COIT20264 Network Design: OZ Dispatch IT Services Logical Design
VerifiedAdded on 2023/03/31
|11
|1950
|180
Report
AI Summary
This report provides a detailed logical network design for OZ Dispatch IT Services, addressing business and technical goals, constraints, and tradeoffs. It includes a table of user communities, data stores, network applications, and traffic flows. The report explains and justifies the chosen logical network design, presenting diagrams with addressing and naming conventions. Routing and switching protocols, specifically OSPF and RSTP, are discussed, along with security mechanisms such as physical security, CIA triad principles, firewalls, and VLAN implementation. The design incorporates a hybrid topology with VPN for secure traffic control between headquarters and remote offices, emphasizing scalability, availability, and security. The document also provides the model for addressing and naming, and the explanation and justification of the logical network design of OZ Dispatch IT Services.

ASSESSMENT1
OZ Dispatch IT Services
Logical Network Design
By
NIDHI A PATEL
Student ID:12076996
RUHILA I VAHORA
Student ID:12067716
BIREN G PATEL
Student ID: 12067937
SHIVAM CHAUHAN
Student ID:12078765
OZ Dispatch IT Services
Logical Network Design
By
NIDHI A PATEL
Student ID:12076996
RUHILA I VAHORA
Student ID:12067716
BIREN G PATEL
Student ID: 12067937
SHIVAM CHAUHAN
Student ID:12078765
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


List of Business Goals and Constraints
According to LeBlanc, a good network design should recognize the fact that client’s requirements
exemplify a lot of technical and business goals. These include but not limited to scalability, availability,
security, affordability and manageability. Clients also need to specify a required level of network
performance also known as service level (LeBlanc, et al., 2015). OZ Dispatch is not an exception. It
requires the above mentioned requirements and meet these requirements, top-down technique will be
deployed. That is to say, the network design will be made by designing the upper layers of OSI reference
model first before moving lower layers. This kind of design pays attention on applications, the sessions
and information transport before choice of switches, media and routers that operate at other lower
layers. Below is a list of business goals for OZ Dispatch
i. Deliver the parcel to the customer
ii. Collect the parcel from suppliers
iii. Pay via phone and
iv. Working remotely form the DC centre
Business constraints denotes to the limitations which can either be physical, fiscal time limitations which
affects the achievement of a business goal. For OZ Dispatch Company, below are the possible business
constraints.
i. Security – it is challenging develop a security system for mobile and web funds transfer.
ii. Collection of parcels from the supplier will require some funding which may be a business
constraint.
List of Technical Goals and Tradeoffs
Analysing client’s technical goals helps the network engineer confidently give recommendations on
technologies which will perform client’s expectations. Below is a list of technical goals for OZ Dispatch
Company:
i. Availability
This is the time percentage when the system is available. Our subject company cannot afford to be
offline since tracking of luggage is done on 24/7. This implies that we must have a redundancy systems
that will minimize the rates of down times.
ii. Security
iii. Scalability
According to LeBlanc, a good network design should recognize the fact that client’s requirements
exemplify a lot of technical and business goals. These include but not limited to scalability, availability,
security, affordability and manageability. Clients also need to specify a required level of network
performance also known as service level (LeBlanc, et al., 2015). OZ Dispatch is not an exception. It
requires the above mentioned requirements and meet these requirements, top-down technique will be
deployed. That is to say, the network design will be made by designing the upper layers of OSI reference
model first before moving lower layers. This kind of design pays attention on applications, the sessions
and information transport before choice of switches, media and routers that operate at other lower
layers. Below is a list of business goals for OZ Dispatch
i. Deliver the parcel to the customer
ii. Collect the parcel from suppliers
iii. Pay via phone and
iv. Working remotely form the DC centre
Business constraints denotes to the limitations which can either be physical, fiscal time limitations which
affects the achievement of a business goal. For OZ Dispatch Company, below are the possible business
constraints.
i. Security – it is challenging develop a security system for mobile and web funds transfer.
ii. Collection of parcels from the supplier will require some funding which may be a business
constraint.
List of Technical Goals and Tradeoffs
Analysing client’s technical goals helps the network engineer confidently give recommendations on
technologies which will perform client’s expectations. Below is a list of technical goals for OZ Dispatch
Company:
i. Availability
This is the time percentage when the system is available. Our subject company cannot afford to be
offline since tracking of luggage is done on 24/7. This implies that we must have a redundancy systems
that will minimize the rates of down times.
ii. Security
iii. Scalability
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Scalability is a factor that determines the capability of a network design to adapt growth. This factor
puts in consideration the downsizing factor. OZ Dispatch network design will allow future growth and
relocation of devices.
iv. Performance
v. Adaptability and affordability
vi. Security
Mariño says, in a decision making process, there is a need to trade off one item against another. Trade-
off comprises of a sacrifice that has to be made in order to get a particular experience or product.
Despite the fact that network engineers make a lot of promises to customers during the initial stages in
network implementations, in ideal world meeting goals need making of trade-offs (Mariño, 2016). For
OZ Dispatch Company, to meet expectations for availability, redundant items are necessary, this implies
there is a raise in cost of network implementation. To meet the required performance, high-cost circuits
and components are required. Deployment of effective throughput for one application may cause
delayed problems of another program.
