operating your mobile device(s) in this environment? Discuss each step that you would take along with its advantages and disadvantages. Each question is worth 25 marks and your overall score will be scaled out of 10. As a guide, your word limit for this assignment should be around 3,000 words. Rationaleback to topThis assessment task will assess the following learning outcome/s:be able to critically analyse the legal, ethical and business concerns for the security and privacy of data to be deployed to the cloud.Marking criteria and standards
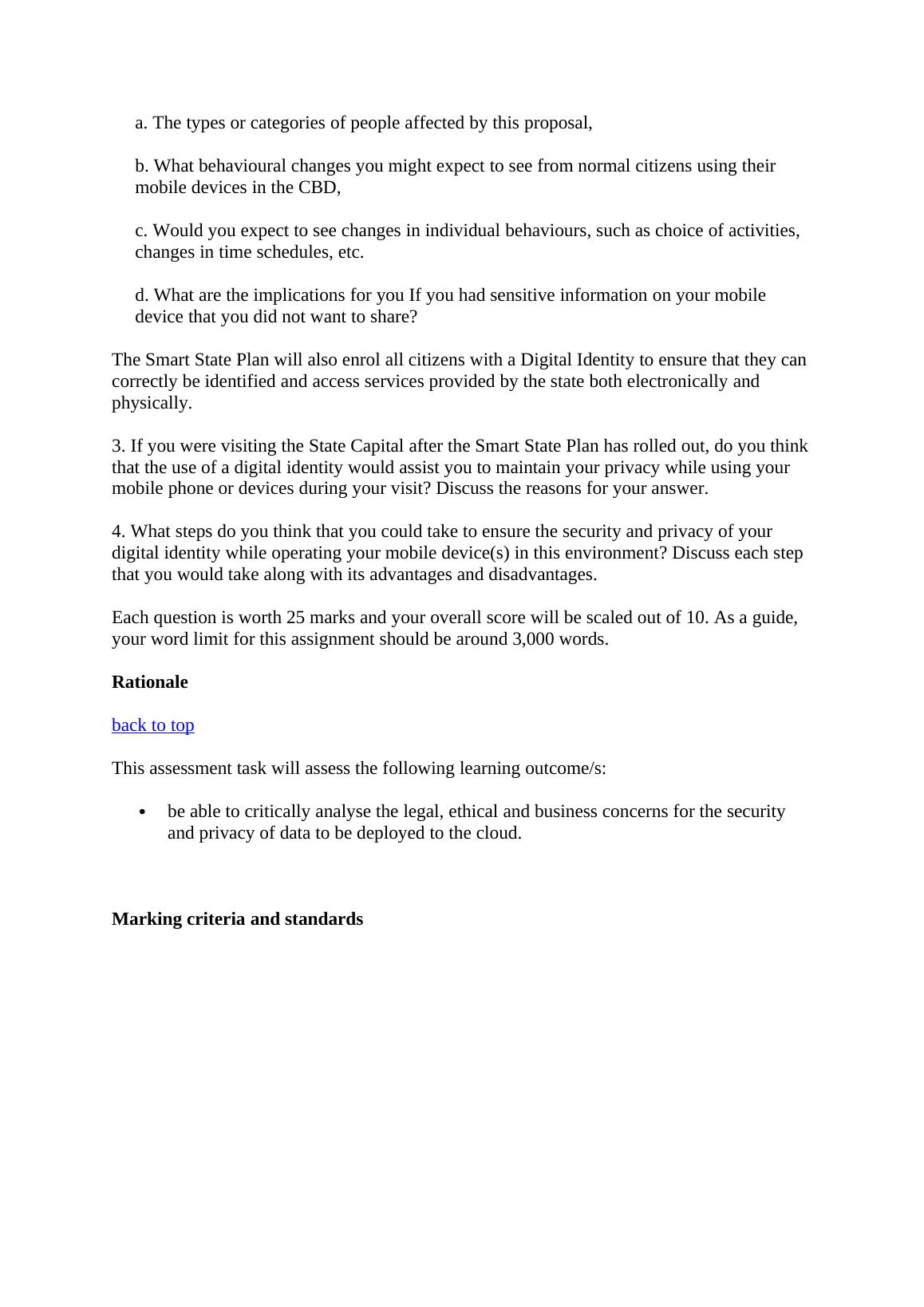
QuestionHDQ1. Smart Sensors (25 marks)Comprehensive exploration of privacyand ethical issues from both personal and behavioural viewpointsThorough exploration of privacy and ethicalissues with good personal and behavioural viewpointsQ2. WiFi hotspots (25 marks)Comprehensive exploration of security & sensitive data issues from both personal and behavioural viewpointsThorough exploration of security & sensitive data issues with many personal and behavioural viewpointsQ3. Digital Identity (25 marks)Comprehensive discussion of issues with use of digital identityThorough discussion of issues with use of digital identity Q4. Security & privacy controls (25 marks)Comprehensive exploration of steps to take to enhance security and privacy of mobile devicesThorough exploration of steps to take toenhance security and privacy devicesPresentation
Assessment item 2Risk AssessmentDue Date:1-Aug-2018Length-5000 wordsValue-25%TaskScenarioYou are the principal consultant for a community based Charity. The Charity is involved in locating and providing accommodation, mental health services, training and support services to disadvantaged people in the community. The Charity currently runs a small data centre that has some 50 x86 64 bit servers running mainly Windows Server 2008 R2 for desktop services, database and file services. It also has 10 Red Hat Enterprise Linux 5 servers to service public facing Web pages, Web services and support.The Charity is considering joining a community cloud provided by a public cloud vendor in order to provide a number of applications to all 500 support staff and administrative users. A small number of the Charity's applications are mission critical and the data that those applications use is both confidential and time sensitive.The community cloud would also be used to store the Charity's 200TB of data. The data would be held in a SaaS database run by the public cloud vendor. The Charity's data contains a considerable amount of confidential information about the people to whom the Charity provides services. The Charity collects PII data on the clients who use its services so that it can assist them to manage their different service requirements. This PII data also includes holding some digital identity data for some of the more disadvantaged clients, particularly if they also have mental health issues.

