Risk Assessment and Risk Management Strategy in Cloud Infrastructure
VerifiedAdded on 2021/05/30
|14
|3121
|81
Report
AI Summary
This report delves into the critical aspects of risk assessment and management within cloud infrastructure, a pivotal area in modern IT. It begins by identifying various risks associated with cloud computing, such as security vulnerabilities in physical assets, unauthorized access, application management issues, data confidentiality concerns, and vendor lock-in. The report then outlines a comprehensive risk strategy, including a conceptual framework and a detailed process for managing these risks. It emphasizes the importance of aligning cloud adoption with organizational goals and prioritizing risk resolution. A key element is the evaluation and assessment of risks, employing a likelihood and severity matrix to rank identified threats. Finally, the report proposes a risk mitigation plan, offering specific strategies to address each identified risk, such as implementing cryptographic procedures, using risk identification tools, and securing login credentials. The overall aim is to provide a robust framework for organizations to navigate the challenges of cloud adoption and ensure a secure and efficient digital transformation.

Assignment
Cyber Security
Cyber Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
1. Introduction...................................................................................................................................2
2. Risks Identification........................................................................................................................2
3. Risks Strategy................................................................................................................................4
Conceptual Framework:.....................................................................................................................4
Process of risk management strategy.................................................................................................5
4. Risks evaluation and Assessment..................................................................................................7
5. Risks Mitigation plan.....................................................................................................................8
6. Discussion...................................................................................................................................11
7. Conclusion...................................................................................................................................12
8. References:..................................................................................................................................12
1. Introduction...................................................................................................................................2
2. Risks Identification........................................................................................................................2
3. Risks Strategy................................................................................................................................4
Conceptual Framework:.....................................................................................................................4
Process of risk management strategy.................................................................................................5
4. Risks evaluation and Assessment..................................................................................................7
5. Risks Mitigation plan.....................................................................................................................8
6. Discussion...................................................................................................................................11
7. Conclusion...................................................................................................................................12
8. References:..................................................................................................................................12

Title: Risk assessment and risk management strategy associated with cloud infrastructure
1. Introduction
Every organization is looking forward to transform their traditional business tactics with the
ICT technology. The Cloud computing technology is the emerging trend for developing
digitization in the organization. The platform of cloud computing provides new innovation,
scalability, flexibility, reliability, of information for improving the working tactics of the
enterprise. The advantages of using cloud computing technology are managing abstraction of
resources, managing scalability and flexibility of the business process, improving instant
provision mechanism for innovation, sharing of hardware, software, network resources,
providing on-demand service, managing virtualization of the business processes and
resources, and others. The cloud computing environment helps in managing effective
relationship between different business units of the enterprise with the inclusion of software
as a service model, infrastructure as a service model, and platform as a service model. With
the increasing growth of digitization, the security is the major concern associated with the
preservation of the confidential information of the organization. The identification and
mitigation of the risks is the important part of the business process for achieving success in
the undertaking project. In this paper, we are looking forward to analyse the risks
identification and management of cloud computing infrastructure.
2. Risks Identification
The adoption of cloud computing architecture helps in transforming traditional business
tactics with the digital environment. The following table shows the risks identified which are
associated with the cloud computing infrastructure:
Risks Identification Description
Security associated with
physical assets
The hardware, software, and network resources uploaded on the
cloud platform are associated with the security risks. The third
party can get unauthorised access of using the devices
Identification security
risks
The user can get unauthorised access by using false identity
1. Introduction
Every organization is looking forward to transform their traditional business tactics with the
ICT technology. The Cloud computing technology is the emerging trend for developing
digitization in the organization. The platform of cloud computing provides new innovation,
scalability, flexibility, reliability, of information for improving the working tactics of the
enterprise. The advantages of using cloud computing technology are managing abstraction of
resources, managing scalability and flexibility of the business process, improving instant
provision mechanism for innovation, sharing of hardware, software, network resources,
providing on-demand service, managing virtualization of the business processes and
resources, and others. The cloud computing environment helps in managing effective
relationship between different business units of the enterprise with the inclusion of software
as a service model, infrastructure as a service model, and platform as a service model. With
the increasing growth of digitization, the security is the major concern associated with the
preservation of the confidential information of the organization. The identification and
mitigation of the risks is the important part of the business process for achieving success in
the undertaking project. In this paper, we are looking forward to analyse the risks
identification and management of cloud computing infrastructure.
2. Risks Identification
The adoption of cloud computing architecture helps in transforming traditional business
tactics with the digital environment. The following table shows the risks identified which are
associated with the cloud computing infrastructure:
Risks Identification Description
Security associated with
physical assets
The hardware, software, and network resources uploaded on the
cloud platform are associated with the security risks. The third
party can get unauthorised access of using the devices
Identification security
risks
The user can get unauthorised access by using false identity
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
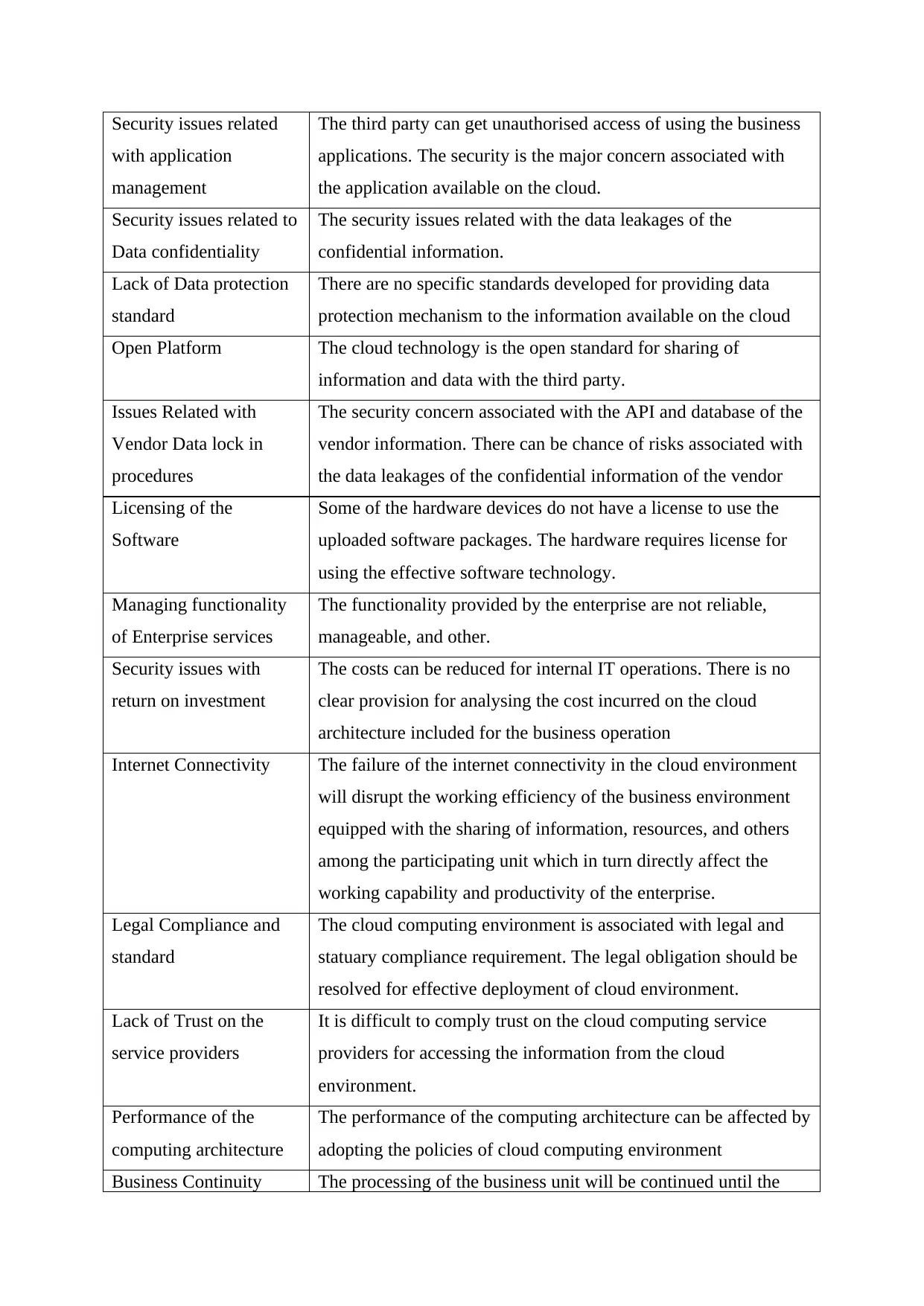
Security issues related
with application
management
The third party can get unauthorised access of using the business
applications. The security is the major concern associated with
the application available on the cloud.
