Singapore Gaming Academy WAN Solution Network Report
VerifiedAdded on 2020/04/21
|25
|4952
|250
Report
AI Summary
This report details a proposed Wide Area Network (WAN) solution for the Singapore Gaming Academy, addressing its current network issues. The solution encompasses the implementation of Local Area Networks (LANs) and Wireless LANs (WLANs), replacing the existing 100Mbps Ethernet network. It includes the deployment of wireless access points, a backbone network for high-volume data transfer, and a comprehensive IP addressing scheme. The report outlines hardware requirements, switching protocols (Spanning Tree, Ether channel, VLAN), routing protocols (EIGRP, HSRP), and Voice over IP (VOIP) integration. Network security is a core focus, with discussions on password protection, Access Control Lists (ACLs), switch port security, firewalls, and Intrusion Detection/Prevention Systems (IDS/IPS). Furthermore, the report incorporates biometric security, network expansion plans, WAN implementation, and IPv6 addressing. Network diagrams illustrate the proposed WAN implementation, wireless access points, and backbone network, including firewall integration. The report aims to enhance connectivity, communication, and security within the academy's network.

Running head: COMPUTER NETWORKING
Computer Networking: Network Report
Name of the Student
Name of the University
Author’s Note
Computer Networking: Network Report
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
COMPUTER NETWORKING
Executive Summary
The report is prepared for Singapore gaming Academy for the proposal of a WAN solution for its
school campus. The WAN solution is proposed and it meets all the requirement of the
organization and mitigate the current problem faced by the organization. The router interface of
the network are configured with an IP addressing scheme and a remote connection is created
between different universities for the development of the network solution. The different
department of the university are connected using different vlan and the security of the network is
taken into consideration for the development of the network solution.
COMPUTER NETWORKING
Executive Summary
The report is prepared for Singapore gaming Academy for the proposal of a WAN solution for its
school campus. The WAN solution is proposed and it meets all the requirement of the
organization and mitigate the current problem faced by the organization. The router interface of
the network are configured with an IP addressing scheme and a remote connection is created
between different universities for the development of the network solution. The different
department of the university are connected using different vlan and the security of the network is
taken into consideration for the development of the network solution.

2
COMPUTER NETWORKING
Table of Contents
1. Introduction..................................................................................................................................5
1.1 Campus Background..............................................................................................................5
1.2 Current Issue Encounter........................................................................................................5
1.3 Objective................................................................................................................................6
2. Proposed Network Solution.........................................................................................................7
2.1 Implementation of LAN and WLAN for the Academy which replace the current wired
100Mbps Ethernet network.........................................................................................................7
2.2. Implementation of access points for wireless access for the students, staff and guests.......7
2.3. To link up all the department together on to a backbone network to support higher volume
of data..........................................................................................................................................8
2.4. IP Address Allocation...........................................................................................................8
2.5. Hardware..............................................................................................................................9
2.6. Switching............................................................................................................................10
2.6.1 Spanning Tree...............................................................................................................10
2.6.2 Ether channel................................................................................................................11
2.6.3 VLAN...........................................................................................................................11
2.7 Routing................................................................................................................................11
2.7.1 EIGRP...........................................................................................................................11
2.7.2 HSRP............................................................................................................................12
COMPUTER NETWORKING
Table of Contents
1. Introduction..................................................................................................................................5
1.1 Campus Background..............................................................................................................5
1.2 Current Issue Encounter........................................................................................................5
1.3 Objective................................................................................................................................6
2. Proposed Network Solution.........................................................................................................7
2.1 Implementation of LAN and WLAN for the Academy which replace the current wired
100Mbps Ethernet network.........................................................................................................7
2.2. Implementation of access points for wireless access for the students, staff and guests.......7
2.3. To link up all the department together on to a backbone network to support higher volume
of data..........................................................................................................................................8
2.4. IP Address Allocation...........................................................................................................8
2.5. Hardware..............................................................................................................................9
2.6. Switching............................................................................................................................10
2.6.1 Spanning Tree...............................................................................................................10
2.6.2 Ether channel................................................................................................................11
2.6.3 VLAN...........................................................................................................................11
2.7 Routing................................................................................................................................11
2.7.1 EIGRP...........................................................................................................................11
2.7.2 HSRP............................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
COMPUTER NETWORKING
2.8 VOIP....................................................................................................................................12
2.9 Wi-Fi....................................................................................................................................13