The cloud vendor has made a presentation to management that indicates that operational costswill drop dramatically if the cloud model is adopted. However, the Board of the Charity is concerned with the privacy and security of the data that it holds on the people that it provides services to in the community. It is concerned that a data breach may cause considerable damage to substantially disadvantaged people in the community.The Board asks that you prepare a report that proposes appropriate privacy and security policies for the Charity's data.The charity has also decided to:Purchase a HR and personnel management application from a US based company that provides a SaaS solution.oThe application will provide the charity with a complete HR suite, which will also include performance management. The application provider has advised that the company's main database is in California, with a replica in Dublin, Ireland. However,all data processing, configuration, maintenance, updates and feature releases are provided from the application provider's processing centre in Bangalore, India.oEmployee data will be uploaded from the charity daily at 12:00 AEST. This will be processed in Bangalore before being loaded into the main provider database.oEmployees can access their HR and Performance Management information througha link placed on the Charity intranet. Each employee will use their internal charitydigital ID to authenticate to the HR and Performance management system. The internal digital ID is generated by the charity's Active Directory instance and is used for internal authentication and authorisation.Move the charity payroll to a COTS (Commercial Off The Shelf) application that it will manage in a public cloud;Move the charity Intranet into a Microsoft SharePoint PaaS offering so that it can provideIntranet services to all agencies in the WofG.TasksYou have been engaged to provide a risk assessment for the planned moves to SaaS application offerings.You are to write a report that assesses the risks to the charity for just their planned moves in the HR area:1.Consider the data and information that the charity holds on its employees in the current HR system.1.Establish the existing threats and risks to the security of that data and informationcontained in the in-house HR database. (10 marks)2.Are there any additional risks and threats to employee data that may arise after migration to an SaaS application? (10 marks)3.Assess the resulting severity of risk and threat to employee data. (10 marks)2.Consider the privacy of the data for those employees who will move to an SaaS application.