Security issues related to
Data confidentiality
The security issues related with the data leakages of the
confidential information.
Lack of Data protection
standard
There are no specific standards developed for providing data
protection mechanism to the information available on the cloud
Open Platform The cloud technology is the open standard for sharing of
information and data with the third party.
Issues Related with
Vendor Data lock in
procedures
The security concern associated with the API and database of the
vendor information. There can be chance of risks associated with
the data leakages of the confidential information of the vendor
Licensing of the
Software
Some of the hardware devices do not have a license to use the
uploaded software packages. The hardware requires license for
using the effective software technology.
Managing functionality
of Enterprise services
The functionality provided by the enterprise are not reliable,
manageable, and other.
Security issues with
return on investment
The costs can be reduced for internal IT operations. There is no
clear provision for analysing the cost incurred on the cloud
architecture included for the business operation
Internet Connectivity The failure of the internet connectivity in the cloud environment
will disrupt the working efficiency of the business environment
equipped with the sharing of information, resources, and others
among the participating unit which in turn directly affect the
working capability and productivity of the enterprise.
Legal Compliance and
standard
The cloud computing environment is associated with legal and
statuary compliance requirement. The legal obligation should be
resolved for effective deployment of cloud environment.
Lack of Trust on the
service providers
It is difficult to comply trust on the cloud computing service
providers for accessing the information from the cloud
environment.
Performance of the
computing architecture
The performance of the computing architecture can be affected by
adopting the policies of cloud computing environment
Business Continuity The processing of the business unit will be continued until the
with application
management
The third party can get unauthorised access of using the business
applications. The security is the major concern associated with
the application available on the cloud.
Security issues related to
Data confidentiality
The security issues related with the data leakages of the
confidential information.
Lack of Data protection
standard
There are no specific standards developed for providing data
protection mechanism to the information available on the cloud
Open Platform The cloud technology is the open standard for sharing of
information and data with the third party.
Issues Related with
Vendor Data lock in
procedures
The security concern associated with the API and database of the
vendor information. There can be chance of risks associated with
the data leakages of the confidential information of the vendor
Licensing of the
Software
Some of the hardware devices do not have a license to use the
uploaded software packages. The hardware requires license for
using the effective software technology.
Managing functionality
of Enterprise services
The functionality provided by the enterprise are not reliable,
manageable, and other.
Security issues with
return on investment
The costs can be reduced for internal IT operations. There is no
clear provision for analysing the cost incurred on the cloud
architecture included for the business operation
Internet Connectivity The failure of the internet connectivity in the cloud environment
will disrupt the working efficiency of the business environment
equipped with the sharing of information, resources, and others
among the participating unit which in turn directly affect the
working capability and productivity of the enterprise.
Legal Compliance and
standard
The cloud computing environment is associated with legal and
statuary compliance requirement. The legal obligation should be
resolved for effective deployment of cloud environment.
Lack of Trust on the
service providers
It is difficult to comply trust on the cloud computing service
providers for accessing the information from the cloud
environment.
Performance of the
computing architecture
The performance of the computing architecture can be affected by
adopting the policies of cloud computing environment
Business Continuity The processing of the business unit will be continued until the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

program availability of the resources and internet connectivity. The failure
of the internet connectivity in the cloud environment will disrupt
the working efficiency of the business environment equipped with
the sharing of information, resources, and others among the
participating unit which in turn directly affect the working
capability and productivity of the enterprise.
3. Risks Strategy
The adoption of the business tactic to the cloud environment requires readiness for the new
working environment to reduce the occurrence of risks associated with the change in
organization culture. The migration to the cloud infrastructure requires the analysis of the
risks associated with it. The next step is to develop a strategy for coping up with the risks
determined with the working of the cloud environment so as to minimize the impact of the
associated risks. The conceptual framework should be developed for analysing the efficiency
of the risks management plan.
Conceptual Framework:
The conceptual framework should be developed for analysing the efficiency of the risks
management plan. The management of the risks can be identified by focusing on the risks,
migration policies, and control. The application of the cloud computing environment should
aligns with the goal and mission of the organization (Zolghadri, and Vahdani, 2015). The
identified risks should be provided priority for resolution. It helps in controlling the impact of
the risks associated with the business risks. The migration to the cloud platform is indulged
with effective decision risks. The deployment of the conceptual model helps in analysing the
facts associated with the concern area of improvement.
The following figure shows the conceptual model and framework required for risk
identification and management.
of the internet connectivity in the cloud environment will disrupt
the working efficiency of the business environment equipped with
the sharing of information, resources, and others among the
participating unit which in turn directly affect the working
capability and productivity of the enterprise.
3. Risks Strategy
The adoption of the business tactic to the cloud environment requires readiness for the new
working environment to reduce the occurrence of risks associated with the change in
organization culture. The migration to the cloud infrastructure requires the analysis of the
risks associated with it. The next step is to develop a strategy for coping up with the risks
determined with the working of the cloud environment so as to minimize the impact of the
associated risks. The conceptual framework should be developed for analysing the efficiency
of the risks management plan.
Conceptual Framework:
The conceptual framework should be developed for analysing the efficiency of the risks
management plan. The management of the risks can be identified by focusing on the risks,
migration policies, and control. The application of the cloud computing environment should
aligns with the goal and mission of the organization (Zolghadri, and Vahdani, 2015). The
identified risks should be provided priority for resolution. It helps in controlling the impact of
the risks associated with the business risks. The migration to the cloud platform is indulged
with effective decision risks. The deployment of the conceptual model helps in analysing the
facts associated with the concern area of improvement.