2.10 Network Security...............................................................................................................13
2.10.1 Password Protection....................................................................................................13
2.10.2 Access List (ACL)......................................................................................................13
2.10.3 Switch Port Security...................................................................................................14
2.10.4 Firewall.......................................................................................................................14
2.10.5 Intrusion Detection System (IDS) and Intrusion Prevention System (IPS)................14
2.11. Biometric..........................................................................................................................15
2.11.1 Advantages of Biometric system................................................................................16
2.11.2 Disadvantages of biometric system............................................................................17
2.12. Further network expansion at the Academy.....................................................................18
2.13. Implementation of WAN..................................................................................................18
2.14. Implementation of IPv6 addressing..................................................................................19
3.0. Network Diagrams for the school network.............................................................................20
3.1. Network Diagram for Implementation of WAN to automate the data transfer between the
school and possible two overseas campuses in Asia Pacific.....................................................20
3.2. Network Diagram for Implement access points for wireless access for the students, staff
and guests..................................................................................................................................20
3.3. Network Diagram for backbone network...........................................................................21
COMPUTER NETWORKING
2.8 VOIP....................................................................................................................................12
2.9 Wi-Fi....................................................................................................................................13
2.10 Network Security...............................................................................................................13
2.10.1 Password Protection....................................................................................................13
2.10.2 Access List (ACL)......................................................................................................13
2.10.3 Switch Port Security...................................................................................................14
2.10.4 Firewall.......................................................................................................................14
2.10.5 Intrusion Detection System (IDS) and Intrusion Prevention System (IPS)................14
2.11. Biometric..........................................................................................................................15
2.11.1 Advantages of Biometric system................................................................................16
2.11.2 Disadvantages of biometric system............................................................................17
2.12. Further network expansion at the Academy.....................................................................18
2.13. Implementation of WAN..................................................................................................18
2.14. Implementation of IPv6 addressing..................................................................................19
3.0. Network Diagrams for the school network.............................................................................20
3.1. Network Diagram for Implementation of WAN to automate the data transfer between the
school and possible two overseas campuses in Asia Pacific.....................................................20
3.2. Network Diagram for Implement access points for wireless access for the students, staff
and guests..................................................................................................................................20
3.3. Network Diagram for backbone network...........................................................................21
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
COMPUTER NETWORKING
3.4. Add firewalls in all the network diagrams..........................................................................22
4. Conclusion.................................................................................................................................22
5. Bibliography..............................................................................................................................23
COMPUTER NETWORKING
3.4. Add firewalls in all the network diagrams..........................................................................22
4. Conclusion.................................................................................................................................22
5. Bibliography..............................................................................................................................23

5
COMPUTER NETWORKING
1. Introduction
The report is prepared for Singapore Gaming Academy providing a brief description of
the campus and the current problem faced in the campus. A network solution is proposed for the
university with proper IP addressing scheme for all the interface of the device used for the
configuration of the network solution. A list of the hardware and the protocol used for the
implementation of the network is given for estimation of the cost of the network solution. The
security of the network is also implemented with the application of the password protection and
configuration of the firewall. A biometric device is added with the network solution for
increasing the security of the network and maintaining the attendance schedule of the students.
The network is also configured with VOIP protocol for communicating with the different
branches.
1.1 Campus Background
Singapore Gaming Academy has 200 nodes in the campus and they are needed to be
connected for improvement of the connectivity and communication in the network. The nodes
are located in different department and they are required to be connected in different vlan for
increasing the security of the network and communicate with the other department securely.
With the implementation of the vlan in the network the network would become flexible and it
can adopt the future expansion of the network easily. Moreover a VPN connection is configured
for the allowing the remote user to access the network elements.
1.2 Current Issue Encounter
The main problem identified in the current network of Singapore Gaming Academy is the
slow network speed and limitation of the bandwidth for supporting the network to send and
COMPUTER NETWORKING
1. Introduction
The report is prepared for Singapore Gaming Academy providing a brief description of
the campus and the current problem faced in the campus. A network solution is proposed for the
university with proper IP addressing scheme for all the interface of the device used for the
configuration of the network solution. A list of the hardware and the protocol used for the
implementation of the network is given for estimation of the cost of the network solution. The
security of the network is also implemented with the application of the password protection and
configuration of the firewall. A biometric device is added with the network solution for
increasing the security of the network and maintaining the attendance schedule of the students.
The network is also configured with VOIP protocol for communicating with the different
branches.