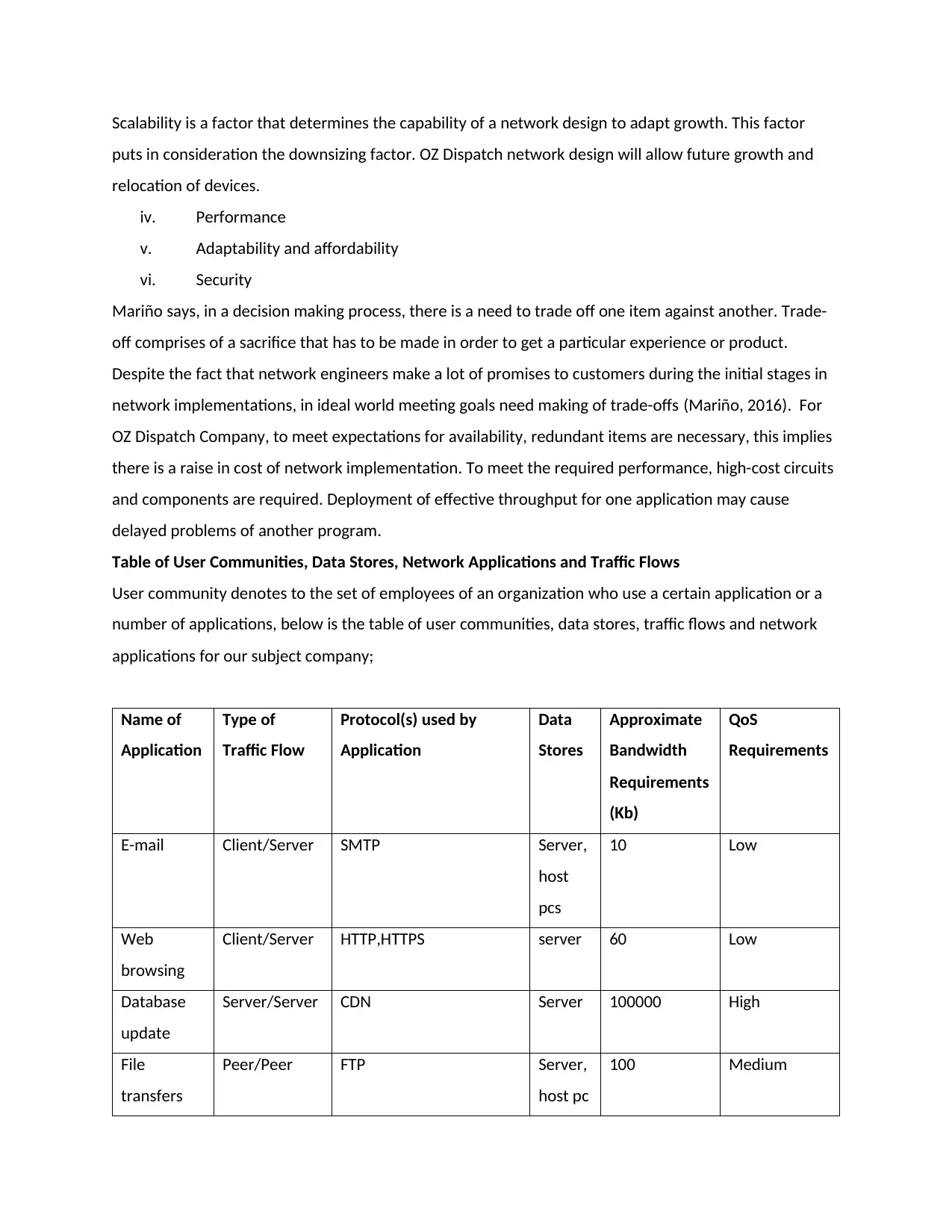
Table of User Communities, Data Stores, Network Applications and Traffic Flows
User community denotes to the set of employees of an organization who use a certain application or a
number of applications, below is the table of user communities, data stores, traffic flows and network
applications for our subject company;
Name of
Application
Type of
Traffic Flow
Protocol(s) used by
Application
Data
Stores
Approximate
Bandwidth
Requirements
(Kb)
QoS
Requirements
E-mail Client/Server SMTP Server,
host
pcs
10 Low
Web
browsing
Client/Server HTTP,HTTPS server 60 Low
Database
update
Server/Server CDN Server 100000 High
File
transfers
Peer/Peer FTP Server,
host pc
100 Medium
puts in consideration the downsizing factor. OZ Dispatch network design will allow future growth and
relocation of devices.
iv. Performance
v. Adaptability and affordability
vi. Security
Mariño says, in a decision making process, there is a need to trade off one item against another. Trade-
off comprises of a sacrifice that has to be made in order to get a particular experience or product.
Despite the fact that network engineers make a lot of promises to customers during the initial stages in
network implementations, in ideal world meeting goals need making of trade-offs (Mariño, 2016). For
OZ Dispatch Company, to meet expectations for availability, redundant items are necessary, this implies
there is a raise in cost of network implementation. To meet the required performance, high-cost circuits
and components are required. Deployment of effective throughput for one application may cause
delayed problems of another program.