The following figure shows the conceptual model and framework required for risk
identification and management.
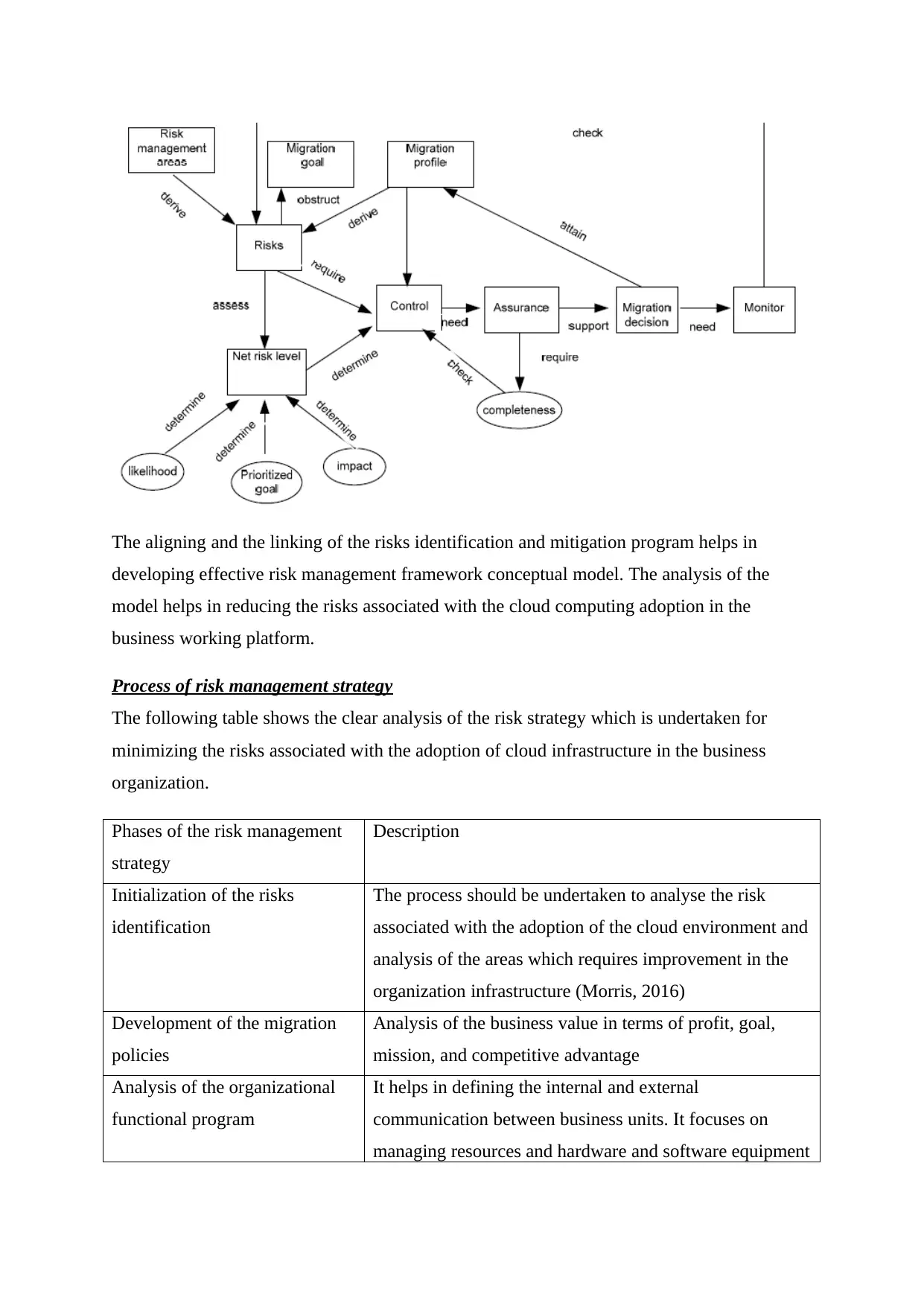
The aligning and the linking of the risks identification and mitigation program helps in
developing effective risk management framework conceptual model. The analysis of the
model helps in reducing the risks associated with the cloud computing adoption in the
business working platform.
Process of risk management strategy
The following table shows the clear analysis of the risk strategy which is undertaken for
minimizing the risks associated with the adoption of cloud infrastructure in the business
organization.
Phases of the risk management
strategy
Description
Initialization of the risks
identification
The process should be undertaken to analyse the risk
associated with the adoption of the cloud environment and
analysis of the areas which requires improvement in the
organization infrastructure (Morris, 2016)
Development of the migration
policies
Analysis of the business value in terms of profit, goal,
mission, and competitive advantage
Analysis of the organizational
functional program
It helps in defining the internal and external
communication between business units. It focuses on
managing resources and hardware and software equipment
developing effective risk management framework conceptual model. The analysis of the
model helps in reducing the risks associated with the cloud computing adoption in the
business working platform.
Process of risk management strategy
The following table shows the clear analysis of the risk strategy which is undertaken for
minimizing the risks associated with the adoption of cloud infrastructure in the business
organization.