1.1 Campus Background
Singapore Gaming Academy has 200 nodes in the campus and they are needed to be
connected for improvement of the connectivity and communication in the network. The nodes
are located in different department and they are required to be connected in different vlan for
increasing the security of the network and communicate with the other department securely.
With the implementation of the vlan in the network the network would become flexible and it
can adopt the future expansion of the network easily. Moreover a VPN connection is configured
for the allowing the remote user to access the network elements.
1.2 Current Issue Encounter
The main problem identified in the current network of Singapore Gaming Academy is the
slow network speed and limitation of the bandwidth for supporting the network to send and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
COMPUTER NETWORKING
receive multimedia files over the network. The current framework of the organization uses the
token ring infrastructure and it is not suitable for handling congestion in the network and
increase the network downtime. There is risk regarding single point failure because all of the
network traffic passes through the main router and thus if the main router stops working the
whole network would collapse.
The network is connected using a single channel and the devices connected in the
network can get access of the other device in the network and thus the network becomes
vulnerable. There is no network administrator for monitoring the activity of the network and
maintain the access rules in the network.
1.3 Objective
The main objectives followed for the development of the WAN solution for the
Singapore Gaming Academy are listed as follows:
To create a list of hardware required to be installed in the campus for the
mitigation of the problem faced by the users.
To increase the security of the network and deploy biometric device to track the
records of the students and the other users using the system.
To provide wireless access to the users using mobile devices and secure it from
unauthorized access.
To implement VOIP support in the network for communicating with the different
departments and other universities.
COMPUTER NETWORKING
receive multimedia files over the network. The current framework of the organization uses the
token ring infrastructure and it is not suitable for handling congestion in the network and
increase the network downtime. There is risk regarding single point failure because all of the
network traffic passes through the main router and thus if the main router stops working the
whole network would collapse.
The network is connected using a single channel and the devices connected in the
network can get access of the other device in the network and thus the network becomes
vulnerable. There is no network administrator for monitoring the activity of the network and