Table of User Communities, Data Stores, Network Applications and Traffic Flows
User community denotes to the set of employees of an organization who use a certain application or a
number of applications, below is the table of user communities, data stores, traffic flows and network
applications for our subject company;
Name of
Application
Type of
Traffic Flow
Protocol(s) used by
Application
Data
Stores
Approximate
Bandwidth
Requirements
(Kb)
QoS
Requirements
E-mail Client/Server SMTP Server,
host
pcs
10 Low
Web
browsing
Client/Server HTTP,HTTPS server 60 Low
Database
update
Server/Server CDN Server 100000 High
File
transfers
Peer/Peer FTP Server,
host pc
100 Medium
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
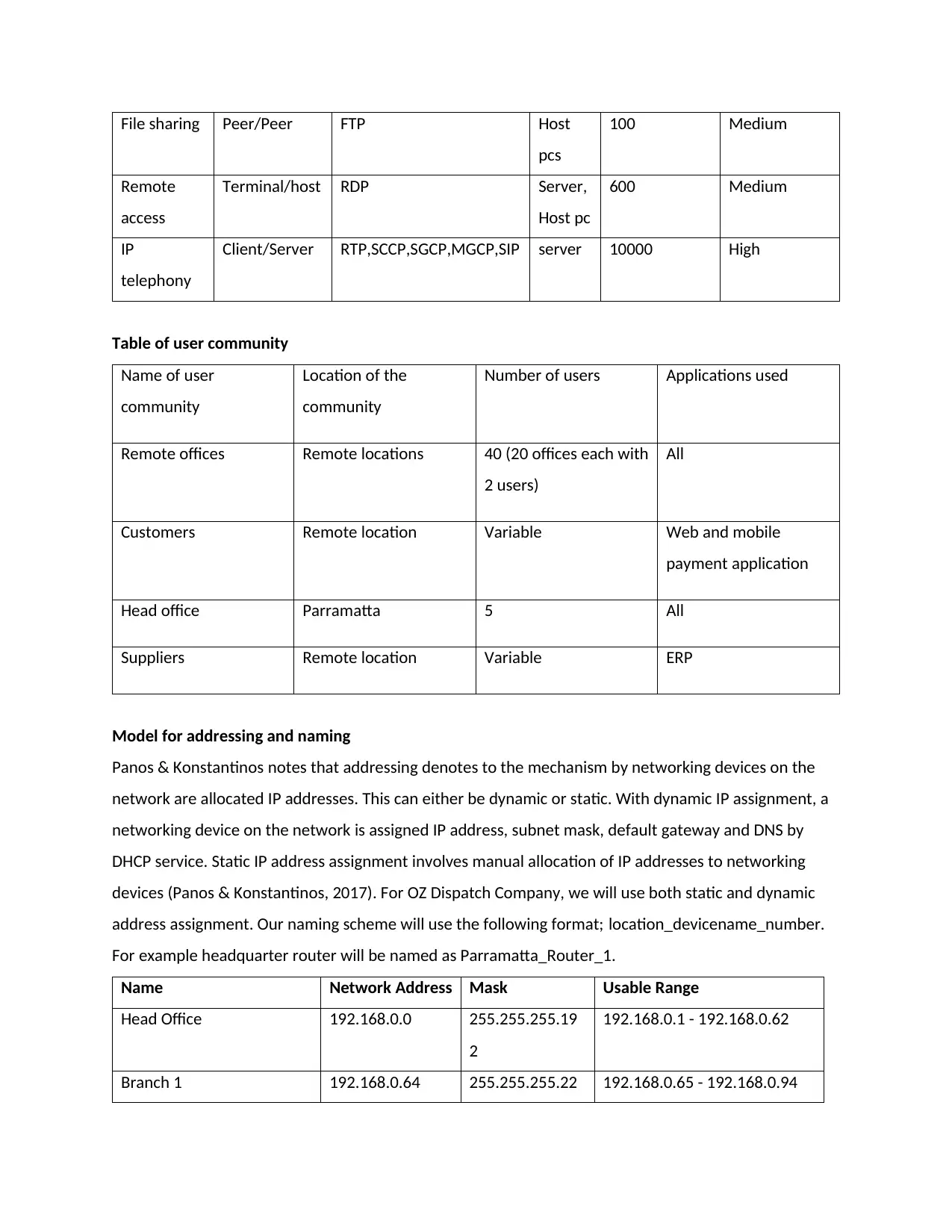
File sharing Peer/Peer FTP Host
pcs
100 Medium
Remote
access
Terminal/host RDP Server,
Host pc
600 Medium
IP
telephony
Client/Server RTP,SCCP,SGCP,MGCP,SIP server 10000 High
Table of user community
Name of user
community
Location of the
community
Number of users Applications used
Remote offices Remote locations 40 (20 offices each with
2 users)
All
Customers Remote location Variable Web and mobile
payment application
Head office Parramatta 5 All
Suppliers Remote location Variable ERP
Model for addressing and naming
Panos & Konstantinos notes that addressing denotes to the mechanism by networking devices on the
network are allocated IP addresses. This can either be dynamic or static. With dynamic IP assignment, a
networking device on the network is assigned IP address, subnet mask, default gateway and DNS by
DHCP service. Static IP address assignment involves manual allocation of IP addresses to networking
devices (Panos & Konstantinos, 2017). For OZ Dispatch Company, we will use both static and dynamic
address assignment. Our naming scheme will use the following format; location_devicename_number.
For example headquarter router will be named as Parramatta_Router_1.
Name Network Address Mask Usable Range
Head Office 192.168.0.0 255.255.255.19
2
192.168.0.1 - 192.168.0.62
Branch 1 192.168.0.64 255.255.255.22 192.168.0.65 - 192.168.0.94
pcs
100 Medium
Remote
access
Terminal/host RDP Server,
Host pc
600 Medium
IP
telephony
Client/Server RTP,SCCP,SGCP,MGCP,SIP server 10000 High
Table of user community
Name of user
community
Location of the
community
Number of users Applications used
Remote offices Remote locations 40 (20 offices each with
2 users)
All
Customers Remote location Variable Web and mobile
payment application
Head office Parramatta 5 All
Suppliers Remote location Variable ERP
Model for addressing and naming
Panos & Konstantinos notes that addressing denotes to the mechanism by networking devices on the
network are allocated IP addresses. This can either be dynamic or static. With dynamic IP assignment, a
networking device on the network is assigned IP address, subnet mask, default gateway and DNS by
DHCP service. Static IP address assignment involves manual allocation of IP addresses to networking
devices (Panos & Konstantinos, 2017). For OZ Dispatch Company, we will use both static and dynamic
address assignment. Our naming scheme will use the following format; location_devicename_number.
For example headquarter router will be named as Parramatta_Router_1.