Phases of the risk management
strategy
Description
Initialization of the risks
identification
The process should be undertaken to analyse the risk
associated with the adoption of the cloud environment and
analysis of the areas which requires improvement in the
organization infrastructure (Morris, 2016)
Development of the migration
policies
Analysis of the business value in terms of profit, goal,
mission, and competitive advantage
Analysis of the organizational
functional program
It helps in defining the internal and external
communication between business units. It focuses on
managing resources and hardware and software equipment
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
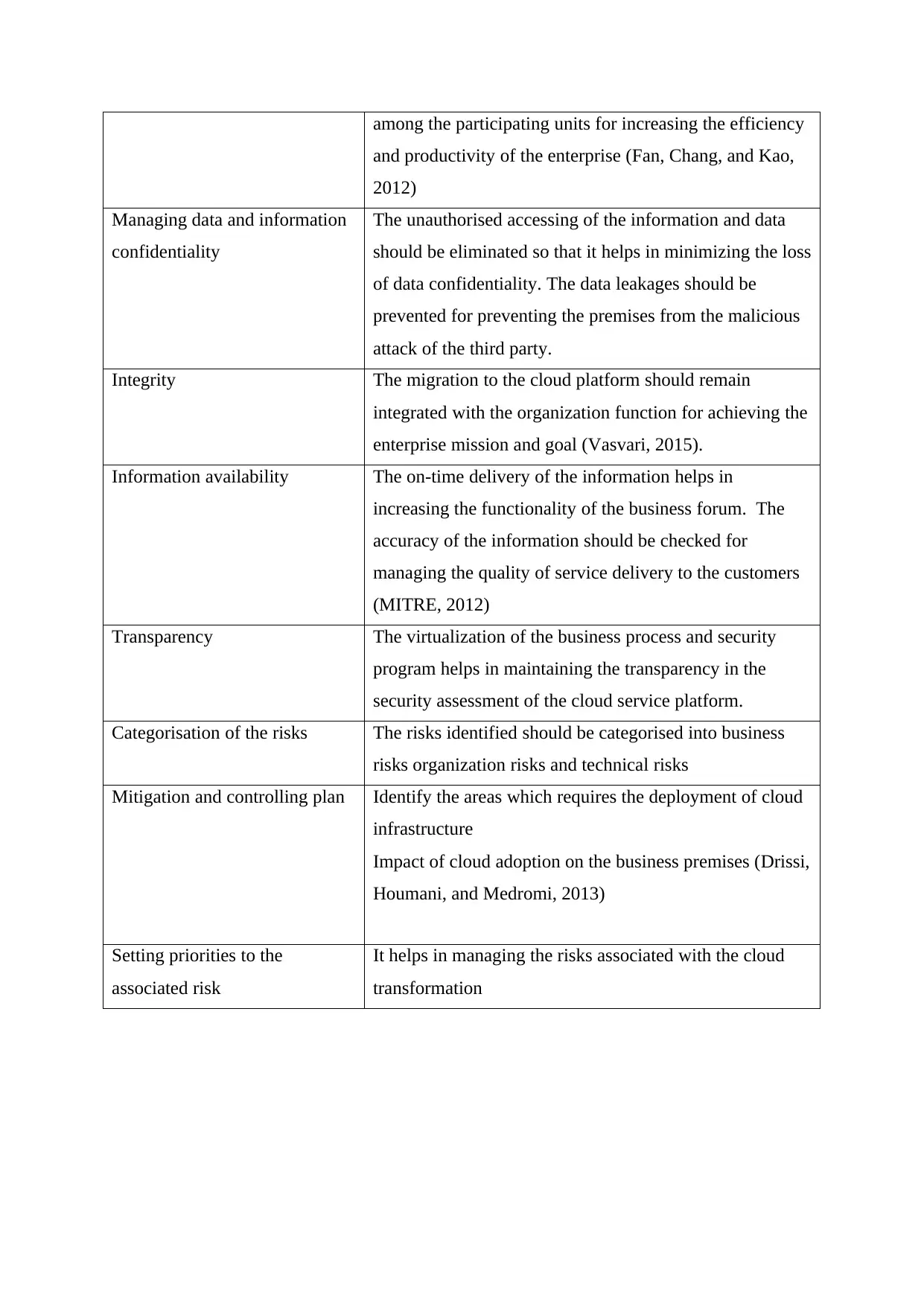
among the participating units for increasing the efficiency
and productivity of the enterprise (Fan, Chang, and Kao,
2012)
Managing data and information
confidentiality
The unauthorised accessing of the information and data
should be eliminated so that it helps in minimizing the loss
of data confidentiality. The data leakages should be
prevented for preventing the premises from the malicious
attack of the third party.
Integrity The migration to the cloud platform should remain
integrated with the organization function for achieving the
enterprise mission and goal (Vasvari, 2015).
Information availability The on-time delivery of the information helps in
increasing the functionality of the business forum. The
accuracy of the information should be checked for
managing the quality of service delivery to the customers
(MITRE, 2012)
Transparency The virtualization of the business process and security
program helps in maintaining the transparency in the
security assessment of the cloud service platform.
Categorisation of the risks The risks identified should be categorised into business
risks organization risks and technical risks
Mitigation and controlling plan Identify the areas which requires the deployment of cloud
infrastructure
Impact of cloud adoption on the business premises (Drissi,
Houmani, and Medromi, 2013)
Setting priorities to the
associated risk
It helps in managing the risks associated with the cloud
transformation
and productivity of the enterprise (Fan, Chang, and Kao,
2012)
Managing data and information
confidentiality
The unauthorised accessing of the information and data
should be eliminated so that it helps in minimizing the loss
of data confidentiality. The data leakages should be
prevented for preventing the premises from the malicious
attack of the third party.
Integrity The migration to the cloud platform should remain
integrated with the organization function for achieving the
enterprise mission and goal (Vasvari, 2015).
Information availability The on-time delivery of the information helps in
increasing the functionality of the business forum. The
accuracy of the information should be checked for
managing the quality of service delivery to the customers
(MITRE, 2012)
Transparency The virtualization of the business process and security
program helps in maintaining the transparency in the
security assessment of the cloud service platform.
Categorisation of the risks The risks identified should be categorised into business
risks organization risks and technical risks
Mitigation and controlling plan Identify the areas which requires the deployment of cloud
infrastructure
Impact of cloud adoption on the business premises (Drissi,
Houmani, and Medromi, 2013)
Setting priorities to the
associated risk
It helps in managing the risks associated with the cloud
transformation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
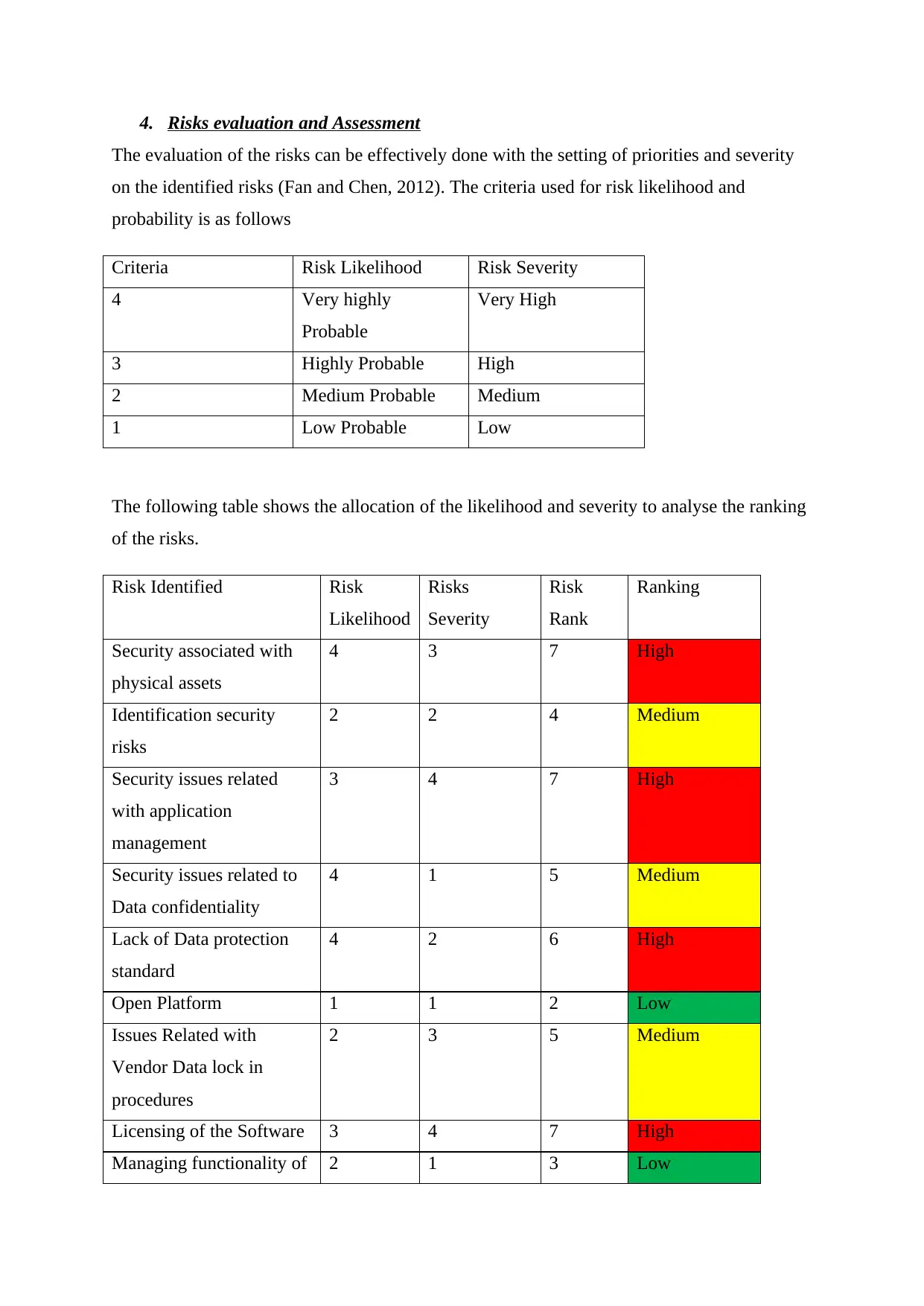
4. Risks evaluation and Assessment
The evaluation of the risks can be effectively done with the setting of priorities and severity
on the identified risks (Fan and Chen, 2012). The criteria used for risk likelihood and
probability is as follows
Criteria Risk Likelihood Risk Severity
4 Very highly
Probable
Very High
3 Highly Probable High
2 Medium Probable Medium
1 Low Probable Low
The following table shows the allocation of the likelihood and severity to analyse the ranking
of the risks.