maintain the access rules in the network.
1.3 Objective
The main objectives followed for the development of the WAN solution for the
Singapore Gaming Academy are listed as follows:
To create a list of hardware required to be installed in the campus for the
mitigation of the problem faced by the users.
To increase the security of the network and deploy biometric device to track the
records of the students and the other users using the system.
To provide wireless access to the users using mobile devices and secure it from
unauthorized access.
To implement VOIP support in the network for communicating with the different
departments and other universities.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
COMPUTER NETWORKING
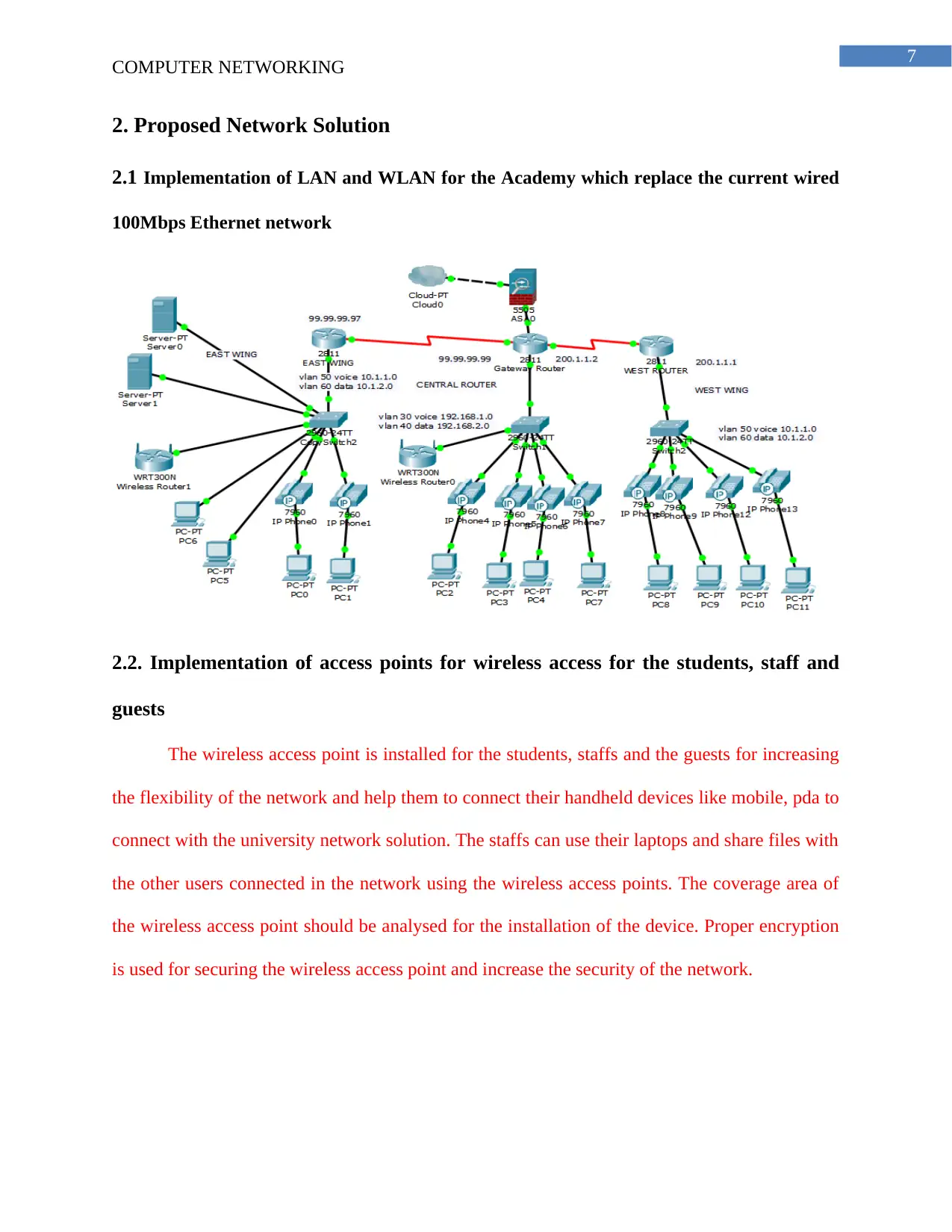
2. Proposed Network Solution
2.1 Implementation of LAN and WLAN for the Academy which replace the current wired
100Mbps Ethernet network
2.2. Implementation of access points for wireless access for the students, staff and
guests
The wireless access point is installed for the students, staffs and the guests for increasing
the flexibility of the network and help them to connect their handheld devices like mobile, pda to
connect with the university network solution. The staffs can use their laptops and share files with
the other users connected in the network using the wireless access points. The coverage area of
the wireless access point should be analysed for the installation of the device. Proper encryption
is used for securing the wireless access point and increase the security of the network.
COMPUTER NETWORKING
2. Proposed Network Solution
2.1 Implementation of LAN and WLAN for the Academy which replace the current wired
100Mbps Ethernet network
2.2. Implementation of access points for wireless access for the students, staff and
guests
The wireless access point is installed for the students, staffs and the guests for increasing
the flexibility of the network and help them to connect their handheld devices like mobile, pda to
connect with the university network solution. The staffs can use their laptops and share files with
the other users connected in the network using the wireless access points. The coverage area of
the wireless access point should be analysed for the installation of the device. Proper encryption
is used for securing the wireless access point and increase the security of the network.
8
COMPUTER NETWORKING
2.3. To link up all the department together on to a backbone network to support
higher volume of data
All the department are connected using a gateway router and different vlan are created for
the voice and data such that there is no congestion in the voip transmission. Each wing have
different router and IP routing is configured in the router such that each of the branches and
departments are connected with each other.