Name Network Address Mask Usable Range
Head Office 192.168.0.0 255.255.255.19
2
192.168.0.1 - 192.168.0.62
Branch 1 192.168.0.64 255.255.255.22 192.168.0.65 - 192.168.0.94
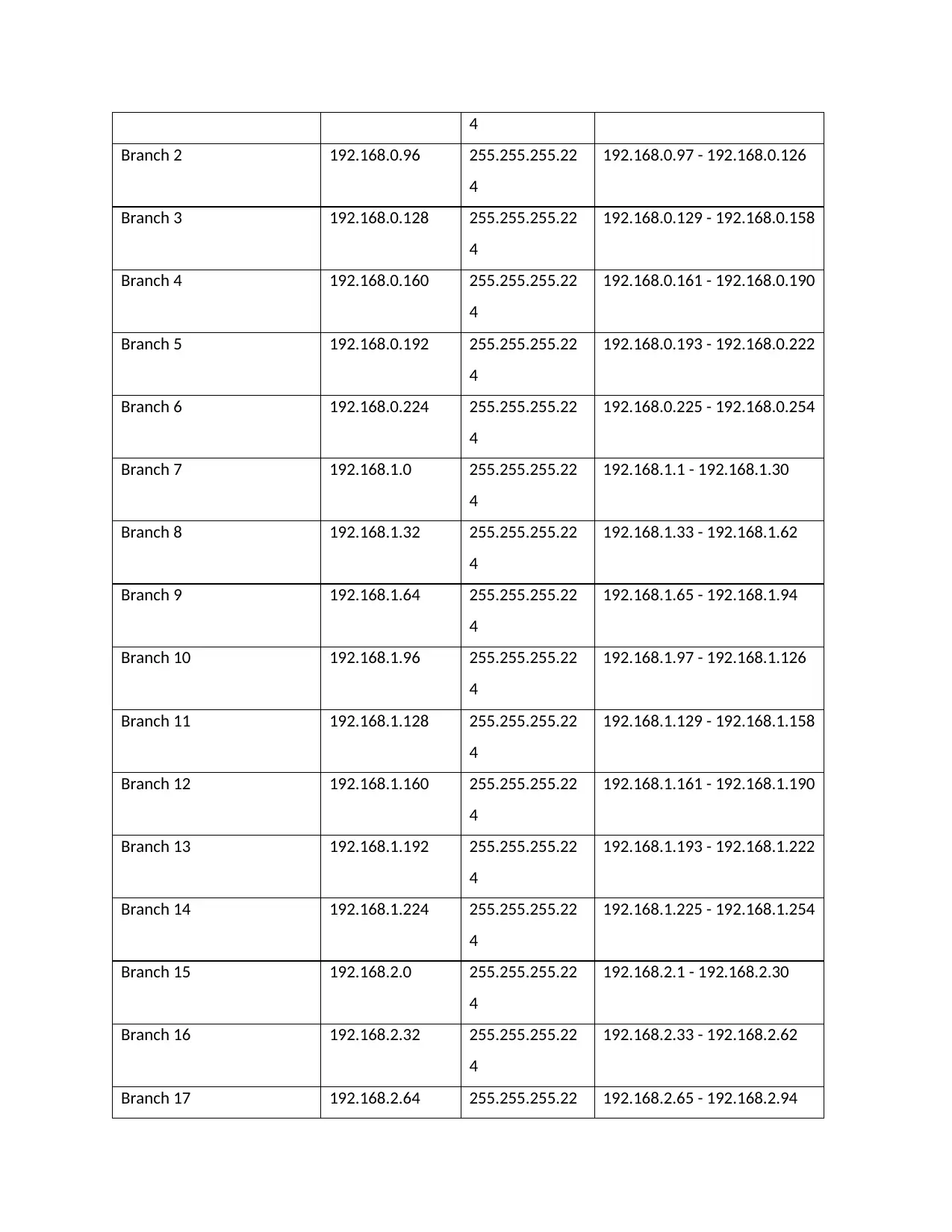
4
Branch 2 192.168.0.96 255.255.255.22
4
192.168.0.97 - 192.168.0.126
Branch 3 192.168.0.128 255.255.255.22
4
192.168.0.129 - 192.168.0.158
Branch 4 192.168.0.160 255.255.255.22
4
192.168.0.161 - 192.168.0.190
Branch 5 192.168.0.192 255.255.255.22
4
192.168.0.193 - 192.168.0.222
Branch 6 192.168.0.224 255.255.255.22
4
192.168.0.225 - 192.168.0.254
Branch 7 192.168.1.0 255.255.255.22
4
192.168.1.1 - 192.168.1.30
Branch 8 192.168.1.32 255.255.255.22
4
192.168.1.33 - 192.168.1.62
Branch 9 192.168.1.64 255.255.255.22
4
192.168.1.65 - 192.168.1.94
Branch 10 192.168.1.96 255.255.255.22
4
192.168.1.97 - 192.168.1.126
Branch 11 192.168.1.128 255.255.255.22
4
192.168.1.129 - 192.168.1.158
Branch 12 192.168.1.160 255.255.255.22
4
192.168.1.161 - 192.168.1.190
Branch 13 192.168.1.192 255.255.255.22
4
192.168.1.193 - 192.168.1.222
Branch 14 192.168.1.224 255.255.255.22
4
192.168.1.225 - 192.168.1.254
Branch 15 192.168.2.0 255.255.255.22
4
192.168.2.1 - 192.168.2.30
Branch 16 192.168.2.32 255.255.255.22
4
192.168.2.33 - 192.168.2.62
Branch 17 192.168.2.64 255.255.255.22 192.168.2.65 - 192.168.2.94
Branch 2 192.168.0.96 255.255.255.22
4
192.168.0.97 - 192.168.0.126
Branch 3 192.168.0.128 255.255.255.22
4
192.168.0.129 - 192.168.0.158
Branch 4 192.168.0.160 255.255.255.22
4
192.168.0.161 - 192.168.0.190
Branch 5 192.168.0.192 255.255.255.22
4
192.168.0.193 - 192.168.0.222
Branch 6 192.168.0.224 255.255.255.22
4
192.168.0.225 - 192.168.0.254
Branch 7 192.168.1.0 255.255.255.22
4
192.168.1.1 - 192.168.1.30
Branch 8 192.168.1.32 255.255.255.22
4
192.168.1.33 - 192.168.1.62
Branch 9 192.168.1.64 255.255.255.22
4
192.168.1.65 - 192.168.1.94
Branch 10 192.168.1.96 255.255.255.22
4
192.168.1.97 - 192.168.1.126
Branch 11 192.168.1.128 255.255.255.22
4
192.168.1.129 - 192.168.1.158
Branch 12 192.168.1.160 255.255.255.22
4
192.168.1.161 - 192.168.1.190
Branch 13 192.168.1.192 255.255.255.22
4
192.168.1.193 - 192.168.1.222
Branch 14 192.168.1.224 255.255.255.22
4
192.168.1.225 - 192.168.1.254
Branch 15 192.168.2.0 255.255.255.22
4
192.168.2.1 - 192.168.2.30
Branch 16 192.168.2.32 255.255.255.22
4