Risk Identified Risk
Likelihood
Risks
Severity
Risk
Rank
Ranking
Security associated with
physical assets
4 3 7 High
Identification security
risks
2 2 4 Medium
Security issues related
with application
management
3 4 7 High
Security issues related to
Data confidentiality
4 1 5 Medium
Lack of Data protection
standard
4 2 6 High
Open Platform 1 1 2 Low
Issues Related with
Vendor Data lock in
procedures
2 3 5 Medium
Licensing of the Software 3 4 7 High
Managing functionality of 2 1 3 Low
The evaluation of the risks can be effectively done with the setting of priorities and severity
on the identified risks (Fan and Chen, 2012). The criteria used for risk likelihood and
probability is as follows
Criteria Risk Likelihood Risk Severity
4 Very highly
Probable
Very High
3 Highly Probable High
2 Medium Probable Medium
1 Low Probable Low
The following table shows the allocation of the likelihood and severity to analyse the ranking
of the risks.
Risk Identified Risk
Likelihood
Risks
Severity
Risk
Rank
Ranking
Security associated with
physical assets
4 3 7 High
Identification security
risks
2 2 4 Medium
Security issues related
with application
management
3 4 7 High
Security issues related to
Data confidentiality
4 1 5 Medium
Lack of Data protection
standard
4 2 6 High
Open Platform 1 1 2 Low
Issues Related with
Vendor Data lock in
procedures
2 3 5 Medium
Licensing of the Software 3 4 7 High
Managing functionality of 2 1 3 Low
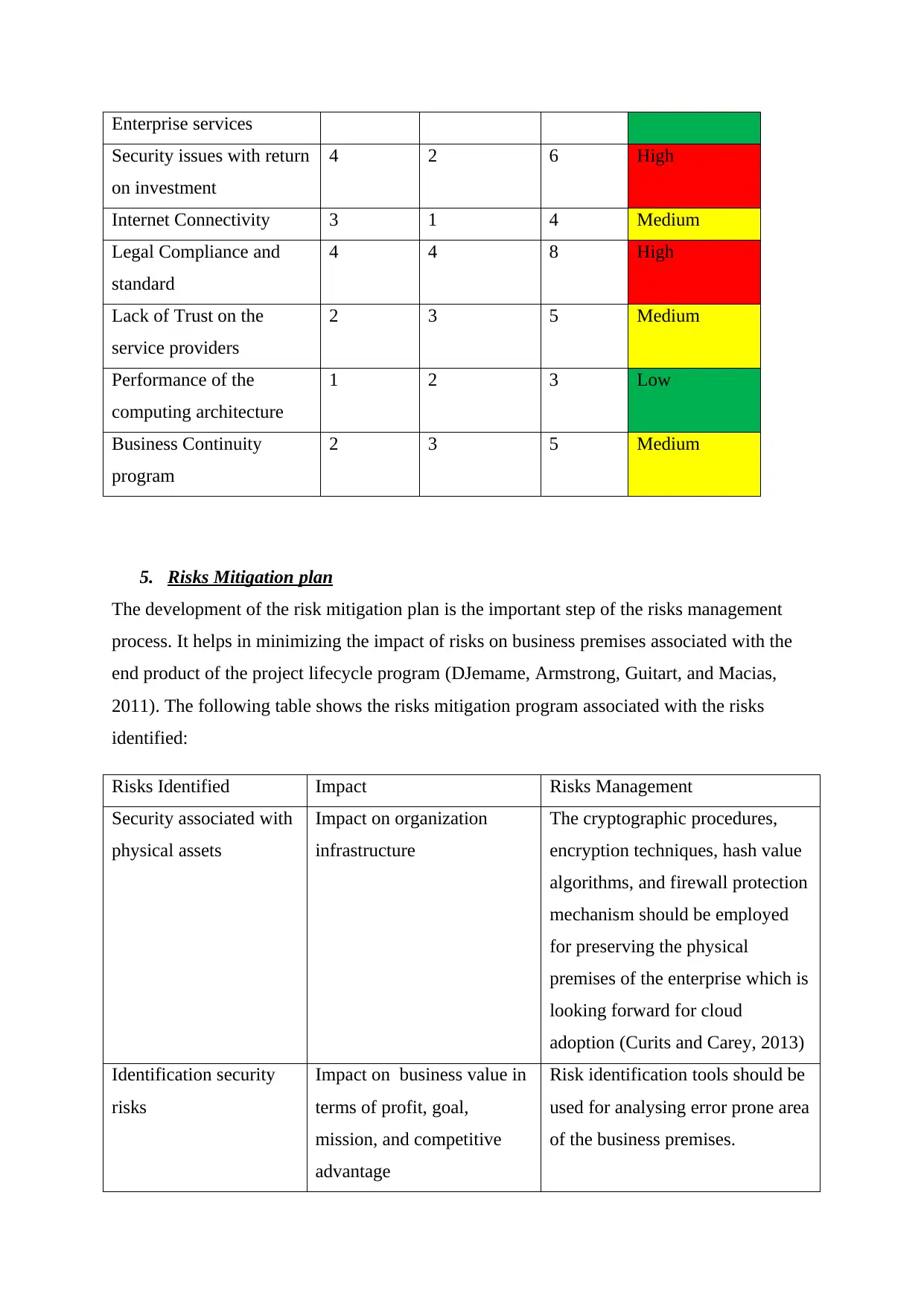
Enterprise services
Security issues with return
on investment
4 2 6 High
Internet Connectivity 3 1 4 Medium
Legal Compliance and
standard
4 4 8 High
Lack of Trust on the
service providers
2 3 5 Medium
Performance of the
computing architecture
1 2 3 Low
Business Continuity
program
2 3 5 Medium
5. Risks Mitigation plan
The development of the risk mitigation plan is the important step of the risks management
process. It helps in minimizing the impact of risks on business premises associated with the
end product of the project lifecycle program (DJemame, Armstrong, Guitart, and Macias,
2011). The following table shows the risks mitigation program associated with the risks
identified:
Risks Identified Impact Risks Management
Security associated with
physical assets
Impact on organization
infrastructure
The cryptographic procedures,
encryption techniques, hash value
algorithms, and firewall protection
mechanism should be employed
for preserving the physical
premises of the enterprise which is
looking forward for cloud
adoption (Curits and Carey, 2013)
Identification security
risks
Impact on business value in
terms of profit, goal,
mission, and competitive
advantage
Risk identification tools should be
used for analysing error prone area
of the business premises.