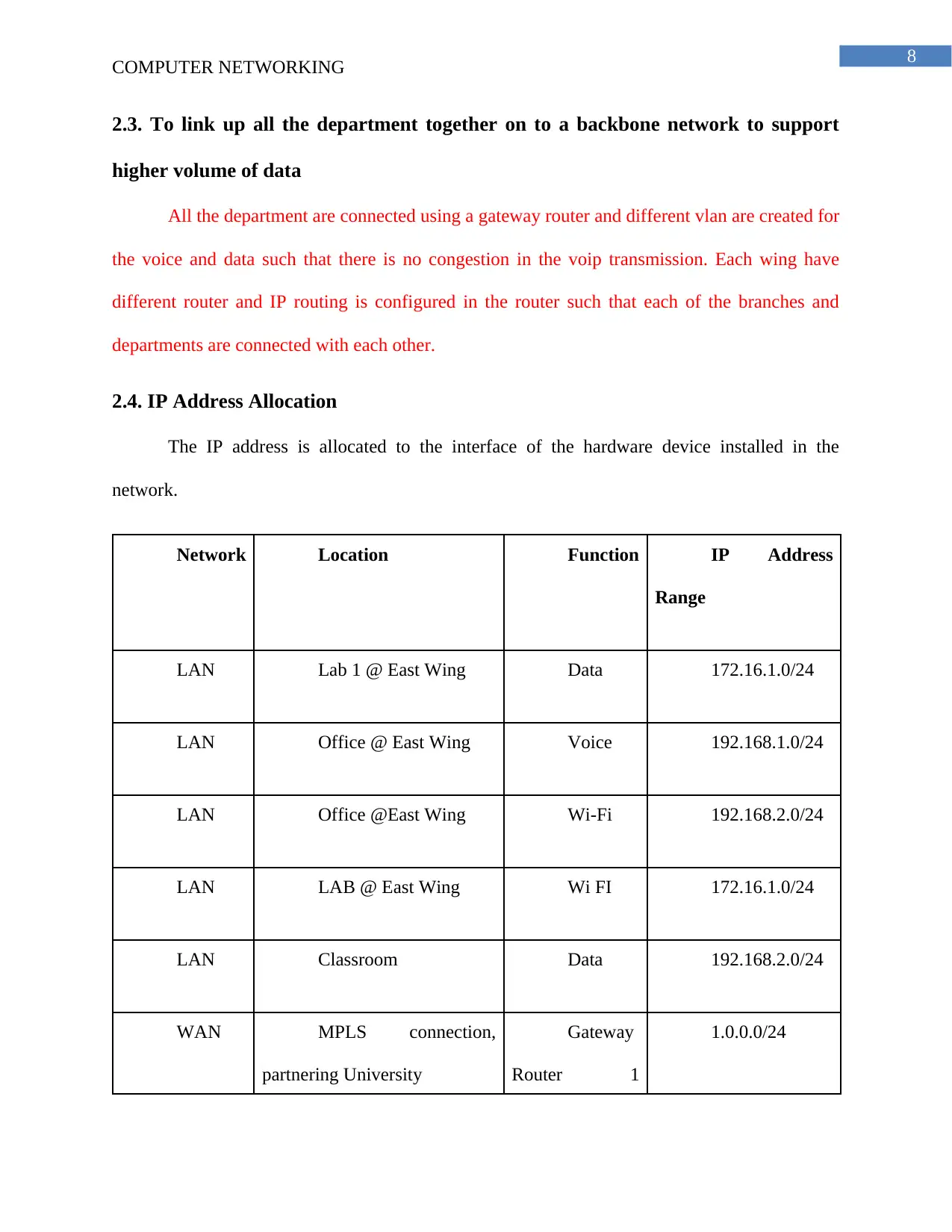
2.4. IP Address Allocation
The IP address is allocated to the interface of the hardware device installed in the
network.
Network Location Function IP Address
Range
LAN Lab 1 @ East Wing Data 172.16.1.0/24
LAN Office @ East Wing Voice 192.168.1.0/24
LAN Office @East Wing Wi-Fi 192.168.2.0/24
LAN LAB @ East Wing Wi FI 172.16.1.0/24
LAN Classroom Data 192.168.2.0/24
WAN MPLS connection,
partnering University
Gateway
Router 1
1.0.0.0/24
COMPUTER NETWORKING
2.3. To link up all the department together on to a backbone network to support
higher volume of data
All the department are connected using a gateway router and different vlan are created for
the voice and data such that there is no congestion in the voip transmission. Each wing have
different router and IP routing is configured in the router such that each of the branches and
departments are connected with each other.
2.4. IP Address Allocation
The IP address is allocated to the interface of the hardware device installed in the
network.