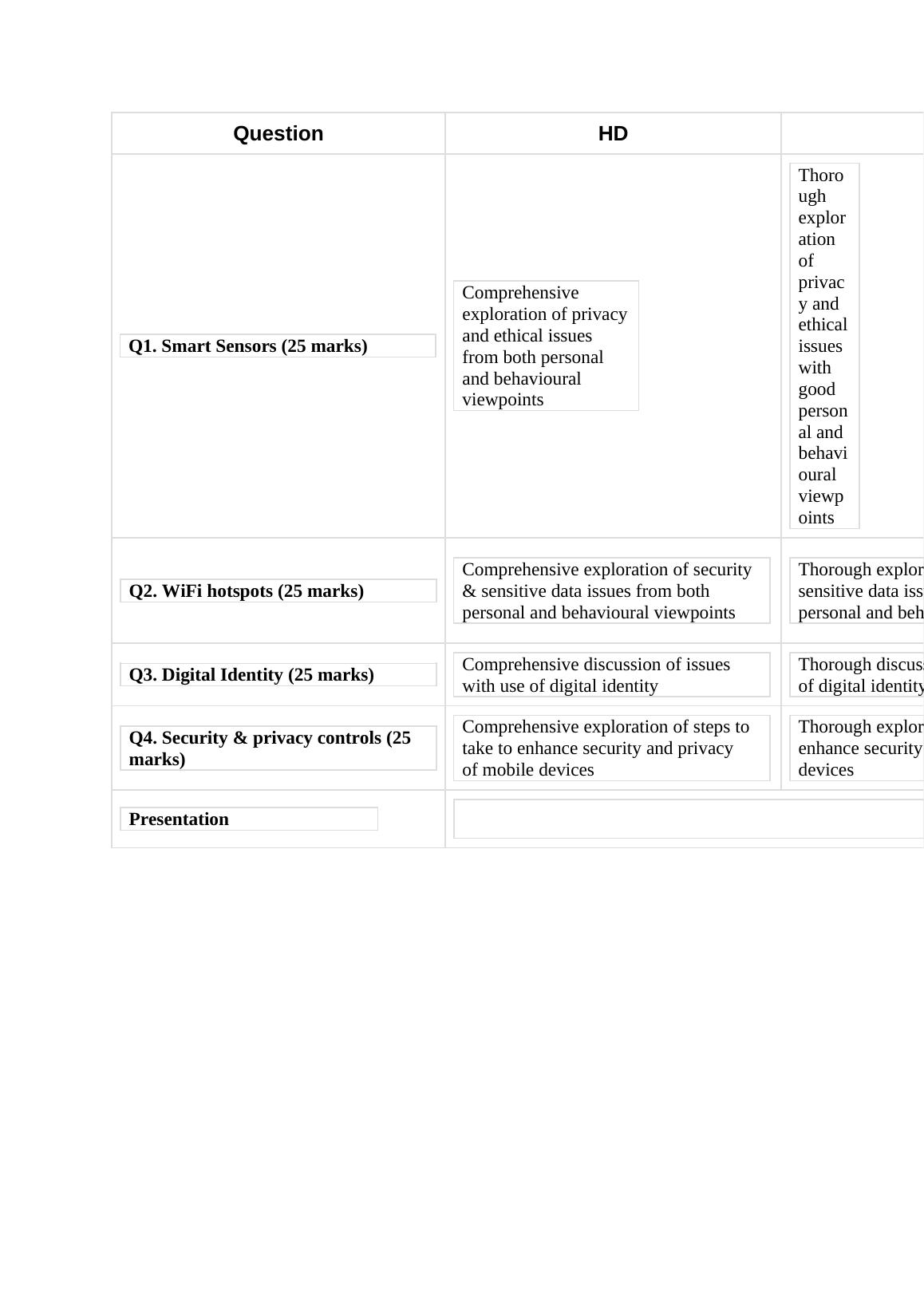
1.Establish the existing threats and risks to the privacy of that data and informationcontained in the in house HR database. (10 marks)2.Are there any additional risks and threats to the privacy of the employee data after migration to an SaaS application? (10 marks)3.Assess the resulting severity of risk and threat to the privacy of employee data. (10 marks)3.What are the threats and risks to the digital identities of charity employees from the moveto SaaS applications? (10 marks)4.Consider the operational solution and location(s) of the SaaS provider for HR management.Does either the operational solution, or the operational location, or both, increase or mitigate the threats and risks identified for the security and privacy of employee data? (20 marks)5.Are there any issues of ethics, data sensitivity or jurisdiction that should be considered by the charity? (10 marks)You are to provide a written report with the following headings:Security of Employee DataPrivacy of Employee DataDigital Identity IssuesProvider Solution IssuesData SensitivityAs a rough guide, the report should not be longer than about 5,000 words. RationaleThis assessment task will assess the following learning outcome/s:be able to examine the legal, business and privacy requirements for a cloud deploymentmodel.be able to evaluate the risk management requirements for a cloud deployment model.be able to critically analyse the legal, ethical and business concerns for the security and privacy of data to be deployed to the cloud.Marking criteria and standardsQuestionHDDIQ1.1. Existing threats to Security of Comprehensive exploration of threats Thorough exploration of threats and

End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Information Security and Privacy in Proposed Government's Smart Sensor and WiFi Networkslg...
|18
|4715
|464
Cloud Privacy And Securitylg...
|16
|3918
|206
Cloud Privacy and Securitylg...
|15
|4258
|259
Cloud Privacy and Securitylg...
|14
|4268
|50
Cloud Privacy and Securitylg...
|15
|4167
|116
Cloud privacy and securitylg...
|15
|4122
|53