Security issues with return
on investment
4 2 6 High
Internet Connectivity 3 1 4 Medium
Legal Compliance and
standard
4 4 8 High
Lack of Trust on the
service providers
2 3 5 Medium
Performance of the
computing architecture
1 2 3 Low
Business Continuity
program
2 3 5 Medium
5. Risks Mitigation plan
The development of the risk mitigation plan is the important step of the risks management
process. It helps in minimizing the impact of risks on business premises associated with the
end product of the project lifecycle program (DJemame, Armstrong, Guitart, and Macias,
2011). The following table shows the risks mitigation program associated with the risks
identified:
Risks Identified Impact Risks Management
Security associated with
physical assets
Impact on organization
infrastructure
The cryptographic procedures,
encryption techniques, hash value
algorithms, and firewall protection
mechanism should be employed
for preserving the physical
premises of the enterprise which is
looking forward for cloud
adoption (Curits and Carey, 2013)
Identification security
risks
Impact on business value in
terms of profit, goal,
mission, and competitive
advantage
Risk identification tools should be
used for analysing error prone area
of the business premises.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
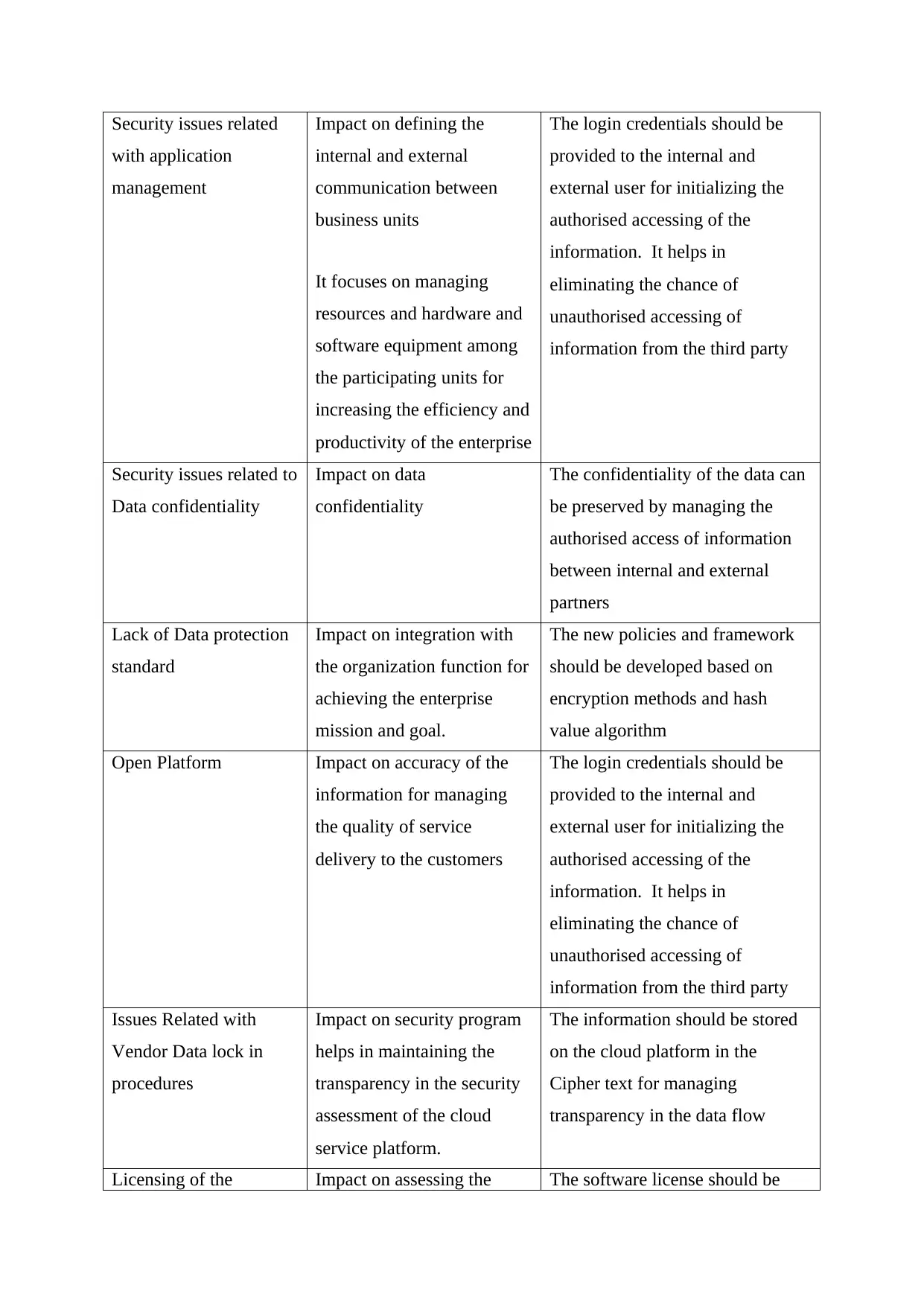
Security issues related
with application
management
Impact on defining the
internal and external
communication between
business units
It focuses on managing
resources and hardware and
software equipment among
the participating units for
increasing the efficiency and
productivity of the enterprise
The login credentials should be
provided to the internal and
external user for initializing the
authorised accessing of the
information. It helps in
eliminating the chance of
unauthorised accessing of
information from the third party
Security issues related to
Data confidentiality
Impact on data
confidentiality
The confidentiality of the data can
be preserved by managing the
authorised access of information
between internal and external
partners
Lack of Data protection
standard
Impact on integration with
the organization function for
achieving the enterprise
mission and goal.