Network Location Function IP Address
Range
LAN Lab 1 @ East Wing Data 172.16.1.0/24
LAN Office @ East Wing Voice 192.168.1.0/24
LAN Office @East Wing Wi-Fi 192.168.2.0/24
LAN LAB @ East Wing Wi FI 172.16.1.0/24
LAN Classroom Data 192.168.2.0/24
WAN MPLS connection,
partnering University
Gateway
Router 1
1.0.0.0/24
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
COMPUTER NETWORKING
connection
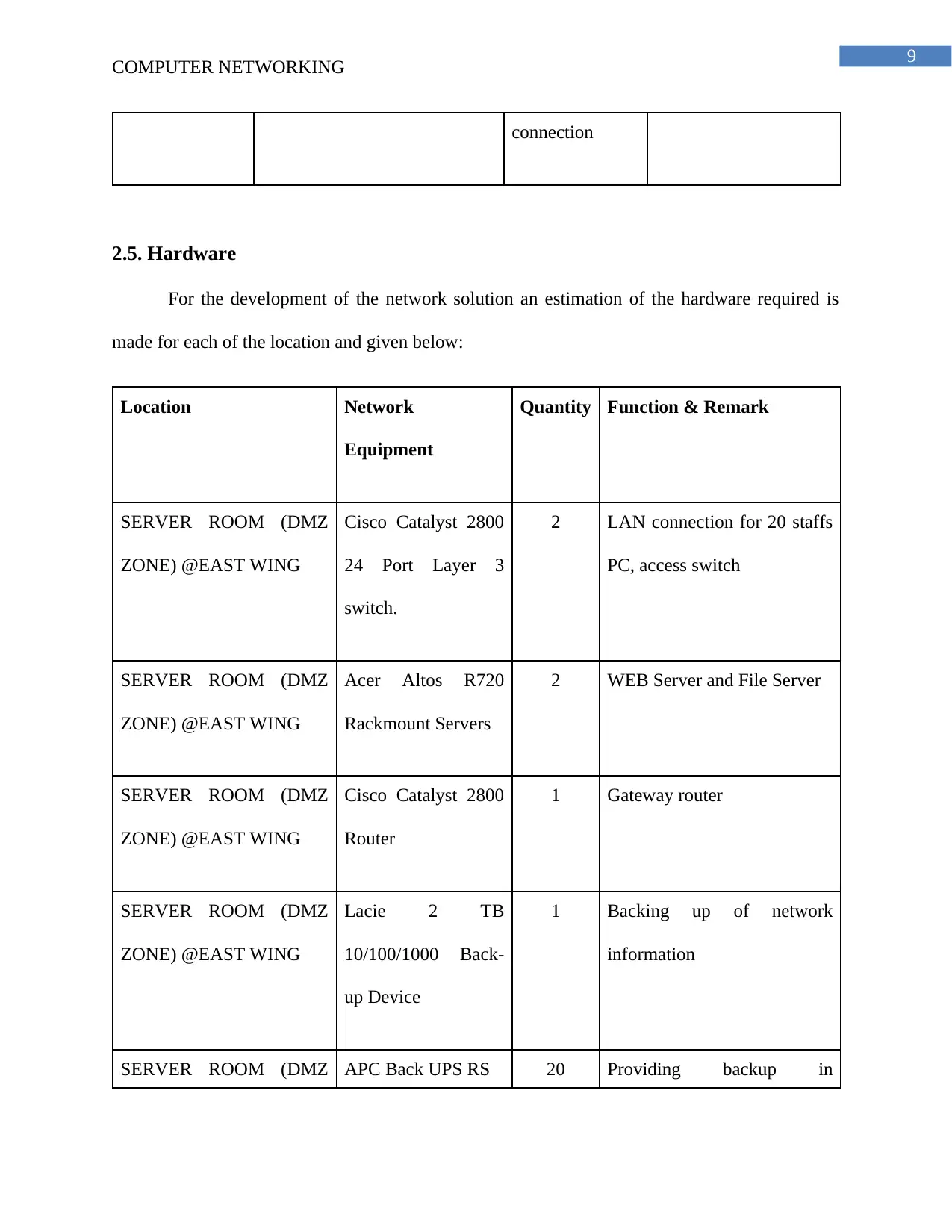
2.5. Hardware
For the development of the network solution an estimation of the hardware required is
made for each of the location and given below:
Location Network
Equipment
Quantity Function & Remark
SERVER ROOM (DMZ
ZONE) @EAST WING
Cisco Catalyst 2800
24 Port Layer 3
switch.
2 LAN connection for 20 staffs
PC, access switch
SERVER ROOM (DMZ
ZONE) @EAST WING
Acer Altos R720
Rackmount Servers
2 WEB Server and File Server
SERVER ROOM (DMZ
ZONE) @EAST WING
Cisco Catalyst 2800
Router
1 Gateway router
SERVER ROOM (DMZ
ZONE) @EAST WING
Lacie 2 TB
10/100/1000 Back-
up Device
1 Backing up of network
information
SERVER ROOM (DMZ APC Back UPS RS 20 Providing backup in
COMPUTER NETWORKING
connection
2.5. Hardware
For the development of the network solution an estimation of the hardware required is
made for each of the location and given below:
Location Network
Equipment
Quantity Function & Remark
SERVER ROOM (DMZ
ZONE) @EAST WING
Cisco Catalyst 2800
24 Port Layer 3
switch.