192.168.2.33 - 192.168.2.62
Branch 17 192.168.2.64 255.255.255.22 192.168.2.65 - 192.168.2.94
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
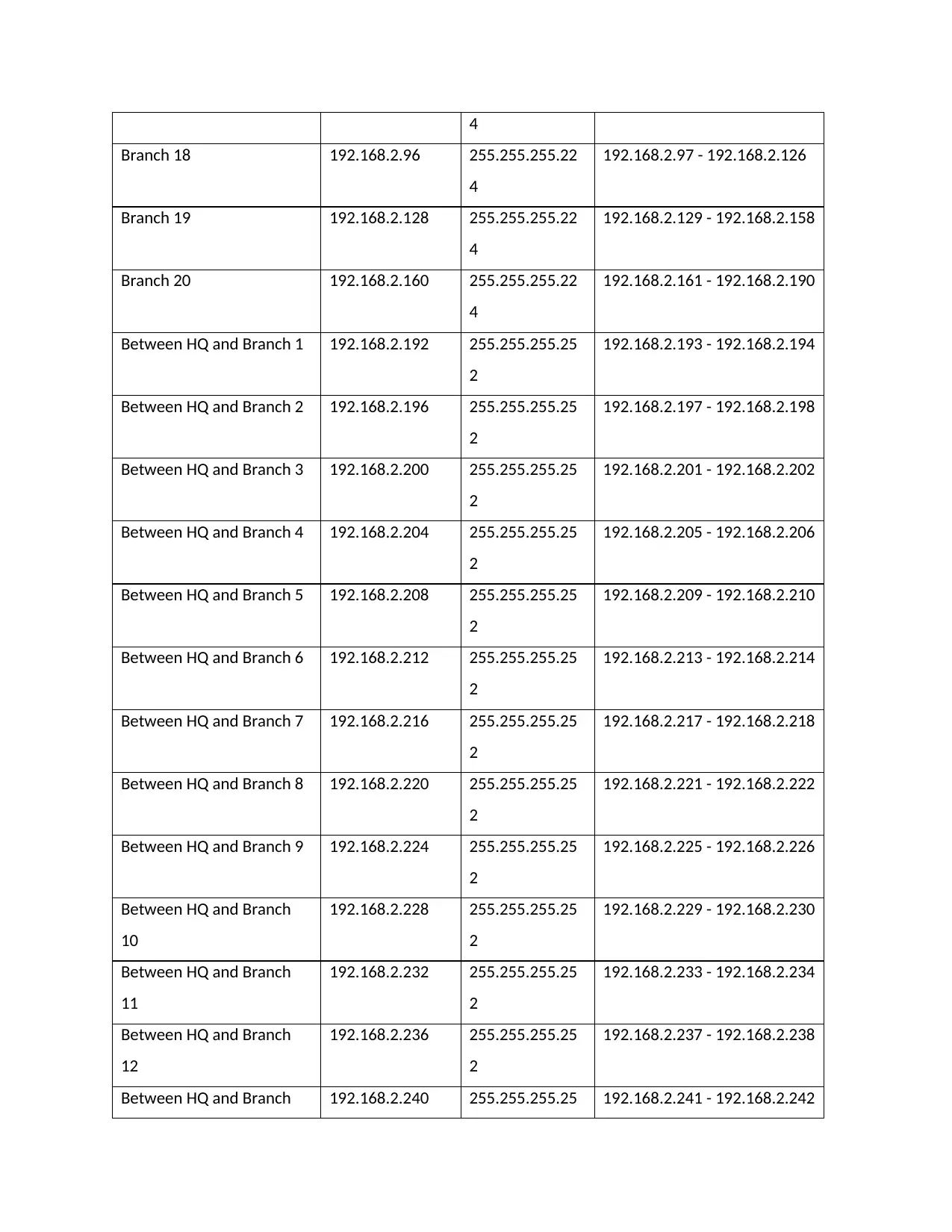
4
Branch 18 192.168.2.96 255.255.255.22
4
192.168.2.97 - 192.168.2.126
Branch 19 192.168.2.128 255.255.255.22
4
192.168.2.129 - 192.168.2.158
Branch 20 192.168.2.160 255.255.255.22
4
192.168.2.161 - 192.168.2.190
Between HQ and Branch 1 192.168.2.192 255.255.255.25
2
192.168.2.193 - 192.168.2.194
Between HQ and Branch 2 192.168.2.196 255.255.255.25
2
192.168.2.197 - 192.168.2.198
Between HQ and Branch 3 192.168.2.200 255.255.255.25
2
192.168.2.201 - 192.168.2.202
Between HQ and Branch 4 192.168.2.204 255.255.255.25
2
192.168.2.205 - 192.168.2.206
Between HQ and Branch 5 192.168.2.208 255.255.255.25
2
192.168.2.209 - 192.168.2.210
Between HQ and Branch 6 192.168.2.212 255.255.255.25
2
192.168.2.213 - 192.168.2.214
Between HQ and Branch 7 192.168.2.216 255.255.255.25
2
192.168.2.217 - 192.168.2.218
Between HQ and Branch 8 192.168.2.220 255.255.255.25
2
192.168.2.221 - 192.168.2.222
Between HQ and Branch 9 192.168.2.224 255.255.255.25
2
192.168.2.225 - 192.168.2.226
Between HQ and Branch
10
192.168.2.228 255.255.255.25
2
192.168.2.229 - 192.168.2.230
Between HQ and Branch
11
192.168.2.232 255.255.255.25
2
192.168.2.233 - 192.168.2.234
Between HQ and Branch
12
192.168.2.236 255.255.255.25
2
192.168.2.237 - 192.168.2.238
Between HQ and Branch 192.168.2.240 255.255.255.25 192.168.2.241 - 192.168.2.242
Branch 18 192.168.2.96 255.255.255.22
4
192.168.2.97 - 192.168.2.126
Branch 19 192.168.2.128 255.255.255.22
4
192.168.2.129 - 192.168.2.158
Branch 20 192.168.2.160 255.255.255.22
4
192.168.2.161 - 192.168.2.190
Between HQ and Branch 1 192.168.2.192 255.255.255.25
2
192.168.2.193 - 192.168.2.194
Between HQ and Branch 2 192.168.2.196 255.255.255.25
2
192.168.2.197 - 192.168.2.198
Between HQ and Branch 3 192.168.2.200 255.255.255.25
2
192.168.2.201 - 192.168.2.202
Between HQ and Branch 4 192.168.2.204 255.255.255.25
2
192.168.2.205 - 192.168.2.206
Between HQ and Branch 5 192.168.2.208 255.255.255.25
2
192.168.2.209 - 192.168.2.210
Between HQ and Branch 6 192.168.2.212 255.255.255.25
2
192.168.2.213 - 192.168.2.214
Between HQ and Branch 7 192.168.2.216 255.255.255.25
2
192.168.2.217 - 192.168.2.218
Between HQ and Branch 8 192.168.2.220 255.255.255.25