The new policies and framework
should be developed based on
encryption methods and hash
value algorithm
Open Platform Impact on accuracy of the
information for managing
the quality of service
delivery to the customers
The login credentials should be
provided to the internal and
external user for initializing the
authorised accessing of the
information. It helps in
eliminating the chance of
unauthorised accessing of
information from the third party
Issues Related with
Vendor Data lock in
procedures
Impact on security program
helps in maintaining the
transparency in the security
assessment of the cloud
service platform.
The information should be stored
on the cloud platform in the
Cipher text for managing
transparency in the data flow
Licensing of the Impact on assessing the The software license should be
with application
management
Impact on defining the
internal and external
communication between
business units
It focuses on managing
resources and hardware and
software equipment among
the participating units for
increasing the efficiency and
productivity of the enterprise
The login credentials should be
provided to the internal and
external user for initializing the
authorised accessing of the
information. It helps in
eliminating the chance of
unauthorised accessing of
information from the third party
Security issues related to
Data confidentiality
Impact on data
confidentiality
The confidentiality of the data can
be preserved by managing the
authorised access of information
between internal and external
partners
Lack of Data protection
standard
Impact on integration with
the organization function for
achieving the enterprise
mission and goal.
The new policies and framework
should be developed based on
encryption methods and hash
value algorithm
Open Platform Impact on accuracy of the
information for managing
the quality of service
delivery to the customers
The login credentials should be
provided to the internal and
external user for initializing the
authorised accessing of the
information. It helps in
eliminating the chance of
unauthorised accessing of
information from the third party
Issues Related with
Vendor Data lock in
procedures
Impact on security program
helps in maintaining the
transparency in the security
assessment of the cloud
service platform.
The information should be stored
on the cloud platform in the
Cipher text for managing
transparency in the data flow
Licensing of the Impact on assessing the The software license should be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
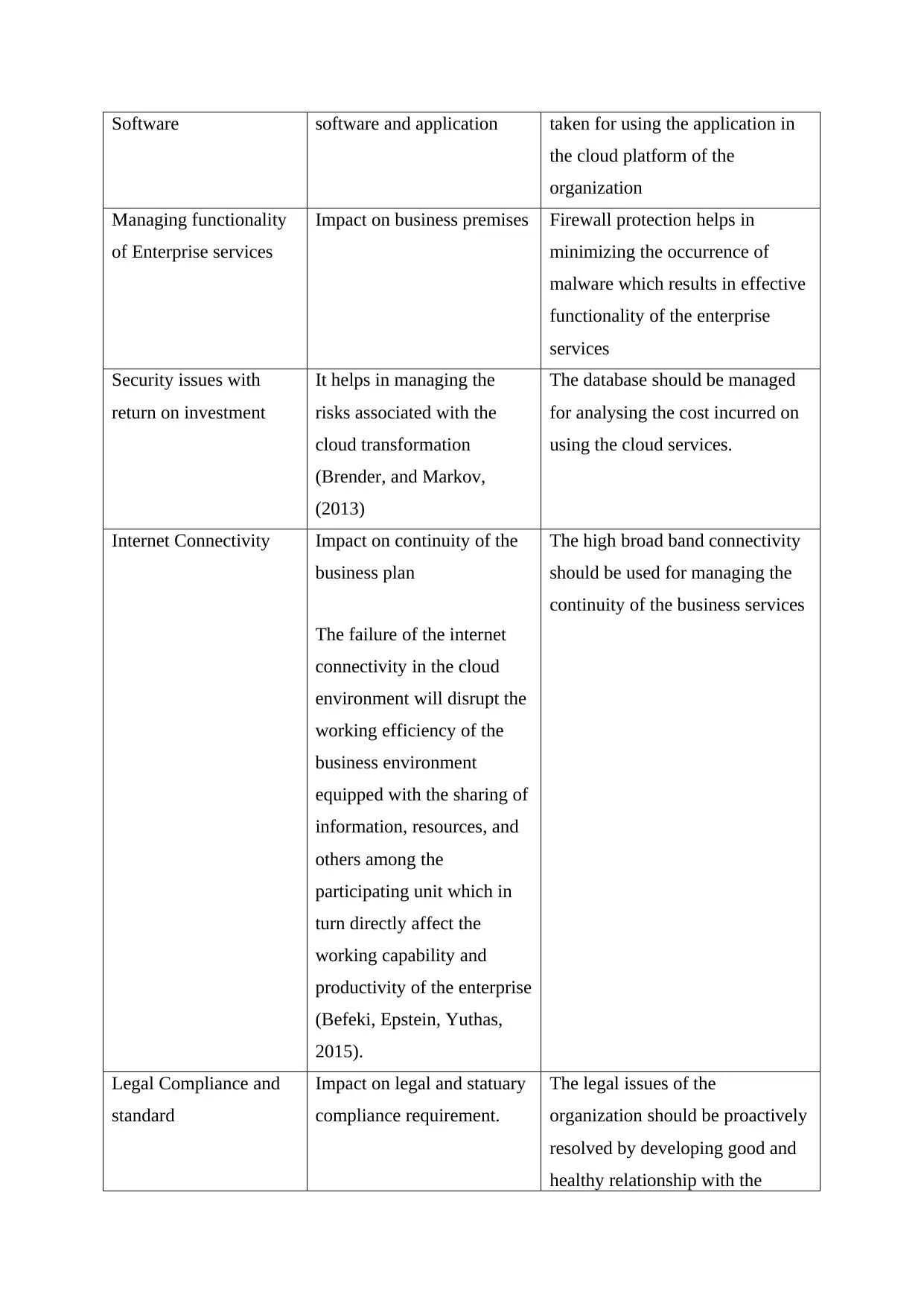
Software software and application taken for using the application in
the cloud platform of the
organization
Managing functionality
of Enterprise services
Impact on business premises Firewall protection helps in
minimizing the occurrence of
malware which results in effective
functionality of the enterprise
services
Security issues with
return on investment
It helps in managing the
risks associated with the
cloud transformation
(Brender, and Markov,
(2013)
The database should be managed
for analysing the cost incurred on
using the cloud services.
Internet Connectivity Impact on continuity of the
business plan
The failure of the internet
connectivity in the cloud
environment will disrupt the
working efficiency of the
business environment
equipped with the sharing of
information, resources, and
others among the
participating unit which in
turn directly affect the
working capability and
productivity of the enterprise
(Befeki, Epstein, Yuthas,
2015).
The high broad band connectivity
should be used for managing the
continuity of the business services
Legal Compliance and
standard
Impact on legal and statuary
compliance requirement.
The legal issues of the
organization should be proactively
resolved by developing good and
healthy relationship with the
the cloud platform of the
organization
Managing functionality
of Enterprise services
Impact on business premises Firewall protection helps in
minimizing the occurrence of
malware which results in effective
functionality of the enterprise
services
Security issues with
return on investment
It helps in managing the
risks associated with the
cloud transformation
(Brender, and Markov,
(2013)
The database should be managed
for analysing the cost incurred on
using the cloud services.
Internet Connectivity Impact on continuity of the
business plan
The failure of the internet
connectivity in the cloud
environment will disrupt the
working efficiency of the
business environment
equipped with the sharing of
information, resources, and
others among the
participating unit which in
turn directly affect the
working capability and
productivity of the enterprise
(Befeki, Epstein, Yuthas,
2015).