2 LAN connection for 20 staffs
PC, access switch
SERVER ROOM (DMZ
ZONE) @EAST WING
Acer Altos R720
Rackmount Servers
2 WEB Server and File Server
SERVER ROOM (DMZ
ZONE) @EAST WING
Cisco Catalyst 2800
Router
1 Gateway router
SERVER ROOM (DMZ
ZONE) @EAST WING
Lacie 2 TB
10/100/1000 Back-
up Device
1 Backing up of network
information
SERVER ROOM (DMZ APC Back UPS RS 20 Providing backup in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
COMPUTER NETWORKING
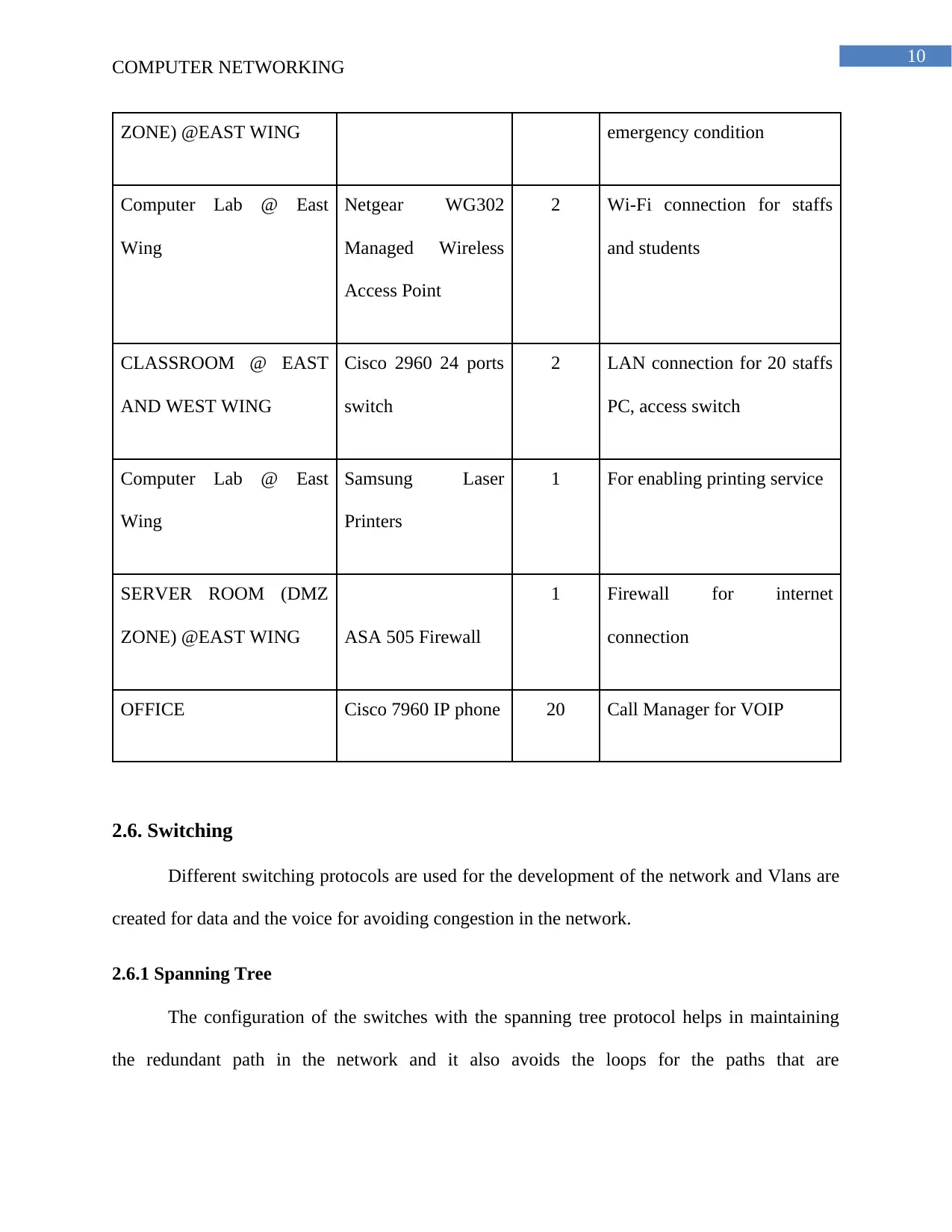
ZONE) @EAST WING emergency condition
Computer Lab @ East
Wing
Netgear WG302
Managed Wireless
Access Point
2 Wi-Fi connection for staffs
and students
CLASSROOM @ EAST
AND WEST WING
Cisco 2960 24 ports
switch
2 LAN connection for 20 staffs
PC, access switch
Computer Lab @ East
Wing
Samsung Laser
Printers
1 For enabling printing service
SERVER ROOM (DMZ
ZONE) @EAST WING ASA 505 Firewall
1 Firewall for internet
connection
OFFICE Cisco 7960 IP phone 20 Call Manager for VOIP
2.6. Switching
Different switching protocols are used for the development of the network and Vlans are
created for data and the voice for avoiding congestion in the network.