2
192.168.2.221 - 192.168.2.222
Between HQ and Branch 9 192.168.2.224 255.255.255.25
2
192.168.2.225 - 192.168.2.226
Between HQ and Branch
10
192.168.2.228 255.255.255.25
2
192.168.2.229 - 192.168.2.230
Between HQ and Branch
11
192.168.2.232 255.255.255.25
2
192.168.2.233 - 192.168.2.234
Between HQ and Branch
12
192.168.2.236 255.255.255.25
2
192.168.2.237 - 192.168.2.238
Between HQ and Branch 192.168.2.240 255.255.255.25 192.168.2.241 - 192.168.2.242
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
13 2
Between HQ and Branch
14
192.168.2.244 255.255.255.25
2
192.168.2.245 - 192.168.2.246
Between HQ and Branch
15
192.168.2.248 255.255.255.25
2
192.168.2.249 - 192.168.2.250
Between HQ and Branch
16
192.168.2.252 255.255.255.25
2
192.168.2.253 - 192.168.2.254
Between HQ and Branch
17
192.168.3.0 255.255.255.25
2
192.168.3.1 - 192.168.3.2
Between HQ and Branch
18
192.168.3.4 255.255.255.25
2
192.168.3.5 - 192.168.3.6
Between HQ and Branch
19
192.168.3.8 255.255.255.25
2
192.168.3.9 - 192.168.3.10
Between HQ and Branch
20
192.168.3.12 255.255.255.25
2
192.168.3.13 - 192.168.3.14
Explanation and justification of the logical network design
According to Cain, et al, logical network design denotes to how the network appears to the user as a
sole, different entity though it may in fact be either an entity created from a number of networks. IP
addressing scheme defines a logical network (Cain, et al., 2015). For OZ Dispatch Company, we assume
that our ISP provide address is 180.16.0.0/16. Our logical network design will be determined by the
following table whose contents are location, network address, usable address range, subnet mask and
broadcast addresses.
(Rogers, 2014)
For large organisations, the hybrid topology with VPN is applied. The topology can be applied at
headquarters and remote offices to control the traffic. The major advantage of using such topology is
that accessed network can be more secured. As, well as using the hybrid topology can minimize the
overall cost of the company. Here, large customers are attached with the system so firewall is
maintained between the ISP and headquarter router. The disadvantage of using such approach is the
design generated is more complex and more ACLs are connected to the network to control the whole
delivery system of OZ Dispatch.