The high broad band connectivity
should be used for managing the
continuity of the business services
Legal Compliance and
standard
Impact on legal and statuary
compliance requirement.
The legal issues of the
organization should be proactively
resolved by developing good and
healthy relationship with the
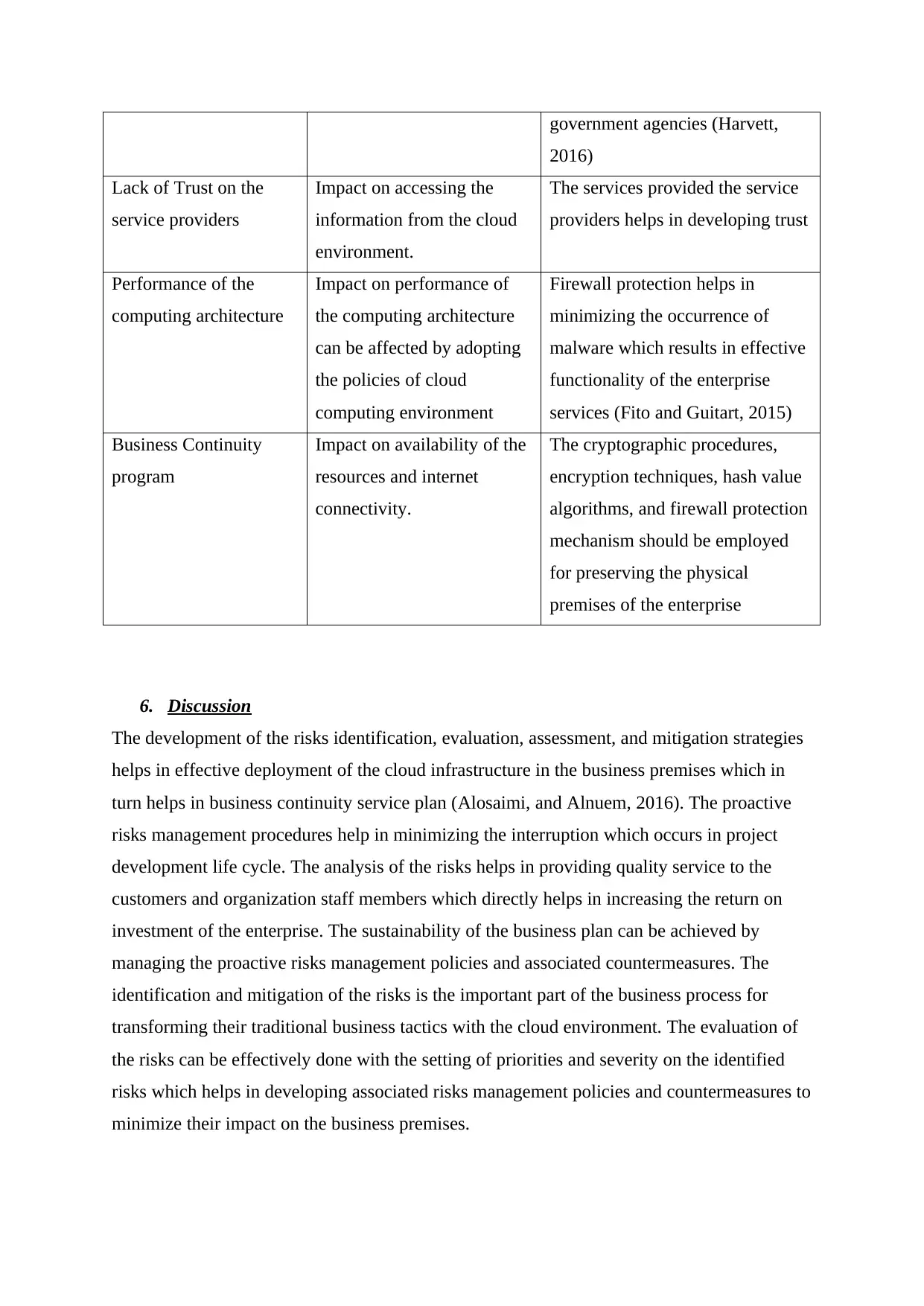
government agencies (Harvett,
2016)
Lack of Trust on the
service providers
Impact on accessing the
information from the cloud
environment.
The services provided the service
providers helps in developing trust
Performance of the
computing architecture
Impact on performance of
the computing architecture
can be affected by adopting
the policies of cloud
computing environment
Firewall protection helps in
minimizing the occurrence of
malware which results in effective
functionality of the enterprise
services (Fito and Guitart, 2015)
Business Continuity
program
Impact on availability of the
resources and internet
connectivity.
The cryptographic procedures,
encryption techniques, hash value
algorithms, and firewall protection
mechanism should be employed
for preserving the physical
premises of the enterprise
6. Discussion
The development of the risks identification, evaluation, assessment, and mitigation strategies
helps in effective deployment of the cloud infrastructure in the business premises which in
turn helps in business continuity service plan (Alosaimi, and Alnuem, 2016). The proactive
risks management procedures help in minimizing the interruption which occurs in project
development life cycle. The analysis of the risks helps in providing quality service to the
customers and organization staff members which directly helps in increasing the return on
investment of the enterprise. The sustainability of the business plan can be achieved by
managing the proactive risks management policies and associated countermeasures. The
identification and mitigation of the risks is the important part of the business process for
transforming their traditional business tactics with the cloud environment. The evaluation of
the risks can be effectively done with the setting of priorities and severity on the identified
risks which helps in developing associated risks management policies and countermeasures to
minimize their impact on the business premises.
2016)
Lack of Trust on the
service providers
Impact on accessing the
information from the cloud
environment.
The services provided the service
providers helps in developing trust
Performance of the
computing architecture
Impact on performance of
the computing architecture
can be affected by adopting
the policies of cloud
computing environment
Firewall protection helps in
minimizing the occurrence of
malware which results in effective
functionality of the enterprise
services (Fito and Guitart, 2015)
Business Continuity
program
Impact on availability of the
resources and internet
connectivity.
The cryptographic procedures,
encryption techniques, hash value
algorithms, and firewall protection
mechanism should be employed
for preserving the physical
premises of the enterprise
6. Discussion
The development of the risks identification, evaluation, assessment, and mitigation strategies
helps in effective deployment of the cloud infrastructure in the business premises which in
turn helps in business continuity service plan (Alosaimi, and Alnuem, 2016). The proactive
risks management procedures help in minimizing the interruption which occurs in project
development life cycle. The analysis of the risks helps in providing quality service to the
customers and organization staff members which directly helps in increasing the return on
investment of the enterprise. The sustainability of the business plan can be achieved by
managing the proactive risks management policies and associated countermeasures. The
identification and mitigation of the risks is the important part of the business process for
transforming their traditional business tactics with the cloud environment. The evaluation of
the risks can be effectively done with the setting of priorities and severity on the identified
risks which helps in developing associated risks management policies and countermeasures to
minimize their impact on the business premises.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