2.6.1 Spanning Tree
The configuration of the switches with the spanning tree protocol helps in maintaining
the redundant path in the network and it also avoids the loops for the paths that are
COMPUTER NETWORKING
ZONE) @EAST WING emergency condition
Computer Lab @ East
Wing
Netgear WG302
Managed Wireless
Access Point
2 Wi-Fi connection for staffs
and students
CLASSROOM @ EAST
AND WEST WING
Cisco 2960 24 ports
switch
2 LAN connection for 20 staffs
PC, access switch
Computer Lab @ East
Wing
Samsung Laser
Printers
1 For enabling printing service
SERVER ROOM (DMZ
ZONE) @EAST WING ASA 505 Firewall
1 Firewall for internet
connection
OFFICE Cisco 7960 IP phone 20 Call Manager for VOIP
2.6. Switching
Different switching protocols are used for the development of the network and Vlans are
created for data and the voice for avoiding congestion in the network.
2.6.1 Spanning Tree
The configuration of the switches with the spanning tree protocol helps in maintaining
the redundant path in the network and it also avoids the loops for the paths that are

11
COMPUTER NETWORKING
interconnected with each other. A root bridge is selected for each of the vlan in the network for
communication in the network.
2.6.2 Ether channel
It is used for creation of a high speed Ethernet link by combining more than one channel
for fault tolerance and decrease the congestion in the network. The ether channel can be used on
the layer 3 switch and a virtual link can be created for the increasing the availability of the
bandwidth and reducing the bottleneck situation in the network. With the implementation of the
ether channel the redundancy in the network can be improved and thus decreases the network
downtime.
2.6.3 VLAN
Different VLAN are created for the voice and data such that there is no lag in the voice
channel and sufficient amount of bandwidth is allocated for each of the channel. A small lag in
the voice channel can degrade the quality of communication and thus QoS implemented for
maintaining quality in the network. The port of the switch are allowed access to the voice and the
data vlan for dhcp pool is created for allocating Ip address to the nodes connected on the port.
2.7 Routing
Three routers are used for designing the network and routing is necessary for
communicating with the different interface of the router and redundancy is created between the
routers for connecting with the other university.
2.7.1 EIGRP
Router eigrp is used for the communicating with the other interfaces of the router and it
consumes less resources in the network and it can also adopt the new changes in the network
COMPUTER NETWORKING
interconnected with each other. A root bridge is selected for each of the vlan in the network for
communication in the network.
2.6.2 Ether channel
It is used for creation of a high speed Ethernet link by combining more than one channel
for fault tolerance and decrease the congestion in the network. The ether channel can be used on
the layer 3 switch and a virtual link can be created for the increasing the availability of the
bandwidth and reducing the bottleneck situation in the network. With the implementation of the
ether channel the redundancy in the network can be improved and thus decreases the network
downtime.
2.6.3 VLAN
Different VLAN are created for the voice and data such that there is no lag in the voice
channel and sufficient amount of bandwidth is allocated for each of the channel. A small lag in
the voice channel can degrade the quality of communication and thus QoS implemented for
maintaining quality in the network. The port of the switch are allowed access to the voice and the
data vlan for dhcp pool is created for allocating Ip address to the nodes connected on the port.
2.7 Routing
Three routers are used for designing the network and routing is necessary for
communicating with the different interface of the router and redundancy is created between the
routers for connecting with the other university.
2.7.1 EIGRP
Router eigrp is used for the communicating with the other interfaces of the router and it
consumes less resources in the network and it can also adopt the new changes in the network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