Between HQ and Branch
14
192.168.2.244 255.255.255.25
2
192.168.2.245 - 192.168.2.246
Between HQ and Branch
15
192.168.2.248 255.255.255.25
2
192.168.2.249 - 192.168.2.250
Between HQ and Branch
16
192.168.2.252 255.255.255.25
2
192.168.2.253 - 192.168.2.254
Between HQ and Branch
17
192.168.3.0 255.255.255.25
2
192.168.3.1 - 192.168.3.2
Between HQ and Branch
18
192.168.3.4 255.255.255.25
2
192.168.3.5 - 192.168.3.6
Between HQ and Branch
19
192.168.3.8 255.255.255.25
2
192.168.3.9 - 192.168.3.10
Between HQ and Branch
20
192.168.3.12 255.255.255.25
2
192.168.3.13 - 192.168.3.14
Explanation and justification of the logical network design
According to Cain, et al, logical network design denotes to how the network appears to the user as a
sole, different entity though it may in fact be either an entity created from a number of networks. IP
addressing scheme defines a logical network (Cain, et al., 2015). For OZ Dispatch Company, we assume
that our ISP provide address is 180.16.0.0/16. Our logical network design will be determined by the
following table whose contents are location, network address, usable address range, subnet mask and
broadcast addresses.
(Rogers, 2014)
For large organisations, the hybrid topology with VPN is applied. The topology can be applied at
headquarters and remote offices to control the traffic. The major advantage of using such topology is
that accessed network can be more secured. As, well as using the hybrid topology can minimize the
overall cost of the company. Here, large customers are attached with the system so firewall is
maintained between the ISP and headquarter router. The disadvantage of using such approach is the
design generated is more complex and more ACLs are connected to the network to control the whole
delivery system of OZ Dispatch.
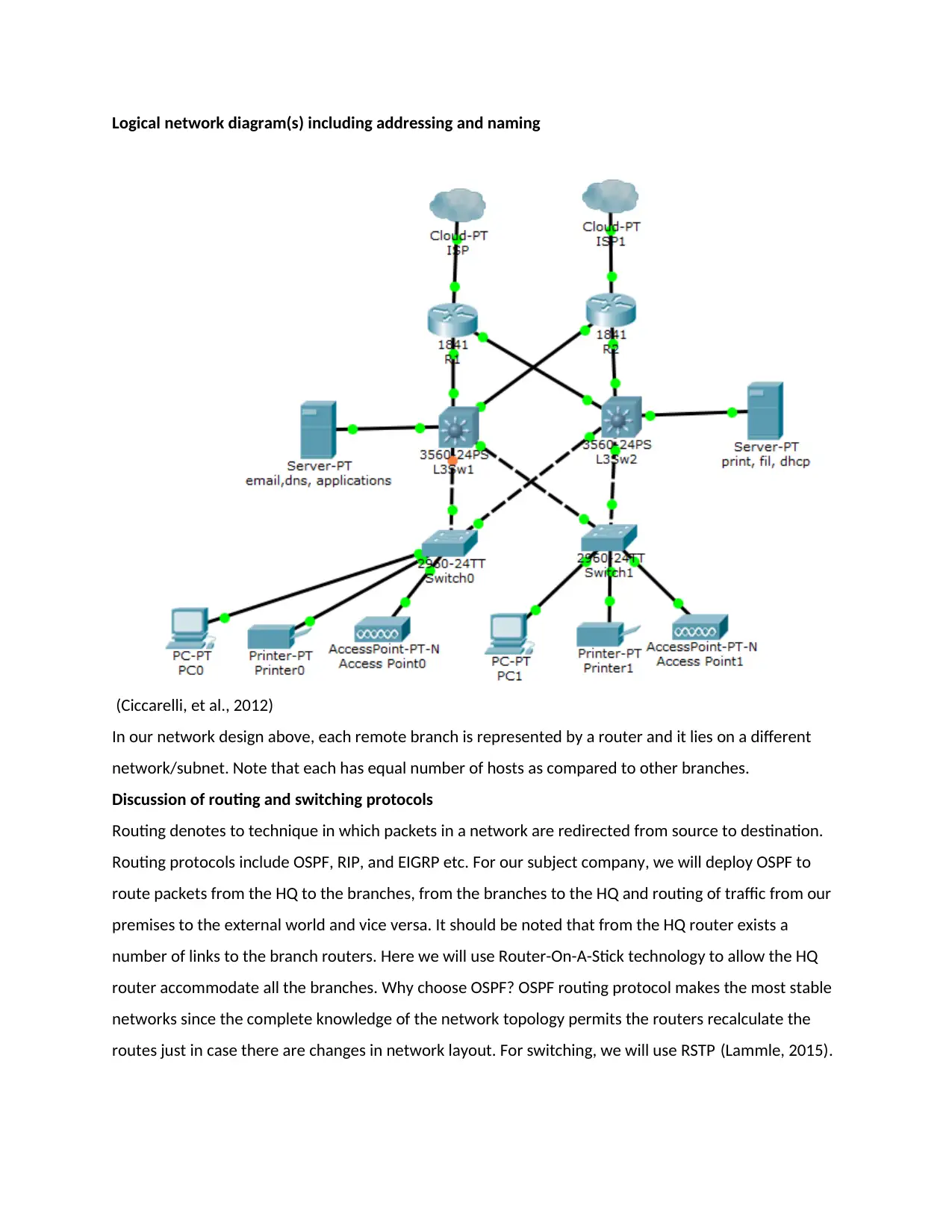
Logical network diagram(s) including addressing and naming
(Ciccarelli, et al., 2012)
In our network design above, each remote branch is represented by a router and it lies on a different
network/subnet. Note that each has equal number of hosts as compared to other branches.
Discussion of routing and switching protocols
Routing denotes to technique in which packets in a network are redirected from source to destination.
Routing protocols include OSPF, RIP, and EIGRP etc. For our subject company, we will deploy OSPF to
route packets from the HQ to the branches, from the branches to the HQ and routing of traffic from our
premises to the external world and vice versa. It should be noted that from the HQ router exists a
number of links to the branch routers. Here we will use Router-On-A-Stick technology to allow the HQ
router accommodate all the branches. Why choose OSPF? OSPF routing protocol makes the most stable
networks since the complete knowledge of the network topology permits the routers recalculate the
routes just in case there are changes in network layout. For switching, we will use RSTP (Lammle, 2015).
(Ciccarelli, et al., 2012)
In our network design above, each remote branch is represented by a router and it lies on a different
network/subnet. Note that each has equal number of hosts as compared to other branches.
Discussion of routing and switching protocols
Routing denotes to technique in which packets in a network are redirected from source to destination.
Routing protocols include OSPF, RIP, and EIGRP etc. For our subject company, we will deploy OSPF to
route packets from the HQ to the branches, from the branches to the HQ and routing of traffic from our
premises to the external world and vice versa. It should be noted that from the HQ router exists a
number of links to the branch routers. Here we will use Router-On-A-Stick technology to allow the HQ
router accommodate all the branches. Why choose OSPF? OSPF routing protocol makes the most stable
networks since the complete knowledge of the network topology permits the routers recalculate the
routes just in case there are changes in network layout. For switching, we will use RSTP (Lammle, 2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Rapid Spanning tree protocol is our best protocol for switching due its fast convergence time. It has an
approximate convergence time of 2 seconds.
Discussion of security mechanisms
Network security is key every for every institution which carries out its business processes digitally since
out there, there are numerous flux of hackers who would want to break into organizational systems with
ill motive intends. For our network design for OZ Dispatch Company, we will use both physical and
logical mechanisms to protect our subject company. Physical mechanisms will include strong room
server rooms, use of door locks, use of CCTV cameras, use of biometric systems for access of server
room and use of Occurrence Book during entry and exit of the server rooms. Logical mechanism will
include use of CIA triad to protect our network systems. That is to say, confidentiality, integrity and
authenticity will be highly regarded in our network system.
Firewall also will be one of our security mechanisms to secure the network. The firewall will be placed at
the edge router so that it can monitor the incoming and outgoing traffic.
VLAN implementation will also be one of the security measures that will be put in place. By having vlans,
just in case one of the vlans is invaded by the attackers, rest of the VLANs will still be safe, (Daimi,
2017).
approximate convergence time of 2 seconds.
Discussion of security mechanisms
Network security is key every for every institution which carries out its business processes digitally since
out there, there are numerous flux of hackers who would want to break into organizational systems with
ill motive intends. For our network design for OZ Dispatch Company, we will use both physical and
logical mechanisms to protect our subject company. Physical mechanisms will include strong room
server rooms, use of door locks, use of CCTV cameras, use of biometric systems for access of server
room and use of Occurrence Book during entry and exit of the server rooms. Logical mechanism will
include use of CIA triad to protect our network systems. That is to say, confidentiality, integrity and
authenticity will be highly regarded in our network system.
Firewall also will be one of our security mechanisms to secure the network. The firewall will be placed at
the edge router so that it can monitor the incoming and outgoing traffic.
VLAN implementation will also be one of the security measures that will be put in place. By having vlans,
just in case one of the vlans is invaded by the attackers, rest of the VLANs will still be safe, (Daimi,
2017).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Cain, N., Luescher, . & Flynn, ., 2015. Logical networks. In: Microsoft System Center Building a Virtualized
Network Solution. Carmel, Indiana: Sams Publishing, pp. 67-77.
Ciccarelli, P., Faulknern, . & FitzGerald, ., 2012. Introduction to Networking Basics. 2nd ed. Hoboken:
John Wiley & Sons.
Daimi, K., 2017. In: Computer and Network Security Essentials. Salmon Tower Building New York City:
Springer, pp. 333-410.
Lammle, T., 2015. CompTIA Network+ Study Guide, (Exam: N10-006). 4th ed. New York City: John Wiley
& Sons..
LeBlanc, P., Moss, . M. & Chinchilla, ., 2015. Overview of business Intelligence. In: Applied Microsoft
Business Intelligence. Hoboken, New Jersey: John Wiley & Sons. , pp. 78 -99.
Mariño, P. P., 2016. Optimization of Computer Networks: Modeling and Algorithms: A Hands-On
Approach. 3rd ed. Hoboken, New Jersey: John Wiley & Sons.
Panos, P. & Konstantinos, ., 2017. Network Design And Optimization For Smart Cities. 3rd ed. Singapore:
World Scientific.
Rogers, B. E., 2014. CompTIA Mobility+ Certification All-in-One Exam Guide. 3rd ed. New York: McGraw
Hill Professional.
Cain, N., Luescher, . & Flynn, ., 2015. Logical networks. In: Microsoft System Center Building a Virtualized
Network Solution. Carmel, Indiana: Sams Publishing, pp. 67-77.
Ciccarelli, P., Faulknern, . & FitzGerald, ., 2012. Introduction to Networking Basics. 2nd ed. Hoboken:
John Wiley & Sons.
Daimi, K., 2017. In: Computer and Network Security Essentials. Salmon Tower Building New York City:
Springer, pp. 333-410.
Lammle, T., 2015. CompTIA Network+ Study Guide, (Exam: N10-006). 4th ed. New York City: John Wiley
& Sons..
LeBlanc, P., Moss, . M. & Chinchilla, ., 2015. Overview of business Intelligence. In: Applied Microsoft
Business Intelligence. Hoboken, New Jersey: John Wiley & Sons. , pp. 78 -99.
Mariño, P. P., 2016. Optimization of Computer Networks: Modeling and Algorithms: A Hands-On
Approach. 3rd ed. Hoboken, New Jersey: John Wiley & Sons.
Panos, P. & Konstantinos, ., 2017. Network Design And Optimization For Smart Cities. 3rd ed. Singapore:
World Scientific.
Rogers, B. E., 2014. CompTIA Mobility+ Certification All-in-One Exam Guide. 3rd ed. New York: McGraw
Hill Professional.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





